Routing Information Protocol Version 2 (RIP-2)
RIP version 2 (RIP-2) is an updated version of the original Routing Information Protocol. There are a few additional features in RIP-2 that make it a far more appropriate routing choice for many network administrators, especially as we continue with the problem of the IP addressing shortage. The first of these new features is the ability to add information gleaned from an Exterior Gateway Protocol (EGP). See the section, “Exterior Gateway Protocol,” in Chapter 3, “Introduction to Border Routing Protocols,” for more information regarding the data carried from one router to another.
Essentially, RIP-2 packets contain a backpack into which data from an EGP can be dropped and carried from router to router. Take another look at the example network in Figure 1.10. In this image it’s shown isolated, yet somewhere along the way this network talks to the outside world through the Internet.
Let’s say that there is a straight line going up from router Phys that leads to the Internet Service Provider (ISP) for this campus’s entire network, as shown in Figure 1.11.The example network now magically uses RIP-2 instead of RIP-1.
Figure 1.11. The example network’s connection to the outside world.
This line leads to a router running a different protocol from your network, which I’ll call router zero. Router zero is passed information from another router and includes that information as a little add-on, as shown in Figure 1.12. Much more detail about what might be carried by EGP is provided in Chapter 3.
Figure 1.12. Incoming EGP information.

As this data reaches router Phys, RIP-2 is able to accept it and incorporate it into its next 30-second update, as shown in Figure 1.13.
Figure 1.13. RIP-2 carries EGP data piggyback with its own data.
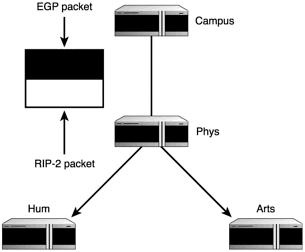
This combined data is then sent to Hum and Arts, and so on. The nice thing about this capability is that it decreases the need for direct administrator intervention; however, it also creates a new problem.
Introducing the ability to obtain and pass information gained from outside sources opens the door for someone to feed the routers false information. Having anticipated this dilemma, another addition to RIP-2 allows for a simple password authentication scheme. You can set your router to accept updates only from those to which you have given the password.
The administrators in our example network trust one another. Rather than agreeing upon one password for all of their routers, they each choose one and notify the administrator of their neighbor routers in writing. Please note that email is most definitely not a secure alternative unless you use encryption such as Pretty Good Privacy (PGP) or Gnome Pretty Good Privacy (GPGP). The administrators then add the American Standard Code for Information Interchange (ASCII) passwords to their configuration files for each of the neighbors. For example, router Phys would have passwords for Campus, Hum, and Arts. If there are neighbors that the administrators do not want to accept updated information from, then the administrator simply does not give out the password to that neighbor’s administrator. Data can still pass from router to router; that function is not hampered. That particular neighbor just cannot input data into the routing tables.
Another interesting addition that makes up RIP-2 is the ability to advertise alternative routes that use other protocols to other RIP-2 routers. To utilize this feature, RIP-2 must be running on the same router with the other protocol. Let’s look at the sample network again. Routers Chem and Math are heavily subnetworked not only for their individual departments, but for groups inside the departments as well. Therefore, we decide that their networking needs require a different routing protocol than RIP-2.Which protocol we choose specifically doesn’t matter for the moment.
If RIP-1 were being used, then Chem and Math wouldn’t be able to talk to the others anymore. Sure, data could pass from their neighbors through them, but Chem and Math could not send updates to the other routers about the networks past them. RIP-2 allows for these updates to happen regardless of protocol. Math’s administrator then adds a new network behind this router. The administrator adds the information about the new network to Math’s routing tables.
Math has no problem informing Chem about the change. Fortunately, even though Chem and Math are using some unknown, as yet not discussed, protocol, Arts, Abacus, and Ag are all using RIP-2. The updates pass through just fine, and eventually all of the routers in the network and beyond find out how to get to this new network.
Finally, the new capability that brings RIP-2 into the next Internet age is its ability to carry subnet mask information. In fact this was the primary reason for building a new version of RIP-1 in the first place. One solution to the IP addressing shortage is the use of variable subnet masks rather than using a single mask for an entire network. The original RIP-1 was unable to comprehend this type of setup.
As you can see, RIP-2 is a more sophisticated version of RIP-1 that handles updating information slightly better and also speaks the language of the modern Internet. However, this is still not a protocol for a huge set of networks. It really is meant for more limited use.
The program used to implement RIP-2 under Linux is gated or zebra. Both of these daemons can handle more than one protocol at once. See Chapter 5 for more information on where to find these programs and how they work.
