Network Security versus Application Security: The Parable of the Wizard and the Magic Fruit Trees
In order to understand the difference between network security issues and application security issues a little better, consider this parable of the wizard and the magic fruit trees.
Once upon a time there lived a kindly old wizard who loved fruit. He used his magic spells to create a magnificent orchard full of all different kinds of fruit trees. He created apple trees, banana trees, and plum trees. He conjured up entirely new kinds of fruit trees that never existed in nature, fields of vineyards that grew cherries the size of cantaloupes, and shrubs that grew oranges with purple skin and tasted like watermelons.
As we said, this wizard was a kindly wizard, and he didn’t mind sharing his magical fruit with all the people of the village. He let them all come and go as they pleased through his groves, picking as much fruit as they wanted—after all, the trees were magic and grew new fruit the second the old fruit was picked. Life was good and everyone was happy, until one day the wizard caught a lovesick young farm boy carving his sweetheart’s initials into one of the lemonpear trees. He scolded the boy, sent him away, and turned the boy’s ears into big floppy donkey ears as a punishment (just for a few hours, of course).
The wizard thought that was that and started to get back to his scrolls, but then he saw another villager trying to dig up a tree so he could take it back to his house and plant it there. He rushed over to stop this thief but an even more horrific sight caught his eye first. Two apprentices of the evil wizard who lived across the valley had come with torches and were trying to burn down the whole orchard to exact revenge for their master’s embarrassing defeat at wizard chess earlier that month.
Now the wizard had had enough! He threw everyone out, and cast a spell that opened up a moat of boiling lava to surround the orchard. Now no one could get in to vandalize his beloved fruit trees, or to steal them, or try to burn them down. The trees were safe—but the wizard felt unhappy that now he wasn’t able to share his fruit with everyone. And the villagers did tend to spend a lot of gold pieces buying potions from him while they were there picking his fruit. To solve this problem, he came up with an ingenious new solution.
The wizard invited his friend the giant to come live in the orchard. Now whenever someone wanted a piece of fruit, he would just shout what he wanted to the giant. The giant would go pick the fruit for them, jump over the lava moat, and then hand them the fruit. This was a better deal for both the wizard and the villagers. The wizard knew that all the miscreants would be kept away from the trees, and the villagers didn’t even have to climb trees any more: the fruit came right to them.
Again, life was good and everyone was happy, until one day one very clever young man walked up to the edge of the lava where the giant was standing. Instead of asking the giant to bring him back a basket of persimmons or a fresh raisinmelon, he asked the giant to go up into the tower and fetch him the wizard’s scrolls. The giant thought this request was a little strange, but the wizard had just told him to get the people whatever they asked for. So he went to the tower and brought back the magic scrolls for the young man, who then ran off with all of the wizard’s precious secrets.
Real-World Parallels
If you were hoping for a happy end to this story, there isn’t one—not yet, at least. First, let’s take a look at the parallels between this story and the real-world security issues that organizations like yours face every day.
You (the wizard) have data (fruit) that you’d like to share with some people. But you know that if you just let everyone have free access to your server farm (orchard), there’ll be disastrous results. People will deface your servers (vandalize the trees), they’ll install botnets or other malware to take the servers over for themselves (steal the trees), and they’ll try to deny service to the servers so no one can use them (burn the trees down).
In response to these threats, you erect a firewall (lava moat) to keep everyone out. This is good because it keeps the attackers out, but unfortunately it keeps all your legitimate users out too, as you can see in Figure 1-2. So, you write a web application (a giant) that can pass through the firewall. The web application needs a lot of privileges on the server (the way a giant is very powerful and strong) so it can access the system’s database and the file system. However, while the web application is very powerful, it’s not necessarily very smart, and this is where web application vulnerabilities come in.
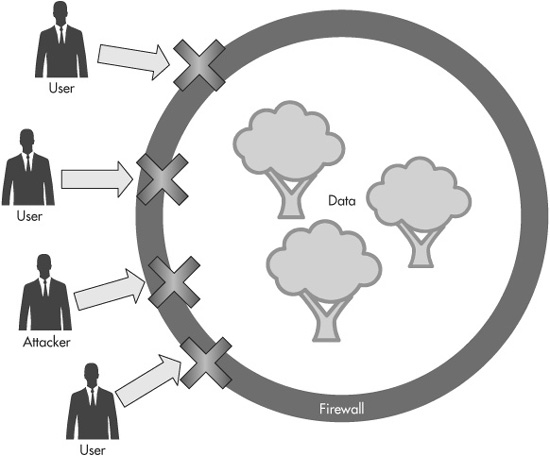
Figure 1-2 A firewall (lava moat) keeps attackers out, but keeps legitimate users out as well.
By exploiting logic flaws in the web application, an attacker can essentially “trick” the web application into performing attacks on his behalf (getting the giant to do his bidding). He may not be able to just connect into the servers directly to vandalize them or steal from them any more, but if he can get a highly privileged application to do it for him, then that’s just as good. He may even be able to read the application source code (the wizard’s scrolls) out of the file system.
The moral of the story is that it’s necessary to use network-level defenses like firewalls to keep attackers out, but network-level defenses alone are not sufficient. You also need to weed out all the logic flaws in your web applications so that they can’t be subverted.
