The IEEE and Networking Standards
Specify the main features of the 802.2 (LLC), 802.3 (Ethernet), 802.5 (Token Ring), 802.11b (wireless), and FDDI networking technologies, including the following:
Speed
Access method
Topology
Media
Whereas a topology defines the structure of a network, network standards define how it works. As early as the 1970s, it was apparent that networks were going to play a large role in future corporate environments. Many manufacturers saw the computing and network trend and became increasingly active in network component development. These companies realized that in order for their products to work together, standards would be necessary to ensure compatibility. The task of producing the standards fell to an international body called the IEEE.
The IEEE developed a set of standards called the 802 project. These standards are still used today, although there have been many changes and additions along the way. By using the standards defined by the IEEE, manufacturers can be sure that their products will work with products from other companies that adhere to the standards.
Some of the IEEE 802 standards define only certain technologies, whereas others, such as the 802.3 standard, define entire networking systems. The following are some of the most important IEEE 802 standards:
802.1, internetworking— Defines internetwork communications standards between devices and includes specifications for routing and bridging.
802.2, the LLC sublayer— Defines specifications for the Logical Link Control (LLC) sublayer in the 802 standard series.
802.3, CSMA/CD— Defines the carrier-sense multiple-access with collision detection (CSMA/CD) media access method used in Ethernet networks. This is the most popular networking standard used today.
802.4, a token passing bus (rarely used)— Defines the use of a token-passing system on a linear bus topology.
802.6, metropolitan area network (MAN)— Defines a data transmission method called distributed queue dual bus (DQDB), which is designed to carry voice and data on a single link.
802.7, Broadband Technical Advisory Group— Defines the standards and specifications of broadband communications methods.
802.8, Fiber-Optic Technical Advisory Group— Provides assistance to other IEEE 802 committees on subjects related to the use of fiber-optics.
802.9, Integrated Voice and Data Networks Group— Works on the advancement of integrated voice and data networks.
802.10, network security— Defines security standards that make it possible to safely and securely transmit and exchange data.
802.11, wireless networks— Defines standards for wireless LAN communication.
802.12, 100BaseVG-AnyLAN— Defines standards for high-speed LAN technologies.
For the Network+ exam and day-to-day real-life networking, some of these standards are more important than others. The Network+ exam focuses on the LAN standards: 802.2, 802.3, 802.5, and 802.11. These IEEE standards specify the characteristics of the networking systems, including the cable types used, access methods, speeds, and topologies. Although you don't need detailed knowledge of all these IEEE standards in real-world applications, a general understanding of these standards will be an asset.
Characteristics Specified in the IEEE 802 Standards
Let's review some of the characteristics that are specified within each standard: speed, access methods, topology, and media.
Speed
Many factors contribute to the speed of a network. The standard defines the maximum speed of a networking system. The speed normally is measured in megabits per second (Mbps), although some faster network systems use gigabits per second (that is, Gbps, where 1Gbps is equivalent to 1000Mbps).
A maximum speed of 1Gbps might seem very fast, but in standard computing terms, it is quite slow. Roughly translated, 1Gbps is 1MBps. That means it would take 10 seconds to transfer a 10MB file across a link, assuming (which you can't do) that you could access 100% of the bandwidth. Even the slowest Small Computer Systems Interface (SCSI) standard is 5 times faster than this; the newest standard, Ultra320, is (as you might have guessed) 320 times faster. As you can see, although a 1Gbps network connection might be fast in networking terms, it is still considered the weakest link in the data communications path between two devices.
Some networks are faster than others. For example, a Token Ring (802.5) network has a maximum speed of 16Mbps. Many Ethernet networks (802.3x) now operate at 100Mbps. As you will see later in this chapter, when we discuss networking components, it is possible to further increase these figures. However, the maximum speed attainable on a network can be affected by many factors. Networks that achieve 100% of their potential bandwidth are few and far between.
NOTE
Bandwidth The term bandwidth describes the amount of data that can travel over a network connection in a given time period. Generally speaking, WAN network links have a lower bandwidth than LAN connections.
Access Methods
Access methods govern the way in which systems access the network media and send data. Access methods are necessary to ensure that systems on the network can communicate with each other. Without an access method, it would be possible for two systems to communicate at the exclusion of every other system. Access methods ensure that everyone gets an opportunity to use the network.
Several access methods are used in networks; the most popular are CSMA/CD and token passing. Other methods, such as demand priority and contention, are also used. We'll look at each of these access methods separately.
CSMA/CD
CSMA/CD, which is defined in the IEEE 802.3 standard, is the most popular media access method because it is associated with Ethernet networking, which is by far the most popular networking system.
On a network that uses CSMA/CD, when a system wants to send data to another system, it first checks to see if the network media is free. It must do this because each piece of network media used in a LAN can carry only one signal at a time. If the sending node detects that the media is free, it transmits, and the data is sent to the destination. It seems simple.
Now, if it always worked like this, you wouldn't need the CD part of CSMA/CD. Unfortunately, in networking, as in life, things do not always go as a planned. The problem arises when two systems attempt to transmit at exactly the same time. It might seem like a long shot that two systems will pick the same moment to send data, but we are dealing with communications that occur many times in a single second—and most networks have more than two machines.
NOTE
Nodes A node is any device that is connected to the network. A node might be a client computer, server computer, printer, router, or gateway.
Imagine that 200 people are in a room. The room is silent, but then two people decide to say something at exactly the same time. Before they start to speak, they check (listen) to see if someone else is speaking; because no one else is speaking, they begin to talk. The result is two people speaking at the same time, which is similar to a network collision.
NOTE
Contention CSMA/CD is known as a contention media access method because systems contend for access to the media.
Collision detection works by detecting fragments of the transmission on the network media that result when two systems try to talk at the same time. The two systems wait for a randomly calculated amount of time before attempting to transmit again. This amount of time—a matter of milliseconds—is known as the backoff.
When the backoff period has elapsed, the system attempts to transmit again. If the system doesn't succeed on the second attempt, it keeps retrying until it gives up and reports an error.
The upside of CSMA/CD is that it has relatively low overhead, meaning that not much is involved in the workings of the system. The downside is that as more systems are added to the network, more collisions occur and the network becomes slower. The performance of a network that uses CSMA/CD degrades exponentially as more systems are added. Its low overhead means that CSMA/CD systems theoretically can achieve greater speeds than high-overhead systems, such as token passing. However, because collisions take place, the chances of all that speed translating into usable bandwidth are relatively low.
NOTE
A Variation on a Theme A variation of CSMA/CD (or the other way around, depending on your point of view) is carrier-sense multiple-access with collision avoidance (CSMA/CA). Computer systems that use CSMA/CA send a special signal to notify other computers on the network that they are going to send data. This way, data is sent only when the media is clear, thereby avoiding collisions. Although this system may seem safer than CSMA/CD, it's also slower, due to the overhead associated with systems broadcasting their intent to transmit.
Despite its problems, CSMA/CD is a very efficient system. As a result, rather than replace it with some other technology, workarounds have been created that reduce the likelihood of collisions. One such strategy is the use of network switches that create multiple collision domains and therefore reduce the impact of collisions on performance. Chapter 3 provides more information about using switches.
Table 1.6 summarizes the advantages and disadvantages of the CSMA/CD access method.
Token Passing
Although token passing, which is specified in IEEE 802.5, is the second most popular media access method, the domination of Ethernet networking makes it second by a considerable margin. However, it might not be popular, but it is clever.
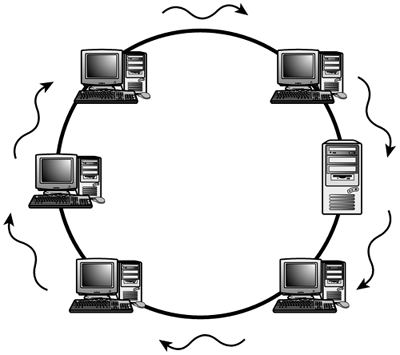
On a token-passing network, a special packet called a token is passed among the systems on the network. The network has only one token, and a system can send data only when it has possession of the token.
When the data arrives, the receiving computer sends a verification message to the sending computer. The sender then creates a new token, and the process begins again. Standards dictate how long a system can have control over the token. Figure 1.12 shows how data is sent on a token-passing network.
One of the big advantages of the token-passing access method is the lack of collisions. Because a system can transmit only when it has the token, there is no contention. Even under heavy load conditions, the speed of a token-passing system does not degrade in the same way as a contention-based method such as CSMA/CD. In a practical scenario, this fact makes token passing more suitable than other access methods for applications such as videoconferencing.
However, token passing does have drawbacks. The creation and passing of the token generate overhead on the network, which reduces the maximum speed. In addition, the software and hardware requirements of token-passing network technologies are more complex—and therefore more costly—than those of other media access methods.
EXAM TIP
RI and RO Ports on MSAU Be sure you understand the function and purpose of the RI and RO ports on an MSAU for the Network+ exam. Also make sure you understand how the cables should be connected between MSAUs and the consequences of not connecting them correctly (that is, most likely none of the systems on the ring will be able to communicate).
You might have difficulty grasping the difference between the physical and the logical topologies of ring networks. For example, a common implementation of the token-passing method is Token Ring. A Token Ring network operates and passes data around the network in a logical ring, as shown in Figure 1.12. The physical layout of a ring network is altogether different from this. Ring networks are most commonly wired in a star configuration. In a Token Ring network, a multistation access unit (MSAU) is equivalent to a hub or switch on an Ethernet network. The MSAU performs the token circulation internally. To create the complete ring, the Ring In (RI) port on each MSAU is connected to the Ring Out (RO) port on another MSAU. The last MSAU in the ring is then connected to the first, to complete the ring. Figure 1.13 shows how this works.
NOTE
MSAU Versus MAU MSAU is sometimes, incorrectly, shortened to MAU. A media access unit (MAU) is a device used in Ethernet networks to provide a connection between certain types of network interfaces and the network media.
Table 1.7 summarizes the advantages and disadvantages of the token-passing access method.
Demand Priority
Demand priority was developed for use on an Ethernet standard known as 100VG-AnyLAN.
On a demand priority network, a special hub queries each computer connected to it, trying to find one that has data to send. When a computer is found that has information to send, the hub opens a connection for that computer, and no other computer is allowed to transmit. This eliminates the possibility of collisions and therefore provides for very high access speeds and controlled media access.
NOTE
100VG-AnyLAN Even though 100VG-AnyLAN is based on an Ethernet standard, it is defined in its own IEEE standard (802.12) because it uses demand priority as an access method instead of CSMA/CD.
Demand priority lets the administrator assign a priority to requests for media access. If there is contention for media access, the link with the highest priority wins, making the demand priority system good for time-sensitive applications.
Networks that use demand priority require specialized network devices to manage access. Thus demand priority implementations are more expensive than alternatives such as CSMA/CD. The polling process and evaluation of priorities also add to the network traffic and so create more overhead than is experienced with other networking systems.
Table 1.8 summarizes the advantages and disadvantages of the demand priority access method.
Topology
As discussed earlier in this chapter, topologies dictate both the physical and logical layouts of the network. Remember that topologies include bus, star, ring, mesh, and wireless. Each of the IEEE LAN standards can be implemented by using the topology specified within the standard. Some standards, such as 802.3 (Ethernet), have multiple physical topologies, but always use the same logical topology. Token Ring has two possible physical topologies and a single logical topology. We'll talk more about the different topologies in the sections about their respective standards, which is discussed in the next section.
Media
Each IEEE specification defines what media are available to transport the signal around the network. The term media, which is the plural of medium, generically describes the methods by which data is transported from one point to another. Common network media types include twisted-pair cable, coaxial cable, and fiber-optic cable. Wireless media include infrared, microwave, and radio waves. Chapter 2 provides a detailed discussion of media types.
The IEEE 802 Standards
Now that we have looked at some of the characteristics defined by the IEEE standards, let's examine the standards themselves. Be sure you are completely familiar with the information provided in each of the following sections before you take the Network+ exam.
802.2. The LLC Sublayer
The IEEE 802.2 standard, often referred to as LLC sublayer, is different from the other IEEE 802 networking standards because it does not define a complete networking model. Instead, it defines the standards for controlling the data received and sent by a system. Specifically, it specifies protocols and technologies that perform data flow control and error-checking functions. These control functions form the foundation for the other IEEE 802 networking standards. You can think of 802.2 as an enabler for the other standards. More information on the function of the 802.2 standard can be found in Chapter 4, “The OSI Model,” which discusses the Open System Interconnect (OSI) model.
802.3. Ethernet
The Ethernet standard, IEEE 802.3, is by far the most common networking standard in use today, due in part to its flexibility and ease of implementation. Similar to the other IEEE standards, the 802.3 standard specifies the key characteristics of the network model. In addition to the original standard, a number of other standards are based on 802.3. These standards are assigned a designator, such as 802.3u for Fast Ethernet. Collectively, they are often referred to as the 802.3x standards.
Different implementations of Ethernet accommodate different physical topologies. For example, the 802.3 standard accommodates physical bus and physical star configurations. Other Ethernet standards support only the physical star topology. The logical topology for Ethernet is the linear bus, regardless of the physical topology used.
Table 1.9 provides a summary of the original Ethernet (802.3) standard.
EXAM TIP
Ehternet Ethernet is far and away the most popular LAN networking system, and its coverage in the Network+ objectives is much more detailed than the coverage of the other networking systems. The information presented here is intended as a means for comparison with the other networking standards rather than a full tutorial on the subject. That is left to Chapter 2.
802.3u. Fast Ethernet
In networking, speed is everything. At 10Mbps, the original Ethernet standard is too slow for modern implementations. An improved version of the standard, known as 100BaseT, or Fast Ethernet, transmits data at 100Mbps and higher. Fast Ethernet, which is defined in IEEE 802.3u, is available only over twisted-pair and fiber-optic cable.
Table 1.10 summarizes the characteristics of Fast Ethernet (100BaseT).
802.3z. Gigabit Ethernet
Gigabit Ethernet (1000BaseX) is another extension of the 802.3 Ethernet standard. Gigabit Ethernet, which is defined in IEEE 802.3z, can transmit data at 1Gbps (that is 1000Mbps) and can be used with Ethernet and Fast Ethernet devices. Gigabit Ethernet has the same characteristics as the original standard and is backward compatible with older Ethernet technologies such as 10BaseT and 100BaseT. Table 1.11 summarizes the characteristics of Gigabit Ethernet.
NOTE
100VG-AnyLAN As mentioned earlier in this chapter, the 100VG-AnyLAN standard is based on the Ethernet standard but uses the demand priority access method instead of CSMA/CD. The 100VG-AnyLAN standard defines a physical star networking system over twisted-pair or fiber-optic cable at 100Mbps. 100VG-AnyLAN is defined by the IEEE 802.12 standard.
| Characteristic | Description |
|---|---|
| Specification | IEEE 802.3z |
| Topology | Star |
| Access method | CSMA/CD |
| Media | Twisted-pair cable, fiber-optic cable |
| Speed | 1Gbps |
802.5. Token Ring
Token Ring was introduced by IBM in the mid-1980s and quickly became the network topology of choice—that is, until the rise in popularity of Ethernet. Token Ring is defined for physical and logical ring topologies as well as the physical star topology. Token Ring is defined in the 802.5 specification. Table 1.12 summarizes the characteristics of the Token Ring standard.
NOTE
Ethernet Versus Token Ring Some people compare Token Ring and Ethernet to Betamax and VHS. Although this comparison may be a little too harsh, it's not far from the truth. Some sources put the ratio of Ethernet networks to Token Ring networks as high as 99 to 1.
| Characteristic | Description |
|---|---|
| Specification | IEEE 802.5 |
| Topology | Physical star, physical ring logical ring[*] |
| Access method | Token passing |
| Media | Twisted-pair cable[*] |
| Speed | 4Mbps or 16Mbps |
[*] The 802.5 standard does not mandate these characteristics, but Token Ring networks are most commonly implemented using these specifications.
EXAM TIP
Token Ring This is the one and only section of the Network+ objectives that mentions Token Ring. Concentrate on the basic information provided here, and you should be able to tackle any Token Ring–related questions on the exam.
As you can see from Table 1.12, Token Ring networks can operate at 4Mbps or 16Mbps. The key word here is or. All devices on the ring must operate at the same speed. Placing a system on the network without configuring the speed correctly will make it unable to participate on the ring. The maximum length of the ring depends on the cable type being used.
Although Token Ring is a very good networking system, the simplicity of Ethernet networking and the low cost of Ethernet equipment has all but eliminated Token Ring from the networking market. Some organizations still use it, mainly for historical reasons, but you are unlikely to see new Token Ring implementations.
802.11b. Wireless
Today we have untethered high-speed networking at our fingertips. The IEEE 802.11b standard defines wireless Ethernet networking for use in LANs.
The 802.11b standard can be implemented many different ways, but the most common is to have special devices called wireless access points that allow multiple wireless devices to communicate with each other. In addition, these wireless access points can be connected to wired networks to create wireless portions of entire networks. Wireless access points can cover distances up to several hundred feet, but the actual range depends on the location of the receiver and the local conditions.
Wireless network access now makes it possible to provide network access in any environment, from a coffee shop to an airport and everywhere in between.
The 802.11b standard provides for a maximum transmission speed of 11Mbps. However, devices are designed to be backward compatible with previous standards that provided for speeds of 1-, 2-, and 5.5Mbps. Table 1.14 defines the characteristics of the 802.11b standard.
NOTE
War Driving The advent of wireless networking has led to a new phenomenon: war driving. Armed with a Global Positioning System (GPS) receiver and a laptop with an 802.11b wireless NIC, hackers drive around metropolitan areas seeking out wireless networks. Once they find one, the hackers attempt to gain access to the network just as if they were connected to the network through a physical link. Such practices are illegal, although little can be done to prevent them other than using the built-in security features of 802.11b. The problem is, not many installations use these features. If you are responsible for a network that has a wireless element, be sure to implement all the security features available. Not doing so is tantamount to letting a hacker into your building and letting him use one of your PCs to access the server.
| Characteristic | Description |
|---|---|
| Specification | 802.11b |
| Topology | Wireless |
| Access method | CSMA/CA |
| Media | 2.4GHz radio waves |
| Speed | 11Mbps |
EXAM TIP
WiFi Standards aside, there are no guarantees that one manufacturer's wireless products will work with another's. For that reason, the Wireless Ethernet Compatibility Alliance has a Wireless Fidelity (WiFi) certification program that guarantees compatibility between products. When you're specifying or buying wireless networking equipment, look for WiFi approval.
Although the popularity of 802.11b is still relatively low, it is sure to become a major feature of the networking landscape in coming years. As speeds rise and the cost of wireless networking equipment falls, wireless is likely to become the networking method of choice, particularly because new standards that provide for much faster transmissions are being developed at a rapid rate.
NOTE
CDDI It is possible to use the FDDI protocols over copper wire; this is called CDDI. Like FDDI, CDDI uses a dual-ring configuration and has transfer rates of 100Mbps.
FDDI
FDDI was developed by the American National Standards Institute (ANSI) in the mid-1980s, to meet the growing need for reliable, fast network transmissions to accommodate distributed applications. In particular, FDDI was intended for use in specific applications such as backbones.
FDDI is a 100Mbps token-passing network standard. FDDI uses fiber-optic cable as its main transmission media, but it can also work over copper wire (in which case it is called Copper Distributed Data Interface [CDDI]).
Although FDDI is a ring topology, it does not suffer from the fault-tolerance issues inherent in the IEEE 802.5 standard. To avoid a single break in the ring that could disrupt network connectivity, FDDI uses a dual-ring configuration. If one computer or cable is damaged, the other ring will form a single ring topology, and the data signals can continue to travel around the network. Devices that must remain available in the event of a media failure can be attached to both rings. Less important systems can be connected to just the primary ring. Figure 1.14 shows the dual-ring configuration of FDDI.
In many ways, FDDI is similar to Token Ring. It uses a logical ring and a physical star topology, and it uses token passing as a media access method. However, FDDI has much faster data transmission rates than Token Ring, so is better suited to today's high-bandwidth applications. Table 1.15 summarizes the characteristics of FDDI.
| Characteristic | Description |
|---|---|
| Specification | ANSI X3T9.5 |
| Topology | Dual ring |
| Access method | Token passing |
| Media | Fiber-optic (Shielded Twisted Pair [STP] or Unshielded Twisted Pair [UTP] is CDDI) |
| Speed | 100Mbps |
For more information on FDDI, see Chapter 7, “WAN Technologies.”