Chapter 14. Secure Communication and Collaboration
This chapter covers the following topics:
![]() Security of Unified Collaboration Tools: Tools covered include web conferencing, video conferencing, instant messaging, desktop sharing, remote assistance, presence, email, telephony, and collaboration sites.
Security of Unified Collaboration Tools: Tools covered include web conferencing, video conferencing, instant messaging, desktop sharing, remote assistance, presence, email, telephony, and collaboration sites.
![]() Remote Access: This section describes guidelines and measures to take to ensure secure remote access.
Remote Access: This section describes guidelines and measures to take to ensure secure remote access.
![]() Mobile Device Management: This section covers security issues with mobile device management, including a discussion of securing a bring your own device (BYOD) policy.
Mobile Device Management: This section covers security issues with mobile device management, including a discussion of securing a bring your own device (BYOD) policy.
![]() Over-the-Air Technologies Concerns: This section describes issues with and mitigation techniques for securing wireless technologies.
Over-the-Air Technologies Concerns: This section describes issues with and mitigation techniques for securing wireless technologies.
This chapter covers CAS-002 objective 4.2.
Increasingly, workers and the organizations for which they work are relying on new methods of communicating and working together that introduce new security concerns. As a CASP candidate, you need to be familiar with these new technologies, understand the security issues they raise, and implement controls that mitigate the security issues. This chapter describes these new methods and technologies, identifies issues, and suggests methods to secure these new workflow processes.
Foundation Topics
Security of Unified Collaboration Tools
Two intersecting trends are introducing new headaches for security professionals. People are working together or collaborating more while at the same time becoming more mobile and working in nontraditional ways, such as working from home. This means that sensitive data is being shared in ways we haven’t had to secure before. The following sections discuss the specific security issues that various collaboration tools and methods raise and the controls that should be put in place to secure these solutions.
Web Conferencing
Web conferencing has allowed companies to save money on travel while still having real-time contact with meeting participants. Web conferencing services and software often have robust meeting tools that allow for chatting, sharing documents, and viewing the screen of the presenter. Many also allow for video. (Video conferencing is specifically covered in the next section.) When the information you are chatting about and the documents you are sharing are of a sensitive nature, security issues arise, and you should take special care during the web conference. Specifically, some of the security issues are:
![]() Data leakage: Because web conference data typically resides on a shared server for a little while, there is always a possibility of the data leaking out of the conference into hostile hands.
Data leakage: Because web conference data typically resides on a shared server for a little while, there is always a possibility of the data leaking out of the conference into hostile hands.
![]() Uninvited guests: Most systems use a simple conference code for entrance to the conference, so there is always a possibility that uninvited guests will arrive.
Uninvited guests: Most systems use a simple conference code for entrance to the conference, so there is always a possibility that uninvited guests will arrive.
![]() Data capture en route: The possibility of information being captured en route is high. Using encrypting technologies can prevent this.
Data capture en route: The possibility of information being captured en route is high. Using encrypting technologies can prevent this.
![]() DoS attack: There is a possibility of DoS attacks on local servers when a web conferencing solution is integrated with existing applications.
DoS attack: There is a possibility of DoS attacks on local servers when a web conferencing solution is integrated with existing applications.
To address these issues, you should:
![]() Take ownership of the process of selecting the web conferencing solution. Often other departments select a product, and the IT and security departments are faced with reacting to whatever weaknesses the solution may possess.
Take ownership of the process of selecting the web conferencing solution. Often other departments select a product, and the IT and security departments are faced with reacting to whatever weaknesses the solution may possess.
![]() Ensure compatibility with all devices in your network by choosing products that use standard security and networking components, such as SSL.
Ensure compatibility with all devices in your network by choosing products that use standard security and networking components, such as SSL.
![]() Ensure that the underlying network itself is secured.
Ensure that the underlying network itself is secured.
![]() Define a process for selecting the product and using the product. The following four steps should be completed:
Define a process for selecting the product and using the product. The following four steps should be completed:
1. Define the allowed uses of the solution.
2. Identify security needs before selecting the product.
3. Ensure that usage scenarios and security needs are built into the request for proposal (RFP).
4. Include security practitioners in the planning and decision-making process.
![]() Disable or strongly audit read/write desktop mode, if supported by the product. This mode allows other meeting participants to access the host desktop.
Disable or strongly audit read/write desktop mode, if supported by the product. This mode allows other meeting participants to access the host desktop.
![]() Execute nondisclosure documents covering conferences that disclose confidential material or intellectual property.
Execute nondisclosure documents covering conferences that disclose confidential material or intellectual property.
![]() Ensure that unique passwords are generated for each conference to prevent reuse of passwords for inappropriately attending conferences.
Ensure that unique passwords are generated for each conference to prevent reuse of passwords for inappropriately attending conferences.
Consider requiring a VPN connection to the company network to attend conferences. If this approach is taken, you can provide better performance for the participants by disallowing split tunneling on the VPN concentrator. While split tunneling allows access to the LAN and the Internet at the same time, it reduces the amount of bandwidth available to each session.
Video Conferencing
While most or all of the video conferencing products produced in the past 10 years use 128-bit AES encryption, it is important to remember that no security solution is infallible. Recently, the NSA was accused of cracking the military-grade encryption (better then AES 128) to spy on a UN video conference. The same source reported that the NSA discovered that the Chinese were also attempting to crack the encryption. While it is still unknown if either the NSA or the Chinese actually succeeded, this story highlights the risks that always exist.
Having said that, in high-security networks (Department of Defense, Department of Homeland Security, etc.) that use video conferencing, additional security measures are typically taken to augment the solution. Some examples include:
![]() Device-level physical encryption keys that must be inserted each time the system is used and that are typically exchanged every 30 days
Device-level physical encryption keys that must be inserted each time the system is used and that are typically exchanged every 30 days
![]() Additional password keys that limit access to a device’s functions and systems
Additional password keys that limit access to a device’s functions and systems
![]() Session keys generated at the start of each session that are changed automatically during the session
Session keys generated at the start of each session that are changed automatically during the session
![]() Traffic transmitted on secure data networks that also use advanced encryption technologies
Traffic transmitted on secure data networks that also use advanced encryption technologies
Because 128-bit AES encryption is very secure, in most cases, video conferencing products are secure out of the box.
A nonproprietary approach to securing video conferences as well as VoIP traffic is to extend the H.323 standard to support DES encryption. H.323 is a standard for providing audio-visual communications sessions, such as web conferences, video conferences, and VoIP. Security for these sessions can be provided by H.235 extensions. H.235 includes the ability to negotiate services and functionality in a generic manner. It allows for the use of both standard and proprietary encryption algorithms. It provides a means to identify a person rather than a device, using a security profile that consists of either a password, digital certificates, or both.
In most cases, security issues don’t involve shortcomings in recent products but do involve the following:
![]() Not enabling the encryption
Not enabling the encryption
![]() Using outdated video systems that don’t support encryption
Using outdated video systems that don’t support encryption
![]() Failure in updating the associated software on video systems and other devices
Failure in updating the associated software on video systems and other devices
![]() Devices (such as gateways and video bridges) to which the system connects that either don’t support encryption or have encryption turned off
Devices (such as gateways and video bridges) to which the system connects that either don’t support encryption or have encryption turned off
![]() Deploying software solutions or services that either don’t encrypt or support weaker encryption
Deploying software solutions or services that either don’t encrypt or support weaker encryption
![]() Poor password management
Poor password management
Avoiding these issues can be accomplished by creating and following a process for selecting and using the product, as defined in the “Web Conferencing” section, earlier in this chapter.
Instant Messaging
Instant messaging has become so popular that many users prefer it to email when communicating with coworkers. It is so popular, in fact, that many email systems, such as Google Mail, have an integrated IM system. Users demand it, and thus security professionals need to learn how to secure it.
Table 14-1 lists the security issues that exist with IM systems and the associated measures to take to mitigate them.
Desktop Sharing
Desktop sharing involves a group of related technologies that allow for both remote login to a computer and real-time collaboration on the desktop of a remote user. Both functions use a graphical terminal emulator. Some of these products are built into an operating system, such as Microsoft’s Remote Desktop technology, while others are third-party applications, such as LogMeIn and GoToMyPC.
While these products certainly make managing remote computers and users easier, remote administration software is one of the most common attack vectors used by hackers. Issues that reduce the security of a remote administration solution include:
![]() Misconfiguration or poor deployment
Misconfiguration or poor deployment
![]() Outdated software
Outdated software
![]() Cached administrative credentials
Cached administrative credentials
![]() Poor administrative password management
Poor administrative password management
![]() Failure to adopt two-factor authentication
Failure to adopt two-factor authentication
![]() Lack of encryption
Lack of encryption
As a CASP candidate, you should know the following mitigation techniques to address these issues:
![]() Always use the latest version of the products.
Always use the latest version of the products.
![]() Install all updates.
Install all updates.
![]() If the solution will only be used in a LAN, block the port number used by the solution at the network perimeter.
If the solution will only be used in a LAN, block the port number used by the solution at the network perimeter.
![]() For mobile users, disable automatic listening on the device. This will prevent an open port in an untrusted network.
For mobile users, disable automatic listening on the device. This will prevent an open port in an untrusted network.
![]() Regularly review security logs for evidence of port scans.
Regularly review security logs for evidence of port scans.
![]() Secure access to configuration files used by the solution.
Secure access to configuration files used by the solution.
![]() Implement encryption.
Implement encryption.
![]() Control administrative access to the solution.
Control administrative access to the solution.
![]() Ensure logging settings that establish an audit trail.
Ensure logging settings that establish an audit trail.
![]() Train users on its proper usage.
Train users on its proper usage.
![]() Remove the software from computers on which it should never be used, such as secure servers.
Remove the software from computers on which it should never be used, such as secure servers.
![]() Implement policies to prevent its installation unless administrative approval is given.
Implement policies to prevent its installation unless administrative approval is given.
Remote Assistance
Remote assistance is a feature that often relies on the same technology as desktop sharing. In fact, one if its features is the ability to allow a technician to share a user’s desktop for the purpose of either teaching the user something or troubleshooting an issue for the user. Naturally, some of the same issues that exist for desktop sharing products also exist for remote assistance sessions.
First, the screen data that is sent back and forth between the user and the technician are typically in standard formats, making it easy to rebuild an image that is captured. Many products implement proprietary encryption, but in regulated industries, this type of encryption may not be legal. Always use the level of encryption required by your industry, such as Advanced Encryption Standard (AES).
Second, many remote assistance tools do not provide sufficient auditing capabilities, which are critical in industries like banking and healthcare. If auditing is an issue in your industry, choose a product with the ability to capture the detail you require for legal purposes.
Limited access control also plagues many products. When a technician logs into a remote computer, he has full access to everything on the system as if he were sitting at the console. If he sees patient information at any time, a HIPAA violation occurs. You should choose a product that allows you to determine exactly what remote technicians are allowed to see and do.
Potential liability may result if any information goes missing or if another problem arises that may appear to be the fault of the technician. Consider crafting a standard message that a user sees and must acknowledge before allowing the connection, stating the extent of liability on your part for issues that may arise after the remote session.
Presence
Many collaboration solutions use presence functionality to indicate the availability of a user. A system that uses presence signals to other users whether a user is online, busy, in a meeting, and so forth. If enabled across multiple communication tools, such as IM, phone, email, and video conferencing, it can also help determine on which communication channel the user is currently active and therefore which channel provides the best possibility of an immediate response.
While the information contained in a presence system about each individual helps to make the system function, it is information that could be used maliciously. Specific issues include:
![]() Systems that do not authenticate presence sources during the status update process
Systems that do not authenticate presence sources during the status update process
![]() Systems that do not authenticate receivers of presence information (also called subscribers, or watchers)
Systems that do not authenticate receivers of presence information (also called subscribers, or watchers)
![]() Systems that do not provide confidentiality and integrity of presence information
Systems that do not provide confidentiality and integrity of presence information
![]() Systems that use weak methods to authenticate the user (also called a presentity)
Systems that use weak methods to authenticate the user (also called a presentity)
When selecting a presence product or when evaluating a system that includes a presence feature, follow these guidelines:
![]() Select a product that uses a secure protocol. One example is Extensible Messaging and Presence Protocol (XMPP) over TLS, while another is Session Initiation Protocol for Instant Messaging and Presence Leveraging Extensions (SIMPLE).
Select a product that uses a secure protocol. One example is Extensible Messaging and Presence Protocol (XMPP) over TLS, while another is Session Initiation Protocol for Instant Messaging and Presence Leveraging Extensions (SIMPLE).
![]() Select a product that uses your company’s Public Key Infrastructure (PKI) for authentication. Certificate-based authentication, when possible, is the best.
Select a product that uses your company’s Public Key Infrastructure (PKI) for authentication. Certificate-based authentication, when possible, is the best.
![]() Encrypt the communications both internally and across the Internet.
Encrypt the communications both internally and across the Internet.
![]() Ensure that the product performs authentication of both presence sources and subscribers.
Ensure that the product performs authentication of both presence sources and subscribers.
![]() If the system supports presence groups, use grouping to control the viewing of presence information among groups.
If the system supports presence groups, use grouping to control the viewing of presence information among groups.
Email is without a doubt the most widely used method of communication in the enterprise. It uses three standard messaging protocols. Each of them can be run over SSL to create a secure communication channel. When they are run over SSL, the port numbers used are different. These protocols are discussed in the following sections.
IMAP
Internet Message Access Protocol (IMAP) is an application layer protocol used on a client to retrieve email from a server. Its latest version is IMAP4. Unlike POP3, another email client that can only download messages from the server, IMAP4 allows a user to download a copy and leave a copy on the server. IMAP4 uses port 143. A secure version also exists, IMAPS (IMAP over SSL), and it uses port 993.
POP
Post Office Protocol (POP) is an application layer email retrieval protocol. POP3 is the latest version. It allows for downloading messages only and does not allow the additional functionality provided by IMAP4. POP3 uses port 110. A secure version that runs over SSL is also available; it uses port 995.
SMTP
POP and IMAP are client email protocols used for retrieving email, but when email servers are talking to each other, they use Simple Mail Transfer Protocol (SMTP), a standard application layer protocol. This is also the protocol used by clients to send email. SMTP uses port 25, and when it runs over SSL, it uses port 465.
Unfortunately, email offers a number of attack vectors to those with malicious intent. In most cases, the best tool for preventing these attacks is user training and awareness as many of these attacks are based on poor security practices among users.
Email Spoofing
Email spoofing is the process of sending an email that appears to come from one source when it really comes from another. It is made possible by altering the fields of email headers, such as From, Return Path, and Reply-to. Its purpose is to convince the receiver to trust the message and reply to it with some sensitive information that the receiver would not share with an untrusted source.
Email spoofing is often one step in an attack designed to harvest usernames and passwords for banking or financial sites. Such attacks can be mitigated in several ways. One is to use SMTP authentication, which, when enabled, disallows the sending of an email by a user that cannot authenticate with the sending server.
Another possible mitigation technique is to implement Sender Policy Framework (SPF). SPF is an email validation system that works by using DNS to determine whether an email sent by someone has been sent by a host sanctioned by that domain’s administrator. If it can’t be validated, it is not delivered to the recipient’s inbox.
Spear Phishing
Phishing is a social engineering attack in which a recipient is convinced to click a link in an email that appears to go to a trusted site but in fact goes to the hacker’s site. These attacks are used to harvest usernames and passwords.
Spear phishing is the process of foisting a phishing attack on a specific person rather than a random set of people. The attack may be made more convincing by using details about the person learned through social media.
Several actions can be taken to mitigate spear phishing, including:
![]() Deploy a solution that verifies the safety of all links in emails. An example of this is Invincea FreeSpace, which opens all links and attachments in a secure virtual container, preventing any harm to users’ systems.
Deploy a solution that verifies the safety of all links in emails. An example of this is Invincea FreeSpace, which opens all links and attachments in a secure virtual container, preventing any harm to users’ systems.
![]() Train users to regard all emails suspiciously, even if they appear to come from friends.
Train users to regard all emails suspiciously, even if they appear to come from friends.
Whaling
Just as spear phishing is a subset of phishing, whaling is a subset of spear phishing. In whaling, the person targeted is someone of significance or importance. It might be a CEO, COO, or CTO, for example. The attack is based on the assumption that these people have more sensitive information to divulge. The same techniques that can be used to mitigate spear phishing can also apply to whaling.
Spam
You probably don’t like the way your email box fills every day with unsolicited emails, many of them trying to sell you something. In many cases, you cause yourself to receive this email by not paying close attention to all the details when you buy something or visit a site. When email is sent out on a mass basis that is not requested, it is called spam.
Spam is more than annoyance; it can clog email boxes and cause email servers to spend resources delivering it. Sending spam is illegal, so many spammers try to hide the source of their spam by relaying through other corporations’ email servers. Not only does this hide its true source, but it can cause the relaying company to get in trouble.
Today’s email servers have the ability to deny relaying to any email servers that you do not specify. This can prevent your email system from being used as a spamming mechanism. This type of relaying should be disallowed on your email servers. Moreover, spam filtering should be deployed on all email servers.
Captured Messages
Email traffic, like any other traffic type, can be captured in its raw form with a protocol analyzer. If the email is cleartext, it can be read. For this reason, encryption should be used for all emails of a sensitive nature. While this can be done using the digital certificate of the intended recipient, this is typically possible only if the recipient is part of your organization and your company has a PKI. Many email products include native support for digital signing and encryption of messages using digital certificates.
While it is possible to use email encryption programs like Pretty Good Privacy (PGP), it is confusing for many users to use these products correctly without training. Another option is to use an encryption appliance or service that automates the encryption of email. Regardless of the specific approach, encryption of messages is the only mitigation for information disclosure from captured packets.
Disclosure of Information
In some cases, information is disclosed not because an unencrypted message is captured but because the email is shared with others who may not be trustworthy. Even when an information disclosure policy is in place, it may not be followed by everyone. To prevent this type of disclosure, you can sanitize all outgoing content for types of information that should not be disclosed and have it removed. An example of a product that can do this is Axway’s MailGate.
Malware
Email is a frequent carrier of malware; in fact, email is the most common vehicle for infecting computers with malware. You should employ malware scanning software on both the client machines and the email server. Despite this measure, malware still gets through, and it is imperative to educate users to follow safe email handling procedures (such as not opening attachments from unknown sources). Training users is critical.
Telephony
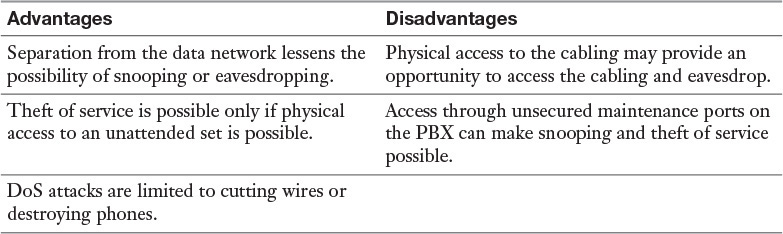
Telephony systems include both traditional analog phone systems and digital, or Voice over IP (VoIP), systems. In traditional telephony, analog phones connect to a private branch exchange (PBX) system. The entire phone network is separate from the IP data network the organization may have. Table 14-2 lists advantages and disadvantages of traditional telephony.
To secure traditional analog system, you should:
![]() Prevent physical access to the cabling plant.
Prevent physical access to the cabling plant.
![]() Secure or disable all maintenance ports on the PBX.
Secure or disable all maintenance ports on the PBX.
While it may seem that analog phone systems offer some security benefits, it should be noted that the Federal Communications Commission (FCC) in the United States is in the process of dismantling the analog phone system that has existed since the days of Bell Labs. While there is no date set for final discontinuation, it seems foolish to deploy a system, however secure, that will soon be obsolete. Moreover, many of the security issues with VoIP seem to be getting solutions (see the next section).
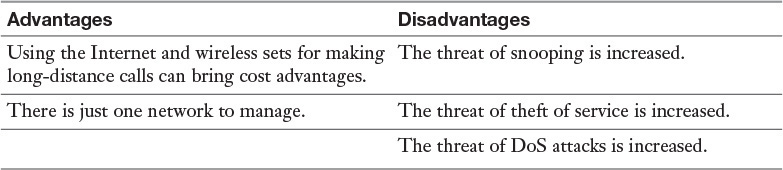
VoIP
Voice over IP (VoIP) phone systems offer some advantages but also introduce security issues. Table 14-3 lists the advantages and disadvantages of VoIP systems. One attack type is a VoIP spam, or SPIT (Spam over Internet Telephony), attack. This type of attack causes unsolicited prerecorded phone messages to be sent. Detecting these attacks is a matter of regularly performing a Session Initiation Protocol (SIP) traffic analysis. SIP is used for call setup and teardown. If you’re using Secure Real-Time Transport Protocol (SRTP), a protocol that provides encryption, integrity, and anti-replay to Real Time Protocol (RTP) traffic, then SRTP traffic analysis should be done as well. RTP is a protocol used in the delivery of voice and video traffic. Some protocol analyzers, like PacketScan from GL Communications, are dedicated to these protocols. Such analysis can help to identify a SPIT attack.
While the threat of snooping, theft of service, and DoS attacks is higher with VoIP than with traditional analog, there are measures that can be taken to mitigate the issues and reduce the risks with VoIP. They are:
![]() Physically separate the phone and data networks.
Physically separate the phone and data networks.
![]() Secure all management interfaces on infrastructure devices (for example, switches, routers, gateways).
Secure all management interfaces on infrastructure devices (for example, switches, routers, gateways).
![]() In high-security environments, use some version of a secure phone (to provide end-to-end encryption).
In high-security environments, use some version of a secure phone (to provide end-to-end encryption).
![]() Deploy network address translation (NAT) to hide the true IP addresses of the phones.
Deploy network address translation (NAT) to hide the true IP addresses of the phones.
![]() Maintain the latest patches for operating system and VoIP applications.
Maintain the latest patches for operating system and VoIP applications.
![]() Disable any unnecessary services or features.
Disable any unnecessary services or features.
![]() To prevent performance issues, especially during DoS attacks on the network, employ 802.11e to provide QoS for the VoIP packets when they traverse a wireless segment, just as you would provide QoS on all wired segments.
To prevent performance issues, especially during DoS attacks on the network, employ 802.11e to provide QoS for the VoIP packets when they traverse a wireless segment, just as you would provide QoS on all wired segments.
![]() Ensure that the SIP servers, which are the servers responsible for creating voice and video sessions, are protected by a firewall.
Ensure that the SIP servers, which are the servers responsible for creating voice and video sessions, are protected by a firewall.
Collaboration Sites
Users are increasingly using web technology to collaborate on cloud-based tools. Organizations are also leveraging social media to connect with and share information with customers and the world at large. While both social media and cloud-based collaboration offer many benefits, they also introduce security issues. The following sections look at these issues and mitigation techniques and offer guidelines on the proper use of both social media and cloud-based collaboration.
Social Media
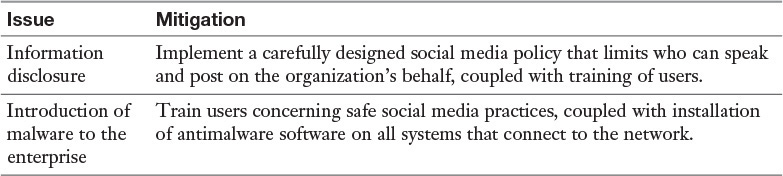
While the subject of social media may conjure thoughts of Facebook and Twitter, the use of both public and enterprise (private) social media presents new security challenges. The security risks of public social media may be more obvious than those of private social media sites, but the fact that most enterprise social media tools offer at least the ability to be tightly integrated with public social media means that many issues of public social media can easily become your problem when there is an enterprise social media site.
Several scenarios illustrating the dangers of social media to the enterprise are discussed in Chapter 10, “Industry Trends.” Most of these security issues can be placed in two categories: disclosure of sensitive enterprise information and introduction of malware to the enterprise. With respect to information disclosure, one of the ways an organization can suffer a disclosure event is by allowing company devices holding sensitive data to access social media sites. Table 14-4 reviews the issues that exist in social media and measures that can be taken to reduce their risk and impact.
Cloud-Based Collaboration
Cloud-based collaboration is primarily used by enterprises and small teams as a means of storing documents, communicating, and sharing updates on projects. The benefits to this are:
![]() Allows you to pay by usage
Allows you to pay by usage
![]() Speeds deployment of new tools, applications, and services to workers
Speeds deployment of new tools, applications, and services to workers
![]() Can be absorbed as an operational expense rather than a capital expense
Can be absorbed as an operational expense rather than a capital expense
![]() Boosts speed of innovation
Boosts speed of innovation
![]() Enhances productivity
Enhances productivity
![]() Increases operational efficiencies
Increases operational efficiencies
Some of the issues or challenges posed by moving to a cloud-based collaboration solution rather than using a premises-based solution are:
![]() Potential need to redesign network to accommodate cloud services
Potential need to redesign network to accommodate cloud services
![]() Data security concerns
Data security concerns
![]() Difficulty enforcing security policies
Difficulty enforcing security policies
![]() Challenges of providing an audit trail
Challenges of providing an audit trail
![]() Meeting regulatory requirements
Meeting regulatory requirements
Because of these concerns, using cloud-based collaboration is not the best solution for many highly regulated industries, such as banking and healthcare. The following types of information should not be stored in a public cloud-based solution:
![]() Credit card information
Credit card information
![]() Trade secrets
Trade secrets
![]() Financial data
Financial data
![]() State and federal government secrets
State and federal government secrets
![]() Proprietary or sensitive data
Proprietary or sensitive data
![]() Personally identifiable information
Personally identifiable information
When a cloud-based collaboration solution is appropriate, the following measures should be taken to secure the solution:
![]() Ensure that you completely understand the respective security responsibilities of the vendor and your organization.
Ensure that you completely understand the respective security responsibilities of the vendor and your organization.
![]() If handling sensitive information, ensure that either the vendor is providing encryption or that you send data through an encryption proxy before it is sent to the provider.
If handling sensitive information, ensure that either the vendor is providing encryption or that you send data through an encryption proxy before it is sent to the provider.
![]() Require strong authentication on the collaboration site.
Require strong authentication on the collaboration site.
![]() If the vendor also provides data loss prevention (DLP) services, strongly consider using these services.
If the vendor also provides data loss prevention (DLP) services, strongly consider using these services.
![]() When databases are also in use, consider implementing database activity monitoring (DAM).
When databases are also in use, consider implementing database activity monitoring (DAM).
Remote Access
Remote access applications allow users to access an organization’s resources from a remote connection. These remote connections can be direct dial-in connections but are increasingly using the Internet as the network over which the data is transmitted. If an organization allows remote access to internal resources, the organization must ensure that the data is protected using encryption when the data is being transmitted between the remote access client and remote access server. Remote access servers can require encrypted connections with remote access clients, meaning that any connection attempt that does not use encryption will be denied. Remote access to the corporate network is a fairly mature technology, and proper security measures have been clearly defined.
Dial-up
A dial-up connection uses the public switched telephone network (PSTN). If such a connection is initiated over an analog phone line, it requires a modem that converts the digital data to analog on the sending end, with a modem on the receiving end converting it back to digital. These lines operate up to 56 Kbps.
Dial-up connections can use either Serial Line Internet Protocol (SLIP) or Point-to-Point Protocol (PPP) at layer 2. SLIP is an older protocol made obsolete by PPP. PPP provides authentication and multilink capability. The caller is authenticated by the remote access server. This authentication process can be centralized by using either a TACACS+ or RADIUS server.
Some basic measures that should be in place when using dial-up are:
![]() Have the remote access server call back the initiating caller at a preset number. Do not allow call forwarding as this can be used to thwart this security measure.
Have the remote access server call back the initiating caller at a preset number. Do not allow call forwarding as this can be used to thwart this security measure.
![]() Set modems to answer after a set number of rings to thwart war dialers. These are automated programs that dial numbers until a modem signal is detected.
Set modems to answer after a set number of rings to thwart war dialers. These are automated programs that dial numbers until a modem signal is detected.
![]() Consolidate the modems in one place for physical security and disable modems that are not in use.
Consolidate the modems in one place for physical security and disable modems that are not in use.
![]() Use the strongest possible authentication mechanisms.
Use the strongest possible authentication mechanisms.
VPN
As you learned in Chapter 3, “Network and Security Components, Concepts, and Architectures,” virtual private network (VPN) connections use an untrusted carrier network but provide protection of the information through strong authentication protocols and encryption mechanisms. While we typically use the most untrusted network, the Internet, as the classic example, and most VPNs do travel through the Internet, they can be used with interior networks as well whenever traffic needs to be protected from prying eyes. For more information on VPN components and scenarios in which VPNs are appropriate, see Chapter 3.
There are several remote access or line protocols (tunneling protocols) used to create VPN connections, including:
![]() Point-to-Point Tunneling Protocol (PPTP)
Point-to-Point Tunneling Protocol (PPTP)
![]() Layer 2 Tunneling Protocol (L2TP)
Layer 2 Tunneling Protocol (L2TP)
PPTP is a Microsoft protocol based on PPP. It uses built-in Microsoft Point-to-Point encryption and can use a number of authentication methods, including CHAP, MS-CHAP, and EAP-TLS. One shortcoming of PPTP is that it only works on IP-based networks. If a WAN connection that is not IP based is in use, L2TP must be used.
L2TP is a newer protocol that operates at layer 2 of the OSI model. Like PPTP, L2TP can use various authentication mechanisms; however, L2TP does not provide any encryption. It is typically used with IPsec, which is a very strong encryption mechanism.
When using PPTP, the encryption is included, and the only remaining choice to be made is the authentication protocol. These authentication protocols are discussed in Chapter 3.
When using L2TP, both encryption and authentication protocols, if desired, must be added. IPsec can provide encryption, data integrity, and system-based authentication, which makes it a flexible and capable option. By implementing certain parts of the IPsec suite, you can either use these features or not.
IPsec is actually a suite of protocols in the same way that TCP/IP is. It includes the following components:
![]() Authentication Header (AH): AH provides data integrity, data origin authentication, and protection from replay attacks.
Authentication Header (AH): AH provides data integrity, data origin authentication, and protection from replay attacks.
![]() Encapsulating Security Payload (ESP): ESP provides all that AH does as well as data confidentiality.
Encapsulating Security Payload (ESP): ESP provides all that AH does as well as data confidentiality.
![]() Internet Security Association and Key Management Protocol (ISAKMP): ISAKMP handles the creation of a security association for the session and the exchange of keys.
Internet Security Association and Key Management Protocol (ISAKMP): ISAKMP handles the creation of a security association for the session and the exchange of keys.
![]() Internet Key Exchange (IKE): Also sometimes referred to as IPsec Key Exchange, IKE provides the authentication material used to create the keys exchanged by ISAKMP during peer authentication. This was proposed to be performed by a protocol called Oakley that relied on the Diffie-Hellman algorithm, but Oakley has been superseded by IKE.
Internet Key Exchange (IKE): Also sometimes referred to as IPsec Key Exchange, IKE provides the authentication material used to create the keys exchanged by ISAKMP during peer authentication. This was proposed to be performed by a protocol called Oakley that relied on the Diffie-Hellman algorithm, but Oakley has been superseded by IKE.
IPsec is a framework, which means it does not specify many of the components used with it. These components must be identified in the configuration, and they must match in order for the two ends to successfully create the required security association that must be in place before any data is transferred. The selections that must be made are:
![]() The encryption algorithm (encrypts the data)
The encryption algorithm (encrypts the data)
![]() The hashing algorithm (ensures the data has not been altered and verifies its origin)
The hashing algorithm (ensures the data has not been altered and verifies its origin)
![]() The mode (tunnel or transport)
The mode (tunnel or transport)
![]() The protocol (AH, ESP, or both)
The protocol (AH, ESP, or both)
All these settings must match on both ends of the connection. It is not possible for the systems to select these on the fly. They must be preconfigured correctly in order to match.
When configured in tunnel mode, the tunnel exists only between the two gateways, but all traffic that passes through the tunnel is protected. This is normally done to protect all traffic between two offices. The security association (SA) is between the gateways between the offices. This is the type of connection that would be called a site-to-site VPN.
The SA between the two endpoints is made up of the security parameter index (SPI) and the AH/ESP combination. The SPI, a value contained in each IPsec header, help the devices maintain the relationship between each SA (and there could be several happening at once) and the security parameters (also called the transform set) used for each SA.
Each session has a unique session value, which helps prevent:
![]() Reverse engineering
Reverse engineering
![]() Content modification
Content modification
![]() Factoring attacks (in which the attacker tries all the combinations of numbers that can be used with the algorithm to decrypt ciphertext)
Factoring attacks (in which the attacker tries all the combinations of numbers that can be used with the algorithm to decrypt ciphertext)
With respect to authenticating the connection, the keys can be preshared or derived from a Public Key Infrastructure (PKI). A PKI creates public/private key pairs that are associated with individual users and computers that use a certificate. These key pairs are used in the place of preshared keys in that case. Certificates that are not derived from a PKI can also be used.
In transport mode, the SA is either between two end stations or between an end station and a gateway or remote access server. In this mode, the tunnel extends from computer to computer or from computer to gateway. This is the type of connection that would be used for a remote access VPN. This is but one application of IPsec. It is also used in other applications, such as a General Packet Radio Service (GPRS) VPN solution for devices using a 3G cellphone network.
When the communication is from gateway to gateway or host to gateway, either transport or tunnel mode may be used. If the communication is computer to computer, transport mode is required. When using transport mode from gateway to host, the gateway must operate as a host.
The most effective attack against an IPsec VPN is a man-in-the middle attack. In this attack, the attacker proceeds through the security negotiation phase until the key negotiation, when the victim reveals its identity. In a well-implemented system, the attacker fails when the attacker cannot likewise prove his identity.
SSL
Secure Sockets Layer (SSL) is another option for creating VPNs. SSL is discussed in Chapter 3.
Remote Administration
In many cases, administrators or network technicians need to manage and configure network devices remotely. Remote administration is covered in Chapter 3.
Mobile Device Management
Chapter 10 discusses the threats to organizations related to the use of mobile devices and briefly mentions the emergence of bring your own device (BYOD) initiatives. The threats presented by the introduction of personal mobile devices (smartphones and tablets) to an organization’s network include:
![]() Insecure web browsing
Insecure web browsing
![]() Insecure Wi-Fi connectivity
Insecure Wi-Fi connectivity
![]() Lost or stolen devices holding company data
Lost or stolen devices holding company data
![]() Corrupt application downloads and installations
Corrupt application downloads and installations
![]() Missing security patches
Missing security patches
![]() Constant upgrading of personal devices
Constant upgrading of personal devices
![]() Use of location services
Use of location services
While the most common types of corporate information stored on personal devices are corporate emails and company contact information, it is alarming to note that almost half of these devices also contain customer data, network login credentials, and corporate data accessed through business applications.
To address these issues and to meet the rising demand to bring and use personal devices, many organizations are creating BYOD policies. The following section looks at what measures should be a part of a BYOD initiative.
BYOD
As a security professional, when supporting a BYOD initiative, you should take into consideration that you probably have more to fear from the carelessness of the users than you do from hackers. Not only are they less than diligent in maintaining security updates and patches on devices, they buy new devices as often as they change clothes. These factors make it difficult to maintain control over the security of the networks in which these devices are allowed to operate.
Centralized mobile device management tools are becoming the fastest-growing solution for both organization issues and personal devices. Some solutions leverage the messaging server’s management capabilities, and others are third-party tools that can manage multiple brands of devices. Systems Manager by Cisco is one example that integrates with their Cisco Meraki cloud services. Another example for iOS devices is the Apple Configurator. One of the challenges with implementing such a system is that not all personal devices may support native encryption and/or the management process.
Typically centralized mobile device management tools handle company-issued and personal mobile devices differently. For organization-issued devices, a client application typically manages the configuration and security of the entire device. If the device is a personal device allowed through a BYOD initiative, the application typically manages the configuration and security of itself and its data only. The application and its data are sandboxed from the other applications and data. The result is that the organization’s data is protected if the device is stolen, while the privacy of the user’s data is also preserved.
Regardless of whether a centralized mobile device management tool is in use, a BYOD policy should add the following to the security policy of the organization:
![]() Identify the allowed uses of personal devices on the corporate network.
Identify the allowed uses of personal devices on the corporate network.
![]() Create a list of allowed applications on the devices and design a method of preventing the installation of applications not on the list (for example, software restriction policies).
Create a list of allowed applications on the devices and design a method of preventing the installation of applications not on the list (for example, software restriction policies).
![]() Ensure that high levels of management are on board and supportive.
Ensure that high levels of management are on board and supportive.
![]() Train users in the new policies.
Train users in the new policies.
In the process of deploying and supporting a mobile solution, follow these guidelines:
![]() Ensure that the selected solution supports applying security controls remotely.
Ensure that the selected solution supports applying security controls remotely.
![]() Ensure that the selected vendor has a good track record of publicizing and correcting security flaws.
Ensure that the selected vendor has a good track record of publicizing and correcting security flaws.
![]() Make the deployment of a mobile device management (MDM) tool a top priority.
Make the deployment of a mobile device management (MDM) tool a top priority.
![]() In the absence of an MDM system, design a process to ensure that all devices are kept up-to-date on security patches.
In the absence of an MDM system, design a process to ensure that all devices are kept up-to-date on security patches.
![]() Update the policy as technology and behaviors change.
Update the policy as technology and behaviors change.
![]() Require all employees to agree to allow remote wipe of any stolen or lost devices.
Require all employees to agree to allow remote wipe of any stolen or lost devices.
![]() Rooted (Android) or jailbroken (iOS) devices should be strictly forbidden from accessing the network.
Rooted (Android) or jailbroken (iOS) devices should be strictly forbidden from accessing the network.
![]() If possible, choose a product that supports:
If possible, choose a product that supports:
![]() Encrypting the solid state hard drive (SSD) and nonvolatile RAM
Encrypting the solid state hard drive (SSD) and nonvolatile RAM
![]() Requiring a PIN to access the device
Requiring a PIN to access the device
![]() Locking the device when a specific number of incorrect PINs are attempted
Locking the device when a specific number of incorrect PINs are attempted
Over-the-Air Technologies Concerns
Perhaps the area of the network that keeps most administrators awake at night is the wireless portion of the network. In the early days of 802.11 WLAN deployments, many chose to simply not implement wireless for fear of the security holes it creates. However, it became apparent that not only did users demand this, but in some cases they were bringing their home access points to work and hooking them up, and suddenly there was a wireless network!
Today, WLAN security has evolved to the point that security is no longer a valid reason to avoid wireless. The following sections look at the protocols used in wireless, the methods used to convert data into radio waves, the various topologies in which WLANs can be deployed, and security measures that should be taken.
FHSS, DSSS, OFDM, FDMA, CDMA, OFDMA, and GSM
When data leaves an Ethernet NIC and is sent out on the network, the ones and zeros that constitute the data are represented with different electric voltages. In wireless, this information must be represented in radio waves. There are a number of different methods of performing this operation, which is called modulation. There are also some additional terms that should be understood to talk intelligently about wireless. The following sections define a number of these terms to provide background for the discussion in the balance of this section. The first section covers techniques used in WLAN, and the second covers techniques used in cellular networking.
802.11 Techniques
Frequency Hopping Spread Spectrum (FHSS) is one of two technologies (along with DSSS) that were a part of the original 802.11 standard. It is unique in that it changes frequencies or channels every few seconds in a set pattern that both the transmitter and receiver know. This is not a security measure because the patterns are well known, although it does make it difficult to capture the traffic. It helps avoid inference by only occasionally using a frequency where the inference is present. Later amendments to the 802.11 standard do not include this technology. It can attain up to 2 Mbps.
Direct Sequence Spread Spectrum (DSSS) is one of two technologies (along with FHSS) that were a part of the original 802.11 standard. This is the modulation technique used in 802.11b. The modulation technique used in wireless has a huge impact on throughput. In the case of DSSS, it spreads the transmission across the spectrum at the same time as opposed to hopping from one to another, as in FHSS. This allows it to attain speeds up to 11 Mbps.
Orthogonal Frequency Division Multiplexing (OFDM) is an advanced technique of modulation in which a large number of closely spaced orthogonal subcarrier signals are used to carry the data on several parallel data streams. It is used in 802.11a and 802.11g. It makes possible speed up to 54 Mbps.
Cellular or Mobile Wireless Techniques
Frequency Division Multiple Access (FDMA) is one of the modulation techniques used in cellular wireless networks. It divides the frequency range into bands and assigns a band to each subscriber. It was used in 1G cellular networks.
Time Division Multiple Access (TDMA) increases speed compared to FDMA by dividing the channels into time slots and assigning slots to calls. This division also helps to prevent eavesdropping in calls.
Code Division Multiple Access (CDMA) assigns a unique code to each call or transmission and spreads the data across the spectrum, allowing a call to make use of all frequencies.
Orthogonal Frequency Division Multiple Access (OFDMA) takes FDMA a step further by subdividing the frequencies into subchannels. This is the technique required by 4G devices.
Global System Mobile Communications (GSM) is a standard for cellphones that contains Subscriber Identity Module (SIM) chips. A SIM chip contains all the information about the subscriber and must be present in the phone for it to function. One of the dangers with these phones is cellphone cloning, a process in which copies of the SIM chip are made, allowing another user to make calls as the original user. Secret key cryptography is used (using a common secret key) when authentication is performed between the phone and the network.
General Packet Radio Service (GPRS) is standard for 2G and 3G cellular communication that is packet oriented. It is best effort, and throughout and latency depends on the number of users sharing the service concurrently.
Enhanced GPRS is an enhancement of GPRS that increases data rates.
Universal Mobile Telecommunications System (UMTS) is a 3G mobile cellular system for networks based on the GSM standard.
WLAN Structure
Before we can discuss 802.11 wireless, which has come to be known as WLAN, we need to discuss the components and the structure of a WLAN. The following sections cover basic terms and concepts.
Access Point
An access point (AP) is a wireless transmitter and receiver that hooks into the wired portion of the network and provides an access point to this network for wireless devices. In some cases, APs are simply wireless switches, and in other cases, they are also routers. Early APs were devices with all the functionality built into each device, but increasingly these “fat,” or intelligent, APs are being replaced with “thin” APs that are really only antennas that hook back into a central system called a controller.
SSID
The service set identifier (SSID) is a name or value assigned to identify the WLAN from other WLANs. An AP and its associated stations comprise a basic service set (BSS). The SSID can either be broadcast by the AP, as is done with a free hot spot, or it can be hidden. When it is hidden, a wireless station has to be configured with a profile that includes the SSID in order to connect. Although some view hiding the SSID as a security measure, it is not an effective measure because hiding the SSID only removes one type of frame, the beacon frame, while the SSID still exists in other frame types and can be easily learned by sniffing the wireless network.
Infrastructure Mode Versus Ad Hoc Mode
In most cases, a WLAN includes at least one AP. When an AP is present, the WLAN is operating in infrastructure mode. In this mode, all transmissions between stations go through the AP, and no direct communication between stations occurs. In ad hoc mode, there is no AP, and the stations communicate directly with one another.
WLAN Standards
The original 802.11 wireless standard has been amended a number of times to add features and functionality. The following sections discuss these amendments, which are sometimes referred to as standards, although they really are amendments to the original standard. The original 802.11 standard specifies the use of either FHSS or DSSS and supports operations in the 2.4 GHz frequency range at speeds of 1 and 2 Mbps. It uses channels 1 to 13.
802.11a
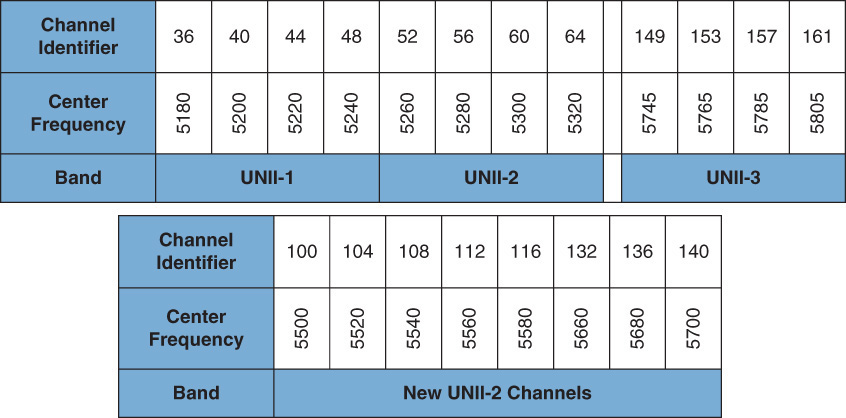
The first amendment to the standard was 802.11a. This amendment called for the use of OFDM. Because that required hardware upgrades to existing equipment, this amendment saw limited adoption for some time. It operates in a different frequency than 802.11 (5 GHz), and by using OFDM, it supports speeds up to 54 Mbps. The channels used in the United States are shown in Figure 14-1. There are four Unlicensed National Information Infrastructure (UNII) bands to which the channels map. The use of these channels, as the name implies, requires no license.
802.11b
The 802.11b amendment dropped support for FHSS and enabled an increase of speed to 11 Mbps, while operating in the 2.4 GHz frequency. It was widely adopted because it operates in the same frequency as 802.11 and is backward compatible with it and can coexist in the same WLAN. It uses channels 1 to 13.
802.11g
The 802.11g amendment added support for OFDM, which made it capable of 54 Mbps. It also operates in the 2.4 GHz frequency, so it is backward compatible with both 802.11a and 802.11b. While 802.11g is just as fast as 802.11a, one reason many switched to 802.11a is that the 5 GHz band is much less crowded than the 2.4 GHz band. 802.11g also uses channels 1 to 13.
802.11n
The 802.11n standard uses several newer concepts to achieve up to 650 Mbps. It does this by using channels that are 40 MHz wide and using multiple antennas, which allow for up to four spatial streams at a time (a feature called Multiple Input Multiple Output [MIMO]). It can be used in both the 2.4 GHz and 5.0 GHz bands but performs best in a pure 5.0 GHz network.
802.11ac
The 802.11ac standard builds on concepts introduced with 802.11n. While it operates only in the 5.0 GHz frequency, it increases the channel width from 40 MHz to 80 MHz. It also increases the possible number of MIMO spatial streams from four to eight. It also introduces Multi-User MIMO, in which multiple stations, each with one or more antennas, can transmit independent data streams simultaneously. These streams are not separated by frequency but are resolved spatially, as in 802.11n. The result is that in cases where the AP has eight antennas and the wireless station has four antennas, the data rate is about 6.77 Gbps.
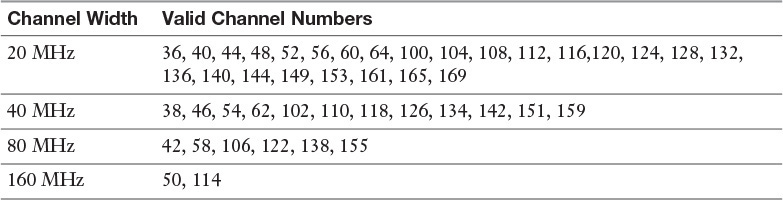
802.11ac changes how we reference larger channel widths. Instead of continuing to reference the 20 MHz extension channel(s), we now reference the center channel frequency for the entire 20, 40, 80 or 160 MHz-wide channel. The channel numbers are dependent on the width of the channels in use. The valid channel numbers for various channel widths are indicted in Table 14-5.
Bluetooth
Bluetooth is a wireless technology that is used to create personal area networks (PANs), which are short-range connections between devices and peripherals, such as headphones. It operates in the 2.4 GHz frequency at speeds of 1 to 3 Mbps at a distance of up to 10 meters.
Several attacks can take advantage of Bluetooth technology. With Bluejacking, an unsolicited message is sent to a Bluetooth-enabled device, often for the purpose of adding a business card to the victim’s contact list. This type of attack can be prevented by placing the device in non-discoverable mode.
Bluesnarfing is the unauthorized access to a device using the Bluetooth connection. In this case, the attacker is trying to access information on the device rather than send messages to the device.
Infrared
Infrared is a short-distance wireless process that uses light (in this case, infrared light) rather than radio waves. It is used for short connections between devices that have infrared ports. It operates up to 5 meters at speeds up to 4 Mbps and requires a direct line of sight between the devices. There is one infrared mode or protocol that can introduce security issues. The IrTran-P (image transfer) protocol is used in digital cameras and other digital image capture devices. All incoming files sent over IrTran-P are automatically accepted. Because incoming files might contain harmful programs, users should ensure that the files originate from a trustworthy source.
WLAN Security
To safely implement 802.11 wireless technologies, you must understand all the methods used to secure a WLAN. The following sections discuss the most important measures, including some that, although they are often referred to as security measures, provide no real security.
WEP
Wired Equivalent Privacy (WEP) was the first security measure used with 802.11. It was specified as the algorithm in the original specification. It can be used to both authenticate a device and encrypt the information between an AP and a device. The problem with WEP is that it implements the RC4 encryption algorithm in a way that allows a hacker to crack the encryption. It also was found that the mechanism designed to guarantee the integrity of data (that is, that the data has not changed) was inadequate and that it was possible for the data to be changed and for this fact to go undetected.
WEP is implemented with a secret key or password that is configured on the AP, and any station needs that password in order to connect. Above and beyond the problem with the implementation of the RC4 algorithm, it is never good security for all devices to share the same password in this way.
WPA
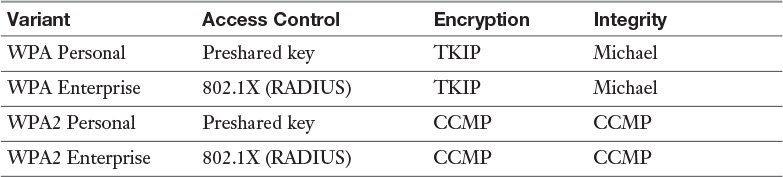
To address the widespread concern with the inadequacy of WEP, the Wi-Fi Alliance, a group of manufacturers that promotes interoperability, created an alternative mechanism, called Wi-Fi Protected Access (WPA), that is designed to improve on WEP. There are four types of WPA, and we’ll talk about that shortly, but first let’s talk about how the original version improves over WEP.
First, WPA uses the Temporal Key Integrity Protocol (TKIP) for encryption, which generates a new key for each packet. Second, the integrity check used with WEP is able to detect any changes to the data. WPA uses a message integrity check algorithm called Michael to verify the integrity of the packets. There are two versions of WPA (covered in the section “Personal Versus Enterprise WPA” below).
Some legacy devices may support only WPA. You should always check with a device’s manufacturer to find out if a security patch has been released that allows for WPA2 support.
WPA2
WPA2 is an improvement over WPA. WPA2 uses Counter Cipher Mode with Block Chaining Message Authentication Code Protocol (CCMP), which is based on Advanced Encryption Standard (AES), rather than TKIP. AES is a much stronger method and is required for Federal Information Processing Standard (FIPS)-compliant transmissions. There also two versions of WPA2 (covered in the next section). WPA2 may not be supported on all devices. In scenarios where some devices support only WEP, you should put those devices on a separate SSID and only allow required communication paths between the two wireless networks.
Personal Versus Enterprise WPA
Both WPA and WPA2 come in Enterprise and Personal versions. The Enterprise versions require the use of an authentication server, typically a RADIUS server. The Personal versions do not require RADIUS and use passwords configured on the AP and the stations. Table 14-6 provides a quick overview of WPA and WPA2.
SSID Broadcast
Issues surrounding the SSID broadcast are covered in the section “WLAN Structure,” earlier in this chapter.
MAC Filter
Another commonly discussed security measure is to create a list of allowed MAC addresses on an AP. When this is done, only the devices with MAC addresses on the list can make a connection to the AP. While on the surface this might seem like a good security measure, a hacker can easily use a sniffer to learn the MAC addresses of devices that have successfully authenticated. Then, by changing the MAC address on his device to one that is on the list, he can gain entry.
MAC filters can also be configured to deny access to certain devices. The limiting factor in this method is that only the devices with the denied MAC addresses are specifically denied access. All other connections are allowed.
Satellites
Satellites have been used to provide TV service for some time, but now they can also be used to deliver Internet access to homes and businesses. When this is done, the connection is two-way rather than one-way, as is done with TV service. This typically happens using microwave technology. In most cases, the downloads come from the satellite signals, while the uploads occur through a ground line. Microwave technology can also be used for terrestrial transmission, which means ground station to ground station rather than satellite to ground. Satellite connections are very slow but are useful in remote locations where no other solution is available. Because satellite communications can be captured by anyone, it important to encrypt IP traffic that is of a sensitive nature; this is usually done with IPsec.
Wireless Attacks
Wireless attacks are some of the hardest attacks to prevent because of the nature of the medium. If you want to make radio transmissions available to users, then you must make them available to anyone else in the area as well. Moreover, there is no way to determine when someone is capturing your radio waves! You may be able to prevent someone from connecting to or becoming a wireless client on the network, but you can’t stop them from using a wireless sniffer to capture the packets. The following sections cover some of the most common attacks, as well as some mitigation techniques.
Wardriving
Wardriving is the process of riding around with a wireless device connected to a high-power antenna, searching for WLANs. It could be for the purpose of obtaining free Internet access, or it could be to identify any open networks that are vulnerable to attack. While hiding the SSID may deter some, anyone who knows how to use a wireless sniffer could figure out the SSID in two minutes, so there really is no way to stop wardriving.
Warchalking
Warchalking is a practice that used to typically accompany wardriving. Once the wardriver located a WLAN, she would indicate in chalk on the sidewalk or on the building the SSID and the types of security used on the network. This activity has gone mostly online now, as there are many sites dedicated to compiling lists of found WLANs and their locations. As there is no way to prevent wardriving, there is no way to stop warchalking either.
Rogue Access Points
Rogue access points are APs that you do not control and manage. There are two types: those that are connected to your wired infrastructure and those that are not. The ones that are connected to your wired network present a danger to your wired and wireless network. They may be placed there by your own users without your knowledge, or they may be purposefully put there by a hacker to gain access to the wired network. In either case, they allow access to your wired network. Wireless intrusion prevention system (WIPS) devices are usually used to locate rogue access points and alert administrators of their presence.
Exam Preparation Tasks
You have a couple of choices for exam preparation: the exercises here and the exam simulation questions on the CD-ROM.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 14-7 lists these key topics and the page number on which each is found.
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
Advanced Encryption Standard (AES)
Extensible Messaging and Presence Protocol (XMPP)
Session Initiation Protocol for Instant Messaging and Presence Leveraging Extensions (SIMPLE)
SPIT (Spam over Internet Telephony)
Secure Real-time Transport Protocol (or SRTP)
RTP (Real-time Transport Protocol)
Session Initiation Protocol (SIP) server
Serial Line Internet Protocol (SLIP)
Point-to-Point Tunneling Protocol (PPTP)
Layer 2 Tunneling Protocol (L2TP)
Encapsulating Security Payload (ESP)
Internet Security Association and Key Management Protocol (ISAKMP)
security parameter index (SPI)
mobile device management (MDM)
Frequency Hopping Spread Spectrum (FHSS)
Direct Sequence Spread Spectrum (DSSS)
Orthogonal Frequency Division Multiplexing (OFDM)
Frequency Division Multiple Access (FDMA)
Time Division Multiple Access (TDMA)
Code Division Multiple Access (CDMA)
Orthogonal Frequency Division Multiple Access (OFDMA)
Global System for Mobile Communications (GSM)
Wired Equivalent Privacy (WEP)
Review Questions
1. Your company is planning to procure a web conferencing system to cut costs on travel. You have been asked to investigate the security issues that should be considered during this process. Which of the following is not an issue to consider?
a. Preventing uninvited guests at meetings
b. The dangers of data being stored on a vendor’s shared server
c. The potential for the solution to affect network performance
d. The possibility of information being captured during transmission
2. Your users use a VPN connection to connect to the office for web conferences. Several users have complained about poor performance during the meetings. Which of the following actions could help improve the performance of the video conference for all participants without reducing security?
a. Change the encryption used from AES to DES.
b. Disable split tunneling.
c. Enable read/write desktop mode.
d. Change the hashing algorithm to SHA-1.
3. Your organization just deployed an enterprise instant messaging solution. The CIO is concerned about the transfer of worms, Trojans, and other malware through the IM connections. Which of the following would not be a measure that could help mitigate the introduction of malware through the IM system?
a. Disable the ability to transfer files through the system.
b. Purchase a product that performs encryption.
c. Install an antimalware product that can plug into the IM client.
d. Train users in the dangers of using IM.
4. Your organization is planning the deployment of a new remote assistance tool. The security team is trying to determine the level of encryption the selected product must support. Which of the following factors should be the most important consideration?
a. the type required by industry regulations
b. the strongest available
c. the opinion of the third-party vendor
d. the level supported by the desktops
5. To improve the security of products providing presence information, which protocol could you use?
a. SPF
b. XMPP
c. SPIT
d. SKRT
6. What type of traffic is the SIMPLE protocol designed to secure?
a. IM
b. presence
c. video conference
d. email
7. The email administrator has suggested that a technique called SPF should be deployed. What issue does this address?
a. spear phishing
b. whaling
c. email spoofing
d. captured messages
8. The organization is planning the deployment of a VoIP phone system. During the risk analysis, which of the following is not a valid consideration?
a. increased threat of snooping in VoIP
b. increased threat of theft of service
c. access through unsecured maintenance ports on the PBX
d. Increased threat of DoS attacks
9. Your company is determining what data to make accessible in the new cloud-based collaboration solution. Which of the following types of information should not be stored in a public cloud-based collaboration solution?
a. price lists
b. financial data
c. catalogues
d. company forms
10. Which component of IPsec provides the authentication material used to create the keys exchanged during peer authentication?
a. AH
b. ESP
c. ISAKMP
d. IKE