9
Finite ON–OFF Multirate Loss Models
In this chapter we consider ON–OFF multirate loss models of quasi‐random arriving calls with fixed bandwidth requirements. In‐service calls do not constantly keep their assigned bandwidth but alternate between transmission periods (ON) and idle periods (OFF). As we discussed in Chapter , ON–OFF loss models can be used for the analysis of the call‐level behavior of bursty traffic. The finite ON–OFF multirate loss models are based on the EnMLM (see Chapter ); their recurrent form facilitates their computer implementation.
9.1 The Finite ON–OFF Multirate Loss Model
9.1.1 The Service System
In the finite ON–OFF multirate loss model (f‐ON–OFF), we consider a link of capacity ![]() b.u. that accommodates
b.u. that accommodates ![]() service‐classes of ON–OFF‐type calls. Calls of a service‐class
service‐classes of ON–OFF‐type calls. Calls of a service‐class ![]() come from a finite source population
come from a finite source population ![]() . The mean arrival rate of service‐class
. The mean arrival rate of service‐class ![]() idle sources is
idle sources is ![]() , where
, where ![]() is the number of in‐service sources of service‐class
is the number of in‐service sources of service‐class ![]() in state
in state ![]() state ON,
state ON, ![]() state OFF) and
state OFF) and ![]() is the arrival rate per idle source. A call of service‐class
is the arrival rate per idle source. A call of service‐class ![]() requires
requires ![]() b.u. and competes for the available bandwidth of the system under the CS policy. If the
b.u. and competes for the available bandwidth of the system under the CS policy. If the ![]() b.u. are available then the call enters the system in state ON, otherwise the call is blocked and lost, and the occupied link bandwidth is characterized as real. The capacity
b.u. are available then the call enters the system in state ON, otherwise the call is blocked and lost, and the occupied link bandwidth is characterized as real. The capacity ![]() , named real (real link), corresponds to state ON.
, named real (real link), corresponds to state ON.
At the end of an ON‐period a call of service‐class k releases the ![]() b.u. and may begin an OFF‐period with probability
b.u. and may begin an OFF‐period with probability ![]() , or depart from the system with probability
, or depart from the system with probability ![]() . While the call is in state OFF, it seizes fictitious
. While the call is in state OFF, it seizes fictitious ![]() b.u. of a fictitious link of capacity
b.u. of a fictitious link of capacity ![]() . The fictitious capacity
. The fictitious capacity ![]() corresponds to state OFF. The call holding time of a service‐class k call in state ON or OFF is exponentially distributed with mean
corresponds to state OFF. The call holding time of a service‐class k call in state ON or OFF is exponentially distributed with mean ![]() .
.
At the end of an OFF‐period the call returns to state ON with probability 1 (i.e., the call cannot leave the system from state OFF), while re‐requesting ![]() b.u. When
b.u. When ![]() b.u. are always available for that call in state ON, i.e., no blocking occurs while returning to state ON. When
b.u. are always available for that call in state ON, i.e., no blocking occurs while returning to state ON. When ![]() , and there is available bandwidth in the link, i.e., if
, and there is available bandwidth in the link, i.e., if ![]() (where
(where ![]() is the occupied real link bandwidth), the call returns to state ON and a new burst begins; otherwise, burst blocking occurs and the call remains in state OFF for another period. A new service‐class k call is accepted in the system with
is the occupied real link bandwidth), the call returns to state ON and a new burst begins; otherwise, burst blocking occurs and the call remains in state OFF for another period. A new service‐class k call is accepted in the system with ![]() b.u. if it meets the constraints of (5.1) and (5.2).
b.u. if it meets the constraints of (5.1) and (5.2).
Based on (5.1) and (5.2), the state space ![]() of all possible states
of all possible states ![]() (where
(where ![]() is the occupied bandwidth of the fictitious link) is given by (5.3). In terms of
is the occupied bandwidth of the fictitious link) is given by (5.3). In terms of ![]() , the CAC is identical to that of the ON–OFF multirate loss model (see Section 5.1.1).
, the CAC is identical to that of the ON–OFF multirate loss model (see Section 5.1.1).
9.1.2 The Analytical Model
9.1.2.1 Steady State Probabilities
To describe the analytical model in the steady state we present the following notations 1:
 : the vector of the number of in‐service service‐class k calls in state
: the vector of the number of in‐service service‐class k calls in state  state ON,
state ON,  state OFF)
state OFF) ,
,
 : a vector that shows a service‐class k call transition from state OFF to ON
: a vector that shows a service‐class k call transition from state OFF to ON : a vector that shows a service‐class k call transition from state ON to OFF
: a vector that shows a service‐class k call transition from state ON to OFF
![]() the offered traffic‐load to state i from service‐class k; it is determined by:
the offered traffic‐load to state i from service‐class k; it is determined by:

where ![]() is the total arrival rate of service‐class k calls to state i and is given by:
is the total arrival rate of service‐class k calls to state i and is given by:

![]() is the external arrival rate of service‐class k calls to state i determined by:
is the external arrival rate of service‐class k calls to state i determined by:

![]() is the
is the ![]() and is given by (5.5a) and (5.5b).
and is given by (5.5a) and (5.5b).
Figure 9.1 shows the state transition rates of the f‐ON–OFF model (in equilibrium).

Figure 9.1 The state transition diagram of the f‐ON–OFF model.
Assuming the existence of LB between adjacent states, the following LB equations are extracted from the state transition diagram of Figure 9.1:
where ![]() ,
, ![]() ,
, ![]() ,
, ![]() , and
, and ![]() are the probability distributions of the corresponding states
are the probability distributions of the corresponding states ![]() ,
, ![]() .
.
Equations (9.4b) and (9.4c) describe the balance between the rates of a new call arrival of service‐class k and the corresponding departure from the system, while (9.4a) and (9.4d) refer to the ON–OFF alternations of a service‐class k call. Based on the LB assumption, the probability distribution ![]() has a PFS which satisfies (9.4a)–(9.4d) and has the form [ 1]:
has a PFS which satisfies (9.4a)–(9.4d) and has the form [ 1]:

where ![]() is the normalization constant.
is the normalization constant.
We now define by ![]() the b.u. held by a service‐class k call in state
the b.u. held by a service‐class k call in state ![]() according to (5.10). We also define a
according to (5.10). We also define a ![]() matrix
matrix ![]() whose elements are the values of
whose elements are the values of ![]() and let
and let ![]() be the
be the ![]() row of
row of ![]() , where
, where ![]() . In addition, let
. In addition, let ![]() with
with ![]() where the occupied bandwidth
where the occupied bandwidth ![]() of link
of link ![]() real link,
real link, ![]() fictitious link) is given by (5.11).
fictitious link) is given by (5.11).
Having found an expression for ![]() and since the CS policy is a coordinate convex policy (see Section I.12, Example I.30), the probability
and since the CS policy is a coordinate convex policy (see Section I.12, Example I.30), the probability ![]() can be expressed by [ 1]:
can be expressed by [ 1]:
where ![]() while
while ![]() , and
, and 
![]() .
.
Consider now the set of states ![]() whereby the occupied real and fictitious link bandwidths are exactly j
whereby the occupied real and fictitious link bandwidths are exactly j ![]() and j
and j ![]() , respectively. Then, the probability
, respectively. Then, the probability ![]() (links occupancy distribution) is denoted as in (5.13).
(links occupancy distribution) is denoted as in (5.13).
Summing (9.6) over ![]() we have:
we have:

The LHS of (9.7) is written as: ![]() . Since
. Since ![]() we continue by using the following change of variables:
we continue by using the following change of variables:
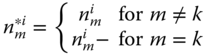
Thus the LHS of ( 9.7) can be written as:

where ![]() , and
, and ![]() . The first term of (9.8) is equal to
. The first term of (9.8) is equal to ![]() , while the second term is written as:
, while the second term is written as:


where ![]() is the expected value of
is the expected value of ![]() given
given ![]() .
.
By substituting the “new” first and second terms in ( 9.8), we have:
The RHS of ( 9.7) can be written as:

for ![]() and
and ![]() .
.
Combining (9.9) and (9.10), we have:
Multiplying both sides of (9.11) by ![]() and summing over
and summing over ![]() , we have [ 1]:
, we have [ 1]:

The estimator ![]() in (9.12) is not known. To determine it, we use a lemma initially proposed in [2] for the determination of a similar estimator in the EnMLM. According to the lemma, two stochastic systems with (i) the same traffic description parameters
in (9.12) is not known. To determine it, we use a lemma initially proposed in [2] for the determination of a similar estimator in the EnMLM. According to the lemma, two stochastic systems with (i) the same traffic description parameters ![]() and (ii) exactly the same set of states are equivalent, since they result in the same CBP. The purpose is therefore to find a new stochastic system in which we can determine the estimator
and (ii) exactly the same set of states are equivalent, since they result in the same CBP. The purpose is therefore to find a new stochastic system in which we can determine the estimator ![]() . By choosing the bandwidth requirements of calls of all service‐classes and the capacities
. By choosing the bandwidth requirements of calls of all service‐classes and the capacities ![]() in the new stochastic system according to the criteria (i) conditions (a) and (b) are valid and (ii) each state has a unique occupancy
in the new stochastic system according to the criteria (i) conditions (a) and (b) are valid and (ii) each state has a unique occupancy ![]() , then each state
, then each state ![]() can be reached only via state
can be reached only via state ![]() . Thus, the estimator
. Thus, the estimator ![]() and ( 9.12) can be written as (for
and ( 9.12) can be written as (for ![]() ):
):

Equation (9.13) is the two‐dimensional recursive formula used for the determination of ![]() . The
. The ![]() can be calculated in terms of an arbitrary
can be calculated in terms of an arbitrary ![]() under the normalization condition of
under the normalization condition of ![]() . Although ( 9.13) is simple, it cannot be used for the determination of
. Although ( 9.13) is simple, it cannot be used for the determination of ![]() unless an equivalent system (mentioned above) is defined by enumeration and processing of the system's state space. The following example reveals the problems that can arise when one tries to use ( 9.13) prior to the state space enumeration and processing, and how these problems can be overcome.
unless an equivalent system (mentioned above) is defined by enumeration and processing of the system's state space. The following example reveals the problems that can arise when one tries to use ( 9.13) prior to the state space enumeration and processing, and how these problems can be overcome.
Example 9.2
Consider a link of ![]() b.u. and
b.u. and ![]() b.u. The link accommodates calls of
b.u. The link accommodates calls of ![]() service‐classes whose calls require
service‐classes whose calls require ![]() and
and ![]() b.u., respectively. Let
b.u., respectively. Let ![]() calls/sec,
calls/sec, ![]() calls/sec,
calls/sec, ![]() sec, and
sec, and ![]() . In Table 9.1 we present the system state‐space of this example, consisting of 12 unique states of the form
. In Table 9.1 we present the system state‐space of this example, consisting of 12 unique states of the form ![]() , the respective real and fictitious link occupancies (
, the respective real and fictitious link occupancies (![]() ), the real and fictitious link occupancies of the equivalent system (
), the real and fictitious link occupancies of the equivalent system (![]() ), and the blocking states for each service‐class. We observe that the link occupancies are not unique, e.g., (
), and the blocking states for each service‐class. We observe that the link occupancies are not unique, e.g., (![]() appears twice: for
appears twice: for ![]() and for
and for ![]() . Because of this, we cannot use ( 9.13) unless we find an equivalent system whose states have unique link occupancy. Also, in both the initial and the equivalent system, the blocking states of each service‐class should be the same. Such an equivalent system has
. Because of this, we cannot use ( 9.13) unless we find an equivalent system whose states have unique link occupancy. Also, in both the initial and the equivalent system, the blocking states of each service‐class should be the same. Such an equivalent system has ![]() and
and ![]() b.u. The required bandwidth per call of the service‐classes of the equivalent system is chosen by a simple heuristic algorithm. This is an iterative procedure where in each iteration the required bandwidth of each service‐class is increased unit‐by‐unit from its initial value and checked whether or not the equivalent system has been found, according to the criteria mentioned above.
b.u. The required bandwidth per call of the service‐classes of the equivalent system is chosen by a simple heuristic algorithm. This is an iterative procedure where in each iteration the required bandwidth of each service‐class is increased unit‐by‐unit from its initial value and checked whether or not the equivalent system has been found, according to the criteria mentioned above.
Table 9.1 State space, ![]() , and blocking states (Example 9.2).
, and blocking states (Example 9.2).
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | ||
| 0 | 0 | 0 | 1 | 0 | 1 | 0 | 2 | * | |
| 0 | 0 | 0 | 2 | 0 | 2 | 0 | 4 | * | |
| 0 | 0 | 0 | 3 | 0 | 3 | 0 | 6 | * | * |
| 0 | 0 | 1 | 0 | 0 | 3 | 0 | 5 | * | * |
| 0 | 1 | 0 | 0 | 1 | 0 | 2 | 0 | * | |
| 0 | 1 | 0 | 1 | 1 | 1 | 2 | 2 | * | |
| 0 | 1 | 0 | 2 | 1 | 2 | 2 | 4 | * | * |
| 0 | 2 | 0 | 0 | 2 | 0 | 4 | 0 | * | |
| 0 | 2 | 0 | 1 | 2 | 1 | 4 | 2 | * | * |
| 0 | 3 | 0 | 0 | 3 | 0 | 6 | 0 | * | * |
| 1 | 0 | 0 | 0 | 3 | 0 | 5 | 0 | * | * |
Having found an equivalent system, we calculate the ![]() via ( 9.13), and then determine the TC probabilities of each service‐class:
via ( 9.13), and then determine the TC probabilities of each service‐class: ![]() via (9.14) (see below).
via (9.14) (see below).
Before we proceed with the determination of the various performance measures, we show the relationship between the f‐ON–OFF model and the EnMLM. These models are equivalent in the sense that they provide the same TC probabilities and CBP, when:
 (i.e., when state OFF does not exist) for each service‐class
(i.e., when state OFF does not exist) for each service‐class 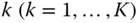 . In that case the calculation of
. In that case the calculation of  can be done via (6.27).
can be done via (6.27). and
and  . Then we can determine the mean holding time,
. Then we can determine the mean holding time,  , of a service‐class k call of the f‐ON–OFF model via (5.20). In that case, the f‐ON–OFF model is equivalent to the EnMLM with traffic parameters,
, of a service‐class k call of the f‐ON–OFF model via (5.20). In that case, the f‐ON–OFF model is equivalent to the EnMLM with traffic parameters,  and
and  determined by (5.20).
determined by (5.20).
9.1.2.2 TC Probabilities, CBP, and Utilization
The following performance measures can be determined based on ( 9.13):
9.1.2.3 BBP
To illustrate the idea behind the formula for the BBP determination we consider Example 9.3.
Example 9.3
Consider again Example 9.2 (![]() ) and let
) and let ![]() b.u. The latter results in the appearance of burst blocking for calls of both service‐classes (because
b.u. The latter results in the appearance of burst blocking for calls of both service‐classes (because ![]() ); OFF calls of service‐classes 1 and 2 will face burst blocking when
); OFF calls of service‐classes 1 and 2 will face burst blocking when ![]() and
and ![]() , respectively.
, respectively.
In Table 9.2 we present the system state‐space of this example, consisting of 19 unique states of the form ![]() , the respective real and fictitious link occupancies
, the respective real and fictitious link occupancies ![]() , the real and fictitious link occupancies of the equivalent system
, the real and fictitious link occupancies of the equivalent system ![]() as well as the call and burst blocking states for each service‐class. An equivalent system is
as well as the call and burst blocking states for each service‐class. An equivalent system is ![]() , and
, and ![]() b.u.
b.u.
Table 9.2 State space, ![]() , call, and burst blocking states (Example 9.3).
, call, and burst blocking states (Example 9.3).
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | ||||
| 0 | 0 | 0 | 1 | 0 | 1 | 0 | 2 | ||||
| 0 | 0 | 0 | 2 | 0 | 2 | 0 | 4 | * | |||
| 0 | 0 | 0 | 3 | 0 | 3 | 0 | 6 | * | |||
| 0 | 0 | 0 | 4 | 0 | 4 | 0 | 8 | * | * | ||
| 0 | 0 | 1 | 0 | 0 | 3 | 0 | 5 | * | |||
| 0 | 0 | 1 | 1 | 0 | 4 | 0 | 7 | * | * | ||
| 0 | 1 | 0 | 0 | 1 | 0 | 2 | 0 | * | * | ||
| 0 | 1 | 0 | 1 | 1 | 1 | 2 | 2 | * | * | ||
| 0 | 1 | 0 | 2 | 1 | 2 | 2 | 4 | * | * | ||
| 0 | 1 | 0 | 3 | 1 | 3 | 2 | 6 | * | * | * | |
| 0 | 1 | 1 | 0 | 1 | 3 | 2 | 5 | * | * | * | |
| 0 | 2 | 0 | 0 | 2 | 0 | 4 | 0 | * | * | ||
| 0 | 2 | 0 | 1 | 2 | 1 | 4 | 2 | * | * | ||
| 0 | 2 | 0 | 2 | 2 | 2 | 4 | 4 | * | * | * | |
| 0 | 3 | 0 | 0 | 3 | 0 | 6 | 0 | * | * | * | * |
| 0 | 3 | 0 | 1 | 3 | 1 | 6 | 2 | * | * | * | * |
| 1 | 0 | 0 | 0 | 3 | 0 | 5 | 0 | * | * | * | * |
| 1 | 0 | 0 | 1 | 3 | 1 | 5 | 2 | * | * | * | * |
In order to determine the BBP of calls of a service‐class ![]() , we need to find the number of service‐class k calls in state OFF,
, we need to find the number of service‐class k calls in state OFF, ![]() , when the system is in a burst blocking state, e.g., according to Table 9.2, a burst blocking state of service‐class 2 is
, when the system is in a burst blocking state, e.g., according to Table 9.2, a burst blocking state of service‐class 2 is ![]() and the corresponding value of
and the corresponding value of ![]() .
.
Multiplying ![]() by the corresponding
by the corresponding ![]() and the service rate in state OFF
and the service rate in state OFF ![]() , we obtain the rate whereby service‐class
, we obtain the rate whereby service‐class ![]() OFF calls would depart from the burst blocking state if it were possible. By summing these rates over the burst blocking state‐space
OFF calls would depart from the burst blocking state if it were possible. By summing these rates over the burst blocking state‐space ![]() we obtain the summation
we obtain the summation ![]() .
.
By normalizing it (taking into account the whole state space ![]() ), we obtain the following formula for the BBP calculation:
), we obtain the following formula for the BBP calculation:

where ![]() and
and ![]() are calculated by ( 9.13).
are calculated by ( 9.13).
Thus, (9.15) can be seen as the normalized rate of service‐class k OFF calls by which OFF calls would depart from the burst blocking states if it were possible.
For the record, the BBP of each service‐class in Example 9.3 are ![]() and
and ![]() , while the corresponding simulation results (with 95% confidence interval) are
, while the corresponding simulation results (with 95% confidence interval) are ![]() and
and ![]() .
.
9.2 Generalization of the f‐ON–OFF Model to include Service‐classes with a Mixture of a Finite and an Infinite Number of Sources
Consider a link with a pair of capacities ![]() and
and ![]() , accommodating
, accommodating ![]() service‐classes of finite ON–OFF sources (quasi‐random input) and
service‐classes of finite ON–OFF sources (quasi‐random input) and ![]() service‐classes of infinite ON–OFF sources (random–Poisson input). Then, the calculation of the link occupancy distribution is done by the combination of ( 9.13) and (5.17) [3]:
service‐classes of infinite ON–OFF sources (random–Poisson input). Then, the calculation of the link occupancy distribution is done by the combination of ( 9.13) and (5.17) [3]:

Such a mixture of service‐classes does not destroy the accuracy of the model. The TC probabilities calculation can be done via ( 9.14), while the BBP calculation can be done via ( 9.15) for the service‐classes of finite population and via (5.39) for the service‐classes of infinite population.
Example 9.4
Consider two service‐classes which require ![]() and
and ![]() b.u. per call, respectively, and a link of capacity
b.u. per call, respectively, and a link of capacity ![]() b.u. Calls of service‐class 1 arrive according to a quasi‐random process, while calls of service‐class 2 arrive according to a Poisson process. The number of sources of service‐class 1 is
b.u. Calls of service‐class 1 arrive according to a quasi‐random process, while calls of service‐class 2 arrive according to a Poisson process. The number of sources of service‐class 1 is ![]() . The traffic description parameters are:
. The traffic description parameters are:
Service‐class 1:
Service‐class 2:
Assuming that ![]() (no burst blocking occurs), then the equivalent system used for the TC probabilities calculation is
(no burst blocking occurs), then the equivalent system used for the TC probabilities calculation is ![]() , and
, and ![]() . Assuming that
. Assuming that ![]() , then the equivalent system used for the TC probabilities and the BBP determination is
, then the equivalent system used for the TC probabilities and the BBP determination is ![]() , and
, and ![]() . Finally, assuming that
. Finally, assuming that ![]() , then the equivalent system is
, then the equivalent system is ![]() , and
, and ![]() . For both service‐classes and the different values of
. For both service‐classes and the different values of ![]() , provide (i) analytical TC probabilities results and (ii) analytical and simulation BBP results. For both (i) and (ii), assume that
, provide (i) analytical TC probabilities results and (ii) analytical and simulation BBP results. For both (i) and (ii), assume that ![]() is constant, while
is constant, while ![]() increases in steps of 0.1, i.e., point 1 is
increases in steps of 0.1, i.e., point 1 is ![]() , point 2 is
, point 2 is ![]() , and point 7 is
, and point 7 is ![]() .
.
Figures 9.2 and 9.3 show the analytical TC probabilities results of service‐class 1 and 2, respectively, for (i) ![]() , (ii)
, (ii) ![]() , and (iii)
, and (iii) ![]() , while Figure 9.4 shows the analytical and simulation BBP results for both service‐classes and
, while Figure 9.4 shows the analytical and simulation BBP results for both service‐classes and ![]() . Simulation results are mean values of 10 runs with 95% confidence interval. As Figures 9.2 and 9.3 show, there is a significant decrease in the TC probabilities of both service‐classes when we increase the fictitious capacity
. Simulation results are mean values of 10 runs with 95% confidence interval. As Figures 9.2 and 9.3 show, there is a significant decrease in the TC probabilities of both service‐classes when we increase the fictitious capacity ![]() from 46 to 56. This decrease was anticipated because when
from 46 to 56. This decrease was anticipated because when ![]() increases, more calls may pass to state OFF, releasing bandwidth (in state ON) for new calls. However, the increase in
increases, more calls may pass to state OFF, releasing bandwidth (in state ON) for new calls. However, the increase in ![]() results in the burst blocking increase, as Figure 9.4 shows.
results in the burst blocking increase, as Figure 9.4 shows.

Figure 9.2 TC probabilities for service‐class 1 when a)  , (b)
, (b)  , and (c)
, and (c)  (Example 9.4).
(Example 9.4).

Figure 9.3 TC probabilities for service‐class 2 when (a)  , (b)
, (b)  , and (c)
, and (c)  (Example 9.4).
(Example 9.4).

Figure 9.4 BBP for both service‐classes when (a) 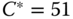 and (b)
and (b)  (Example 9.4).
(Example 9.4).
9.3 Applications
An interesting application of the f‐ON–OFF model has been proposed in [4], where the OCDMA PON architecture of Figure 9.5 with ![]() ONUs is considered.
ONUs is considered.

Figure 9.5 A basic configuration of an OCDMA PON.
All ONUs are connected to the OLT through a passive optical splitter/combiner (PO‐SC). The PO‐SC is responsible for collecting data from all ONUs and transmitting them to the OLT (upstream direction), as well as for broadcasting data from the OLT to the ONUs (downstream direction). The analysis of [ 4] concentrates on the upstream direction; however, it can also be applied to the downstream direction. Users that are connected to an ONU alternate between active and passive (silent) transmission periods. The PON uses ![]() codewords, which have the same length
codewords, which have the same length ![]() and the same weight
and the same weight ![]() , while the auto‐correlation
, while the auto‐correlation ![]() and cross‐correlation
and cross‐correlation ![]() parameters are defined according to the desired BER at the receiver. The PON supports
parameters are defined according to the desired BER at the receiver. The PON supports ![]() service‐classes which are differentiated via the parallel mapping technique. Under this technique, the OLT assigns
service‐classes which are differentiated via the parallel mapping technique. Under this technique, the OLT assigns ![]() codewords to a service‐class
codewords to a service‐class ![]() call for the entire duration of the call. More precisely, during the holding time of a service‐class
call for the entire duration of the call. More precisely, during the holding time of a service‐class ![]() call the data bits of this call are grouped per
call the data bits of this call are grouped per ![]() bits and transmitted in parallel in each bit period. One codeword is used to encode bit “1”, while data bit “0” is not encoded. Thus, the call uses a number of these
bits and transmitted in parallel in each bit period. One codeword is used to encode bit “1”, while data bit “0” is not encoded. Thus, the call uses a number of these ![]() codewords in each bit period and this number is equal to the number of data bits “1” that are transmitted during a bit period. In this way, the complex procedure of assigning codewords in each data bit period is avoided. Furthermore, since
codewords in each bit period and this number is equal to the number of data bits “1” that are transmitted during a bit period. In this way, the complex procedure of assigning codewords in each data bit period is avoided. Furthermore, since ![]() bits are transmitted in each data bit period, the data rate of service‐class
bits are transmitted in each data bit period, the data rate of service‐class ![]() is
is ![]() , where
, where ![]() is the basic data rate of a single codeworded call.
is the basic data rate of a single codeworded call.
When a single codeword is assigned to an active user (active call), the received power of this call at the OLT is denoted by ![]() (
(![]() corresponds to the received power per bit, for a specific value of the BER [5]). Since the PON supports multiple service‐classes of different data rates, a number of single codewords is assigned to each service‐class, therefore the received power
corresponds to the received power per bit, for a specific value of the BER [5]). Since the PON supports multiple service‐classes of different data rates, a number of single codewords is assigned to each service‐class, therefore the received power ![]() of an active call of service‐class
of an active call of service‐class ![]() is proportional to
is proportional to ![]() , since
, since ![]() data bits are simultaneously transmitted for service‐class
data bits are simultaneously transmitted for service‐class ![]() during a bit period, therefore:
during a bit period, therefore:
The connection establishment between the end‐user and the OLT is based on a three‐way handshake (request/ACK/confirmation). Calls of service‐class ![]() arrive at ONU
arrive at ONU ![]() from a finite number of traffic sources
from a finite number of traffic sources ![]() ; the total number of service‐class
; the total number of service‐class ![]() traffic sources in the PON is
traffic sources in the PON is ![]() . The mean call arrival rate of service‐class
. The mean call arrival rate of service‐class ![]() is
is ![]() , where
, where ![]() is the arrival rate per idle source, while
is the arrival rate per idle source, while ![]() and
and ![]() are the numbers of service‐class
are the numbers of service‐class ![]() calls in the PON in the active and passive states, respectively. Calls that are accepted for service start an active period and may remain in the active state for their entire duration, or alternate between active and passive periods. During an active period, a burst of data is sent to the OLT, while no data transmission occurs throughout a passive period. When a service‐class
calls in the PON in the active and passive states, respectively. Calls that are accepted for service start an active period and may remain in the active state for their entire duration, or alternate between active and passive periods. During an active period, a burst of data is sent to the OLT, while no data transmission occurs throughout a passive period. When a service‐class ![]() call is transferred from the active to the passive state the total number of in‐service codewords is reduced by
call is transferred from the active to the passive state the total number of in‐service codewords is reduced by ![]() . When a passive call attempts to become active, it re‐requests the same number of codewords (but not necessarily the same codewords) as in the previous active state. If the total number of codewords in use does not exceed a maximum threshold (the PON capacity), the call begins a new active period, otherwise burst blocking occurs and the call remains in the passive state for another period. At the end of an active period, the call is transferred to the passive state with probability
. When a passive call attempts to become active, it re‐requests the same number of codewords (but not necessarily the same codewords) as in the previous active state. If the total number of codewords in use does not exceed a maximum threshold (the PON capacity), the call begins a new active period, otherwise burst blocking occurs and the call remains in the passive state for another period. At the end of an active period, the call is transferred to the passive state with probability ![]() or departs from the system (the connection is terminated) with probability
or departs from the system (the connection is terminated) with probability ![]() . The active and passive periods of service‐class
. The active and passive periods of service‐class ![]() calls are exponentially distributed with mean
calls are exponentially distributed with mean ![]() (
(![]() indicates active state,
indicates active state, ![]() indicates passive state).
indicates passive state).
In OCDMA systems, an arriving call should be blocked, after the new call acceptance, if the noise of all in‐service calls is increased above a predefined threshold; this noise is called multiple access interference (MAI). We differentiate the MAI from other forms of noise (thermal, fiber‐link, beat, and shot noise). The thermal noise and fiber link noise are typically modeled as Gauss distributions ![]() and
and ![]() , respectively, while the shot noise is modeled as a Poisson process
, respectively, while the shot noise is modeled as a Poisson process ![]() [6]. The beat noise is modeled as a Gauss distribution
[6]. The beat noise is modeled as a Gauss distribution ![]() [7]. According to the central limit theorem, we can assume that the total additive noise is modeled as a Gauss distribution
[7]. According to the central limit theorem, we can assume that the total additive noise is modeled as a Gauss distribution ![]() , considering that the number of noise sources in the PON is relatively large. Therefore, the total interference
, considering that the number of noise sources in the PON is relatively large. Therefore, the total interference ![]() caused by the thermal, the fiber‐link, the beat, and the shot noise is modeled as a Gauss distribution with mean
caused by the thermal, the fiber‐link, the beat, and the shot noise is modeled as a Gauss distribution with mean ![]() and variance
and variance ![]() .
.
Upon a call arrival at an ONU, a CAC located at the OLT decides on its acceptance or rejection according to the total received power at the OLT. More precisely, the CAC estimates the total received power (together with the power of the new call); if it exceeds a maximum threshold ![]() , the call is blocked and lost. The maximum received power is calculated based on the worst case scenario that all
, the call is blocked and lost. The maximum received power is calculated based on the worst case scenario that all ![]() data bits transmitted in parallel are “1”, in order to ensure that the BER will never increase above the desired value. The value of
data bits transmitted in parallel are “1”, in order to ensure that the BER will never increase above the desired value. The value of ![]() is also determined by the desired BER at the receiver [ 5]. This condition is expressed by the following relation:
is also determined by the desired BER at the receiver [ 5]. This condition is expressed by the following relation:

The summation in (9.18) refers to the received power of all in‐service active calls of all ![]() service‐classes multiplied by the average probability of interference
service‐classes multiplied by the average probability of interference ![]() . This probability is a function of the weight
. This probability is a function of the weight ![]() , the length
, the length ![]() , and the maximum cross‐correlation parameter
, and the maximum cross‐correlation parameter ![]() of the codewords, as well as of the hit probabilities between two codewords of different users. Specifically, the hit probabilities
of the codewords, as well as of the hit probabilities between two codewords of different users. Specifically, the hit probabilities ![]() of getting
of getting ![]() hits during a bit period out of the maximum cross‐correlation value
hits during a bit period out of the maximum cross‐correlation value ![]() are given by [8]:
are given by [8]:

where the factor ![]() is due to the fact that data bit “0” is not encoded. In the case of
is due to the fact that data bit “0” is not encoded. In the case of ![]() , the percentage of the total power of a data bit that interferes with a bit of the new call is
, the percentage of the total power of a data bit that interferes with a bit of the new call is ![]() , since 1 out of
, since 1 out of ![]() “1” of the codewords may interfere. In this case
“1” of the codewords may interfere. In this case ![]() . When
. When ![]() , the probability of interference is given by:
, the probability of interference is given by:

The condition expressed by ( 9.18) is also examined at the receiver, when a passive call tries to become active. Based on ( 9.18), we define the LBP ![]() that a service‐class
that a service‐class ![]() call is blocked due to the presence of the additive noise, when the number of in‐service active calls is
call is blocked due to the presence of the additive noise, when the number of in‐service active calls is ![]() , as:
, as:

or
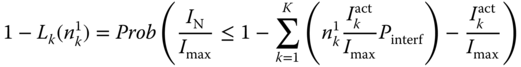
Assuming that the total additive noise ![]() follows a Gauss distribution
follows a Gauss distribution ![]() , the variable
, the variable ![]() follows a Gauss distribution
follows a Gauss distribution ![]() too. Therefore, the RHS of (9.22) is the CDF of the Gauss variable
too. Therefore, the RHS of (9.22) is the CDF of the Gauss variable ![]() and is denoted as
and is denoted as ![]() :
:

where ![]() is the well‐known error function.
is the well‐known error function.
By using ( 9.22) and (9.23), we can calculate ![]() of service‐class
of service‐class ![]() calls by substituting
calls by substituting  :
:

Now, let ![]() be the capacity of the (real) shared link, which is the PON capacity. This is discrete because it is expressed by the total number of codewords, which could be assigned to the PON users. When a call is transferred to a passive state, it is assumed that a number of fictitious codewords are assigned to it from a total number of fictitious codewords
be the capacity of the (real) shared link, which is the PON capacity. This is discrete because it is expressed by the total number of codewords, which could be assigned to the PON users. When a call is transferred to a passive state, it is assumed that a number of fictitious codewords are assigned to it from a total number of fictitious codewords ![]() . That is, each passive call is accommodated in a fictitious shared link of fictitious discrete capacity
. That is, each passive call is accommodated in a fictitious shared link of fictitious discrete capacity ![]() [9]. The number of codewords assigned to a passive call is equal to the number of codewords assigned to the call at the active state.
[9]. The number of codewords assigned to a passive call is equal to the number of codewords assigned to the call at the active state.
To show the role of the fictitious system in call admission, let ![]() be the number of codewords of all active calls and
be the number of codewords of all active calls and ![]() be the number of codewords of all passive calls:
be the number of codewords of all passive calls:

If an arriving call is not blocked because of local blocking, then the CAC works as follows, taking into account the hard blocking conditions of (5.1) and (5.2). Let ![]() be the set of all permissible states of the whole system (real and fictitious links), then the occupancy distribution of
be the set of all permissible states of the whole system (real and fictitious links), then the occupancy distribution of ![]() , denoted by
, denoted by ![]() , is given by a two‐dimensional approximate recursive formula, which is similar to ( 9.13):
, is given by a two‐dimensional approximate recursive formula, which is similar to ( 9.13):

where ![]() and
and ![]() for the real and the fictitious link, respectively, and
for the real and the fictitious link, respectively, and ![]() is the occupied capacity of the system, given by:
is the occupied capacity of the system, given by:

and

9.4 Further Reading
Due to the relationship between the f‐ON–OFF model and the EnMLM (see Section 9.1.2.1), the f‐ON–OFF model can be extended to include various characteristics of the EnMLM extensions (see, e.g., Chapter ). Thus, the interested reader may actually study extensions of the EnMLM and consider as a candidate model the f‐ON–OFF model, especially when the combination of call blocking and burst blocking is necessary.
References
- 1 I. Moscholios, M. Logothetis and M. Koukias, An ON–OFF multirate loss model of finite sources. IEICE Transactions on Communications, E90‐B(7):1608–1619, July 2007.
- 2 G. Stamatelos and J. Hayes, Admission control techniques with application to broadband networks. Computer Communications, 17(9):663–673, September 1994.
- 3 I. Moscholios, M. Logothetis and M. Koukias, An ON–OFF multi‐rate loss model with a mixture of service‐classes of finite and infinite number of sources. Proceedings of IEEE ICC, Seoul, Korea, May 2005.
- 4 J. Vardakas, I. Moscholios, M. Logothetis and V. Stylianakis, Performance analysis of OCDMA PONs supporting multi‐rate bursty traffic. IEEE Transactions on Communications, 61(8):3374–3384, August 2013.
- 5 C.‐S. Weng and J. Wu, Optical orthogonal codes with nonideal cross correlation. IEEE/OSA Journal of Lightwave Technology, 19(12):1856–1863, December 2001.
- 6 W. Ma, C. Zuo and J. Lin, Performance analysis on phase‐encoded OCDMA communication system. IEEE/OSA Journal of Lightwave Technology, 20(5):798–803, May 2002.
- 7 X. Wang and K. Kitayama, Analysis of beat noise in coherent and incoherent time‐spreading OCDMA. IEEE/OSA Journal of Lightwave Technology, 22(19):2226–2235, October 2004.
- 8 H.‐W. Chen, G.‐C. Yang, C.‐Y. Chang, T.‐C. Lin and W. C. Kwong, Spectral efficiency study of two multirate schemes for asynchronous optical CDMA. IEEE/OSA Journal of Lightwave Technology, 27(14):2771–2778, July 2009.
- 9 J. Vardakas, I. Moscholios, M. Logothetis and V. Stylianakis, On code reservation in multi‐rate OCDMA passive optical networks. Proceedings of IEEE CSNDSP, Poznan, Poland, July 2012.

