Chapter 15. Security Across the Technology Life Cycle
This chapter covers the following topics:
![]() End-to-End Solution Ownership: Topics discussed include operational activities, maintenance, commissioning/decommissioning, asset disposal, asset/object reuse, and general change management.
End-to-End Solution Ownership: Topics discussed include operational activities, maintenance, commissioning/decommissioning, asset disposal, asset/object reuse, and general change management.
![]() Systems Development Life Cycle: This section discusses the security system development life cycle (SSDLC)/security development life cycle (SDLC), the security requirements traceability matrix (SRTM), validation and acceptance testing, and security implications of agile, waterfall, and spiral software development methodologies.
Systems Development Life Cycle: This section discusses the security system development life cycle (SSDLC)/security development life cycle (SDLC), the security requirements traceability matrix (SRTM), validation and acceptance testing, and security implications of agile, waterfall, and spiral software development methodologies.
![]() Adapt Solutions to Address Emerging Threats and Security Trends: This section covers how to research emerging threats and security trends to adapt the enterprise’s security solutions and controls.
Adapt Solutions to Address Emerging Threats and Security Trends: This section covers how to research emerging threats and security trends to adapt the enterprise’s security solutions and controls.
![]() Asset Management (Inventory Control): This section discusses device-tracking technologies (including geolocation/GPS location) and object-tracking and containment technologies (including geotagging/geofencing and RFID).
Asset Management (Inventory Control): This section discusses device-tracking technologies (including geolocation/GPS location) and object-tracking and containment technologies (including geotagging/geofencing and RFID).
This chapter covers CAS-002 objective 4.3.
When managing the security of an enterprise, security practitioners must be mindful of security across the entire technology life cycle. As the enterprise changes and new devices and technologies are introduced, maintained, and retired, security practitioners must ensure that the appropriate security controls are deployed. Providing security across the technology life cycle includes understanding end-to-end solution ownership, implementing the systems development life cycle, adapting solutions to address emerging threats and security trends, and ensuring asset management.
Foundation Topics
End-to-End Solution Ownership
Security must be considered from a device’s or technology’s introduction until its retirement. Proper planning ensures that an enterprise is protected during device or technology design and introduction. Keep in mind that security is often compromised by rushing to implement a new technology or device. Security practitioners should ensure that management understands the need to fully assess any security issues with a new technology or device prior to deployment. After a device or technology is introduced, security practitioners must ensure that operational activities can be carried out in a secure manner. In addition, maintenance of the device or technology is crucial. When an asset has reached the end of its use, the enterprise must determine when to decommission the asset and whether to dispose of the asset or reuse/repurpose it. Finally, in any enterprise, change management is part of everyday operation. A formal change management process is necessary to ensure that changes are analyzed for their impact on security before implementation.
End-to-end solution ownership includes consideration of operational activities, maintenance, commissioning/decommissioning, asset disposal, asset/object reuse, and general change management.
Operational Activities
Operational activities are activities that are carried out on a daily basis when using a device or technology. Security controls must be in place to protect all operational activities and should be tested regularly to ensure that they are still providing protection. While operational activities include day-to-day activities, they also include adding new functionality, new applications, or completely new systems to the infrastructure. Any new introduction of any type will introduce risks to the enterprise. Therefore, it is imperative that security practitioners complete a risk analysis and deploy the needed security controls to mitigate risks.
Introduction of functionality, an application, or a system can affect an organization’s security policy. For example, an organization may have a policy in place that prevents the use of any wireless technology at the enterprise level. If a new device or technology requires wireless access, the organization will need to revisit the security policy to allow wireless access. However, the organization must ensure that the appropriate security controls are implemented when wireless access is added to the enterprise. Performing a security impact analysis examines the impact of the new functionality, application, or system on the organization’s confidentiality, integrity, and availability. Threats, vulnerabilities, and risks are covered in greater detail in Chapter 7, “Risk Mitigation Planning, Strategies, and Controls.”
Finally, as mentioned many other times throughout this book, security awareness and training are vital to ensure that day-to-day operational activities are carried out in a secure manner. Security awareness and training should be updated as new issues arise. Employees should attend this training at initial employment and at least once a year thereafter.
Maintenance
Maintenance involves ensuring that systems are kept up-to-date with patches, hotfixes, security updates, and service packs. Any updates should be tested in a lab environment before being introduced into production. When maintenance occurs, it is always necessary to reassess the security controls in place and to implement any new controls as risks are identified. Maintenance occurs for both hardware and software, and both of these assets are equally important in a maintenance plan. Just because a device or application is not used as much as others does not exempt it from getting timely updates.
Updating hardware and software can often have unanticipated consequences. A new application update may cause false positives on the enterprise firewall because the application communicates in a new manner. Simply ignoring a false positive (or disabling the alert) is not adequate. Security practitioners should research issues such as this to determine the best way to address the problem.
Another consequence could be that an update causes issues that cannot be resolved at the time of deployment. In such a case, it may be necessary to temporarily roll back the hardware or software to its previous state. However, it is important that the update not be forgotten. A plan should be implemented to ensure that the update is applied as quickly as possible. It may be necessary to allocate personnel to ensure that the issue is researched so that the update can be redeployed.
Let’s look at a maintenance example and its effects on security. Say that after a system update causes significant downtime, the chief information security officer (CISO) asks the IT manager who was responsible for the update. The IT manager responds that five different people have administrative access to the system, so it is impossible to determine the responsible party. To increase accountability in order to prevent this situation from reoccurring, the IT manager should implement an enforceable change management system and enable user-level auditing on all servers.
Any maintenance program should include documenting all maintenance activities, including the personnel who completed the maintenance, the type of maintenance that occurred, the result of the maintenance, and any issues that arose, along with the issue resolution notes. This documentation will provide guidance in the future.
Commissioning/Decommissioning
Commissioning an asset is the process of implementing the asset in an enterprise, and decommissioning an asset is the process of retiring an asset from use in an enterprise. When an asset is placed into production, the appropriate security controls should be deployed to protect the asset. These security controls may be implemented at the asset itself or on another asset within the enterprise, such as a firewall or router. When an asset is decommissioned, it is important that the data that is stored on the asset still be protected. Sometimes an asset is decommissioned temporarily, and sometimes the decommissioning is permanent. No matter which is the case, it is important that the appropriate asset disposal and asset reuse policies be followed to ensure that the organization’s confidentiality, integrity, and availability are ensured. In most cases, you need to back up all the data on a decommissioned asset and ensure that the data is completely removed from the asset prior to disposal. These policies should be periodically reviewed and updated as needed, especially when new assets or asset types are added to the enterprise.
Let’s look at an example. Suppose an information security officer (ISO) asks a security team to randomly retrieve discarded computers from the warehouse dumpster. The security team retrieves two older computers and a broken multifunction network printer. The security team connects the hard drives from the two computers and the network printer to a computer equipped with forensic tools. They retrieve PDF files from the network printer hard drive but are unable to access the data on the two older hard drives. As a result of this finding, the warehouse management should update the hardware decommissioning procedures to remediate the security issue.
Let’s look at another example. Say that a new vendor product has been acquired to replace a legacy product. Significant time constraints exist due to the existing solution nearing end-of-life with no options for extended support. For this project, it has been emphasized that only essential activities be performed. To balance the security posture and the time constraints, you should test the new solution, migrate to the new solution, and decommission the old solution.
Asset Disposal
Asset disposal occurs when an organization has decided that an asset will no longer be used. During asset disposal, the organization must ensure no data remains on the asset. The most reliable, secure means of removing data from magnetic storage media, such as a magnetic hard drive, is through degaussing, which exposes the media to a powerful alternating magnetic field. It removes any previously written data, leaving the media in a magnetically randomized (blank) state. Some other disposal terms and concepts with which you should be familiar are:
![]() Data purging: This involves using a method such as degaussing to make the old data unavailable even with forensics. Purging renders information unrecoverable against laboratory attacks (forensics).
Data purging: This involves using a method such as degaussing to make the old data unavailable even with forensics. Purging renders information unrecoverable against laboratory attacks (forensics).
![]() Data clearing: This involves rendering information unrecoverable by a keyboard.
Data clearing: This involves rendering information unrecoverable by a keyboard.
![]() Remanence: This term refers to any data left after the media has been erased. This is also referred to as data remnants or remnant magnetization. Some assets must be completely destroyed, including physical destruction to protect the contents. For example, the most cost-effective solution for sanitizing a DVD with sensitive information on it is to shred the DVD. A solid-state drive requires a full format or a secure erase utility to ensure that data cannot be retrieved from it.
Remanence: This term refers to any data left after the media has been erased. This is also referred to as data remnants or remnant magnetization. Some assets must be completely destroyed, including physical destruction to protect the contents. For example, the most cost-effective solution for sanitizing a DVD with sensitive information on it is to shred the DVD. A solid-state drive requires a full format or a secure erase utility to ensure that data cannot be retrieved from it.
Functional hard drives should be overwritten three times prior to disposal or reuse, according to Department of Defense (DoD) Instruction 5220.22. Modern hard disks can defy conventional forensic recovery after a single wiping pass, based on NIST Special Publication (SP) 800-88.
Keep in mind that encrypting the data on a hard drive will always make the data irretrievable without the encryption key, provided that the encryption method used has not been broken. For all media types, this is the best method for protecting data.
For example, suppose a company plans to donate 1,000 used computers to a local school. The company has a large research and development department, and some of the computers were previously used to store proprietary research data. The security administrator should be concerned about data remnants on the donated machines. If the company does not have a device sanitization section in its data handling policy, the best course of action for the security administrator to take would be to delay the donation until all storage media on the computers can be sanitized.
An organization should also ensure that an asset is disposed of in a responsible manner that complies with local, state, and federal laws and regulations.
Asset/Object Reuse
When an organization decides to reuse an asset, a thorough analysis of the asset’s original use and new use should be understood. If the asset will be used in a similar manner, it may only be necessary to remove or disable unneeded applications or services. However, it may be necessary to return the asset to its original factory configuration. If the asset contains a hard drive or other storage medium, the media should be thoroughly cleared of all data, especially if it contains sensitive, private, or confidential data.
General Change Management
Technology evolves, grows, and changes over time. Examples of changes that can occur include:
![]() Operating system configuration
Operating system configuration
![]() Software configuration
Software configuration
![]() Hardware configuration
Hardware configuration
Companies and their processes also evolve and change, which is a good thing. But change should be managed in a structured way so as to maintain a common sense of purpose about the changes. By following recommended steps in a formal process, change can be prevented from becoming a problem. The following are guidelines to include as a part of any change control policy:
![]() All changes should be formally requested.
All changes should be formally requested.
![]() Each request should be analyzed to ensure that it supports all goals and polices.
Each request should be analyzed to ensure that it supports all goals and polices.
![]() Prior to formal approval, all costs and effects of the methods of implementation should be reviewed.
Prior to formal approval, all costs and effects of the methods of implementation should be reviewed.
![]() After they’re approved, the change steps should be developed.
After they’re approved, the change steps should be developed.
![]() During implementation, incremental testing should occur, relying on a predetermined fallback strategy, if necessary.
During implementation, incremental testing should occur, relying on a predetermined fallback strategy, if necessary.
![]() Complete documentation should be produced and submitted with a formal report to management.
Complete documentation should be produced and submitted with a formal report to management.
One of the key benefits of following this method is that it yields documentation that can be used in future planning. Lessons learned can be applied, and even the process itself can be improved through analysis.
For the CASP exam, you need to keep in mind that change management works with configuration management to ensure that changes to assets do not unintentionally diminish security. Because of this, all changes must be documented, and all network diagrams, both logical and physical, must be updated constantly and consistently to accurately reflect each asset’s configuration now and not as it was two years ago. Verifying that all change management policies are being followed should be an ongoing process.
Let’s look at an example. Suppose that a company deploys more than 15,000 client computers and 1,500 server computers. The security administrator is receiving numerous alerts from the IDS of a possible infection spreading through the network via the Windows file sharing service. The security engineer believes that the best course of action is to block the file sharing service across the organization by placing ACLs on the internal routers. The organization should call an emergency change management meeting to ensure that the ACL will not impact core business functions.
In many cases, it is beneficial to form a change control board. The tasks of the change control board can include:
![]() Ensuring that changes made are approved, tested, documented, and implemented correctly
Ensuring that changes made are approved, tested, documented, and implemented correctly
![]() Meeting periodically to discuss change status accounting reports
Meeting periodically to discuss change status accounting reports
![]() Maintaining responsibility for ensuring that changes made do not jeopardize the soundness of the verification system
Maintaining responsibility for ensuring that changes made do not jeopardize the soundness of the verification system
Systems Development Life Cycle (SDLC)
When an organization defines new functionality that must be provided either to its customers or internally, it must create systems to deliver that functionality. Many decisions have to be made, and a logical process should be followed in making those decisions. This process is called the systems development life cycle (SDLC). Rather than being a haphazard approach, the SDLC provides clear and logical steps to follow to ensure that the system that emerges at the end of the development process provides the intended functionality with an acceptable level of security.
The steps in the SDLC are as follows:
1. Initiate
2. Acquire/develop
3. Implement
4. Operate/maintain
5. Dispose
In the initiation phase, the realization is made that a new feature or functionality is desired or required in the enterprise. This new feature might constitute an upgrade to an existing asset or the purchase or development of a new asset. In either case, the initiation phase includes making a decision about whether to purchase or develop the product internally.
In this stage, an organization must also give thought to the security requirements of the solution. A preliminary risk assessment can detail the CIA requirement and concerns. Identifying these issues at the outset is important so that these considerations can guide the purchase or development of the solution. The earlier in the SDLC that the security requirements are identified, the more likely that the issues will be successfully addressed in the final product.
In the acquisition stage of the SDLC, a series of activities takes place that provides input to facilitate making a decision about acquiring or developing the solution; the organization then makes a decision on the solution. The activities are designed to get answers to the following questions:
![]() What functions does the system need to perform?
What functions does the system need to perform?
![]() What potential risks to CIA are exposed by the solution?
What potential risks to CIA are exposed by the solution?
![]() What protection levels must be provided to satisfy legal and regulatory requirements?
What protection levels must be provided to satisfy legal and regulatory requirements?
![]() What tests are required to ensure that security concerns have been mitigated?
What tests are required to ensure that security concerns have been mitigated?
![]() How do various third-party solutions address these concerns?
How do various third-party solutions address these concerns?
![]() How do the security controls required by the solution affect other parts of the company security policy?
How do the security controls required by the solution affect other parts of the company security policy?
![]() What metrics will be used to evaluate the success of the security controls?
What metrics will be used to evaluate the success of the security controls?
The answers to these questions should guide the questions during the acquisition step as well as the steps that follow this stage of the SDLC.
In the implementation stage, senior management formally approves of the system before it goes live. Then the solution is introduced to the live environment, which is the operation/maintenance stage, but not until the organization has completed both certification and accreditation. Certification is the process of technically verifying the solution’s effectiveness and security. The accreditation process involves a formal authorization to introduce the solution into the production environment by management. It is during this stage that the security administrator would train all users on how to protect company information when using the new system and on how to recognize social engineering attacks.
The process doesn’t end right when the system begins operating in the environment. Doing a performance baseline is important so that continuous monitoring can take place. The baseline ensures that performance issues can be quickly determined. Any changes over time (addition of new features, patches to the solution, and so on) should be closely monitored with respect to the effects on the baseline.
Instituting a formal change management process, as discussed in the “General Change Management” section, earlier in this chapter, ensures that all changes are both approved and documented. Because any changes can affect both security and performance, special attention should be given to monitoring the solution after any changes are made.
Finally, vulnerability assessments and penetration testing after the solution is implemented can help discover any security or performance problems that might either be introduced by a change or arise as a result of a new threat.
The disposal stage consists of removing the solution from the environment when it reaches the end of its usefulness. When this occurs, an organization must consider certain issues, including:
![]() Does removal or replacement of the solution introduce any security holes in the network?
Does removal or replacement of the solution introduce any security holes in the network?
![]() How can the system be terminated in an orderly fashion so as not to disrupt business continuity?
How can the system be terminated in an orderly fashion so as not to disrupt business continuity?
![]() How should any residual data left on any systems be removed?
How should any residual data left on any systems be removed?
![]() How should any physical systems that were part of the solution be disposed of safely?
How should any physical systems that were part of the solution be disposed of safely?
![]() Are there any legal or regulatory issues that would guide the destruction of data?
Are there any legal or regulatory issues that would guide the destruction of data?
For the CASP exam, you need to understand how to cover the SDLC from end to end. For example, suppose a company wants to boost profits by implementing cost savings on non-core business activities. The IT manager seeks approval for the corporate email system to be hosted in the cloud. The compliance officer must ensure that data life cycle issues are taken into account. The data life cycle end-to-end in this situation would be data provisioning, data processing, data in transit, data at rest, and deprovisioning.
In conjunction with the SDLC, security practitioners must also understand the Security System Development Life Cycle (SSDLC)/Security Development Life Cycle (SDL), security requirements traceability matrix (SRTM), validations and acceptance testing, and security implications of agile, waterfall, and spiral software development methodologies.
Security System Development Life Cycle (SSDLC)/Security Development Life Cycle (SDL)
Integrating security into the SDLC has been formally documented by the National Institute of Standards and Technology (NIST). The security system development life cycle (SSDLC) follows the same basic steps as the SDLC and includes major security activities as part of the steps. For full information, security practitioners should consult NIST SP 800-64. The following guidelines are taken directly from this publication. The security development life cycle (SDL) has the same steps as the SSDLC but usually involves the overall security of the organization, while the SSDLC includes security as part of systems design.
During systems initiation, the following security activities should occur:
![]() Initiate security planning.
Initiate security planning.
![]() Identify key security roles.
Identify key security roles.
![]() Identify sources of security requirements, such as relevant laws, regulations, and standards.
Identify sources of security requirements, such as relevant laws, regulations, and standards.
![]() Ensure that all key stakeholders have a common understanding, including security implications, considerations, and requirements.
Ensure that all key stakeholders have a common understanding, including security implications, considerations, and requirements.
![]() Outline any initial thoughts on key security milestones, including time frames or triggers that signal a security step is approaching.
Outline any initial thoughts on key security milestones, including time frames or triggers that signal a security step is approaching.
![]() Provide a security category for the system.
Provide a security category for the system.
![]() Assess the business impact of the system.
Assess the business impact of the system.
![]() Assess the privacy impact of the system.
Assess the privacy impact of the system.
![]() Ensure the use of a secure information system development processes.
Ensure the use of a secure information system development processes.
A new or replacement system has its business case approved during systems initiation stage. In preparation for a requirements workshop, an architect works with a business analyst to ensure that appropriate security requirements have been captured. This leads to the creation of the business requirements document.
During systems acquisition or development, the following security activities should occur:
![]() Assess the risk to the system.
Assess the risk to the system.
![]() Design the security architecture.
Design the security architecture.
![]() Select or develop, document, and implement security controls.
Select or develop, document, and implement security controls.
![]() Develop security documentation.
Develop security documentation.
![]() Conduct developmental, functional, and security testing.
Conduct developmental, functional, and security testing.
Testing is one of the most important aspects of systems acquisition. It is during this time that any issues with the new system should be discovered, including latency or other performance issues. If proper testing is not completed, problems can occur during implementation that will result in the need to take the new system offline until the problem can be resolved.
During system implementation and assessment, the following security activities should occur:
![]() Develop a detailed plan for certification and accreditation.
Develop a detailed plan for certification and accreditation.
![]() Integrate security into established systems.
Integrate security into established systems.
![]() Assess system security.
Assess system security.
![]() Authorize the system.
Authorize the system.
![]() Test the system for security functionality and resistance to attack.
Test the system for security functionality and resistance to attack.
During systems operations and maintenance, the following security activities should occur:
![]() Review operational readiness.
Review operational readiness.
![]() Perform configuration management and control.
Perform configuration management and control.
![]() Conduct continuous monitoring.
Conduct continuous monitoring.
During systems disposal or sunset, the following security activities should occur:
![]() Build and execute a disposal or transition plan.
Build and execute a disposal or transition plan.
![]() Ensure information preservation.
Ensure information preservation.
![]() Sanitize the media.
Sanitize the media.
![]() Dispose of the hardware and software.
Dispose of the hardware and software.
![]() Formally close the system.
Formally close the system.
Let’s look at an example of what happens when a new solution must be deployed and the organization must consider security life cycle–related concerns. Suppose a security engineer at a major financial institution prototypes multiple secure network configurations. The testing focuses on understanding the impact each potential design will have on the three major security tenets of the network. All designs must consider the stringent compliance and reporting requirements for most worldwide financial institutions. The security concerns related to deploying the final design include:
![]() Decommissioning the existing network smoothly
Decommissioning the existing network smoothly
![]() Implementing maintenance and operations procedures for the new network in advance
Implementing maintenance and operations procedures for the new network in advance
![]() Ensuring compliance with applicable regulations and laws
Ensuring compliance with applicable regulations and laws
Security Requirements Traceability Matrix (SRTM)
A security requirements traceability matrix (SRTM) documents the security requirements that a new asset must meet. The matrix maps the requirements to security controls and verification efforts in a grid, such as an Excel spreadsheet. Each row in the grid documents a new requirement, and the columns document the requirement identification number, description of the requirement, source of the requirement, test objective, and test verification method. It allows security practitioners and developers to ensure that all requirements are documented, met in the final design, and tested properly.
An SRTM would help to determine whether an appropriate level of assurance to the security requirements specified at the project origin are carried through to implementation.
Let’s look at an example. Suppose a team of security engineers applies regulatory and corporate guidance to the design of a corporate network. The engineers generate an SRTM based on their work and a thorough analysis of the complete set of functional and performance requirements in the network specification. The purpose of an SRTM in this scenario is to allow certifiers to verify that the network meets applicable security requirements.
Validation and Acceptance Testing
Validation testing ensures that a system meets the requirements defined by the client, and acceptance testing ensures that a system will be accepted by the end users. If a system meets the client’s requirements but is not accepted by the end users, its implementation will be greatly hampered. If a system does not meet the client’s requirements, the client will probably refuse to implement the system until the requirements are met.
Validation testing should be completed before a system is formally presented to the client. Once validation testing has been completed, acceptance testing should be completed with a subset of the users.
Validation and acceptance testing should not just be carried out for systems. As a security practitioner, you will need to make sure that validation and acceptance testing are carried out for any security controls that are implemented in your enterprise. If you implement a new security control that does not fully protect against a documented security issue, there could be repercussions for your organization. If you implement a security control that causes problems, delays, or any other user acceptance issues, employee morale will suffer. Finding a balance between the two is critical.
Security Implications of Agile, Waterfall, and Spiral Software Development Methodologies
When you implement security activities across the technology life cycle, you may need to use the agile, waterfall, and spiral software development methodologies. As a security practitioner, you need to understand the security implications of these methodologies.
Agile Software Development
Agile software development is an iterative and incremental approach. Developers work on small modules. As users’ requirements change, developers respond by addressing the changes. Changes are made as work progresses. Testing and customer feedback occur simultaneously with development. The agile method prioritizes collaboration over design.
With the agile software development methodology, the highest priority is to satisfy the customer. Requirements for the software change often. New deliveries occur at short intervals. Developers are trusted to do their jobs. A working application is the primary measure of success.
Risks with this software development method include:
![]() Security testing may be inadequate.
Security testing may be inadequate.
![]() New requirements may not be assessed for their security impact.
New requirements may not be assessed for their security impact.
![]() Security issues may be ignored, particularly if they would cause schedule delays.
Security issues may be ignored, particularly if they would cause schedule delays.
![]() Security often falls by the wayside.
Security often falls by the wayside.
![]() Software that functions correctly may not necessarily be secure.
Software that functions correctly may not necessarily be secure.
To address these issues, organizations should include a security architect as part of the development team. Security awareness training should be mandatory for all team members. Security standards and best practices should be documented and followed by the entire team. Security testing tools should be used to test each development piece.
The Waterfall Model
The waterfall model is a linear and sequential model. In this model, the team moves to the next phase only after the activities in the current phase are over. However, the team cannot return to the previous stage. The phases of this model are:
![]() Requirements and analysis
Requirements and analysis
![]() Design
Design
![]() System integration
System integration
![]() Testing and debugging
Testing and debugging
![]() Delivery
Delivery
![]() Maintenance
Maintenance
With the waterfall software development methodology, the development stages are not revisited, projects take longer, and testing is harder because larger pieces are released. Often risks are ignored because they can negatively impact the project. Risks with this software development method include:
![]() Developers cannot return to the design stage if a security issue is discovered.
Developers cannot return to the design stage if a security issue is discovered.
![]() Developers may end up with software that is no longer needed or that doesn’t address current security issues.
Developers may end up with software that is no longer needed or that doesn’t address current security issues.
![]() Security issues are more likely to be overlooked due to time constraints.
Security issues are more likely to be overlooked due to time constraints.
The Spiral Model
The spiral model was introduced due to the shortcomings in the waterfall model. In it, the activities of software development are carried out like a spiral. The software development process is broken down into small projects. The phases of the spiral model are as follows:
![]() Planning
Planning
![]() Risk analysis
Risk analysis
![]() Engineering
Engineering
![]() Coding and implementation
Coding and implementation
![]() Evaluation
Evaluation
With the spiral software development methodology, requirements are captured quickly and can be changed easily. But if the initial risk analysis is inadequate, the end project will have issues. Involving a risk analysis expert as part of the team can help ensure that the security is adequately assessed and designed.
Agile and spiral are usually considered better methods than the waterfall method, especially considering how quickly the security landscape can change. However, each organization needs to decide which method best works for their enterprise.
Adapt Solutions to Address Emerging Threats and Security Trends
New threats and security trends emerge every day. Organizations and the security practitioners they employ must adapt to these new threats and understand new security trends to ensure that the enterprise is protected. But the security objective of an organization rarely changes.
Retail organizations are increasingly under attack. One company released a public statement about hackers breaching their security and stealing private customer data. Unfortunately, it seems that not every major retailer took notice when this attack occurred, as almost monthly a new victim came forth. As a result, banks and other financial institutions were forced to issue new credit/debit cards to their customers. These attacks affected the retail companies, their customers, and the financial institutions. What could these companies have done differently to prevent these attacks? Perhaps more should be shared within the retail industry and between security professionals when these types of attacks occur. Occurrences like this will become the norm unless we find some solutions, and this is just one recent example of emerging threats to which organizations must adapt.
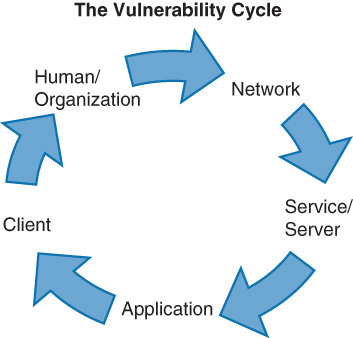
A popular vulnerability cycle that explains the order of vulnerability types that attackers run through over time is taught in many security seminars. This vulnerability cycle is shown in Figure 15-1.
Trends tend to work through this vulnerability cycle. A trending period where human interaction and social engineering are prevalent will soon be followed by a period where network attacks are prevalent. Once organizations adapt, attackers logically move to the next area in the cycle: services and servers. As time passes, organizations adapt, but so do the attackers. As a security professional, you must try to stay one step ahead of the attackers. Once you have implemented a new security control or solution, you cannot rest! You must then do your research, watch your enterprise, and discover the new threat or trend. One thing is for sure: A security practitioner with real skills and willingness to learn and adapt will always have job security!
Asset Management (Inventory Control)
Asset management and inventory control across the technology life cycle are critical to ensuring that assets are not stolen or lost and that data on assets is not compromised in any way. Asset management and inventory control are two related areas. Asset management involves tracking the devices that an organization owns, and inventory control involves tracking and containing inventory. All organizations should implement asset management, but not all organizations need to implement inventory control.
Device-Tracking Technologies
Device-tracking technologies allow organizations to determine the location of a device and also often allow the organization to retrieve the device. However, if the device cannot be retrieved, it may be necessary to wipe the device to ensure that the data on the device cannot be accessed by unauthorized users. As a security practitioner, you should stress to your organization the need to implement device-tracking technologies and remote wiping capabilities.
Geolocation/GPS Location
Device-tracking technologies include geolocation or Global Positioning System (GPS) location. With this technology, location and time information about an asset can be tracked, provided that the appropriate feature is enabled on the device. For most mobile devices, the geolocation or GPS location feature can be enhanced through the use of Wi-Fi networks. A security practitioner must ensure that the organization enacts mobile device security policies that include the mandatory use of GPS location features. In addition, it will be necessary to set up appropriate accounts that allow personnel to use the vendor’s online service for device location. Finally, remote locking and remote wiping features should be seriously considered, particularly if the mobile devices contain confidential or private information.
Object Tracking and Containment Technologies
Object tracking and containment technologies are primarily concerned with ensuring that inventory remains within a predefined location or area. Object tracking technologies allow organizations to determine the location of inventory. Containment technologies alert personnel within the organization if inventory has left the perimeter of the predefined location or area.
For most organizations, object tracking and containment technologies are used only for inventory assets above a certain value. For example, most retail stores implement object containment technologies for high-priced electronics devices and jewelry. However, some organizations implement these technologies for all inventory, particularly in large warehouse environments.
Technologies used in this area include geotagging/geofencing and radio frequency identification (RFID).
Geotagging/Geofencing
Geotagging involves marking a video, photo, or other digital media with a GPS location. In recent news, this feature has received bad press because attackers can use it to pinpoint personal information, such as the location of a person’s home. However, for organizations, geotagging can be used to create location-based news and media feeds. In the retail industry, it can be helpful for allowing customers to locate a store where a specific piece of merchandise is available.
Geofencing uses the GPS to define geographical boundaries. A geofence is a virtual barrier, and alerts can occur when inventory enters or exits the boundary. Geofencing is used in retail management, transportation management, human resources management, law enforcement, and other areas.
RFID
RFID uses radio frequency chips and readers to manage inventory. The chips are placed on individual pieces or pallets of inventory. RFID readers are placed throughout the location to communicate with the chips. Identification and location information are collected as part of the RFID communication. Organizations can customize the information that is stored on an RFID chip to suit their needs.
Two types of RFID systems can be deployed: active reader/passive tag (ARPT) and active reader/active tag (ARAT). In an ARPT system, the active reader transmits signals and receives replies from passive tags. In an ARAT system, active tags are woken with signals from the active reader.
RFID chips can be read only if they are within a certain proximity of the RFID reader. A recent implementation of RFID chips is the Walt Disney Magic Band, which is issued to visitors at Disney resorts and theme parks. The band verifies park admission and allows visitors to reserve attraction restaurant times and pay for purchases in the resort.
Different RFID systems are available for different wireless frequencies. If your organization decides to implement RFID, it is important that you fully research the advantages and disadvantages of different frequencies. However, that information is beyond the scope of the CASP exam.
Exam Preparation Tasks
You have a couple of choices for exam preparation: the exercises here and the exam simulation questions on the CD-ROM.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 15-1 lists these key topics and the page number on which each is found.
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
data remanence
systems development life cycle (SDLC)
security system development life cycle (SSDLC)
security requirements traceability matrix (SRTM)
radio frequency identification (RFID)
Review Questions
1. As your company’s security practitioner, you must be concerned about end-to-end solution ownership. You have been asked to develop a policy that will cover any assets that are added to the enterprise. Which areas should you consider? (Choose all the apply.)
a. operational activities
b. asset disposal
c. asset reuse
d. maintenance
2. You have been hired as a security analyst for your company. Recently, several assets have been marked to be removed from the enterprise. You need to document the steps that should be taken in relation to security. Which of the following guidelines should be implemented?
a. Deploy the appropriate security controls on the asset.
b. Deploy the most recent updates for the asset.
c. Back up all the data on the asset and ensure that the data is completely removed.
d. Shred all the hard drives in the asset.
3. Your organization has decided to formally adopt a change management process. You have been asked to design the process. Which of the following guidelines should be part of this new process?
a. Only critical changes should be fully analyzed.
b. After formal approval, all costs and effects of implementation should be reviewed.
c. Change steps should be developed only for complicated changes.
d. All changes should be formally requested.
4. You have been asked to join the development team at your organization to provide guidance on security controls. During the first meeting, you discover that the development team does not fully understand the SDLC. During which phase of this life cycle is the system actually deployed?
a. Acquire/develop
b. Implement
c. Initiate
d. Operate/maintain
5. A development team has recently completed the deployment of a new learning management system (LMS) that will replace the current legacy system. The team successfully deploys the new LMS, and it is fully functional. Users are satisfied with the new system. What stage of the SDLC should you implement for the old system?
a. Dispose
b. Operate/maintain
c. Initiate
d. Acquire/develop
6. You have been asked to participate in the deployment of a new firewall. The project has just started and is still in the initiation stage. Which step should be completed as part of this stage?
a. Develop security controls.
b. Assess the system security.
c. Ensure information preservation.
d. Assess the business impact of the system.
7. You are working with a project team to deploy several new firewalls. The initiation stage is complete, and now the team is engaged in the acquisition stage. Which step should the team complete as part of this stage?
a. Provide security categories for the new routers.
b. Test the routers for security resiliency.
c. Design the security architecture.
d. Update the routers with the latest updates from the vendor.
8. What documents the security requirements that a new asset must meet?
a. SDLC
b. SRTM
c. SSDLC
d. RFID
9. Which of the following is a device-tracking technology?
a. geolocation
b. geotagging
c. geofencing
d. RFID
10. Which technology uses chips and receivers to manage inventory?
a. geolocation
b. geotagging
c. SRTM
d. RFID