NAT and PAT
Now that the ASA knows how to forward to the Internet and the DHCP clients on the inside know to use the ASA as their default gateway, we have a problem with the IP addresses the clients are using on the inside: They are all using private IP address space. Those packets will not be allowed on the Internet. Have no fear, because we know that the ASA can do Network/Port Address Translation (NAT/PAT). To implement this, navigate to Configuration > Firewall > NAT Rules and click Add (see Figure 16-13).
In the top half of the dialog box, you specify the source traffic (where the traffic will be coming from). I specified that the traffic will be coming into the inside interface from an object group that I created named Inside_Hosts. This interface allows you to dynamically create object groups by using the ellipsis button (...). It also asks about the exit interface that packet will have to be taking for the address translation to be used. The bottom half of the dialog box asks what you want to translate the IP address to. If you want to translate the addresses to the outside interface (meaning you are going to use PAT and the global address that is on the outside interface of the ASA), you can specify that you want to use Dynamic PAT (Hide) mode and then select the outside interface. The ASA translates the user’s source IP addresses, and to the Internet it will appear that all transmitted packets (from your clients) are coming from the source address of the outside interface of the ASA. When you click OK and Apply, this configuration change is sent to the ASA. Example 16-7 shows the CLI equivalent.
Example 16-7 CLI Equivalent for Implementing Dynamic PAT
! creates a network object that refers to the 10.0.0.0/24 network
ASA1(config)# object network Inside_Hosts
ASA1(config-network-object)# subnet 10.0.0.0 255.255.255.0
ASA1(config-network-object)# description Inside_Hosts
ASA1(config-network-object)# exit
! creates a NAT rule that says any traffic sourced from devices
! from the Inside_Hosts object group (network the 10.0.0.0/24 network),
! and coming in on the inside interface, as well as exiting (being routed
! through) the outside interface (based on the routing table of the ASA),
! it would then translate the source address of these packets, and
! substitute the source address of the outside interface of the ASA.
! Additionally it would track this in a NAT/PAT table, that is separate
! from the stateful database, and the ASA would manage both of these
! tables.
ASA1(config)# nat (inside,outside) 1 source dynamic Inside_Hosts interface
! With the NAT on version 8.3 and newer, there are multiple options of
! configuring the NAT, including a NAT command done within object group
! configuration mode. These additional options, including advanced ASA NAT
! configuration are covered in the CCNP Security curriculum.
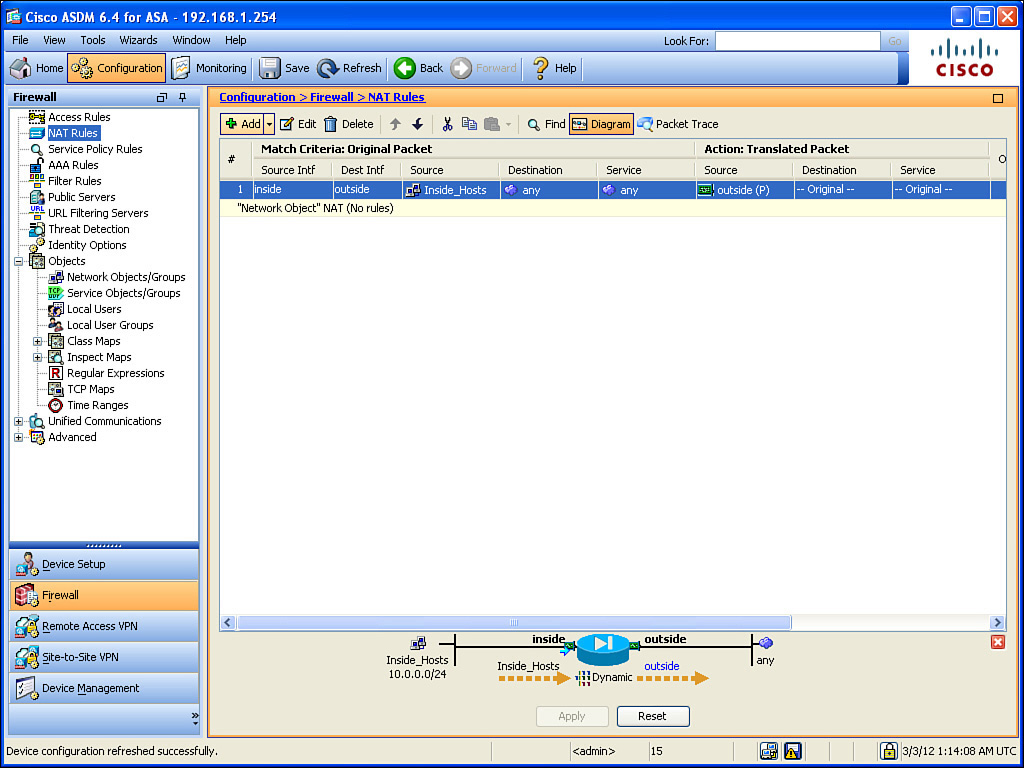
To verify the NAT configuration, navigate to the same location shown in Figure 16-13 and look at the NAT rules, as shown in Figure 16-14.
Figure 16-14 shows that devices from the Inside_Hosts group are identified, but we do not know exactly what’s in that group. On a live interface, you can hover over that group until a pop-up shows you the details of that group. Another option is to click the Network Objects/Groups link in the left navigation pane in Figure 16-14 to look at the details there. One other challenge that might need to be addressed is that we can see the NAT will happen using the outside interface’s IP address. But how do we know what that IP address is (on the outside interface)? Referring to Figure 16-10, we could look at the details of that interface, and even if it is DHCP-assigned for the outside interface (assigned to us by the service provider), the IP address will be revealed there, next to the interface name.