CHAPTER 18
Conditional Access in Configuration Manager
IN THIS CHAPTER
![]() Understanding Modern Authentication
Understanding Modern Authentication
![]() Implementing Configuration Manager Policies
Implementing Configuration Manager Policies
![]() Enabling Conditional Access for Exchange Online
Enabling Conditional Access for Exchange Online
![]() Enabling Conditional Access for SharePoint Online
Enabling Conditional Access for SharePoint Online
![]() Enabling Conditional Access for Skype for Business Online
Enabling Conditional Access for Skype for Business Online
As described in Chapter 16, “Integrating Intune Hybrid into Your Configuration Manager Environment,” System Center Configuration Manager (ConfigMgr) can be integrated with Microsoft Intune. This integration provides many powerful new features for ConfigMgr. One of the most widely deployed of those features, conditional access, involves securing access to corporate resources from mobile devices and is the focus of this chapter.
One of the greatest challenges for today’s information technology (IT) professionals is the elimination of corporate boundaries. The advent of bring your own device (BYOD) requires IT to adapt its security policies to control a myriad of devices and security settings. Administrators previously could protect corporate devices and data from the outside world by hiding them behind many layers of security. That is no longer possible; IT must allow external access to data as users are demanding total flexibility in managing their professional and personal business wherever they are and on their devices of choice.
At the time this book was published, ConfigMgr’s conditional access feature could secure access to the following services:
![]() Microsoft Exchange Online
Microsoft Exchange Online
![]() SharePoint Online
SharePoint Online
![]() Skype for Business Online
Skype for Business Online
![]() Microsoft Exchange On-Premises
Microsoft Exchange On-Premises
This chapter provides an overview of modern authentication and describes the steps to implement conditional access for each of these services.
Understanding Modern Authentication
Modern apps use modern authentication. This Microsoft solution is utilized during the conditional access workflow. Modern authentication is based on the Active Directory Authentication Library (ADAL) and OAuth 2.0 (an open standard for authorization). ADAL is a code library, designed to allow secure access for client applications to resources via security tokens. ADAL works with OAuth 2.0 to enable advanced authentication and authorization scenarios; this includes multi-factor authentication (MFA) and additional forms of Security Assertion Markup Language (SAML) Authentication.
ADAL assists developers in easily obtaining access tokens from Azure Active Directory (AD) and Windows Server Active Directory Federation Services (ADFS) for Windows Server 2012 R2, which can be used to request access to protected resources.
ADAL removes the need for modern apps to use basic authentication protocols and allows them to use browser-based authentication (known as passive authentication), where the user is directed to an identity provider’s web page to authenticate.
Apps that act as clients can leverage modern authentication. Modern authentication conversations have the following features:
![]() A client app, which makes a request to access a resource (for example, Outlook for iOS) and attempts to access Exchange Online
A client app, which makes a request to access a resource (for example, Outlook for iOS) and attempts to access Exchange Online
![]() A resource to which the client needs a specific level of access, and this resource is secured by a directory service (such as Exchange Online)
A resource to which the client needs a specific level of access, and this resource is secured by a directory service (such as Exchange Online)
![]() An OAuth connection, which authorizes a user to access a resource
An OAuth connection, which authorizes a user to access a resource
Table 18.1 shows the current availability of modern across Office applications.
TABLE 18.1 Modern Authentication in Office Apps
Client App |
Windows |
Windows Phone |
iOS |
Android |
Office |
Available in Office 2013 and Office 2016 |
Not available |
Available in Word, Access, and PowerPoint |
Available in Word, Access, and PowerPoint |
Outlook |
Included with Office 2013 and 2016 |
Not available |
Available |
Available |
Skype for Business |
Included with Office 2013 and 2016 |
Not available |
Available |
Available |
OneDrive for Business |
Included with Office 2013 and 2016 |
Available for Windows Phone 8.1 and later |
Available |
Available |
Modern authentication may not turned on by default for all services. For example, Table 18.2 shows the default modern authentication states for Office 365 services.
TABLE 18.2 Modern Authentication States for Office 365 Services
Service |
Default State |
Details |
Exchange Online |
Off |
Turn on with PowerShell; see http://social.technet.microsoft.com/wiki/contents/articles/32711.exchange-online-how-to-enable-your-tenant-for-modern-authentication.aspx. |
SharePoint Online |
On |
Not available. |
Skype for Business Online |
Off |
Turn on with PowerShell; see http://social.technet.microsoft.com/wiki/contents/articles/34339.skype-for-business-online-enable-your-tenant-for-modern-authentication.aspx. |
NOTE: MODERN AUTHENTICATION STATES
Table 18.2 shows the modern authentication state of the services for all tenants created before August 1, 2017. The services are turned on by default for all tenants created after that time.
NOTE: MODERN AUTHENTICATION
Conditional access requires modern authentication for use with modern apps. However, you can also implement conditional access without modern authentication by using other supported apps, such as built-in mail clients for iOS and Android, which use basic authentication.
Implementing Configuration Manager Policies
There are two policy types for implementing conditional access in ConfigMgr:
![]() Compliance Policies: These policies contain the rules and settings used to determine whether a device is compliant. Compliance rules include advanced password settings, encryption, whether a device is jailbroken or rooted, and whether email on the device is managed by an Intune policy. Rules can also check for minimum and maximum operating system (OS) versions.
Compliance Policies: These policies contain the rules and settings used to determine whether a device is compliant. Compliance rules include advanced password settings, encryption, whether a device is jailbroken or rooted, and whether email on the device is managed by an Intune policy. Rules can also check for minimum and maximum operating system (OS) versions.
![]() Conditional Access Policies: Conditional access policies are used to enable conditional access for a particular service. These policies define which user groups are targeted or exempt. A conditional access policy permits only devices deemed compliant (that is, satisfying the compliance policy) to access a service.
Conditional Access Policies: Conditional access policies are used to enable conditional access for a particular service. These policies define which user groups are targeted or exempt. A conditional access policy permits only devices deemed compliant (that is, satisfying the compliance policy) to access a service.
NOTE: ABOUT COMPLIANCE POLICIES
Compliance policies are optional. If no compliance policy is configured, all devices are deemed compliant by the conditional access policies.
Supported Compliance Policy Settings
Table 18.3 and Table 18.4 list the compliance policy settings for Windows, iOS, and Android, showing supported settings for these systems. These tables also show how noncompliant settings are managed when a policy is used with a conditional access policy.
TABLE 18.3 Supported Compliance Settings and Noncompliant Device Management in Windows
Compliance Setting |
Windows 8.1 and Later |
Windows Phone 8.1 and Windows Mobile 10 |
PIN or password configuration |
Remediated |
Remediated |
Device encryption |
N/A |
Remediated |
Jailbroken or rooted device |
N/A |
N/A |
Email profile |
N/A |
N/A |
Minimum OS version |
Quarantined |
Quarantined |
Maximum OS version |
Quarantined |
Quarantined |
TABLE 18.4 Supported Compliance Policy Settings and Noncompliant Device Management in iOS and Android
Compliance Setting |
iOS |
Android |
Samsung Knox |
PIN or password configuration |
Remediated |
Quarantined |
Quarantined |
Device encryption |
Remediated |
Quarantined |
Quarantined |
Jailbroken or rooted device |
Quarantined |
Quarantined |
Quarantined |
Email profile |
Quarantined |
N/A |
N/A |
Minimum OS version |
Quarantined |
Quarantined |
Quarantined |
Maximum OS version |
Quarantined |
Quarantined |
Quarantined |
Noncompliant settings are managed as follows:
![]() Remediated: The device OS is capable of enforcing compliance.
Remediated: The device OS is capable of enforcing compliance.
![]() Quarantined: The device OS is not capable of enforcing compliance. The device is blocked, and the user is notified about the non-compliance.
Quarantined: The device OS is not capable of enforcing compliance. The device is blocked, and the user is notified about the non-compliance.
NOTE: DEPLOYING COMPLIANCE POLICIES TO USERS
Compliance policies are deployed to user collections. The policies are then evaluated on all devices enrolled by those users.
Creating a Compliance Policy
Follow these steps in the ConfigMgr console to create a compliance policy:
1. Navigate to Assets and Compliance -> Compliance Settings -> Compliance Policies.
2. Right-click Compliance Policies and select Create Compliance Policy. The Create Compliance Policy Wizard is launched, as displayed in Figure 18.1.

FIGURE 18.1 The Create Compliance Policy Wizard.
3. Enter a suitable name and description for the policy. Select to create a policy for devices with or without the ConfigMgr client. For this example, choose Compliance rules for devices managed without the Configuration Manager client for mobile devices.
4. Select the device type. Figure 18.1 shows iOS chosen.
5. Specify the severity level to be reported in ConfigMgr reports if a device is deemed noncompliant with this policy. (The default setting is Warning.) Click Next to continue.
6. Select the platforms to be provisioned with this policy. The choices presented are dependent on the device type chosen on the previous page. Click Next.
7. Specify the rules for evaluating a compliant device. Some rules are specified by default. You can edit or delete these rules. Click New for additional rules, shown in Figure 18.2. After completing the Add Rule page, click Next to continue. Table 18.5 provides examples of compliance policy rules and the supported platforms.

FIGURE 18.2 Additional compliance policy rules.
TABLE 18.5 Compliance Policy Rules
Rule |
Details |
Supported Platforms |
Require password settings on mobile device |
Forces users to enter a password on the device. Enabled by default. |
iOS 8.0 and later Android 4.0 and later Samsung Knox Standard 4.0 and later Windows Phone 8 and later |
Minimum password length |
Six characters by default. |
iOS 8.0 and later Android 4.0 and later Samsung Knox Standard 4.0 and later Windows Phone 8 and later Windows 8.1 and later |
Allow simple passwords |
Simple passwords have repeated or consecutive numbers, for example. Disabled by default. |
iOS 8.0 and later Windows Phone 8 and later |
File encryption on mobile device |
Requires device encryption. Enabled by default. (See the note “iOS Encryption” in this section.) |
Android 4.0 and later Samsung Knox Standard 4.0 and later Windows Phone 8 and later (automatically encrypted) Windows 8.1 and later |
Jailbroken (iOS) or rooted (Android) devices will be non-compliant. Disabled by default. |
iOS 8.0 and later Android 4.0 and later Samsung Knox Standard 4.0 and later |
|
Minimum operating system version |
Earlier operating system versions will be non-compliant. |
iOS 8.0 and later Android 4.0 and later Samsung Knox Standard 4.0 and later Windows Phone 8 and later Windows 8.1 and later |
Maximum operating system version |
Later operating system versions will be non-compliant. |
iOS 8.0 and later Android 4.0 and later Samsung Knox Standard 4.0 and later Windows Phone 8 and later Windows 8.1 and later |
Email profile must be managed by Intune |
Device must use the email profile deployed to the device by Intune. Disabled by default. |
iOS 8.0 and later |
NOTE: IOS ENCRYPTION
iOS devices are encrypted when you configure the setting Require password settings on mobile devices.
8. Review the details on the Summary page. Click Next to complete the wizard. The compliance policy is now created.
9. Click Close to close the wizard.
NOTE: EDITING COMPLIANCE POLICY SETTINGS
Note that you cannot just turn some compliance settings on and off by toggling between True and False because this value is grayed out, as shown in Figure 18.3. You must remove the setting and add it again with a different value.
Deploying a Compliance Policy
To view a compliance policy, navigate to Assets and Compliance -> Compliance Settings -> Compliance Policies in the console. To deploy a policy to a user collection, follow these steps:
1. Right-click the policy and choose Deploy.
2. In the Deploy Compliance policy page, click Browse and select a user collection (see Figure 18.4).

FIGURE 18.4 Deploying a compliance policy.
3. Optionally choose to generate an alert when policy compliance falls below a defined amount (percentage).
4. Configure the policy evaluation schedule. Click OK to deploy the policy.
You now can use the compliance policy in conjunction with conditional access policies to control access to corporate services, as described in the following sections.
Enabling Conditional Access for Exchange Online
One of the most common use cases for conditional access is to protect and secure access to corporate email. This section demonstrates securing access to Exchange Online. Use the ConfigMgr console to begin the process of configuring a conditional access policy, which launches the Intune console to complete the operation.
Figure 18.5 shows the flow that conditional access policies for Exchange Online use to evaluate whether to allow or block devices.

FIGURE 18.5 Conditional access policy flow for Exchange Online.
Requirements for Exchange Online
There are a number of prerequisites to meet before implementing conditional access for Exchange Online. Only specific mail apps on specific devices are supported. There are also some Azure and Exchange requirements. Finally, modern authentication must be turned on for Exchange Online. These requirements are described in the following sections.
Exchange Online Supported Platforms and Apps
It is possible to control access to Exchange Online from the built-in Exchange ActiveSync mail client on the platforms and versions listed in Table 18.6. These clients use basic authentication.
The Microsoft Outlook app for iOS and Android is also supported for conditional access for Exchange Online (see Table 18.7). These are modern apps and require modern authentication to be turned on for Exchange Online.
TABLE 18.6 Exchange Online Conditional Access: Supported Built-in Mail Clients
Platform |
Supported Versions |
Google Android |
Version 4.0 and later (including Samsung Knox) |
Apple iOS |
Version 8.0 and later |
Windows Phone |
Version 8.1 and later |
Windows |
Windows 8.1 and later (managed as mobile devices) |
TABLE 18.7 Exchange Online Conditional Access: Additional Supported Apps
App |
Supported Platforms |
Microsoft Outlook |
Android and iOS |
Outlook 2013 and 2016 |
Windows desktop |
Additional Requirements for Exchange Online
Support for conditional access to Exchange Online depends on the following additional requirements:
![]() Devices must be workplace joined or enrolled with Intune. Devices must also be registered with the Azure Active Directory Device Registration Service. This is automatic when a device is enrolled or workplace joined.
Devices must be workplace joined or enrolled with Intune. Devices must also be registered with the Azure Active Directory Device Registration Service. This is automatic when a device is enrolled or workplace joined.
![]() Exchange Online subscription is required.
Exchange Online subscription is required.
![]() Users must each be assigned an Exchange Online license.
Users must each be assigned an Exchange Online license.
Turning on Modern Authentication for Exchange Online
Exchange Online must be configured to accept a modern authentication connection from modern apps. This is achieved by running PowerShell commands on the tenant:
1. Connect to Exchange Online by using remote PowerShell. For details, see https://technet.microsoft.com/library/jj984289(v=exchg.160).aspx.
2. Run the following command:
Set-OrganizationConfig -OAuth2ClientProfileEnabled:$true
3. Verify that the change was successful by running the following command:
Get-OrganizationConfig | ft name, *OAuth*
Enabling Conditional Access for Exchange Online
After all prerequisites are in place, conditional access can be enabled. A number of phases are involved, as discussed in the following sections:
![]() Evaluating the effect of the conditional access policy (optional but recommended)
Evaluating the effect of the conditional access policy (optional but recommended)
![]() Configuring Azure AD security groups (targeted and exempted)
Configuring Azure AD security groups (targeted and exempted)
![]() Configuring the conditional access policy
Configuring the conditional access policy
Evaluating the Effect of the Conditional Access Policy for Exchange Online
In the ConfigMgr console, navigate to Monitoring -> Reporting -> Reports. Under Device Management, run the report List of Devices by Conditional Access State to identify devices that will be blocked from Exchange Online when you enable conditional access. Select the collection to be evaluated and choose View Report. Figure 18.6 shows a sample report. Notice that one of the devices shown is not compliant, so email access to this device will be blocked. Notify affected users to remediate their devices before enabling conditional access; otherwise, they will not have access to email.

FIGURE 18.6 Conditional access evaluation report.
Configuring Security Groups for Exchange Online
Two group types can be specified when enabling conditional access. The conditional access policy is applied to targeted groups and is not applied to exempted groups.
NOTE: TARGETED AND EXEMPTED GROUPS
A user in both groups is exempt from the conditional access policy.
These groups are Azure AD security user groups and can be configured in one of two portals:
![]() Office 365 admin center
Office 365 admin center
![]() Azure portal
Azure portal
Configuring the Conditional Access Policy for Exchange Online
Follow these steps to enable conditional access for Exchange Online:
NOTE: ENABLING CONDITIONAL ACCESS
The technique described in this section is the supported method for enabling conditional access at the time this book was published. The ConfigMgr console provides a link that directs you to the conditional access node in the Intune portal. However, the authors anticipate that the mobile device management component of the Intune portal will be deprecated later in 2018.
Should that occur, the authors recommend that conditional access be enabled using the Azure portal.
1. In the ConfigMgr console, navigate to Assets and Compliance -> Compliance Settings -> Conditional Access.
2. Select Exchange Online. You are notified that conditional access policies for Exchange Online must be configured through the Intune console, as shown in Figure 18.7. Select Configure conditional access policy in the Intune console.

FIGURE 18.7 Conditional access for Exchange Online.
3. The Intune administration console is launched. Log in with the user account previously used to create the Intune subscription in ConfigMgr. You are immediately directed to the Exchange Online Policy page in the Intune console, shown in Figure 18.8.
4. Check the box Enable conditional access policy.
5. Choose to restrict all noncompliant devices or select the specific platforms.
6. Select whether to allow access to email in cases where Intune cannot manage the device.
7. Select the required targeted and exempt groups.
8. Click Save to save the policy, and it takes effect immediately.
NOTE: CONDITIONAL ACCESS POLICY DEPLOYMENT
A conditional access policy does not have to be deployed to users or devices. It takes effect immediately and is automatically applied when it is created.
Exchange Online End-User Experience
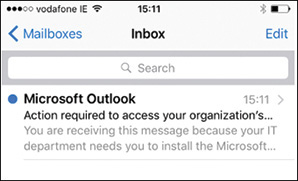
When conditional access is enabled, if a user tries to add an email account on an unmanaged or noncompliant device, the device is immediately blocked. The built-in mail client on an iPhone 6 is used in the example shown in Figures 18.9 and 18.10.
The user successfully added an Exchange Online mail account but sees only a single email, shown in Figure 18.9, warning that further action is required. This notification email cannot be customized.
The email contains further instructions and explains that the device must be enrolled with Intune before corporate email can be accessed. The user can click the Get started now hyperlink shown in Figure 18.10, which directs the user to download and install the Intune company portal. See Chapter 17, “Managing Mobile Devices,” for information on device enrollment.

FIGURE 18.10 Conditional access: Getting started.
Once the device is enrolled and compliant, the user can access his or her corporate email.
NOTE: CONDITIONAL ACCESS EMAIL BLOCKING INTERVALS
If a device is blocked (meaning it is not enrolled or is noncompliant), it is unblocked within two minutes if the user enrolls or remediates the device.
If the user subsequently un-enrolls a device, email is blocked after approximately six hours.
Enabling Conditional Access for SharePoint Online
Enabling conditional access for SharePoint Online is very similar to the process for Exchange Online, described in the preceding section. Conditional access for SharePoint Online allows you to control access to OneDrive for Business files located on SharePoint Online. Use the ConfigMgr console to begin the process of configuring a conditional access policy, which launches the Intune console, where you can complete the operation.
Figure 18.11 shows the flow used by conditional access policies for SharePoint Online when a targeted user attempts to connect to a file using a supported app such as OneDrive.

FIGURE 18.11 Conditional access policy flow for SharePoint Online.
Requirements for SharePoint Online
A number of prerequisites must be in place before you can enable conditional access for SharePoint Online. Only specific platforms, browsers, and apps are supported. There are also additional Azure and SharePoint requirements, described in the following sections.
Supported Platforms for SharePoint Online
You can control access to SharePoint Online from the platforms listed in Table 18.8. The built-in browsers on these devices use basic authentication.
TABLE 18.8 SharePoint Online Conditional Access: Supported Devices
Platform |
Supported Versions |
Google Android |
Version 4.0 and later (including Samsung Knox) |
Apple iOS |
Version 8.0 and later |
Windows Phone |
Version 8.1 and later |
Windows |
Windows 8.1 and later (managed as mobile devices) |
You can control access to SharePoint Online from the apps listed in Table 18.9. These apps require modern authentication, which is turned on by default for SharePoint Online.
NOTE: SHAREPOINT ONLINE DEFAULT STATE
For tenants created before August 1, 2017, SharePoint Online is the only Office 365 service for which modern authentication is turned on by default.
TABLE 18.9 SharePoint Online Conditional Access: Supported Apps
Apps |
Supported Platforms |
Microsoft Office Mobile |
Android |
Microsoft OneDrive |
Android and iOS |
Microsoft Word |
Android and iOS |
Microsoft Excel |
Android and iOS |
Microsoft PowerPoint |
Android and iOS |
Microsoft OneNote |
Android and iOS |
Additional Requirements for SharePoint Online
Additional requirements to support conditional access to SharePoint Online follow:
![]() Devices must be workplace joined or enrolled with Intune. Devices must also be registered with the Azure Active Directory Device Registration Service. This is automatic when a device is enrolled or workplace joined.
Devices must be workplace joined or enrolled with Intune. Devices must also be registered with the Azure Active Directory Device Registration Service. This is automatic when a device is enrolled or workplace joined.
![]() A SharePoint Online subscription is required.
A SharePoint Online subscription is required.
![]() Users must each be assigned a SharePoint Online license.
Users must each be assigned a SharePoint Online license.
Enabling Conditional Access for SharePoint Online
Evaluating the effect of the SharePoint Online conditional access policy in advance is the same as for Exchange Online, discussed earlier in this chapter, in the section “Evaluating the Effect of the Conditional Access Policy for Exchange Online.” The configuration of the targeted and exempted groups is also the same; see the earlier section “Configuring Security Groups for Exchange Online.”
Evaluating the Effect of the Conditional Access Policy for SharePoint Online
In the ConfigMgr console, navigate to Monitoring -> Reporting -> Reports. Under Device Management, use the List of Devices by Conditional Access State report to identify devices that will be blocked from SharePoint Online when you enable conditional access. Select the collection to evaluate and choose View Report. As shown in Figure 18.6, earlier in this chapter, one of the devices shown is not compliant, and access to protected corporate files by that device will be blocked. Notify affected users to remediate their devices before enabling conditional access; otherwise, they will not be able to access corporate SharePoint resources.
Configuring Security Groups for SharePoint Online
Two group types can be specified when enabling conditional access. The conditional access policy is applied to targeted groups and is not applied to exempted groups. These groups are Azure AD security user groups and can be configured in one of two portals:
![]() Office 365 admin center
Office 365 admin center
![]() Azure portal
Azure portal
Configuring the Conditional Access Policy for SharePoint Online
Follow these steps to enable conditional access for SharePoint Online:
1. In the ConfigMgr console, navigate to Assets and Compliance -> Compliance Settings -> Conditional Access.
2. Select SharePoint Online. You are notified that conditional access policies for SharePoint Online must be configured through the Intune console.
3. Select Configure conditional access policy in the Intune console. The Intune administration console is launched.
4. Log in with the user account used to create the Intune subscription in ConfigMgr. You are immediately directed to the Exchange Online Policy page in the Intune console.
5. Switch to Policy -> Conditional Access -> SharePoint Online Policy (see Figure 18.12).

FIGURE 18.12 Enabling conditional access for SharePoint Online.
6. Check the box Enable conditional access policy.
7. Choose the specific platforms for the policy.
8. Select the required targeted and exempted groups.
9. Click Save to save the policy, and it takes effect immediately.
The SharePoint Online End-User Experience
When conditional access is enabled, a user cannot open a SharePoint document on an unmanaged or a noncompliant device. The following example uses an iPhone 6 with Word for iOS installed.
The user opens a browser and navigates to the SharePoint site. The user wants to open a Word document, as shown in Figure 18.13.

FIGURE 18.13 Word document on SharePoint Online.
However, the device has not been enrolled, so the user cannot open the document and is notified that this SharePoint site is secured by conditional access, as shown in Figure 18.14.

FIGURE 18.14 Message that This SharePoint Site is secured by conditional access.
The user must enroll the device in order to proceed.
Enabling Conditional Access for Skype for Business Online
The process of enabling conditional access for Skype for Business Online is similar to the process for other services and is carried out using the Intune console. See the “Enabling Conditional Access for Exchange Online” and “Enabling Conditional Access for SharePoint Online” sections, earlier in this chapter, for details. Modern authentication must be enabled before you can implement conditional access for the Skype for Business app.
Figure 18.15 shows the flow used by conditional access policies when a targeted user attempts to use Skype for Business Online on his or her device. The following sections describe the prerequisites and steps for enabling conditional access.

FIGURE 18.15 Conditional access policy flow for Skype for Business Online.
Requirements for Skype for Business Online
Certain prerequisites must be fulfilled before you can enable conditional access for Skype for Business Online. Only specific platforms and apps are supported. There are also specific Azure and Skype for Business Online requirements. Finally, modern authentication must be turned on. The following sections describe the various requirements.
Supported Platforms for Skype for Business Online
You can control access to Skype for Business Online from the platforms listed in Table 18.10.
TABLE 18.10 Skype for Business Online Conditional Access: Supported Devices
Platform |
Supported Versions |
Google Android |
Version 4.0 and later (including Samsung Knox) |
Apple iOS |
Version 8.0 and later |
You can also control access to Skype for Business Online from the Skype for Business apps for Android and iOS.
Additional Requirements for Skype for Business Online
Additional requirements to support conditional access to Skype for Business Online include the following:
![]() Devices must be workplace joined or enrolled with Intune. Devices must also be registered with the Azure Active Directory Device Registration Service. This is automatic when a device is enrolled or workplace joined.
Devices must be workplace joined or enrolled with Intune. Devices must also be registered with the Azure Active Directory Device Registration Service. This is automatic when a device is enrolled or workplace joined.
![]() Skype for Business Online must be enabled for modern authentication (see the earlier section, “Understanding Modern Authentication”).
Skype for Business Online must be enabled for modern authentication (see the earlier section, “Understanding Modern Authentication”).
Turning on Modern Authentication for Skype for Business Online
Skype for Business Online must be configured to accept a modern authentication connection from modern apps. This is achieved by running PowerShell commands on the tenant. Follow these steps to configure Skype for Business Online:
1. Connect to Skype for Business Online by using remote PowerShell. For more information, see https://technet.microsoft.com/library/dn362795.aspx.
2. Run the following command:
Set-CsOAuthConfiguration -ClientAdalAuthOverride Allowed
3. Verify that the change was successful by running the following command:
Get-CsOAuthConfiguration
TIP: ORDER OF TURNING ON MODERN AUTHENTICATION
The authors recommend turning on modern authentication for Exchange Online prior to turning on modern authentication for Skype for Business Online.
Configuring Conditional Access for Skype for Business Online
Evaluating the effect of the Skype for Business Online conditional access policy in advance is the same as for Exchange Online; refer to the section “Evaluating the Effect of the Conditional Access Policy for Exchange Online,” earlier in this chapter. Configuration of the targeted and exempted groups is also the same. The section “Configuring Security Groups for Exchange Online,” earlier in this chapter, provides additional information.
Evaluating the Effect of the Conditional Access Policy for Skype for Business Online
To evaluate the effect of the conditional access policy, navigate to Monitoring -> Reporting -> Reports in the ConfigMgr console. Under Device Management, run the report List of Devices by Conditional Access State to identify devices blocked from Skype for Business Online when you enable conditional access. Select the collection to evaluate and choose View Report. As shown earlier in Figure 18.6, one of the devices shown is not compliant, and access to Skype for Business will be blocked for that device.
Notify affected users to remediate their devices before enabling conditional access; otherwise, they will not be able to access Skype for Business Online.
Configuring Security Groups for Skype for Business Online
You can specify two group types when enabling conditional access. The conditional access policy is applied to targeted groups and is not applied to exempted groups.
These groups are Azure AD security user groups and can be configured in one of two portals:
![]() Office 365 admin center
Office 365 admin center
![]() Azure portal
Azure portal
Configuring the Conditional Access Policy for Skype for Business Online
All configurations for Skype for Business Online are carried out directly using the Intune portal, https://manage.microsoft.com. Follow these steps:
1. Launch the portal and log in with a global administrator account.
2. Navigate to Policy -> Conditional Access -> Skype for Business Online Policy, as shown in Figure 18.16.
3. Check the box Enable conditional access policy.
4. Choose the specific platforms for the policy.
5. Select the required targeted and exempted groups.
6. Click Save to save the policy, and it takes effect immediately.
Enabling Conditional Access for Exchange On-Premises
Enabling conditional access for Exchange On-Premises is a very different process from the scenarios already described in this chapter for Exchange Online, SharePoint Online, and Skype for Business Online. In the case of Exchange On-Premises, all configurations are carried out using the ConfigMgr console rather than the Intune console. You must add an on-premise Exchange Server connector and configure a conditional access policy.
Several technologies are combined in the implementation of this solution:
![]() Microsoft Intune: Manages the compliance and conditional access policies for the device.
Microsoft Intune: Manages the compliance and conditional access policies for the device.
![]() Microsoft Azure AD: Authenticates the user and provides device compliance status.
Microsoft Azure AD: Authenticates the user and provides device compliance status.
![]() Configuration Manager: Manages device enrollment and provides reporting.
Configuration Manager: Manages device enrollment and provides reporting.
![]() Exchange On-Premises: Enforces access to email, based on the device state.
Exchange On-Premises: Enforces access to email, based on the device state.
Figure 18.17 shows the flow that conditional access policies for Exchange On-Premises use to evaluate whether to allow or block devices. The following sections describe the process.

FIGURE 18.17 Conditional access policy flow for Exchange On-Premises.
Requirements for Exchange On-Premises
A number of prerequisites must be in place before you can enable conditional access for Exchange On-Premises. Only specific devices and versions of Exchange are supported. Also, the on-premise Exchange connector must be deployed. These requirements are described in the following sections.
Supported Platforms for Exchange On-Premises
You can control access to Exchange On-Premises from the default mail client on the platforms listed in Table 18.11.
TABLE 18.11 Exchange On-Premises Conditional Access: Supported Devices
Platform |
Supported Versions |
Google Android |
Version 4.0 and later (including Samsung Knox) |
Apple iOS |
Version 8.0 and later |
Windows Phone |
Version 8.1 and later |
Windows |
Windows 8.1 and later (managed as mobile devices) |
Additional Requirements for Exchange On-Premises
Additional requirements to support conditional access to Exchange On-Premises include the following:
![]() The On-Premises Exchange version must be Exchange 2010 or later.
The On-Premises Exchange version must be Exchange 2010 or later.
![]() The On-Premises Exchange connector must be deployed (as discussed in the next section, “Implementing the Exchange Server connector”).
The On-Premises Exchange connector must be deployed (as discussed in the next section, “Implementing the Exchange Server connector”).
Implementing the Exchange Server Connector
To implement the Exchange Server connector, first create an AD account and configure it to run the following Exchange cmdlets:
![]()
Clear-ActiveSyncDevice
![]()
Get-ActiveSyncDevice
![]()
Get-ActiveSyncDeviceAccessRule
![]()
Get-ActiveSyncDeviceStatistics
![]()
Get-ActiveSyncMailboxPolicy
![]()
Get-ActiveSyncOrganizationSettings
![]()
Get-ExchangeServer
![]()
Get-Mailbox
![]()
Get-Recipient
![]()
Get-User
![]()
Set-ADServerSettings
![]()
Set-ActiveSyncDeviceAccessRule
![]()
Set-ActiveSyncMailboxPolicy
![]()
Set-CASMailbox
![]()
New-ActiveSyncDeviceAccessRule
![]()
New-ActiveSyncMailboxPolicy
![]()
Remove-ActiveSyncDevice
This account will be used as the Exchange Server connector account.
Follow these steps in the ConfigMgr console to add the Exchange Server connector:
1. Navigate to Administration -> Overview -> Exchange Server Connectors.
2. Right-click and select Add Exchange Server. The Add Exchange Server Wizard, shown in Figure 18.18, launches.
3. Specify the server address of an on-premise Exchange client access server and click Next to continue.
4. Specify the Exchange Server connector account. Also set an account to be used to send quarantine email notifications to clients that are blocked by conditional access. This account must have a valid mailbox on the Exchange server. If you do not specify both accounts, conditional access will fail. Click Next to continue.
5. Specify when and how to find the mobile devices to be managed using the Exchange Server connector. Choose whether the connector will discover all devices (the default) or just those in a specified organizational unit (OU). Set a synchronization schedule and click Next to continue. The Exchange ActiveSync policies already deployed on the Exchange Server are displayed.
6. Set the External mobile device management option to Allowed to ensure that mobile devices continue to receive email from Exchange after Configuration Manager enrolls them. Click Next to continue.
7. Review the Summary page and click Next to add the Exchange Server connector.
NOTE: EXCHANGE SERVER CONNECTOR SUPPORT
ConfigMgr supports a single connector per Exchange organization.
Configuring Conditional Access for Exchange On-Premises
When all the prerequisites are in place, conditional access can be enabled. There are a number of phases to follow, discussed in the following sections:
![]() Evaluating the effect of the conditional access policy (optional but recommended)
Evaluating the effect of the conditional access policy (optional but recommended)
![]() Creating ConfigMgr user collections (targeted and exempted)
Creating ConfigMgr user collections (targeted and exempted)
![]() Configuring the conditional access policy
Configuring the conditional access policy
Evaluating the Effect of the Conditional Access Policy for Exchange On-Premises
To evaluate the effect of the conditional access policy, navigate to Monitoring -> Overview -> Reporting -> Reports in the ConfigMgr console and run the report List of Devices by Conditional Access State to identify devices that will be blocked from accessing Exchange after you configure the conditional access policy.
Select the collection to be evaluated and choose View Report. As shown earlier in Figure 18.6, one of the devices shown is not compliant, and email access will be blocked.
Creating User Collections
Two collections can be specified when enabling conditional access. The conditional access policy is applied to targeted collections and is not applied to exempted collections.
NOTE: TARGETED AND EXEMPT COLLECTIONS
A user in both collections is exempt from the conditional access policy.
Navigate to Assets and Compliance -> Overview -> User Collections in the ConfigMgr console to create these collections.
Configuring the Conditional Access Policy for Exchange On-Premises
Follow these steps to enable conditional access for Exchange On-Premises:
1. In the ConfigMgr console, navigate to Assets and Compliance -> Compliance Settings -> Conditional Access.
2. Right click On-Premises Exchange and select Configure Conditional Access Policy to launch the Configure Conditional Access Policy Wizard, shown in Figure 18.19.
3. When you are presented with details on how the policy works, decide whether to select the Default rule override check box, which allows Intune enrolled and compliant devices to access Exchange. Click Next to continue.
4. Specify the targeted collection and click Next to continue.
5. Specify an exempted collection (optional).
6. Create custom text for the email Exchange sends to the users of blocked devices. You could also accept the default text, displayed in Figure 18.20.
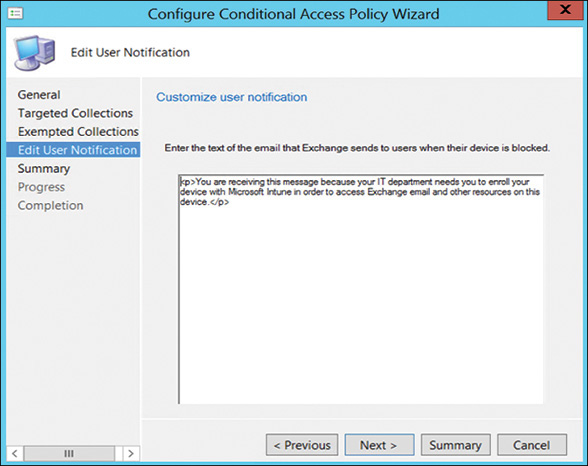
FIGURE 18.20 Customizing the notification email.
7. Review the Summary page and click Next to create the policy to enable conditional access.
The conditional access policy does not have to be deployed. It takes effect immediately.
The Exchange On-Premises End User Experience
When conditional access is enabled, if a user tries to add an email account on an unmanaged or a noncompliant device, the device is immediately blocked.
Refer to Figures 18.9 and 18.10, earlier in this chapter, which show that the user successfully added a mail account but sees only a single email warning that further action is required. The email contains instructions and explains that the device must be enrolled with Intune before corporate email can be accessed.
The end-user experience for conditional access with Exchange On-Premises is slightly different than the experience for Exchange Online users:
![]() When a user sets up an Exchange ActiveSync profile on a supported device, it may take from one to three hours for the device to be blocked if it is not compliant or enrolled with Intune.
When a user sets up an Exchange ActiveSync profile on a supported device, it may take from one to three hours for the device to be blocked if it is not compliant or enrolled with Intune.
![]() If a blocked user enrolls the device (or remediates non-compliance), email access is unblocked within two minutes.
If a blocked user enrolls the device (or remediates non-compliance), email access is unblocked within two minutes.
![]() If the user un-enrolls a device from Intune, it could take from one to three hours for the device to be blocked.
If the user un-enrolls a device from Intune, it could take from one to three hours for the device to be blocked.
Monitoring and Troubleshooting Conditional Access
Conditional access involves many components working together to protect corporate resources. Because many of the components are out of your control, it can sometimes be difficult to understand why a solution is not performing as you expect it should.
Conditional access is also a work in progress with significant development focus at this time. New functionality is being released rapidly and published on the Microsoft blogs. Refer to the following blogs for new information:
![]() ConfigMgr Team Blog: https://blogs.technet.microsoft.com/configmgrteam/
ConfigMgr Team Blog: https://blogs.technet.microsoft.com/configmgrteam/
![]() Intune Team Blog: https://blogs.technet.microsoft.com/microsoftintune/
Intune Team Blog: https://blogs.technet.microsoft.com/microsoftintune/
The following sections discuss what you can do to monitor and troubleshoot conditional access issues.
Monitoring Conditional Access Compliance
Use the ConfigMgr console to view the compliance status of conditional access policies. Follow these steps:
1. Navigate to Monitoring -> Overview -> Deployments and select a compliance policy deployment to review.
2. Right-click the policy and select View Status.
Figure 18.21 shows an example of a compliance policy deployment status.

FIGURE 18.21 Viewing compliance policy deployment status.
The deployment status page contains the following compliance states:
![]() Compliant
Compliant
![]() Error
Error
![]() Non-compliant
Non-compliant
![]() Unknown
Unknown
3. Double-click a user or device in the Asset Details pane for more details on the asset message. Figure 18.22 shows an example.
Troubleshooting Conditional Access
Troubleshooting conditional access is not as straightforward as troubleshooting other ConfigMgr features. ConfigMgr administrators are typically provided with many log files and error messages to investigate. However, because conditional access integrates with so many external services (mostly cloud based), it does not have the same extensive logging available. The exception is easdisc.log, which records the activities and the status of the Exchange Server connector for Exchange On-Premises access.
Troubleshoot conditional access by walking through each step of the solution to determine what was overlooked. Consider the following:
![]() Client Side: What client is configured in your solution? Are you using a modern app or a built-in mail client? Remember that not all combinations are supported. For example, modern apps are not supported for implementing conditional access with Exchange On-Premises.
Client Side: What client is configured in your solution? Are you using a modern app or a built-in mail client? Remember that not all combinations are supported. For example, modern apps are not supported for implementing conditional access with Exchange On-Premises.
![]() Server Side: If you are using modern apps, remember that modern authentication may not be turned on by default for Exchange Online or Skype for Business Online.
Server Side: If you are using modern apps, remember that modern authentication may not be turned on by default for Exchange Online or Skype for Business Online.
![]() Compliance Policy: Compliance policies are optional. However, have you deployed a policy that includes the settings you require?
Compliance Policy: Compliance policies are optional. However, have you deployed a policy that includes the settings you require?
![]() Conditional Access Policy: Has conditional access been enabled for the service you require? Have you configured your targeted and exempted users correctly?
Conditional Access Policy: Has conditional access been enabled for the service you require? Have you configured your targeted and exempted users correctly?
At the time this book was published, you could create free Microsoft support requests for all Intune-related activities. If you have difficulties with troubleshooting, locate your local number for Intune support at http://technet.microsoft.com/jj839713.aspx.
Summary
This chapter described conditional access, one of the most widely implemented features of the hybrid ConfigMgr and Intune solution. It discussed how conditional access ensures that access to corporate data can be limited to devices that are managed and compliant. This chapter talked about modern authentication, the cornerstone for conditional access for modern apps, and explained terms such as ADAL and OAuth.
The chapter introduced compliance and conditional access policies. It demonstrated how to configure and deploy these policies to control access to corporate services: Exchange Online, SharePoint Online, Skype for Business Online, and Exchange On-Premises. It also discussed monitoring the compliance of the conditional access policies on corporate devices.
Chapter 19, “Endpoint Protection,” discusses endpoint protection—that is, how to protect endpoints from malware. Beginning with ConfigMgr 2012, this feature, formerly called System Center Endpoint Protection, is now an integrated component of ConfigMgr.