IN THIS CHAPTER
Welcome to the newest version of Systems Management Server—System Center Configuration Manager (ConfigMgr) 2007. Chapter 1, “Configuration Management Basics,” discussed the hurdles in systems management and configuration management. This chapter looks at the history of Configuration Manager and discusses terminology, key concepts, changes through Configuration Manager 2007 R2 and Service Pack 2, and feature dependencies Configuration Manager has on other technologies.
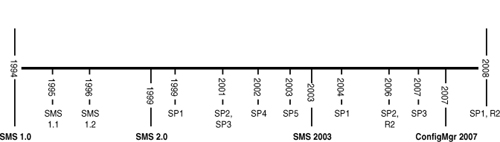
There have been four major versions of the product, beginning with Systems Management Server (SMS) 1.0, launched by Microsoft in 1994. Since then, Microsoft has released versions 1.1, 1.2, 2.0, 2003 and now version 2007, which the company rebranded as System Center Configuration Manager 2007. Figure 2.1 displays a timeline showing the various versions of SMS and Configuration Manager.
Microsoft introduced the first version of its desktop management software, Systems Management Server 1.0 (code-named Hermes), in January 1994. SMS 1.1 came out in mid 1995, and SMS 1.2, discussed in the next section, followed in 1996.
Note
SMS 1.1 and 1.2 were initially intended as service packs to the base release of SMS 1.0, but became feature-heavy enough to call real releases. The fact that each year Microsoft had a new version of SMS points to the fact that the 1.x product needed some serious work, hence, the annual updates.
Microsoft touted SMS 1.2 as a systems management solution that provided an array of tools—from remote control to software distribution—helping local area network (LAN) administrators to monitor and manage their networks. In reality, SMS 1.2 was behind the competition for the following reasons:
• The software was cumbersome to use, with SMS site servers requiring installation on a Windows NT 4.0 backup domain controller (BDC).
• SMS 1.2 could only manage the domain it resided in.
• The end-user experience was very poor; you can still hear people joke today about the extremely long logon times in SMS 1.2. These long logins were due to the product inventorying the client systems during their network login, using a login script.
• SMS 1.2 was Microsoft’s management software during the latter part of the 1990s, but the console only ran on a Windows NT 4.0 workstation. This was at a time when NT 4.0 was competing with Windows 95 and 98, two systems that were able to run on laptop computers much more efficiently. The console platform limitations further limited the adoption of SMS 1.2.
Microsoft released SMS 2.0 (code-named Opal) in January 1999, and shortly after that, its first service pack (SP). The product was one of the first management tools utilizing the Microsoft Management Console (MMC), and it incorporated major changes for SMS administrators and the worldwide community. Enhancements included the following:
• Logon experience— Eliminating the use of login scripts (although smsls.bat was still used with logon points).
• Software discovery— Removing the requirement to specify the software files to inventory (a poor way to determine what exists because you obviously don’t know the information to begin with).
• Site server placement— Eliminating the requirement for the site server to reside on a BDC or domain controller (DC).
• Subnet targeting— Targeting a group of subnets as its management scope. Targeting subnets made the tool much more flexible and allowed managing multiple domains from a single SMS site.
The following sections discuss additional enhancements.
SMS 2.0 introduced separate Hardware and Software Inventory Agent components. The agents were configurable independently of one another and able to run on completely different schedules. Most noticeably for the end-user experience, inventories did not run at login time. These changes allowed administrators to become aggressive and run inventories based on business requirements, without affecting end users’ systems.
Microsoft listened to the SMS community’s feedback and coded the Hardware Inventory Agent to run 15 minutes after the SMSExec service started if inventory was scheduled. The Software Inventory Agent was coded to behave similarly, 30 minutes after the service started.
SMS 2.0 introduced software metering and license enforcement. Although the initial implementation was not as successful as Microsoft hoped, SMS 2.0’s software metering served as a learning opportunity for what corporations considered acceptable regarding license management. The SMS 2.0 version allowed administrators to track applications, ensure license compliance, and monitor software usage throughout their organization.
The component required its own database, did not support mobile computing, and was generally intrusive on the user experience. The issues associated with metering, which grew exponentially as laptops became increasingly prevalent in the workplace, ultimately shut down most deployments.
SMS 2.0 released in early 1999, just prior to Y2K (Year 2000). One of the product’s biggest draws—a feature used by SMS administrators worldwide—was its ability to implement Y2K patches. Y2K patching was a huge milestone for SMS and led to a large adoption rate for version 2.0. The flip side of this was that the quick adoption rate created a situation where many bugs were uncovered, some quite serious, almost immediately.
The most noteworthy feature in Service Pack 5, released in 2003, was its vast improvement in data discovery record (DDR) processing. SMS uses DDRs to report discovery information to the site database. Prior to SP 5, a DDR took approximately 1 second to process. (Because SP 5 was only a service pack, Microsoft did not update official numbers about the improved scalability.)
The SMS product team and veteran SMS administrators still remember the hectic early days of SMS 2.0. SMS 2.0 was a complete rewrite from the ground up and had numerous bugs. There is still debate today over whether SMS 2.0 became a truly stable platform with Service Pack 2 (released June 2000) or until SP 3 (released in August 2001). Service Pack 4 for SMS 2.0 became available in August 2002, and Microsoft released SP 5 in April 2003.
However, one of SMS 2.0’s largest failings was that none of its service packs included integration with Active Directory (AD), which released with Windows 2000 just a year after the base release of SMS 2.0.
Microsoft launched SMS 2003 (code-named Emerald) in November 2003. Two major and three minor changes to SMS 2003 helped set it apart as the dominant systems management suite for Windows:
• The two major changes were Active Directory Integration and the Advanced Client.
• The minor, not-so-well-recognized changes included the following:
• Implementing software metering in a passive, silent fashion
• Adding a built-in reporting system
• Leveraging Background Intelligent Transfer Service (BITS) to handle bandwidth throttling
Incorporating BITS helped minimize the impact of software updates and downloads on the user experience.
SMS 2003 had the capability to extend and store key configuration data about its hierarchy in AD, using a small handful of schema extensions that were an optional part of the installation. This led to a number of benefits:
• Site boundaries— Using Active Directory let SMS administrators use AD sites rather than specify subnets for site boundaries.
Using Active Directory sites as site boundaries added flexibility to SMS and saved hours of painstaking and tedious work. Incorporating AD sites also let SMS 2003 implementations easily adapt to network changes, because SMS could automatically detect changes when network administrators changed subnets at various locations and in Active Directory.
• Schema extensions— SMS schema extensions are a series of classes and attributes stored within AD and replicated among global catalog servers. Schema extensions facilitate client installation, site assignment, and global roaming.
• Advanced security— Advanced security allowed administrators to use machine accounts in AD to grant permissions across the organization.
Using machine accounts eliminated a plethora of problems, including account lockout issues, password resets, site resets, and broken clients due to corporate password change policies. (Security problems were such an issue in SMS 2.0 that Microsoft’s only workaround for account-related issues was recommending SMS administrators place sites in resource domains with looser security!)
With advanced security, only one service account was necessary to push clients from the server, allowing a cleaner security implementation.
• Discovery process— AD Integration allowed SMS administrators to be selective about the objects they discovered. Administrators could target any Organizational Unit (OU) or Lightweight Directory Access Protocol (LDAP) path possible for any system, user, or group discovery process. This eliminated maintaining unneeded objects in the site, database, or collections because of product limitations.
• Distribution points— Distribution points (DPs) were also able to leverage AD, by using AD sites defined as their boundaries.
SMS administrators could define who could and could not connect to a DP by specifying permitted AD sites. This stopped clients from pulling content from a remote DP, improved the overall end-user experience with fast package installation times, and minimized the risk of saturating wide area network (WAN) links due to a package installation occurring across a slow link.
• Roaming boundaries— Roaming boundaries were a new concept in SMS 2003 and took advantage of AD integration as well.
Roaming boundaries allowed clients to move from one Internet Protocol (IP) network to another without uninstalling the client, a major drawback with SMS 2.0. Roaming always involves an IP network change for the client, either between offices or from an office to the user’s home network. SMS 2.0 uninstalled the client and then reinstalled it when the computer returned to the corporate network, initiating new full hardware and software inventories and potentially package installations, depending on their configuration. Although there were some workarounds for this behavior in version 2.0, they did not really address the roaming issue as well as the Advanced Client did in SMS 2003.
The single biggest improvement in SMS 2003 was undoubtedly the Advanced Client, referred to as the Mobile Client during the beta test cycle. The Advanced Client had a completely new architecture, which included the following features:
• Sending inventories using a compressed eXtensible Markup Language (XML) format.
• Not automatically uninstalling clients.
• Easily building clients into an image, without concern of duplicating the client Globally Unique Identifier (GUID).
• Clients checking into AD themselves and storing their history in Windows Management Instrumentation (WMI), not in the file system like the 2.0 client. Therefore, uninstalling and reinstalling a client did not mean the user got all the applications he or she previously received, again.
The Advanced Client used BITS and downloaded packages from DPs using the Hypertext Transfer Protocol (HTTP). Using BITS allowed a download to pick up where it left off if the connection was broken during the download (also known as checkpoint restarting). BITS increased package deployment success rates and minimized deployment times for the following reasons:
• Clients now could download the package to their local cache in the background, during daily activity.
• At execution time, the clients could be configured to run the package from a local disk, thus reducing server disk contention on DPs and allowing clients to run packages when not connected to the infrastructure.
If an Advanced Client traversed the WAN, it would still only receive policy from its own site, thus addressing another issue SMS 2.0 was plagued with—the traveling corporate user. No longer would these users automatically be reassigned to a site because they spent time working there.
SMS 2003 also included a Legacy Client, which was purely for backward compatibility to support Microsoft operating systems unable to run the Advanced Client. These systems included Windows 95 and 98, Windows NT 4.0 SP 6a, and Windows 2000 systems prior to SP 4.
Service Pack 1 for SMS 2003 was released in September 2004. Although primarily a hotfix rollup, the service pack included new functionality:
• SP 1 limited legacy support to Windows 98 and Windows NT 4.0 SP 6a only—support was removed for Windows 95, Windows NT 4.0 SP5, and earlier versions. Optionally, administrators could publish a child site server in the hierarchy running an older version of SMS to support these clients if necessary.
• The service pack dropped the requirement for the Windows Internet Naming Service (WINS) if the AD schema was extended and DNS was configured to enable SMS clients and servers to resolve each other’s NetBIOS names.
• The service pack provided SMS administrators the ability to categorize and organize objects in the SMS Administrator console using folders, a new feature with SP 1.
• SP 1 provided SMS support for managing systems that were members of a workgroup.
Microsoft released SMS 2003 Service Pack 2 in June 2006. SP 2 included hotfix rollups and new functionality, including querying AD security groups, Fully Qualified Domain Name (FQDN) support, support for x64, IA64, and R2-based Windows Server 2003 installations, multithreaded software inventory processing, replicating decommissioned DDRs up the hierarchy, and updates to the Inventory Tool for Microsoft Updates (ITMU).
In late 2006, Microsoft announced its first SMS version using the branding R2 (for Release 2). SMS 2003 R2 built on SMS 2003 SP 2, with enhancements that included the Inventory Tool for Custom Updates (ITCU) and the Scan Tool for Vulnerability Assessment.
Service Pack 3 for SMS 2003 was released in April 2007. Microsoft’s acquisition of AssetMetrix introduced Asset Intelligence for SMS 2003, included in the service pack. Asset Intelligence brings categorization of over 400,000 software titles in over 100,000 categories. SP 3 also gave SMS administrators the ability to deploy Windows Vista using the Operating System Deployment (OSD) feature pack. Administrators could also deploy updates to Vista clients and applications as well as perform hardware and software inventory on Vista clients.
Microsoft released System Center Configuration Manager 2007 in August 2007. Known as SMS v4 during beta testing days, the product was rebranded toward the end of the development phase. This version is the first to include the previously separate “feature packs” directly in the product. Using SMS 2003, one might install four to eight different feature packs to incorporate various capabilities, but then some of these items did not show up on the administrator’s console without running a local installation!
In Configuration Manager 2007, Desired Configuration Management, Operating System Deployment, Device Management, Patch Management and other features come built in to every ConfigMgr console—these components previously required multiple, separate installations. ConfigMgr 2007 no longer has a Legacy Client; there is only one ConfigMgr client for all supported operating systems, starting with Windows 2000 Professional.
ConfigMgr 2007 has a concept of native mode as the security mode. Native mode allows using Public Key Infrastructure (PKI) to secure client-to-server communication, as discussed in detail in Chapter 6, “Architecture Design Planning.” ConfigMgr also supports an implementation model known as Internet-Based Client Management (IBCM). IBCM allows managing clients across numerous firewalls, including unmanaged ones. This implementation allows ConfigMgr administrators to push software or updates to clients surfing the Web from home or a hotel. Chapter 6 also discusses IBCM.
Table 2.1 compares the SMS 2003 and ConfigMgr 2007 feature sets.
Microsoft released Service Pack 1 for Configuration Manager 2007 in May 2008. SP 1 includes hotfix rollups and adds support for Vista SP 1 and Windows Server 2008. The service pack also provides support and integration with the Intel Active Management Technology (AMT), which allows remotely powering on and off systems as well as remote diagnostic capabilities. Asset Intelligence-related changes in the service pack include its addition as an independent node in the ConfigMgr console, an expanded catalog, new customization capabilities, new reports, hardware and software inventory enhancements, software license management capabilities, Client Access License-related data for Windows Server and Exchange Server, and Key Management Servers (KMS) for Windows Vista activation.
The R2 release of ConfigMgr 2007 (August 2008) incorporates a number of new features:
• Application virtualization
• Client status reporting
• Multicast delivery of images
• Forefront client monitoring using a new Desired Configuration Management (DCM) configuration pack
• OSD unknown computer support
• Run As capability in the run command-line option of the Task Sequence Wizard
• The ability to convert from the traditional ConfigMgr reporting environment to using SQL Reporting Services for reports
Now that you have had a glimpse of the history of Configuration Manager, it is time to look at some key terminology for the product.
Configuration Manager uses terminology that is unique and specific to its management infrastructure and the actions it can carry out among its clients; these clients can be servers, workstations, or mobile devices such as PDAs and smartphones. The next sections of this chapter describe site, hierarchy, and role terms, providing a foundation to understand how these objects interact with one another, ConfigMgr clients, and the infrastructure.
The site server is a site system role assigned to the server where the Configuration Manager setup program runs. By definition, each ConfigMgr site has at least one site server. This system has the ConfigMgr binary files installed on it, and can have clients assigned to it for management purposes. The site server manages all components belonging to its site, including management points and distribution points.
Site servers are divided out into two types:
• Primary site servers
• Secondary site servers
Although both are types of site servers, there are significant differences between the two, differences you will need to understand to place them properly in your organization. The next sections discuss these differences.
Primary site servers reference a SQL Server installation and store their configurations, client inventories, statuses, and other attributes in a SQL Server site database. SQL Server is typically installed locally, and Microsoft recommends this as a best practice. A local database installation provides the following advantages:
• Simplified management
• Reduced chance of resource contention
• Allows implementing the most secure and simple installation of SQL Server, thus safeguarding the client’s inventory data
Primary site servers can scale to approximately 100,000 clients per server, although political or organizational reasons may mandate more than one site server and a lower client count per site. Primary site servers require a Microsoft Configuration Manager 2007 license for each site. (Chapter 4, “Configuration Manager Solution Design,” discusses ConfigMgr licensing.)
Every Configuration Manager implementation has a minimum of one primary site, also known as the central site. The central site is the top primary site in the hierarchy. Whether there is one Configuration Manager site or multiple sites, the top of the hierarchy is always the central site. All inventory rolls up the hierarchy, making this site server the central repository for all client configuration data in the enterprise.
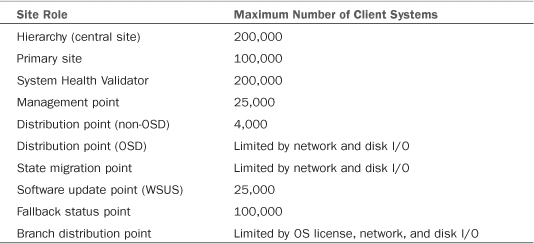
Scalability in ConfigMgr 2007 has increased substantially from SMS 2003 to support some of the largest and most complex enterprise environments around the world. Because ConfigMgr has so many unique roles, each of them has its own respective scalability limits due to the type of traffic involved.
Microsoft made public the scalability figures listed in Table 2.2 at the 2008 Microsoft Management Summit.
To achieve numbers in the ranges listed in Table 2.2, you must perform proper sizing of the ConfigMgr hardware and allocation of ConfigMgr resources. A great difference exists between the types of traffic, such as patch management, application distribution, and OS deployments. Sizing is also discussed in Chapter 4.
Given the capabilities of a primary site server, what is the role of a secondary site server?
• A secondary site does not have a SQL Server database.
• A secondary site server can only be a child of a primary site.
• Secondary site servers typically are used to manage a large amount of client data over WAN links.
Here are some examples when you may want to use secondary site servers:
• If you are concerned about network traffic between the clients and the Configuration Manager hierarchy, secondary sites can host a Distribution Point role and then throttle and limit when packages are updated on that DP.
• Let’s say you have a large number of clients at a remote location and desire to cache client inventories and upload them to their primary site server at a more opportune time. This capability requires leveraging the proxy management point to have the secondary site server cache, compress, and then upload the data to the primary, while complying with a rate limit and schedule defined on the server’s address.
You perform secondary site server administration through the parent site or some other site higher in the hierarchy, such as the parent’s parent. In essence, a secondary site server can reduce the load on its parent primary site server, and it is more efficient with network bandwidth usage during peak times over a WAN link.
Tip
Distribution Points on Secondary Site Servers
Over the years, many SMS administrators have implemented distribution points on secondary site servers without configuring the SMS address for the sender, used by SMS to communicate with the site system. This results in a more complex architecture with no real benefit. If you do not configure bandwidth throttling, there is no point in having the DP belong to the secondary site.
Site systems are servers, and in some cases workstations, that host roles for the Configuration Manager infrastructure. Site systems include the following:
• Component server— A computer with ConfigMgr software installed on it. A component server is a ConfigMgr server that has had the ConfigMgr setup run on it locally and ConfigMgr software installed.
• Site database server— Required for primary sites only. This is the server running SQL Server and hosting the site database.
• SMS provider— Required for primary sites only. The provider is the WMI layer sitting between the ConfigMgr console and site database.
• Management point— Used for client and policy download. This is a location where Configuration Manager computer and device clients can exchange data with the ConfigMgr site services. ConfigMgr clients and the site server do not communicate directly with each other; all communication is facilitated via the management point. There must be at least one default management point for every ConfigMgr hierarchy.
• Distribution point— A distribution point is a share containing ConfigMgr packages for clients that will download them for installation. DPs are used with software distribution, software updates, and OSD. DPs do not require an additional ConfigMgr license.
• Branch distribution point— A branch distribution point allows a distribution point to be defined as a workstation. This is ideal for remote locations with fewer than 10 workstations, removing the need to install a secondary site server. (New with ConfigMgr 2007.)
• Server locator point— Used when the AD schema is not extended or when managing clients in workgroups or untrusted AD forests. The SLP helps clients find management points when they cannot find that information through AD and informs clients which MP to access to install the client software, completing client site assignment on the intranet.
• Software update point— The software update point (SUP) is assigned to the computer running WSUS, and is only required if using the Software Updates capability. New with ConfigMgr 2007 is its integration with WSUS and thus the SUP. WSUS enables administrators to deploy Microsoft updates to computers running the Windows operating system, leveraging built-in Automatic Updates technology. ConfigMgr now uses this role to distribute various updates to Microsoft client systems.
• State migration point— OSD uses the state migration point when migrating user state and settings from one computer OS load to another as part of operating system image deployment. The SMP can be used in both Refresh PC and Replace PC deployment scenarios. The state migration point requires Internet Information Services (IIS). You can use the state migration point for other functions, such as automating backup of the user’s state to the network.
• Fallback status point— The fallback status point (FSP) is used to help administrators monitor client deployment and identify any problems encountered during installation or assignment. It also helps to identify clients that are unmanaged because they have problems communicating with their MP, which is particularly relevant when operating in native mode. (New with ConfigMgr 2007.)
• Reporting point— Hosts the Report Viewer component that provides web-based reporting functionality. The reporting point is only required if reports are run on a particular primary site.
• PXE service point— Responds to Preboot Execution Environment (PXE) requests from computers requesting operating system deployment. (New with ConfigMgr 2007.)
• Device management point— An extension to the management point or proxy management point. The device management point allows mobile devices to connect to ConfigMgr servers and receive policy and configuration settings.
• Out of Band service point— Used to enable out of band management for clients; can only be installed on primary site servers. (New with ConfigMgr 2007 SP 1.)
• Reporting Services point— Delivers integration with Microsoft SQL Server Reporting Services. (New with ConfigMgr 2007 R2.)
• System Health Validator point— Assigned to the computer running the Network Policy service. Only required if the Network Access Protection feature is being used. (New with ConfigMgr 2007.)
Site systems should always reside in the same AD forest as the site server. Spanning Active Directory forests with Configuration Manager sites is not recommended because you would span the Active Directory security boundary by allowing administration from a different forest.
Although not recommended, it is possible to have the following site systems in a remote forest:
• Server locator point
• Fallback status point
• Distribution point
• Management point
• Software update point
• System Health Validator point
• PXE service points
Site hierarchies exist when there are more than one Configuration Manager site server and the servers have a parent/child relationship defined between them. Hierarchies can be very simple and flat or complex and deep to support an organization’s requirements for systems management.
A parent ConfigMgr site implies there is at least one child site. A parent site can have many children, and those children can have children. Secondary sites cannot have child sites, and the parent of a secondary site is always a primary parent site, because secondary sites do not have their own database.
Only the PMP and DP roles can leverage the sender that the secondary site relies on for communication to the parent primary site.
A common hierarchical model is for a central site to manage servers and a child primary to manage workstations. This architecture provides a structure for the server administrators to manage their systems and the workstation administrators to manage their systems while segregating the management of those systems, the features enabled, schedules, and so on. Figure 2.2 illustrates an example of a three-tiered hierarchy with two branches, one of which is two-tiered.
Configuration Manager 2007 uses a new client, known as the Configuration Manager client. This client is the agent residing on all managed systems. The ConfigMgr Client agent periodically checks in with the ConfigMgr infrastructure, using an administrator-defined interval. This interval is every 60 minutes by default, and can be set to be as wide as 1,440 minutes (every 24 hours). The client supports installation in a number of ways—preloaded into an image, manually installed, installation with a silent command line, via WSUS, or a pushed installation by the ConfigMgr server (manually or automatically) using the discovery processes defined later in the “Discovery” section of this chapter.
The ConfigMgr client is responsible for installing and removing software, running inventory, reimaging a system, performing patch management compliance scans, monitoring desired configuration compliance, software metering, remote control support, maintenance tasks, file collection, downloading policies, and uploading status messages. The client is bandwidth aware and leverages BITS to determine available network capacity and utilize that to download packages without affecting end-user performance. Chapter 5, “Network Design,” describes BITS in detail.
Installing the Configuration Manager Computer Client agent gives an administrator the ability to enable hardware and software inventory client agents to collect specific types of data and upload them to the ConfigMgr infrastructure in an efficient and compressed XML format. Hardware and software inventory run under the client SMS Agent Host service. The settings (policies) defined for the various client agents, often referred to as sitewide settings, affect all clients monitored by the ConfigMgr site.
Hardware inventory enables collecting data on client systems from their motherboard, BIOS, hard disk, CPU, video card, network card, Registry, WMI, and other components. Hardware inventory uses MOF (Management Object Format) files to define what is to be inventoried and the format used to report that data. The Hardware Inventory Client agent defines hardware inventory frequency.
ConfigMgr incorporates a major shift in handling MOF files. In earlier versions, the SMS_Def.mof file was the only MOF file SMS provided natively to collect inventory. The problem was most administrators modified the file directly to extend inventory to include things such as proxy settings or antivirus definition dates and versions. Service packs and site resets overrode any customizations to the SMS_Def.mof file, making it critical to maintain backups.
ConfigMgr 2007 MOF files are functionally similar to OpsMgr management packs. The Configuration.mof file defines the data classes inventoried by the Hardware Inventory Client agent. You can create data classes to inventory existing or custom WMI repository data classes, or registry keys present on client systems.
The Configuration.mof file also defines and registers the WMI providers used to access computer information during hardware inventory. Registering providers defines the type of provider used and the classes it supports. WMI and Configuration Manager 2007 hardware inventory will only access registered providers.
The SMS_Def.mof file defines the reporting classes used by the Hardware Inventory Client agent to determine whether specific client data class information is reported. Reporting classes are based on the WMI repository data classes and the attributes of those classes; these exist on clients by default, or you can add them by customizing the Configuration.mof file.
Reporting class information in SMS_Def.mof is converted into a reporting policy provided to clients during their normal computer policy polling interval. After the client compiles the new reporting policy, the reporting policy information is stored in the client system WMI repository in the InventoryDataItem class of the RootCCMPolicyMachine WMI namespace.
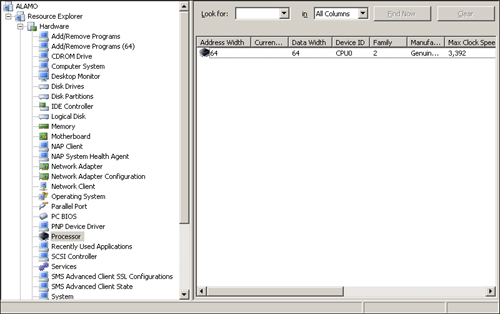
The initial hardware inventory generated by the client is a full inventory. Subsequent inventories are deltas, information that has changed since the initial inventory. All of the hardware inventory data is viewable via the Configuration Manager Resource Explorer, displayed in Figure 2.3, which shows hardware for the Alamo computer system.
ConfigMgr 2007’s Software Inventory Client agent has the ability to scan files, inventory them, and upload this data to the site server. The Software Inventory Client agent can also collect and copy files to the site server. The ConfigMgr administrator enables and configures the Software Inventory Client agent from the Configuration Manager console.
Caution
File Collection Warning
Be careful when you identify files to collect. If you specify collecting a 1MB file, for example, ConfigMgr will collect every occurrence of that file on each client; with 10,000 clients, you would send 10GB across the network and to the site server. Sending this amount of data will affect server storage capacity and introduce network bandwidth concerns.
Software Inventory scans the header and footer of every file with a file extension specified in the user interface (UI). By default, ConfigMgr scans only .exe files. Individual organizations may add additional file types to this list to identify specific software. When Software Inventory initially runs on a system, it performs a full scan of the drive and generates a manifest of all files the system contains. All subsequent inventories generate delta reports, thus minimizing network traffic and server processing load. Software Inventory catalogs file and product details, including a file’s publisher, product name, creation date, and file version, to name a few. Figure 2.4 shows Software Inventory for the Alamo system.
With Software Inventory, the ConfigMgr administrator can define which drives to scan, and whether to include the Windows system directory, encrypted files, or compressed files. Similar to the Hardware Inventory Client agent, a schedule can be specified determining when the Software Inventory Client agent will run.
The agent also has the ability to group various files it has scanned, which may come from the same manufacturer but show up with different names, under the same overall name. This feature is very similar to the Asset Intelligence integration introduced in SMS 2003 SP 3.
Configuration Manager 2007 uses the MMC, version 3.0, to provide the user interface to configure the Configuration Manager hierarchy and manage clients. An important part of ConfigMgr deployments is installing the ConfigMgr console on administrators’ workstations. A best practice is to run the console from a remote system, not directly from the server.
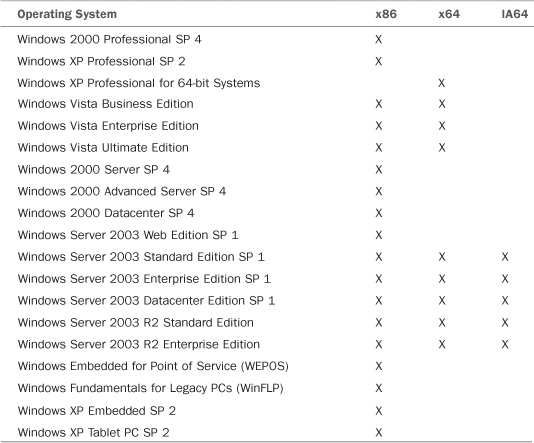
Table 2.3 lists the platforms on which you can install the Configuration Manager 2007 console.
When upgrading to ConfigMgr 2007, many organizations have SMS 2003 and Configuration Manager 2007 coexisting to maximize end-user support. If performing an upgrade or migration from SMS 2003, you can run the SMS 2003 and the Configuration Manager 2007 consoles on the same computer in parallel. In addition, most functions an administrator can perform on a secondary site server, using the primary parent SMS Administrator console, are available with the ConfigMgr 2007 console.
Because the console now uses MMC 3.0, it can take advantage of a new feature called the Actions pane. This pane is context sensitive and allows administrators to quickly see and execute different tasks, based on what they selected elsewhere in the console. The console is used to configure and manage the ConfigMgr infrastructure, to execute tasks such as distributing packages and advertising packages and task sequences, to review inventory, and so on.
Caution
Mixed SMS/ConfigMgr Scenarios
Do not install the ConfigMgr 2007 console on an SMS 2003 secondary site server. Doing so will result in an SMS 2003 secondary site server that cannot be upgraded.
The ConfigMgr console displays what are known as top-level objects, also referred to as nodes. SMS 2003 had 12 top-level objects in the SMS Administrator’s console. Microsoft substantially redesigned the ConfigMgr 2007 console to be more intuitive and logical in regard to grouping objects that work in conjunction with one another. The console now has only five top-level objects: the Site Management, Computer Management, System Status, Security Rights, and Tools nodes.
You can view an example of how this change is implemented by looking at the top-level Computer Management object, which has 12 child objects. Software Distribution is one of the child objects and contains packages and advertisements, which are two nodes where administrators spend a lot of time. Figure 2.5 displays the Configuration Manager console with the Software Distribution node highlighted.
Collections are logical groupings of computer systems, users, or groups. They identify objects for a variety of purposes, such as the following:
• Pushing software
• Viewing inventory
• Viewing the result of a query
• Providing remote support via remote control and remote tools
• Grouping of systems with a common piece of hardware or software
You can populate collections using a direct membership or query membership rule. Both these methods allow the administrator to populate a collection. Collections are discussed in more detail in Chapter 14, “Distributing Packages.”
Collections can have subcollections. This is useful for organizational reasons as well as for software distribution, due to the ability to advertise a package to a collection or its subcollections. Subcollections are also discussed in Chapter 14.
Collection security gives Configuration Manager administrators the ability to manage which administrators will have varying levels of access to specific collections. Configuration Manager 2007 uses an implementation of WBEM (Web-Based Enterprise Management) security, a standard created by the DMTF (Distributed Management Task Force). Chapter 3, “Looking Inside Configuration Manager,” discusses WBEM and the DMTF. The WBEM security model leverages a class/instance model and is extremely granular. Most ConfigMgr objects have specific rights, which you can grant unique to an object.
ConfigMgr discovers resources in a networked environment using a variety of built-in discovery methods. These discoveries create DDRs, which you can display in collections and queries. ConfigMgr has six types of discovery methods:
• Active Directory System Group Discovery
• Active Directory Security Group Discovery
• Active Directory System Discovery
• Active Directory User Discovery
• Heartbeat Discovery
• Network Discovery
The Active Directory discovery methods have the ability to specify LDAP paths for which you want to discover objects. Although some discovered objects such as users and groups are not capable of management, they are useful for reporting and using in query criteria to populate collections for application distribution.
Each discovery method has its own schedule, allowing configuration on a recurring interval and at non-peak times. See Chapter 12, “Client Management,” for further information on discovery methods.
Software metering in ConfigMgr is passive, collecting data for a specified amount of time about the usage frequency of applications. Software metering gives administrators the ability to monitor specific application usage across the entire enterprise. Unlike in earlier versions, administrators no longer need to define most commonly used applications because ConfigMgr creates these rules automatically if an administrator-specified percentage of the environment is using an application.
ConfigMgr uses packages to distribute software and changes to clients. Think of a package as a change in a client’s configuration. Historically, administrators have only thought of packages as software installs. Packages can be the silent uninstallation of an application, a remediation package from a desired configuration baseline that has been strayed from, a change to a Registry key, the startup behavior of a service, and so on. See Chapter 13, “Creating Packages,” for a discussion of packaging.
Packages are distributed to DPs where they reside for clients to access. This distributed copy of the package architecture allows efficient use of bandwidth-sensitive links and minimizes the impact to the network infrastructure. Clients can download packages into their local cache and execute them later, mitigating the scenario where hundreds of clients all run an installation off a server at the same time.
Once distributed, packages are advertised to collections, which contain computer, user, or group resources. This process allows the package command line to execute according to a strict schedule and set of parameters that determines how the package will run and how the client operating system behaves, not only while the package is installing but also after it completes.
Advertisements are policies that ConfigMgr clients download and execute on a schedule. Advertisements define when clients can execute the program in a package and whether to run it from a distribution point or copy it to their local cache and run it locally. Chapter 13 also discusses advertisements.
By definition, advertisements require a user to initiate launching the package command. Mandatory advertisements do not require any user input and are actually a push-install, opposed to the pull-install used with advertisements in their default mode. You can use features such as Wake On LAN (WOL) in conjunction with mandatory advertisements to minimize impact to the end-user community.
Tip
Using Mandatory Advertisements with WOL
With mandatory advertisements, the ConfigMgr administrator can keep his enterprise patched to the level desired, without any user impact or interaction. Users can shut their computer down when they leave for the day to help with the company’s green (energy-saving) initiative. An administrator can push a package out with a mandatory advertisement configured to shut down the computer on completion of the installation. When the user arrives the next day and turns on the machine, the startup completes the reboot cycle needed to complete the patch installation.
ConfigMgr administrators can create DPs throughout an enterprise having a large number of client systems, thus minimizing network traffic over the WAN and slower links. Distribution points can utilize BITS, but not for throttling package traffic from the site server to the DP. BITS also allows checkpoint restarting. In other words, if there was an interruption to a download at 60% completion, using BITS allows the download to resume at that point instead of starting over again from the beginning, which is what happens when clients connect to DPs using Server Message Block (SMB) traffic. Distribution points can be installed on a system as either a package share or a server share. See Chapter 14 for additional information regarding the use of distribution points.
Senders are located on primary and secondary sites. Senders define how ConfigMgr sites use existing network connectivity to manage the connection, ensure the integrity of transferred data, recover from errors, and close the connection if no longer needed.
Sender types include the following:
• Standard sender
• Courier sender
• Asynchronous RAS sender
• ISDN RAS sender
• X25 RAS sender
• SNA RAS sender
The most common sender used is the standard sender, which is the only type required when there is basic network connectivity across a LAN or WAN. Microsoft designed the courier sender for sending excessively large packages across a network with slow links. The purpose of the courier sender is to create a parcel, which is a collection of files from a package, and ship the parcel on tape or CD to the remote site location where the administrator can then load the package into the site. Chapter 5 discusses the courier sender. Asynchronous RAS, ISDN, X25, and SNA senders communicate over each of those respective types of links.
Addresses define a site code and the security account used to communicate with a remote site. Addresses also give ConfigMgr administrators the ability to schedule when traffic can flow between the two sites by priority of the traffic, as well as the percentage of bandwidth the sites may use during communications. All communication between ConfigMgr sites use SMB and travels on TCP port 445. By default, ConfigMgr secures site-to-site communication by secure key exchange, which only needs to be defined per parent/child connection. Figure 2.6 displays the Rate Limits tab for the Dallas site, limiting the transfer rate used to send data to that site.
BITS is a subcomponent of IIS, a component of Windows. Using BITS allows administrators to prioritize and throttle asynchronous file transfer between two Windows systems. BITS uses available network bandwidth to handle transfers, making them transparent to the end user’s experience. BITS monitors network traffic on the local network interface and throttles itself accordingly. BITS also provides the ability to continue transferring data when network connectivity is intermittent or unreliable by leveraging checkpoint restarting.
Task sequences are new in ConfigMgr 2007. Task sequences consist of a series of customizable tasks or sequentially performed steps running in an unattended fashion on a system. Task sequences often are only thought of in the context of operating system deployments. Because you can advertise task sequences directly to client systems, you can use them for a multitude of things, including chaining a series of actions together. Task sequences allow each action in the sequence to be independent of the other, let you change the order of tasks, and allow each action to have its behavior individually defined if errors occur. Task sequences consist of actions, custom and built-in actions, conditions, and steps. Task sequences also support grouping of actions for organizational purposes.
ConfigMgr maintains status on many of its technologies. Package status provides a summary of the version and time packages were copied to various distribution points. Advertisement status details when clients have received advertisements and started advertisements. It also shows the succeeded or failed status in the overall execution of the advertisement. Site status gives administrators a bird’s-eye view of the health of the entire ConfigMgr site’s infrastructure. ConfigMgr’s component status details the health of each individual component in the site, such as discovery method’s running state, sender health, DPs, MPs, and so on. Figure 2.7 shows the site status system from the ConfigMgr console.
DCM is a component built in to ConfigMgr that was previously provided in an SMS 2003 feature pack. DCM allows you to assess the compliance of computers with regard to a number of configurations, such as whether the correct Microsoft Windows operating system versions are installed and configured appropriately, whether all required applications are installed and configured correctly, whether optional applications are configured appropriately, and whether prohibited applications are installed. You can also check for compliance with software updates and security settings.
DCM is a framework where the ConfigMgr client has an agent, enabled at the site level, tracking baselines defined by the ConfigMgr administrator. You can also track deviations from the baseline. Each item, known as a configuration item, is tracked against a baseline; the item can be reported against or be corrected when the deviation occurs. System Center Configuration Packs, available from the Microsoft System Center Pack Catalog at http://go.microsoft.com/fwlink/?Linkid=71124, define Microsoft best practices for various product configurations.
You can evaluate both published and manually created baselines for compliance in your organization. Published configuration data from Microsoft and other vendors is available at http://go.microsoft.com/fwlink/?LinkId=71837. You can assign these configuration baselines to a collection, just like an advertisement, and evaluate them on a schedule independent of inventory and other agent schedules. Similar to inventory information, you can evaluate configuration baseline compliance when clients are offline; ConfigMgr sends the compliance data upon reconnection to the site hierarchy. Figure 2.8 displays the DCM home page in the Configuration Manager 2007 console.
See Chapter 16, “Desired Configuration Management,” for a complete discussion of DCM.
NAP, new in ConfigMgr 2007, works with the Microsoft Windows Network Policy Server (NPS) on Windows Server 2008. NAP helps enforce compliance with selected software updates on clients capable of supporting NAP (NAP-capable clients). These clients include Windows XP SP 3 and Windows Vista. Using NAP, a client has restricted network access until it becomes compliant.
Configuration Manager by itself does not enforce compliance with Network Access Protection; it provides the means by which Configuration Manager clients produce a statement of health with a noncompliant status if they do not have the required software updates in the Configuration Manager NAP policies you configure. A Configuration Manager System Health Validator (SHV) point confirms the health state of the computer as compliant or noncompliant and passes this information to the Network Policy Server. Policies on the NPS then determine whether noncompliant computers will be remediated and, additionally, whether they will have restricted network access until they are compliant.
Remediation is the mechanism of making a noncompliant computer compliant to ensure that clients conform to compliance policies. Configuration Manager remediation uses the software update packages you have already created, with the Software Updates feature. See Chapter 15, “Patch Management,” for further discussion.
Reporting in ConfigMgr is functionally very similar to that in SMS 2003. Dozens of reports, utilizing Transact-SQL (T-SQL), expose detailed hardware and software inventory data about the clients in the hierarchy. ConfigMgr 2007 adds a number of troubleshooting reports.
You can launch reports directly through the ConfigMgr console or through the reporting point site system website, and you can easily create custom reports utilizing the existing SQL views exposing the ConfigMgr site’s data. Chapter 18, “Reporting,” discusses ConfigMgr reporting.
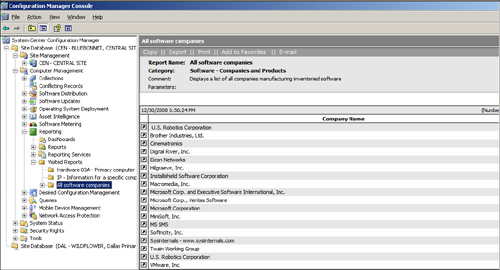
Figure 2.9 illustrates ConfigMgr reports; this particular report lists all software companies collected during software inventory. With Configuration Manager 2007 R2, you can choose to use Microsoft SQL Reporting Services for reporting.
Reports only query data from the local site server, some of which will be from child sites in the hierarchy if they exist. Because inventory and other types of data flow up the hierarchy, child sites data will show up in ConfigMgr reports run on a parent site. ConfigMgr groups reports into categories to facilitate organization, and reports may link to one another to provide an experience similar to drill-down reporting. You can configure reports to prompt the user for data, to provide lists of available options for prompts, or to be fully automated.
Security in ConfigMgr is based completely on WMI, Microsoft’s implementation of Web-Based Enterprise Management. WBEM allows access to providers such as Win32, WMI, SNMP, and Desktop Management Interface (DMI). In addition to collecting data, WBEM provides a method to secure the data by utilizing a class and instance model. As an example, the Packages node is a class containing a package for Microsoft Office, which would be an instance within the Packages class.
As shown in Figure 2.10, you need to permit granular rights specific to the class to individuals or groups, and then to specific instances of that class. Although a ConfigMgr administrator may have administrative rights on the ConfigMgr server and the SQL database for ConfigMgr, if not granted class and instance rights through the ConfigMgr console, the administrator cannot access any of the ConfigMgr objects within the ConfigMgr console.
By default, only the account used to install ConfigMgr has rights to all ConfigMgr classes and instances. As a best practice, the account used to install ConfigMgr should be a service or application account.
Those topics are covered in Chapter 20, “Security and Delegation in Configuration Manager 2007.”
The next sections discuss how Configuration Manager 2007 can reduce IT’s total cost of ownership (TCO) in a networked environment. ConfigMgr 2007 facilitates standardizing applications and the operating system, and provides methods for remotely supporting users and their systems in a fast and efficient manner. With the ability to pull data and push software across a LAN/WAN comes responsibility in understanding the impact these processes can have on the infrastructure and the end user’s computing experience and overall productivity.
The most successful implementations of SMS, or any other software distribution tool, historically have been in standardized environments. Standardizing operating systems, patch levels, application loads, hardware, and overall configuration allows administrators to test their deployments before rolling them out to the enterprise. Hardware-independent imaging, only recently a reality, allows administrators to build a single image and inject drivers on the fly during the deployment process. This process allows you to use one image for any number of hardware manufacturers and models, creating the most standardized OS deployment process available today.
Inventory allows administrators to logically group systems by any combination of hardware and software. This inventory data is useful in defining deviations from the standards created by an organization. Inventory data allows organizations to see the software installed on client systems, and software metering allows organizations to see the software executed on client systems. Analyzing these two sets of data helps organizations make educated decisions regarding software deployments and licensing.
Operating system deployments and migrations allow organizations to standardize their environment, thus controlling installations and configurations at the operating system and application level. Historically, operating system deployments have been a manual and time-consuming process, making it extremely difficult for large organizations to standardize their environment. Now operating system deployments are easier than ever, allowing levels of standardization that previously were out of reach due to technology, resources, and expense.
Information Technology has increasingly become a top expense in today’s organizations. The ability to resolve issues quickly after they are identified requires tools that the first tier of support (usually referred to as Tier1) can use to perform tasks as though they were at the end user’s system. These tools are critical to managing and lowering TCO of IT assets.
Tools such as Remote Control, Remote Desktop, and Remote Assistance give administrators the ability to run commands, see the hardware and software installed, and above all see the user interface the user is seeing. This type of remote control support has become an industry standard for remote user support. Branch offices and micro-branch offices, which have fewer than 10 users, have become increasingly common as corporations change and grow to stay competitive. These business models further complicate the remote management issue, making site visits not an option and remote tools critical to the support of the environment.
Deploying software is one of the most primary functions of any Information Technology group. Getting users the applications, updates, security patches, and other changes required to keep an environment running is critical to a business’s success. For any company to stay agile in today’s market, IT must be able to adapt and meet the business’s needs in a timely, efficient, and inexpensive manner. Being able to deploy software to systems, regardless of location and user’s knowledge or rights of a system, is critical.
There are two primary methods to get a software update to a system—push and pull. Each of these methods ultimately gives the targeted systems the software desired for roll out, but there are many differences between the two and neither is necessarily right all the time.
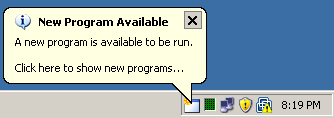
“Pulling” implies that the owner or recipient of the package must initiate some action. This allows the recipient to initiate the change when it is convenient, thus minimizing the impact on productivity. Allowing a user to pull down an application and install it at his or her leisure is also useful for rolling out software with user-specific settings the recipient needs to specify during installation. Even on locked-down systems where users have no rights, the end user can initiate and execute software installations as long as they were set up and approved by the IT administrative staff. Figure 2.11 illustrates the end-user notification that a program is available for installation.
The problem with a software change sent out in a “pull” fashion is that without that user initiation, the change never occurs. You can see how this will be a problem where there are changes that must take place on systems due to company policy. This could also be something a user may not want to do, such as removing a personal application from a company asset. This type of application distribution typically takes place when the users are very self-sufficient and avoiding negative impact to the end user is important.
“Pushing” software speaks to the process of forcing changes to be rolled out in the enterprise. Pushing does not require user interaction, and it can be executed like policy. In fact, pushing software assumes there is no requirement for user interaction, although a need for user interaction with the installation routine does not prohibit an administrator from pushing it out. You can push software whether or not a user is logged on to a system, unlike a pull, where the user must be logged on to initiate the change. This ability to kick off a change on systems with no one logged on addresses multiple items:
• It eliminates file-locking issues
• It removes disruption to the end user’s productivity
• Systems may be shut down afterward, allowing the user starting up the computer to complete a reboot cycle.
• Installation duration is not an issue because there is no user impact.
• Systems may be woken up using Wake On LAN technology to kick off an installation.
• Users are unable to interrupt the installation.
Networks are critical to the daily functions of corporations today. Due to the heavy demand placed on networks, ConfigMgr utilizes several concepts and technologies to minimize the impact it places on the network infrastructure. Many of these technologies can be configured centrally, allowing other administrators to leverage the ConfigMgr architecture without needing deep knowledge of the enterprise’s network infrastructure. Technologies such as BITS, distribution points, branch distribution points, download and execute, senders, and compressed XML are just a few of the technologies available.
• BITS— BITS monitors traffic in and out of the local network interfaces and throttles itself throughout a download, utilizing only the available idle bandwidth. This minimizes impact to the user experience with other network-aware applications, such as Microsoft Outlook or Internet Explorer.
As users’ demand increases for more data from their applications across the network, BITS throttles itself down; as the demand drops, BITS throttles itself up to use as much bandwidth as available. Using BITS also allows an interrupted download to resume where it previously left off. BITS is covered in Chapter 5.
• Distribution Points— The “Distribution Points” section of this chapter previously touched on the DPs concept. It is important to understand that you can place distribution points anywhere, and it is not unusual to have multiple DPs on a single subnet! This is a common architectural design if there is a high demand to run packages from the distribution point or a large number of clients. A common design is to implement multiple DPs in a single location when there are concerns about router contention or high switch traffic.
• Branch Distribution Points— Branch distribution points, introduced in the “Site Systems” section, gives ConfigMgr the ability to push a package across a WAN link to a location with a very small number of clients and only traverse the WAN link one time with the package. SMS 1.x through 2003 pushed a separate package over the WAN link for every client in the remote location. Although third-party software existed to address this SMS architectural deficiency, it was costly and not well known. Now with support available for a client workstation to be a distribution point, the branch office or microbranch office model can easily be targeted and have packages pushed to it.
Whereas ordinary distribution points have packages published (also referred to as copied or pushed) to them by the ConfigMgr administrator, branch distribution points receive their package copy by updating their policy and then downloading the package source using BITS. This pull process is the opposite of how packages are ordinarily published to conventional distribution points.
• Download and Execute— Download and Execute is a feature introduced in SMS 2003; it leverages the BITS technology to cache a copy of the package from the DP. Many people ask, “Why would I want to cache a copy of a package if I have a local DP?”
The reason is quite simple: When packages are assigned, they are mandatory and will launch at the time stated in the advertisement. Because Kerberos tickets are time sensitive, clocks on computer systems today all synchronize with the clock on the PDC Emulator DC. This means that all clients with a mandatory advertisement will start it at exactly the same time, thus placing a heavy load on the local distribution point. The Download and Execute capability gives administrators the ability for clients to cache a copy of the package and upon execution, perform the installation from their local hard drive. BITS allows administrators to configure many things about its behavior, including how long to hold the copy of the package in its cache.
• Senders— Senders allow the throttling and prioritization of traffic by time between ConfigMgr sites. Administrators often overlook configuring senders, leaving the default of allowing all traffic at all times of the day. Without configuring senders, there is no throttling, and the network infrastructure may be utilized by traffic that could have waited until nonpeak hours of the day. Whenever parent/child relationships exist, you should experiment with senders to determine what is right for the environment in regard to time of day and workload.
• Inventory— Even at the inventory level, there are changes allowing a more efficient use of the technology now available. Hardware and software inventories are generated by their respective agents, with the output created in XML. This XML file is then compressed and sent up to the MP immediately. If the MP is not available, the client caches the inventory until the next time it is available or until the next inventory schedule, where it is rerun.
• Testing— With all this technology available to tread the network lightly, it is important to experiment with these settings in a lab environment. It is not uncommon for administrators to make mistakes that will saturate WAN links due to the nature of the product. Test whenever the ability exists to affect a network in a negative way, confirming in advance that the experience will be a positive one. Experimenting with different site configurations, package pushes, and client package execution can determine the overall load on the site, network, and distribution points.
Creating a lab for ConfigMgr is not only necessary for validating the site hierarchy and load testing, but it can also be used for package, security, patch, and upgrade testing. Figure 2.12 illustrates the lab environment used for the writing of this book. The lab incorporates a central site server (Bluebonnet) and four primary child site servers:
Mockingbird and Roadrunner are installed as SMS 2003 site servers; the HOU site, Mockingbird, is upgraded to ConfigMgr 2007 during the upgrade process in Chapter 9, “Migrating to Configuration Manager 2007.”
Microsoft introduces a number of new capabilities in Configuration Manager 2007. The next sections focus on the new and improved features.
Branch distribution points were introduced earlier in the “Site Systems” section. They have the following characteristics:
• While functioning similar to standard DPs, branch distribution points provide greater control over network traffic, which is necessary for branch offices that may have limited network bandwidth availability.
• Branch distribution points allow not only for manual content provisioning, but also provide configurable settings for scheduling and throttling network traffic to help minimize network impact.
• Branch distribution points allow on-demand package distributions, where packages are downloaded to the branch distribution point only when specifically requested by a client computer.
• Branch distribution points are limited to only being able to handle 10 concurrent connections, due to limitations in Microsoft desktop operating systems.
Figure 2.13 shows the General Properties page for a DP; there is a radial button midway down the page to enable the DP as a branch distribution point.
The SUP installs as a site system role in the Configuration Manager console. Each site must have an active SUP before you can enable software updates. You can install a second SUP for communications from Internet-based client computers. You must create the software update point site system role on a server that has Windows Server Update Services (WSUS) 3.0 already installed and configured.
The software update point provides communication with WSUS and synchronizes with the WSUS database to retrieve the latest software update metadata from Microsoft Update, as well as locally published software updates. Once this is configured via the Configuration Manager console, the administrator does not need to perform any patch management in the WSUS console. Instead, all patch management configuration and administration occurs in the ConfigMgr console. Figure 2.14 shows the integration between Configuration Manager and WSUS.
The primary purpose of the fallback status point is to resolve client health issues. Client health describes the overall percentage of clients regularly checking into their designated management points, downloading policy, uploading inventory, and executing specified actions such as running an advertisement to install a package such as Microsoft Office.
The FSP in Configuration Manager 2007 always communicates with clients using HTTP, which uses unauthenticated connections and sends data in clear text, even when the site is in native mode. This makes the fallback status point vulnerable to attack, particularly when used with IBCM. To help reduce the attack surface, always dedicate a server to running the FSP and do not install other site system roles on that server in a production environment.
Install an FSP in the site if all the following scenarios exist:
• You want client computers to report any failures to the site database, particularly when they cannot contact an MP.
• You want to utilize the Configuration Manager 2007 client deployment reports that use data sent by the FSP.
• You have a dedicated server for this site system role and have additional security measures to help protect the server from attack.
• The benefits of using an FSP outweigh any security risks associated with unauthenticated connections and clear–text transfers over HTTP traffic.
PXE is a technology allowing individuals to boot a computer from the network instead of a local disk. You can use this capability in situations where the disk needs to be written to in a way where no files can be in use, such as deploying an operating system.
The PXE service point must be configured to respond to PXE boot requests by Configuration Manager 2007 clients so that those clients can interact with the ConfigMgr infrastructure to determine the appropriate installation actions to take.
Other site systems new to ConfigMgr 2007 include the state migration point and branch distribution point, both introduced in the “Site Systems” section of this chapter.
OSD in ConfigMgr is very different from the OSD Feature Pack on SMS 2003. ConfigMgr 2007 exposes a brand-new task sequencer, which sometimes is thought to be from BDD 2007 because it was available in the Business Desktop Deployment (BDD) Solution Accelerator released slightly earlier. The task sequencer from ConfigMgr was actually integrated into the BDD Solution Accelerator and Microsoft Deployment Toolkit (MDT). This integration allows for interoperability between OS deployments made in BDD/MDT and ConfigMgr. See Chapter 19, “Operating System Deployment,” for a discussion of OSD.
ConfigMgr also now provides the ability to build a complete reference PC, Sysprep, and image it all using a single unattended task sequence. This new capability provides administrators a mechanism to ensure the build process across all systems, regardless of platform or image, is consistent.
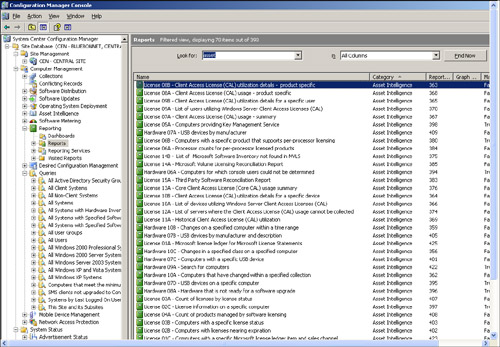
First introduced in SMS 2003 SP 3, Microsoft enhanced Asset Intelligence significantly in Configuration Manager 2007. The Asset Intelligence reports include nine new License Management reports, three new Hardware reports, and six new Software reports.
Besides tracking installed software, auto-start software, and browser helper objects, new Software reports provide information about recently used executables. In addition to the Hardware reports that track USB devices, processor age, and readiness for upgrade, these new reports identify computers that have software or hardware changes since the last inventory cycle. New Client Access License reports, added to the existing License Ledger reports, complete the ability to compare license usage with Microsoft License Statements. Figure 2.15 lists some of the Asset Intelligence reports included with ConfigMgr 2007. Asset Intelligence is discussed further in Chapter 18.
Mobile device management has changed substantially since SMS 2003. ConfigMgr device management enables discovering, inventorying, and reporting on the following mobile device categories:
• Hardware inventory
• Software inventory
• File collection
• Software distribution
• Mobile device configuration items
ConfigMgr 2007 also adds support for the following mobile devices:
• Windows Mobile for Pocket PC 2003
• Windows Mobile for Pocket PC 2003 Second Edition
• Windows Mobile for Pocket PC Phone Edition 2003
• Windows Mobile for Pocket PC Phone Edition 2003 Second Edition
• Windows Mobile Smartphone 2003
• Windows Mobile for Pocket PC 5.0
• Windows Mobile for Pocket PC Phone Edition 5.0
• Windows Mobile 5.0 Smartphone
• Windows CE 4.2 (ARM processor only)
• Windows CE 5.0 (ARM and x86 processors)
• Windows Mobile 6 Standard
• Windows Mobile 6 Professional
• Windows Mobile 6 Classic
The R2 release adds support for Windows Mobile 6.1.
SMS 2003 required connecting mobile devices to a host device running the SMS 2003 client. In ConfigMgr, mobile devices can be managed over Ethernet, wireless, or via IBCM. You can manage mobile devices when they have a standard Internet connection.
IBCM allows you to manage ConfigMgr clients that are outside your network firewall. This configuration has a number of advantages, including the reduced costs of not having to run virtual private networks (VPNs) and being able to deploy software updates in a timelier manner.
Because of the higher security requirements of managing client computers on a public network, IBCM requires the site to be in native mode. Native mode ensures an independent authority mutually authenticates connections to the management point, software update point, and distribution points, and that data to and from these site systems is encrypted using Secure Sockets Layer (SSL). IBCM in essence allows ConfigMgr administrators to manage their client systems wherever they are (home, hotel, and so on) without them having to VPN in. See Chapter 6 for a discussion of IBCM.
Desired Configuration Management and Network Access Protection, both new in Configuration Manager 2007, were discussed previously in the “Desired Configuration Management” and “Network Access Protection” sections, respectively.
ConfigMgr 2007 requires a minimum of SQL Server 2005 with Service Pack 2 for the site database. Microsoft also supports using SQL Server 2005 SP 3 and SQL Server 2008.
The following caveats apply to using SQL Server 2008 with Configuration Manager 2007:
• There is no support for a clean installation of SQL Server 2008 with ConfigMgr 2007 RTM. You need to first install SQL Server 2005, then upgrade the database, and apply hotfix 955229.
• With ConfigMgr 2007 SP 1, Microsoft supports a clean installation of SQL Server 2008; hotfix 955262 is required.
TCP/IP is the only protocol now used for SQL Server to communicate with ConfigMgr; there is no longer a reliance on Named Pipes. The default port SQL uses is 1433, which you can change using the SQL Server Configuration Manager utility. Ports are discussed further in Chapter 5.
In most cases, Microsoft recommends having SQL Server and ConfigMgr on the same server when you install a primary site. Alternatively, Microsoft now recommends that if you are going to use a remote SQL Server, to install an additional network card in both the SQL Server and the ConfigMgr server and dedicate each card to communicate with one another, similar to a heartbeat network on a cluster.
SQL Server has supported using instances (which are multiple installations of SQL in parallel on the same server) since SQL Server 2000. Microsoft now supports the installation of the ConfigMgr 2007 database on a SQL named instance.
ConfigMgr also supports SQL replications, where you can point the MP or SLP roles at a SQL replica to improve performance in low-bandwidth scenarios. This is discussed further in Chapter 8, “Installing Configuration Manager 2007.”
Microsoft does not support the Configuration Manager client on any operating system prior to Windows 2000 Service Pack 4. Installing the Configuration Manager client explicitly is not supported on the following operating system versions:
• Windows 95
• Windows 98
• Windows Millennium Edition
• Windows XP Media Center Edition
• Windows XP Starter Edition
• Windows XP Home Edition
• Windows XP Professional, with less than Service Pack 2 applied
• Windows Vista Starter Edition
• Windows Vista Home Basic Edition
• Windows Vista Home Premium Edition
• Windows NT Workstation 4.0
• Windows NT Server 4.0
• Windows 2000 Server, Service Pack 3 and earlier
• Windows 2003 Server, with no service pack installed
• Windows CE 3.0
• Windows Mobile Pocket PC 2002
• Windows Mobile Smartphone 2002
Many features of ConfigMgr are dependent on other technologies. As an example, Active Directory requires extending the schema to realize many of the benefits of client management. Without schema extensions, many of the automated tasks that clients perform would require manual workarounds.
Internet Information Services is required on several roles, such as management points, server locator points, and reporting points. Distribution points do not require IIS, but are dependent on it if they are going to use the BITS technology.
Windows Software Update Services is the underlying technology for all of Patch Management within ConfigMgr. This dependency on WSUS is why the ConfigMgr installation requirements state the WSUS console at a minimum must be installed on the site server. Having the WSUS console and binaries local to the site server allows ConfigMgr to manipulate the WSUS application and let the administrator authorize the necessary changes through the Configuration Manager console.
ConfigMgr 2007 uses certificates heavily for network access authentication because they provide strong security for authenticating users and computers and eliminate the need for less secure password-based authentication methods.
Network Access Protection is dependent on Windows Server 2008 and native mode in ConfigMgr. ConfigMgr by default installs itself into mixed mode, which means the ConfigMgr site server generates all the self-signed certificates it needs. These certificates are only used within ConfigMgr. By upgrading to native mode (discussed in Chapter 6), industry-standard PKI certificates are used. These certificates are created and managed independently from Configuration Manager, and they can be integrated with other business solutions. In native mode, clients communicate over HTTPS to the following site systems:
• Management points
• Default management point
• Network load-balanced management point
• Proxy management point
• Internet-based management point
• Standard distribution points
• Software update points
• State migration point
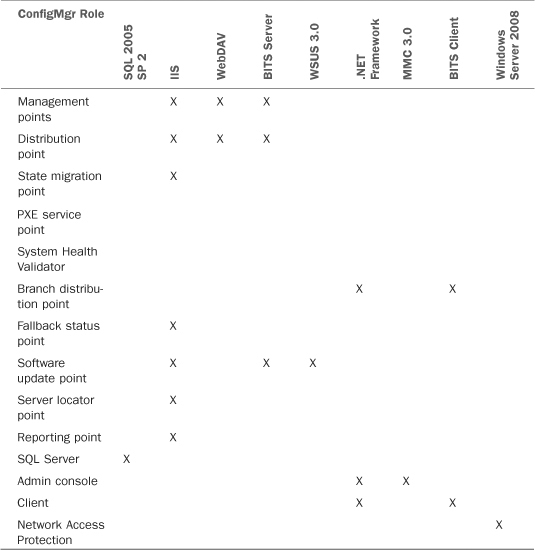
Table 2.4 lists the feature dependencies in ConfigMgr 2007.
For most companies, managing IT systems is a costly endeavor, making efficiency in the field essential. ConfigMgr can help you meet the technical and management challenges facing IT departments today. Its use of an open architecture, which is distributed and scalable to the largest and most complex enterprises, builds on top of existing Microsoft technologies to help you automate configuration and release management in the enterprise.
Configuration Manager 2007 allows you to standardize your application portfolio and desktop images, release software changes to thousands of computers in minutes, reimage systems in minutes, remotely support end users in a timely fashion, track and correct configuration management deviations, and report against all these, plus detailed inventory of all clients in the enterprise. No other Microsoft product lowers the total cost of ownership (TCO) of IT assets in the enterprise.
The next chapter, “Looking Inside Configuration Manager,” discusses the design concepts and working principles of Configuration Manager 2007, along with the ways that ConfigMgr utilizes core Windows technologies.