Chapter 4: Monitoring Windows
In This Chapter
![]() Watching Windows with the built-in tools
Watching Windows with the built-in tools
![]() Finding and fixing problems
Finding and fixing problems
![]() Viewing connections
Viewing connections
![]() Working with the Event Viewer
Working with the Event Viewer
![]() Tracking reliability over time
Tracking reliability over time
Windows 8.1 ships with a tremendous array of tools designed to help you look at your system and warn you if something’s wrong.
Microsoft dropped the WEI in Windows 8.1. One of its biggest motivations: The original Surface Pro — Microsoft’s flagship Windows machine — scored a meager 5.9 on a scale from 1 to 9.9, which put it below just about any laptop or desktop you could mention. For years I used a slapped-together Pavilion with a WEI of 4.8. It cost less than $300.
Instead of improving the Surface Pro — or changing the benchmark — Microsoft simply dropped the Windows Experience Index.
In Microsoft’s zeal to make Windows less intimidating to new users, some of those tools are tucked away in rather obscure corners. But if you know what you’re doing, you cannot only find them but you can also use them to help make your machine hum.
Or at least burble.
Obeying the Action Center
The Windows Action Center may sound like the title of a Grade B movie or the locus of a local television news program, but it serves a simple and worthwhile purpose: Whenever Windows wants to get your attention, it nags you through the Action Center.
The Action Center consolidates security warnings with status notifications about updates, backups, and various troubleshooting tips. The Center’s most important work revolves around security.
In theory, the Windows Action Center offers one-stop shopping for all your security needs. In practice, it’s a short stop indeed — and taking control of security settings that aren’t accessible through the Action Center can be quite a headache.
But, hey, at least you don’t see the notice There Are Unused Icons on Your Desktop every time you boot Windows. See, there have been some real improvements since Windows XP.
Entering the Action Center
If you go looking for it, the Windows Action Center sits buried in an obscure corner of the desktop infrastructure. But the Security flag sits up front and, uh, center. The easiest way to get to it: on the desktop, tap or click the flag near the system clock and choose Open Action Center from the pop-up menu. The Action Center appears in all its glory, which, if you’ve been a moderately good Windows custodian, looks like Figure 4-1.

Figure 4-1: The Action Center, ready for, oh, you know.
The little flag on the desktop can take on three personas:
![]() A plain, unfettered flag means that you conform to Microsoft expectations. You may have security messages waiting or troubleshooting tips available in the Action Center but, on the whole, you’re doing fine and needn’t upset the applecart.
A plain, unfettered flag means that you conform to Microsoft expectations. You may have security messages waiting or troubleshooting tips available in the Action Center but, on the whole, you’re doing fine and needn’t upset the applecart.
 Surprisingly, refreshingly, Windows shows you a flag without an overlay if you tell it to check for Windows Updates but don’t download them. That’s a big improvement over earlier versions of Windows, which would go into conniption fits if you prevented Microsoft from reaching into your machine and applying any change it deemed appropriate. (See Book VIII, Chapter 3 for details.)
Surprisingly, refreshingly, Windows shows you a flag without an overlay if you tell it to check for Windows Updates but don’t download them. That’s a big improvement over earlier versions of Windows, which would go into conniption fits if you prevented Microsoft from reaching into your machine and applying any change it deemed appropriate. (See Book VIII, Chapter 3 for details.)
![]() A yellow exclamation point means that a portion of Windows wants your attention, and you should attend to it rather quickly. Important security releases that haven’t been applied fall into this category — at least, updates that Microsoft feels are important — as do hardware problems that leave a piece of your computer out of order.
A yellow exclamation point means that a portion of Windows wants your attention, and you should attend to it rather quickly. Important security releases that haven’t been applied fall into this category — at least, updates that Microsoft feels are important — as do hardware problems that leave a piece of your computer out of order.

![]() A red circle with an X through it (see Figure 4-2) means that something is wrong and you need to check it quickly.
A red circle with an X through it (see Figure 4-2) means that something is wrong and you need to check it quickly.

Figure 4-2: The dreaded red X appears.
In some respects, the Action Center works as a central clearinghouse for Windows problems: In many cases, if a Windows program hits a problem, the program notifies the Action Center, and the Action Center talks to you. In other respects, the Action Center takes on a proactive stance: It actively goes out and checks to see whether something is wrong and reports on its findings.
Unfortunately, these notifications don’t work in lockstep with tiled notifications, which are far more dramatic: You can get a tiled notification without a concomitant desktop notification and vice versa.
Working with the Action Center
The Action Center itself consolidates a wide range of settings from many different parts of Windows — indeed, from places outside of Windows — all in one place.
Watching Security settings
To see the monitored Security items, click the down arrow to the right of the Security heading as shown in Figure 4-3. The Action Center monitors the status of the following elements:
![]() Network Firewall: Blocks access to your computer from the Internet. Although there are many firewalls available, the vast majority of Windows users employ the one built in to Windows, which is Windows Firewall. (I talk about Windows Firewall in Book IX, Chapter 3.)
Network Firewall: Blocks access to your computer from the Internet. Although there are many firewalls available, the vast majority of Windows users employ the one built in to Windows, which is Windows Firewall. (I talk about Windows Firewall in Book IX, Chapter 3.)
 A firewall program insulates your PC (or network) from the Internet. At its heart, the Windows inbound firewall keeps track of requests that originate on your PC. When data from the Internet tries to make its way into your PC, the firewall checks to make sure that one of your programs requested the data. Unsolicited data gets dropped; requested data comes through. That way, rogues on the Internet can’t break in.
A firewall program insulates your PC (or network) from the Internet. At its heart, the Windows inbound firewall keeps track of requests that originate on your PC. When data from the Internet tries to make its way into your PC, the firewall checks to make sure that one of your programs requested the data. Unsolicited data gets dropped; requested data comes through. That way, rogues on the Internet can’t break in.

Figure 4-3: The security components of Action Center status reporting.
 Windows also has an outbound firewall, which is basically unusable. In my experience, an outbound firewall is more hassle than it’s worth; see Book IX, Chapter 3 for details. The Network Firewall line in the Action Center says On even if you don’t have outbound firewall protection.
Windows also has an outbound firewall, which is basically unusable. In my experience, an outbound firewall is more hassle than it’s worth; see Book IX, Chapter 3 for details. The Network Firewall line in the Action Center says On even if you don’t have outbound firewall protection.
You may be using the Windows Firewall or you may have a third-party firewall installed. It’s possible (but maddening) to run more than one firewall at the same time.
![]() Windows Update: Allows Windows to phone home and check for patches and patches to patches of patches. If you trust Microsoft, you can even allow Windows to patch itself, kinda like getting a license for self-administered lobotomies. I don’t recommend this, however, and explain why in Book VIII, Chapter 3.
Windows Update: Allows Windows to phone home and check for patches and patches to patches of patches. If you trust Microsoft, you can even allow Windows to patch itself, kinda like getting a license for self-administered lobotomies. I don’t recommend this, however, and explain why in Book VIII, Chapter 3.
![]() Virus Protection: Tells you whether you have a functional antivirus (AV) program. Windows Defender comes built-in (see Book IX, Chapter 3), but if you got suckered into buying an AV product, it’ll appear here.
Virus Protection: Tells you whether you have a functional antivirus (AV) program. Windows Defender comes built-in (see Book IX, Chapter 3), but if you got suckered into buying an AV product, it’ll appear here.
![]() Spyware and Unwanted Software Protection: Looks at your computer and tries to determine whether you have spyware/scumware detection and blocking in force. Of course, Microsoft Windows Defender appears here — it’s built in to Windows itself. But if you have a different antispyware package, it’ll appear here, too.
Spyware and Unwanted Software Protection: Looks at your computer and tries to determine whether you have spyware/scumware detection and blocking in force. Of course, Microsoft Windows Defender appears here — it’s built in to Windows itself. But if you have a different antispyware package, it’ll appear here, too.
![]() Internet Security Settings: Refers only to your security settings in Internet Explorer.
Internet Security Settings: Refers only to your security settings in Internet Explorer.
![]() User Account Control: Refers to Windows’ effort to put dialog boxes like the one shown in Figure 4-4 on the screen. I explain how to control UAC in Book IX, Chapter 3.
User Account Control: Refers to Windows’ effort to put dialog boxes like the one shown in Figure 4-4 on the screen. I explain how to control UAC in Book IX, Chapter 3.

Figure 4-4: User Account Control settings trigger messages like this one.
![]() Windows SmartScreen: Tries to keep you from installing potentially malicious software. There are pros and cons to its use, but as long as you understand what’s going on, it’s relatively innocuous. I talk about it in Book IX, Chapter 3.
Windows SmartScreen: Tries to keep you from installing potentially malicious software. There are pros and cons to its use, but as long as you understand what’s going on, it’s relatively innocuous. I talk about it in Book IX, Chapter 3.
![]() Network Access Protection: Covers a feature that works only in large, client-server domain networks. If you have a problem with your NAP settings, you need to contact your network administrator.
Network Access Protection: Covers a feature that works only in large, client-server domain networks. If you have a problem with your NAP settings, you need to contact your network administrator.
![]() Microsoft Account: If you use a Microsoft account to sign in (typically an
Microsoft Account: If you use a Microsoft account to sign in (typically an @hotmail.com or @live.com or @outlook.com ID, but it can be any e-mail address), this item tells you of any problems with the account. Foremost among them is the possibility that you don't know the current password to the account. See Book II, Chapter 4.
Checking Maintenance settings
To see the general Windows programs that the Action Center monitors, tap or click the down arrow to the right of the Maintenance heading. You see the following options (see Figure 4-5):

Figure 4-5: The maintenance components of the Action Center.
![]() Check for Solutions to Problem Reports: This is one of the passive settings. Windows Action Center monitors problem events as they occur and keeps tabs on your computer’s reliability history.
Check for Solutions to Problem Reports: This is one of the passive settings. Windows Action Center monitors problem events as they occur and keeps tabs on your computer’s reliability history.
 You can go back and see whether Microsoft has posted any solutions to problems that your computer has reported in the past. It’s rare, but it does happen. If you want to see which problems your computer has reported, tap or click the View Archived Messages link.
You can go back and see whether Microsoft has posted any solutions to problems that your computer has reported in the past. It’s rare, but it does happen. If you want to see which problems your computer has reported, tap or click the View Archived Messages link.
If you tap or click the View Reliability History link, you see the Reliability Monitor, as shown in Figure 4-6. (I talk about the Reliability Monitor later in this chapter in the “Gauging System Reliability” section.)

Figure 4-6: The Windows Reliability Monitor can help you pinpoint faulty software or hardware.
![]() Automatic Maintenance: Gives you the current status of the programs Windows automatically schedules to keep your system running, from mundane tasks like defragmenting drives, to system updates, and reboots as needed.
Automatic Maintenance: Gives you the current status of the programs Windows automatically schedules to keep your system running, from mundane tasks like defragmenting drives, to system updates, and reboots as needed.
![]() HomeGroup: Tells you whether you’re connected to a HomeGroup. (I talk about HomeGroups in Book VII, Chapter 5.)
HomeGroup: Tells you whether you’re connected to a HomeGroup. (I talk about HomeGroups in Book VII, Chapter 5.)
![]() File History: Lets you know whether your backups are working properly. (I talk about File History in Book VIII, Chapter 1.)
File History: Lets you know whether your backups are working properly. (I talk about File History in Book VIII, Chapter 1.)
![]() Drive Status: Warns you whether you should expect giant flames and acrid smoke. If your status turns red, increase your house insurance, like, right away, okay? Actually, this monitors the automatic reporting of problems by your hard drive and raises a flag if your drive says it’s having problems. In my experience, it isn’t very reliable.
Drive Status: Warns you whether you should expect giant flames and acrid smoke. If your status turns red, increase your house insurance, like, right away, okay? Actually, this monitors the automatic reporting of problems by your hard drive and raises a flag if your drive says it’s having problems. In my experience, it isn’t very reliable.
Reviewing Your Network Status
Windows keeps you well informed about the status of your Internet connection, with a badge icon on the lock screen, an icon in the desktop’s notification area, and easy access to the latest info through the Settings charm: Right-swipe (or hover your mouse in the upper-right corner or Windows key+C), and then choose Settings, and the Internet Access icon is in the upper-left corner, per Figure 4-7.

Figure 4-7: Quick network status is only a right-swipe and tap away.
If you want to see more about your network status, you have to flip over to the desktop. In the notification area, next to the time, tap and hold or right-click the Internet Access icon and then choose Open Network and Sharing Center. An overview of your network appears (see Figure 4-8).

Figure 4-8: For more details on network status, you have to venture over to the desktop side.
From the Network and Sharing Center, you can troubleshoot all sorts of networking problems. For a host of details, see Doug Lowe’s Networking All-in-One For Dummies (published by John Wiley & Sons, Inc.).
Turning sharing on or off
If you have a network and other computers on the network can’t “see” your PC, the most likely cause is that you’ve turned off sharing. Conversely, if you can’t see other computers on your network, you probably turned off sharing. Finally, if you can’t get a HomeGroup working (see Book VII, Chapter 5), chances are good you turned off sharing.
See a pattern here?
Everything you know about network admin you learned in kindergarten, right?
Fortunately, turning on sharing is very easy. Here’s how:
1. Swipe from the right or hover your mouse in the upper-right corner. When the Charms bar appears, choose Settings.
The status pane appears. Depending on where you were when you swiped from the right, the status pane may look a little different, but there’s always a network icon.
2. Tap or click the network icon.
It’s the top one on the left. A network connections pane like the one in Figure 4-9 appears.

Figure 4-9: Network connections appear here.
3. Tap and hold or right-click Connected.
A Turn Sharing On or Off box appears.
4. Tap or click the box.
You’re given the choices shown in Figure 4-10.

Figure 4-10: Open your network connection.
5. To turn off sharing, tap or click the top box; and to turn on sharing, tap or click the bottom box.
It may take a few minutes for Windows to change the sharing setting to open itself to the network and, if necessary, run out to the network and shout, “I’m here! I’m here!”
Sharing and discovery is, in fact, a very complex topic, with all sorts of gotchas. Anyone who’s ever tried to get a Windows XP computer to talk to a Mac knows just what I mean. If you find yourself trying to plumb the depths of networking hell, get a copy of Networking All-in-One For Dummies (published by John Wiley & Sons, Inc.) by Doug Lowe.
Troubleshooting network adapters
When I have trouble with a network and the standard Windows Troubleshooter doesn’t work (it appears at the bottom of Figure 4-8, if your network isn’t working), I always start pushing and prodding my network adapters.
There are several ways to see your network adapters. This is the method I like best because of the detour through the Network and Sharing Center. Try this:
1. Bring up Control Panel:
• Without a mouse, flip over to the desktop, swipe from the right, choose Settings, and then, at the top, choose Control Panel.
• With a mouse, right-click the lower-left corner of the screen and choose Control Panel.
2. Under the Network and Internet heading, tap or click the View Network Status and Tasks link.
The Network and Sharing Center appears (refer to Figure 4-8).
The Network and Sharing Center gives you a solid overview of what’s connected and to where.
3. On the left, tap or click the Change Adapter Settings link.
Windows shows you a list of all your adapters, as shown in Figure 4-11.
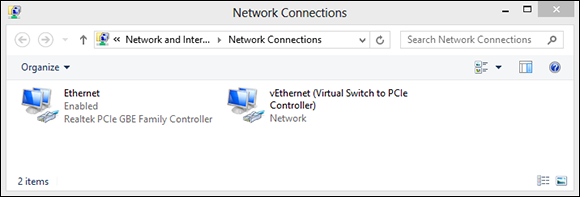
Figure 4-11: Network adapters — the pieces of hardware that connect your PC with the outside world — appear here.
4. Tap or click an adapter that may be causing problems and then tap or click Diagnose This Connection.
 Windows performs a full diagnostic on the adapter. You also have the options to disable and then re-enable the adapter (which often works wonders) or to view the status of the connection (where you can change some heavy duty settings, such as a manual override of the adapter’s IP address or locking in a DNS Server — see Networking All-in-One For Dummies (published by John Wiley & Sons) by Doug Lowe for details).
Windows performs a full diagnostic on the adapter. You also have the options to disable and then re-enable the adapter (which often works wonders) or to view the status of the connection (where you can change some heavy duty settings, such as a manual override of the adapter’s IP address or locking in a DNS Server — see Networking All-in-One For Dummies (published by John Wiley & Sons) by Doug Lowe for details).
5. When you’ve solved the problem (or you’re ready to give up), tap or click the X’s to close the Control Panel.
That should fix it.
Setting up a virtual private network
Here’s how a VPN works:
1. You set up an account with a VPN provider.
Typically the VPN provider has locations — or servers — located in several places around the world.
2. You connect to the Internet using the VPN’s server.
After you’re connected to the VPN server, all your interactions with the Internet go through the server, and communication between your computer and the server is quite secure.
So, for example, if I have a VPN account on a server in Los Angeles, I log on to that server using my account. From the moment that I establish the connection, all my interactions with the Internet look like they’re coming from Los Angeles. The only people who know that I’m using the connection are the ones who sell me the VPN service. To everyone else, I’m coming from an anonymous location in L.A.
As long as you don’t break the connection — disconnect or intentionally log off the VPN server — all your interactions with the server are encrypted, and all your interactions with the outside world can be traced only to the server.
Even your ISP is in the dark. To your ISP, it just looks like you’re pushing a lot of data through a server in Los Angeles.
There are hundreds of free VPNs but, as you may guess, they’re wholly dependent on the ability of their server(s) to keep up with the load. Google can help you find many of them. My experience with free VPNs has been spotty at best.
Years ago, I switched to a paid VPN service, VyprVPN. It works on Windows, but it's also great for my iPad, iPhone, and Android phone. (Don't tell anybody, but I use it on my Mac, too.) If you've read some of my earlier books, you probably recognize the name: VyprVPN (www.vyprvpn.com) comes from the same people who run the Giganews Usenet service (www.giganews.com) and is a good option if you get tired of the free, slow VPNs.
Viewing Events
Every Windows user needs to know about Event Viewer, if only to protect themselves from scammers and con artists who make big bucks preying on peoples’ fears.
As I explain in Book IX, Chapter 1, scammers are calling people in North America, Europe, Australia, and other locations all around the world, trying to talk Windows users into allowing these con artists to take over victims’ systems via Remote Assistance. The scammers typically claim to be from Microsoft, or associated with Microsoft. They may get your phone number by looking up names of people posting to help forums.
The scam hinges around the Windows Event Viewer feature. It’s an interesting, useful tool — but only if you take the initiative to use it, and don’t let some fast talker use it to bilk you out of hundreds of bucks.
Using Event Viewer
Windows has had an Event Viewer for almost a decade. Few people know about it. At its heart, the Event Viewer looks at a small handful of logs that Windows maintains on your PC. The logs are simple text files, written in XML format. Although you may think of Windows as having one Event Log file, in fact, there are many — Administrative, Operational, Analytic, and Debug, plus application log files.
Every program that starts on your PC posts a notification in an Event Log, and every well-behaved program posts a notification before it stops. Every system access, security change, operating system twitch, hardware failure, and driver hiccup all end up in one or another Event Log. The Event Viewer scans those text log files, aggregates them, and puts a pretty interface on a deathly dull, voluminous set of machine-generated data. Think of Event Viewer as a database reporting program, where the underlying database is just a handful of simple flat text files.
Here’s how to use the Event Viewer:
1. On the Start screen, type event. Click or tap View Event Logs.
The Event Viewer appears.
2. On the left, choose Event Viewer⇒Custom Views⇒Administrative Events.
It may take a while, but eventually you see a list of notable events like the one in Figure 4-12.
3. Don’t freak out.
Even the best-kept system (well, my production system anyway) boasts reams of scary-looking error messages — hundreds, if not thousands of them. That’s normal.

Figure 4-12: Events logged by various parts of Windows.
Events worthy — and not worthy — of viewing
Before you get all hot and bothered about the thousands of errors on your PC, look closely at the date and time field. There may be thousands of events listed, but those probably date back to the day you first installed the PC. Chances are good that you can see a handful of items every day — and most of the events are just repeats of the same error or warning. Most likely, they have little or no effect on the way you use Windows. An error to Windows should usually trigger a yawn and “Who cares?” from you.
For example, looking through my most recent Event Log, I see a bunch of errors generated by a source called DistributedCOM, telling me that the server Microsoft.WindowsLive.Mail.App didn’t register with DCOM within the required timeout. Really and truly, no biggie. Fugeddaboutit.
That’s exactly my advice. If you aren’t experiencing problems, don’t sweat what’s in the Event Viewer. Even if you are experiencing problems, the Event Viewer may or may not be able to help you.
Gauging System Reliability
Every Tom, Dick, ’n Hairy Windows routine leaves traces of itself in the Windows Event Log. Start a program, and the ignoble event gets logged. Stop it, and the Log gets updated. Install a program or a patch, and the Log knows all, sees all. Every security-related event you can imagine goes in the Log. Windows Services leave their traces, as do errors of many stripes. Things that should’ve happened but didn’t get logged, as well as things that shouldn’t have happened but did. Soup to nuts.
The Event Log contains items that mere humans can understand. Sometimes. It also logs things that only a propeller head could love. The Event Log actually consists of a mash-up of several files that are maintained by different Windows system programs in different ways. The Event Viewer, discussed in the preceding section, looks at the trees. The Reliability Monitor tries to put the forest in perspective.
Here’s how to bring up the Reliability Monitor:
1. On the Start screen, type reli. Below the search box, click or tap View Reliability History.
The Reliability Monitor springs to life, as shown in Figure 4-13.

Figure 4-13: When something goes out to lunch, it leaves a trace in the Reliability Monitor.
2. In the View By line, flip between Days and Weeks.
Reliability Monitor goes back and forth between a detailed view and an overview.
The top line in the monitor is supposed to give you a rating, from one to ten, of your system’s stability. In fact, it doesn’t do anything of the sort, but if you see the line drop like a wood barrel over Victoria Falls, something undoubtedly has gone bump in the night.
If you tap or click a day (or a week), the box at the bottom shows you the corresponding entries in your Windows Event Log. Many events at the bottom have a more detailed explanation, which you can see by tapping/clicking the View Technical Details link.
The real value of the Reliability Monitor lies in showing you a time sequence of key events — connecting the temporal dots so you may be able to discern a cause and effect. For example, if you suddenly start seeing blue screens repeatedly, check the Reliability Monitor to see whether something untoward has happened to your system. Installing a new driver, say, can make your system unstable, and the Reliability Monitor can readily show you when it was installed. If you see your rating tumble on the same day that a driver update got installed, something’s fishy, and you may be able to readily identify the scaly culprit.
Proverbial bottom line: The Reliability Monitor doesn’t keep track of everything, and some of it is a bit deceptive, but it can provide some worthwhile information when Windows starts kicking. The Reliability Monitor is well worth adding to your Win bag of tricks.

 Windows 8 included a rag-tag, system performance benchmarking routine known as the Windows Experience Index. I used to use WEI all the time as a quick way to check PCs in shops to see which ones were great and which merely mediocre: It wasn’t the best test, but it was good enough for quick comparisons, and every Windows PC had a copy.
Windows 8 included a rag-tag, system performance benchmarking routine known as the Windows Experience Index. I used to use WEI all the time as a quick way to check PCs in shops to see which ones were great and which merely mediocre: It wasn’t the best test, but it was good enough for quick comparisons, and every Windows PC had a copy. All these settings focus on preventing bad stuff outside your PC from getting inside — a noble goal, to be sure, but the baddies that lurk outside your box are only part of the problem. The other part? You. To get — and keep — your security and sanity in Windows, you must understand how your PC can be attacked and what you can do to forestall those attacks, both from a computer point of view and by thinking “outside the box.” (That’s the theme of Book IX,
All these settings focus on preventing bad stuff outside your PC from getting inside — a noble goal, to be sure, but the baddies that lurk outside your box are only part of the problem. The other part? You. To get — and keep — your security and sanity in Windows, you must understand how your PC can be attacked and what you can do to forestall those attacks, both from a computer point of view and by thinking “outside the box.” (That’s the theme of Book IX,