Thinking like a Defender
The goal of this book is to help you prevent the logic flaws that lead to web application vulnerabilities, and we’ll do this in two ways. First, we’ll examine the code and configuration problems underlying specific web application vulnerabilities like cross-site scripting and SQL injection. It’s crucial to be properly educated in defense techniques for these vulnerabilities, because you will need to put them to the test.
![]() Note
Note
A lot of people think that they’re safe from attack because their company is too small to be noticed by attackers. Hackers only go after the big guys like Google and Microsoft, right? Think again: According to statistics from the IBM X-Force security research team, products from the top ten software vendors accounted for only 20 percent of reported vulnerabilities in 2010 (as seen in Table 1-1), and this number is down from 23 percent in 2009. Attackers are increasingly targeting the “long tail” of smaller organizations’ web applications, so never think that you’re too small to slip under their radar.
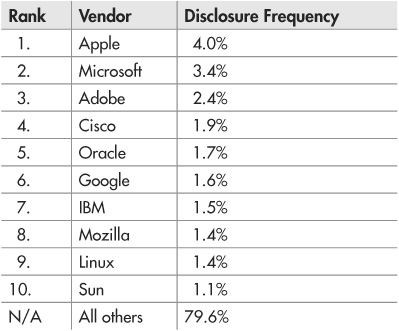
Table 1-1 2010 First-Half Vulnerability Disclosure Rates per Vendor (IBM X-Force 2010 Mid-Year Trend and Risk Report)
However, as with firewalls, knowing how to defend against specific web application attacks is necessary but not sufficient by itself. Beyond just looking at specific attacks, we also want to educate you on larger, more general security principles.
This is important because attack methods change all the time. Attackers refine their methods, finding new ways to break into systems that were previously thought to be secure. Every year, some security researcher will present a paper at the BlackHat or DefCon security conference that negates a built-in browser or operating system defense that developers had come to rely on.
You need to be prepared not just for the attacks that are going to come today, but for the new attacks that are going to come tomorrow. You can do this not by thinking like an attacker (which you’re not), but by learning to think like a defender (which you now are). This is why it’s so important to learn the general security principles behind the specific defenses.
It’s good to know how to appropriately encode HTML output to prevent cross-site scripting attacks, but it’s even better to know that mixing code and data can lead the application to interpret user input as command instructions. Knowing this—and developing your applications with an eye to avoiding this—can help you prevent not just cross-site scripting, but SQL injection, buffer overflows, request header forgery, and many others. And there’s a good chance it’ll help you prevent whatever new attacks get dropped at DefCon next year. The methods may change from year to year, but the underlying principles will always remain the same.
