CHAPTER 9
Protecting Remote Access
As you learned earlier in Part II, computers do not have to be connected to other computers to be at risk. Although many computers might not be part of a corporate network, almost all modern personal computers at least occasionally get attached to the largest data network in the world: the Internet. As such, these standalone computing and control devices are exposed to corruption and exploitation from remote sources.
- Analyze and Differentiate Between Anti-Virus/Anti-Malware Products.
- Secure the Web Browser of a Standalone Computing Device.
- Configure and Test a Local Firewall Installation.
- Explain the Importance of Application Security.
- Audit Local Operating System Services and Events.
- Establish a Local Security Policy on a Standalone Host Device.
- Describe the Importance of Conducting Local Updates and Patch Maintenance Activities.
Protecting Local Computing Devices
There are nine basic steps for protecting local computing devices from Internet-based threats:
- Use a secure connection.
- Establish and configure a firewall to control the flow of information between the computing device and the Internet.
- Install and use anti-malware on the local computer.
- Remove unnecessary software from the computer.
- Disable any nonessential services running on the computer.
- Disable unnecessary OS default features.
- Secure the web browser.
- Apply operating system and application software updates and patches.
- Require strong passwords.
One of first steps in securing an Internet connection is to implement security options on the local router. If a particular connection does not include a router, you may want to consider installing one, as well-configured routers offer one of the best initial lines of defense. Routers and other network connectivity devices are covered in detail in Part III. Some basic items to consider when configuring a router’s security features include:
You should always establish and configure a firewall to control the flow of information between the computing device and the Internet. For standalone or local computers, this can be addressed through the local software firewall available with the operating system and/or through the protective router. Local firewall configurations are discussed later in this chapter. Anti-malware software can be installed using an inclusive malware-prevention product or by combining different types of specific prevention programs, such as antivirus and antispyware products from different vendors. Different malware types and prevention methods are discussed in detail at the end of this chapter. Keeping unused software products on a computer provides additional avenues of possible attack and exploitation. If you don’t know what a suspected software program does, research it and get rid of it if it is not important to the operation of that system. Some viruses are designed to exploit nonessential services in order to migrate from device to device. In particular, disengage any file-sharing or device-sharing services that are running, unless they are somehow required for proper operation of the system (this is almost never the case in nonconsumer usage). Photo-sharing and music-sharing services should always be disabled, while file and printer should be disabled unless required to pass information from one device to another to perform work tasks. (This would pertain to a networked computer, which is discussed in detail in Part IV.) As mentioned earlier, Autorun is a highly exploitable feature of the Microsoft line of operating systems. When this feature is enabled, the OS will detect the presence of the removable media and execute its contents. If the SD card or CD/DVD contains a virus, it will automatically be executed and infect the host computer. The web-browsing class of application software has attracted an increasing number of attacks. Initial browser configurations may not offer much in the way of security. As such, it is usually necessary to configure a new browser’s security options to safeguard the system from attack through this portal. Steps for securing different web browsers are discussed later in this chapter. People and groups that produce malware are always busy designing the next exploit. For this reason, operating systems and applications must constantly be updated to counteract these efforts. This requires a planned methodology for obtaining and applying the latest upgrades and security patches for each software product on the system. The main user authentication tool used with personal computing devices is the username and password login. In general, there are three types of user-related logons with which to contend:
For a password to be effective, it must possess a certain amount of complexity. Its length, width, and depth must be designed to thwart the efforts of the previously mentioned password-cracking techniques. Refer back to Chapter 8 for an in-depth discussion of passwords.Using a Secure Connection
Establishing and Using a Firewall
Installing and Using Anti-Malware Software
Removing Unnecessary Software
Disabling Nonessential Services
Disabling Unnecessary OS Default Features
Securing the Web Browser
Applying Updates and Patches
Requiring Strong Passwords
Implementing Local Protection Tools
Five common tools are used at the local level to protect computing devices from exploitation through the Internet world:
- Local firewalls
- Host-based intrusion-detection systems
- Browser security options
- Antivirus/anti-malware tools
- Software updates and patches
Each topic is discussed in greater detail later in this book. The materials presented in this chapter are specific to local host security. However, each topic expands in scope as the local hosts are attached to larger networks and Internet systems.
Software-Based Local Firewalls
Computers connected directly to the Internet are vulnerable to attacks from outsiders. One way to protect standalone computers from outside attacks is to install a local firewall. A firewall is a device or a program that is placed between a local device and an outside network such as the Internet.
Local software-based firewalls can be installed on an individual computer to protect it from malicious activities introduced through the Internet connection. In some cases, the operating system provides a built-in firewall option that can be used to protect the local computer.
The firewall inspects all traffic going to and coming from the outside connection and can be configured to control traffic flow between the Internet and the local device based on desirable properties, as illustrated in Figure 9.1. Firewalls are configured so they will only pass data to and from designated IP addresses and TCP/UDP ports.

FIGURE 9.1 Firewall Operation
Normally, firewall filters are configured around services recognized by the TCP and UDP networking protocols. These protocols use port numbers to identify specific processes such as HTTP or FTP and are used to refer incoming packets to a software application that will process them. Many of the port numbers are standardized and are referred to as well-known ports. Similarly, their associated applications are called well-known services.
Table 9.1 lists several well-known port numbers and their associated services. The Internet Assigned Numbers Authority (IANA) has assigned standard port numbers ranging from 0 to 1023 to specific services. Port numbers from 1024 through 49151 are called registered ports and are used in vendor applications. Ports 49152 through 65535 are dynamic, or ephemeral, ports and are used by computer applications to communicate with other applications.
TABLE 9.1 Typical I/O Ports
| Service | Well-Known Port Number |
| FTP | 20, 21 |
| Telnet | 23 |
| SMTP Mail | 25 |
| HTTP (WWW) | 80 |
| POP3 (Mail) | 110 |
| News | 144 |
| HTTPS | 443 |
| PPTP | 1723 |
| IRC | 6667 |
When the firewall examines the incoming packet, it can read the source and destination IP addresses of the packet and any TCP/UDP port numbers, as shown in Figure 9.2. It will use the IP address and port information in the packet headers to determine if an incoming packet should be routed into the internal network.

FIGURE 9.2 Firewall Functionality
If you have configured the firewall with the IP address of an internal computer that provides FTP services and opened ports 20 and 21, the firewall will recognize the IP address and port numbers in the incoming header as valid and route the packet to that computer. However, all other incoming requests will still be blocked.
Using Local Intrusion-Detection Tools
As with physical security efforts, preventing unauthorized access is the first line of security at the local computing and control-device level. However, it is just as important at this level to be able to detect the occurrence of an intrusion and notify the proper authorities of its nature.
Computer-based Intrusion Detection Systems (IDS) can be implemented in two ways: as network-based IDS (NIDS) or as host-based IDS (HIDS). In both cases, the system is designed primarily to monitor the system (local computer or network environment), log key events and policy violations, and report them as directed.
Intrusion Prevention Systems (IPS), also referred to as Intrusion Detection and Prevention Systems (IDPS), provide an additional level of protection aimed at preventing the detected threat from succeeding.
As their definitions imply, HIDS and NIDS operate in different areas of the computer/network environment. For now, we will hold off on the discussion of NIDS. Instead, we will focus on HIDS tools that run on individual hosts or devices.
All IDS devices are based on one of two strategies:
- Signature analysis – Incoming and outgoing traffic is compared to a database of stored specific code patterns that have been identified as malicious threats.
- Anomaly analysis – Incoming and outgoing traffic is compared to an established baseline of normal traffic for the system.
The baseline is “learned” (generated) by applying mathematical algorithms to data the system obtains from the traffic flow.
Signature-based IDS/IDPS products generally work by looking for specific patterns in content, known as signatures. If a “known bad” pattern is detected, the appropriate actions can be taken to protect the host. However, because of the dynamic nature of programming languages, scripting in web pages can be used to evade such protective systems.
The signature-based IDS database is typically generated and distributed by its manufacturer in response to observed malicious signatures. Therefore, the malicious code is already in existence before a signature can be identified and added to the database to be acted on. The time delay between the release of the malicious code and the issuing of its signature presents its own security issue.
Anomaly-based IDS/IDPS systems apply statistical analysis techniques to the data stream to determine whether it is “normal” or “anomalous” at any given time. There are two common methods of implementing statistical anomaly detection:
- Profile-based anomaly-detection systems
- Threshold-based anomaly-detection systems
These systems use mathematical algorithms to monitor normal data traffic and develop a “profile” of rules that describe what normal traffic for that system looks like. The profile developed reflects evaluations of users’ past behaviors and is configured to signal when deviations from these behaviors reach a certain level (or threshold).
These IDS systems are designed to track the number of occurrences of specific events over time and generate an intrusion warning if the number of events exceeds a predetermined number. Most commonly available IDS systems are designed for use on local host systems. However, there is an increasing effort in producing network-based IDS systems to provide a more effective intrusion-detection-and-prevention arsenal. Network-Based Distributed Intrusion Systems are described in Part IV.Profile-Based Anomaly-Detection Systems
Threshold-Based Anomaly-Detection Systems
Configuring Browser Security Options
Web browsers are designed to be highly flexible to offer users as many usage options as possible. They are also designed to appeal to users who by and large are nontechnical. Coupled together with the abundance of people connected to the Internet who use their access to the web for less-than-honorable purposes and you have a huge security window into your local system.
For example, Figure 9.3 shows a sample of the Internet options available with the Windows Internet Explorer (IE) web browser. As you can see, some of these options are personal preferences, such as colors, fonts, and toolbars. However, there are a variety of security-related activities that involve the browser and searching the Internet.

FIGURE 9.3 Internet Options
As the figure illustrates, web browsers routinely offer a variety of user-selectable security options that can be established to compensate for the added vulnerability Internet browsing and searching brings to the system. These options include:
- Configuring security levels
- Configuring scripting
- Configuring proxies
- Controlling cookies
Although each browser is designed differently, they all tend to provide similar web security options. The user may have to search for specific tools to configure their browser for secure operation, but the same basic configuration techniques apply to all browsers.
Configuring Security Levels
Because the browser is the portal to the wider outside world, its security settings are very important. In addition, other Internet tools on the machine may rely on components of the browser to perform their functions. These applications may bring with them enhancements that create additional vulnerabilities. These features should be evaluated and turned off if they do not contribute to the operation of the system.
As with other applications, browsers come with a preconfigured set of security levels. In Microsoft IE, these functions are located on the Security tab depicted in Figure 9.4.
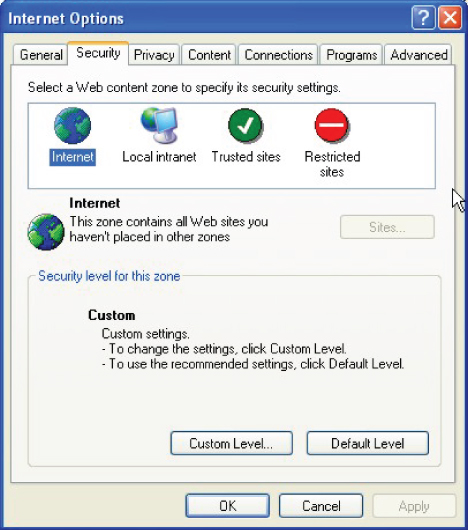
FIGURE 9.4 IE Security Tab
In this browser example, Internet sites may be categorized under different Internet security zones that enable sites listed in each zone to be governed by security restrictions that apply to that group (Internet, Local Intranet, Trusted Sites, and Restricted Sites).
This allows different websites to be accessed with different security restrictions. Trusted Sites could be established to work with less security overhead, while Restricted Sites can be assigned heightened security settings. The Internet zone option is the default zone for all sites not assigned to one of the other zone options.
The best option for configuring security levels is to set them as high as possible without restricting the browser to the point where sites do not load or function correctly.
Configuring Script Support
Scripts are executable applications that provide interactive content on websites. They are also capable of retrieving information in response to user selections. However, the user may not have to do anything to run a script program; they are simply embedded in the website being accessed.
Scripts encountered on websites should be controlled because they are one of the main sources of virus infections. Attackers reconfigure scripts to contain viruses that clients may download unwittingly. They also facilitate automatic pop-up windows that appear without warning on the client’s browser. These windows normally contain unrequested advertisements that tend to annoy users.
The capability to load and run scripts in a browser can be controlled through the browser’s Security feature. The list of individual web page components that you can control includes different script types, such as ActiveX and JavaScript.
ActiveX is a Microsoft utility that enables web applications to build extended, interactive features, and functionality around the presence of the ActiveX framework in the browser. When the ActiveX-enabled browser encounters a web page calling for an ActiveX control function, it automatically downloads without involving the user. Of course, this creates a potential security vulnerability that can be used by crackers to embed malicious code in hacked websites.
A similar scripting language called JavaScript is often used in web browsers to make websites more interactive. It is particularly interesting for developing interactive content in games and other audio/video-rich web pages. However, it is also widely used to transmit information about remote activities, such as browsing and reading habits for use in advertisement tracking and analysis. It does this without reloading the page where the information was gathered and without notifying the reader. This again creates a potential portal for malicious (or at least unwanted) activities.
Another area of concern in the interaction between websites and browsers is the use of plug-ins to add new features to existing software applications, such as search engines and antivirus functions. These script controls are similar to ActiveX controls but cannot be executed outside of a web browser. Adobe Flash and QuickTime Player are the most recognized examples of web browser plug-ins.
Most browsers support various plug-ins by default and rely on them for some portion of their operation. Along with the automatic nature of these components comes an increasing vulnerability both in terms of design deficiencies and as potential hacking targets. Historically, ActiveX controls, Adobe’s PDF Reader and Flash products, as well as Apple’s QuickTime product have represented the highest number of documented vulnerabilities among script products.
As with the other security objects, the browser can typically be configured to Enable, Disable, or present a user prompt whenever it encounters these scripted items on a page. As a rule of thumb, all add-ons (including Java, JavaScript, Flash, and ActiveX) should be disabled on websites unless you know that they can be trusted.
Controlling Cookies
Cookies are small files that web servers send to web browsers when their pages are accessed. The legitimate use of these files is to enable the server to automatically recognize the client browser any time it connects to the server. The basic HTTP page transfer process is described in Figure 9.5.

FIGURE 9.5 HTTP Transfer Operations
Web page transfers are initiated on the client side through the local web browser. The browser sends an HTTP request to the designated web server, which in turn sends back the requested page along with an HTTP response message. One piece of information in the message may be a request for the browser to set (accept and store) cookies, so that a more efficient, automated page transfer process can be carried out.
The cookie may also contain several pieces of configuration information known as cookie attributes. One key security-related attribute is the setting for when the cookie expires. There are basically two varieties of cookies to be concerned with: session cookies and persistent cookies. Session cookies are cleared when the browser is closed, and persistent cookies will remain on the computer until the specified expiration date is reached. Persistent cookies pose a higher risk than session cookies because they remain on the client computer for a longer period of time.
Cookies were originally developed to keep users logged into online shopping environments while they moved from page to page and placed items in online shopping baskets. However, the use of cookies has expanded to include a lot more than just shopping baskets. They may be designed to gather and track any information that a website is designed to place in it—for example, they may track information about the sites the user visited or credentials used to access the site. Cookies designed to perform these types of functions are called tracking cookies.
This is the type of information that makes cookies attractive to crackers. If a website uses cookies for authentication, then an attacker may be able to acquire unauthorized access to that site by obtaining the cookie. This is referred to as cookie theft.
The attacker only needs to employ a packet sniffer utility to monitor the network traffic and capture the cookie in order to gain access to their credentials (username, passwords, network address, and so on). With this information in hand, the attacker has the ability to pretend to be the original user when they access other sites.
The attacker can also use a technique called cross-site scripting, or XSS, to cause the returning cookie to be redirected to a third-party server operated by the attacker. The attacker can then use the stolen cookie to spoof the original site posing as the original user. The redirection is typically accomplished by simply hiding the script on the site and using social engineering techniques to trick the user into clicking on the code. When they do, their cookie is transmitted to the third-party location specified by the attacker.
In addition, the attacker may simply alter the contents of a stolen cookie to perform an attack on the original web server. For example, if the cookie was the product of an ecommerce sales site, it might include pricing information about products in a shopping cart. The attacker could alter that information and send it back to the original server, causing it to charge the customer a lower price for the item. This type of attack, as depicted in Figure 9.6, is a form of a man-in-the-middle (MITM) attack referred to as cookie poisoning.
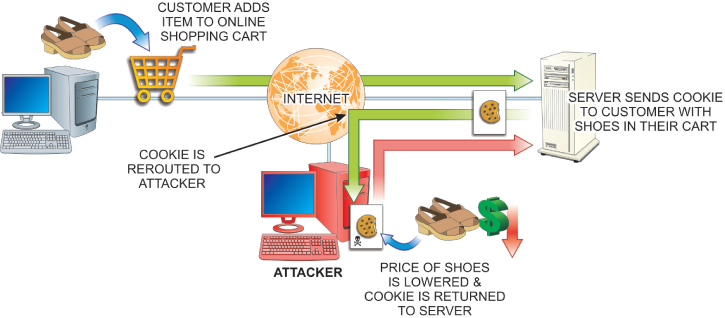
FIGURE 9.6 Cookie Poisoning
Virtually all browsers support cookies by default. Some offer the user the option to completely enable or completely disable cookies, while others provide a more robust cookie manager that enables the user to view and select individual cookies to remove from the system.
For security purposes, the best recommendation for handling cookies is to disable the option to Always Set Cookies. In addition, use transmission encryption to prevent third parties from being able to read the cookies if they are intercepted along the way. This is particularly important when using Wi-Fi communications. If the wireless link is not encrypted, attackers can easily intercept and then read the data including the cookies sent.
The use of secure socket layer (SSL) links provides data encryption security for the transmitted data (including the cookies) and prevents unauthorized access to the data as it moves across the communication link. SSL links are always identified as HTTPS:// sites instead of simply HTTP://.
Defending Against Malicious Software
Increased connectivity through networks and the Internet have made personal computers vulnerable to an array of different types of malware and grayware. Malware is the term used to describe programs designed to be malicious in nature. The term grayware describes programs that have behavior that is undisclosed or that is undesirable.
New malware threats are constantly emerging, and successful cybersecurity personnel must stay abreast of them. The following list identifies some of the more advanced malware threats being produced. Some of these have been around for many years but have continued to be very dangerous and continue to be modified and difficult to detect:
- Viruses are destructive programs designed to replicate and spread on their own. Viruses are designed to replicate themselves within a local computer environment. This most often happens when users download programs from the Internet or open email attachments. Many “free” products obtained from the Internet have something attached to them—a virus, spyware, or some other form of malware.
- Worms (sometimes referred to as network viruses) are circulated through a network connection. Unlike a virus, worms do not need a host program in order to infect your computer. Worms search for vulnerabilities to exploit in an application. Once the worm has taken advantage of the vulnerability, it seeks to replicate to another computer on the network. While initially intended to slow down network environments, worms often leave payloads on systems to cause further malicious activity.
- Trojans appear to be a legitimate program that might be found on any system. They are made to appear to be actual applications so that users will be tricked into using them. Although they function and work properly, they have malicious code that initiates when the application is launched.
- Rootkits are a type of software designed to gain administrative control of a computer system while remaining undetected. Normally, the purpose is to enable malicious operations to occur on a target computer without the knowledge of its users or system administrators. Rootkits can occur in hardware or software by going after the BIOS, boot loader, OS kernel, and sometimes applications or libraries.
Rootkits are designed to operate at the root level of the operating system and appear as a benign entity at that level. After the rootkit has been installed in a system, it will take measures to hide itself from detection. They modify the behavior of the operating system’s core components by altering drivers or kernel modules. These programs have the ability to steal PINs, account passwords, credit cards, and other sensitive information. They can infect nearly any operating system type.
- Ransomware is software designed to keep the user from their data and hold it hostage for payment. Spam email is the most common delivery vehicle for spreading the malware. It is then activated by the user clicking an attachment or a link in the email message. It then disables essential system services or even locks the computer so that the user cannot gain access to it.
Hackers can encrypt personal files on the computer keeping the user from gaining access to their data. The hacker will normally prompt the user to enter a code that can be attained only after wiring payment through cryptic means such as Bitcoin cryptocurrency. They will also typically try to get the user to purchase a legal decryption or removal tool. The author (hacker) is the only person(s) who knows the required private decryption key.
- Spyware programs are generally introduced to the system through Internet downloads that appear to be useful programs. Unlike viruses and Trojans, spyware typically does not self-replicate. Once spyware is installed on a system, it monitors the system’s operation and collects information such as usernames, passwords, credit card numbers, and other PII.
- Adware programs introduce unwanted, unsolicited advertising displays to web browsers. They can also be designed to gather user selection information from the browser, constructing a more personalized advertising scheme. Adware is typically introduced to the system through downloads such as free software (freeware).
- Logic bombs are a type of malware typically used to delete data. A logic bomb is computer code that, much like other malware, is attached to a legitimate program. The code sits idle until a specific logical event is concluded. This includes a number of days passing, a number of programs being opened, or executing a program in a specific manner. Logic bombs are hard to detect because they are often included in large programs with thousands of lines of code.
- Zombies are infected computers that can be placed under the remote control of a malicious user. Zombies can be used to create Denial of Service (DoS) attacks that flood targeted networks to slow down and sometimes stop servers completely. Computers are often infected and become zombies by way of viruses, worms, and Trojans.
- Botnets are a large collection of zombies, or bots, controlled by a bot herder. This type of network can consist of literally millions of unsuspecting computers. Botnets can be used to send out spam (usually through email lists) originating from unsuspecting users’ computers. It is estimated that 50 to 80 percent of spam worldwide is created by zombie computers.
It is common to install a number of different defensive products to protect PCs and their data from unauthorized access and malicious interference. Most products these days include protections against multiple fronts. The products most widely used for these purposes include:
- Antivirus programs
- Antispyware programs
- Spam blockers
- Pop-up blockers
Every computer should have some means of protecting itself against computer viruses. The most common means of virus protection involve installing a virus-scanning (antivirus) program that checks disks and files before using them in the computer. Several companies offer third-party virus-protection software that can be configured to operate in various ways. If the computer is a standalone unit, it might be nonproductive to have the antivirus software run each time the system is booted up. It would be much more practical to have the program check any removable media attached to the system, only because this is the only possible non-network entryway into the computer. All computers with connections to the Internet should be protected by an antivirus solution before they are ever attached to the Internet. In these cases, setting the software to run at each bootup is more desirable. In addition, most antivirus software includes utilities to check email and files downloaded to the computer through network or Internet connections. As indicated earlier, when an antivirus application is installed on the system, it can be configured to provide different levels of virus protection. You will need to configure when and under what circumstances you want the virus software to run. As shown in Figure 9.7, there are basically two types of antispyware products available: those that find and remove spyware after it has been installed and those that block spyware when it is trying to install itself. Both of these methods stand a better chance of keeping computers free from spyware when they are combined with user information about how to avoid spyware. FIGURE 9.7 Antispyware Product Types The detect-and-remove method is by far the simpler type of antispyware product to write. Therefore, there are several commercially available products that use this method. Like antivirus software packages, this type of antispyware product relies on databases of existing definitions to recognize spyware threats. These databases must be updated frequently to recognize new spyware versions that have been identified. The real-time-prevention type of antispyware product does not rely on historical data to identify spyware. Instead, it monitors certain configuration parameters and notifies the user when suspicious installation activity occurs. The user then has the option to allow or block the installation effort. Some antispyware products incorporate both methods of dealing with spyware. In addition to installing antispyware applications, users can fight spyware in a number of other ways:
Using Antivirus Programs
Using Antispyware

Hardening Operating Systems
As noted earlier, the second level of hardening local computer systems against attacks is to secure their operating systems. This involves updating vulnerable code segments of the OS as they become known. OS hardening occurs through the application of new programming in the form of:
- Service packs
- Patches
- Updates
After an operating system has been in the field for some time, vendors may combine several product improvements and distribute a numbered service pack for the specific operating system being upgraded. Critical files should always be backed up in the event that the service pack or OS fails to work after installing the service pack. Patches are general improvements to a given operating system that have been released for distribution. Many patches and updates are purely cosmetic and convenient add-on features, while others are critical security upgrades designed to respond to a particular virus, discovered threat, or weakness found in the operating system. An update is a service pack or patch that improves the reliability, security, or attractiveness of an operating system. The most reliable source of operating system updates is the OS manufacturer. These organizations are always seeking ways to improve their products. Some updates may make the OS more convenient but may not necessarily make it more secure. Therefore, they should be tested before implementing. Consider backing up critical files in the event that the patch or OS fails to work after installation.Service Packs
Patches
Updates
Overseeing Application Software Security
Software application packages operate as extensions of the operating system. Depending on the type of operating system being used, an application program may directly control some system resources, such as printers and network interfaces, while the operating system lends fundamental support in the background. In more advanced systems, the operating system supplies common input, output, and disk management functions for all applications in the system.
Some applications include built-in security tools that control access to the application beyond the levels presented by the operating system. However, many applications are written with very little concern for security issues. The focus of such programs is functionality and sharing, leaving security issues to the operating system and security utilities.
Software Exploitation
The term software exploitation is used to describe cyber attacks designed to take advantage of vulnerabilities or weaknesses in software products—operating systems and applications. These vulnerabilities may be the result of software that is created with little or no thought for security issues, or they may be the product of software that has been inadequately tested before being released for use.
There are two very conflicting objectives in the computer software industry:
- Make the product as open and easy to use as possible so that otherwise nontechnical users will be able to work with it.
- Make the application bullet proof so that nothing bad can happen to it—ever.
Software programmers are asked to meet both of these objectives in the same product.
In some cases, the programmers may be trying to create a truly open product without concerns about how it might be exploited by malicious people. In other cases, they may not be experienced enough to envision how their product might be exploited. With the worldwide pool of programmers continuously growing, there are many individuals with a significant knowledge base of how to test, manipulate, and modify programming. This includes black hat hackers.
Modern operating system and application programming is very complex. When programmers initially develop a product, they may make coding mistakes or create portions of a product that do not work well with elements created by other programmers in the development team. Attackers will often use software vulnerabilities to insert and hide malicious code that can be used to disrupt services or operations.
In particular, the attacker may alter the existing code to create a condition in the computer’s memory known as a buffer overflow, which results in erratic behavior, memory access errors, and/or system crashes. The system is effectively disabled to the point where the user cannot use it. This kind of attack is a type of Denial of Service (DOS) attack.
Applying Software Updates and Patches
From the previous section, you can see that due to the nature of product development and the pressures on software producers to bring new products to the market, new software releases never seem to be complete or perfect. As security issues are revealed with software products, their producers are forced to issue security patches for their product that correct the weakness.
Security patches are updates issued for the specific purpose of correcting an observed weakness to prevent exploitation of the vulnerability. Microsoft issues security patches for its products once a month. Other software developers use dedicated security teams to develop and issue security patches as soon as possible after a vulnerability has been discovered.
For security and stability reasons, you should always patch operating systems on computing devices that are connected to the Internet. However, this is not the case with all PCs. Stable PC systems that are not connected to the Internet should not be patched unless doing so resolves some sort of existing problem.
Hands-On Exercises
Objectives
- Manage the local firewall configuration.
- Explore Windows Firewall with Advanced Security.
- Recognize the need for outbound filtering.
- Create a port filtering rule.
- Create an ICMP filtering rule.
Resources
- PC-compatible desktop/tower computer system
- Windows 10 Professional installed
- User account with Administrative access
- Internet access from a network connection
Discussion
Computers connected directly to the Internet are vulnerable to attacks from outsiders. One way to protect standalone computers from outside attacks is to install a local firewall.
Local software-based firewalls can be installed on an individual computer to protect it from malicious activities introduced through their Internet connection. In some cases, the operating system provides a built-in firewall option that can be used to protect the local computer.
In this lab, you will explore the options associated with Windows Firewall to apply the local (software) firewall. You will also recognize the need for inbound and outbound filtering and testing various security options. In some scenarios, you may want to download a software-based firewall, but Microsoft includes Windows Firewall, as well as Windows Firewall with Advanced Security, with their operating system.
Procedures
Accessing Windows Firewall Basic Settings
To access the basic Windows Firewall settings, follow these steps:
- Power on the computer, and choose Windows 10 Professional if a given a choice.
- Log on to your administrative account.
- Click on the embedded search bar on your taskbar, type Control Panel, and then click on Control Panel in the menu presented.
- If necessary, switch to viewing the Control Panel with the View by: Small Icons, locate and click Windows Firewall. Figure 9.8 shows the basic Windows Firewall settings.

FIGURE 9.8 Basic Windows Firewall Settings
In this window, you can see the current firewall states for each type of network.
- Expand each network type by clicking the down arrows located in the top-right of each network. Examine the current states and the rules associated with each. List the three types of networks in Table 9.2.
TABLE 9.2 Types of Networks
Domain networks Home or work (private) networks Public networks - In the left pane, click Turn Windows Firewall On Or Off, located next to a Windows Defender Shield indicating Administrative access is required.
In the left pane, Turn Windows Firewall On Or Off and Change Notifications lead to the same window. Figure 9.9 depicts the Customize Settings window.

FIGURE 9.9 Customize Settings Window for Windows Firewall
This window shows the basic options associated with each type of network. You turn on or off the firewall. If the firewall is turned on (recommended), you can decide if you want to block all incoming traffic and if you want to be notified if and when a program is blocked.
The firewall inspects all traffic going to and coming from the outside connection and can be configured to control traffic flow between the Internet and the local device based on desirable properties. Firewalls are configured so they will only pass data to and from designated IP addresses and TCP/UDP ports.
There are very few reasons to turn off Windows Firewall (not recommended).
- If any network type has Turn Off Windows Firewall selected, click Turn On Windows Firewall. Click OK to exit the Windows Firewall Customize Settings.
Examining Windows Firewall with Advanced Security
To examine Windows Firewall with Advanced Security, follow these steps:
- In the left pane, click Advanced Settings, next to a Windows Defender Shield, to launch the Windows Firewall with Advanced Security console. (See Figure 9.10.)
FIGURE 9.10 Windows Firewall with Advanced Security Console
This opening view in the console shows an overview of the current state of the firewall, along with a basic Getting Started tutorial that includes:
- Authenticate communications between computers
- View and create firewall rules
- View current firewall and IPsec policy and activity
- At the bottom of the Overview section, select Windows Firewall Properties to launch the Windows Firewall with Advanced Security on Local Computer Properties window, as shown in Figure 9.11.
FIGURE 9.11 Windows Firewall with Advanced Security on Local Computer Properties
This window gives you another option to control settings for each of the three types of networks. You can also customize the various settings and set rules for logging.
- Explore the tabs without changing the configurations and then click Cancel to close out this window.
- In the left pane, select Outbound Rules. The central and right panes will be similar to Figure 9.12.
FIGURE 9.12 Outbound Rules in Windows Firewall with Advanced Security
Creating a TCP Outbound Rule
To create a TCP outbound rule, follow these steps:
- In the right pane, click New Rule. The New Outbound Rule Wizard will appear, as shown in Figure 9.13.
FIGURE 9.13 New Outbound Rule Wizard
On any page within the New Outbound Rule Wizard, you can learn more about the options by selecting the Learn More About (Subject) link located near the bottom of each page.
- Select the Port radio button, and then click on the Next button to continue the steps in the left pane, as shown in Figure 9.14.

FIGURE 9.14 New Outbound Rule Wizard Steps: Protocol and Ports
- In the Protocol and Ports window that appears, make sure the TCP radio button is selected along with the Specific Remote Ports radio button. Input 135 into the text field.
TCP port 135 is one of many ports through which malware often attempts to initiate network requests via NetBIOS/SMB/RPC. Creating an outbound block rule will prevent your system from connecting to malicious external hosts.
- Click the Next button to proceed to the Steps: Action page.
- Examine the options, but leave the Block The Connection radio button selected. Click the Next button to continue onto the Steps: Profile page.
- Here you will decide the type of network to which your rule should apply. Leave all three check boxes marked to apply the rule to all networks. Click Next to continue to the Steps: Name page.
- On the Name page, enter My First TCP Rule into the Name text box. Type This is my first TCP outbound rule into the Description (Optional): field box. Figure 9.15 shows the Steps: Name page with the information entered.

FIGURE 9.15 New Outbound Rule Wizard Steps: Name Page
- Click Finish. You should see your rule in the Rules list in the center pane, as shown in Figure 9.16.
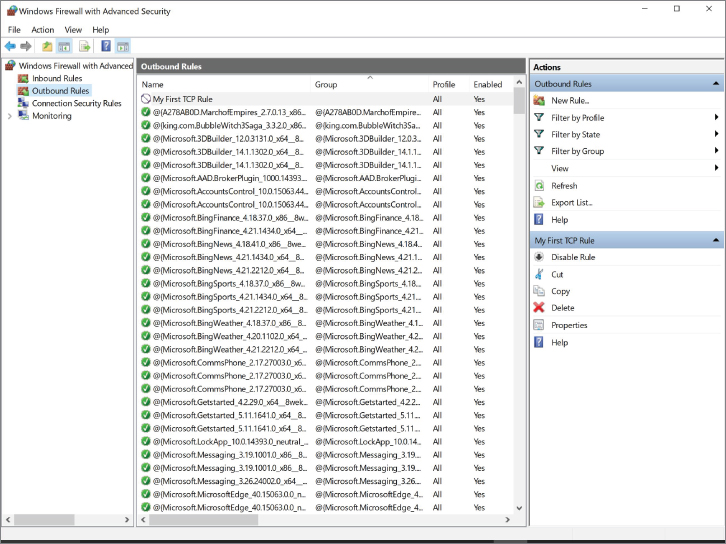
FIGURE 9.16 Windows Firewall with Advanced Security New Outbound Rule
Creating an ICMP Outbound Rule
Outbound communications can be in the form of ICMP types or codes in addition to TCP/UDP ports. The following steps will show you how to block outgoing ICMP communications.
- Click on New Rule in the right pane. The New Outbound Rule Wizard will appear.
- Select the Custom radio button. Notice that the Steps located in the left pane have grown in numbers. Click Next to continue.
- Leave the All Programs radio button selected, as shown in Figure 9.17.

FIGURE 9.17 New Outbound Rule Wizard Steps: Program Page
- Click Next to continue to the Steps: Protocol and Ports page.
- Select ICMPv4 from the Protocol Type drop-down menu. Click on the Customize button to access the Customize ICMP Settings, as shown in Figure 9.18.

FIGURE 9.18 Customize ICMP Settings
- In the Customize ICMP Settings window, select the Specific ICMP Types radio button. Click the check box next to Echo Request.
You can block outbound ICMP echo requests, also known as
pings, when your machine has been affected by malware and is now part of a botnet. In this instance, the botnet may be sending ICMP requests to create apingflood (DoS attack). - Select OK to return to the Steps: Protocol and Ports page.
- Click Next to continue to the Steps: Scope page, as shown in Figure 9.19.

FIGURE 9.19 New Outbound Rule Steps: Scope Page
- Leave the Any IP Address radio buttons selected and then click Next to continue to the Steps: Action page.
- Leave the Block The Connection radio button selected, and then click Next to continue to the Steps: Profile page.
- Leave all the profile check boxes marked, and then click Next to continue to the Steps: Name page.
- In the Name text box that appears, enter My First ICMP Rule. Enter ICMP Echo Requests into the Description (Optional) text box. Figure 9.20 shows the completed Steps: Name page.

FIGURE 9.20 New Outbound Rule Wizard Steps: Name Page
- Click Finish to complete and exit the New Outbound Rule Wizard.
You should see your rule in the Rules list in the center pane, as shown in Figure 9.21.

FIGURE 9.21 New Outbound Rule in Windows Firewall with Advanced Security
Testing ICMP Outbound Rule
Now it is time to test the previously made ICMP Echo Requests rule. This is completed in a command-line operation involving the PING utility.
- Leave the Windows Firewall with Advanced Security console open.
- Click the embedded search bar on the taskbar and enter cmd. This is the quick method to access the command line. Press Enter to launch the command line.
- To test the ICMP rule,
pinga well-known server of Google. Typeping 8.8.8.8into the command line, and then press Enter.
Notice that there is a general failure. The outbound rule has effectively blocked ICMP echo requests. Figure 9.22 shows the failure to ping (100% loss).

FIGURE 9.22 Ping Failure
- Leave the command-line terminal open and select the Windows Firewall with Advanced Security console.
- Find My First ICMP Rule and right-click it for more options. Select the top option to Disable Rule.
- Return to the command-line terminal. Pressing the Up arrow on your keyboard once will insert the last typed line into the terminal, which is
ping 8.8.8.8. - Press Enter to see if the disabled rule allows
pingto reach the Google server. Figure 9.23 shows that thepingsucceeded (0% loss).
FIGURE 9.23 Ping Success
- Close the command-line terminal by clicking the red X in the top-right of the window.
- Back at the Windows Firewall with Advanced Security console, delete the two rules you created by right-clicking each and selecting Delete. When you are prompted to confirm the delete function, select Yes.
- Close the Windows Firewall with Advanced Security console by clicking the red X in the top-right of the window.
- Shut down the computer.
See Table 9.3 and Table 9.4 at the end of the Procedures exercise for lists of ports, ICMP types, and codes to close in order to exercise best practices.
Tables
TABLE 9.3 Recommended Ports to Close
| Port Name | TCP or UDP | Port Number(s) | Reason for Closure |
| MS RPC | Both | 135 | Windows systems use these ports to send out queries. This can leak information or be construed as an attack by another network. |
| NetBIOS/IP | Both | 137–139 | |
| SMB/IP | TCP | 445 | |
| Trivial File Transfer Protocol | UDP | 69 | Closing this prevents a hacker from moving their toolkit onto your system. |
| Syslog | UDP | 514 | Both of these send out information about the network topology, which is something to avoid. |
| Simple Network Management Protocol | UDP | 161–162 | |
| SMTP (all but your mail server) | TCP | 25 | This prevents your network infrastructure from being turned into a Spam relay, which could get your network on one or more blacklists. |
| Internet Relay Chat | TCP | 6660–6669 | These are used by hackers to send and receive communications from the systems that they infect. |
TABLE 9.4 Recommended ICMP Types and Codes to Close
| ICMP Name | Type | Code | Reason for Closure |
| Echo – Replies | 0 | 0 | These are used for covert communications. |
| Host Unreachables | 3 | 1 | Host Unreachables are used by hackers to map out networks and to identify which hosts are online and offline. |
| Time Exceeded in Transit | 11 | 0 | Closing these prevents some network-mapping tools from functioning. |
Lab Questions
- What are the three main types of networks that Windows Firewall handles?
Answer: The three types of networks include: Domain networks, Home or work (private) networks, and Public networks.
- It is important to turn Windows Firewall off. True or False?
Answer: False. There are only a few legitimate reasons to turn off Windows Firewall. Overall, it is a necessary security tool within the Windows environment.
- What are the four Rule types that you can create with the New Rule Outbound Wizard?
Answer: The four types of rules that are listed for you to choose from within the New Outbound Rule Wizard include: Program, Port, Predefined, and Custom.
- What is an easy way to test ICMP echo requests?
Answer: An easy way to test ICMP echo requests is to use the ping function inside a command-line terminal—for example,
ping 8.8.8.8. - You have the option to block all incoming traffic. True or False?
Answer: True. If the firewall is turned on (recommended), you can decide if you want to block all incoming traffic and if you want to be notified if and when a program is blocked.
