Misplaced Priorities and the Need for a New Focus
A recent survey of security executives from Fortune 1000 companies (http://www.fishnetsecurity.com/News-Release/Firewalls-Top-Purchase-Priority-In-2010-Survey-Says-) showed that the number one IT security spending priority was network firewalls. Given that, you’d guess that the number one way these companies are getting attacked is through open ports on their networks, wouldn’t you? In fact, if you did, you’d be dead wrong. The number one way Fortune 1000 companies and other organizations of all sizes get attacked is through their web applications.
How often do web applications get attacked? Security industry analysts suggest that as much as 70 percent of attacks come through web applications. And that 70 percent figure doesn’t just represent a large number of small nuisance attacks like the site defacements that were so common in the early days of the Web. Vulnerabilities in web applications have been responsible for some of the most damaging, high-profile breaches in recent news. Just a small sample of attacks in the first half of 2011 alone includes:
![]() The SQL injection attacks on the Sony Music web sites in May 2011 by the LulzSec organization. While unconfirmed by Sony, it’s also believed that SQL injection vulnerabilities were responsible for the attacks against the Sony PlayStation Network and Qriocity that leaked the private data of 77 million users and led Sony to shut down the services for over a month. The overall cost of this breach to Sony has been estimated to exceed 171 million dollars (US).
The SQL injection attacks on the Sony Music web sites in May 2011 by the LulzSec organization. While unconfirmed by Sony, it’s also believed that SQL injection vulnerabilities were responsible for the attacks against the Sony PlayStation Network and Qriocity that leaked the private data of 77 million users and led Sony to shut down the services for over a month. The overall cost of this breach to Sony has been estimated to exceed 171 million dollars (US).
![]() A cross-site scripting vulnerability in the Android Market discovered in March 2011 that allowed attackers to remotely install apps onto users’ Android devices without their knowledge or consent.
A cross-site scripting vulnerability in the Android Market discovered in March 2011 that allowed attackers to remotely install apps onto users’ Android devices without their knowledge or consent.
![]() The attack on information security firm HBGary Federal in February 2011 by the hacker group Anonymous. Another simple SQL injection vulnerability in the www.hbgaryfederal.com website, combined with a poorly implemented use of cryptographic hash functions, enabled Anonymous to extract the company officers’ usernames and passwords, which then enabled them to read the officers’ confidential internal e-mails. The CEO of HBGary Federal resigned from the company shortly thereafter, citing a need to “take care of his family and rebuild his reputation.”
The attack on information security firm HBGary Federal in February 2011 by the hacker group Anonymous. Another simple SQL injection vulnerability in the www.hbgaryfederal.com website, combined with a poorly implemented use of cryptographic hash functions, enabled Anonymous to extract the company officers’ usernames and passwords, which then enabled them to read the officers’ confidential internal e-mails. The CEO of HBGary Federal resigned from the company shortly thereafter, citing a need to “take care of his family and rebuild his reputation.”
None of these attacks were stopped by the sites’ firewalls! But IT budgets still focus primarily on firewall defenses. This is puzzling, since network firewalls are completely useless to prevent almost any web application attack. You can’t use firewalls to close off ports from which your web applications are being served, because then nobody could come to your web site. Organizations spend billions of dollars a year on advertising to get people to come to their sites; they’re certainly not going to close them up with firewalls. Figure 1-1 shows a diagram of an attacker evading a server’s firewall defenses by simply entering through the web site port 80.
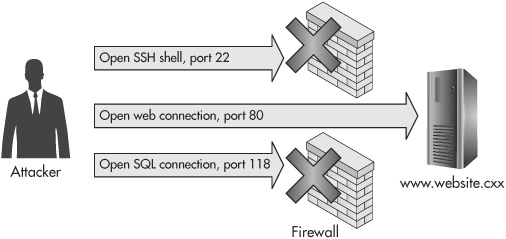
Figure 1-1 A server firewall preventing users (and attackers) from accessing most server ports but leaving port 80 open for web site traffic
We as an industry definitely have some misplaced priorities when it comes to security spending, but the magnitude of the imbalance is simply staggering. In another recent survey of IT professionals (http://www.barracudanetworks.com/ns/downloads/White_Papers/Barracuda_Web_App_Firewall_WP_Cenzic_Exec_Summary.pdf), almost 90 percent of companies reported that they spend less money on web application security than they spend on coffee: less than $1 per day per employee. We’re willing to spend billions of dollars a year to protect our networks, but when it comes to the targets that are really getting hit the hardest, we skimp and cut corners. To repeat an often-used analogy, this is like installing burglar alarms and steel bars on all of the windows in your home, but leaving the front door wide open.
Since the same survey showed that almost 70 percent of organizations rely on network firewalls for their web application defense—which is essentially the same as having no defense at all—it’s hard to see this as anything besides an issue of being appropriately educated on web application security. People know their web applications are important, but they don’t know how to secure them.
That’s where this book comes in.
