Chapter 16: Understanding ARP
When data travels across networks, the packets use a logical or Internet Protocol (IP) address to identify the destination host. However, on a local area network (LAN), the packets use a physical or media access control (MAC) address to deliver data to a host. When a packet is transported from a website across the internet to a host on a LAN, the switch only has an IP address to identify the host. How does the device locate the destination host? That is the responsibility of the Address Resolution Protocol (ARP), which resolves an IP address to a MAC address so that the data gets delivered to the correct host.
In this chapter, we'll learn how ARP works, and why it is an important protocol in ensuring the timely delivery of data. We'll then take a closer look at ARP headers and fields in Wireshark. We'll also examine the different types of ARP that you may encounter while doing analysis, including gratuitous, reverse, inverse, and proxy. Finally, so that you are aware that ARP may be used in a malicious way, we'll discuss ARP attacks and possible ways to defend against these types of threats.
This chapter will cover the following:
- Understanding the role and purpose of ARP
- Exploring ARP headers and fields
- Examining the different types of ARP
- Comparing ARP attacks and defense methods
Understanding the role and purpose of ARP
ARP is one of the three main network layer protocols (ARP, IPv4, and Internet Control Message Protocol (ICMP)), all of which are essential in delivering data.
In the following diagram, we see that ARP is actually in between Layer 3 and Layer 2 of the Open Systems Interconnection (OSI) model, as ARP resolves an IP address (network layer) to a MAC address (data link layer):

Figure 16.1 – The OSI model network layer protocols
Note
Although ARP resides in between Layer 2 and Layer 3 of the OSI model, many consider ARP as a Layer 3 protocol.
In this section, we'll see how ARP resolves a MAC address. We'll then learn how the ARP cache helps provide a speedier response. In addition, we'll discover how an IPv6 network uses the Neighbor Discovery Protocol (NDP) to resolve an IPv6 address to a MAC address.
On a LAN using IPv4, the frame header must use a MAC address to identify the receiving host. To obtain the correct MAC address, the sending device will issue an ARP broadcast on the network. In the next section, let's discuss why this is important.
Resolving MAC addresses
When data travels through different networks, packets use an IP (or logical) address. However, to deliver the data to its final destination, a MAC (or physical) address is needed to place in the frame header. The device will first check its local ARP cache. If there is no entry, the device issues an ARP request in the form of a broadcast, and will wait for a reply.
Note
A broadcast message is sent from one host to all devices on a network. While every host will receive the frame, only one will respond.
As shown in the following diagram, Host A needs the MAC address for the gateway, which is the router interface for the LAN:
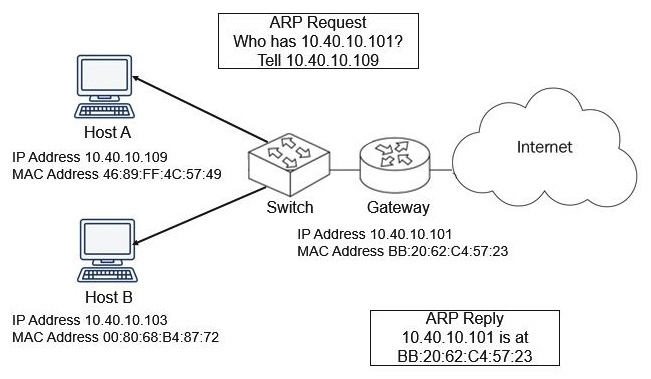
Figure 16.2 – ARP broadcast on a network
To obtain the MAC address of the gateway, Host A issues an ARP request. The ARP request asks the question, "Who has the IP address 10.40.10.101? Tell 10.40.10.109," and waits for a reply. The gateway then sends an ARP reply to let the host know that 10.40.10.101 is at MAC address BB:20:62:C4:57:23.
Now that we understand the basics of an ARP request and reply, let's step through what we will see while viewing the process in Wireshark.
Viewing an ARP request and reply
To see an example of an ARP request and reply so that you can follow along, go to https://crnetpackets.files.wordpress.com/2015/08/arptrace.zip, download the file, extract it, and open it in Wireshark, as shown here:

Figure 16.3 – ARP request/reply
In the ARP trace file, the first two packets are the ARP request/reply.
In Frame 1, the device sends an ARP request. The source and destination addresses are as follows:
- The source MAC address is 00:15:5d:0f:49:18, which is the MAC address of the device requesting the resolution.
- The destination MAC address is ff:ff:ff:ff:ff:ff, which is a broadcast address.
In Frame 2, the device identifies itself with an ARP reply. The source and destination addresses are as follows:
- The source MAC address is d4:be:d9:af:3e:4d, which is the device with the IP address 172.16.2.27.
- The destination MAC address is 00:15:5d:0f:49:18, which is the MAC address of the device requesting the resolution.
Keep in mind, when doing a capture in Wireshark, it is normal to see several ARP broadcasts before seeing an ARP reply.
We now know that ARP resolves an IP address to a MAC address. This is so the device has a MAC address that can be placed in the frame header in order for the data to be delivered on a LAN. So that the device is able to quickly retrieve the MAC address of a device on the network, it holds the IP address to MAC address pairings in a temporary holding area called the ARP cache. The next section explains an ARP cache, how it's used, and how long the table entries remain.
Investigating an ARP cache
Network devices, such as routers, switches, and PCs, hold a form of an ARP cache table, which is a storage area to store IP to MAC address pairings. To see your own ARP cache on a Windows machine, open a Command Prompt and enter arp -a to see the entries in the ARP table, as shown here:
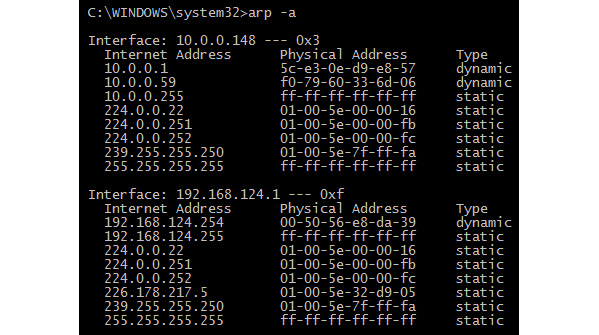
Figure 16.4 – Using the arp -a command
In the previous figure, the ARP cache table lists the following:
- Internet Address: Displays the IP address
- Physical Address: Displays the corresponding MAC address
- Type: Displays whether the entry is either static (stays the same) or dynamic (periodically refreshed)
The dynamic ARP cache values will time out after a period of time. Once the timeout limit is reached, the entry will go away. If the operating system (OS) needs the MAC address and there is no entry in the ARP table, it will need to issue a new ARP request.
Note
The ARP table timeout values are specific to the system. For example, a Cisco switch has a default timeout timer of 4 hours.
In a Windows OS, you can determine the timeout value by going to the command-line interface (CLI) and running the netsh interface ipv4 show interface NNN command.
Note
When using the command, replace NNN with the name of the interface you want to check.
As shown in the screenshot, we see the output of running netsh interface ipv4 show interface Wi-Fi, which provides information on that interface:

Figure 16.5 – Issuing the netsh show interface command
Within the output, you will see Base Reachable Time is 30000 ms or 30 seconds, which is how long ARP can live in the cache before going away. After 30 seconds, if a MAC address is needed for a specific IP address, the system must send an ARP request out on the network.
We now understand how ARP works in an IPv4 network, but what happens in an IPv6 network? The following section outlines how NDP takes the place of ARP in an IPv6 network.
Replacing ARP with NDP in IPv6
ARP is essential in an IPv4 network, however, IPv6 doesn't use ARP. Instead, ARP is replaced with NDP, which resolves an IP address to a MAC address.
To see an example of NDP, go to http://packetlife.net/captures/protocol/icmpv6/ and open the IPv6_NDP.pcap file in Wireshark. As shown in the following screenshot, the first packet in the trace file is a Neighbor Solicitation (NS), followed by a neighbor advertisement:
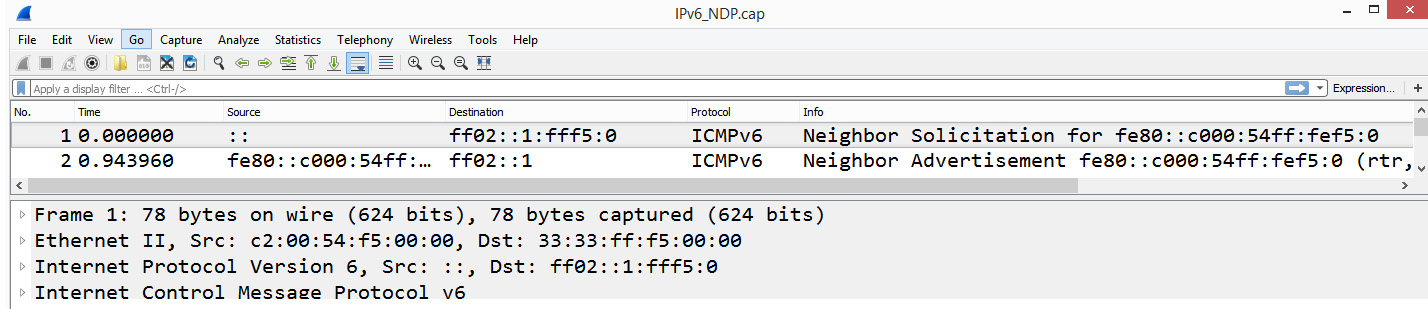
Figure 16.6 – Example of NDP
An NS has the same purpose as an ARP broadcast. However, IPv6 doesn't use broadcasts. It uses Internet Control Message Protocol version 6 (ICMPv6) with a solicited-node multicast address message that is directed to a specific host. As a result, if you are analyzing a network that only uses IPv6, you may only see a few ARP broadcasts, if any.
As we can now understand, ARP is a common protocol that you will most likely see while doing analysis, as IPv4 is still widely used. So that you better understand a standard ARP request and reply, the following section provides an overview of an ARP header and corresponding field values.
Exploring ARP headers and fields
While in a trace file, if you enter arp in the display filter, you will most likely see a series of ARP requests and replies. Within each ARP header, there are several field values, such as Operation Code (Opcode), sender, and target IP address, which help ensure that the ARP requests/replies are received. Let's first take a look at a typical ARP transaction.
Identifying a standard ARP request/reply
Open ARPTrace.pcapng, and take a look at the first two packets, which are the ARP request/reply. Expand each ARP request/reply, and you will see that ARP is wrapped in an Ethernet frame. However, there are no network or transport layer headers.
First, let's investigate the components of an ARP request.
Inspecting an ARP request
To view a standard ARP request, expand Frame 1. Once expanded, you can see that there are several field values, which provide information about the transaction, as shown here:
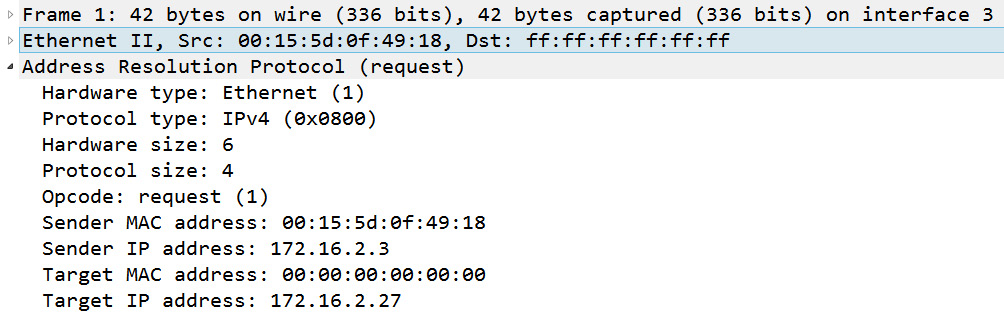
Figure 16.7 – Frame 1 ARP request
We see within this ARP request that the host at 172.16.2.3 is requesting the MAC address of the host that has the IP address 172.16.2.27. Key field values include Opcode, which shows that this is a request, along with the IP addresses of both the sender and target.
The ARP reply is similar to the request; however, the target MAC address will be present.
Evaluating an ARP reply
Frame 2 is the ARP reply, where the host at 172.16.2.27 replies with its MAC address, which is d4:be:d9:af:3e:4f, as shown here:

Figure 16.8 – Frame 2 ARP reply
Key field values include the Opcode, which shows that this is a reply, along with the MAC and IP addresses of both the sender and target. Once the ARP reply is received, the MAC address is resolved.
As shown, an ARP header has several field values, which we'll review next.
Breaking down the ARP header fields
In this section, we'll review the ARP field values. So that you understand the role and purpose of each field, I will list the following:
- Name of the field
- Number of bytes
- Purpose of the field
To follow along, open ARPTrace.pcapng and select Frame 22. Expand the ARP header as follows:

Figure 16.9 – Frame 22 ARP request
Within an ARP header, the field values that provide information on the ARP transaction are outlined in the following table:

Table 16.1 – APR field values
Some of the parameters, such as the Opcode and hardware type are represented by a number. The values are defined by iana.org, and can be found here: https://www.iana.org/assignments/arp-parameters/arp-parameters.xhtml.
Some of the defined values include the following:
- Hardware Type 31 – IPsec tunnel
- Hardware Type 18 – Fiber Channel
Now that we can see the header and fields in a standard ARP header, let's take a look at some other types of ARP you might encounter during an analysis.
Examining different types of ARP
On an IPv4 network, the most common types of ARP messages are requests and replies:
- A standard ARP request is a broadcast message that is sent out on the network requesting a resolution of an IP address to a MAC address.
- A standard ARP reply is a unicast message that is sent to the requesting host that provides the address resolution.
However, as we'll outline in this section, there are a few other types of ARP messages. We'll start with the Reverse Address Resolution Protocol (RARP), which is the reverse of ARP.
Reversing ARP
The opposite of ARP is RARP, in that with RARP, a client requests its IPv4 address from a computer network by using its MAC address.
Using an example rarp_request.cap found at https://wiki.wireshark.org/SampleCaptures?action=AttachFile&do=view&target=rarp_request.cap, we can see the host requesting its IP address, as shown in the following screenshot:

Figure 16.10 – Viewing a RARP request
The sender's MAC address is 00:00:a1:12:dd:88. The IP address is unknown, so it is listed as 0.0.0.0. The Opcode is reverse request (3).
Note
RARP is an obsolete protocol that has been replaced by more efficient protocols, such as the Dynamic Host Configuration Protocol (DHCP); therefore, you won't see any RARP traffic on a LAN. However, RARP is used in virtualized environments to keep the MAC tables updated.
Next, let's look at a lesser-known type of ARP called the Inverse Address Resolution Protocol (InARP).
Evaluating InARP
InARP is an extension of the ARP protocol. We can see an example of this by going to CloudShark at https://www.cloudshark.org/captures/87be3b4b6625 and opening FrameRelay-101.pcap in Wireshark, as shown here:
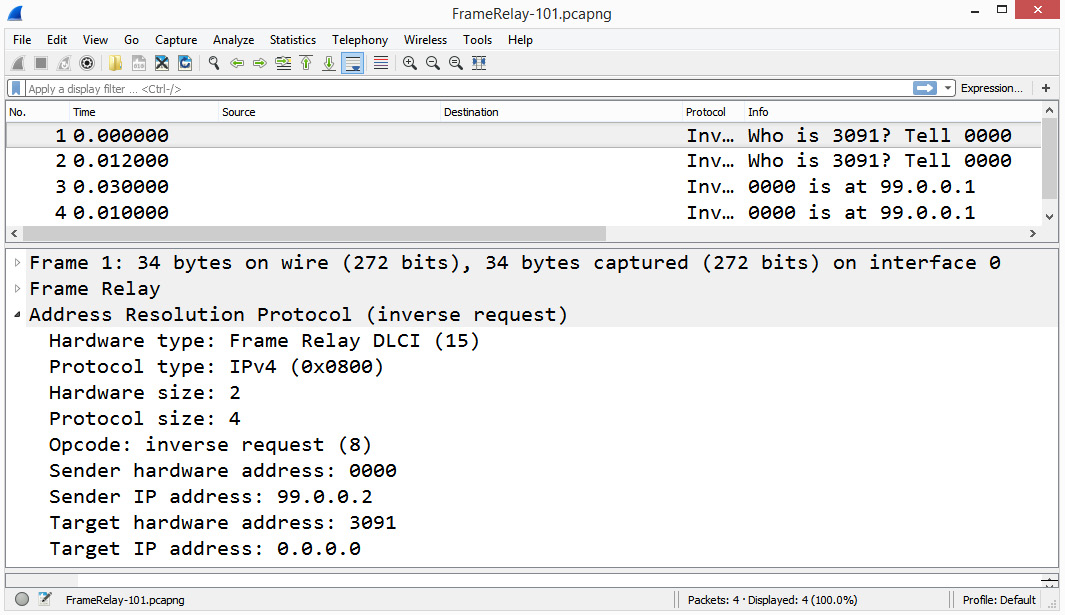
Figure 16.11 – An InARP example
On a wide area network (WAN), Frame Relay was a widely used packet-switching method to transmit data between LANs. When communicating with one another, each router's interface uses a data link connection identifier (DLCI) of the desired station, which is the device's hardware address.
InARP is used in the same way as a standard ARP in resolving an IP address. However, it does not use broadcasts, as it already knows the DLCI of the desired station. As shown in the following diagram, the sending router, 99.0.0.2, attempts to resolve the IP address of DLCI 3091 by using InARP:

Figure 16.12 – InARP over Frame Relay
The use of Frame Relay is being phased out and replaced by a more efficient method of transmitting data on a WAN, Asynchronous Transmission Mode (ATM). As a result, you will rarely, if ever, see InARP in a capture.
While you may not see InARP while conducting an analysis, you most likely will see a more common type of ARP called a gratuitous ARP, as outlined next.
Issuing a gratuitous ARP
On a LAN, a duplicate IP address can cause conflicts. To prevent this, hosts issue a gratuitous ARP, which is an unsolicited ARP used to prevent duplicate IP addresses. To see an example, go to https://www.cloudshark.org/captures/54af88021aa8, and then download and open the file in Wireshark. Once open, expand the ARP header as shown:
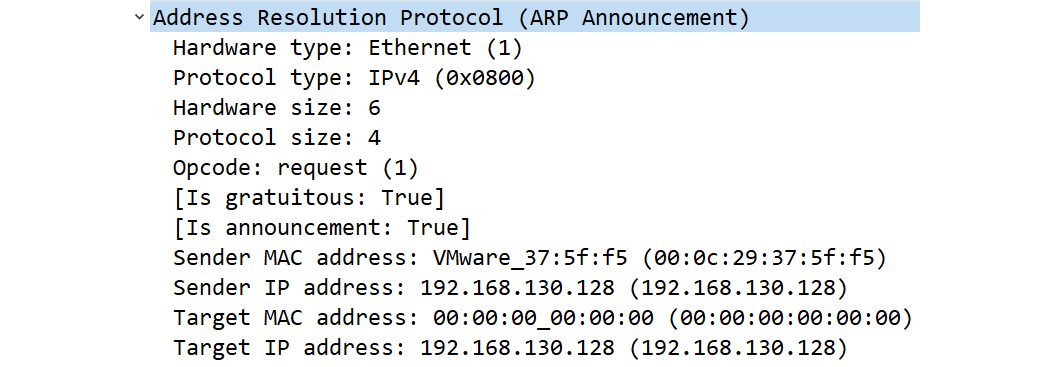
Figure 16.13 – Gratuitous ARP
In this frame, we see Opcode: request (1). However, we also see that Sender IP address: 192.168.130.128 is the same as Target IP address: 192.168.130.128, which identifies the frame as a gratuitous ARP.
Note
Wireshark will identify a gratuitous ARP as ARP Announcement.
A gratuitous ARP request is sent as a broadcast; however, no reply is expected. In addition to checking for duplicate IP addresses, this type of ARP can provide a way for a host to share IP and MAC address pairings. For example, if a network device's interface goes down and then is brought back up, a gratuitous ARP is sent so that all hosts can update their ARP tables.
Next, we'll see an example that is not actually an ARP type, but a technique used on the network called a proxy ARP.
Working on behalf of ARP
A proxy is something that works on behalf of another entity. A proxy ARP is a technique whereby another entity resolves a MAC address. On a network, there are a few instances when a proxy ARP can be used.
One way to use a proxy ARP is when concealing a host behind a firewall.
Obscuring a host
When a machine with a public IP address is in a private network behind a firewall, it's best to hide its existence.
If you do have a host behind a firewall, a way to resolve the MAC address is by having the firewall use a proxy ARP to and from the hidden device. This will maintain the illusion that the machine is on the public side in front of the firewall.
A proxy ARP can also be used in a LAN when a host in one subnetwork is separated by a proxy router.
Acting as a proxy
On a LAN, it's sometimes necessary to use a proxy ARP. For example, a proxy ARP is necessary when an ARP broadcast is sent to a host on another subnetwork. Because an ARP request is a broadcast, it will stop at the router's interface.
In this case, the router responds with its own MAC address and acts as a proxy to the host on the other subnetwork. The router will encapsulate the ARP request packet with its own MAC address as the source and will then issue a broadcast on the appropriate network, as shown here:
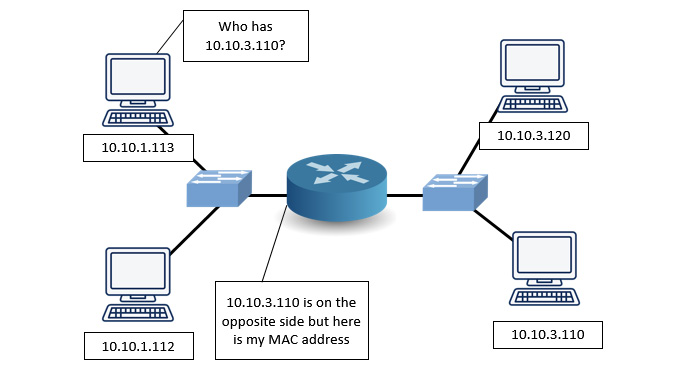
Figure 16.14 – Proxy ARP
You can now understand that there are many different types of ARP messages and techniques that may be used on a LAN. ARP is an essential protocol but can be a vulnerable target. In the next section, let's take a look at some ARP attacks along with defense methods.
Comparing ARP attacks and defense methods
ARP is a widely used protocol that resolves an IP address to a MAC address. In most cases, ARP works well to ensure devices can find one another. However, the protocol was standardized many years ago, and there has never been a way to ensure the authenticity of ARP messages.
As a result, we'll outline a few ARP attacks that can misdirect traffic and interfere with normal network behavior. In response, we'll also take a look at some of the ways to defend against these types of attacks.
Let's begin by covering some of the attacks against ARP.
Comparing ARP attacks and tools
ARP is used on a LAN, which can be a vulnerable target. Some of the attacks and techniques used to penetrate an ARP framework include spoofing and storming, which can misdirect traffic or cause problems on the network. In this section, we'll compare some of the attacks you or a colleague might encounter.
Let's start with using ARP in a way that can trick or deceive hosts on a network.
Discovering ARP spoofing
On an IPv4 network, ARP is a critical protocol used when delivering data to the correct host. A malicious actor can redirect traffic to their machine by using an ARP cache poison (or ARP spoofing) attack on the LAN. This man-in-the-middle attack is done by tricking hosts on the network into believing the malicious actor's MAC address is some other host, with the intention of intercepting traffic.
Note
For a more in-depth review of an ARP spoofing attack, go to Chapter 1, Appreciating Traffic Analysis, in the Arming hackers with information subsection.
In addition to ARP spoofing, an attacker can launch an ARP storm, as discussed next.
Reviewing the ARP storm
On a LAN, it's normal to see ARP request/reply messages. However, when there is a large number of ARP requests, as shown in the following screenshot, this is an indication of an ARP storm, which is a form of denial of service (DoS) attack:

Figure 16.15 – An ARP storm
Let's step through how an ARP storm works:
- In order to efficiently deliver data, a switch uses a content-addressable memory (CAM) table that contains pairings of MAC addresses and their associated physical switch ports.
- An ARP storm floods the CAM table and overwhelms the switch with thousands of bogus entries.
- At that point, the switch simply acts as a hub and sends data out from all of the ports, which can result in the following:
- Allowing traffic sniffing that could possibly expose sensitive data
- Preventing the network from functioning normally
As you can see, an ARP storm is possible. In Wireshark, you can monitor for ARP storms. To modify this, select an ARP header, right-click, and select Protocol Preferences | Open Address Resolution Protocol Preferences…, which will display the following screenshot:

Figure 16.16 – ARP/RARP preferences
Once in the Preferences menu, you can modify the following:
- Number of requests to detect during period: Enter an appropriate value, for example, 30 requests.
- Detection period (in ms): Enter an appropriate value, for example, 100 ms.
Although Wireshark can't prevent an ARP storm, it can help you identify a potential attack.
We now know that there are attacks such as spoofing and storming. How are these attacks launched? The following section outlines some of the tools that are available to launch an ARP attack on a LAN.
Understanding ARP attack tools
ARP attacks can occur on a LAN. Many tools that are available are built into Kali Linux. Kali Linux is a collection of software tools designed to assist the network administrator with conducting ethical hacking on a network. For a complete list, go to https://tools.kali.org/tools-listing.
Some of the tools in Kali Linux that are used to launch an ARP attack include the following:
- dsniff is a suite of tools that includes arpspoof, which allows a hacker to advertise a spoofed MAC address as a way to misdirect traffic.
- Ettercap is an easy-to-use tool for ARP attacks, along with other tools that make it possible to intercept network traffic.
- Arpoison is a free command-line tool that allows a hacker to custom build an ARP packet and define the sender and target addresses.
As shown, there are several ways to launch an ARP attack, and hackers have many tools at their disposal. The following section outlines some of the ways we can defend against ARP attacks.
Defending against ARP attacks
As discussed, ARP can be a vulnerable target. In addition to the attacks listed, there are others as well. The network administrator should be aware of methods to detect, as well as defend against, these types of attacks.
Some of the tools and techniques to prevent an ARP attack include the following:
- Intrusion detection systems/intrusion prevention systems (IDSs/IPSs): Tune devices to monitor for abnormal ARP activity such as ARP storms, which generally have specific signatures. The device should send an alert if unsolicited replies are detected.
- Static ARP entries: Hardcode address mappings to prevent spoofing. Although static ARP entries can prevent an ARP spoof, this isn't the best defensive method, as it doesn't scale well with large networks.
- Firewalls: Use an access-control list with packet filtering to ensure only authorized traffic is allowed on the network segment.
- Anti-ARP software: This software monitors for spoofing, which can present itself as two IP addresses having the same MAC address. Many times, the software will also include methods to detect other malicious ARP behavior.
- Secure Neighbor Discovery (SEND): On an IPv6 network, it is possible to use the SEND protocol. This is an extension of NDP that provides authentication by using cryptographic techniques and reduces the ability to successfully launch an ARP spoofing attack on a LAN.
While it's possible for a network to fall victim to malicious ARP activity, it's best to activate possible defensive strategies, to prevent a crippling attack.
Summary
By now, you have a better understanding of ARP, how it works, and why it is important for delivering data. So that you have an appreciation of what takes place during an ARP request and reply, we stepped through the process, and then reviewed the ARP headers and field values. We also discussed the fact that, in addition to a standard ARP, you may encounter different types of ARP while analyzing traffic in Wireshark, such as a gratuitous ARP or InARP. Finally, so that you are aware that ARP may be used in a malicious way, we covered some of the attacks, along with a few of the tools used to launch an ARP attack. We then summarized some of the methods you should employ to defend against various types of attacks.
The next chapter will look at how Wireshark can help identify and troubleshoot network latency issues. You'll be able to appreciate the importance of time values on a network and discover several ways to display time. In addition, you'll see the value of coloring rules within Wireshark and the Intelligent Scrollbar that helps highlight interesting traffic. Finally, you'll learn how to use the expert information, so that you can zero in on trouble spots during an analysis.
Questions
Now, it's time to check your knowledge. Select the best response, and then check your answers with those in the Assessment appendix:
- On a LAN, the _____ layer uses the MAC address of the destination machine, rather than the IP address:
- Network
- Presentation
- Data link
- Transport
- The ARP Opcode lists what operation the sender is executing. Although there are many, the most common opcodes are _____:
- 10 and 12
- 0 and 8
- 7 and 8
- 1 and 2
- With a(n) _____, a client requests its IPv4 address from a computer network by using its MAC address:
- InARP
- RARP
- Gratuitous ARP
- Proxy ARP
- The _____ is an unsolicited ARP used to prevent duplicate IP addresses on a network. No reply is expected:
- InARP
- RARP
- Gratuitous ARP
- Proxy ARP
- An ARP_____ is a large number of ARP requests that creates a DoS attack and prevents the network from functioning normally:
- Storm
- Spoof
- Gratuitous
- Inverse
- The _____ defines what operation the sender is executing:
- Storm
- Spoof
- Opcode
- Protocol type
- A possible defensive strategy to defend against an ARP attack is to use a(n) _____ and tune the device to monitor for abnormal ARP activity such as ARP storms:
- Otter Box
- IDS/IPS
- Gratuitous Code
- CAM alert
Further reading
Please refer to the following links for more information:
- For a list of hardware types identified in the ARP header, go to the following: https://www.iana.org/assignments/arp-parameters/arp-parameters.xhtml#arp-parameters-2.
- The Opcode defines what operation the sender is executing. View the entire approved list of Opcodes at the following: https://www.iana.org/assignments/arp-parameters/arp-parameters.xhtml#arp-parameters-1.
- Discover when hosts issue a gratuitous ARP by visiting the following: https://wiki.wireshark.org/Gratuitous_ARP.
