Risks of Social Media
This chapter discusses some of the common risks associated with social media. While everyone has information they want to keep secure, the possibility of sensitive data being leaked is a genuine concern. There is also a risk when the information you share is false, as this can affect your credibility. These and other events can result in public embarrassment, costing you your reputation and possibly clients. We’ll also see how risks such as the loss of data or equipment can be mitigated through various tools available on the Internet and a regular process of archiving important data.
Keywords
Social networking; social media; communications; privacy; security; archiving; retention; theft; misrepresentation
Information in This Chapter:
Risks of social media
You’ll find that the risks you face with social media are the same ones encountered by large organizations. This shouldn’t be too surprising. Even the largest company’s social media presence is handled by a person or small group, with employees using social media in ways similar to you. Everyone faces similar concerns when they’re interacting with others, including embarrassment, misrepresentation, losing data, or sensitive information falling into the wrong hands. The scale may be different, but they’re accessing the same sites, using the same apps, and need protection from the same threats.
When it comes to social media, you’ll often find that the risks you face fall into two categories: technology and the people using it. Technical problems can be dealt with by implementing proper security and having the right tools in place to handle any issues that arise. When it comes to people, you need to change their behavior through policies, training, and communication. The user-generated problems of social media are diminished as a person learns what they should and should not do.
Sources of risk
People recognize risks based on their education and experience. If you’d ask people to identify the risks associated with social media, you’d get different answers related to their expertise or profession. A member of your IT department would see viruses or malware as a major threat and be worried about the impact of data loss to the company. A lawyer would be concerned about potential litigation from such things as discrimination, sexual harassment, and liability from personal messages. A records manager would be concerned about retention of data, data leakage, and sensitive information sharing. An educator or a parent might see cyberbullying as a primary risk and the lack of safeguards to protect children. While some problems may be unique to a person or business, many share similar risks that can be handled in similar ways.
Because everyone focuses on risks that affect them directly, it’s always wise to gather input from a diverse selection of people. Departments in an organization will be able to identify any would-be issues that are unique to them and provide input on how to mitigate those risks and their potential impact. You can also benefit by asking peers, partners, and others who have similar situations.
If you feel improvements could be made in safeguarding yourself from potential threats, you’re not alone. The Ponemon Institute conducted a survey of IT professionals and found that 63% saw social media as a serious business risk, and only 29% felt their companies had adequate controls to manage the risk. All too often, people will jump into using social media without recognizing the pitfalls and taking proper precautions. However, even if you’ve been using social media for a while, you can backtrack and take steps to protect yourself in the future.
Public embarrassment
People are concerned about their reputations and want to be viewed in a positive light by peers, coworkers, family, and the public. It’s basic human nature to want acceptance. For individuals, it makes for a happier life and successful career. For companies, a reputation will affect their ability to do business and impact sales. Because of this, it should come as no surprise that people and businesses are concerned about elements that negatively impact their reputation and see public embarrassment as a major risk of using social media.
As we saw in previous chapters, there are many ways to embarrass yourself and your company. Making derogatory or outrageous tweets, or posting inappropriate content and uncensored blog entries, can be a concern for businesses and individuals alike. Put simply, there are times when you regret what you post. When this happens, delete it and apologize. No one goes through life without making mistakes, so people will generally understand or at least won’t judge you as harshly. An apology shows that you care about how it may have affected others and will go a long way to making amends.
Prior to posting a comment, image, or video on a site, you should consider how it may be viewed by others. If the content compromises the reputation or safety of others or yourself, then don’t post it. As we said earlier in this book, imagine your parents or employer viewing the post and then decide whether it’s appropriate. A moment of consideration will go a long way to avoiding problems.
The content you post can and will be held against you
If you post something that could be seen as threatening, potentially violent, or slanders another person, it could result in serious consequences. The hurtful breakup of a relationship may have you spitting venom about the person, or a bad day at work may have you venting about your boss or job. Even if you meant nothing by it, a coworker could show your boss what you said or be concerned as to whether your comments are an indicator of workplace violence. Similarly, bashing someone online could be seen as libelous and results in a civil suit. Again, if this happens, delete it and make a generic apology that doesn’t contain your original comments. After all, you don’t want to repost what you just deleted. The fact that you deleted the offending remarks and apologized may be taken into consideration by those you’ll have to answer to.
As we’ll discuss later in this chapter, prior to deleting a post that could get you in hot water, make sure you make a copy of it. This could involve making a screenshot, printing the page, or making a backup of the content. If you need to defend yourself, you may need a copy of the post to accurately show what was said and what you did about it.
You should also be aware that social media sites commonly have policies that limit the types of content you’re allowed to post. Sites may forbid offensive or abusive images, video, comments, or messages and may close down your account if you post content to deliberately humiliate someone. As we’ll see in Chapter 7, such actions could be considered cyberbullying or harassment and lead to civil or criminal litigation.
What’s allowed will vary from site to site, and sometimes differ to dramatic degrees. If you look at content communities, you would see that YouTube doesn’t allow pornography, but RedTube (www.redtube.com) is a video sharing site for pornographic video. What’s offensive on one site may not be seen as offensive on others. Before posting or reporting content, you should review the Terms of Service to identify what kinds of content aren’t allowed.
Divorce cases and social media
While any kind of court case might use a person’s social media activity as evidence, it’s often seen in divorces and child custody cases. The posts and comments you make, photos you upload, and other information found on a social networking site could be used to dispute previous testimony, support claims against you, and show relationships to other people. The flirty messages you’ve sent or adding a past lover as a friend could corroborate an accusation of infidelity, while angry posts might strengthen claims that you have a bad temper. The people you’re friends with could lend credence to allegations that you’re associating with people of poor character, and perhaps have a bearing on claims that you’re an unfit parent and should get reduced visitation to children. Regardless of whether it’s true, as a documented record of your thoughts, feelings, actions, and intentions, social media can tell the courtroom a lot about you.
It’s increasingly common to see a person’s online activity used as evidence in divorce cases. In 2010, the American Academy of Matrimonial Lawyers (AAML) reported that 81% of divorce lawyers saw an increase in evidence from social networks. Of the various sites where evidence was acquired, Facebook was the most commonly used, with 66% of the lawyers finding it was a primary source, followed by MySpace (15%) and Twitter (5%). In 2013, the same organization revealed that 59% of divorce lawyers found an increase in evidence from dating sites, with 64% saying that Match.com was a primary source, followed by eHarmony (9%). You need to be careful about what you do online during a divorce, because someone may very well be watching.
Evidence isn’t limited to the content you post. Your profile information may also be used to show dishonesty. In the 2013 survey by the AAML, 57% of divorce lawyers cited a person’s relationship status as the most common piece of evidence, followed by Salary and Occupation (15%) and Parental Status (7%). Alton Abramowitz, president of the AAML explained that “Identifying yourself as single when you are not, or listing that you have no children when you are actually a parent, can represent some key pieces of evidence against you during the divorce process.”
In terms of securing social media accounts, divorce and child custody cases are unique. During a divorce, the mutual friends of a couple will often split off into different camps, choosing which person they want to support and continue a friendship. Even if you’ve gone through your settings to prevent information from being public, and removed your estranged spouse and his/her family as friends, you probably haven’t unfriended the mutual friends of you and your ex-spouse. Your ex can still go through those people to see what’s on your Timeline, profile page, or other content you’ve made available. While you could remove all of your mutual friends, it gets more convoluted when your children have been added as friends to your account. You’re probably not going to remove them, so you’re left with the open possibility of your ex-spouse having access through your children.
While honesty is the best policy, it doesn’t mean that you should allow everything to be on display. Discretion is the key. As we suggested when looking for a job, sanitizing your social media sites you use is a good step to putting your best foot forward. You should remove any posts, photos, and information that could potentially be used against you in divorce proceedings. In your profile information, you should review what’s said and make certain that it’s accurate or removed. Your own words, contents, and actions can be used to support accusations against you, so you need to be careful about what appears on your social media.
To prevent your ex-spouse from seeing everything on your account, modifying the information, and possibly posting as you, you need to prevent others from logging with your password. During the marriage, you’ve probably used the other person’s computer, meaning your passwords may have been saved in the browser. Also, your husband or wife may know your password or at least some of the common ones you use. Because of this, as soon as the relationship ends, you should change your password immediately.
Removing videos from YouTube
Old videos and photos of us being silly can be a major source of embarrassment. While anyone might be mortified at being featured in an online video, some are better able to keep it somewhat private. In 2013, the Tajikistan President Emomali Rahmon had to relive awkward moments from his son’s 2007 wedding, when a home video was uploaded to YouTube under the title of “Drunk Tajik President Sings a Song.” The video shows the leader merrily dancing and singing out of tune and was viewed almost 300,000 times. To prevent people in his country from seeing the video, YouTube access was blocked in Tajikistan.
Since most of us can’t block content in this way, we have to settle with privacy controls on the videos we post. On YouTube, you can set a video to any of the following visibility levels:
• Public, which allows anyone to view the video.
• Unlisted, which allows people to view the video if they have the link. It won’t appear in search results or YouTube’s public spaces.
• Private, which allows you and up to 50 other people you invite to view the video. Like the unlisted setting, it won’t appear on your channel or search results.
Even if a video is unlisted, people can still view it if they know how to find it. You or another person may have shared a link on other sites or acquired it via email. Your settings also won’t stop people from viewing and sharing any copies that have been downloaded from YouTube and uploaded elsewhere. To change the privacy setting of a video on your YouTube channel:
1. Log on to YouTube and go to your Video Manager at www.youtube.com/my_videos.
2. Choose the video you want to change the privacy settings for, and click the Edit button.
Of course, these settings only apply to the videos you uploaded to YouTube and not those belonging to other people. If you’re uncomfortable with the content of a video, you can report it by flagging it as inappropriate. In doing so, YouTube staff will review the video to determine if it goes against their community guidelines and should be removed, or should be restricted so that younger users can’t view it. To flag a video, you simply click on the flag icon beneath the video and check the option that applies to your complaint. Options include the video containing objectionable content or that it infringes on your rights.
You can also contact the person who posted the video and ask them to remove it. If they don’t remove it or you’re uneasy about contacting the person directly, you can file a complaint with YouTube through their Policy and Safety Hub at www.youtube.com/yt/policyandsafety. There are different kinds of complaints you can make, including copyright complaints where someone has copied a video that you created. If you’re identifiable within a video, you can also file a privacy complaint. In doing so, the request will be reviewed, so the video can be removed from the site.
Removing photos and tags that others post on Facebook
Embarrassing photos can cause problems for businesses and individuals alike. A person may indicate where they work on their profile page and then upload a photo that doesn’t mesh well with the corporate image. Perhaps it’s a silly image that looks unprofessional, shows the employee drinking or involved in drunken antics, or depicts something unflattering or even offensive. Depending on the picture, once it’s associated with an employer, it could damage the brand or reputation of the company.
Even if an employee is mindful of the photos they upload, others may not be. You may appear in a photo taken by another person that’s uploaded to Facebook. The photo might focus on you or show you in the background, where you would have gone unnoticed if someone hadn’t tagged the photo and identified you. By tagging you in the photo, others will see who you are and be able to follow the tag to your profile page.
If you are tagged by someone in an embarrassing photo, you can remove the tag yourself. Untagging a photo is done from the Activity Log of your account. After logging onto Facebook, do the following:
1. Click on the Privacy Shortcuts icon, which is shaped like a padlock in the upper right-hand corner of the page.
2. From the menu that appears, click Who can see my stuff?
3. When it expands click on the Use Activity Log link.
4. On the left side of the page, click Photos. Alternatively, to only see the photos of you, inclusive to ones you’re tagged in, you can click the Photos of You link.
5. Look through the list of photos until you see the one you don’t want to be tagged in. Click the checkbox beside the photo, so it appears checked.
6. At the top of the page, click the Report/Remove Tags button.
7. When the box appears, select the option you want:
a. I want the photo untagged, which removes the tag from the photo.
b. I want the photo untagged and taken down, in which the tag is removed and you can ask the person to take down the photo.
Once a tag is removed, the photo no longer has a link indicating you in the picture. However, the photo is still visible to others. People will be able to see it in the album of whoever posted it, when it’s shared, and may still appear in search results. If the photo is truly embarrassing or damages your reputation, send a request to remove the photo so that no one will see it.
Removing posts on Facebook
Facebook also provides ways to report other people’s posts as abusive or offensive. When you click the Report Story or Spam link, you have the option of clicking undo, hiding all stories from that person, or submitting a report (Figure 6.1). If you click submit a report, the post is flagged for review.
Hiding content
There may be content that you find offensive, but others may not. In such a case, you may want to hide the post so that you and others don’t see it on your Timeline. As mentioned in the previous section, when you hover your mouse over a post on Facebook, an image of a downward arrow appears. As seen in Figure 6.1, if you click on the arrow, a menu appears with a link titled Hide…. When you click on it, the post is hidden and a message will appear giving you the chance to unhide it and the option of hiding all posts from that person.
When you hide content in this way, it isn’t deleted. You may not see it, but it is still available on the poster’s Timeline. To view your Timeline, click on your name in the upper right-hand corner of Facebook and you’ll see the status updates and other content you’ve posted. To hide one of your posts:
1. Hover your mouse over a post. An icon that looks like a pencil will appear in the upper right-hand corner. Clicking on this icon, a menu will appear.
While the post will no longer appear on your Timeline, it will still appear in searches, news feeds, and other areas of Facebook. If you want one of your posts to be completely removed, then instead of clicking Hide from Timeline, you should click the Delete menu item.
Reporting abuse
In addition to the methods already mentioned, sites commonly have an email address or a process in which you can report abusive users, such as those who are harassing you. The methods of reporting abuse vary from site to site, with some providing email addresses and others using online forms that you use to submit a report. Some resources to report abusive behavior include:
• Twitter, https://support.twitter.com/forms/abusiveuser
• Facebook, www.facebook.com/help/reportlinks
• LinkedIn, [email protected]
These aren’t your only options. You should always contact the police if threats are made, and/or you’re concerned about your safety. A threat is a threat, and there’s no difference between threatening someone in person or online. By contacting the authorities, an investigation can be conducted and the person may be charged.
If you see content that is illegal, you should also make an effort to report it. For example, if someone uploaded child pornography or posted information on child prostitution, molestation, or sexual tourism involving children, you should contact authorities immediately. In the United States, you can make an online report through the National Center for Missing and Exploited Children’s CyberTipline at www.missingkids.com/cybertipline. In Canada, you can make an online report to the Canadian Centre for Child Protection at www.cybertip.ca. Once a report is made, the appropriate law enforcement agencies will be notified.
Once it’s out there, it’s out there
There’s a common belief that once something is on the Internet, it’s there forever. The permanence of social media requires you to accept that once data is released online, it may be available forever. While not necessarily true, it can sure seem like it, especially when it’s embarrassing. The Internet can have a long memory for moments you wish were forgotten.
Every year, you’ll see new photos on social networking sites of drunken parties and young women flashing a crowd at Spring Break or Mardi Gras. While it may seem unlikely when your entire life is ahead of you, such photos can haunt you years later, especially when a potential employer, significant other, or your child sees how you led your life. Such photos can be shared, copied, and downloaded, making them available for years. Even if they aren’t online now, they may be later.
A reason why data has such longevity on the Internet is due to the ease of sharing it. In 2012, a girl posted a sexual image of herself on a social networking site, which was then distributed through text messages to other students at Golden Bay High School in New Zealand. The parents expected the school to aid their daughter, but since the images were posted outside of school hours, there was little they could do. Unfortunately, as the images are shared, there are more and more copies that can be further distributed, making them harder to get rid of. The more scandalous or salacious the content, the more likely it won’t be deleted.
Embarrassing content can create significant problems even years later. In 2008, Carmen Kontur-Gronquist was the Mayor of Arlington, Oregon, when lingerie photos taken of her at a fire hall were noticed on MySpace. Even though the photos were taken 4 years earlier, it resulted in a recall election where she was voted out of office.
A similar problem was encountered by Stacy Snyder, who posted a photo of herself at a party, drinking and wearing a pirate hat. The caption of the photo was aptly titled “Drunken Pirate.” Years later, the photo was discovered on MySpace. Days before her graduating as a teacher from Millersville University School of Education, she was denied her degree. The school felt that she was promoting drinking online, where underage students would be exposed to it. They claimed she wouldn’t have received the degree even without this incident, but Snyder sued on the grounds that her First Amendment rights had been violated, and she had done nothing illegal. Unfortunately, in 2008, the judge rejected her claim, stating that the photo wasn’t protected because it didn’t relate to matters of public concern.
While this chapter discusses a number of ways to remove data from social media sites, the process can be difficult. In some cases, you may even have to bring in legal assistance to fight the battle in court, making it a lengthy and an expensive process. Even when information no longer appears to be online, it may still be there. As we discussed earlier, content on social media sites may be hidden or you may be blocked from seeing it. For example, in 2012, Afghanistan blocked YouTube in an effort to prevent people from watching the film Innocence of Muslims. Even though the content has disappeared to some, it didn’t mean it was gone.
The best way to avoid embarrassing photos, videos, and comments from coming back to haunt you is to be proactive. Carefully consider what you’re uploading or writing before you make it available to others. If you believe that it may be around forever, you may think twice about posting it in the first place.
False information
While the Internet is a great resource for information, not all of what you see is true. Beyond the hoaxes we discussed in Chapter 5, people will make false or misleading claims, which are then shared with others. Because a friend or someone you follow has shared the information, it can lend credibility to it, making it seem even more believable.
Often, the user-generated content and crowdsourced information on social media sites lack any process to verify the facts or will be available for public consumption before the errors have been edited out. Sites like Wikipedia rely on other users reading the articles and identifying errors that are then edited out. While the article will eventually become a valid source of information, people consider it to be a valid source between the time it’s written and the false information is removed.
This isn’t to say that social media isn’t a vital part of sharing information. According to a report by the Pew Research Center, as events were unfolding during the Boston Marathon bombing in 2013, 6% of people used social network sites to keep in touch with friends and family. The report also showed that a large number of people got their news from social networking sites. Twenty-six percentage of people overall got their information from sites like Twitter and Facebook, and younger Americans (56%) aged 18–29 were more likely to use social media to obtain updates. For many people, social media is an important source of the latest information.
Unfortunately, while much was said, quantity doesn’t always mean quality. Due to the competitive nature of news outlets trying to report a story first, journalists covering the bombing saw false information on social media sites and reported it as fact. An example was a campaign on Reddit called “Find Boston Bombers,” in which amateur sleuths attempted to identify the bomber. It turned into a witch hunt, where innocent people were misidentified as suspects and targeted by news outlets and social networking users as having a connection to the attack. One “suspect” on Reddit was Sunil Tripathi, a missing student from Brown University whose family was harassed after the misidentification. During the furor of dangerous speculation, Tripathi was found dead due to unrelated circumstances. The quality of information on social media sites can be debatable, sometimes dubious, and quickly compound a tragedy.
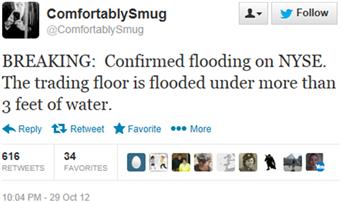
This isn’t the only time-sharing false information that had serious consequences. As seen in Figure 6.2, during the onslaught of Hurricane Sandy, Shashank Tripathi (@ComfortablySmug) tweeted false information that caused additional panic. While not the only one spreading lies that were retweeted hundreds of times, it was reported by CNN and New York Magazine as truth. The lies resulted in him losing his job as a congressional campaign manager and facing the possibility of criminal charges.
In 2011, Gilberto Martinez Vera (@gilius_22) and Maria de Jesus Bravo Pagola (@MARUCHIBRAVO) started a series of lies about gunmen holding children hostage at a school in Boca del Rio, Mexico. The rumors were spread on Facebook and Twitter and mentioned multiple schools, causing a panic especially among parents of students. The two were later jailed on charges of terrorism and sabotage.
Every day you can find false information shared and retweeted on social media sites with little concern to its accuracy. While information flows quickly online, verifying it can be slow. A tweet or post can go viral in a short time, but it will take a while for comments to appear about how the claims are false. To ensure you’re getting the right information, it’s wise to take a moment to do a quick search in Google or Bing to see if what you’re reading is true. If you simply share bogus information without verifying it, your credibility will suffer. If you make serious claims that are false, you could lose your job and face civil suits or criminal charges.
Misrepresenting yourself
The Internet gives a false impression of anonymity, and many people use it to create an artificial persona. Many people will tweak their age to look a little younger or change minor details to appear more interesting. Others will go farther. A person may provide false information about their experience, education, or personal details to misrepresent themselves to potential employers, clients, or romantic partners.
Omitting information or providing some misleading information may be used as a defensive measure. For example, rather than providing the city you live in, you might exclude that information from your profile or say you live in a nearby larger city. However, there is a difference between protecting yourself and creating a façade.
If you use dating sites or social networking to meet others, you’ll want to stay honest. If you misrepresent yourself, eventually the ruse is discovered when the other person meets you. As you associate yourself with others on the basis of similarities and common interests, you’ll also miss out on making genuine connections if the facts about you are false.
In chat rooms, it’s common to find people who have created a false profile, complete with fake pictures and personal details. In some cases, it’s harmless. The false information may be used as a defensive measure to keep others at a safe distance, or the person may be uncomfortable about his or her appearance and post a picture of someone more attractive. Of course, the person may have more sinister reasons. Serial killer John Edward Robinson met many of his victims in chat rooms and became known as the Internet’s first serial killer. As we’ll discuss in Chapter 7, pedophiles, rapists, and other predators may introduce themselves to victims through social networking sites or chat rooms prior to meeting them. The false persona may be used on social networking or chat room sites to deter you from finding a criminal record or an inclusion in a sex offender registry.
If you use sites like LinkedIn to interact with colleagues or meet potential employers, you’ll want to be honest about your education and experience. If false credentials are used as part of your application for employment, you can be fired for misrepresenting yourself. Again, whether it’s in person or online, honesty is the best policy.
Misrepresenting your business
Under no circumstances you want to misrepresent your business on social media sites by making false claims about your company or its products. Just as consumer protection laws prohibit making misleading or deceptive claims about products and services in traditional media, these same laws apply to false claims made online. Not only can you be subject to litigation, but the negative public relations of showing you can’t be trusted will damage your brand.
You also don’t want customers or fans making false claims. If a person makes a comment that misrepresents your business, you should address the comment and correct them and/or delete the misleading comment. For example, let’s say someone said your company’s product was 100% environmentally friendly, but it was incorrect or there was no research to support the claim. Alternatively, a fan of your brand might make negative comments about a competitor that you know is false. Leaving such comments unaddressed is essentially the same as endorsing it as being valid. As a business, you need to be responsible for the claims you make and those of people posting on your page.
False information isn’t necessarily bad
While falling for a hoax or spreading false information can make you appear foolish, a good campaign can use false information to promote a product or brand. Every year, the BBC, Google, and other companies create false commercials and news reports as a joke for April Fools Day. When it’s good-natured fun or well crafted, most people laugh off the hoax and appreciate how it was done.
A great example of how false information can promote a brand is seen in the 2007 campaign in which a ghost was seen in the window of a house in downtown Toronto, Ontario. The ghost of the young girl was actually an image from a holographic projector, which passersby could see skipping, walking, and doing other movements. In the second week of these sightings, a video of the apparition was posted on YouTube, Google Video, and other sites. It quickly went viral and became the topic of discussion on blogs and various sites. A second video was released a short time later, and the two generated an excess of 2.1 million hits. When the address of the house was “leaked,” even more people visited it, hoping to catch a glimpse of her nightly appearance.
After 3 weeks of the engineered phenomena, the ghost was seen in the window holding a sign that said “Get scared more often” with the logo of a subscription horror channel called Scream TV. The paranormal promotion was advertised as a hoax in television commercials, online, and by media outlets covering the story. For a cost of $50,000, the campaign resulted in an immediate subscription increase of 35%.
Another horror example that used the Internet is The Blair Witch Project. The 1999 movie was the first movie to use the Internet as a primarily target for marketing, spreading rumors in chat rooms, message boards, and other online venues that the film was authentic found footage. The claims were “verified” as legitimate by a Web site, which provided manufactured television news clips about the disappearance of people in the movie. Box office sales resulted in it becoming one of the most profitable independent movies of all time. Results like this show that if you can make the false information entertaining, it can have a positive effect on what you’re selling.
Information leakage
One of the most significant risks for businesses and individuals is sensitive information being leaked. There are many kinds of information that could result in financial losses or embarrassment if it was shared with the wrong person or publicized online. Such information may be proprietary, such as trade secrets or a new product under development being revealed too early, or could reveal information that compromises security. Businesses and their employees may also be at risk by personally identifiable information being revealed. It can be dangerous when people reveal sensitive facts about themselves, the business, or their work.
Be clear about what’s private
Since revealing company information can jeopardize your job and devastate a business, it’s important to understand what can and can’t be discussed in public. Training and policies can assist in this regard, showing employees how they should handle the information available to them in their day-to-day work. If you’re unsure what you can share, then follow a basic rule: if it’s not in a press release, don’t discuss it.
You should determine whether your organization uses an information classification scheme, which categorizes records and data based on their sensitivity. Strict policies and procedures may exist as to what kinds of information can be shared with the public and under what circumstances it can be accessed or released to others. For example, information may be categorized as follows:
• Secret, which restricts who can view the data to a small people with a high clearance level.
• Confidential, in which information is restricted to people who need to know it. This might include client or employee information like Social Security Numbers, medical history, criminal records, or other confidential data. It may also be restricted under legislation or regulations, such as the Sarbanes–Oxley Act, Payment Card Industry, or privacy acts that protect personal data.
• Internal, which means the data can’t be shared outside of the organization without specific permission. This might include such things as employee information (addresses, phone number, etc.), corporate policies, and so on.
• Public, which means it is unclassified and has few or no restrictions. Such information can be disseminated to the public and could include such things as press releases, public job postings, promotional material, and so on.
Organizations may also use a more basic scheme, consisting of classified and unclassified data. Classified information may consist of information about technology being used and current and upcoming projects. Unclassified information might be anything that can be discussed openly with partners, vendors, or even the public. Whatever method your organization uses, it’s important to identify it before you accidently reveal something that could cost you your job.
Providing too much information
Everyone’s had the experience of getting or giving a little too much information. Someone may tell you the indiscrete details of a personal experience or some office gossip they heard at the water cooler. Some people have trouble keeping their own information private, so you can understand why a business would be concerned about the confidentiality of corporate data.
The terminology that strangers are “friends” on social networking sites can lull you into a false sense of security. You can feel like you’re addressing your family and friends and forget that a post may be read by coworkers, acquaintances you barely know, or even strangers you’ve added to play games. People using their personal accounts to discuss work-related information can cause dramatic problems for themselves and the business. They may cause damage to the corporate image by complaining about staff or the brand itself, violate privacy by mentioning employees or clients, or mention a key piece of information that a competitor may use to their advantage. A tweet or public post can be displayed for the world to see, and even more secure posts may be copied or shared for others to see. What you say on social media can be a public announcement.
Information security is important on both a personal and work-related level. A 2010 survey conducted by the Consumer Reports National Research Center found that 38% of people posted their full birthdate and 8% posted their street address. The same study projected that approximately 1.7 million online households had been victims of identity theft over the previous year. The number of victims is not surprising when you realize how transparent some people’s personal information is on social networking sites.
As we’ve seen throughout this book, the tidbits of information you reveal about yourself or your work can be compiled into a telling profile. As we’ll see in Chapters 7 and 11, the address on a LinkedIn profile, a birthdate on your Facebook page, and other fragments of information can be useful for the purposes of identity theft or to identify passwords and other security information that can leave you and your organization vulnerable.
Small bits of information can be accumulated from any number of sources, even the most unlikely ones, and used to access other information. During the 2008 US presidential election, vice presidential candidate Sarah Palin’s email account was hacked by David Kernell, the son of Memphis Democratic state representative Mike Kernell. The hacker obtained Palin’s birthdate and other personal details from a Wikipedia page and then used the information to reset the password with Yahoo!’s account recovery for forgotten passwords. The password was posted by Kernell on the site 4chan, and screenshots of the email account were uploaded to WikiLeaks. What started as a few innocuous factoids became clues to hack her account, so that private emails could be leaked to the public.
WikiLeaks
Leaking information can be done in a number of ways. It may be done directly, as in the case of someone writing a blog or post and mentioning sensitive facts about the organization or its employees. It can also be done through traditional methods, where the data is given to a journalist who then parrots what you’ve provided or does additional investigative reporting. With the Internet, people can now leak information to third-party sites that make the information available to everyone.
One such site that has received much publicity and been the focus of controversy is WikiLeaks (www.wikileaks.org). Since 2007, the whistle-blowing site has published classified and sensitive material belonging to government and high- profile organizations. The site provides a secure drop box, where people can upload files anonymously, which is then reviewed by members of their staff and volunteers who are part of mainstream media outlets or journalists. The information is then published on their site, but unlike many wikis cannot be edited by visitors to the site. This keeps the content unaltered from its intended publication.
Sites that post leaked documents are seen as a serious security risk. In 2010, WikiLeaks released a list of infrastructure sites that was compiled to protect US interests from terrorist attacks. It’s one of numerous incidents that have led to WikiLeaks being called a threat to national security. Another issue is that some information has been provided by hackers. In 2012, WikiLeaks began publishing over 5 million email messages belonging to the global intelligence company Stratfor. In 2011, a hacking group called Anonymous admitted to stealing email and credit card information from the company and uploaded the data to WikiLeaks.
While such sites are an obvious risk for organizations and governments, they’re also not without merit. Content on WikiLeaks has been widely reported by mainstream news. In 2010, WikiLeaks released classified footage taken by US Apache helicopters on July 12, 2007 showing civilians being injured or killed in air-to-ground attacks. The video showed a group of eight men (including two Reuters war correspondents) being shot at with 30 mm cannons. After the first airstrike, one of the correspondents was dead and the other was severely wounded and tried crawling away. In an act of compassion, a father and his two children saw the wounded man and decided to pull over, and several others tried to carry the correspondent into their van. When the helicopter opened fire again, the father was killed and his children were seriously wounded. Audio on the video shows the children were denied evacuation to the military hospital. Instead, they were given to Iraqi police and sent to a local hospital. The soldiers are heard blaming the Iraqis, saying “it’s their fault for bringing their kids into a battle.” After the incidents, Reuters requested the video under a Freedom of Information Act request but their request was denied. The US military defended the incident as correct actions taken against insurgents. It wasn’t until the classified video appeared on WikiLeaks that the truth was revealed publicly.
When you leak information to the public, it’s important to realize that you’re putting your job at risk and making yourself vulnerable to civil litigation and criminal prosecution. In May 2010, Bradley Manning was arrested for leaking the Baghdad airstrike video and hundreds of thousands of other documents to WikiLeaks. It is the largest leak of classified documents in the US history. The FBI discovered his involvement through a hacker named Adrian Lamo, who confided that Manning admitted in their online chats to leaking the information. In 2013, Manning pled guilty to a number of lesser charges, and at the time of this writing is facing trial. If convicted, he could face life imprisonment.
Corporate espionage
Governments and corporations will use social media to obtain intelligence. While a government agency will spy on a person or group of interest for national security reasons, corporate espionage is used to gather and analyze on competitors for commercial reasons. By obtaining privileged data that’s available to insiders of a company, a competitor gains a clear advantage over other businesses in an industry.
Gathering sensitive data doesn’t necessarily require finding a disgruntled employee or whistle-blower that’s ready to hand over the keys to the kingdom. Often, anyone will do. By doing a simple search for a company name, you’ll find numerous accounts where people mention their place of employment. You can then follow their tweets and posts to scrape together key pieces of information that can be used to your advantage. Often, it involves getting the big picture by gathering smaller pieces of a puzzle.
In 2011, the security company CyberRoam released information about an online study they conducted on 20 businesses over a 6-month period. By looking at the tweets made by the sales director, a department head, and designers of a company in Singapore, they saw that several people were looking elsewhere for employment and salaries were not being paid. Obviously, if this was public knowledge, you would think twice before applying for a job, being a supplier or even being a customer. CyberRoam was able to accurately predict they’d file for bankruptcy.
Another company in the study targeted the financial director of a New York firm. Finding that he was recently divorced, a male consultant for CyberRoam created a fake Facebook account and posed as a female. By appealing to loneliness and desire for romance, confidential information was obtained. In initial chats, the financial director mentioned that he couldn’t disclose the revenues of his company but later revealed that they were $6.5 million.
Such confidential information doesn’t have to be obtained through full-time employees of the company. It can be acquired through partners, vendors, temporary employees, volunteers, or anyone else who has inside knowledge of the company. Consider how many businesses take coop students from high schools, colleges, and universities. The students may only be at an organization for a short time, but may be exposed to volumes of information. If they work in an IT department, they gain knowledge of the network, know procedures, and may even have administrator passwords. Students may be aware of upcoming projects, the release dates of new products, or overhear information that indicates the stability of the business.
To protect your organization, it’s important that employees know that they shouldn’t discuss business-related information through their own accounts. The disclosure of information should only come through official channels, as in the case of an official social media account. By employees not mentioning anything that’s business-critical, or involving ongoing or upcoming projects, your organization will be much safer online.
Retention and archiving content
Organizations are often required to retain and archive records for specific periods of time. Even if regulations mandating the retention of records don’t apply to you, it’s still a good idea to keep copies of your social media. If you ever needed to refer to an old post or a tweet that was deleted, such as for evidence in a legal case or to verify something, it is useful to have a snapshot of what you did online.
For many organizations, retaining records is a must. As we’ll discuss further in Chapter 8, public companies are required to comply with legislation like the Sarbanes–Oxley Act of 2002, which defines what records are to be stored and for how long. It doesn’t limit this to paper records. Information is information, which is why any business records, including those in an electronic format are to be saved for not less than 5 years.
If your business has a records manager, it is wise to discuss the obligations for archiving social media content. They may be able to provide you with a records retention schedule, which outlines how long a record has to remain active and why it needs to be an active record. In some cases, the records need to be available for certain lengths of time for legal or fiscal reasons, while in other cases, it needs to be retained as a historical record for a specific time or indefinitely.
Beyond individual organizations, there are also institutions that archive social media for historical purposes. In January 2013, the Library of Congress announced that it would be archiving the tweets sent by Twitter users. In 2010, an agreement was signed with Twitter, allowing them to access tweets dating back to 2006, when Twitter was founded. While there are an estimated 400 million tweets sent each day, the daunting task of archiving an estimated 170 billion tweets for posterity is done through a social media aggregation company in Boulder, Colorado called Gnip (www.gnip.com). By keeping these tweets archived, they provide a snapshot of our interests, concerns, and activities in the twenty-first century.
There are different ways of keeping records of social media activity. According to the Environmental Protection Agency’s (EPA) guide entitled InterimGuidance for EPAEmployees who are Representing EPA Online Using Social Media, the records created or received by the agency “using social media tools must be printed to paper and managed according to the applicable records schedule in a recordkeeping system.” As we’ll discuss later, making copies to a hard disk, which can then be backed up with other data is another option. Finally, there are services on the Internet that can be used to back up your social media, so that the content of any given time can be referred to when needed.
eDiscovery
The content posted on social media sites is subject to the same laws and regulations as other information. Because a record is a record regardless of its form, it may be used as evidence in criminal or civil legal cases. Electronic discovery or eDiscovery is the process of searching, locating, and securing information for the purpose of using it as evidence.
Digital information is extremely useful as evidence. When you save a file, it’s time-stamped to show the date and time of its creation and the last time it was accessed. Such files are also easy to search, unlike paper documents that need to be scrutinized manually, and can be quite revealing. People tend to be less reserved when conversing in email, chat rooms, or other electronic methods of communication. In many cases, people will reveal information that they normally wouldn’t through traditional documentation.
As social media has become a popular medium for communication and publishing information, it has also come into focus as important evidence. In 2011, Gartner, an information technology research and advisory company, predicted that by the end of 2013, half of all companies will have been asked to produce social media content for eDiscovery. Even in personal law suits or court cases like divorce or child custody battles, the information you post on social media sites can be used as evidence.
If you don’t have the information backed up and available when needed, you could face strict penalties. For example, the Sarbanes–Oxley Act has strict regulations regarding information that may be used in an investigation, including documents in an electronic format. It imposes fines, imprisonment, or both for “altering, destroying, mutilating, concealing, falsifying records, documents, or tangible objects with the intent to obstruct, impede, or influence a legal investigation.”
Inappropriate use of social media is a major problem for organizations, and many employees have been fired for mistakes they’ve made. If someone made a libelous comment about you, you wouldn’t want the evidence disappear by someone deleting it. At its most basic level, printing out the page containing the comments or taking screenshots could be useful evidence to support your claim. Similarly, if an employee deleted content that was contrary to confidentiality agreements, social media policies, or legislation, you might be unable to prove it occurred if it was removed from the site. Archiving the site, printing, or taking screenshots will be necessary to support any discipline taken against the person.
If you’re the person who needs to defend against something that was posted or tweeted, it’s equally important to have an accurate copy of any content that is relevant to the accusations. This would include a copy of the information, as well as dates it was posted and deleted, and actions taken afterwards, such as an apology or updates that were posted.
Backing up social media
A backup is a process or system where a copy of the data is stored separately from the original, protecting you from potential data loss. While you’re probably familiar with backing up hard disks, it’s also possible to back up your social media content. There are many tools available to store copies of your data online or download it to your computer.
While you might think that the content you upload is safe, this might not be the case. There are no guarantees that a social media site is backing up the photos, videos, and other information you’ve posted. If a server storing the data failed, it might be gone for good.
As we’ll discuss later in this chapter, once you’ve downloaded a copy of your social media content, you should include it in your backups. Doing so serves multiple purposes. First and foremost, if anything happens to the data, you can restore it from the backup. It also provides an archive of information from different dates, allowing you to view snapshots of your social media experience.
Archive Facebook
Facebook provides a feature to download a copy of the content you’ve posted online. This includes status updates, photos, videos, messages, chat conversations, information from your profile, and more. To download your Facebook content, follow these steps:
1. After logging onto Facebook, click on the gear-shaped icon in the upper right-hand corner of the page.
2. Click General in the left pane of the page.
3. Click on the Download a copy of your Facebook data link.
4. When the Download Your Information page appears, click the Start My Archive button.
5. Enter your password when prompted, and click the Submit button.
6. Click the Start My Download button when prompted.
7. A dialog box will appear informing you that an email will be sent to the address associated with your account when the download is ready. Click Okay.
8. Check your email, and when you find the email sent by Facebook, click the link to download your data.
9. When the page to download your data opens in the browser, click the Download Archive button.
The link you receive in the email from Facebook will only work for a few days. After that, you’ll need to repeat the process again. The content will be downloaded as a compressed zip file and can be quite large depending on the amount of photos and other content you’ve published since joining Facebook.
Once you’ve downloaded and extracted the contents of the zip file to a folder, you can open a file called Index.html to navigate between your settings, photos, and other content. The Web page opens in your browser and provides a quick and concise way of viewing your information and finding specific content in your profile.
Archive Twitter
Twitter also provides a feature similar to the one we just discussed. In archiving your Twitter account, every tweet you’ve made since starting your Twitter account will be available to view on your computer.
1. After logging in, click the gear icon in the upper right-hand corner, and click Settings on the menu that appears.
2. Scroll to the bottom of the page. You’ll see a section entitled Your Twitter Archive.
After following these steps, you’ll be emailed a link that allows you to download all of your tweets. After clicking the link, the page that appears has a button you’ll click to download your Twitter content in a compressed zip file. By opening a file called Index.html in the zip file, you’ll see a graphical display of the number of tweets you’ve made each month and can navigate between the months to view tweets you’ve made.
Multisite third-party tools
There are a number of tools and services on the Internet that can be used to backup your content. Many social media sites provide Application Programming Interfaces (APIs) that developers can use to access services and content on the sites. The backup tools query your account through the APIs, gaining access to the data so it can create a copy of new and updated files. Before choosing a tool, it’s important that you compare features and identify how often it backs up data, what it backs up, and the sites it can access. Not all of services are the same, so it will require some shopping.
A popular social media backup site is Frostbox (www.frostbox.com). Using the site, you can create a copy of multiple social media accounts, including Facebook, Twitter, LinkedIn, Foursquare, Flickr, Instagram, and Gmail. The backups are performed weekly and stored securely on their server. The site also provides other tools, such as social media dashboards for monitoring various sites from a single location.
Backupify (www.backupify.com) is another online service that will automatically back up Gmail, Facebook pages, Twitter accounts, Google Sites, and more. The data is backed up to their site, but information can be exported. For example, Twitter feeds can be exported to PDF files, allowing you to keep a copy on your local computer. Should you need to restore the data, it provides an easy one-click restore. The free version of the service allows you to back up to three services on a weekly basis, but subscriptions are available for daily backups and an increased number of sites.
While the previous services back up your content to their site, SocialSafe (www.socialsafe.net) is an application that backs up social network content to your computer. After installing it, you can authorize SocialSafe to connect to numerous sites and back them up to your machine. The sites you can backup through it include Facebook, Twitter, LinkedIn, Google+, Pinterest, your blog, and others. New updates to your social networking can be automatically downloaded and organized for your review. As seen in Figure 6.3, by clicking on icons in the left pane, you can search through content, navigate through all of your social network interactions by date, or view photo albums from all sites using a single interface. It also provides information on the most popular photos, posts, days with the most activity, and other information about your social network use.
Other tools for individual sites
In addition to the multisite tools, there are some useful tools for individual sites. Downloadr (www.janten.com/downloadr/) and FlicrEdit (www.sunkencity.org/flickredit) are tools for downloading copies of the photos you’ve posted on Flickr. Both will allow you to search and backup photos, but FlickrEdit also provides the ability to edit and upload new versions of the picture.
Free YouTube Download (www.dvdvideosoft.com/products/dvd/Free-YouTube-Download.htm) is a tool that allows you to save and convert videos found on YouTube. This not only includes individual files, but all the videos from a playlist or channel. You can convert them to MP4, AVI, and WMV formats and also save the download history of the video.
Loss of data/equipment
Even if you’ve taken steps to archive content, it may not be completely safe. If you’ve downloaded it, your hard disk could crash, and you’d lose anything on the machine. Data could also be lost on your cell phone or tablet, losing any pictures or information on those devices. If you think it’s rare, think again. According to a 2012 survey commissioned by Seagate Technology, 54% of American adults have and/or know someone who has lost data.
On the other side of the coin, there are times you won’t want the data to be available. You may be selling or trading in your device, or it could be lost or stolen. In such cases, you’d want to find it, lock it so it can’t be used, or wipe it to remove any personal information. There have been many situations where people and companies have sold such equipment, not realizing there are photos, documents, and other files that can be accessed on the machine. To protect yourself, you’ll want to install the proper software, so that the data is still accessible to you and not others.
Selling and recycling equipment
The latest technology doesn’t stay cutting edge for very long. The computer, tablet, mobile phone, and other devices that you buy today will become outdated and need to be upgraded or replaced. There are good reasons to upgrade your equipment. Once a device has reached a certain age, the cost of maintaining and supporting it increases, and it may be more exposed to security risks. Devices will run slower, break down more often, may not support the latest operating system and software, and have more known vulnerabilities than newer equipment. While a person or company may avoid replacing devices during tough times like a slow economy, Intel recommends that the optimal time to upgrade a computer is every 2–4 years.
To recoup some of the cost of upgrading, or environmental concerns of old devices going to a landfill, many people and companies will resell or refurbish equipment. For example, a mobile phone you’re leasing might go back to the manufacturer, where it’s restored to its original working condition and resold to someone else at a cheaper price. Similarly, you or your company might sell an old computer at auction or donate it to charity. When you purchase new equipment, the vendor may have a “buy your old device” option, where they’ll offer a rebate or discount for trading in your old one. In doing so, they may promise to wipe your old data, and in the case of a phone, erase your SIM card. However, are you comfortable enough with any company that you’ll trust them to do it for you?
While keeping up-to-date with technology is important, there’s a serious security risk in improperly disposing of old equipment. There are countless stories of people buying a used computer or hard disk, only to find it was full of information. In 2008, an IT Manager in Oxford, England bought a computer on eBay, only to find it contained sensitive information on several million bank customers. The old server was sold by a company that archived data for American Express, NatWest, and the Royal Bank of Scotland, but the data on its hard drives had never been properly erased. Similarly, in 2010, NASA sold a number of computers that were used for the Space Shuttle program. The hard disks contained highly sensitive information, but the data hadn’t been properly deleted. Unfortunately, residual or undeleted data on used disks isn’t uncommon.
According to a 2009 study by Kessler International, a computer forensics firm, over 40% of the hard disks for sale on eBay contains personal, private, or sensitive information. Similar results were found when BT Security Research Centre and the University of Glamorgan bought disks from the United Kingdom, France, Germany, Australia, and the United States. Of the 300 hard disks purchased, 34% contained personal information, inclusive to medical records and bank account details. One disk purchased on eBay contained details of test launch procedures for a ground-to-air missile defense system, while another contained security logs from an embassy in France.
Wiping hard disks
As we’ll see in the next chapter, even if a hard disk has been formatted, there are still forensic tools that can be used to retrieve deleted data. These tools can read and restore files, so long as they haven’t been completely overwritten by other data. Because of this, it’s important that you use software that will not only erase your information but overwrite it with patterns of data so that the previous data is unrecoverable.
When you delete a file, it is no longer visible in the computer’s file system. The operating system removes a reference to the file from the file system table but doesn’t remove the data. It will remain on the hard disk until the area of the disk where the file resided is overwritten with other data. Using any number of undelete utilities on the Internet, you can easily recover it. Even if it’s partially overwritten, it’s still possible to recover the remaining data using forensic software.
To securely erase data, you can use any number of tools. Some of these include:
• Eraser (http://eraser.heidi.ie)
• Active@ KillDisk (www.killdisk.com)
• Darik’s Boot and Nuke (www.dban.org)
Using such tools, the existing data is destroyed by overwriting it with other data, as either a single pass wipe or overwriting it dozens of times. The more sensitive the data, the more passes you’ll want to use.
Lost or stolen phone/tablet
A problem with mobile devices is they’re mobile; they can be taken anywhere, so it’s easier for them to be lost or stolen. When this happens, sensitive data stored on a tablet or mobile phone could fall into the wrong hands. This is where location and remote wiping features may provide a layer of protection.
As we’ll discuss in Chapter 9, mobile devices commonly have a location awareness feature, which is used to determine the physical location of a device using Global Positioning System, Wi-Fi data, or by identifying its position between radio and cell phone towers. By activating the “Location On” feature of a mobile phone or tablet, you can then use software or visit a Web site to see where the device is at that particular moment. This can be useful if you’ve forgotten the device somewhere and can still retrieve it.
If you’re concerned it’s irretrievable, then you should consider remotely wiping the device. When a device is wiped, personal information and other data on it are deleted. If it belongs to your company, you may need to contact your IT department. Depending on the systems and devices used by your company, they would send a command to the phone through mail server like Microsoft Exchange Server or middleware like Blackberry Enterprise Server. The command might have the handset erase all data, do a complete factory reset, and/or completely disable the device.
If you have a small company or using a personal mobile device, you can still protect your information if it’s lost or stolen. There are a number of apps available that will provide security and allow you to remote wipe a device. One example is Lookout Security and Antivirus, which runs on iPhone and Android devices. After going to the app store on your mobile phone or tablet and installing the app, you’re prompted to set up an account using your email address and a password. An email is sent with a link to confirm the new account, and you’ll receive notification emails whenever someone uses the app to locate your device, remote wipe it, or use other features. These notifications are useful in alerting you if someone has accessed your account, and may be using it to track your whereabouts or perform other remote actions.
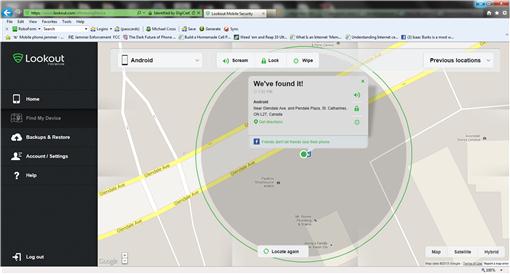
Once the app is installed on a mobile phone or tablet, you can interact with it on Lookout Security and Antivirus’ Web site (www.lookout.com). On the site, you can view devices setup to work with your account, locate your device, and see the results of anti-malware and malware scans Lookout has run against your device. As seen in Figure 6.4, by clicking on the Find My Device tab on the left side of the screen, you’ll see a map appear showing the location of your device. At the top of the screen, you can click any of the following buttons to interact with it:
• Scream, which will cause the device to emit a loud alarm sound. The blaring noise is useful if you’ve misplaced it in your house, car, or another location you have access to, and may make a thief think twice about keeping it.
• Lock, which will prevent access to the device. When you remotely lock the device from the Web site, you’re provided a numeric code to unlock it. Phone functions won’t work until a code has been entered, so it can’t be answered if you call it. Optionally, if someone enters the wrong code three times, a photo of the person will be taken with the front facing camera of the device and emailed to you.
• Wipe, which will erase the following from the device: contacts and call logs, calendar events, browser history, associated accounts, text messages, data in the SD card, and all pictures, videos, and documents.
Wiping your device should be considered a final solution. In doing so, it’s reset to factory defaults, so it’s just like when you first bought the device. Your data, apps, and settings will be gone. If you tried using Lookout or another tracking app to locate the device, it wouldn’t work because the apps would no longer be on the device.
While remotely wiping or locking a device provides an element of protection in preventing others from having your information, it isn’t foolproof. These methods require a command being sent to the device, so circumventing it simply requires cutting off its ability to receive that command. In other words, if it can’t connect to the Internet, it can’t be located, locked, or wiped remotely. The easiest way to do this is to turn it off. However, even if it wasn’t turned off, the device couldn’t be wiped if it was in a location where it lost service or didn’t have a data plan and it couldn’t connect to a nearby Wi-Fi.
There are also methods of jamming a mobile device so that it can’t connect to a data network. Jammers are devices that emit radio waves on the same frequencies as a digital cell phone. Even if a phone works on multiple bands, jamming a single band can prevent it from connecting to the network to send and receive calls. Jammers are illegal in most countries, as in the United States where federal law prohibits the operation, sale, and use of these devices. However, even if a country makes jammers illegal, there are often exceptions. Military installations or government agencies may use them as a security measure. Prisons might use them to prevent gang members from texting each other or other unauthorized communication by prisoners. Some countries like France and Japan have permitted jammers in areas where calls may disturb others, such as theaters, public performances, art galleries, and other venues. However, if someone were stealing a mobile device to acquire your information, would you really expect them to adhere to legalities of jammers?
Backup and restore
Losing personal photos and videos can be devastating, and losing company data like orders, contact lists, or important documents could equate to serious business losses. When you consider the consequences, you’d expect most people regularly backup their data, but this isn’t the case. The 2012 survey commissioned by Seagate found that 90% of people don’t back up data on a daily basis and 89% don’t use continuous backup, where the data is backed up at regular intervals or when changed.
While everyone agrees backups are important, there are many reasons why they don’t. Traditionally, lack of storage has been a common excuse. Backup devices used to be fairly pricey, and if a computer had an extra hard disk, the space was used instead of dedicating it to storing backup files. Fortunately, this is no longer an excuse. A person can use a rewritable DVD to back up important files, and the price of hard disks have dropped considerably, with a 1TB external hard drive costing just over $100. People can even back up their data to the cloud, so it’s stored on secure servers on the Internet.
Another perceived issue is cost. There are a number of excellent commercial solutions, such as Norton Ghost to back up files and make an image of your machine. The cost of such software is often marginal. If you’re looking for a free solution then you can use Windows Backup, which is included with the operating system and discussed in the next section.
Companies are usually better at having a backup plan than individuals, as the continuity of a business can depend on the stability of data. Since backups are handled by an IT department, this provides a worry-free solution for most people. In a larger organization, files are backed up using software designed for networks, such as CommVault (www.commvault.com), and saved to tapes that can then be stored offsite. In companies using SharePoint, files are uploaded to document libraries, with the actual data saved in a backend SQL Server. CommVault then backs up this data using SharePoint agent, which allows the software to back up and restore individual sites and documents. However, even in the best of places, not everything on a network is backed up. You’ll often find that a company will back up files on the network but not those saved on workstations, mobile devices, and social media sites. Policies or settings may be used to enforce where users should save their files and restrict them from saving files to a local hard drive.
Using windows backup
A backup and restore utility has been included with Windows since its earliest versions. Like a lot of tools bundled with their operating system, older incarnations have been less than inspired, difficult for a novice user, and hardly a competition for third-party tools. Windows Backup could be daunting and intimidating if you were new to computers. However, if you haven’t looked at it since Windows XP, then you’re in for a pleasant surprise.
Windows Backup has undergone radical changes, providing an easy-to-use interface that takes you step by step through the process of backing up and restoring files. It performs incremental backups of your files, including just the files that are newly created or modified since the previous backup. If several versions of the same file have been backed up, you can choose which version you want to restore. Once you’ve gone through the process of setting up your first backup, you can schedule it so that the system will automatically back up your files.
To set up a Windows 7 machine to back up files on your computer, you would do the following:
1. Click Start|Control Panel|Backup and Restore. (Alternatively, you can click Start and type “Backup and Restore” in the search field, and press Enter on your keyboard.)
3. When the Setup backup dialog box appears, select the drive where your backup will be saved. Click Next.
4. To choose the files to back up, click Let me choose. Alternatively, you could select “Let Windows choose (recommended).” Click Next.
5. On the What do you want to back up? screen, you’ll see files saved in libraries, on user desktops, and default Windows folders have already been selected. Select any additional files or folders you want to back up.
6. Uncheck the Include a system image of drives checkbox, as we’ll discuss this later. Click Next.
7. In the Schedule section, click Change Schedule.
8. Ensure that the Run backup on a schedule (recommended) checkbox is checked.
9. In the How often dropdown list, select whether the backup will run monthly, weekly, or daily.
10. In the What day dropdown list, select the day on which the backup to run.
11. In the What time dropdown list, select a time that the backup will run.
Once you’ve completed these steps you’ll notice the backup of your files is running, and a backup file will be saved where you created. Also, if you return to the Backup and Restore app in Control Panel, you’ll see your new backup job listed. To reconfigure what you’ve done, simply click on the Change settings link to rerun the wizard.
To restore your files, you could click on the Restore my files button. This will start a wizard that will walk you through the process of selecting which files or folders you’d like to restore. Once you’ve selected what to restore, you then can chose whether to restore it to the original location or another location.
You can also create a system image of a disk, which will create an exact copy of a drive. This is extremely useful if your computer fails or the hard disk crashes. The image contains your operating system, drivers, programs, and any other data on the disk. By restoring the image file, you’re completely restoring the computer to the point that the image was created.
To create a system image on Windows 7, you would use Backup and Restore in Control Panel, and click on the Create a system image link in the left pane. Once the program starts, you would then follow these steps:
1. On the first screen, select where you would like to save the backup. Your options are on a hard disk, DVD(s), or a network location. After specifying where to save the backup, click Next.
2. The screen that appears will show the system drive (containing the operating system) checked. If you have additional hard disks on your computer, you can check the checkbox beside each drive to include it in the image. Click Next.
When backing up a computer, there are some things you should take into consideration. You shouldn’t back up files to the same hard disk that Windows is installed on (i.e., your system disk) or to the same hard disk as the original files. After all, if the computer fails or the hard disk crashes, you wouldn’t be able to access the original or backed up files. Also, because anyone who has your backups can restore the files to their machine, you should store any external disks, rewritable DVDs, or other storage media containing your backups in a safe place.
Keeping your backups secure is important. Remember that anyone who has access to the external hard disk or other storage media could simply walk off with it. For home use, you may choose to keep it in a locked room, a locked fire box, or somewhere else that’s not easily accessible to guests. Businesses will often keep backups in a secure server room or safe and keep older copies offsite in case there is a fire or other disaster.
Web-based solutions
While storing data in the cloud is touted as if it were a new craze, web-based backup solutions have been around for years and provide some advantages over backing up files and folders to a local drive. For personal use and small businesses, the option of keeping backups off premises may be impractical or impossible. With online backups, data is stored offsite on a secure server. Your data is automatically uploaded to a server on the Internet, so it remains safe even if your disks were damaged or stolen, or your premises falls victim to a disaster.
One of the more mature sites is Carbonite (www.carbonite.com), which provides unlimited storage for files on your home computer. If you have multiple computers or servers that need to be backed up, there are also packages for businesses. The basic home package will back up files on your computer, but there are also packages that will mirror your hard disk, so that you can restore the entire system if needed. As with a number of other companies, Carbonite allows you to upload data at higher speeds until you reach an upload limit and then lower the speed at which data is transferred. Therefore, if you have a large system, it may take longer to back up once you reach this limit. Being that it constantly runs in the background on your computer, any new or modified files are automatically encrypted and uploaded to the server on a regular basis. This means that using the service requires little interaction after the initial setup.
Backing up a cell phone or tablet
For some, losing the data on a mobile phone or tablet can be devastating, as it may contain important contacts, files, or other information. If that’s the case, then prior to losing your mobile device, you should consider using apps that will back up and restore the data.
Many online backup sites provide apps for mobile devices. For example, Carbonite offers free apps for tablets and mobile phones, which will automatically back up photos and videos to their secure servers. The backed up data can then be accessed from your computer, allowing you to view, share, and restore them as you would other data backed up from your computer. These apps also offer security features that were discussed earlier in this chapter, where you can lock or wipe a device remotely if your phone or tablet is lost or stolen.
There are a number of apps that you can install on a device to back up your cell phone or tablet. A tool we previously discussed is Lookout, which can back up the device remotely through the following steps:
1. After logging onto Lookout’s site (www.lookout.com), click the Backups & Restore tab on the left side of the screen.
2. Click the Backup now button on the top right of the screen.
Restoring the device is just as easy and also done remotely through their Web site by following these steps:
Personal data or equipment
Some employees will use their own devices for business purposes or use corporate equipment for personal use. A phone or tablet might be set up to access work email or have additional apps installed to back up and wipe data. If your device is set up this way, you may be vulnerable to having the data wiped by your employer.
As we discussed earlier, a device can be locked or wiped by sending a command to it. If the employer installed security apps with this capability or set up the device to access work email, there is a possibility that your data could be destroyed accidentally or on purpose. If your employment was terminated or a command was accidentally sent to do a remote wipe, you would lose any personal and business data on the phone or tablet.
Another risk involves backups of data. An employee may do unauthorized backups of data on corporate devices they were issued. If he or she were fired, the employer could wipe the device but wouldn’t be able to delete any data the employee had backed up to a site like Carbonite. The fired employee could simply restore the data to another device at a later time.
To ensure the security of business and personal data, you should keep the two separate. A business laptop, phone, or tablet should be used for business purposes and locked down to prevent the user from installing any additional apps. In the same way, personal devices should not contain business data. While this might mean you have to carry two phones, it would protect the employee and business from data being destroyed or copied without authorization.
The other potential liability is related to damage of equipment. If you installed personal apps on a work tablet or phone, or malware was installed while visiting social networking sites without authorization, an employer might fire you or hold you responsible for repairs. Similarly, an organization might be held responsible for any personal equipment and data loss if they allowed employees to use their own devices for business purposes. A policy outlining proper use of equipment can help to clarify these matters and the rights of the employee and employer. As additional protection, if you get the IT department to configure a personal device to use corporate email, have them clearly explain what was installed and whether they have the ability to remotely lock or wipe the device.
BYOD
Even though it may be safer to keep corporate and personal devices separate, there is a growing shift toward allowing employees to use their own devices. If you own a business, you may have had job candidates asking about the company’s BYOD policy or asked a potential employer about it yourself. BYOD is an acronym for “Bring Your Own Device,” which permits employees to use their own mobile devices in the workplace. While the person owns the device, it is connected to the corporate network, allowing them to do work on devices that aren’t owned by the company.
BYOD does have a number of positive points. Since the employee is bringing their own device to work, this saves the company equipment costs. As the person is already familiar with their own mobile phone, tablet, or laptop, this can increase their productivity and decrease training time on how to use it.
As we mentioned, there are drawbacks in people using their own devices. Noncorporate devices are now connected to corporate resources and services, which create a security risk. Since it’s owned by the employee, he or she has the right to install any apps or visit any sites without restriction, increasing the possibility of malware and viruses being installed. As we mentioned earlier, if a person lost their phone or tablet, anyone finding it could now retrieve any unsecured data on the device. Added to this is the risk of what happens when a person leaves the company. Even if the corporate data is wiped from a mobile phone, the company doesn’t own that phone number. Business contacts may continue calling the former employee, allowing the person to steal customers if he or she goes to work for the competition.
To address these problems, the company needs a BYOD agreement that sets conditions on the use of personal devices at work. It also gives the company permission to manage the person’s device. Mobile Device Management (MDM) software can be used to monitor and manage devices, make configuration settings, remotely lock and wipe the device, distribute applications, and more. Some popular MDM systems include:
• SOTI (www.soti.net)
• Symantec Mobile Management (www.symantec.com/en/ca/mobile-management)
• MobileIron (www.mobileiron.com)
• Airwatch (www.air-watch.com)
Being that BYOD is increasingly common, you’ll find that there are a wide range of choices in MDM systems. You will however want to ensure that the MDM supports a wide range of platforms. Employees may have devices running Android, iOS, Windows, or other operating systems. You never know what someone is going to bring to work, but you’ll want them all protected.
Bibliography
1. @ComfortablySmug. (2012, October 29). Tweet by @ComfortablySmug. Retrieved July 25, 2013, from Twitter:<https://twitter.com/ComfortablySmug/status/263083953152466947>.
2. American Academy of Matrimonial Lawyers. (2010, February 10). Big surge in social networking evidence says survey of nation’s top divorce lawyers. Retrieved August 13, 2013, from American Academy of Matrimonial Lawyers:<http://www.aaml.org/about-the-academy/press/press-releases/e-discovery/big-surge-social-networking-evidence-says-survey->.
3. American Academy of Matrimonial Lawyers. (2013, February 11). Dating websites providing more divorce evidence says survey: nation’s top matrimonial lawyers cite Match.com as most common source. Retrieved August 13, 2013, from American Academy of Matrimonial Lawyers:<http://www.aaml.org/about-the-academy/press/press-releases/divorce/dating-websites-providing-more-divorce-evidence-says>.
4. Arghandiwal, M. (2012, September 12). Afghanistan bans YouTube to block anti-Muslim film. Retrieved June 23, 2013, from Reuters:<http://www.reuters.com/article/2012/09/12/us-afghanistan-youtube-idUSBRE88B0SC20120912>.
5. BBC News. (2008, August 26). Bank customer data sold on eBay. Retrieved June 4, 2013, from BBC News:<http://news.bbc.co.uk/2/hi/uk_news/7581540.stm>.
6. BBC News. (2009, May 7). Missile data found on hard drives. Retrieved June 4, 2013, from BBC News:<http://news.bbc.co.uk/2/hi/uk_news/wales/8036324.stm>.
7. BBC News Technology. (2010, December 8). NASA sells shuttle PCs without wiping secret data. Retrieved June 4, 2013, from BBC News Technology:<http://www.bbc.co.uk/news/technology-11947721>.
8. Buchholz, D., DeVetter, D., Gonzalez, J., Livne, O., & Mahvi, J. (2012, July). PC Lifecycle managment: boosing productivity and IT efficiency. Retrieved June 4, 2013, from Intel:<http://www.intel.com/content/dam/www/public/us/en/documents/best-practices/pc-lifecycle-management.pdf>.
9. Choney, S. (2012, November 1). Man who made false tweet about Sandy apologizes; could face prosecution. Retrieved July 25, 2013, from NBC News Technology:<http://news.yahoo.com/blogs/abc-blogs/superstorm-sandy-rumors-cost-congressional-campaign-manager-job-140408935--abc-news-politics.html>.
10. Facebook. (2013, July 21). Important message from Facebook’s White Hat Program. Retrieved August 13, 2013, from Facebook:<https://www.facebook.com/notes/facebook-security/important-message-from-facebooks-white-hat-program/10151437074840766>.
11. Garrett-Walker, H. (2012, April 12). Teens warned about posting dodgy images online. Retrieved June 24, 2013, from The New Zealand Herald:<http://www.nzherald.co.nz/nz/news/article.cfm?c_id=1&objectid=10798360>.
12. Gartner, Inc. (2011, February 17). Gartner says by year-end 2013, half of all companies will have been asked to produce material from social media websites for E-Discovery.Retrieved July 30, 2013, from Gartner:<http://www.gartner.com/newsroom/id/1550715>.
13. Hernandez, D. (2011, September 1). Terrorism charges for 2 in Mexico who spread attack rumor on Twitter, Facebook. Retrieved July 25, 2013, from Los Angeles Times:<http://latimesblogs.latimes.com/laplaza/2011/09/twitter-tweets-veracruz-mexico-terrorism-drug-war-censorship-rumors.html>.
14. International Business Times. (2013, June 9). Odd News: Tajikistan president ordered YouTube shutdown for uploading his “Bad Dancing and Singing” at son’s wedding. Retrieved June 19, 2013, from International Business Times:<http://au.ibtimes.com/articles/476420/20130609/takijistan-president-emomali-rahmon-youtube-bad-dancing.htm>.
15. ISACA. (2010, June). Top five social media risks for business: New ISACA white paper. Retrieved June 13, 2013, from ISACA:<http://www.isaca.org/About-ISACA/Press-room/News-Releases/2010/Pages/Top-Five-Social-Media-Risks-for-Business-New-ISACA-White-Paper.aspx>.
16. Kessler International. (2009, February). Is your confidential information being sold on eBay? Retrieved June 4, 2013, from Kessler International:<http://www.investigation.com/press/press75.htm>.
17. Pew Research Center for the People & the Press. (2013, April 23). Most expect ‘occasional acts of terrorism’ in the future. Retrieved June 24, 2013, from Pew Research Center for the People & the Press:<http://www.people-press.org/2013/04/23/most-expect-occasional-acts-of-terrorism-in-the-future/>.
18. Ponemon Institute. (2011, September). Global survey on social media risks. Retrieved June 13, 2013, from Websense:<http://www.websense.com/assets/reports/websense-social-media-ponemon-report.pdf>.
19. Rosen, J. (2010, July 21). The web means the end of forgetting. Retrieved June 24, 2013, from New York Times:<http://www.nytimes.com/2010/07/25/magazine/25privacy-t2.html?pagewanted%26equals;all>.
20. Sarbanes–Oxley Act of 2002. (2002, July 30). Retrieved July 30, 2013, from Office of the Law Revision Counsel:<http://uscode.house.gov/download/pls/15C98.txt>.
21. Seagate. (2012, June 12). Seagate reinvents backup for your digital life. Retrieved June 10, 2013, from Business Wire:<http://www.businesswire.com/news/home/20120611005277/en/Seagate-Reinvents-Backup-Digital-Life>.
22. Sonwane, A. (2011, July 9). Privacy disasters in social media – how vulnerable is your organization? Retrieved July 25, 2013, from<http://www.lsec.be/upload_directories/documents/110906_SocialNetworkingThreats/6_Sonwane_Abhilash_Cyberoam_110906_2.pdf>.
23. Stanglin, D. (2013, April 25). Student wrongly tied to Boston bombings found dead. Retrieved July 25, 2013, from USA Today:<http://www.usatoday.com/story/news/2013/04/25/boston-bombing-social-media-student-brown-university-reddit/2112309/>.
24. Tapellini, D. (2010, May 4). Consumer reports survey: Social network users post risky information. Retrieved June 19, 2013, from Consumer Reports:<http://news.consumerreports.org/electronics/2010/05/social-networks-facebook-risks-privacy-risky-behavior-consumer-reports-survey-findings-online-threats-state-of-the-net-report.html>.
25. The Telegraph. (2013, January 22). Library of congress is archiving all of America’s tweets. Retrieved June 24, 2013, from<http://www.businessinsider.com/library-of-congress-is-archiving-all-of-americas-tweets-2013-1>.
26. Travers, L. A., & Oster, S. (2010, January 26). Guidance: Representing EPA online using social media. Retrieved July 1, 2013, from Social Media Subcouncil:<http://govsocmed.pbworks.com/w/page/21329932/Guidance%3A%20Representing%20EPA%20Online%20Using%20Social%20Media>.
27. WikiLeaks. (2010, April 5). Collateral murder, 5 Apr 2010. Retrieved July 25, 2013, from WikiLeaks:<http://wikileaks.org/wiki/Collateral_Murder,_5_Apr_2010>.
28. YouTube. (2013, May 16). Video privacy settings. Retrieved June 20, 2013, from YouTube:<http://support.google.com/youtube/bin/answer.py?hl=en&answer=157177>.
29. zig. (2007, June 15). An online phenomenon that started in a house. Retrieved June 19, 2013, from zig:<http://www.zigideas.com/screamtv/pdf/campaign_rollout.pdf>.