Chapter 7: Protecting Yourself with Windows Firewall
IN THIS CHAPTER
Understanding how firewalls protect your computer
Using Security Center
Using Windows Firewall
Configuring Windows Firewall
If you use the Internet, a firewall is a must-have security tool. It's not the only tool you need, but it's an important one. It protects your computer from hackers and worms. Hackers are people who would attempt to access your computer through the Internet without your knowing it. Worms are programs, such as viruses, that are usually written to do intentional harm.
Windows 8.1 comes with its own built-in firewall. If you didn't know about it before going online, relax. It's enabled by default. So, most likely, it's been protecting you since the very first moment you went online. (Plus, your Internet service provider protects you from most invasions.) In this chapter, you learn how the firewall works and how to configure it for maximum protection.
How Firewalls Work
To understand what a firewall is, you need to first understand what a network connection is. Even though you have only one skinny set of wires connecting your computer to the Internet (through a DSL phone line or cable outlet), that connection actually consists of 65,535 ports. Each port can simultaneously carry on its own conversation with the outside world. So, theoretically, you could have 65,535 things going on at a time. Of course, nobody ever has that much going on all at one time. A handful of ports is more like it.
The ports are divided into two categories:
- TCP (Transmission Control Protocol): This is generally used to send text and pictures (web pages and e-mail), and includes some error checking to make sure all the information that's received by a computer matches what the sending computer sent.
- UDP (User Datagram Protocol): This works more like broadcast TV or radio, where the information is just sent out and there is no error checking. UDP is generally used for real-time communications, such as voice conversations and radio broadcasts sent over the Internet.
Each port has two directions: incoming (or ingress) and outgoing (or egress). The direction is in relation to stuff coming into your computer from the outside — namely, the Internet. It's the stuff coming into your computer that you have to watch out for. But you can't close all ports to all incoming traffic. If you did, there'd be no way to get the good stuff in. But you don't want to let everything in, either. You need a way to separate the wheat from the chaff, so to speak.
Anti-spyware and antivirus software are good tools for keeping out viruses and other bad things that are attached to files coming into your computer. But hackers can actually sneak worms and other bad things in through unprotected ports without involving a file in the process. That's where the firewall comes into play. A stateful firewall, such as the one that comes with Windows 8.1, keeps track of everything you request. When traffic from the Internet wants to come in through a port, the firewall checks to make sure the traffic is something you requested. If it isn't, the firewall assumes this is a hacker trying to sneak something in without your knowing it and, therefore, prevents the traffic from entering your computer. Figure 7.1 illustrates how it works.
Figure 7.1
A stateful firewall.
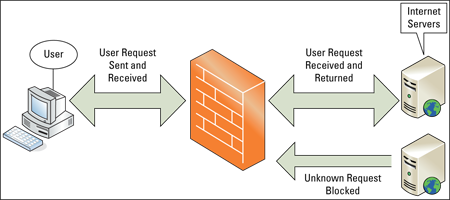
So, there's really more to it than just having a port open or closed. It's also about filtering — making sure that data coming into an open port is something you requested and not some rogue, uninvited traffic sent by some hacker. Many of the worms that infected so many computers in the 1990s did so by sneaking in undetected through unfiltered ports. These days, you really want to make sure you have a firewall up whenever you go online to prevent such things.
Introducing Action Center
Before you explore Windows Firewall, take a look at the Action Center. This is a single point of notification for most of your PC's security. You can open the Action Center in several ways. Use whichever is most convenient for you:
- From the Windows Start screen, show the Charms Bar and click Search Control Panel. Click Control Panel, click System and Security, and then click Action Center.
- On the desktop, right-click the flag icon in the notification area and choose Open Action Center.
- On the desktop, press Windows+X, choose Control Panel, click System and Security, and then click Action Center.
Whichever method you use, the Action Center opens. Figure 7.2 shows an example. We clicked the arrow button to the right of each heading so that you can see the descriptive text under each heading. You can click that button to show or hide the same descriptive text.
Figure 7.2
Action Center.
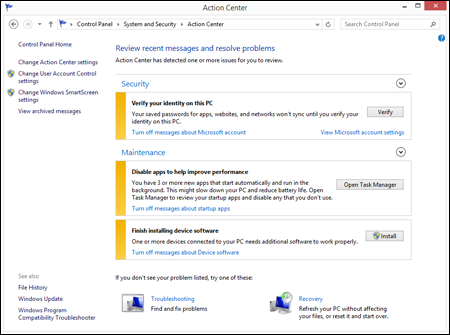
How you know Windows Firewall is on
By default, Windows Firewall is turned on and working at all times, so your Action Center should show “On” beside the Firewall item, as in Figure 7.2 (and you see only the Network Firewall item in Action Center if you click the arrow beside the Security heading). If your version of Figure 7.2 shows Off or Not Monitored, you may have a third-party firewall program running in place of Windows Firewall. Many such programs are available, such as McAfee, Symantec, and Check Point. If your firewall is turned off and you don't know why, it would be good to find out the reason — perhaps from your computer manufacturer or a support person who worked on your computer. If you don't have any firewall up, you should definitely turn on Windows Firewall.
Turning Windows Firewall on or off
To turn Windows Firewall on or off, you must have administrative privileges. In the System and Security Control Panel window, click Windows Firewall. You should see the current firewall status in the right pane, and options for controlling the firewall in the left pane. Click Change Notification Settings or Turn Windows Firewall On or Off in the left pane to see the options shown in the foreground of Figure 7.3.
If you have a third-party firewall that you feel is more secure than the Windows Firewall, you can choose the Off option to turn off Windows Firewall. Just make sure you have a firewall up when you go online. Otherwise, you won't have anything to stop uninvited traffic on your network connection after the traffic gets by your Internet service provider.
Figure 7.3
Settings for Windows Firewall.

Making Exceptions to Firewall Protection
When Windows Firewall is turned on and running, you don't really have to do anything special to use it. It will be on constant vigil, automatically protecting your computer from hackers and worms trying to sneak in through unprotected ports. Ports for common Internet tasks such as e-mail and the web will be open and monitored so that you can easily use those programs safely.
Internet programs that don't use standard e-mail and web ports may require that you create an exception to the default firewall rules for incoming traffic. Examples include instant messaging programs and some online games. When you try to use such a program, Windows Firewall displays a security alert like the one in Figure 7.4.
Figure 7.4
Windows Firewall security alert.
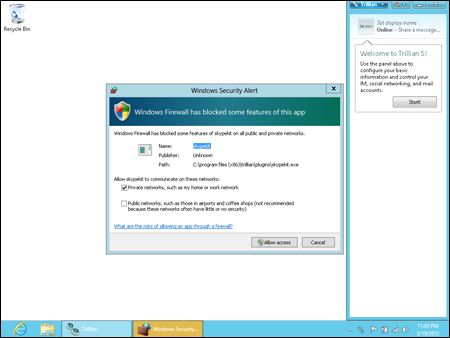
The message doesn't mean that the program is “bad.” It just means that to use the program, the Firewall has to open a port. If you don't recognize the program name and publisher shown, click Cancel. If you want to use the program, first decide for which networks the exception will be allowed. For example, if the traffic is coming from another computer on your local network, select the Private Networks option. For traffic coming from the Internet, select Public Networks (you can select either or both, as needed). Then, click Allow Access. Allowing access for a program doesn't leave the associated port wide open. It just creates a new rule that allows that one program to use the port. You're still protected because the port is closed when you're not using that specific program. The port is also closed to programs other than the one for which you unblocked the port. If you change your mind in the future, you can always reblock the port, as described in the next section.
Manually configuring firewall exceptions (allowed apps and programs)
Normally, when you try to use a program (or an app) that needs to work through the firewall, you get a message like the example shown in Figure 9.4. Occasionally, you might need, or want, to manually allow or block a program through the firewall. If you have administrative privileges, you can do that via the Allowed Apps page shown in Figure 7.5. To open that page, click Allow an App through Windows Firewall in System and Security (by the Windows Firewall item in the Control Panel).
Figure 7.5
Windows Firewall Allowed Apps and Features.

Items on the list with a check mark beside them represent apps that work through the firewall. You'll also see any exceptions you created in response to a security alert.
You probably aren't familiar with most of the apps and programs listed in the Allowed Apps and Features list, so you should not select or deselect a box just by guessing. But you don't need to guess, either. If you just leave things as they are, everything will be fine. If you later decide to use one of the listed features, you'll be prompted at that point to allow access for the app or program if it's necessary to do so.
Adding an app exception
You can unblock ports for apps and programs that aren't listed under Allowed Apps and Features. You would do this only if specifically instructed to do so by an app or program manufacturer you know and trust.
If the app or program for which you want to create an exception isn't listed under Allowed Apps and Features, you can do the following:
- Click Change Settings and then click the Allow Another App button. When you do so, you see a list of installed programs that might require Internet access, as shown in Figure 7.6.
Figure 7.6
Add an App dialog box.
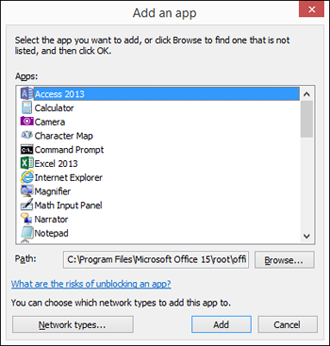
- Click the app or program that you want to add to the list. Optionally, if the program isn't listed, but you know where it's installed, you can use the Browse button to get to the main executable for that program (typically the
.exefile). - Clicking the Network Location Types button lets you define the addresses from which any unsolicited traffic is expected to originate. For example, if you're using a program that provides communications among programs within your local network only, you wouldn't want to accept unsolicited traffic coming to that port from the Internet. You'd want to accept unsolicited traffic coming only from computers within your own network. When you click Network Types, you see the options shown in Figure 7.7. Your options are as follows:
- Private: For home or workplace networks. If the program in question has nothing to do with the Internet, and is for your home or business network only, choose this option to block Internet access, but allow programs within your own network to communicate with each other through the program.
- Public: For public networks, such as those in an airport or coffee shop. If you want the program to be able to connect to the Internet, choose this option.
- Click OK to save your settings.
Figure 7.7
The Choose Network Types dialog box.

Disabling, changing, and deleting exceptions
The check boxes in the Allowed Apps and Features list indicate whether the exception is enabled or disabled. When you clear a check box, the exception is disabled, and traffic for that program is rejected. This makes it relatively easy to enable and disable a rule for a program on an as-needed basis because the program name always remains in the list of exceptions.
To change the scope of an exception in your exceptions list, click the check box in the Private or Public column, as needed. To remove a program from the exceptions list, and stop accepting unsolicited traffic through its port, click the program name and then click the Remove button.
Advanced Firewall Configuration
The rest of this chapter goes well beyond anything that would concern the average home computer user. It's for more advanced users and network and security administrators who might need to configure Windows Firewall to comply with an organization's security policy. All these options require administrative privileges. We don't go into great detail on what the various options mean because we assume you're working to comply with an existing policy.
Open Windows Firewall with Advanced Security
To get to the advanced configuration options for Windows Firewall, first open Windows Firewall from the System and Security item in the Control Panel. Then click the Advanced Settings link in the left pane. The firewall console, shown in Figure 7.8, opens.
As you can see in the figure, you have three independently configurable profiles to work with:
- Domain Profile: This is active when the computer is logged in to a network domain, such as in a corporation or business setting.
- Private Profile: This applies to computers within a local, private network.
- Public Profile: This protects your computer from the public Internet.
Figure 7.8
The Windows Firewall with Advanced Security console.

Changing firewall profile properties
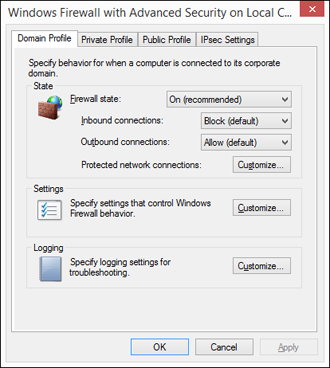
Clicking the Windows Firewall Properties link near the bottom of the console (or the Properties item in the Actions pane) takes you to the dialog box shown in Figure 7.9. Notice that you can use tabs at the top of the dialog box to configure the Domain, Private, and Public settings. The fourth option applies to IPsec (IP Security), commonly used with virtual private networks (VPNs), which are described a little later in this section. By default, Inbound Connections are set to Block and Outbound Connections are set to Allow. You can change either setting by clicking the appropriate button.
Firewall alerts, unicast responses, local administrator control
Each profile tab has a Customize button in its Settings section. Clicking that button provides an option to turn off firewall notifications for that profile. Administrators can also use options on that tab to allow or prevent unicast responses to multicast and broadcast traffic. There's also an option to merge local administrator rules with rules defined through group policy.
Figure 7.9
Windows Firewall advanced properties.
Security logging
Each profile tab also offers a Logging section with a Customize button. Click the Customize button to set a name and location for the log file and a maximum size, and to choose whether you want to log dropped packets, successful connections, or both. You can use that log file to review firewall activity and to troubleshoot connection problems caused by the firewall configuration.
Customizing IPsec settings
The IPsec Settings tab in the firewall properties provides a way to configure IPsec (IP Security). Clicking the Customize button under IPsec Defaults reveals the options shown in Figure 7.10. The Default settings in each case cause settings to be inherited from a higher-level group policy object (GPO). To override the GPO, choose whichever options you want to apply to the current Windows Firewall instance. When you override the default, you can choose key exchange and data integrity algorithms. You can also fine-tune Kerberos V5 authentication through those settings.
Figure 7.10
The Customize IPsec Defaults dialog box.
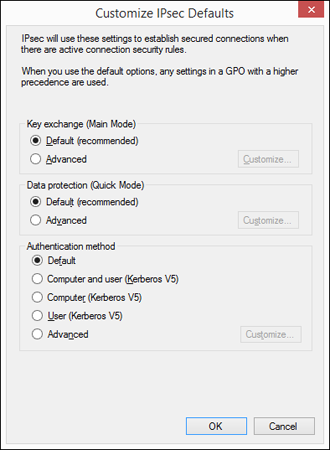
Clicking OK or Cancel in the Customize IPsec Defaults dialog box takes you back to the IPsec Settings tab. There you can use the IPsec Exemptions section to exempt ICMP from IPsec, which may help with connection problems caused by ICMP rules.
That covers the main firewall properties. You can configure plenty more outside the Properties dialog box. Again, most of these go far beyond anything the average home user needs to be concerned with, so we're being brief here. Advanced users needing more information can find plenty of information in the Help section for the firewall.
Inbound and outbound rules
In the left column of the main Windows Firewall with Advanced Security window shown back in Figure 7.8, you see Inbound Rules and Outbound Rules links. These provide very granular control over Windows Firewall rules for incoming and outgoing connections. Figure 7.11 shows a small portion of the possibilities there. Use the scrollbars to see them all.
Figure 7.11
Advanced outbound exceptions control.
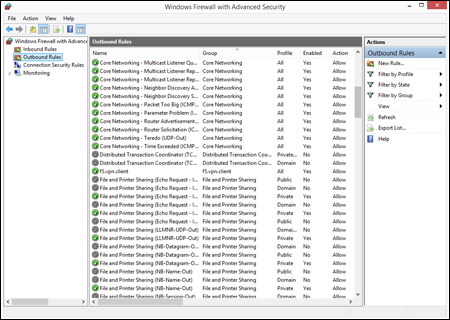
Here we're getting into security matters that go beyond the scope of this book. But we think it will be easy for any professional administrator to figure out what's going on there. Options (and the Help link) in the Actions column on the right tell all. You can also change any exception in the center column by right-clicking and choosing Properties.
Wrap-Up
A firewall is an important component of a larger overall security strategy. Windows 8.1 comes with a built-in firewall that's turned on and working from the moment you first start your computer. The firewall is automatically configured to prevent unsolicited Internet traffic from getting into your computer, thereby protecting you from worms and other hacking attempts. The Windows 8.1 firewall also provides advanced options for professional network and security administrators who need more granular control over its behavior. In summary:
- A firewall protects your computer from unsolicited network traffic, which is a major cause of worms and other hack attempts.
- A firewall will not protect your computer from viruses, pop-up ads, or junk e-mail.
- You don't need to configure the firewall to use standard Internet services such as the web and e-mail. Those will work through the firewall automatically.
- When you start an Internet program that needs access to the Internet through a closed port, you'll be given a security alert with options to Unblock, or Keep Blocking, the port. You must choose Unblock to use that program.
- Windows Firewall is one of the programs in the Security Center. To open Security Center, press Windows+X and choose Control Panel⇒Security⇒Security Center.
- To get to Windows Firewall configuration options, from the Windows Start screen, open the Charms Bar and choose Search. On the Search page, click Control Panel⇒Security⇒Security Center.
- Exceptions in Windows Firewall are programs that are allowed to work through the firewall.
- Professional network and security administrators can configure Windows Firewall through the Windows Firewall with Advanced Security console in Administrative Tools.
