Implementing NFP
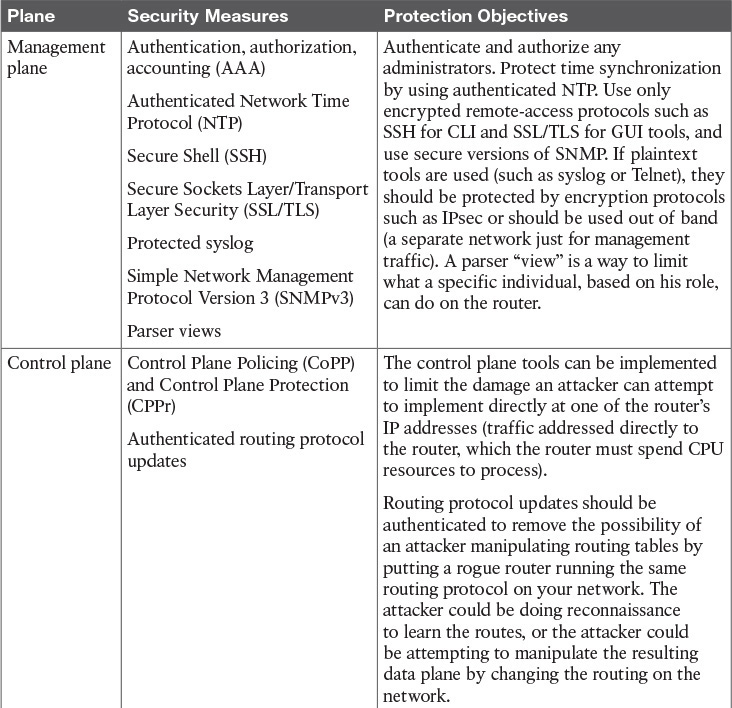
You learn more about each of these three planes later in this chapter as well as in each of the subsequent chapters dedicated to each of the three planes individually. Before that, however, Table 10-2 describes security measures you can use to protect each of the three planes.
As you might have noticed, NFP is not a single feature but rather is a holistic approach that covers the three components (that is, planes) of the infrastructure, with recommendations about protecting each one using a suite of features that you can implement across your network.
A command-line utility called auto secure implements security measures (several in each category) across all three of the planes. You will see the equivalent of auto secure in Cisco Configuration Professional (CCP), the graphical user interface (GUI) tool that you can use to manage routers) in the next chapter.
When implementing the best practices described by NFP, does that mean your network is going to be up forever and not have any problems? Of course not. If the network is designed poorly, with no fault tolerance, for example, and a device fails (because of a mechanical or software failure or a physical problem or because cables were removed), if you do not have the failovers in place to continue to move traffic, your data plane is going to suffer. Other factors, such as lack of change control or an administrator accidentally putting in the incorrect configuration, are, of course, ongoing potential opportunities for the network to stop functioning.