Distributed Denial-of-Service Attacks
Denial-of service (DoS) and distributed DoS (DDoS) attacks have been around for quite some time now, but there has been heightened awareness of them over the past few years. The reason for this increased attention is in large part due to the attacks that took place against the financial services sector in the fall of 2012 and spring of 2013.
DDoS attacks can generally be divided into the following three categories:
![]() Direct: Direct DDoS attacks occur when the source of the attack generates the packets, regardless of protocol, application, and so on, that are sent directly to the victim of the attack.
Direct: Direct DDoS attacks occur when the source of the attack generates the packets, regardless of protocol, application, and so on, that are sent directly to the victim of the attack.
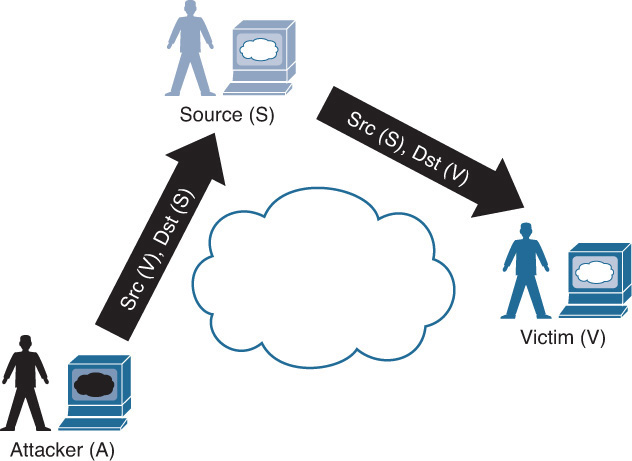
![]() Reflected: Reflected DDoS attacks occur when the sources of the attack are sent spoofed packets that appear to be from the victim, and then the sources become unwitting participants in the DDoS attacks by sending the response traffic back to the intended victim. UDP is often used as the transport mechanism because it is more easily spoofed due to the lack of a three-way handshake. For example, if the attacker (A) decides he wants to attack a victim (V), he will send packets (for example, Network Time Protocol [NTP] requests) to a source (S) who thinks these packets are legitimate. The source (S) then responds to the NTP requests by sending the responses to the victim (V), who was never expecting these NTP packets from source (S) (see Figure 2-1).
Reflected: Reflected DDoS attacks occur when the sources of the attack are sent spoofed packets that appear to be from the victim, and then the sources become unwitting participants in the DDoS attacks by sending the response traffic back to the intended victim. UDP is often used as the transport mechanism because it is more easily spoofed due to the lack of a three-way handshake. For example, if the attacker (A) decides he wants to attack a victim (V), he will send packets (for example, Network Time Protocol [NTP] requests) to a source (S) who thinks these packets are legitimate. The source (S) then responds to the NTP requests by sending the responses to the victim (V), who was never expecting these NTP packets from source (S) (see Figure 2-1).
![]() Amplification: Amplification attacks are a form of reflected attacks in which the response traffic (sent by the unwitting participants) is made up of packets that are much larger than those that were initially sent by the attacker (spoofing the victim). An example of this is when DNS queries are sent and the DNS responses are much larger in packet size than the initial query packets. The end result is that the victim gets flooded by large packets for which it never actually issued queries.
Amplification: Amplification attacks are a form of reflected attacks in which the response traffic (sent by the unwitting participants) is made up of packets that are much larger than those that were initially sent by the attacker (spoofing the victim). An example of this is when DNS queries are sent and the DNS responses are much larger in packet size than the initial query packets. The end result is that the victim gets flooded by large packets for which it never actually issued queries.