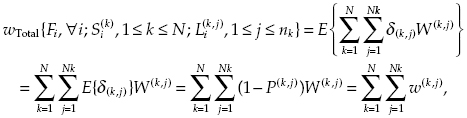CHAPTER 13
Counter-Terrorism: Protection Resources Allocation
This section is based on a presentation made by the author at the joint meeting of CREATE1 and GAZPROM2 delegation in Los Angeles in 2007. The meeting was dedicated to problems of defense against terrorists' attacks.
13.1 Introduction
For decades, the United States has focused its military and intelligence capabilities on potential enemies beyond its own borders. After September 11, 2001, it has become increasingly clear that our enemies have the ability and determination to reach through our defenses and strike at critical assets here at home.
Modern terrorism has gone from the frame of simple intimidation to the active destruction of the chosen country: the goal of terrorists' attacks is to cause the maximum possible material damage and/or human casualties. It is obvious that terrorists' activity is getting more and more organized and modern counter-terrorism is a real war with an invisible enemy.
The problem of protection of human beings, material objects, and political/historical objects of possible terrorist attacks arose. A defender usually spends more resources than terrorists, so optimal allocation of these resources is very important. It is clear that terrorists have many advantages: they choose the time of the attack, they choose the object of the attack, and they choose the weapon of destruction. In general, a defender does not know what terrorists' intentions are.
The proposed mathematical model was developed for optimal allocation of defenders' resources for best protection of the defended objects.
13.2 Written Description of the Problem
13.2.1 Types of Counter-Terrorism Actions
What kind of protective actions against terrorists should we consider? They are in general as follows:
Safety includes a set of measures attempting to prevent terrorist actions (check points at airports, checking cargo, profiled visa control, registration of foreign visitors and control of their staying in the country, control over the purchase of dangerous components for composing bombs, etc.). The objective of these measures is to prevent the possibility of organizing the terrorists' acts by limiting the admittance of suspicious people in the country and by eliminating the possibility of collection/creation of a weapon of mass destruction (WMD).
Survivability includes a set of measures that help to lose fewer lives and to prevent public panic.
Pre-emptive measures include political steps and economical steps.
Of course, some unjustified actions (such as Bush's war in Iraq) could even increase terrorists' activity.
Our belief is that all these sides of the terror-fighting problem must be combined in an aggregated model, which can be used by decision makers of various positions.
Here, at the first step of modeling of counter-terrorism resources allocation, we will focus on the measure of protection of a single object, that is, on the safety problem. For this problem, one can formulate the following problems:
Direct Problem: Optimally allocate resources that guarantee a desirable level of protection of defended objects against terrorists' attacks with minimum possible expenses.
Inverse Problem: Optimally allocate available limited resources that guarantee the maximum possible level of protection of defended objects against terrorists' attacks.
Thus, there are two objective functions:
- Guarantee level of the object protection, and
- Cost of protective measures.
Different objects have different priorities (or values). For instance, a terrorist attack on a stadium during a performance or game might lead to huge loss of human life; an attack on a large bridge might create a serious communication problem for a relatively long time; the destruction of a national symbol might be a reason for widespread panic and a strong hit to the country's prestige.
It is assumed that counter-terrorism experts are able to formulate measures of priority, or “weights” of defended objects because without such priority, object defense is rather amorphous.
13.2.2 Definition and Notations
Let us assume that there are three distinct layers of objects safety protection: federal, state, and local (individual). All input data are assumed to be given by counter-terrorism experts. Let us introduce the following notations:
Fi (φ i): Subjective probability that an object within the country will be protected against terrorists attack of type i under the condition that on the federal level one spends φ i resources. (Notice that this type of protection might be not applicable to all objects. For instance, increasing control of purchasing chemical materials for WMD design has no relation to possible hijacking.)
![]() : Subjective probability that an object within state k will be protected against terrorist attack of type i under the condition that on the level of this particular state one spends
: Subjective probability that an object within state k will be protected against terrorist attack of type i under the condition that on the level of this particular state one spends ![]() resources.
resources.
![]() : Subjective probability that particular object j within state k (denoted as pair “k, j”) will be protected against terrorists' attack of type i under the condition that one spends
: Subjective probability that particular object j within state k (denoted as pair “k, j”) will be protected against terrorists' attack of type i under the condition that one spends ![]() resources.
resources.
W(k , j): “Weight” (or “measure of priority”) of object (j, k).
13.3 Evaluation of Expected Loss
In this stage, we consider a single object, j, located in state k. Assume that only set Gk,j of possible types of terrorists' attacks is possible against object (k, j). Under the condition of uncertainty, we have to assume that terrorists choose the most vulnerable object to strike. In this case, federal protection delivers to this particular object a level of safety equal to:
![]()
Now consider state k level. Using the same arguments, we can write for object (k, j) the level of protection delivered by the protective measures on the state level:
![]()
Assume that on a local level, object (k, j)'s protection is equal to L(k , j). (Postpone, for a while, how this value is obtained.) Then we can assume that measures of protection on all three layers (federal, state, and local) influence an object independently.
Let us, for the sake of concreteness, consider the safety of a stadium: federal measures are usually relatively rough and non-specific (general visa control, etc.), state measures are more specific (traffic control, attention to local communities' behavior, etc.), and local measures are focused on specific sides (police blocking of transportation, stronger patrolling, using dynamite-sniffing dogs, etc.). It is possible to say that the federal layer nets “large fish,” the state layer can net “smaller fish,” and, finally, the local layer nets even smaller though “very poisonous fish.” So, the total probability of possible terrorist attack will be lessened by all three layers practically independently, that is, the probability of successful protection of object (k, j) can be found as:
(13.1) ![]()
Hence, the expected loss, w(k, j), from a possible attack in this case is equal to
(13.2) ![]()
13.4 Algorithm of Resource Allocation
Now we return to calculation of L(k, j) and to the problem of optimal allocation of resources for object (k, j) protection.
Consider Gk,j, a set of possible terrorists' actions against object (k, j). On the local layer we know functions Li (λ i)—subjective probability of protection of object (j, k) depending on spent resources λ i for all possible types of terrorist attacks, where superscripts (k, j) are omitted, for the sake of simplicity. These functions are presented in Figure 13.1, where for illustration purposes only we depict only three such functions. (They should be defined by counter-terrorism experts.)
FIGURE 13.1 Examples of possible functions Li (λ i).
First, consider the direct problem: obtaining the desired level of safety due to measures on the local layer. If the chosen level is L*, then each of functions L1(λ1), L2(λ2), and L3(λ3) has to have its value not less than L* because inequality
![]()
has to be held.
It is obvious that for the minimax criterion to have any Li (λ i) larger than L* makes no sense. So, the problem of protection resource allocation is solved: the local safety level L* can be reached if all Li (λ i) = L*, and in this case one spends total
![]()
resources. This amount of resources is the minimum for reaching safety level L*.
In an analogous way, if one needs to reach the safety level L**, the expenses related to this level of safety are
![]()
and also are the minimum for this case.
The inverse problem (maximization of safety under limited total resources) can be solved with the use an iterative process of numerical extrapolation. For instance, let total resources λ0 be given. One can find two arbitrary solutions of the inverse problem, say, L* and L** with corresponding values λ* and λ**. Let all three values satisfy condition
![]()
Applying linear extrapolation, one finds value L(1) and then, having solved the Inverse Problem for this value, finds a new value λ(1), which is used on the second step of the iterative process instead of value λ*, used at the beginning (see Fig. 13.2).
FIGURE 13.2 Illustration of iterative procedure.

If initially found values λ* and λ** satisfy conditions λ* ≤ λ** ≤ λ0 or λ0 ≤ λ* ≤ λ**, obviously, the iterative process is absolutely similar.
For the sake of transparency, consider a conditional example with stadium safety that gives us the possibility to explain everything less abstractly. Assume that protection measures on federal and state layers (for instance, attentive visa issuing with profiling nationality and country of applicant, checking pilot school attendees, observation of abnormal activity within specific communities, etc.) have been already undertaken.
Assume that three possible types of terrorist attacks are considered:
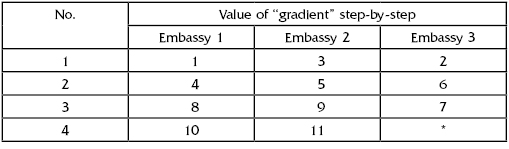
Assume that there are the following protection measures:
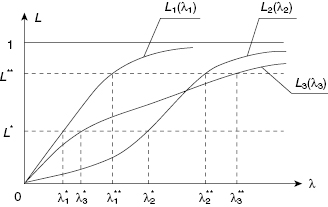
Fictional numerical input data (expenses of these protective measures) used in this illustrative example is given in Table 13.1.
TABLE 13.1 Example Data
Here symbol “–” means that the protection level is absent; for instance, if one begins to use measure A3, after applying 2 cost units the protection level jumps to 0.95, though there is no level 0.9 at all.
For the given example, expenses related to the protection level 0.95 are equal to 2+10+2+10+75=99 conditional units (numbers in the table are taken from most to least). Expenses related to level 0.995 are equal to 8+40+5+20+200=273 conditional units. Here bold fonts denote “jumps” described above, that is, one is forced to “overkill” protection since otherwise the required protection is not delivered.
We have outlined a very general theoretical approach that can be used for the assessing, planning, modeling, and managing of cost-effective counter-terrorism measures. The second phase of the proposed approach deals with an aggregated model for sets of defended objects within the states and in the country as whole. Of course, due to increasing dimensions of the problem on the higher layer it is possible to make only a computer model.
Having that computer model, one can formulate much more complex and realistic problems to include various “what if” scenarios and additional information: known gaps in security systems, counter-terrorism intelligence, impact of preemptive strike against terrorist groups, fuzzy (or not reliable enough) information about terrorist plans and capabilities.
Of course, among the protection measures, one should include secrecy of all undertaken defense activity, intentional propagation of disinformation about protective measures, and so on.
13.5 Branching System Protection
Protecting the country against terrorist attacks cannot be accomplished without cost–performance analysis because of natural limitations on possible defending resources. The main problem for mathematical modeling of the phenomenon is its huge dimension.
Fortunately, the nature of the problem allows disaggregating the problem without loss of the sense of the problem. The system of a country defending target objects can be presented as a system with a special type of a branching structure with an additive type of global objective function.
The proposed approach assumes that input data are delivered by counter-terrorism experts.
13.5.1 Description of Levels of Protection
Counter-terrorism measures can be divided into three relatively independent levels in such a way that each level presents a kind of a sieve: the lower the level, the higher its “recognition,” as shown in Figure 13.3.
FIGURE 13.3 Explanation of different levels of protection.

On the federal and regional level the big “fish” are caught, and then after such sifting, chances of penetrating the three-level counter-terrorism protection barrier should be extremely small. Though errors in danger recognition, global protection actions, or preventive operations could lead to much more serious consequences than insufficient protection of local objects.
Thus an adequate mathematical structure of such a protection process is the so-called “branching structure” (see Fig. 13.4). The upper layer is presented by federal counter-terrorism protection, the middle layer consists of state-level protection, and defended objects present the lower layer.
FIGURE 13.4 Three-level branching system.
13.5.2 Model of Branching Structure
In this section we are using notation and terminology used in Section D. If for each object of the lower layer we choose an individual performance index, then the branching system performance index might be considered as a sum of individual indices. It follows from probability theory: mathematical expectation of the sum of random variables is equal to the sum of the mathematical expectations of random variables irrespective of dependence of the variables.
Indeed, introduce the so-called indicator function of the type:
(13.3) 
Then random loss for object (k, j) is equal to δ(k,j) W(k, j) and total random loss of all objects is
(13.4) 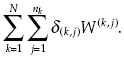
Mathematical expectation of this sum of random variables is defined as
where P(k, j) = 1– (1– F(k , j)) ⋅ (1– S(k , j)) ⋅ (1– L(k , j)), and, in turn, these values are defined as
![]()
In other words, Equation (13.5) gives the total expected loss with taking into respect the “weight” of each loss.
At the same time, it is easy to calculate the total expenses, CTotal, on all protection measures on all three layers:
Having objective Equations (13.5) and (13.6), one can formulate the following optimization problems:
Optimally allocate total available resources C0 that guarantee the minimum possible loss of defended objects against terrorists' attacks, that is,
(13.7) ![]()
Optimally allocate resources that guarantee the acceptable expected loss of defended objects against terrorist attacks with minimum possible expenses, that is,
(13.8) ![]()
Solution of these problems with the use of the steepest descent method is demonstrated on a simple illustrative numerical example.
Consider a fictional case study concerning embassy protection. There are three embassies within a geographical zone (Fig. 13.5). Embassies are assumed to have different indices according to priority (“weights”) and location in countries with different attitudes toward the country presented by the respective embassy. The problem is to protect all these embassies from terrorist attacks. Assume that there are available resources for embassy protection within each given zone (financial, military, logistics, etc.). How should they be allocated in the most reasonable way?
FIGURE 13.5 Allocation of embassies within a geopolitical region.
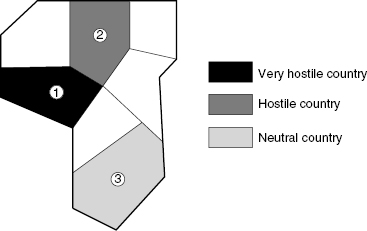
Let the following data be given by counter-terrorism experts. Assume that we consider only three embassies. The characteristics of these embassies are presented in Table 13.2, Table 13.3, and Table 13.4. The “weight” of importance might depend, for instance, on the size of the embassy (number of employees) or its political significance.
TABLE 13.2 “Weight” of Importance = 10; Level of Protection with No Special Measures P1(0) = 0.5
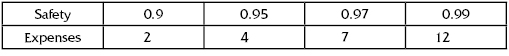
TABLE 13.3 “Weight” of Importance = 3; Level of Protection with No Special Measures P2(0) = 0.8
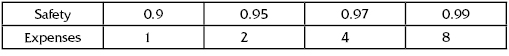
TABLE 13.4 “Weight” of Importance = 7; Level of Protection with No Special Measures P3(0) = 0.9

Calculate “discrete gradients” (relative increments) for each embassy k by using the formula:
(13.9) 
where Wk = “weight” of importance of the Embassy k,![]() = level of protection at step s of the process of defense improving, and
= level of protection at step s of the process of defense improving, and ![]() = expenses related to the level of protection at step s of the process of defense improving.
= expenses related to the level of protection at step s of the process of defense improving.
Let us construct Table 13.5, which will be used (in a very simple way!) to get an optimal allocation of money for defenses of all three embassies.
TABLE 13.5 Values of Step-by-Step “Gradients”
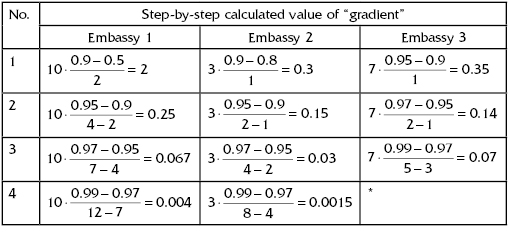
Now number all cells of Table 13.5 by decreasing values (Table 13.6). These numbers give the order of introducing corresponding protective measures. So, the final results are given as follows:


and the spent resources are equal to C(1) = 2.
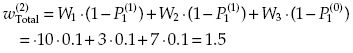
and the spent resources are equal to C(2) = 2 + 1 = 3.

and the spent resources are equal to C(3) = 2 + 1 + 1 = 4.
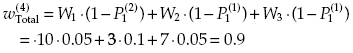
and the spent resources are equal to C(4) = 2 + 1 + 1 + 2 = 6.
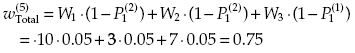
and the spent resources are equal to C(5) = 2 + 1 + 1 + 2 + 1 = 7.
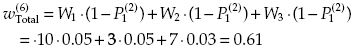
and the spent resources are equal to C(6) = 2 + 1 + 1 + 2 + 1 + 1 = 8.
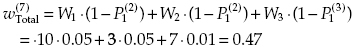
and the spent resources are equal to C(7) = 2 + 1 + 1 + 2 + 1 + 1 + 2 = 10.
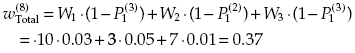
and the spent resources are equal to C(8) = 2 + 1 + 1 + 2 + 1 + 1 + 2 + 3 = 13.
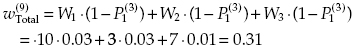
and the spent resources are equal to C(9) = 2 + 1 + 1 + 2 + 1 + 1 + 2 + 3 + 2 = 15.
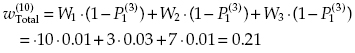
and the spent resources are equal to C(10) = 2 + 1 + 1 + 2 + 1 + 1 + 2 + 3 + 2 + 5 = 20.
TABLE 13.6 Ordered Values of “Gradients”
The process of constructing tradeoff cost–protection can be continued. Graphical presentation of the steepest descent solution is presented in Figure 13.6.
FIGURE 13.6 Tradeoff cost–protection.

This theoretical approach can be used for assessing, planning, modeling, and managing counter-terrorism measures. Some ideas of this approach were applied to modeling survivability of the National Energy System for the former USSR.
Further development of proposed theoretical approach and its implementation for various possible scenarios can significantly boost the analytic resources and predictive capabilities of fighting against terrorism. The approach is powerful enough for the solution of complex and highly unstructured problems. Based on this approach, one can formulate much more complex and realistic problems to include various “what if” scenarios and additional information: known gaps in security system, counter-terrorism intelligence, impact of preemptive strikes against terrorist groups, fuzzy information about terrorist plans and capabilities, and so on. Also, the proposed approach can be used to identify the most appropriate security measures and develop an optimal strategy aimed at providing maximum possible protection against terrorist threat. Finally, it may be useful in exploring the impact of budget cuts and resource reallocation scenarios on protection issues.
13.6 Fictional Case Study
13.6.1 Some Preliminary Comments
Before considering the fictional case study, let us once more briefly characterize the proposed model.
This mathematical model can be used for design of an interactive computer model, which can be used by counter-terrorism decision makers to solve the following problems:
- What are the priorities of the subjects of protection?
- What measures are most appropriate to protect these subjects?
- What is the best money allocation for this protection?
Notice from the very beginning that we are going to design a model for analysis of the entire problem as a unique and single “body.”
A decision-maker will be able to “play” with the model, change parameters and limitations and get current results. In other words, it will be a “what if” type of model.
13.6.2 Suggested Procedure to Use the Model
An expert enters the following input data into the model:
- List of assumed objects of terrorists' attacks
- Priority of defended objects
- Estimated cost of various defending measures
- Estimated performance of the protection of listed subjects
- Limitation on the resources assigned for the protection program.
The model will present an output (solution) in the form of resource allocation between various measures of protection and between the chosen subjects of defense.
13.6.3 Input Data
- List of subjects of protection
- Categorization of the subjects of protection: human lives (at stadiums, conventions, etc.), economical, political, historical/symbolical
- Expert-prepared relative priorities of these subjects (on scale from 1 to 10, for instance)
- Assumed enemy's priorities of destruction of the same subjects
- Total resources for anti-terrorist activity on the country level and on regional levels
- Categorization of types of possible terrorist attacks for each subject of protection
- Expert's evaluation of the “degree of assurance” that the given subject of protection would be saved if some specified measures would have been undertaken
- Cost of reliable information about terrorists' plans, their location, forms of their support, and so on
- Experts' evaluation of the performance of the pre-emptive anti-terrorist strikes depending on the expenses.
Of course, the number of listed types of input information should be corrected (as well as the model itself) during real implementation.
Expected results of the modeling:
- The computer tool will allow a decision maker to estimate numerically the effect of counter-terrorism measures and will help to make optimal (rational) allocation of the available resources.
- The model will give the decision maker a range of human resources, finances, logistics, and so on needed for achieving the desired goal of protection of the chosen objects.
13.6.4 Description of the Subjects of Defense
Consider some fictional city, let's call it Freedom City, where there are the following subjects for counter-terrorism protection:
Let πk be a priority number of subject k. The priority number in some sense reflects the priority of the subject for the society. Of course, such “scalar” evaluation is a trivialization of the problem, but this method is used in many cases by Operations Research analysts. The numerical value of πk has to be decided by counter-terrorism experts. Let the priority numbers for the considering fictional example are:
For the beginning, we do not pay attention to the specifics of the protected subject (human, economic, or political). These factors might be taken into account on the further stages of the research.
13.6.5 Description of types of possible attacks
Consider possible types of terrorists' attacks on the listed subjects and measures of protection.
Stadium
Possible types of attacks:
- Suicide bomber
Form of protection:
- Private planes or helicopters used as kamikaze
Form of protection:
- Regular civil planes
Form of protection:
Monument of Glory
Possible types of attacks:
- Suicide bomber
Form of protection:
- Private planes or helicopters
Form of protection:
- Regular civil planes
Form of protection:
Great Bridge
Possible types of attacks:
- Suicide car bomber
Form of protection:
- Bomb at the pier of the bridge
Form of protection:
Stock Exchange
Possible types of attacks:
- Suicide car bomber
Form of protection:
- Suicide bomber
Form of protection:
National Park
Possible types of attacks:
- Suicide bomber
Form of protection:
From a brief analysis of measures above, one can see that some measures are local and specific for a particular subject of protection, some of them are common for objects within a particular region (or area), and, finally, some measures protect all subjects in the country.
For instance, the following two measures:
- police checking suspicious vehicles entering Freedom City and
- gathering information about unusual or suspicious activity within some communities
are local measures effective for the entirety Freedom City, but only for this city. At the same time, such measures as:
- strong visa checking at the country borders
- attentive attendee checking at the pilot training centers (with strong profiling of the trainees)
- closer checking at airports, especially to and from main cities, and
- putting marshals at the civil planes influence the subjects of protection within the entire country. All counter-terrorism pre-emptive strikes abroad always have an effect on the level of entire country.
13.7 Measures of Defense, Their Effectiveness, and Related Expenses
In Table 13.7 we consider the simplest case study for the situation described above. All numbers are fictional. Expenses for various protection measures are taken in some conditional units (CU).
TABLE 13.7 Measures of Protection at the Federal Level

13.7.1 Federal Level of Protection
All expenses are to protect all objects within the country, so “individual” expenses for a single object will be relatively small. (For instance, defending 10,000 objects within the country due to introducing strong control for staying in the country with guest visas will correspond approximately from 0.03 to 0.05 CU of expenses for each object.)
The list of possible types of protection measures on all levels, corresponding levels of protection, and related expenses have to be prepared by experts familiar with security problems.
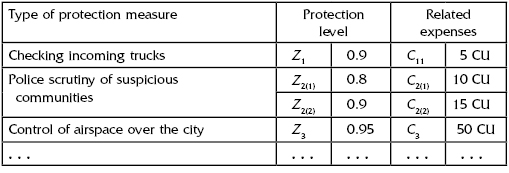
13.7.2 Zone (Regional) Level of Protection
Every zone has to be considered individually because they have their own specific characteristics and their own measures of protection. Consider Freedom City as a zone and consider possible protection measures on the zone (regional) level (Table 13.8).
TABLE 13.8 Measures of Protection on the State Level
13.7.3 Local (Object) Level of Protection
All objects have to be considered individually because they have their own specific characteristics and their own measures of protection. Besides, the same measures of protection might have different effects on different objects (Table 13.9, Table 13.10, Table 13.11, Table 13.12, and Table 13.13).
TABLE 13.9 Measures of Stadium Protection

TABLE 13.10 Measures of Monument of Glory Protection
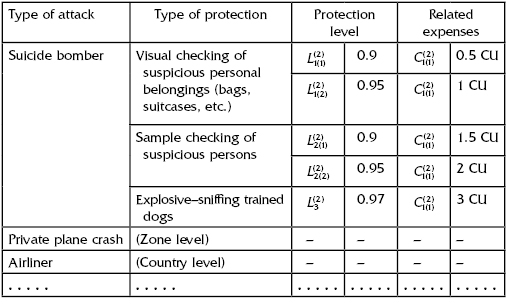
TABLE 13.11 Measures of Great Bridge Protection

TABLE 13.12 Measures of Stock Exchange Protection
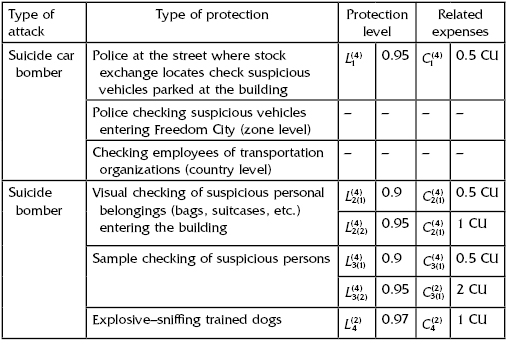
TABLE 13.13 Measures of National Park Protection

13.7.4 Calculation of Protection Level for Subjects of Defense
Demonstration of calculation of protection level will be performed on a single object, since calculation by hand is too time-consuming, and in addition, a huge number of numerical results could make explanation not transparent.
which after substitution of numerical values gives the result LOSSstadium = 0.0001.
Corresponding expenses are: on the country level = 55 CU, on the zone level = 10 CU, and on the object level = 4 CU. Notice once more that the largest expenses are on the country level though these expenses are “shared” by all objects.
Taking into account only local (individual) factors, Equation (13.10) can be rewritten as follows:
(13.11) ![]()
that is, we keep only variables related to the local level. Then, analyzing all possible measures, we will get the results presented in Table 13.14. In more visual form, the results are presented in Figure 13.7.
FIGURE 13.7 Tradeoff cost–protection.
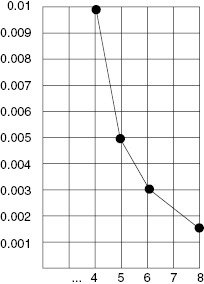
TABLE 13.14 Results of Solutions
All these values can be used as members of the dominating sequences for further analysis. Such kind of analysis allows one to choose a balanced and effective allocation of resources between all three levels and to assign measures for each defended object depending on the possible type of terrorist attack.
13.8 Antiterrorism Resource Allocation under Fuzzy Subjective Estimates
13.8.1 Preliminary
The problem of optimal resource allocation for antiterrorism measures is naturally based on subjective estimates made by experts in this field. Relying on expert estimates is inevitable in this case: there is no other way to get input data for the system survivability analysis. There is no way to collect real data; moreover, there are no homogenous samples for consistent statistical analysis of observations, since any case is unique and nonreproducible. Nevertheless, quantitative analysis of necessary levels of protection has to be performed.
What are the subjects of such expertise? It seems to us that they are the following:
- Possibility of terrorist attacks on some object or group of objects
- Possible time of such attack
- Expected consequences of the attack and possible losses
- Possible measure of protection and related expenses.
Since expert estimates of such complex things are fuzzy due to lack of common understanding of the same actions and counter-actions within a group of experts, the question arises: is it possible at all to make any reasonable prognosis and, moreover, judgment about “optimal allocation of protection resources”?
First of all, we should underline that the concept of “optimal solution” relates only to mathematical models. In practice unreliable (and even inconsistent) data and inevitable inaccuracy of the model (i.e., the difference between a model and reality) allow us to speak only about “rational solutions.”
Nevertheless, in practice the problem exists and in any particular case has to be solved with or without using mathematical models. Our objective is to analyze the stability of solutions of optimal resource allocation under the fuzziness of experts' estimates.
13.8.2 Analysis of Solution Stability: Variation of the Expense Estimates
First, let us analyze how variation of expenses estimates influences the solution of the problem on the level of a single object that has to be protested against terrorist attack. For transparency of explanation, we avoid considering the influence of defense on the federal and state levels.
Let us consider some conditional object (Object 1) that can be a subject of a terrorist attack. It is assumed that there may be three different types of enemy actions (Act. 1, Act. 2, and Act. 3). The defending side can choose several specific protection measures against each type of action {M(i, j), where i corresponds to the action type, and j corresponds to the type of undertaken protective measure.
Assume that we have three variants of estimates of protection measure costs: lower, middle, and upper as are presented in Table 13.15, Table 13.16, and Table 13.17. Here the lower estimates are about 20% lower of the corresponding middle estimates, and the upper ones are also about 20% higher.
TABLE 13.15 Case of Optimistic Estimates
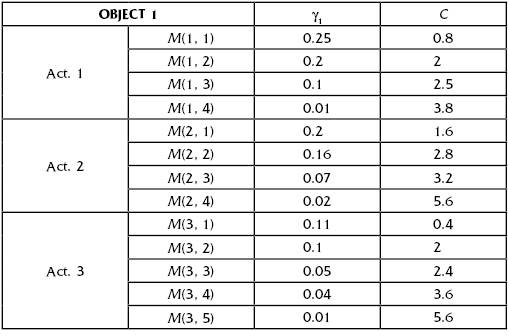
TABLE 13.16 Case of Moderate Estimates
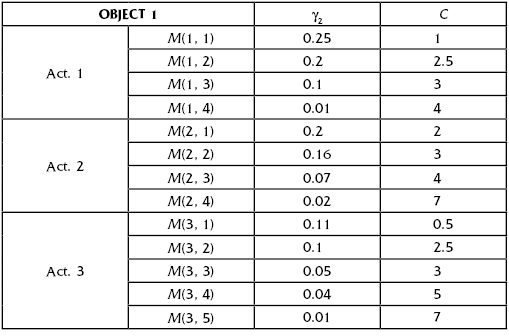
TABLE 13.17 Case of Pessimistic Estimates

There are three types of expert estimates: “optimistic,” “moderate,” and “pessimistic.” The first ones assume that success in each situation can be reached by low expenses for protective measures, the last group requires larger expenses for protection in the same situation, and the middle group lies in between.
How can data in these tables be interpreted?
Let us consider the possibility of Act. 1 against the object. With no protection at all, the object's vulnerability equals 1 (or 100%). If one would have spent ΔE = 0.8 conditional cost units (CCU) and undertook measure M(1, 1), the object's vulnerability decreases to 0.25. If one does not satisfy such a level of protection, the next protective measure (M(1, 2)) is applied; that leads to decreasing the object vulnerability from 0.25 to 0.3 and costs 2 CCU.
Now let us consider all three possible terrorist actions. In advance nobody knows what kind of action will be undertaken against the defending object. In this situation the most reasonable strategy is providing equal defense levels against all considered types of terrorist attacks. It means that if one needs to ensure that a level of protection equals γ then one has to consider only such measures against each action that deliver a vulnerability level not less than γ. For instance, in the considered case, if the required level of vulnerability has to be no higher than 0.1, one has to use simultaneously the following measures of protection against possible terrorists' attacks: M(1, 3), M(2, 3), and M(3, 2).
The method of equal protection against the various types of hostile attacks appears to be quite natural. If dealing with natural or other unintended impacts, one can speak about the subjective probabilities of impacts of some particular type of course; in a case of intentional attack from a reasonably thinking enemy, such an approach is not appropriate. The fact is that as soon as the enemy knows about your assumptions about his possible actions, he takes advantage of this knowledge and choose the hostile action that you expect least of all.
In the example considered earlier in this chapter, if one chooses measures M(1, 2) with γ1 = 0.2, M(2, 3) with γ2=0.07 and M(3, 4) with γ3=0.04, the guaranteed level of the object protection is
![]()
For choosing a required (or needed) level of object protection, one can compile a function reflecting the dependence of vulnerability of protection cost (Table 13.18). This function is depicted in Figure 13.8. Without detailed explanations, we present numerical results for the cases of “moderate” (Table 13.19 and Fig. 13.9) and “pessimistic” (Table 13.20 and Fig. 13.10) estimates.
FIGURE 13.8 Dependence of the object survivability on cost of protection measures (for “optimistic” estimates).

FIGURE 13.9 Dependence of the object survivability on cost of protection measures (for “moderate” estimates).

FIGURE 13.10 Dependence of the object survivability on cost of protection measures (for “pessimistic” estimates).

TABLE 13.18 Case of Optimistic Estimates

TABLE 13.19 Case of Moderate Estimates

TABLE 13.20 Case of Pessimistic Estimates

Such analysis allows the possibility to find what measures should be undertaken for each required level of protection (or admissible level of vulnerability) and given limited resources. The final trajectory of the dependency of expenses versus vulnerability is presented in Figure 13.11. Using the the data presented for each estimate, consider two solutions of the direct problem with required levels of vulnerability 0.1 and 0.02.
FIGURE 13.11 Comparison of solutions for three types of estimates.
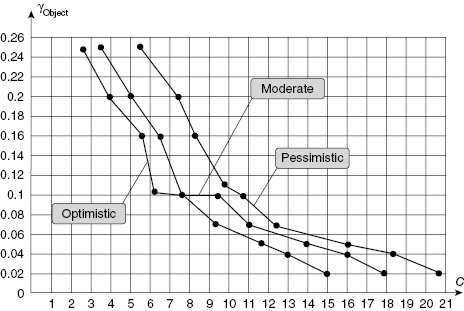
However, decision makers are interested mostly in the correctness of undertaken measures, rather than in the difference in absolute values of the estimated costs of the object protection.
It is obvious that if the goal is to reach some given level of vulnerability the vector of the solution (i.e., set of undertaken measures for protecting the object against terrorist attacks) in the frame of considered conditions the vector of solution will be the same, though will lead to different expenses.
Consider solutions for the required level of object vulnerability not higher than 0.1 and not lower than 0.02. They are presented in Table 13.21. One can see that solutions for all three scenarios coincide for both levels of object protection. Of course, such situations do not always occur, however, we should underline that vectors of the solution for minimax criterion γObject = max (γ1, γ2, γ3) are much more stable than vectors for probabilistic criterion ![]() ).
).
TABLE 13.21 Comparison of Solutions for Three Types of Scenarios
| Type of scenario | Undertaken protection measures | |
|---|---|---|
| γObject ≤ 0.1 | γObject ≤ 0.02 | |
| Optimistic | M(1, 3), M(2, 3), M(3, 2) | M(1, 4), M(2, 4), M(3, 5) |
| Moderate | M(1, 3), M(2, 3), M(3, 2) | M(1, 4), M(2, 4), M(3, 5) |
| Perssimistic | M(1, 3), M(2, 3), M(3, 2) | M(1, 4), M(2, 4), M(3, 5) |
13.9 Conclusion
The presented analysis shows that the model of optimal allocation of counter-terrorism resources suggested in the previous section is working stably enough. Development of an improved computer model will allow analysis of more realistic situations, including random instability of input data. However, it seems that such “one-side biased” expert estimates can lead to more serious errors than random variations of the parameters.
Notes
1 CREATE: National Center for Risk and Economic Analysis of Terrorism Events (at the University of Southern California, Los Angeles).
2 GAZPROM is the largest Russian company and the world's biggest owner of oil and natural gas.
Chronological Bibliography
Rudenko, Y., and Ushakov, I. 1979. “On evaluation of survivability of complex energy systems.” Journal of the Academy of Sciences of the USSR, Energy and Transportation, no. 1
Kozlov, M., Malashenko, Y., Rogozhin, V., Ushakov, I., and Ushakova, T. 1986. “Computer model of energy systems survivability: methodology, model, implementation” (in Russian). The Computer Center of the Academy of Sciences of the USSR, Moscow.
I. Ushakov. 1994. “Vulnerability of Complex Systems.” In Handbook of Reliability Engineering. ed. I. A. Ushakov. John Wiley & Sons.
Barbacci M. 1996. “Survivability in the age of vulnerable systems.” Computer, no. 29.
Levitin, G., and Lisnianski, A. 2000. “Survivability maximization for vulnerable multi-state system with bridge topology.” Reliability Engineering and System Safety, no. 70.
Levitin, G., and Lisnianski, A. 2001. “Optimal separation of elements in vulnerable multi-state systems.” Reliability Engineering and System Safety, no. 73.
Levitin, G. 2003. “Optimal allocation of multi-state elements in linear consecutively-connected systems with vulnerable nodes.” European Journal of Operational Research, no. 2.
Levitin, G. 2003. “Optimal multilevel protection in series-parallel systems.” Reliability Engineering and System Safety, no. 81.
Levitin, G., and Lisnianski, A. 2003. “Optimizing survivability of vulnerable series-parallel multi-state systems.” Reliability Engineering and System Safety, no. 79.
Levitin G., Dai Y., Xie M., Poh K. L. 2003. “Optimizing survivability of multi-state systems with multi-level protection by multi-processor genetic algorithm.” Reliability Engineering and System Safety, no. 82.
Bier, V. M., Nagaraj, A. and Abhichandani, V. 2005. “Protection of simple series and parallel systems with components of different values,” Reliability Engineering and System Safety, no. 87.
Korczak, E., Levitin, G. and Ben Haim, H. 2005. “Survivability of series-parallel systems with multilevel protection.” Reliability Engineering and System Safety, no. 90.
Ushakov, I. A. 2005. “Cost-effective approach to counter-terrorism.” Communication in Dependability and Quality Management, no. 3.
Ushakov, I., and Muslimov, A. 2005. “Cost-effective approach to counter-terrorism.” International Symposium on Stochastic Models in Reliability, Safety, Security and Logistics (book of abstracts), Beer-Sheva.
Ushakov, I. A. 2006. “Counter-terrorism: protection resources allocation. Part I. Minimax criterion.” Reliability: Theory and Applications, no. 2.
Ushakov, I. A. 2006. “Counter-terrorism: protection resources allocation. Part II. Branching system.” Reliability: Theory and Applications, no. 3.
Bochkov, A. V., and Ushakov, I. A. 2007. “Sensitivity analysis of optimal counter-terrorism resources allocation under subjective expert estimates.” Reliability: Theory and Applications, no. 2
Korczak, E., and Levitin, G. 2007. “Survivability of systems under multiple factor impact.” Reliability Engineering and System Safety, no. 2.
Levitin, G. 2007. “Optimal defense strategy against intentional attacks.” IEEE Transactions on Reliability, no. 1.
Ushakov, I. A. 2007. “Counter-terrorism: protection resources allocation. Part III. Fictional ‘case study.’ ” Reliability: Theory and Applications, no. 1.
Hausken, K. 2008. “Strategic defense and attack for series and parallel reliability systems.” European Journal of Operational Research, no. 2.
Hausken, K. 2008. “Strategic defense and attack of complex networks.” International Journal of Performability Engineering, no. 4.
Hausken K., and Levitin, G. 2009. “Minmax defense strategy for complex multi-state systems.” Reliability Engineering and System Safety, no. 94.