Classless IPv4 Addressing
While many of the tenets of IP v4 addressing apply here, such as there being 32 bits in an address divided into four bytes, separated by dots, the new concept you need to become familiar with is Classless Interdomain Routing (CIDR). This subset of IP v4 adds such words to our vocabularies as supernetting and Variable Length Subnet Masks (VLSM). So, buckle your seatbelts—it’s going to be a fun ride.
Differences Between Classful and Classless IPv4 Addressing
There is no class A, B, and so on in CIDR IP v4. No, this does not cause chaos. Instead, all xxx.xxx.xxx.xxx (decimal) combinations come in turn with a bit mask (also called a prefix length). While this item is utilized in IP v4 as a shortcut instead of typing out the whole netmask, we chose to cover the math behind it in the following section,“Classless IP v4 Math,” because calculating these values is an absolutely necessary skill. Everything has limitations. Classless IP v4 does not allow you unfettered ability to assign address blocks as you see fit. We’ll get more into this when we actually start doing the math in the next section.
In Classful (original) IP v4, there are 32 bits (8 bits per byte x 4 bytes) in an address, and we use a subnet structure similar to what’s shown in Figure 4.2. All subnets are the same size and are contained within a single larger network. While handy, this is a pretty rigid framework that leads to much loss of host addresses and prevents any further subdivisions.
Figure 4.2. Subnetting from the Classful IP v4 perspective.

Classless IPv4 Math
As was said before, almost all of CIDR works properly because of bit mask or prefix length assignments. A bit mask is written in the format /xx, where the x’s merely represent digits. In IP v4, only /8, /16, or /24 bit masks exist. These values correspond to the number of bits used for the network portion of the IP address. So, for a class A, you have nnnnnnnn.hhhhhhhh.hhhhhhhh.hhhhhhhh, or /8. For class B, you have nnnnnnnn.nnnnnnnn.hhhhhhhh.hhhhhhhh or /16, and for C you have nnnnnnnn.nnnnnnnn.nnnnnnnn.hhhhhhhh or /24.
Classless IP v4 tosses the whole address class thing out the window. However, as you were warned, there are still limits on what you can do. The number of addresses you give to a network in this system must be a power of two: 2, 4, 8, 16, 32, 64, 128, 256, 512, and so on. Notice that this didn’t say the bit mask has to be a power of two. We’re talking about addresses right now.
So, how do you figure out what bit mask to use for a particular host range? Once again, let’s look at the IP address template xxxxxxxx.xxxxxxxx.xxxxxxxx.xxxxxxxx. The bit mask (network bits) and host bits must add up to 32, as there are 32 bits in the addressing scheme. Let’s say that for our campus setup we need an address block of 4096. It would take 12 bits to express 4096 unique addresses because 2 to the 12th power is 4096. So, that’s 12 host bits, which leaves the remaining 20 for network bits. So this address ends in a /20. It doesn’t matter what the network bits are. In CIDR, machines do not assume anything from the network bits.We’ll keep repeating this because it is one of the biggest changes you’ll have to get used to.
Though we can’t entirely get rid of the netmasks, it’s pretty easy to make them. Let’s go back to our /20 network, which looks like nnnnnnnn.nnnnnnnn.nnnnhhhh.hhhhhhhh.We’re using all of the network bits in the first and second bytes so they both have a decimal value of 255.The third bytes only has the first four network bits in use, and their positions add up to 128 + 64 + 32 + 16, or 240. The last position is entirely host bits, so it’s 0. That gives us a netmask of 255.255.240.0. Table 4.6 gives the bit mask and netmask particulars for a range of CIDR possibilities.
| Bit Mask | Netmask | Host Addresses |
|---|---|---|
| /17 | 255.255.128.0 | 32,766 |
| /18 | 255.255.192.0 | 16,382 |
| /19 | 255.255.224.0 | 8,190 |
| /20 | 255.255.240.0 | 4,094 |
| /21 | 255.255.248.0 | 2,046 |
| /22 | 255.255.252.0 | 1,022 |
| /23 | 255.255.254.0 | 510 |
| /24 | 255.255.255.0 | 254 |
| /25 | 255.255.255.128 | 126 |
| /26 | 255.255.255.192 | 62 |
| /27 | 255.255.255.224 | 30 |
| /28 | 255.255.255.240 | 14 |
| /29 | 255.255.255.248 | 6 |
Notice that the host addresses are all a power of 2 minus 2. Because a network still needs a network address and a broadcast address, this accurately represents how many hosts you get per piece.
Applying Classless IPv4 Addressing Across Subnets
The concept of subnets might not seem to make a lot of sense when we start talking about classless networking, but it’s still there. After all, what if we’re assigned an address chunk and need to break it down into smaller pieces? Further still, maybe we don’t want all of our subnets to be exactly the same size. Here’s where we get into those Variable Length Subnet Masks (VLSMs).
In VLSM, you can apply multiple subnet masks to the same overall network to create subnets of different sizes. We do this in a hierarchal way.We create a collection of same-size larger subnets, and then where we need smaller networks, we subnet the subnet.We can keep breaking these down into smaller networks as far as we need to.
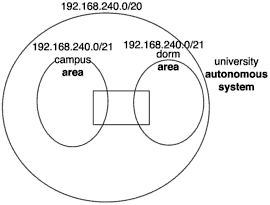
Here is where the extended-network-prefix comes in. Let’s go back to that /20 network we discussed in the previous section. The /20 is the bit mask, as we already discussed. So the network bits and bytes are structured like nnnnnnnn.nnnnnnnn.nnnnhhhh.hhhhhhhh. Now that we have such a large address space—capable of containing 4,094 hosts—we need to break it down further. In the case of our example network, we have a huge autonomous system for the entire university that contains two smaller but still huge routing areas, one for the campus and one for the dorms.
So first we want to divide our 192.168.240.0/20 network into two large subnets, one for each. As you know, 2 is 2 to the power of 1, which means that we only need a single bit to handle this subnetting.We now need to use a new series of symbols to help keep everything clear in our address bits. The n stands not just for network, but for the main network—the bit mask portion of the network.We’ll now add an e for the extended-network-prefix to the mix. So we now have nnnnnnnn.nnnnnnnn.nnnnehhh.hhhhhhhh.
We just need the network addresses for the subnets now. This is actually easier than you’d think. The first network is 192.168.240.0/21, and the second is 192.168.248.0/21, as shown in Figure 4.3.
Figure 4.3. The beginning of our hierarchal Classless IP v4 networking scheme.
As you already know from the previous chapters, each building has its own router because it has its own network. Therefore, we need to divide each of the subnets above further into subnets for each building. Let’s start with the campus area. There are seven different buildings defined here.We might add more some day. To break on a bit boundary, we want a power of two. The two closest and bigger than seven powers of two are eight and 16, and while it would be nice to break 192.168.240.0/21 down into 16 subnets to leave plenty of room to maneuver, this would limit us to just 126 machines per network (/25) rather than 254 (/24). How do we know this? The network bits for 192.168.240.0/21 are nnnnnnnn.nnnnnnnn.nnnnehhh.hhhhhhhh, and if an f is used to represent this subnet, then there are two choices:
Eight subnets will require three more bits and give me nnnnnnnn.nnnnnnnn.nnnnefff.hhhhhhhh or /24.
Sixteen subnets will require four more bits—including those used for the eight subnet option—and give me nnnnnnnn.nnnnnnnn.nnnnefff.fhhhhhhh or /25.
Because eight has been chosen, the first of the eight subnets is 192.168.241.0/24 (nnnnnnnn.nnnnnnnn.nnnne001.hhhhhhhh)—where we already know that the third bit’s nnnne is 240. The full list of eight subnets is detailed in Table 4.7.
| Subnet | Bit-wise | Network |
|---|---|---|
| Ag | .nnnne000.hhhhhhhh | 192.168.240.0/24 |
| Eng | .nnnne001.hhhhhhhh | 192.168.241.0/24 |
| Phys | .nnnne010.hhhhhhhh | 192.168.242.0/24 |
| Hum | .nnnne011.hhhhhhhh | 192.168.243.0/24 |
| Arts | .nnnne100.hhhhhhhh | 192.168.244.0/24 |
| Chem | .nnnne101.hhhhhhhh | 192.168.245.0/24 |
| Math | .nnnne110.hhhhhhhh | 192.168.246.0/24 |
| spare | .nnnne111.hhhhhhh | 192.168.247.0/24 |
In each subnet, you get 254 addresses—if this seems like a class C to you, it is; a class C is just a /24 network. From here, you can actually subnet further for different departments or whatever suits your needs.
On the dorm side there are six buildings. This means once again that if you want one subnet per building, the closest you can get is eight. The dorm network is 192.168.248.0/21. Its eight subnets are calculated exactly the same way, and the results are given in Table 4.8.
| Subnet | Bit-wise | Network |
|---|---|---|
| Runk | .nnnne000.hhhhhhhh | 192.168.248.0/24 |
| East | .nnnne001.hhhhhhhh | 192.168.249.0/24 |
| Trud | .nnnne010.hhhhhhhh | 192.168.250.0/24 |
| Wash | .nnnne011.hhhhhhhh | 192.168.251.0/24 |
| Wall | .nnnne100.hhhhhhhh | 192.168.252.0/24 |
| Poin | .nnnne101.hhhhhhhh | 192.168.253.0/24 |
| spare | .nnnne110.hhhhhhhh | 192.168.254.0/24 |
| spare | .nnnne111.hhhhhhhh | 192.168.255.0/24 |
In this case, you might decide to have a subnet for each floor in the dorm or not make any subnetworks at all. Figure 4.4 shows you what our new network-addressing scheme looks like.
Figure 4.4. The current hierarchal Classless IP v4 networking scheme.

Classless IPv4 Routing Issues
It might sound like Classless IP v4 puts a huge burden on the Internet’s routers. Even worse, it could explode the routing tables into an unmanageable size that slows down all Internet traffic. Fortunately this is not the case. Not only does Classless IP v4 allow you to create subnets of subnets of subnets, it also allows you to hide the layers from the outside world—if you plan your network correctly. See Chapter 7, “Planning Router Layout and Function,” for further information.
A well-planned VLSM setup includes route aggregation, a concept that allows you to hide subnetting from the outside world. Let me break down theVLSM subnets created in the previous section,“Applying Classless IP v4 Addressing Across Subnets,” to demonstrate this concept. Each of the subnet layers was mathematically derived from its parent layer. We started with the overall network 192.168.240.0/20. The 20-bit mask translates to nnnnnnnn.nnnnnnnn.nnnnhhhh.hhhhhhhh, where n is a network bit and h is a host bit. This means that you have access to the address range 192.168.240.0 through 192.168.255.255.
The two subnets within this network are 192.168.240.0/21 and 192.168.248.0/21. Both of these network addresses are within the main network’s address range. Therefore, no matter which subnet the traffic ultimately needs to go to, it first has to go to network 192.168.240.0/20 according to how the IP v6 routing works. No router outside the main university router (prime) needs to know that there are any subnets at all.
Our major subnets have their own address ranges. The campus subnet, 192.168.240.0/21, has the bit mask nnnnnnnn.nnnnnnnn.nnnnehhh.hhhhhhhh. This gives it the address range 192.168.240.0 through 192.168.247.255. The dorm subnet, on the other hand, is 192.168.248.0/21 and gets 192.168.248.0 through 192.168.255.255. Take a look back at Tables 4.7 and 4.8. Every network address listed there falls within one of these two major subnets’ available address ranges. Therefore, every network address in the campus and dorm buildings can be sent just to the main router, then to just the campus or dorm router, then to the appropriate building, and then directly to the correct machine.
In each case, only the router above the subnet layer needs to know that there are subnets involved at all. This is a good example of route aggregation, a term mentioned earlier. It is also the key to CIDR success.The more routing information that we can keep hidden at local levels, the smaller the overall routing tables need to be.
Routers under Classless IP v4 must carry information that IP v4 routers simply would not understand.While Classful IP v4 requires the netmask, Classless IP v4 needs the bit mask. The technique the routers use from that point is called longest match. The router looks at the address the information is trying to get to—let’s say 192.168.250.52—and looks for the entry in its routing table that is closest to this number. The best it’s going to find in a main routing table in this case is 192.168— remember that our parent network (the supernet) is 192.168.240.0/20.
Longest match isn’t well demonstrated at the beginning. Rather than sending the data to 192.168.0.0, the router trying to send the data to 192.168.250.52 will have to look up 192.168.240.0/20 in the routing tables unless all of 192.168.0.0 is owned by a single ISP that then hands out parts of the addressing to others. Let’s say that this is the case.The packet meant for 192.168.250.52 gets sent to the ISP that owns 192.168.0.0.
When the packet arrives at the ISP’s routers, they don’t see a longest match for 192.168.250.x. They do have 192.168.240.0/20 in their routing tables, however, so off the packet goes to our router Prime. Prime doesn’t have a longest match for 192.168.250.x either. However, it has in its routing tables that the network 192.168.248.0/21 exists, so now the packet is sent to router East.
Now, when router East looks for a longest match for 192.168.250.x, it finds one. That’s the network range assigned to the Trud router. The packet is sent to Trud, which immediately knows where to send data to 192.168.250.52. Once again, not only does this example illustrate the longest match concept, but it also shows just how much routing table information the routers outside of our campus don’t need. As long as they can get the data to router Prime, it can do the rest.
What About Hosts That Don’t Understand CIDR?Not all machines can handle CIDR out of the box. This includes Linux. We’ll get into the route command in depth in Chapter 6, “Inside The Commands,” but you might already be familiar with the data route requires. This command wants to know the network address, gateway address, IP address, and netmask. It has no place for a bit mask. Therefore, it assumes a class for every IP address. This just won’t do if you’re using Classless IP v4. In fact, take a look at the other commands as well—and the kernel. You’ll run into the same problem throughout. The first Linux kernel series to have built-in Classless IP v4 support is 2.2.x. However, the Classless IP v4 module in this case is still labeled experimental. If you must have this host able to understand Classless IP v4, recompile the kernel with the Classless IP v4 modules attached and then go to http://www.tazenda.demon.co.uk/phil/net-tools/ to download the latest version of the nettools package. This Tarball contains all of the basic utilities you’ll need for networking with Linux, and versions 1.52 and later add support for Classless IP v4. Be sure to read all README files before installing these programs. |
