Internet Information Services Security with Windows 2000
Recall from Chapter 3, "Integrating IIS with Windows 2000 Security," that Internet Information Services utilizes a four-step process in controlling Web site access. That chapter discussed the two steps based on Windows 2000 security features.
This chapter focuses on the other two steps, which are provided by Internet Information Services:
Checks for specific IP restrictions
Verifies Web site permissions
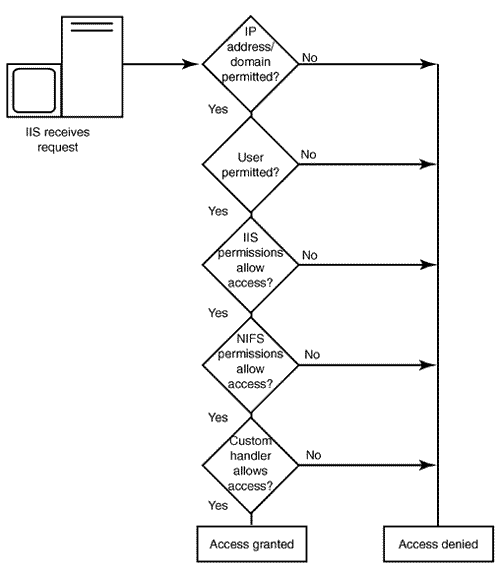
Figure 4.1 shows a graphical representation of the Internet Information Services security process.[1]
[1] Note that in Figure 4.1, there are five steps instead of four. In addition to the standard steps, IIS gives you the flexibility of creating your own custom security handler.
Figure 4.1. The first two steps in the IIS security process are performed by Internet Information Services.
In addition to discussing this process, this chapter devotes considerable time to discussing access control. Access control is the method by which Internet Information Services identifies the user connecting to the Web or FTP service. After the user is identified and verified, IIS can leverage Windows 2000 security features for both the account permissions and NTFS permissions. These Windows 2000 security features were discussed in the previous chapter. This chapter focuses on the methodology of identifying the account and the characteristics of each account.
