MDM Deployment Options
Within the BYOD solution, there are generally two available options for deployment of MDM, as described in the sections that follow.
On-Premise MDM Deployment
In an on-premise deployment, MDM application software is installed on servers that are located within the corporate data center and are completely supported and maintained by the network staff of the corporation.
The benefits of having an on-premise MDM solution include greater control over management of the BYOD solution, a potentially higher degree of security, particularly with respect to intellectual property, and, depending on the vertical in which the organization resides, an easier means of meeting certain regulatory compliance.
The on-premise MDM solution diagram shown in Figure 4-2 consists of the following topology and network components:
![]() Data center: In addition to the core and distribution layer switches, the data center consists of the Cisco ISE to enforce posture assessment and access control as well as DNS/DHCP servers to provide DNS/DHCP services for network connectivity, a CA server to enable onboarding of endpoints that meet certificate requirements for access to the corporate network, and an AD server that restricts access to only those users with valid authentication credentials.
Data center: In addition to the core and distribution layer switches, the data center consists of the Cisco ISE to enforce posture assessment and access control as well as DNS/DHCP servers to provide DNS/DHCP services for network connectivity, a CA server to enable onboarding of endpoints that meet certificate requirements for access to the corporate network, and an AD server that restricts access to only those users with valid authentication credentials.
![]() Internet edge: The Internet edge, in addition to providing connectivity to the public Internet, includes an ASA firewall to enforce security controls for all traffic going to and coming from the Internet. Also located in the Internet edge layer is a WLC, which is dedicated to any of the APs in the network to which guest users can connect. The last key component in the Internet edge layer is the on-premise MDM, which provides all the policies and profiles, digital certificates, applications, data, and configuration settings for all the BYOD devices that require connectivity to the corporate network.
Internet edge: The Internet edge, in addition to providing connectivity to the public Internet, includes an ASA firewall to enforce security controls for all traffic going to and coming from the Internet. Also located in the Internet edge layer is a WLC, which is dedicated to any of the APs in the network to which guest users can connect. The last key component in the Internet edge layer is the on-premise MDM, which provides all the policies and profiles, digital certificates, applications, data, and configuration settings for all the BYOD devices that require connectivity to the corporate network.
![]() Services: In Figure 4-2, this module contains the WLC for all APs to which the corporate users connect; however, any other network-based services required for the corporate network (for example, Network Time Protocol [NTP]) can potentially be found within the Services module.
Services: In Figure 4-2, this module contains the WLC for all APs to which the corporate users connect; however, any other network-based services required for the corporate network (for example, Network Time Protocol [NTP]) can potentially be found within the Services module.
![]() Core: There are no other functions served by the Core module for the BYOD solution beyond what it normally provides. The Core serves as the main distribution and routing point for all network traffic traversing the corporate network environment.
Core: There are no other functions served by the Core module for the BYOD solution beyond what it normally provides. The Core serves as the main distribution and routing point for all network traffic traversing the corporate network environment.
![]() Campus building: A distribution switch provides the main ingress/egress point for all network traffic entering and exiting from the campus environment. All users requiring network connectivity within the campus building do so through either hardwired connections to the access switches or via WLAN access to the corporate APs.
Campus building: A distribution switch provides the main ingress/egress point for all network traffic entering and exiting from the campus environment. All users requiring network connectivity within the campus building do so through either hardwired connections to the access switches or via WLAN access to the corporate APs.
Cloud-Based MDM Deployment
In a cloud-based MDM deployment, MDM application software is hosted by a managed service provider who is solely responsible for the deployment, management, and maintenance of the BYOD solution.
The benefits of having a cloud-based MDM solution include a much more simplified solution from a customer perspective because the customer is no longer responsible for configuring, operating, and maintaining the MDM software. Giving up this control, however, brings with it some potential concerns with the overall security of the solution. The cloud-based solution also brings with it greater scalability, flexibility, and speed of deployment over an on-premise MDM solution.
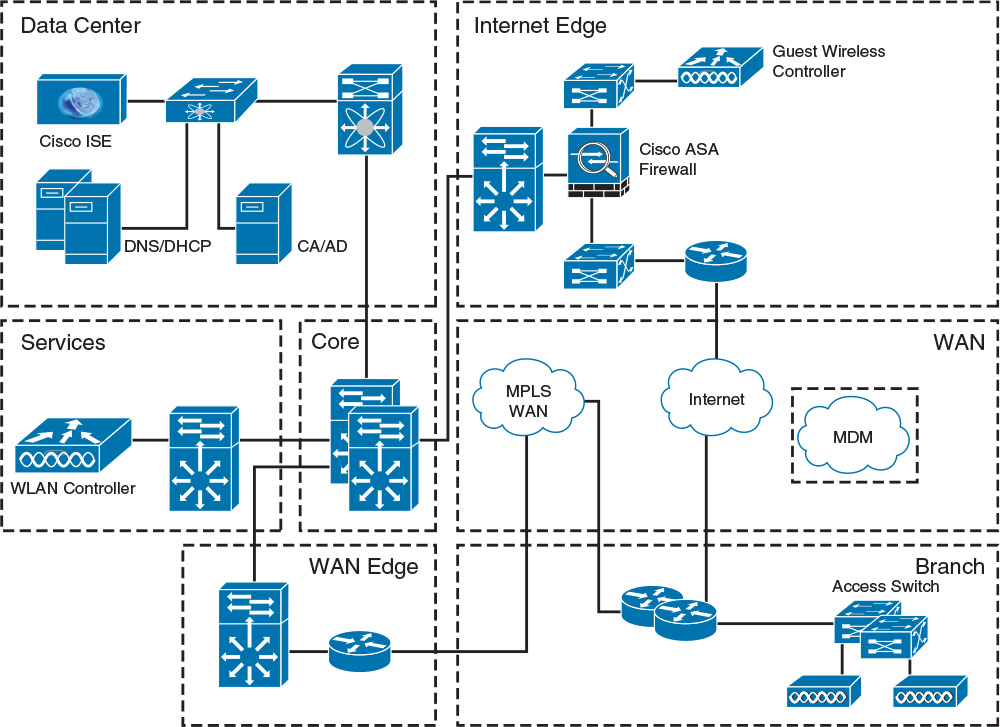
The cloud-based MDM solution diagram shown in Figure 4-3 consists of the following topology and network components:
![]() Data Center: In addition to the core and distribution layer switches, the data center consists of the Cisco ISE to enforce posture assessment and access control, in addition to DNS/DHCP servers to provide DNS/DHCP services for network connectivity, a CA server to enable onboarding of endpoints that meet certificate requirements for access to the corporate network, and an AD server that restricts access to only those users with valid authentication credentials.
Data Center: In addition to the core and distribution layer switches, the data center consists of the Cisco ISE to enforce posture assessment and access control, in addition to DNS/DHCP servers to provide DNS/DHCP services for network connectivity, a CA server to enable onboarding of endpoints that meet certificate requirements for access to the corporate network, and an AD server that restricts access to only those users with valid authentication credentials.
![]() Internet edge: The Internet edge, in addition to providing connectivity to the public Internet, includes an ASA firewall to enforce security controls for all traffic going to and coming from the Internet. Also located in the Internet edge layer is a WLC that is dedicated to any of the APs in the network to which guest users can connect.
Internet edge: The Internet edge, in addition to providing connectivity to the public Internet, includes an ASA firewall to enforce security controls for all traffic going to and coming from the Internet. Also located in the Internet edge layer is a WLC that is dedicated to any of the APs in the network to which guest users can connect.
![]() WAN: The WAN module, which you didn’t see within the on-premise MDM solution, serves three primary functions for the BYOD solution: (1) It provides MPLS VPN connectivity for the branch office back to corporate network, (2) Internet access for the branch office, and (3) access to the cloud-based MDM functionality. As with the on-premise solution, the cloud-based MDM provides all the policies and profiles, digital certificates, applications, data, and configuration settings for all of the BYOD devices that require connectivity to the corporate network.
WAN: The WAN module, which you didn’t see within the on-premise MDM solution, serves three primary functions for the BYOD solution: (1) It provides MPLS VPN connectivity for the branch office back to corporate network, (2) Internet access for the branch office, and (3) access to the cloud-based MDM functionality. As with the on-premise solution, the cloud-based MDM provides all the policies and profiles, digital certificates, applications, data, and configuration settings for all of the BYOD devices that require connectivity to the corporate network.
![]() WAN edge: The primary function of the WAN edge is to serve as the ingress/egress point for the MPLS WAN traffic entering from and exiting to the branch office environment.
WAN edge: The primary function of the WAN edge is to serve as the ingress/egress point for the MPLS WAN traffic entering from and exiting to the branch office environment.
![]() Services: In Figure 4-3, this module contains the WLC for all APs to which the corporate users connect; however, any other network-based services required for the corporate network (for example, NTP) can potentially be found within the Services module.
Services: In Figure 4-3, this module contains the WLC for all APs to which the corporate users connect; however, any other network-based services required for the corporate network (for example, NTP) can potentially be found within the Services module.
![]() Core: There are no other functions served by the Core module for the BYOD solution beyond what it normally provides. The Core serves as the main distribution and routing point for all network traffic traversing the corporate network environment.
Core: There are no other functions served by the Core module for the BYOD solution beyond what it normally provides. The Core serves as the main distribution and routing point for all network traffic traversing the corporate network environment.
![]() Branch office: In Figure 4-3, a pair of routers provides the main ingress/egress point for all network traffic entering and exiting from the branch office environment. All users requiring network connectivity within the branch office do so through either hardwired connections to the access switches or via WLAN access to the corporate APs.
Branch office: In Figure 4-3, a pair of routers provides the main ingress/egress point for all network traffic entering and exiting from the branch office environment. All users requiring network connectivity within the branch office do so through either hardwired connections to the access switches or via WLAN access to the corporate APs.