8
Anti-Theft Technology of Museum Cultural Relics Using RFID Technology
B. Ramesh Reddy1, K. Bhargav Manikanta1, P.V.V.N.S. Jaya Sai1, R. Mohan Chandra1, M. Greeshma Vyas1 and K. Girija Sravani2*
1 Department of Electronics and Communication Engineering, LBR College of Engineering, Mylavaram, Krishna District, Andhra Pradesh, India
2 Department of Electronics and Communication Engineering, KL University, Green Field, Vaddeswaram, Guntur, Andhra Pradesh, India
Abstract
As progress progressed, the galleries showed a growing number of social relics, the number of visitors expanded, and definitely, valuable exhibits were taken by an expanding number of hoodlums. Customary techniques to prevent robbery cannot stop them. This examination gives a gallery a hostile to burglary strategy dependent on RFID innovation, which utilizes uninvolved RFID perusers/journalists to evaluate whether social resources are inside the protected reach. The RFID labels are attached to the social fortunes, and when they are taken out, they leave the powerful RFID ID range, alarming the framework and setting off the counter-burglary system. The suggested against robbery strategy checking is more prompt and has a higher security factor, and it is anything but restricted by the constraints of a customary infrared enemy of burglary, entryway attractive discovery, and different strategies. At long last, this exertion involves equipment circuit plans, programming advancement, and a progression of testing to get the necessary outcomes.
Keywords: RFID, reader, RFID tag
8.1 Introduction
As individuals’ social life has improved, craftsmanship displays and galleries have become a major attraction for explorers from one side of the planet to the other. By the start of 2019, China’s total number of galleries had risen to 5,136. Exhibition halls have consistently viewed not-forprofits and public advantage as a social accord. Numerous administrations command that historical centers be free to general society. In 2018, the National Museum introduced more than 20,000 shows, drawing in around 1 billion guests and urging individuals to make a habit of visiting historical centers. Subsequently, the historical centers social fortunes have attracted greater levels of criminality. Burglary of curios is something that nobody likes to see. The historical center will plan the scope of social relics security strategies to guarantee the exhibition hall’s wellbeing. In any case, burglary is boundless even in this climate.
The criminal alert is the most broadly utilized enemy of burglary innovation, with applications in a wide scope of businesses. Against-burglary alert frameworks introduced in monetary establishments, like banks, ATMs, and different areas can help to lessen the number of burglaries. Hostile-toburglary frameworks can recognize gatecrashers, yet the main part of data in military areas should remain classified. In high-traffic regions, for example, train stations and schools, face acknowledgment innovation might be utilized to advise guilty parties and suspected individuals on the boycott. This fruitful strategy can limit the quantity of savage and criminal occurrences to secure individuals’ lives and property, and thief caution gadgets are broadly used locally to ensure inhabitants’ property and are transferred to the police as evidence. But every system has its limitations where there are situations they can network. So to overcome these problems our paper mainly focuses on Radio Frequency Identification Technology.
8.2 Literature Survey
The Internet of Things is an example of rapidly growing technology in the modern world and new technologies are emerging day by day with improving functionalities. The basic idea behind this spreading technology like RFID sensors, actuators, is to create an intercommunication channel between those technologies. This technology plays an important role in both working and domestic fields. Some of the technologies developed for domestic fields are e-health, enhanced learning, etc., and on the working field the technologies such as transportation, automation, industrial management, etc. [1].
The suggestion of Radio Frequency Identification innovation expresses that there are a few different ways of execution to ensure the things and trimmings in arcades or galleries, yet every one of the advances has its limits. A portion of the model is a glass breaking locator which demonstrates the sign if and just if the sensor is in the scope of following the sound, this is the constraint of glass breaking identifier. Here the authors S.B.A. Hamid, A.D. Rosli, W. Ismail, and A-Z. Rosli address the idea of RFID innovation for following the exhibition hall things in Turkey. This idea is made by knowing what RFID can do [2].
RFID (Radio Frequency Identification) is an information stockpiling and recovery strategy that gives remarkable IDs to things. It accompanies both an RFID peruser and an RFID tag. An RFID peruser is a gadget that communicates radio waves and gets signals from RFID labels and has at least one receiving wire. The RFID Tag has an interesting ID number that contains all data about the predetermined article. The Anti-burglary System comprises an RFID peruser, an RFID tag, and an interface gadget. After interfacing the Tag with the chosen object, it is anything but an alarm sign to the RFID peruser gadget [3].
The R. Tesorieo provides a system that is connected to both active and passive RFID and may be evaluated at art museums using mobile devices. The individual benefited from this concept since he could access necessary information without having to physically look for it [4].
The creator Geeth Jitendra presents a method of securing social resources by using a vehicle immobilizer, which has the advantage of being impervious to programmer assaults. A sending unit, a getting unit, and a keen vehicle interface make up the fundamental structure of the immobilizing framework. The information received will be placed in the vehicle, while the transmitter will be kept with the proprietor, ensuring that the transmitter and beneficiary have a functioning correspondence channel until they are within 200 meters of one another. As a result of its high pace of insurance against hacking assaults, this framework beats other systems. Others are powerless against digital assaults [5–12].
8.3 Software Implementation
The Arduino is programmed in such a way that it can communicate with the RFID reader, IR Sensor, Temperature Sensor. Arduino is flexible; it can be used to program in different languages. They all communicate with each other by sending the radio signal from the transceiver of the RFID reader through the antenna, and when the RFID tags come in the range of the radio signal, the tag uses this signal as a power to activate the Transponder in the microchip of RFID tags. This RFID tag sends the information about the cultural relic just like a unique id to the Tx present in the RFID reader. So this information can be accessed by the computer whenever needed.
8.4 Components
8.4.1 Arduino UNO
The Arduino Uno is a well-known open-source microcontroller board based on the Microchip ATmega328P microcontroller. Arduino.cc created the Arduino Uno. The board is entirely composed of analog and digital pins, which are then assigned to input or output pins. These digital and analog pins can then be connected to a variety of electronic devices, boards, and circuits. The Arduino Uno has 14 digital I/O pins as well as 6 analog I/O pins (Figure 8.1).
8.4.2 EM18 Reader Module
The EM18 Reader Module is a Radio Frequency Identification (RFID) Reader that is utilized to peruse RFID labels with frequencies of 125 kHz. The EM18 module reads the RFID labels and sends the remarkable ID to the PC or microcontroller utilizing diverse correspondence methods like UART and so forth. It peruses the information which contains an ID which is 12 bytes. It is not difficult to utilize and of minimal expense, low force utilization. The interfacing is finished with Microcontrollers utilizing UART and with PC utilizing RS232 convertor (Figure 8.2).

Figure 8.1 The top view of the Arduino UNO

Figure 8.2 The topview EM18 reader modules.
8.4.3 RFID Tag
The RFID tags are used to identify the objects, persons, etc. It contains the unique ID to identify the object and it senses the presence of the object in the museum in this project. The RFID tag has a frequency of 125KHZ and contains a 32 bit unique ID (Figure 8.3).
8.4.4 LCD Display
The LCD used here is a 16x2 display which is a yellow and green backlight ASCII Alphanumeric Character Display. 16x2 display means 16 characters by 2-line display. It has 16 pins and can operate in 4-bit mode with only four data lines or 8-bit mode with all eight data lines (Figure 8.4).

Figure 8.3 The proposed RFID tag.

Figure 8.4 The measurment LCD display.
8.4.5 Sensors
8.4.5.1 Fire Sensor
Fire sensors are utilized in autos, clinical gadgets, PCs, cooking apparatuses, and different sorts of hardware. They measure the temperature of an item or climate where it is available by coming into contact with the article or by identifying infrared energy transmitted by the item just as the environmental factors (Figure 8.5).
8.4.5.2 IR Sensor
Infrared radiation was discovered in 1800 by cosmologist William Herchel. It is a piece of electronic gear that actions and identifies infrared radiation in its current circumstance. Infrared sensors are characterized into two sorts: dynamic and aloof. Detached sensors recognize infrared radiation but do not discharge it, so they are utilized in this task. These sensors are normally utilized in moving-based location applications. At the point when a moving article producing infrared radiation enters the detecting scope of the finder, the distinction in IR levels between the two pyro-electric components is estimated. The sensor then, at that point, speaks with the PC through an electronic sign (Figure 8.6).

Figure 8.5 The proposed fire sensor.

Figure 8.6 The proposed IR sensor.
8.4.6 Relay
A relay is an electrically controlled switch. It is made up of a set of input terminals for single or multiple control signals, as well as a set of operating contacting terminals. It works on the principle of electromagnetic induction. Relays control one electrical circuit by opening and closing contacts with another electrical circuit (Figure 8.7).

Figure 8.7 The proposed relay.
8.5 Working Principle
The above block diagram shows the proposed model of our project. The model consists of Arduino UNO, EM-18 Reader Module, RFID Tag, LCD, Relay as its major components. A few sensors like fire Sensors, IR sensors are connected for the additional requirement.
8.5.1 Working Principle
The principal equipment segments incorporate Arduino, Radio Frequency Identification, LCD, Infrared, and temperature Sensors. The data from the framework is gotten by Arduino. What’s more, it is customized in such a way. Radio Frequency Identification is an information stockpiling and recovery innovation that gives a personality code to screen objects. By and large, it is comprised of an RFID peruser, a radio wire, and an RFID tag. The unmistakably recognizable proof code is saved in the information base as a personality code. While, contingent upon the particular article, other data about the checked item is additionally put away on the RFID tag.
To screen and control the RFID per user information, a comparing application is introduced on the PC. The electronic tag is versatile and can be introduced on a surface without endangering the fundamental attributes or capacity of the curio. It speaks with the RFID scanner through remote innovation. The perusing scope of an RFID peruser can be sensibly stretched out according to the force size and application program. At standard stretches, the data from each electronic tag is perused to decide if the electronic tag is inside the reach (Figure 8.8).

Figure 8.8 Block diagram of the proposed system.
An RFID peruser’s two principal parts are a regulator unit and a radio recurrence handset module. RFID labels are made out of a chip and a coupling component, and each tag has an extraordinary code that is appended to the outside of the object and can be distinguished. The tag has two memory regions, one for putting away the ID and the other for putting away client data information, which can be changed and erased.
8.6 Results and Discussions
To obtain the desired output, all of the components are connected in this manner. Dumping the codes into the respective Arduino, which will then perform their operations and communicate with one another. We use Assembly language to dump code into Arduino.
This Image shows the RFID tag on the RFID reader module, which detects the card in the range or not. When the RFID tag in the range the blue led will glow and shows the safe message on the LCD screen as shown in Figure 8.9(a).
When the Tag is not in the range the blue led will be in OFF condition and it does not show in the LCD as shown in Figure 8.9(b).

Figure 8.9 The measurment results.

Figure 8.9(a) The measurment results.

Figure 8.9(b) The measurment results.
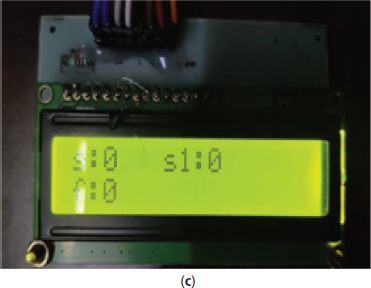
Figure 8.9(c) The measurment results.

Figure 8.9(d) The measurment results.
Here we declare the two Infrared sensors as’s’ and ‘s1’. When the object is in the IR range it shows ‘0’ in the display and when the object is not in the range it shows ‘1’ in the display as shown in Figure 8.9(c).
Here we declared the fire sensor as ‘F’. When fire or smoke is not detected it shows ‘0’ in the display and when the fire is detected the message ‘fire detected’ as shown in Figure 8.9(d).
8.7 Conclusions
This chapter proposes an alternative way to deal with galleries hostile to robbery plans dependent on the Internet of Things (IoT) innovation, which decides if social relics are inside range utilizing Passive Radio Frequency Identification perusers or journalists. On the off chance that an interloper moves toward the item and endeavors to burglarize it, the RFID tag and RFID peruser will impart, and the signal will sound, and information will be transferred to the IoT stage.
So by using this technology we can reduce thefts in a museum by identifying the abnormal in the RF field. In an existing system, we have an Infrared based security system to identify the theft.
So this technology was further extended by adding GPS Module to the object and to track the location of the object. So if the thief breaks all the above-mentioned safety measures and steals the object he or she can be found by tracking the location using the GPS Module.
References
- 1. N.A. Çayirezmez, H.M. Aygün and L. Boz, “Idea of RFID innovation for following exhibition hall objects in Turkey”, Proc. Computerized Heritage Int. Congr. 2013, pp. 315-318.
- 2. S. B. A. Hamid, A.D. Rosli, W. Ismail, and A. Z. Rosli, “Plan and execution of RFID-based enemy of robbery framework”, Proc. IEEE Int. Conf. Control Syst. Comput. Eng. (ICCSCE), 2012, pp. 452-457.
- 3. V. Lakafosis, A. Rida, R. Vyas, L. Yang, S. Nikolaou and M. M. Tentzeris, “Progress towards the principal remote sensor organizations of based RFIDempowered sensor labels”, Proc. IEEE, 2010, Vol. 98, no. 9, pp. 1601-1609.
- 4. Z. Meng and Z. Li, “RFID tag as a sensor—A survey on the imaginative plans and applications”, Meas. Sci. Fire Up., vol. 16, no. 6, pp. 305-315, Dec. 2016.
- 5. E. Valero, A. Adán and C. Cerrada, “Advancement of RFID applications in development: A writing survey”, Sensors Journal, 2015, Vol. 15, no. 7, pp. 15988-16008.
- 6. F. Sahba, “Historical center computerization with RFID”, Proc. World Automat. Congr. (WAC), 2014, pp. 19-22.
- 7. X. B. Yang, “On the counter robbery innovation of present day exhibition halls”, Mod. Phys., vol. 23, no. 5, pp. 43-46, Oct. 2011.
- 8. Y. C. Shen and S. Q. Shen, “Radiofrequency recognizable proof innovation and its improvement status”, Electron. Technol. Appl. 1999, Vol. 1, pp. 2-3.
- 9. J. Shi, “Imaginative use of significant distance RFID in the security field”, China Public Saf. (Complete Ed.), 2006, Vol. 5, pp. 71-74.
- 10. Z. G. Feng, “Analysis of the theory of wisdom museum”, Museum Res. 2019, Vol. 1, pp. 19-25.
- 11. W. Xiaohua, “Exploration on enemy of robbery issue in RFID library”, China Electron. Trade (RFID Technol. Appl.), 2009, Vol. 4, no. 3, pp. 35-37.
- 12. X. Liu, B. Xiao, K. Li, X. Liu, J. Wu, X. Xie, et al., “RFID assessment with blocker labels”, IEEE/ACM Trans. Netw. 2017, Vol. 25, no. 1, pp. 224-237.
Note
- * Corresponding author: [email protected]
