Virtual private networks, commonly referred to as VPNs, are not an entirely new concept in networking. As the name suggests, a VPN can be defined as a private network service delivered over a public network infrastructure. A telephone call between two parties is the simplest example of a virtual private connection over a public telephone network. Two important characteristics of a VPN are that it is virtual and private.
There are many types of VPNs, such as Frame Relay and ATM, and entire books can and have been written about each of these VPN technologies. The focus of this book is on a VPN technology known as IPSec.
This chapter introduces some of the VPN technologies and helps to explain the motivations for deploying a VPN. The primary reason for deploying a VPN is cost savings. Corporations with offices all over the world often need to interconnect them in order to conduct everyday business. For these connections, they can either use dedicated leased lines that run between the offices or have each site connect locally to a public network, such as the Internet, and form a VPN over the public network.
Figure 1-1 shows an international corporation that connects to each site using leased lines. Each connection is point-to-point and requires a dedicated leased line to connect it to another site. If each site needs to be connected to every other site (a situation also known as any-to-any or full-mesh connectivity), n-1 leased lines would be required at each site where n is the number of sites. Leased lines are typically priced based on the distance between the sites and bandwidth offered. Cross-country and intercontinental links are typically very expensive, making full-mesh connectivity with leased lines very expensive.
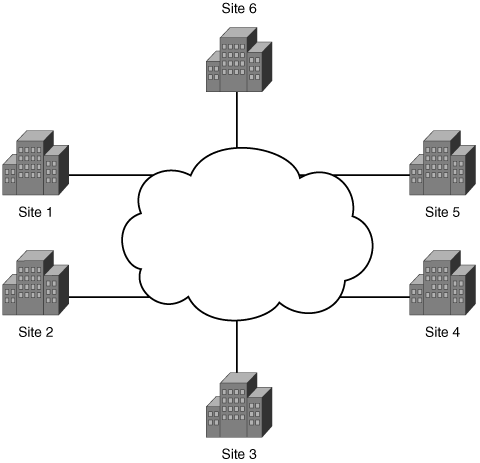
Figure 1-2 shows an alternate method of connecting the same sites of the corporation, this time over a public network such as the Internet. In this model, each site is connected to the public network at its closest point, possibly via a leased line, but all connections between sites are virtual connections. The cloud in the figure represents a virtual connection between the sites, as opposed to a physical dedicated connection between sites in the leased-line model.
Note
A public network can be defined as a network with an infrastructure shared by many users of that network. Bear in mind that the word “public” does not mean that the network is available free to anyone. Many service providers have large ATM and Frame Relay public networks, and the Internet is probably the most ubiquitous public network of them all.
Although connecting the sites over a public network has obvious cost advantages over the dedicated leased line model and provides significant cost savings to the corporation, this model also introduces risks, such as the following:
Data security
Lack of dedicated bandwidth between sites
In the VPN model, the corporation’s data is being transported across a public network, which means other users of the public network can potentially access the corporation’s data and thereby pose a security risk.
The second risk in the VPN model is the lack of dedicated bandwidth availability between sites that the leased line model provides. Because the VPN model connects sites using a virtual connection and the physical links in the public network are shared by many sites of many different VPNs. Bandwidth between the sites is not guaranteed unless the VPN allows some form of connection admission control and bandwidth reservation schemes. Both risks can be mitigated—the next section introduces some VPN technologies that overcome these risks.
In the simplest sense, a VPN connects two endpoints over a public network to form a logical connection. The logical connections can be made at either Layer 2 or Layer 3 of the OSI model, and VPN technologies can be classified broadly on these logical connection models as Layer 2 VPNs or Layer 3 VPNs. Conceptually, establishing connectivity between sites over a Layer 2 or Layer 3 VPN is the same. The concept involves adding a “delivery header” in front of the payload to get it to the destination site. In the case of Layer 2 VPNs, the delivery header is at Layer 2, and in the case of Layer 3 VPNs, it is (obviously) at Layer 3. ATM and Frame Relay are examples of Layer 2 VPNs; GRE, L2TP, MPLS, and IPSec are examples of Layer 3 VPN technologies.
Layer 2 VPNs operate at Layer 2 of the OSI reference model; they are point-to-point and establish connectivity between sites over a virtual circuit. A virtual circuit is a logical end-to-end connection between two endpoints in a network, and can span multiple elements and multiple physical segments of a network. The virtual circuit is configured end-to-end and is usually called a permanent virtual circuit (PVC). A dynamic point-to-point virtual circuit is also possible and is known as a switched virtual circuit (SVC); SVCs are used less frequently because of the complexity involved in troubleshooting them. ATM and Frame Relay are two of the most popular Layer 2 VPN technologies. ATM and Frame Relay providers can offer private site-to-site connectivity to a corporation by configuring permanent virtual circuits across a shared backbone.
One of the advantages of a Layer 2 VPN is the independence of the Layer 3 traffic payload that can be carried over it. A Frame Relay or ATM PVC between sites can carry many different types of Layer 3 traffic such as IP, IPX, AppleTalk, IP multicast, and so on. ATM and Frame Relay also provide good quality of service (QoS) characteristics, which is especially critical for delay-sensitive traffic such as voice.
A connection between sites can be defined as a Layer 3 VPN if the delivery header is at Layer 3 of the OSI model. Common examples of Layer 3 VPNs are GRE, MPLS, and IPSec VPNs. Layer 3 VPNs can be point-to-point to connect two sites such as GRE and IPSec, or may establish any-to-any connectivity to many sites using MPLS VPNs.
Generic routing encapsulation (GRE) was originally developed by Cisco and later standardized as RFC 1701. An IP delivery header for GRE is defined in RFC 1702. A GRE tunnel between two sites that have IP reachability can be described as a VPN, because the private data between the sites is encapsulated in a GRE delivery header.
Because the public Internet is probably the most ubiquitous public network in the world, it is possible to connect many sites of a corporation using GRE tunnels. In this model, each site of the corporation requires only physical connectivity to its Internet service provider, as all of the connections between sites are over GRE tunnels. Although VPNs built over the Internet using GRE are possible, they are rarely used for corporate data due to the inherent risks and lack of strong security mechanisms associated with GRE.
Pioneered by Cisco, Multiprotocol Label Switching was originally known as Tag Switching and later standardized via the IETF as MPLS. Service providers are increasingly deploying MPLS to offer MPLS VPN services to customers. A common principle among all VPN technologies is encapsulation of private data with a delivery header; MPLS VPNs use labels to encapsulate the original data, or payload, to form a VPN between sites.
Note
Creating an MPLS VPN is the most popular application and the primary motivation for deploying MPLS; other applications of MPLS include traffic engineering offering Layer 2 VPN services over MPLS.
RFC 2547 defines a scheme for offering VPN service using MPLS. One of the key advantages of MPLS VPNs over other VPN technologies is that it offers the flexibility to configure arbitrary topologies between VPN sites. For example, if three sites of a corporation all must be connected to one another in a full-mesh (any-to-any) configuration using ATM, Frame Relay, GRE, or IPSec technologies, each site requires two virtual circuits, or tunnels, to every other site. The addition of a fourth site to this full-mesh configuration requires that three tunnels, or virtual circuits, exist at each site, and calls for modification in the configurations at all the sites. If n is the number of sites in a VPN, the configuration complexity for this model is O(n) and the scalability is O(n2). If the same three sites are connected over an MPLS VPN, the addition of the fourth site requires configuration change at only the fourth site. The configuration complexity of this model with n sites is always a constant and is O(1).
The fact that there are virtually no point-to-point tunnels for connecting sites of an MPLS VPN renders them very scalable. Any-to-any connectivity between sites of a VPN and extranet connectivity across VPNs are easy to achieve using MPLS VPNs compared to other tunneling techniques such as GRE. One of the drawbacks of an MPLS VPN is that connectivity between the sites of a VPN is restricted to sites where the provider has points of presence. Although a GRE tunnel could be used across the Internet to extend its reach, GRE by itself has minimal security. We address this issue in Chapter 9, “Network-Based IPSec VPNs.”
One of the main concerns for anyone using any VPN is security of data when it traverses a public network. In other words, how does one prevent malicious eavesdropping of data in a VPN?
Encrypting the data is one way to protect it. Data encryption may be achieved by deploying encryption/decryption devices at each site. IPSec is a suite of protocols developed under the auspices of the IETF to achieve secure services over IP packet-switched networks. The Internet is the most ubiquitous packet-switched public network; therefore, an IPSec VPN deployed over the public Internet can mean significant cost savings to a corporation as compared to a leased-line VPN.
IPSec services allow for authentication, integrity, access control, and confidentiality. With IPSec, the information exchanged between remote sites can be encrypted and verified. Both remote access clients and site-to-site VPNs can be deployed using IPSec. Subsequent chapters focus on the IPSec protocols and deployment models that use IPSec.
As stated previously, VPNs can be classified into site-to-site VPNs and remote access VPNs. Frame Relay, ATM, GRE, and MPLS VPN can be considered site-to-site VPNs because information relevant to the configuration between sites is known in advance at both sides and, more importantly, are static and therefore do not change dynamically. On the other hand, consider a telecommuter who needs VPN access to corporate data over the Internet. The information required to establish a VPN connection such as an IP address of the telecommuter changes dynamically depending on the location of the telecommuter and is not known in advance to the other side of the VPN. This type of VPN can be classified as a remote access VPN.
Remote access to corporate data resources has been a critical enabler for improved productivity, especially for mobile workers. Telecommuters, “road warriors,” and remote offices rely on timely access to mission-critical information in order to maintain a competitive advantage in the marketplace. The reliance on remote access has driven demand for higher capacity connections with extended durations from end users. As a result, increased costs are incurred, primarily in the form of telephony charges, for access to the corporate data.
Although dial-up networking provides a universal local access solution, it can be very expensive for long distance and metered local access calls. Remote access VPN connections provide the best solution, mitigating metered telephone charges while allowing the corporation to leverage new last-mile access technologies such as cable and DSL.
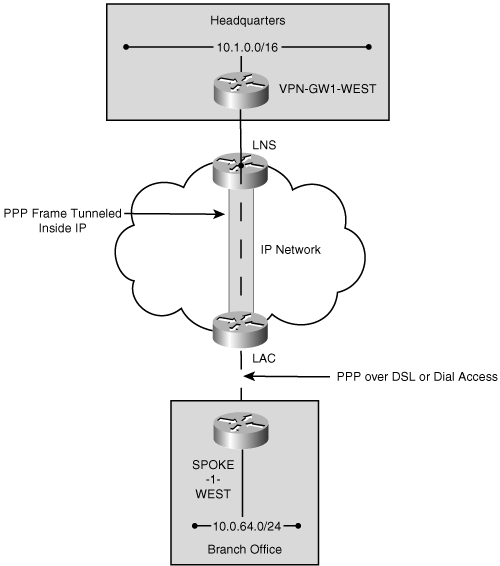
Two of the most common remote access methods for VPN access are Layer 2 tunneling protocol (L2TP) and IPSec. L2TP is an IETF standard (RFC 2661) for transporting PPP frames over IP. L2TP provides dial-up users with a virtual connection to a corporate gateway over an IP network, which could be the Internet. Figure 1-3 shows the L2TP model.
The remote user initiates a PPP session to the closest access server, known as a local access concentrator (LAC) via a local telephone call. The LAC authenticates the remote user and determines which local network server (LNS) will terminate the remote user. An L2TP tunnel is established between the LAC and the LNS, and once the LNS authenticates the user, a virtual interface for PPP termination is created on the LNS analogous to a direct-dialed connection to the LNS.
IPSec is another VPN technology that can be used to connect remote access users. This entire book is devoted to the topic of IPSec VPNs, and remote access is specifically covered in detail in Chapter 4, “IPSec Authentication and Authorization Models.”
In this brief introduction to VPNs, you learned that network designers can choose from a wide range of technologies to create VPNs which can be classified into Layer 2 or Layer 3 VPNs, and further into site-to-site and remote access VPNs. Technologies such as Frame Relay, ATM, GRE, and MPLS are used with site-to-site VPNs. The most common remote access VPN technology is L2TP, and IPSec can be used for both remote access and site-to-site VPNs.