Chapter 8. PerformancePoint Services Security
PerformancePoint Services integration into SharePoint 2010 Enterprise has simplified security setup and maintenance by having the security maintained within SharePoint for development, deployment, and accessing the dashboards. From a data source perspective, the delegation has been changed from connecting on a server level to connecting on a per-data-source connection.
This chapter explains the data source delegation options, SharePoint permissions needed for deploying and using dashboards, and how groups are created within a SharePoint site.
Data Source Delegation
Data sources individually contain the method for connection when a PerformancePoint Services content item is retrieving its data. In the security model, PerformancePoint Services ensures that the data sources are not queried against from untrusted query objects and instead use content that is stored in a trusted location. The options for connecting are as follows:
• Unattended Service Account: Single shared access account to use for any connection that is not connecting on a per-user basis.
• Per-user Identity: The user account is used as the login account to the data source.
• Custom Data: Used for SQL Server Analysis Services data sources only and adds the current user as a custom property to the data connection.
The unattended service account requires setting up a secure store and the service account itself, which is configured in SharePoint Central Administration. The configuration steps are covered in Chapter 6, “PerformancePoint Services Configuration.”
To set up a data source connection to use a per-user identity connection, you must set up Kerberos delegation within the network. With regard to Kerberos configuration, the following Microsoft white paper illustrates the steps to be done by a domain administrator to the SharePoint farm and other servers and service accounts that PerformancePoint Services will be using for connecting: http://go.microsoft.com/fwlink/?LinkID=196600.
External data sources must exist in the same domain as the SharePoint farm. However, you can make external data sources outside of the domain in per-user scenarios. To do so, refer to “Planning Considerations for Services That Access External Data Sources” at http://technet.microsoft.com/en-us/library/cc560988.aspx#ConsiderationsForAccessingExternalData.
When an SQL Server Analysis Services (SSAS) data source is being used, an extra option is available for use as an authentication method: Unattended Service Account and Add Authenticated User Name in Connection String. When this option is set, the authenticated user is passed as part of the Custom Data property of the PropertyList in the session.
Figure 8.1 shows the result of enabling the Unattended Service Account and Add Authenticated User Name in Connection String option and clicking Test Data Source.
Figure 8.1. Additional SSAS authentication option.

To view the connection information being passed from PerformancePoint Services to the SSAS server, create a SQL Profiler trace to view the event.
In order to create a trace in SQL Server Profiler against the SSAS server, you must be a member of the Analysis Services server role.
The following steps create a trace to view the Authenticated User information:
- Launch SQL Server Profiler (StartProgramsMicrosoft SQL Server 2008Performance ToolsSQL Server Profiler).
- Click FileNew Trace, a Connect to Server window appears.
- Select Analysis Services as the Server Type and type in the name of the SSAS server in the Server name textbox and then click the Connect button.
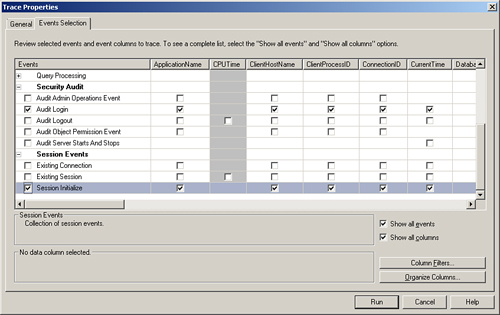
- A Trace Properties window appears with two tabs: General and Events Selection. Click on the Events Selection tab.
- Expand the Security Audit event and check the Audit Login event.
- Expand the Session Events event and check the Session Initialize event.
- After selecting the events, the Trace Properties window will look like Figure 8.2.
Figure 8.2. SQL Server Profiler trace property selection.
- Click the Run button to start the trace.
In the SQL Profiler trace, two events are captured when the Test Data Source button is clicked. An Audit Login event occurs, which displays information about the unattended service account that was configured for PerformancePoint Services. In addition, a Session Initialize event occurs that has the same connection information as the unattended service account. However, as displayed in Figure 8.3, the Property List XML contains the Custom Data property with the authenticated user information.
Figure 8.3. SQL Profiler trace containing the Custom Data property.

PerformancePoint Services and SharePoint Permissions
In PerformancePoint 2007, dashboard contents and items were stored in a separate Monitoring SQL Server database, at which point the dashboard was then deployed to a SharePoint site for interaction. In PerformancePoint Services, the content items are stored within SharePoint content SQL Server databases and use SharePoint permissions for saving the content into the database.
A PerformancePoint Services database, by default named PerformancePoint Service Application_GUID (the GUID is auto generated), is created on the SharePoint database server. However, the database is used for saving Scorecard comments and annotations, not the PerformancePoint content items.
For a typical dashboard, building Performance Point Services content is done as follows:
- Launch Dashboard Designer.
- Create a data source and save it to a SharePoint library.
- Create the PerformancePoint Services content and save it to a SharePoint list.
- Create a dashboard that uses the PerformancePoint Services content and deploy the dashboard to a dashboard library.
- View the dashboard and interact to perform analytics.
To execute any of these steps, you must have the requisite permissions set up within SharePoint for your Windows account, as shown in Table 8.1.
Table 8.1. PerformancePoint Tasks to SharePoint Permission

When you are using the Business Intelligence Center, SharePoint groups are initially created that contain the proper rights for creating and deploying dashboards. However, an administrator might want to create new groups within the site to structure the security differently than the default group set. To create new SharePoint site groups and assign users to the group, follow these steps:
- Click Site Actions and select Site Permissions.
- Click the Create Group button on the SharePoint site ribbon.
- On the Create Group page, supply a group name and select the permissions for the group as needed according to Table 8.1. Figure 8.4 displays the group permissions available.
Figure 8.4. Creating a SharePoint group.

- Click the Create button after setting the permissions for the group.
- Click the NewAdd Users button on the newly created group page to assign users to the group.
- Supply the user accounts to the Grant Permissions screen, as shown in Figure 8.5.
Figure 8.5. Assigning a user account.

- Click OK.
Summary
PerformancePoint Services has updated the architecture to remove a single method for data source authentication and allows for data source connections to be configured on a per-item basis. In addition, the saving of the content and deploying to SharePoint has now been brought into the SharePoint security model. By having SharePoint manage the security, PerformancePoint Services has simplified the overall administration of the application.
This chapter explained the different data source delegation methods, the mapping of Dashboard Designer tasks to SharePoint group permissions, and how to create the groups needed for the development and consumption of PerformancePoint Services content.
Best Practices
• When setting up Kerberos delegation, ensure that all servers reside in the same domain to be used for per-user identity data source connections.
• SharePoint group permissions are used for creating and storing Dashboard Designer content. Administrators should follow the same methodology established on other sites in the farm with regard to how users are granted appropriate access.
• To ensure that authentication methods are being used as expected with SQL Server Analysis Services data sources, capture Audit Login and Session Initialize events using the SQL Profiler in a trace that has these events selected.
