Types of VPNs
Based on the definition of a virtual private network, the following could be considered VPN technologies:
![]() IPsec: Implements security of IP packets at Layer 3 of the OSI model, and can be used for site-to-site VPNs and remote-access VPNs.
IPsec: Implements security of IP packets at Layer 3 of the OSI model, and can be used for site-to-site VPNs and remote-access VPNs.
![]() SSL: Secure Sockets Layer implements security of TCP sessions over encrypted SSL tunnels of the OSI model, and can be used for remote-access VPNs (as well as being used to securely visit a web server that supports it via HTTPS).
SSL: Secure Sockets Layer implements security of TCP sessions over encrypted SSL tunnels of the OSI model, and can be used for remote-access VPNs (as well as being used to securely visit a web server that supports it via HTTPS).
![]() MPLS: Multiprotocol Label Switching and MPLS Layer 3 VPNs are provided by a service provider to allow a company with two or more sites to have logical connectivity between the sites using the service provider network for transport. This is also a type of VPN (called MPLS L3VPN), but there is no encryption by default. IPsec could be used on top of the MPLS VPN to add confidentiality (through encryption) and the other benefits of IPsec to protect the Layer 3 packets. MPLS L3VPNs are not the primary type of VPNs we focus on for the rest of this chapter and book. The primary VPNs that provide encryption, data integrity, authentication of who the peer is on the other end of the VPN, and so on use IPsec or SSL.
MPLS: Multiprotocol Label Switching and MPLS Layer 3 VPNs are provided by a service provider to allow a company with two or more sites to have logical connectivity between the sites using the service provider network for transport. This is also a type of VPN (called MPLS L3VPN), but there is no encryption by default. IPsec could be used on top of the MPLS VPN to add confidentiality (through encryption) and the other benefits of IPsec to protect the Layer 3 packets. MPLS L3VPNs are not the primary type of VPNs we focus on for the rest of this chapter and book. The primary VPNs that provide encryption, data integrity, authentication of who the peer is on the other end of the VPN, and so on use IPsec or SSL.
Two Main Types of VPNs
There are two major categories into which VPNs could be placed: remote-access and site-to-site. The following are details about each, including when they might be used:
![]() Remote-access VPNs: Some users might need to build a VPN connection from their individual computer to the corporate headquarters (or to the destination they want to connect to). This is referred to as a remote-access VPN connection. Remote-access VPNs can use IPsec or Secure Sockets Layer (SSL) technologies for their VPN. Many Cisco customers use the Cisco AnyConnect client for remote access SSL VPNs. SSL VPN use is more prevalent, even though the Cisco AnyConnect client also supports IPsec (IKEv2).
Remote-access VPNs: Some users might need to build a VPN connection from their individual computer to the corporate headquarters (or to the destination they want to connect to). This is referred to as a remote-access VPN connection. Remote-access VPNs can use IPsec or Secure Sockets Layer (SSL) technologies for their VPN. Many Cisco customers use the Cisco AnyConnect client for remote access SSL VPNs. SSL VPN use is more prevalent, even though the Cisco AnyConnect client also supports IPsec (IKEv2).
![]() Site-to-site VPNs: The other main VPN implementation is by companies that may have two or more sites that they want to connect securely together (likely using the Internet) so that each site can communicate with the other site or sites. This implementation is called a site-to-site VPN. Site-to-site VPNs traditionally use a collection of VPN technologies called IPsec.
Site-to-site VPNs: The other main VPN implementation is by companies that may have two or more sites that they want to connect securely together (likely using the Internet) so that each site can communicate with the other site or sites. This implementation is called a site-to-site VPN. Site-to-site VPNs traditionally use a collection of VPN technologies called IPsec.
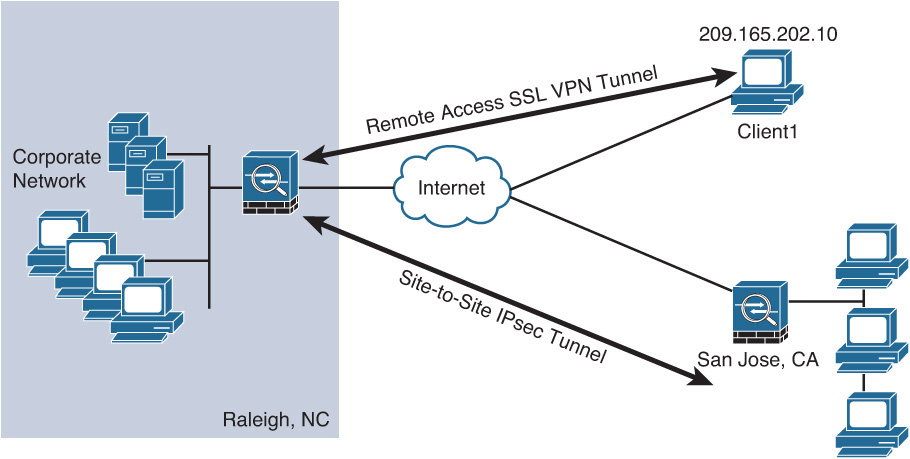
Figure 5-1 shows an example of site-to-site and remote-access VPNs. The Cisco ASA in the Raleigh, North Carolina, corporate headquarters is configured to accept remote-access SSL VPN connections, in addition to a site-to-site tunnel with a branch in San Jose, California.