SNMP Features
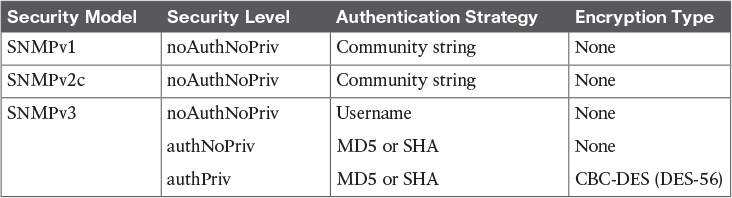
Simple Network Management Protocol (SNMP) has become a de facto standard for network management protocols. The intent of SNMP is to manage network nodes, such as network servers, routers, switches, and so on. SNMP versions range from version 1 to 3, with some intermediate steps in between. The later the version, the more security features it has. Table 11-5 describes some of the components of SNMP.
An SNMP manager can send information to, receive requested information from, or receive unsolicited information (called a trap) from a managed device (a router). The managed device runs an SNMP agent and contains the MIB.
Even though multiple SNMP messages might be sent between an SNMP manager and a managed device, consider the three broad categories of SNMP message types:
![]() GET: An SNMP GET message is used to retrieve information from a managed device.
GET: An SNMP GET message is used to retrieve information from a managed device.
![]() SET: An SNMP SET message is used to set a variable in a managed device or to trigger an action on a managed device.
SET: An SNMP SET message is used to set a variable in a managed device or to trigger an action on a managed device.
![]() Trap: An SNMP trap message is an unsolicited message sent from a managed device to an SNMP manager. It can be used to notify the SNMP manager about a significant event that occurred on the managed device.
Trap: An SNMP trap message is an unsolicited message sent from a managed device to an SNMP manager. It can be used to notify the SNMP manager about a significant event that occurred on the managed device.
Unfortunately, the ability to get information from or send configuration information to a managed device presents a potential security vulnerability. Specifically, if an attacker introduces a rogue NMS into the network, the attacker’s NMS might be able to gather information about network resources by polling the MIBs of managed devices. In addition, the attacker might launch an attack against the network by manipulating the configuration of managed devices by sending a series of SNMP SET messages.
Although SNMP does offer some security against such an attack, the security integrated with SNMPv1 and SNMPv2c is considered weak. Specifically, SNMPv1 and SNMPv2c use community strings to gain read-only access/read-write access to a managed device. You can think of a community string much like a password. Also, be aware that multiple SNMP-compliant devices on the market today have a default read-only community string of “public” and a default read-write community string of “private.”
The security weaknesses of SNMPv1 and SNMPv2c are addressed in SNMPv3. SNMPv3 uses the concept of a security model and a security level:
![]() Security model: A security model defines an approach for user and group authentications.
Security model: A security model defines an approach for user and group authentications.
![]() Security level: A security level defines the type of security algorithm performed on SNMP packets. Three security levels are discussed here:
Security level: A security level defines the type of security algorithm performed on SNMP packets. Three security levels are discussed here:
![]() noAuthNoPriv: The noAuthNoPriv (no authentication, no privacy) security level uses community strings for authentication and does not use encryption to provide privacy.
noAuthNoPriv: The noAuthNoPriv (no authentication, no privacy) security level uses community strings for authentication and does not use encryption to provide privacy.
![]() authNoPriv: The authNoPriv (authentication, no privacy) security level provides authentication using Hashed Message Authentication Code (HMAC) with message digest algorithm 5 (MD5) or Secure Hash Algorithm (SHA). However, no encryption is used.
authNoPriv: The authNoPriv (authentication, no privacy) security level provides authentication using Hashed Message Authentication Code (HMAC) with message digest algorithm 5 (MD5) or Secure Hash Algorithm (SHA). However, no encryption is used.
![]() authPriv: The authPriv (authentication, privacy) security level offers HMAC MD5, or SHA authentication and also provides privacy through encryption. Specifically, the encryption uses the Cipher Block Chaining (CBC) Data Encryption Standard (DES) (DES-56) algorithm.
authPriv: The authPriv (authentication, privacy) security level offers HMAC MD5, or SHA authentication and also provides privacy through encryption. Specifically, the encryption uses the Cipher Block Chaining (CBC) Data Encryption Standard (DES) (DES-56) algorithm.
As summarized in Table 11-6, SNMPv3 supports all three of the previously described security levels. Notice that SNMPv1 and SNMPv2 support only the noAuthNoPriv security level.
Through the use of the security algorithms, as shown in Table 11-6, SNMPv3 dramatically increases the security of network management traffic as compared to SNMPv1 and SNMPv2c. Specifically, SNMPv3 offers three primary security enhancements:
![]() Integrity: Using hashing algorithms, SNMPv3 can ensure that an SNMP message was not modified in transit.
Integrity: Using hashing algorithms, SNMPv3 can ensure that an SNMP message was not modified in transit.
![]() Authentication: Hashing allows SNMPv3 to validate the source of an SNMP message.
Authentication: Hashing allows SNMPv3 to validate the source of an SNMP message.
![]() Encryption: Using the CBC-DES (DES-56) encryption algorithm, SNMPv3 provides privacy for SNMP messages, making them unreadable by an attacker who might capture an SNMP packet.
Encryption: Using the CBC-DES (DES-56) encryption algorithm, SNMPv3 provides privacy for SNMP messages, making them unreadable by an attacker who might capture an SNMP packet.
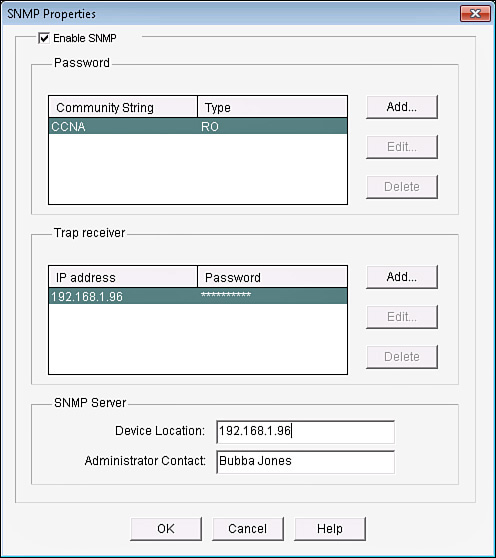
To configure SNMP on the router is simple, especially with CCP. If you know the community strings to use, and the IP address of the SNMP manager, you can configure it on the router by navigating to Configure > Router > SNMP and from there use the Edit button to add, change, or remove any of the SNMP-related settings. CCP enables command-line editing through the Utilities menu, but currently the SNMP Properties window does not support the configuration of SNMPv3. You can configure the basic SNMPv1 information, as shown in Figure 11-7.
The command-line output for this GUI would look similar to that shown in Example 11-13.
Example 11-13 Output Created by CCP for Implementing SNMPv1
snmp-server location 192.168.1.96
snmp-server contact Bubba Jones
snmp-server community CCNA RO
snmp-server host 10.1.0.26 trap cisK0tRap^
Example 11-14 shows the configuration for SNMPv3.
Example 11-14 SNMPv3 Configuration
! Enter global configuration mode
CCNA-Router# configure terminal
! Configure the community string along with an access-list to restrict access
CCNA-Router(config)# snmp-server community CCNA RO 99
! Create the IP Standard Access List defined in the previous step
CCNA-Router(config)# access-list 99 permit 192.168.1.0 /24
! Configure the v3 for no authentication (noauth)
CCNA-Router(config)# snmp-server group CCNA-group v3 noauth
! Configure a v3 user that resides in the v3 group
CCNA-Router(config)# snmp-server user CCNA-user CCNA-group v3
! Configure the community string and access-list to restrict SNMP to hosts in the
! 192.168.1.0/24 subnet
CCNA-Router(config)# snmp-server community CCNA RO 99
! Specify interface to be used for SNMP traps
CCNA-Router(config)# snmp-server trap-source FastEthernet0/1
! Specify the SNMP v3 server that will be allowed SNMP access
CCNA-Router(config)# snmp-server host 192.168.1.96 version 3 noauth CCNA-user
!