12
Tumor Detection Using Morphological Image Segmentation with DSP Processor TMS320C6748
T. Anil Raju1*, K. Srihari Reddy1, Sk. Arifulla Rabbani1, G. Suresh1, K. Saikumar Reddy1 and K. Girija Sravani2†
1 Department of Electronics and Communication Engineering, Lakireddy Bali Reddy College of Engineering, Mylavaram, Krishna District, Andhra Pradesh, India
2 Department of Electronics and Communication Engineering, KL University, Green Fields, Andhra Pradesh, India
Abstract
Image processing continues to enable the technology revolution that we are experiencing today. The main objective is to carry out a new cooperative approach for image segmentation and feature extraction using DSP Processor with good accuracy. The basic process involved in this paper to understand image segmentation is Edge detection. To improve the segmentation process and better estimation of the final clusters centers, involvement of DSP processor is used for computation and accuracy. Image segmentation using DSP processor TMS320C6748 is implemented in this proposed work. After detecting the edges of the image, Segmentation is done based on Morphological operations. The performance is measured by including some various optimization techniques and all results are shown using CCS platform. Hence our proposed method shows that the segmentation computation and accuracy is improved.
Keywords: Image segmentation, DSP processor TMS320C6748, thresholding method
12.1 Introduction
Image processing is an active research area which has become a vital component of a large number of present real-time applications. Segmentation is an important imaging technique for detecting abnormal changes in intensity levels of image. In computer vision, image processing is a highly challenging field; image segmentation is still a broad research topic and also an essential task in many applications because it plays a major role in the MRI image understanding. The MRI Images segmentation [1] has become the focus of contemporary research; some applications require a simple division of image into homogeneous regions while others require more accurate detection [2]. For this reason we need a special unit that we use for digital signal and image processing in a real-time execution and also the high-speed data transfer.
A digital signal processor [3] is one of the core technologies in rapidly growing application that become a key to many domains. Digital signal processors [4] such as the TMS320C6x family of Texas Instruments are like fast special-purpose microprocessors with a specialized type of architecture and an instruction set appropriate for signal processing. All the DSP methods are successful because of the combination of both hardware and software. The proposed algorithm will implement practically on our hardware.
12.2 Image Processing
12.2.1 Image Acquisition
MRI is a modern imaging technique that gives a more detailed image than CT scans and X-rays (Figure 12.1). MRI scans uses a large magnet field or radio waves to take images of the brain and other structures of the body. High spatial resolution and excellent soft tissue diagnosis are the advantages of MRI over other medical imaging techniques. In our research, the input MRI images are simulated with T1-weighted contrast and all images are obtained from the Brain web database from McConnell Brain Imaging Center of Montreal Neurological Institute at McGill University.
12.2.2 Image Segmentation Method
Segmentation is the division of an image into regions or categories which correspond to different objects or parts of objects [4]. Every pixel in an image is allocated to one of a number of these categories. It is an essential step in image processing and also it is a critical stage of image. Image segmentation methods can be classified into three categories [5]: Edge-based, region-based, and pixel-based methods. Clustering and edge detection are important tools for a variety of medical applications.
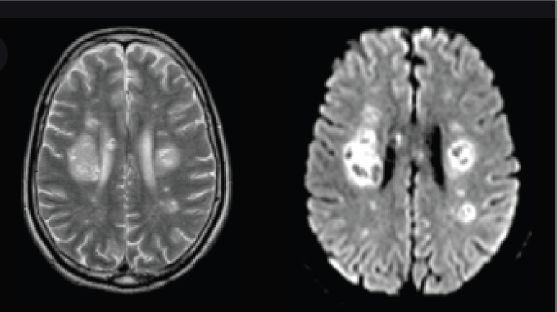
Figure 12.1 Brain MRI image.
12.3 TMS320C6748 DSP Processor
The processor which is going to be used is a TMS320C6748 DSP processor. This is a high-level processor which provides many features. It contains a 5v in power supply which will be given through an adaptor. It contains USB and OTG ports for connecting different devices. This board contains SATA (Serial Advances Technology Attachment) which is an interface for transferring the data between CPU and storage devices. A reset button is also present in this board for resetting the device.
An Ethernet port is also available for connecting to internet. This board provides some user buttons for the performing of different actions. The board is connected to a computer through JTAG. This board comes with a camera sensor through which we can capture images directly from the board. Along with camera sensor, a mic sensor is also present in this board through which we can take input speech signals directly. In accordance with these a fingerprint sensor is also available with this board which is only available in these versions. A VGA (video graphic array) port is also available through which we can connect the output to the display of the computer directly (Figure 12.2).

Figure 12.2 Texas instruments C6748 hardware development kit.
12.4 Code Composer Studio
Code composer studio software is an integrated development environment that supports Texas Instruments microcontrollers and embedded processors. Code composer studio software combines the advantage of eclipse software framework with advanced embedded and debug capabilities. There are some better features available in the Code Composer Studio. They are Program Code Editing, Application Building, and Application Debugging Features. CCS allows ‘C’ and Assembly language program. The Application Building Feature of the CCS is the basic process which is used to create, build, debug, and test the programs. The debugging features of CCS are loading data, FILE I/O, watch window, graphing signals, setting up of break points and usage of probe point. These languages save valuable time in the design process. The C and C++ code can be compiled as well as built to generate the desired file. The project we create keeps track of all the information regarding the input image we provided before preprocessing.
12.5 Morphological Image Segmentation
Thresholds in those algorithms may be decided on manually in step with a priori understanding mechanically through photograph information [6–14]. Algorithms may be in addition divided to facet-primarily based totally ones, region-primarily based totally ones and hybrid ones. Thresholds with inside the facet-primarily based totally algorithms are associated with the facet information. Structures are depicted via way of means of facet points. Common facet detection algorithms such as Canny facet detector and Laplacian facet detector may be categorised to this type. Algorithms try to locate facet pixels even as they get rid of the noise influence.
For example, Canny facet detector uses the brink of gradient value to locate the ability facet pixels and suppresses them through the tactics of the non-maximal suppression and hysterics shareholding. As the operations of algorithms are primarily based totally on pixels, the detected edges consist of discrete pixels and consequently can be incomplete or discontinuous. Hence, it is very important to use post-processing like morphological operation to attach the breaks or get rid of the holes. The technique has the cap potential to phase 3-d photographs with true accuracy; however, the drawback of this technique is the issue of the technique to system the photos of textured blob objects. This can be represented by the block diagram shown in Figure 12.3.
The proposed system has been developed to solve the problem of initial parameters for the level set algorithm such as the initial contour and its centre. Thresholding is a superb way to extract beneficial records encoded into pixels at the same time as minimizing heritage noise. This is performed via making use of a remarks loop to optimize the edge fee earlier than changing the authentic grayscale picture to binary. The concept is to split the picture into parts, the heritage and foreground [6].
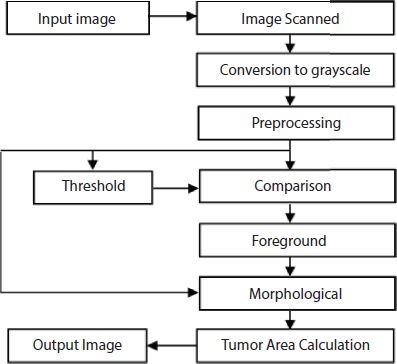
Figure 12.3 Proposed block diagram.
- Select preliminary threshold fee, normally it imply 8-bit fee of the authentic picture.
- Divide the authentic picture into portions:
- Pixel values which can be much less than or same to the edge; heritage (Background)
- Pixel values more than the edge; foreground
- Find the common imply values of the two new images
- Calculate the brand new threshold via averaging the two means.
- If the distinction among the preceding threshold fee and the brand new threshold fee are beneath a distinct limit, the procedure is complete. Otherwise follow the brand new threshold to the authentic picture preserve trying.
The simplest property that pixels in a region can share is intensity. So the natural way to segment those intensities is through thresholding, the separation of light and dark regions. Thresholding creates binary images from grey-level ones by turning all pixels below some threshold to zero and all pixels about that threshold to one. (What you want to do with pixels at the threshold does not matter, as long as you are consistent.) If g(x, y) is a thresholded version of f(x, y) at some global threshold T,
Morphology is nothing but the study of shape and structure of the image. Morphological image processing is a collection of non-linear operations related to the shape or morphology of features in an image. A morphological operation of a binary image creates a new binary image in which the pixel has a non-zero value only if the test is successful at that location in the input image.
12.5.1 Optimization
In order to improve the total execution time on the chip, various optimization techniques were used to check the performance: C code, CCS compiler and cache memory. The TMS320C6748 DSK provides a feature to change the size of cache memory from 0 KB to 256 K Bytes; it can be made by changing the parameters in the General Extension Language (gel file). The number of clock cycles required for each function is calculated and compared by a method called profiling for benchmark. In our methodology of profiling, all of its functions were analyzed and tested to determine the values of clock cycles. The improved performances were after adding the presented optimization technique.
To implement the Image Segmentation using code composer studio, the following steps are to be followed:
- The C compiler accepts C source code and produces assembly language source code.
- The assembler translates assembly language source files into machine language object files. The machine language is based on common object file format (COFF).
- The assembly optimizer allows you to write linear assembly code without being concerned with the pipeline structure or with assigning registers. It assigns registers and uses loop optimization to turn linear assembly into highly parallel assembly that takes advantage of software pipelining.
- The linker combines object files into a single executable object module. As it creates the executable module, it performs relocation and resolves external references. The linker accepts relocatable COFF object files and object libraries as input.
- The archiver allows you to collect a group of files into a single archive file, called a library.
- The archiver also allows you to modify a library by deleting, replacing, extracting, or adding members.
- You can use the library-build utility to build your own customized run-time-support library.
- The run-time-support libraries contain ANSI standard run-time-support functions, compiler-utility functions, floating-point arithmetic functions, and I/O functions that are supported by the C compiler.
- The hex conversion utility converts a COFF object file into TI-Tagged, ASCII-hex, Intel, Motorola-S, or Tektronix object format. You can download the converted file to an EPROM programmer.
- The cross-reference lister uses object files to cross-reference symbols, their definitions, and their references in the linked source files.
- The absolute lister accepts linked object files as input and creates .abs files as output. You assemble the .abs files to produce a listing that contains absolute addresses rather than relative addresses. Without the absolute lister, producing such a listing would be tedious and require many manual operations.
12.6 Results and Discussions
In this section, some of the brain MRI images containing tumor taken for testing our proposed algorithm are shown below.

The results which are obtained by processing the image only by the software platform without involving hardware like DSP Processor is sensitive to noise. But results obtained by involving DSP Processor is not sensitive to noise and it improved the quality of classification (see Table 12.1).
Table 12.1 Performance improvement achieved.
| n° | Using optimization techniques | ||
|---|---|---|---|
| Function | No. of CPU cycles (without optimization) | No. of CPU cycles (with optimization) | |
| 1 | Image conversion | 3924756 | 3131025 |
| 2 | Median filter | 91295273 | 73084236 |
| 3 | Dividing original image | 95877799 | 90436952 |
| 4 | Average means of new images | 3402892 | 2935339 |
| 5 | Calculating new threshold | 98642594 | 92527099 |
| 6 | Comparing new and old threshold values | 98623241 | 91348615 |
| 7 | Obtaining output image after processing | 93635675 | 89908543 |
12.7 Conclusions
This chapter proposed a powerful new approach for segmenting brain tumors and calculating their area using a Thresholding algorithm. The proposed method is tested on scanned MRI images of the human brain, and if there is noise, the non-uniformity is removed using a median filter and also by a modified new threshold value. The results show that the proposed approach to the detection of brain tumors may improve the quality of image segmentation and produce high diagnostic accuracy. Finally, you can make a rough deduction to calculate the shape of the tumor.
References
- 1. Koschan and M. Abidi. “Detection and Classification of Edges in Color Images”, IEEE Signal Processing, 2021, 18, pp. 256-262.
- 2. J. Canny, “A Computational Approach to Edge Detection”, IEEE Trans. Pattern Analysis and Machine Intelligence, 2020, 8, pp. 984-989.
- 3. G.T. Shrivakshan, Dr. C. Chandrasekar, “A Comparison of various Edge Detection Techniques used in Image Processing”, IJCSI International Journal of Computer Science Issues, 2012, Vol. 9, Issue 5, pp. 567-573.
- 4. WenshuoGao, et al., “An improved Sobel edge detection”, Computer Science and Information Technology (ICCSIT), 2010, 3rd IEEE International Conference, China, Volume 5, pp. 67-71.
- 5. Chen, L., “Laplacian Embedded Regression for Scalable Manifold Regularization”, IEEE Transactions on Neural Networks and Learning Systems, 2015, Vol. 23, pp. 902-915.
- 6. L. Chen, C. L. P. Chen and M. Lu, “A multiple-kernel fuzzy C-means algorithm for image segmentation,” 2011, Vol. 41, pp. 1263-1274.
- 7. Z. Chen, H. Yang, G. Zhang, and W. Shi, “Improvement and application of medical image segmentation method based on FCM,” 2011, Vol. 105, pp. 435-439.
- 8. B. Sharmila, N. Karalan, D. Nedumaran, “Image Processing on DSP Environment Using OpenCV,” IJARCSSE. Image Process., 2015, Vol 5, pp. 489-493.
- 9. N. Kumar, S. Mahapatro, S. Pal, “Implementation of Color Image Enhancement using DCT on TMS320C6713,” IJECSE. Image Process., 2001, Vol. 1, no. 3, pp. 1244-1253.
- 10. D. Zung, L.Pham, “Spatial models for fuzzy clustering”, in Computer vision and Image Understanding, 2001, Vol. 84, pp. 285-297, Elsevier Science (USA).
- 11. K. Honda, H. Ichihashi, S. Miyamoto, Algorithms for Fuzzy Clustering Methods in c-Means Clustering with Applications, Springer-Verlag, Berlin Heidelberg, 2008, 23, pp. 56-65.
- 12. R.B. Dubey, M. Hanmandlu, Shantaram Vasikarla, “Evaluation of Three Methods for MRI Brain Tumor segmentation”, IEEE, doi: 10.1109/ITNG.2011.92,2011.
- 13. Badiganti P.K., Peddirsi S., Rupesh A.T.J., Tripathi S.L. (2022) Design and Implementation of Smart Healthcare Monitoring System Using FPGA. In: Rawat S., Kumar A., Kumar P., Anguera J. (eds.) Proceedings of First International Conference on Computational Electronics for Wireless Communications. Lecture Notes in Networks and Systems, vol. 329. Springer, Singapore. https://doi.org/10.1007/978-981-16-6246-1_18
- 14. Vadla P.K., Naga Pawan Y.V.R., Kolla B.P., Tripathi S.L. (2021) Accurate Detection and Diagnosis of Breast Cancer Using Scaled Conjugate Gradient Back Propagation Algorithm and Advanced Deep Learning Techniques. In: Sengodan T., Murugappan M., Misra S. (eds.) Advances in Electrical and Computer Technologies. Lecture Notes in Electrical Engineering, vol 711. Springer, Singapore. https://doi.org/10.1007/978-981-15-9019-1_9
Notes
- * Corresponding author: [email protected]
- † Corresponding author: [email protected]
