In This Chapter
Nowadays, wireless connectivity is king. For example, wireless phones have gone from being a toy of the technological elite to a permanent fixture on the hip of the common man. The shorts that I'm wearing right now have a special pocket just for a cellphone to ride in; when I'm without my phone, it usually carries a 5th Avenue candy bar. (Perhaps that was too personal ...sorry.)
Because people have become accustomed to keeping in touch from wherever they are, they also want to have access to their network, at least within their house or workplace, without the hassle of cables. (Which, by the way, are magnets for pets that enjoy a good chew toy.) This desire for convenience and the advances in wireless technology have combined to bring you the concept of the wireless network — as well as wireless coffee shops, wireless access providers, and even wireless gaming centers. (In fact, Apple's iPhone is a wireless Internet marvel, with instant connectivity to any Bluetooth-enabled Mac and full-featured e-mail and browsing that'll knock your socks off.)
Now you can be connected to your home local area network (LAN) and your shared Internet connection (which I cover in Book VII, Chapter 4) from your balcony, deck, lounge chair in the yard, or even your bedroom. In this chapter, I talk about how wireless networks work and then I give you a lot of information to help you get the right pieces to free yourself — securely, mind you — from the world of the wired.
Wireless networks aren't all that different from their wired siblings. In this chapter, I discuss some of the features and limitations of wireless networking, but you must first be familiar with a foundation of information.
Because of the technology involved in wireless networks and how things are changing rapidly in this area, you'll find yourself swimming in a sea of acronyms and other techno-babble. Although you don't need to know every little detail to be able to set up your own wireless network, you should know some of these terms so that you can avoid getting stung by hackers or stuck with equipment that's on the verge of obsolescence.
Here's a quick list of terms that you'll see on your road to becoming a wireless network guru:
WLAN: WLAN stands for Wireless LAN. If you read previous chapters in this minibook, you know that a LAN (local area network) is just a bunch of connected computers and other devices.
IEEE: This stands for Institute of Electrical and Electronics Engineers, which is an organization that approves standards that allow computers, network equipment, and just about anything else electronic to play nicely together. Sometimes IEEE helps create these standards before approving them, and sometimes it just approves standards that others have produced.
802.11: This is the part of the IEEE standards that deals specifically with wireless networking.
Note
Although wireless is usually generically referred to as wireless networks (or sometimes even Wi-Fi), it's all really a wireless form of Ethernet.
Wireless access point: A wireless access point, or WAP, is a device that allows wireless network devices to connect to a wired Ethernet network.
Service Set Identifier: The Service Set Identifier, or SSID, is used to tell your computer the name of the wireless network that you want to use.
Wired Equivalency Privacy: Wired Equivalency Privacy, or WEP, is an encryption that wireless networks can use to keep your wireless network more secure from snoopers and hackers.
Wi-Fi Protected Access: Usually referred to as WPA, this is a security protocol that's more robust and harder to crack than WEP. The latest version, WPA2, is a common security feature on today's wireless hardware.
Ad Hoc mode: An Ad Hoc wireless network is one in which each wireless device talks directly with all other wireless devices.
Infrastructure mode: This is where all wireless devices talk to a WAP, and the WAP then talks to other wireless devices and the wired network.
As I cover the different parts of wireless networking and how to set it up, you'll find yourself using these terms over and over. Before you know it, you'll be spouting these wireless-related acronyms like a pro. (No, really. I'm not kidding.)
One of the first things that you might notice when you start looking into wireless networking is the existence of different wireless standards. You should at least be aware that these different standards exist: That way, you can be sure to get wireless network components that will work together because some of the different wireless standards are not compatible. (Feel free to photocopy this list and stick it on your fridge door.)
IEEE 802.11b has another name that you'll likely see on product advertisements, literature, or boxes in stores: Wi-Fi, which stands for Wireless Fidelity. (Kinda like that cutting-edge Hi-Fi stereo from the '60s and '70s, where Hi-Fi stands for High Fidelity.) Most folks proclaim Wi-Fi as only 802.11b. Wi-Fi was the first version of wireless Ethernet. This version of wireless runs at speeds up to 11 million bits per second, or 11 Mbps. The reason I say that it runs at speeds up to 11 Mbps is because the actual speed at which the data is transferred depends on things like signal strength and quality. When the conditions are such that your signal strength or quality is decreased — such as an inconvenient concrete wall between you and your AirPort Base Station — you might find that your wireless connection changes down to 5.5 Mbps, 2 Mbps, or even as slow as 1 Mbps.
802.11b has been largely supplanted in current wireless networking, and almost all the equipment you can buy today is either 802.11g or 802.11n (both of which I cover in a moment). However, if you're working with older computers and existing 802.11b hardware, any networking equipment you buy should be backward compatible with 802.11b.
Tip
Apple's AirPort network cards and standard-issue AirPort Base Station used 802.11b. In fact, it's time for Mac owners to swell with pride yet again: Apple was the first computer company to ship 802.11b hardware. (Back then, in 1999, it was the original AirPort Base Station.) Now, of course, Apple has raised the bar with AirPort Extreme, which I discuss later in this chapter, and the AirPort Express mobile Base Station.
In theory, Wi-Fi network cards have the ability to communicate with other Wi-Fi devices and WAPs that are up to 1,000 feet away. Having said that, realize that 1,000 feet is a generous estimate when outdoors on a clear day with no wind blowing — you see what I'm getting at. (You're more likely to see a wildebeest wearing a hula skirt in your living room than see that kind of distance indoors.) In reality, when you set up your wireless network, things such as walls — especially concrete walls, as in basements — and areas with lots of electrical wiring decrease the distance that you can cover. If you use a WAP, plan on no more than 150 feet between wireless computers and the WAP. However, your mileage might vary.
Warning
That 11 Mbps bandwidth is shared between all computers using it. Collisions can also occur if more than one computer tries to communicate at the same time. If you have a lot of people on your wireless network, the network will get noticeably slower because of increased collisions. Remember that the total bandwidth is shared among the computers on the wireless network. This applies not only to Wi-Fi but also to the 802.11a (which I cover in the nearby sidebar) and the 802.11g standards.
Warning
One last thing about 802.11b networking: Wi-Fi uses the 2.4 GHz frequency range. It actually uses 11 different channels, but they're all around the 2.4 GHz range. If you're using a 2.4 GHz cordless phone or even a microwave, using either device can definitely interfere with or even shut down your wireless network. Keep this in mind when you buy your next phone or wonder why your file transfers stop when you're communing with Orville Redenbacher in the microwave.
Apple's release of the first generation of AirPort Extreme provided both the speed of 802.11a and the compatibility with Wi-Fi. That's because it used the 802.11g standard, which operates at speeds up to 54 Mbps (as did 802.11a) but will also operate at the same frequency ranges and play nicely with existing 802.11b equipment. (Notice that we're heading in the right direction again when it comes to naming conventions. Go figure.)
Tip
Apple was once again the first company to offer 802.11g hardware as standard equipment. Feel free to enjoy the Superiority Dance yet again.
Naturally, there's a downside: 802.11g returned to that pesky 2.4 GHz range, so your cordless phone and microwave can also wreak the same havoc that they did with your original AirPort equipment.
I would be remiss if I didn't mention the current wireless standard from IEEE: 802.11n. Most third-party manufacturers (including Apple) now offer only 802.11n wireless equipment. Apple's 802.11n products include the current AirPort Extreme base station, the AirPort Extreme hardware in all of the MacBook line, and the spiffy Apple TV.
Why the hubbub? Oh, I forgot to mention that 802.11n can deliver throughput in excess of 100 Mbps! Don't bet your house that you'll get that kind of speed, though — as with the other members of the 802.11 family, that's likely to be a theoretical maximum speed.
You can't go wrong with the 802.11n standard — think superfast wireless connections in your household or office. Ahh, technology....
I should also mention Bluetooth — a strange name for a wireless standard, I admit, but it works like a charm. Bluetooth devices use 2.4 GHz as well, but they're designed only for very short distances ...up to only about 30 feet. Bluetooth is the future for linking mobile devices (such as personal digital assistants and cell phones) and external peripherals (such as wireless keyboards and mice) to your MacBook. In fact, Bluetooth can turn your MacBook into a completely cordless machine — except for the power cord, of course. Snow Leopard provides built-in support for Bluetooth through the iSync application and the Bluetooth pane in System Preferences.
Are you worried about the security of your AirPort wireless network? You should be, bunkie. Imagine someone in the next apartment or house — or standing right in your street — intercepting and monitoring your data from your wireless network.
But before you decide to toss the idea of a wireless network, keep this in mind: Even though it is technically possible that someone might camp out on your doorstep in order to gain access to your wireless network, for most home networks, this possibility isn't very probable. Even if someone tries to gain access to your wireless network and perhaps even sniff your network — a techno-nerd term meaning to record all the data flying around a network — there isn't a whole lot someone can do with that information.
Tip
If a friend invites you for an evening of war driving, think "recreational mobile hacking." War driving is the act of driving through neighborhoods in a car equipped with a laptop computer and a wireless network card. The payoff? If the hacker is lucky enough to locate a house with an open wireless network, we're talking free wireless Internet access ...from the comfort of his car! (Not to mention any shared files or information that's available on that network.) Again, keep security in mind when installing wireless hardware, and these bozos will get nothing from your network.
You might say, "But I use my credit card on the Internet to buy stuff." Sure, this is a valid concern; however, if you purchase things on the Internet with your credit card, you should already be using a secure connection provided by the Web site for your personal information so that the data you're sending across your wireless network is already encrypted and relatively safe from thieves. (You can find more on this when I discuss Safari in detail in Book VI, Chapter 5.)
"I have shared my files on my computer. Can the Bad Guys access those shared files?" Another good question, but if you read Book VII, Chapter 2, you know that you have to create an account for those whom you want to access your files. Unless the would-be hacker is very good at guessing usernames and passwords, your files are pretty safe, too.
This is not to say that you bear absolutely no risk of being hacked. If a legitimate user on your wireless network connects to your computer and starts transferring a file, a would-be hacker could potentially record all the traffic and then reconstruct the file that was sent from the data that was recorded. In other words, a hacker could grab that user's username and password. That's where WPA comes in.
Wi-Fi Protected Access, or WPA, is A Good Thing (even if it makes for a silly-sounding acronym). It's currently the standard encryption protocol offered for home wireless networking — WPA2 standard is the latest version, and is even better at defending your wireless network. As you might expect, all of Apple's current AirPort wireless hardware uses WPA2 security, as does most of the wireless hardware you'll find on the shelf at your local Hardware Heaven electronics store. (It's still a good idea to check the specifications on the box, though, to make sure that WPA2 is supported.)
WPA2 works well as a deterrent to keep the wrong people out of your stuff. Although WPA2 isn't going to ward off the spies at the National Security Agency, it's good enough to protect home and small-business networks.
WEP is an old friend of mine. Short for Wired Equivalency Privacy, it's another ridiculous acronym for another wireless security system. WEP was one of the first widely supported wireless encryption schemes, but in today's world, WEP is now outdated and pretty easy for a hacker to outwit. I strongly recommend that your network use WPA2 whenever possible.
Apple's implementation of WEP comes in two varieties: 40 bit and 128 bit. The more bits used in the encryption, the more secure (and the better) it is.
To use WEP, you need to select a WEP key, which is really just a code word:
The longer the key, the better.
When making a key, use something like ab8sher7234ksief87 (something that's random with letters and numbers) as opposed to something, like mykey, that's easily guessed.
If you're using an Ad Hoc wireless network, all the computers need to have their wireless network card configured with the same WEP key in order to communicate. If you're using a WAP to connect to the rest of the network, you need to use the same key on your computers that you've configured on your WAP.
Warning
One thing to note about WEP is that it's been broken, meaning that someone has figured out how to undo the encryption that WEP provides. For businesses, especially those with sensitive data, WEP isn't a good security solution.
Lightweight Extensible Authentication Protocol (LEAP) is an encryption protocol developed by Cisco Systems for superior security in the business world. To use LEAP, you need to have a server that's set up to enable users to log in to gain permission to the wireless network. After you initially log in (authenticate) to your network, LEAP changes encryption keys on the fly at a time interval that you determine. You could set it so that every 15 minutes your encryption key is changed: Even if someone is in that hypothetical tent on your front lawn, he could never record enough packets to figure out your key because it changes so often.
Tip
Setting up a server so that you can use LEAP isn't something for the novice to attempt. I would encourage you to read up on LEAP only if you're very serious about airtight security on your WLAN. The Cisco Web site (www.cisco.com) is a good place to read about LEAP.
Tip
All current AirPort Extreme wireless network cards and Base Stations are compatible with the Cisco LEAP for higher security.
On to the good stuff. This section describes how to set up an Ad Hoc or infrastructure-based WLAN (wireless LAN).
Note
All of today's MacBooks come with an AirPort Extreme (802.11n) card built in, so you don't have to add or install any wireless hardware to create or use a wireless network!
Using an Ad Hoc network — also called a computer-to-computer network — is a fairly easy thing to accomplish in Mac OS X. Plus, you're not limited to just Macs: With an Ad Hoc network, you can also swap niceties with PCs and PDAs that have 802.11b/g/n network interface cards (NICs) installed. This Ad Hoc network is great for setting up an impromptu network in a classroom, exchanging recipes and pictures at a family reunion in a park, or blowing your friend up while gaming across the aisle of a Greyhound bus at 70 mph.
To set up an Ad Hoc network, you first have to create the computer-to-computer network on one of your Macs. This takes advantage of the AirPort Software Base Station that's built into Snow Leopard.
To create a computer-to-computer network, follow these steps:
Click the AirPort status icon on the menu bar.
Tip
If you haven't set Snow Leopard to display your AirPort status in the Finder menu bar, follow these steps:
Open the Network pane in System Preferences and choose the AirPort entry in the list at the left of the pane.
Enable the Show AirPort Status in Menu Bar check box.
Close the System Preferences window to save your changes.
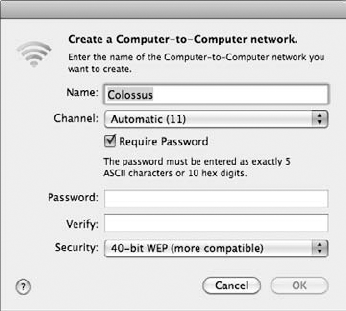
Click Create Network to display the dialog that you see in Figure 3-1.
Enter a name for your network.
Mark the Require Password check box to turn on WEP encryption.
Enter a password for your network and then enter it again to confirm it.
Tip
Although you can leave encryption disabled, I highly recommend that you turn it on and choose a password for that extra bit of security. (Just call me Security Man.) Note that the password must be an exact length (which is determined by whether you choose a 40-bit [5-character] key or a 128-bit [13-character] key).
In general, channels 1, 6, and 11 are the only ones that don't overlap other channels — and are therefore the best choices to use. If you're close to other WAPs, AirPort Base Stations, or other Ad Hoc networks, try to find a channel that's not being used, or performance can be degraded. (If you have only one access point, it doesn't matter which channel you select — just allow Snow Leopard to automatically select a channel, which is typically Channel 11.)
Click OK.
Creating a computer-to-computer network gives the illusion of having an AirPort Base Station. So for people to join your network, they would follow the same steps as those they would use to join any other AirPort network, as I cover in the next section.
After one computer is running a computer-to-computer network or you've set up and configured an AirPort/AirPort Extreme Base Station, you're ready to invite other computers with wireless hardware to the party.
After you have a network set up on one of your wireless-enabled computers, you just need to have the other wireless-enabled computers join that network. You can use the same process, as I describe here, to join any wireless network:
Click the AirPort status icon on the menu bar.
A list of existing network connections appears in the AirPort menu.
Select an existing network connection that you'd like to join.
Tip
If you want to join a network whose name doesn't appear in the list — also called a closed network, follow these steps:
Select Join Other Network from the AirPort status menu.
Enter the name of the network that you want to join and the password (if any is required).
A closed network is another added measure of security — one that's good enough for most people because it's very unlikely that a hacker is going to try to hack a hidden network.
To disconnect from an AirPort/AirPort Extreme network, you can turn off your AirPort card altogether, which I cover in the next section. (Simplicity, they say, is an art.) Another way is to simply connect to another AirPort network — but this option is really only useful if you actually want to connect to another network.
Being able to turn your AirPort/AirPort Extreme hardware on and off actually has its uses:
You might want to use your MacBook in a place where your wireless card shouldn't be used, like
An airplane (when they tell you to turn off all cell phones)
A hospital area that doesn't allow cell phones or other wireless devices
Turning off your AirPort/AirPort Extreme hardware conserves your MacBook's battery life.
To turn your AirPort equipment on or off via the AirPort status icon on the menu bar, give it a click and choose Turn AirPort On/Off from the resulting menu.