Chapter 7. Risk Mitigation Planning, Strategies, and Controls
This chapter covers the following topics:
![]() Classify Information Types into Levels of CIA Based on Organization/Industry: This section includes a discussion of CIA, FIPS 199 levels, information classification (including commercial business and military/government classifications), and the information life cycle.
Classify Information Types into Levels of CIA Based on Organization/Industry: This section includes a discussion of CIA, FIPS 199 levels, information classification (including commercial business and military/government classifications), and the information life cycle.
![]() Incorporate Stakeholder Input into CIA Decisions: This section covers why stakeholder input should be obtained and factored into the decisions made.
Incorporate Stakeholder Input into CIA Decisions: This section covers why stakeholder input should be obtained and factored into the decisions made.
![]() Implement Technical Controls Based on CIA Requirements and Policies of the Organization: This discussion includes access control types and a security requirement traceability matrix.
Implement Technical Controls Based on CIA Requirements and Policies of the Organization: This discussion includes access control types and a security requirement traceability matrix.
![]() Determine the Aggregate CIA Score: This section discusses using the FIPS 199 nomenclature to calculate the aggregate score.
Determine the Aggregate CIA Score: This section discusses using the FIPS 199 nomenclature to calculate the aggregate score.
![]() Extreme Scenario/Worst-Case Scenario Planning: This section discusses guidelines on extreme scenario or worst-case scenario planning.
Extreme Scenario/Worst-Case Scenario Planning: This section discusses guidelines on extreme scenario or worst-case scenario planning.
![]() Determine Minimum Required Security Controls Based on Aggregate Score: This section discusses using the aggregate score to help select security controls.
Determine Minimum Required Security Controls Based on Aggregate Score: This section discusses using the aggregate score to help select security controls.
![]() Conduct System-Specific Risk Analysis: This section discusses analyzing risks based on the system and its attributes.
Conduct System-Specific Risk Analysis: This section discusses analyzing risks based on the system and its attributes.
![]() Make Risk Determination: This section covers qualitative risk analysis, quantitative risk analysis, magnitude of impact, likelihood of threat, return on investment, and total cost of ownership.
Make Risk Determination: This section covers qualitative risk analysis, quantitative risk analysis, magnitude of impact, likelihood of threat, return on investment, and total cost of ownership.
![]() Recommend Which Strategy Should Be Applied Based on Risk Appetite: This discussion covers the following risk strategies: avoid, transfer, mitigate, and accept.
Recommend Which Strategy Should Be Applied Based on Risk Appetite: This discussion covers the following risk strategies: avoid, transfer, mitigate, and accept.
![]() Risk Management Processes: This section covers information and asset value and costs, identification of vulnerabilities and threats, exemptions, deterrence, inherent risk, and residual risk.
Risk Management Processes: This section covers information and asset value and costs, identification of vulnerabilities and threats, exemptions, deterrence, inherent risk, and residual risk.
![]() Enterprise Security Architecture Frameworks: This discussion includes SABSA, CobiT, and NIST 800-53.
Enterprise Security Architecture Frameworks: This discussion includes SABSA, CobiT, and NIST 800-53.
![]() Continuous Improvement/Monitoring: This section covers why continuous improvement and monitoring are important and some guidelines that should be followed.
Continuous Improvement/Monitoring: This section covers why continuous improvement and monitoring are important and some guidelines that should be followed.
![]() Business Continuity Planning: This discussion covers business continuity planning, including the business continuity scope and plan.
Business Continuity Planning: This discussion covers business continuity planning, including the business continuity scope and plan.
![]() IT Governance: This section covers IT governance components, including policies, standards, baselines, guidelines, and procedures.
IT Governance: This section covers IT governance components, including policies, standards, baselines, guidelines, and procedures.
This chapter covers CAS-002 objective 2.2.
Enterprises must consider risk as part of any security strategy. Risk mitigation planning, strategies, and controls are vital to ensuring that organizational risk is minimized. The steps that should be used to establish an enterprise’s security architecture are as follows:
1. Classify information types used within the system into levels of confidentiality, integrity, and availability (CIA).
2. Determine minimum required security controls.
3. Conduct a risk analysis.
4. Decide which security controls to implement.
This chapter covers all the information needed to properly manage enterprise risk, including the following:
![]() Information classification
Information classification
![]() Stakeholder input
Stakeholder input
![]() CIA aggregate score
CIA aggregate score
![]() Worst case scenario
Worst case scenario
![]() Minimum security controls
Minimum security controls
![]() Risk analysis
Risk analysis
![]() Risk determination
Risk determination
![]() Risk strategies
Risk strategies
![]() Risk management processes
Risk management processes
![]() Security architecture frameworks
Security architecture frameworks
![]() Continuous improvement and monitoring
Continuous improvement and monitoring
![]() Business continuity planning
Business continuity planning
![]() IT governance
IT governance
Foundation Topics
Classify Information Types into Levels of CIA Based on Organization/Industry
The three fundamentals of security are confidentiality, integrity, and availability (CIA). Most security issues result in a violation of at least one facet of the CIA triad. Understanding these three security principles will help security professionals ensure that the security controls and mechanisms implemented protect at least one of these principles.
To ensure confidentiality, you must prevent the disclosure of data or information to unauthorized entities. As part of confidentiality, the sensitivity level of data must be determined before putting any access controls in place. Data with a higher sensitivity level will have more access controls in place than data at a lower sensitivity level. The opposite of confidentiality is disclosure. Most security professionals consider confidentiality as it relates to data on the network or devices. However, data can also exist in printed format. Appropriate controls should be put into place to protect data on a network, but data in its printed format needs to be protected, too, which involves implementing data disposal policies. Examples of controls that improve confidentiality include encryption, steganography, access control lists (ACLs), and data classifications.
Integrity, the second part of the CIA triad, ensures that data is protected from unauthorized modification or data corruption. The goal of integrity is to preserve the consistency of data. The opposite of integrity is corruption. Many individuals do not consider data integrity to be as important as data confidentiality. However, data modification or corruption can often be just as detrimental to an enterprise because the original data is lost. Examples of controls that improve integrity include digital signatures, checksums, and hashes.
Finally, availability means ensuring that data is accessible when and where it is needed. Only individuals who need access to data should be allowed access to that data. Availability is the opposite of destruction or isolation. While many consider this tenet to be the least important of the three, an availability failure will affect end users and customers the most. Think of a denial-of-service (DoS) attack against a customer-facing web server. Examples of controls that improve availability include load balancing, hot sites, and RAID. DoS attacks affect availability.
Every security control that is put into place by an organization fulfills at least one of the security principles of the CIA triad. Understanding how to circumvent these security principles is just as important as understanding how to provide them.
A balanced security approach should be implemented to ensure that all three facets are considered when security controls are implemented. When implementing any control, you should identify the facet that the control addresses. For example, RAID addresses data availability, file hashes address data integrity, and encryption addresses data confidentiality. A balanced approach ensures that no facet of the CIA triad is ignored.
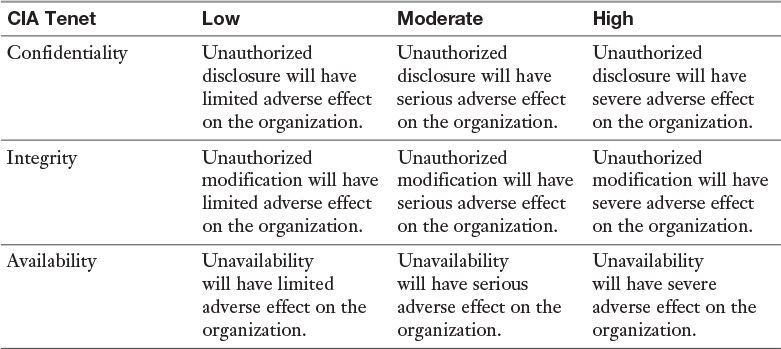
Federal Information Processing Standard Publication 199 (FIPS 199) defines standards for security categorization of federal information systems. This U.S. government standard establishes security categories of information systems used by the federal government.
FIPS 199 requires federal agencies to assess their information systems in each of the categories confidentiality, integrity and availability, rating each system as low, moderate, or high impact in each category. An information system’s overall security category is the highest rating from any category.
A potential impact is low if the loss of any tenet of CIA could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals. This occurs if the organization is able to perform its primary function but not as effectively as normal. This category only involves minor damage, financial loss, or harm.
A potential impact is moderate if the loss of any tenet of CIA could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. This occurs if the effectiveness with which the organization is able to perform its primary function is significantly reduced. This category involves significant damage, financial loss, or harm.
A potential impact is high if the loss of any tenet of CIA could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals. This occurs if an organization is not able to perform one or more of its primary functions. This category involves major damage, financial loss, or severe harm.
FIPS 199 provides a helpful chart that ranks the levels of CIA for information assets, as shown in Table 7-1.
It is also important that security professionals and organizations understand the information classification and life cycle. Classification varies depending on whether the organization is a commercial business or a military/government entity.
Information Classification and Life Cycle
Data should be classified based on its value to the organization and its sensitivity to disclosure. As you learned above, assigning a value to data allows an organization to determine the resources that should be used to protect the data. Resources that are used to protect data include personnel resources, monetary resources, and access control resources. Classifying data as it relates to CIA allows you to apply different protective measures.
After data is classified, the data can be segmented based on the level of protection it needs. The classification levels ensure that data is handled and protected in the most cost-effective manner possible. An organization should determine the classification levels it uses based on the needs of the organization. A number of commercial business and military and government information classifications are commonly used.
The information life cycle should also be based on the classification of the data. Organizations are required to retain certain information, particularly financial data, based on local, state, or government laws and regulations.
Commercial Business Classifications
Commercial businesses usually classify data using four main classification levels, listed here from the highest sensitivity level to the lowest:
1. Confidential
2. Private
3. Sensitive
4. Public
Data that is confidential includes trade secrets, intellectual data, application programming code, and other data that could seriously affect the organization if unauthorized disclosure occurred. Data at this level would only be available to personnel in the organization whose work relates to the data’s subject. Access to confidential data usually requires authorization for each access. Confidential data is exempt from disclosure under the Freedom of Information Act. In most cases, the only way for external entities to have authorized access to confidential data is as follows:
![]() After signing a confidentiality agreement
After signing a confidentiality agreement
![]() When complying with a court order
When complying with a court order
![]() As part of a government project or contract procurement agreement
As part of a government project or contract procurement agreement
Data that is private includes any information related to personnel—including human resources records, medical records, and salary information—that is used only within the organization. Data that is sensitive includes organizational financial information and requires extra measures to ensure its CIA and accuracy. Public data is data that would not cause a negative impact on the organization.
Military and Government Classifications
Military and governmental entities usually classify data using five main classification levels, listed here from the highest sensitivity level to the lowest:
1. Top secret
2. Secret
3. Confidential
4. Sensitive but unclassified
5. Unclassified
Data that is top secret includes weapons blueprints, technology specifications, spy satellite information, and other military information that could gravely damage national security if disclosed. Data that is secret includes deployment plans, missile placement, and other information that could seriously damage national security if disclosed. Data that is confidential includes patents, trade secrets, and other information that could seriously affect the government if unauthorized disclosure occurred. Data that is sensitive but unclassified includes medical or other personal data that might not cause serious damage to national security but could cause citizens to question the reputation of the government. Military and government information that does not fall into any of the other four categories is considered unclassified and usually has to be granted to the public based on the Freedom of Information Act.
Information Life Cycle
All organizations need procedures in place for the retention and destruction of data. Data retention and destruction must follow all local, state, and government regulations and laws. Documenting proper procedures ensures that information is maintained for the required time to prevent financial fines and possible incarceration of high-level organizational officers. These procedures must include both retention period and destruction process.
Incorporate Stakeholder Input into CIA Decisions
Often security professionals alone cannot best determine the CIA levels for enterprise information assets. Security professionals should consult with the asset stakeholders to gain their input on which level should be assigned to each tenet for an information asset. Keep in mind, however, that all stakeholders should be consulted. For example, while department heads should be consulted and have the biggest influence on the CIA decisions about departmental assets, other stakeholders within the department and organization should be consulted as well.
This rule holds for any security project that an enterprise undertakes. Stakeholder input should be critical at the start of the project to ensure that stakeholder needs are documented and to gain stakeholder project buy-in. Later, if problems arise with the security project and changes must be made, the project team should first discuss the potential changes with the project stakeholders before any project changes are approved or implemented.
Any feedback should be recorded and should be combined with the security professional assessment to help determine the CIA levels.
Implement Technical Controls Based on CIA Requirements and Policies of the Organization
Security professionals must ensure that the appropriate controls are implemented for organizational assets to be protected. The controls that are implemented should be based on the CIA requirements and the policies implemented by the organization. After implementing controls, it may also be necessary to perform a gap analysis to determine where security gaps still exist so that other needed security controls can be implemented.
Security professionals should be familiar with the categories and types of access controls that can be implemented.
Access Control Categories
You implement access controls as a countermeasure to identified vulnerabilities. Access control mechanisms that you can use are divided into seven main categories:
![]() Compensative
Compensative
![]() Corrective
Corrective
![]() Detective
Detective
![]() Deterrent
Deterrent
![]() Directive
Directive
![]() Preventive
Preventive
![]() Recovery
Recovery
Any access control that you implement will fit into one or more access control category.
Compensative
Compensative controls are in place to substitute for a primary access control and mainly act as a way to mitigate risks. Using compensative controls, you can reduce risk to a more manageable level. Examples of compensative controls include requiring two authorized signatures to release sensitive or confidential information and requiring two keys owned by different personnel to open a safe deposit box.
Corrective
Corrective controls are in place to reduce the effect of an attack or other undesirable event. Using corrective controls fixes or restores the entity that is attacked. Examples of corrective controls include installing fire extinguishers, isolating or terminating a connection, implementing new firewall rules, and using server images to restore to a previous state. Corrective controls are useful after an event has occurred.
Detective
Detective controls are in place to detect an attack while it is occurring to alert appropriate personnel. Examples of detective controls include motion detectors, intrusion detection systems (IDSs), logs, guards, investigations, and job rotation. Detective controls are useful during an event.
Deterrent
Deterrent controls deter or discourage an attacker. Via deterrent controls, attacks can be discovered early in the process. Deterrent controls often trigger preventive and corrective controls. Examples of deterrent controls include user identification and authentication, fences, lighting, and organizational security policies, such as a nondisclosure agreement (NDA).
Directive
Directive controls specify acceptable practice within an organization. They are in place to formalize an organization’s security directive mainly to its employees. The most popular directive control is an acceptable use policy (AUP) that lists proper (and often examples of improper) procedures and behaviors that personnel must follow. Any organizational security policies or procedures usually fall into this access control category. You should keep in mind that directive controls are efficient only if there is a stated consequence for not following the organization’s directions.
Preventive
Preventive controls prevent an attack from occurring. Examples of preventive controls include locks, badges, biometric systems, encryption, intrusion prevention systems (IPSs), antivirus software, personnel security, security guards, passwords, and security awareness training. Preventive controls are useful before an event occurs.
Recovery
Recovery controls recover a system or device after an attack has occurred. The primary goal of recovery controls is restoring resources. Examples of recovery controls include disaster recovery plans, data backups, and offsite facilities.
Access Control Types
Access control types divide access controls based on their method of implementation. The three types of access controls are:
![]() Administrative (management) controls
Administrative (management) controls
![]() Logical (technical) controls
Logical (technical) controls
![]() Physical controls
Physical controls
In any organization where defense in depth is a priority, access control requires the use of all three types of access controls. Even if you implement the strictest physical and administrative controls, you cannot fully protect the environment without logical controls.
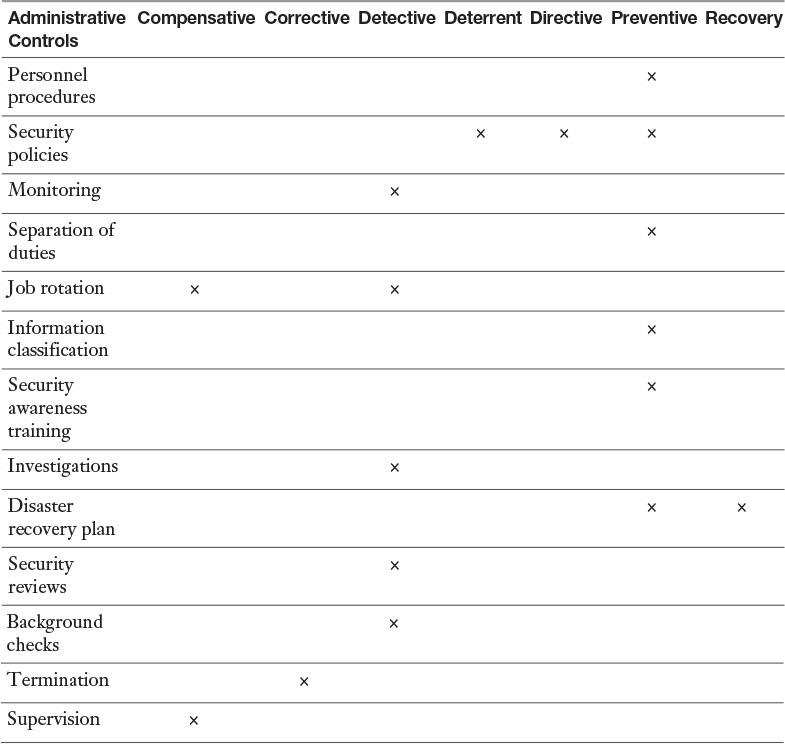
Administrative (Management) Controls
Administrative, or management, controls are implemented to administer the organization’s assets and personnel and include security policies, procedures, standards, baselines, and guidelines that are established by management. These controls are commonly referred to as soft controls. Specific examples are personnel controls, data classification, data labeling, security awareness training, and supervision.
Security awareness training is a very important administrative control. Its purpose is to improve the organization’s attitude about safeguarding data. The benefits of security awareness training include reduction in the number and severity of errors and omissions, better understanding of information value, and better administrator recognition of unauthorized intrusion attempts. A cost-effective way to ensure that employees take security awareness seriously is to create an award or recognition program.
Table 7-2 lists many administrative controls and includes the access control categories the controls fit.
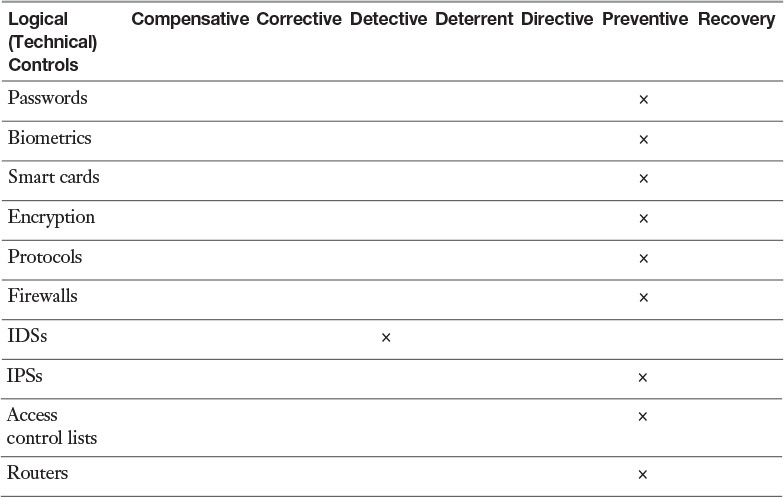
Logical (Technical) Controls
Logical, or technical, controls are software or hardware components used to restrict access. Specific examples of logical controls are firewalls, IDSs, IPSs, encryption, authentication systems, protocols, auditing and monitoring, biometrics, smart cards, and passwords.
An example of implementing a technical control is adopting a new security policy that forbids employees from remotely configuring the email server from a third party’s location during work hours.
Although auditing and monitoring are logical controls and are often listed together, they are actually two different controls. Auditing is a one-time or periodic event to evaluate security. Monitoring is an ongoing activity that examines either the system or users.
Table 7-3 lists many logical controls and includes which access control categories the controls fit.
Physical Controls
Physical controls are implemented to protect an organization’s facilities and personnel. Personnel concerns should take priority over all other concerns. Specific examples of physical controls include perimeter security, badges, swipe cards, guards, dogs, mantraps, biometrics, and cabling.
Table 7-4 lists many physical controls and includes which access control categories the controls fit.
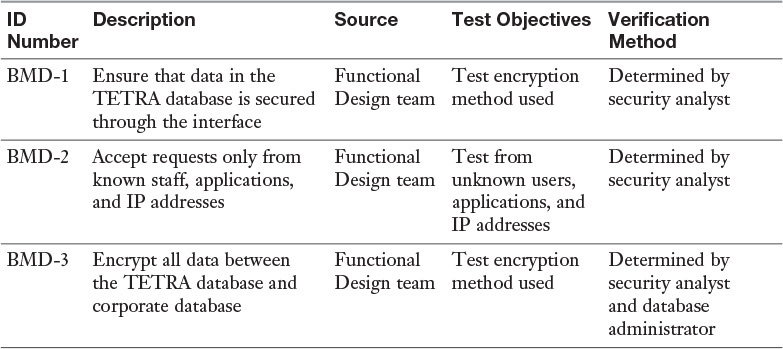
Security Requirements Traceability Matrix (SRTM)
A security requirements traceability matrix (SRTM) is a grid that displays what is required for an asset’s security. SRTMs are necessary in technical projects that call for security to be included. Using such a matrix is an effective way for a user to ensure that all work is being completed.
Table 7-5 is an example of an SRTM for a new interface. Keep in mind that an organization may customize an SRTM to fit its needs.
Determine the Aggregate CIA Score
According to Table 7-1, FIPS 199 defines three impacts (low, moderate, and high) for the three security tenets. But the levels that are assigned to organizational entities must be defined by the organization because only the organization can determine whether a particular loss is limited, serious, or severe.
According to FIPS 199, the security category (SC) of an identified entity expresses the three tenets with their values for an organizational entity. The values are then used to determine which security controls should be implemented. If a particular asset is made up of multiple entities, then you must calculate the SC for that asset based on the entities that make it up. FIPS 199 provides a nomenclature for expressing these values, as shown here:
SCinformation type = {(confidentiality, impact), (integrity, impact), (availability, impact)}
Let’s look at an example of this nomenclature in a real-world example:
SCpublic site = {(confidentiality, low), (integrity, moderate), (availability, high)}
SCpartner site = {(confidentiality, moderate), (integrity, high), (availability, moderate)}
SCinternal site = {(confidentiality, high), (integrity, medium), (availability, moderate)}
Now let’s assume that all of the sites reside on the same web server. To determine the nomenclature for the web server, you need to use the highest values of each of the categories:
SCweb server = {(confidentiality, high), (integrity, high), (availability, high)}
Some organizations may decide to place the public site on a web server and isolate the partner site and internal site on another web server. In this case, the public web server would not need all of the same security controls and would be cheaper to implement than the partner/internal web server.
For the CASP exam, this FIPS 199 nomenclature is referred to as the aggregate CIA score.
Extreme Scenario/Worst-Case Scenario Planning
In any security planning, an organization must perform extreme scenario or worst-case scenario planning. This planning ensures that an organization anticipates catastrophic events before they occur and can put the appropriate plans in place.
The first step to this worst-case scenario planning is to analyze all the threats to identify all the actors who pose significant threats to the organization. Examples of the threat actors include both internal and external actors and include the following:
![]() Reckless employee
Reckless employee
![]() Untrained employee
Untrained employee
![]() Partner
Partner
![]() Disgruntled employee
Disgruntled employee
![]() Internal spy
Internal spy
![]() Government spy
Government spy
![]() Vendor
Vendor
![]() Thief
Thief
![]() Anarchist
Anarchist
![]() Competitor
Competitor
![]() Corrupt government official
Corrupt government official
![]() Data miner
Data miner
![]() Irrational individual
Irrational individual
![]() Legal adversary
Legal adversary
![]() Mobster
Mobster
![]() Activist
Activist
![]() Terrorist
Terrorist
![]() Vandal
Vandal
These actors can be subdivided into two categories: non-hostile and hostile. Of the lists given above, three actors are usually considered non-hostile: reckless employee, untrained employee, and partner. All the other actors should be considered hostile.
The organization would then need to analyze each of these threat actors according to set criteria. All threat actors should be given a ranking to help determine which threat actors will be analyzed. Examples of some of the most commonly used criteria include the following:
![]() Skill level: None, minimal, operational, adept
Skill level: None, minimal, operational, adept
![]() Resources: Individual, team, organization, government
Resources: Individual, team, organization, government
![]() Limits: Code of conduct, legal, extra-legal (minor), extra-legal (major)
Limits: Code of conduct, legal, extra-legal (minor), extra-legal (major)
![]() Visibility: Overt, covert, clandestine, don’t care
Visibility: Overt, covert, clandestine, don’t care
![]() Objective: Copy, destroy, injure, take, don’t care
Objective: Copy, destroy, injure, take, don’t care
![]() Outcome: Acquisition/theft, business advantage, damage, embarrassment, technical advantage
Outcome: Acquisition/theft, business advantage, damage, embarrassment, technical advantage
With these criteria, the organization must then determine which of the actors it wants to analyze. For example, the organization may choose to analyze all hostile actors that have a skill level of adept, resources of organization or government, and limits of extra-legal (minor) or extra-legal (major). Then the list is consolidated to include only the threat actors that fit all of these criteria.
Next, the organization must determine what it really cares about protecting. Most often this determination is made using the FIPS 199 method or some sort of business impact analysis. Once the vital assets are determined, the organization should then select the scenarios that could have a catastrophic impact on the organization by using the objective and outcome values from the threat actor analysis and the asset value and business impact information from the impact analysis.
Scenarios must then be made so that they can be fully analyzed. For example, an organization may decide to analyze a situation in which a hacktivist group performs prolonged denial-of-service attacks, causing sustained outages to damage an organization’s reputation. Then a risk determination should be made for each scenario. Risk determination is discussed later in this chapter.
Once all the scenarios are determined, the organization develops an attack tree for each scenario. Such an attack tree includes all the steps and/or conditions that must occur for the attack to be successful. The organization then maps security controls to the attack trees.
To determine the security controls that can be used, an organization would need to look at industry standards, including National Institute of Standards and Technology (NIST) Special Publication (SP) 800-53 (http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r4.pdf) (discussed later in this chapter) and SANS 20 Critical Security Controls for Effective Cyber Defense (http://www.sans.org/critical-security-controls/). Finally, the controls would be mapped back into the attack tree to ensure that controls are implemented at as many levels of the attack as possible.
As you can see, worst-case scenario planning is an art of its own and requires extensive training and effort to ensure success. For the CASP exam, candidates should focus more on the process and steps required than on how to perform the analysis and create the scenario documentation.
Determine Minimum Required Security Controls Based on Aggregate Score
The appropriate security controls must be implemented for all organizational assets. The security controls that should be implemented are determined based on the aggregate CIA score discussed earlier in this chapter.
It is vital that security professionals understand the types of coverage that are provided by the different security controls that can be implemented. As analysis occurs, security professionals should identify a minimum set of security controls that must be implemented.
Conduct System-Specific Risk Analysis
A risk assessment is a tool used in risk management to identify vulnerabilities and threats, assess the impact of those vulnerabilities and threats, and determine which controls to implement. Risk assessment or analysis has four main goals:
![]() Identify assets and asset value.
Identify assets and asset value.
![]() Identify vulnerabilities and threats.
Identify vulnerabilities and threats.
![]() Calculate threat probability and business impact.
Calculate threat probability and business impact.
![]() Balance threat impact with countermeasure cost.
Balance threat impact with countermeasure cost.
Prior to starting a risk assessment, management and the risk assessment team must determine which assets and threats to consider. This process determines the size of the project. The risk assessment team must then provide a report to management on the value of the assets considered. Management can then review and finalize the asset list, adding and removing assets as it sees fit, and then determine the budget of the risk assessment project.
Let’s look at a specific scenario to help understand the importance of system-specific risk analysis. In our scenario, the Sales division decides to implement touchscreen technology and tablet computers to increase productivity. As part of this new effort, a new sales application will be developed that works with the new technology. At the beginning of the deployment, the chief security officer (CSO) attempted to prevent the deployment because the technology is not supported in the enterprise. Upper management decided to allow the deployment. The CSO should then work with the Sales division and other areas involved so that the risk associated with the full life cycle of the new deployment can be fully documented and appropriate controls and strategies can be implemented during deployment.
Risk assessment should be carried out before any mergers and acquisitions occur or new technology and applications are deployed.
If a risk assessment is not supported and directed by senior management, it will not be successful. Management must define the purpose and scope of a risk assessment and allocate the personnel, time, and monetary resources for the project.
Make Risk Determination
To make a risk determination, an organization must perform a formal risk analysis. A formal risk analysis often asks questions such as: What corporate assets need to be protected? What are the business needs of the organization? What outside threats are most likely to compromise network security?
Different types of risk analysis, including qualitative risk analysis and quantitative risk analysis, should be used to ensure that the data obtained is maximized.
Qualitative Risk Analysis
Qualitative risk analysis does not assign monetary and numeric values to all facets of the risk analysis process. Qualitative risk analysis techniques include intuition, experience, and best practice techniques, such as brainstorming, focus groups, surveys, questionnaires, meetings, interviews, and Delphi. The Delphi technique is a method used to estimate the likelihood and outcome of future events. Although all of these techniques can be used, most organizations will determine the best technique(s) based on the threats to be assessed. Experience and education on the threats are needed.
Each member of the group who has been chosen to participate in the qualitative risk analysis uses his or her experience to rank the likelihood of each threat and the damage that might result. After each group member ranks the threat possibility, loss potential, and safeguard advantage, data is combined in a report to present to management.
Advantages of qualitative over quantitative risk analysis include qualitative prioritizes the risks and identifies areas for immediate improvement in addressing the threats. Disadvantages of qualitative risk analysis include all results are subjective, and a dollar value is not provided for cost/benefit analysis or for budget help.
Note
When performing risk analyses, all organizations experience issues with any estimate they obtain. This lack of confidence in an estimate is referred to as uncertainty and is expressed as a percentage. Any reports regarding a risk assessment should include the uncertainty level.
Quantitative Risk Analysis
A quantitative risk analysis assigns monetary and numeric values to all facets of the risk analysis process, including asset value, threat frequency, vulnerability severity, impact, and safeguard costs. Equations are used to determine total and residual risks.
An advantage of quantitative over qualitative risk analysis is that quantitative uses less guesswork than qualitative. Disadvantages of quantitative risk analysis include the difficulty of the equations, the time and effort needed to complete the analysis, and the level of data that must be gathered for the analysis.
Most risk analysis includes some hybrid use of both quantitative and qualitative risk analyses. Most organizations favor using quantitative risk analysis for tangible assets and qualitative risk analysis for intangible assets.
Keep in mind that even though quantitative risk analysis uses numeric value, a purely quantitative analysis cannot be achieved because some level of subjectivity is always part of the data. This type of estimate should be based on historical data, industry experience, and expert opinion.
Magnitude of Impact
Risk impact or magnitude of impact is an estimate of how much damage a negative risk can have or the potential opportunity cost should a positive risk be realized. Risk impact can be measured in financial terms (quantitative) or with a subjective measurement scale (qualitative). Risks usually are ranked on a scale that is determined by the organization. High-level risks result in significant loss, and low-level risks result in negligible losses.
If magnitude of impact can be expressed in financial terms, use of financial value to quantify the magnitude has the advantage of being easily understood by personnel. The financial impact might be long-term costs in operations and support, loss of market share, short-term costs in additional work, or opportunity cost.
Two calculations are used when determining the magnitude of impact: single loss expectancy (SLE) and annualized loss expectancy (ALE).
SLE
The SLE is the monetary impact of each threat occurrence. To determine the SLE, you must know the asset value (AV) and the exposure factor (EF). The EF is the percent value or functionality of an asset that will be lost when a threat event occurs. The calculation for obtaining the SLE is as follows:
SLE = AV × EF
For example, an organization has a web server farm with an AV of $20,000. If the risk assessment has determined that a power failure is a threat agent for the web server farm and the exposure factor for a power failure is 25%, the SLE for this event equals $5,000.
ALE
The ALE is the expected risk factor of an annual threat event. To determine the ALE, you must know the SLE and the annualized rate of occurrence (ARO). (Note that ARO is explained later in this chapter, in the “Likelihood of Threat” section.) The calculation for obtaining the ALE is as follows:
ALE = SLE × ARO
Using the previously mentioned example, if the risk assessment has determined that the ARO for the power failure of the web server farm is 50%, the ALE for this event equals $2,500.
Using the ALE, the organization can decide whether to implement controls. If the annual cost of a control to protect the web server farm is more than the ALE, the organization could easily choose to accept the risk by not implementing the control. If the annual cost of the control to protect the web server farm is less than the ALE, the organization should consider implementing the control.
Likelihood of Threat
The likelihood of threat is a measurement of the chance that a particular risk event will impact the organization. When the vulnerabilities and threats have been identified, the loss potential for each must be determined. This loss potential is determined by using the likelihood of the event combined with the impact that such an event would cause. An event with a high likelihood and a high impact would be given more importance than an event with a low likelihood and a low impact. The chance of natural disasters will vary based on geographic location. However, the chances of human-made risks are based more on organizational factors, including visibility, location, technological footprint, and so on. The levels used for threat likelihood are usually high, moderate, and low.
The likelihood that an event will occur is usually determined by examining the motivation, source, ARO, and trend analysis.
Motivation
Motivation is what causes organizations and their attackers to act. Not all risks that an organization identifies will have a motivation. For example, natural disasters have no motivation or reasoning behind their destruction other than climatic or other natural conditions that are favorable to them coming into being.
However, most human-made attacks have motivations. These motivations are usually similar to the outcomes discussed earlier in this chapter, in the “Extreme Scenario/Worst-Case Scenario Planning” section. If your organization identifies any risks that are due to the actions of other people or organizations, these risks are usually motivated by the following:
![]() Acquisition/theft
Acquisition/theft
![]() Business advantage
Business advantage
![]() Damage
Damage
![]() Embarrassment
Embarrassment
![]() Technical advantage
Technical advantage
Understanding the motivation behind these risks is vital to determining which risk strategy your organization should employ.
Source
As discussed earlier in this chapter, in the “Extreme Scenario/Worst-Case Scenario Planning” section, the source of organizational risks can fall into several broad categories. Internal sources are those within an organization, and external sources are those outside the organization. These two categories can be further divided into hostile and non-hostile sources. For example, an improperly trained employee might inadvertently be susceptible to a social engineering attack, but a disgruntled employee may intentionally sabotage organizational assets.
When an organization understands the source and motivation behind the risk, the attack route and mechanism can be better analyzed to help determine which controls could be employed to minimize the risk.
ARO
The annualized rate of occurrence (ARO) is an estimate of how often a given threat might occur annually. Remember that an estimate is only as good as the certainty of the estimate. It might be possible that you can obtain the ARO internally just by examining logs and archive information. If you do not have access to this type of internal information, consult with subject matter experts (SMEs), industry experts, organizational standards and guidelines, and other authoritative resources to ensure that you obtain the best estimate for your calculations.
Trend Analysis
In risk management, it is sometimes necessary to identify trends. In this process, historical data is utilized, given a set of mathematical parameters, and then processed in order to determine any possible variance from an established baseline.
If you do not know the established baseline, you cannot identify any variances from the baseline and then track trends in these variances. Organizations should establish procedures for capturing baseline statistics and for regularly comparing current statistics against the baselines. Also, organizations must recognize when new baselines should be established. For example, if your organization implements a two-server web farm, the baseline would be vastly different than the baseline if that farm were upgraded to four servers or if the internal hardware in the servers were upgraded.
Security professionals must also research growing trends worldwide, especially in the industry in which the organization exists. Financial industry risk trends will vary from healthcare industry risk trends, but there are some common areas that both industries must understand. For example, any organizations that have ecommerce sites must understand the common risk trends and be able to analyze their internal sites to determine whether their resources are susceptible to these risks.
Return on Investment (ROI)
The term return on investment (ROI) refers to the money gained or lost after an organization makes an investment. ROI is a necessary metric for evaluating security investments.
ROI measures the expected improvement over the status quo against the cost of the action required to achieve the improvement. In the security field, improvement is not really the goal. Reduction in risk is the goal. But it is often hard to determine exactly how much an organization will save if it makes an investment. Some of the types of loss that can occur include:
![]() Productivity loss: This includes downtime and repair time. Any time personnel are not performing their regular duties because of a security issue, your organization has experienced a productivity loss.
Productivity loss: This includes downtime and repair time. Any time personnel are not performing their regular duties because of a security issue, your organization has experienced a productivity loss.
![]() Revenue loss during outage: If an asset is down and cannot be accessed, the organization loses money with each minute and hour that the asset is down. That is increased exponentially if an organization’s Internet connection goes down because that affects all organizational assets.
Revenue loss during outage: If an asset is down and cannot be accessed, the organization loses money with each minute and hour that the asset is down. That is increased exponentially if an organization’s Internet connection goes down because that affects all organizational assets.
![]() Data loss: If data is lost, it must be restored, which ties back to productivity loss because personnel must restore the data backup. However, organizations must also consider conditions where backups are destroyed, which could be catastrophic.
Data loss: If data is lost, it must be restored, which ties back to productivity loss because personnel must restore the data backup. However, organizations must also consider conditions where backups are destroyed, which could be catastrophic.
![]() Data compromise: This includes disclosure or modification. Measures must be taken to ensure that data, particularly intellectual data, is protected.
Data compromise: This includes disclosure or modification. Measures must be taken to ensure that data, particularly intellectual data, is protected.
![]() Repair costs: This includes costs to replace hardware or costs incurred to employ services from vendors.
Repair costs: This includes costs to replace hardware or costs incurred to employ services from vendors.
![]() Loss of reputation: Any security incident that occurs can result in a loss of reputation with your organization’s partners and customers. Recent security breaches at popular retail chains have resulted in customer reluctance to trust the stores with their data.
Loss of reputation: Any security incident that occurs can result in a loss of reputation with your organization’s partners and customers. Recent security breaches at popular retail chains have resulted in customer reluctance to trust the stores with their data.
Let’s look at a scenario to better understand how ROI can really help with the risk analysis process. Suppose two companies are merging. One company uses mostly hosted services from an outside vendor, while the other uses mostly in-house products. When the merging project is started, the following goals for the merged systems are set:
![]() Ability to customize systems at the department level
Ability to customize systems at the department level
![]() Quick implementation along with an immediate ROI
Quick implementation along with an immediate ROI
![]() Administrative-level control over all products by internal IT staff
Administrative-level control over all products by internal IT staff
The project manager states that the in-house products are the best solution. Because of staff shortages, the security administrator argues that security will be best maintained by continuing to use outsourced services. The best way to resolve this issue is to:
1. Calculate the time to deploy and support the in-sourced systems for the staff shortage.
2. Compare the costs to the ROI costs minus outsourcing costs.
3. Present the document numbers to management for a final decision.
When calculating ROI, there is a degree of uncertainty and subjectivity involved, but once you decide what to measure and estimate, the question of how to measure it should be somewhat easier. The most effective measures are likely to be those you already are using because they will enable you to compare security projects with all other projects. Two popular methods are payback and net present value (NPV).
Payback
Payback is a simple calculation that compares ALE against the expected savings as a result of an investment. Let’s use the earlier example of the server that results in a $2,500 ALE. The organization may want to deploy a power backup if it can be purchased for less than $2,500. However, if that power backup cost a bit more, the organization might be willing to still invest in the device if it is projected to provide protection for more than one year with some type of guarantee.
Net Present Value (NPV)
Net present value (NPV) adds another dimension to payback by considering the fact that money spent today is worth more than savings realized tomorrow. In the example above, the organization may purchase a power backup that comes with a five-year warranty. To calculate NPV, you need to know the discount rate, which determines how much less money is worth in the future. For our example, we’ll use a discount rate of 10%. Now to the calculation: You divide the yearly savings ($2,500) by 1.1 (that is 1 plus the discount rate) to the power of the number of year you want to analyze. So this is what the calculation would look like for the first year:
NPV = $2,500 / (1.1) = $2,272.73
The result is the savings expected in today’s dollar value. For each year, you could then recalculate NPV by raising the 1.1 value to the year number. The calculation for the second year would be:
NPV = $2,500 / (1.1)2 = $2,066.12
If you’re trying to weigh costs and benefits, and the costs are immediate but the benefits are long term, NPV can provide a more accurate measure of whether a project is truly worthwhile.
Total Cost of Ownership
Organizational risks are everywhere and range from easily insurable property risks to risks that are hard to anticipate and calculate, such as the loss of a key employee. The total cost of ownership (TCO) of risk measures the overall costs associated with running the organizational risk management process, including insurance premiums, finance costs, administrative costs, and any losses incurred. This value should be compared to the overall company revenues and asset base. TCO provides a way to assess how an organization’s risk-related costs are changing as compared to the overall organization growth rate. This TCO can also be compared to industry baselines that are available from trade groups and industry organizations. Working with related business and industry experts ensures that your organization is obtaining relevant and comparable risk-related data. For example, a financial organization should not compare its risk TCO to TCOs of organizations in the healthcare field.
Calculating risk TCO has many advantages. It can help organizations discover inconsistencies in their risk management approach. It can also identify areas where managing a particular risk is excessive as compared to similar risks managed elsewhere. Risk TCO can also generate direct cost savings by highlighting risk management process inefficiency.
However, comparable risk TCO is often difficult to find because many direct competitors protect this sensitive data. Relying on trade bodies and industry standards bodies can often help alleviate this problem. Also, keep in mind the risk that TCO may be seen as a cost-cutting activity, resulting in personnel not fully buying in to the process.
Some of the guidelines an organization should keep in mind when determining risk TCO are as follows:
![]() Determine a framework that will be used to break down costs into categories, including risk financing, risk administration, risk compliance costs, and self-insured losses.
Determine a framework that will be used to break down costs into categories, including risk financing, risk administration, risk compliance costs, and self-insured losses.
![]() Identify the category costs by expressing them as a percentage of overall organizational revenue.
Identify the category costs by expressing them as a percentage of overall organizational revenue.
![]() Employ any data from trade bodies for comparison with each category’s figures.
Employ any data from trade bodies for comparison with each category’s figures.
![]() Analyze any differences between your organization’s numbers and industry figures for reasons of occurrence.
Analyze any differences between your organization’s numbers and industry figures for reasons of occurrence.
![]() Set future targets for each category.
Set future targets for each category.
When calculating and analyzing risk TCO, you should remember these basic rules:
![]() Industry benchmarks may not always be truly comparable to your organization’s data.
Industry benchmarks may not always be truly comparable to your organization’s data.
![]() Cover some minor risks within the organization.
Cover some minor risks within the organization.
![]() Employ risk management software to aid in the decision making because of the complex nature of risk management.
Employ risk management software to aid in the decision making because of the complex nature of risk management.
![]() Remember the value of risk management when budgeting. It is not merely a cost.
Remember the value of risk management when budgeting. It is not merely a cost.
![]() Risk TCO does not immediately lead to cost savings. Savings occur over time.
Risk TCO does not immediately lead to cost savings. Savings occur over time.
![]() Not all possible solutions will rest within the organization. External specialists and insurance brokers may be needed.
Not all possible solutions will rest within the organization. External specialists and insurance brokers may be needed.
Recommend Which Strategy Should be Applied Based on Risk Appetite
Risk reduction is the process of altering elements of the organization in response to risk analysis. After an organization understands the ROI and TCO, it must determine how to handle the risk, which is based on the organization’s risk appetite, or how much risk the organization can withstand on its own.
The four basic strategies that must be understood for the CASP exam are avoid, transfer, mitigate, and accept.
Avoid
The avoid strategy involves terminating the activity that causes a risk or choosing an alternative that is not as risky. Unfortunately, this method cannot be used against all threats. An example of avoidance is organizations utilizing alternate data centers in different geographic locations to avoid a natural disaster being able to affect both facilities.
Many times it is impossible to avoid risk. For example, if a CEO purchases a new mobile device and insists that he be given internal network access via this device, avoiding the risk is impossible. In this case, you would need to find a way to mitigate and/or transfer the risk.
Consider the following scenario: A company is in negotiations to acquire another company for $1,000,000. Due diligence activities have uncovered systemic security issues in the flagship product of the company being purchased. A complete product rewrite because of the security issues is estimated to cost $1,500,000. In this case, the company should not acquire the other company because the acquisition would actually end up costing $2,500,000.
Transfer
The transfer strategy passes the risk on to a third party, including insurance companies. An example is to outsource certain functions to a provider, usually involving a service-level agreement (SLA) with a third party. However, the risk could still rest with the original organization, depending on the provisions in the contract. If your organization plans to use this method, legal counsel should be used to ensure that the contract provides the level of protection needed.
Consider the following scenario: A small business has decided to increase revenue by selling directly to the public through an online system. Initially this will be run as a short-term trial. If it is profitable, the system will be expanded and form part of the day-to-day business. Two main business risks for the initial trial have been raised:
![]() Internal IT staff have no experience with secure online credit card processing.
Internal IT staff have no experience with secure online credit card processing.
![]() An internal credit card processing system will expose the business to additional compliance requirements.
An internal credit card processing system will expose the business to additional compliance requirements.
In this situation, it is best to transfer the initial risks by outsourcing payment processing to a third-party service provider.
Mitigate
The mitigate strategy defines the acceptable risk level the organization can tolerate and reduces the risk to that level. This is the most common strategy employed. This strategy includes implementing security controls, including intrusion detection systems (IDSs), intrusion prevention systems (IPSs), firewalls, and so on.
Consider the following scenario: Your company’s web server experiences a security incident three times a year, costing the company $1,500 in downtime per occurrence. The web server is only for archival access and is scheduled to be decommissioned in five years. The cost of implementing software to prevent this incident would be $15,000 initially, plus $1,000 a year for maintenance. The cost of the security incident is calculated as follows:
($1,500 per occurrence × 3 per year) × 5 years = $22,500
The cost to prevent the problem is calculated as follows:
$15,000 software cost + ($1,000 maintenance × 5 years) = $20,000
In this situation, the mitigation (implementing the software) is cheaper than accepting the risk.
Accept
The accept strategy understands and accepts the level of risk as well as the cost of damages that can occur. This strategy is usually used to cover residual risk, which is discussed later in this chapter. It is usually employed for assets that have small exposure or value.
However, sometimes an organization will have to accept risks because the budget that was originally allocated for implementing controls to protect against risks is depleted. Accepting the risk is fine if the risks and the assets are not high profile. However, if they are considered high-profile risks, management should be informed of the need for another financial allocation to mitigate the risks.
Risk Management Processes
Risk management includes several steps in a process that are followed to help guide an organization. These steps are documented in NIST SP 800-30.
According to NIST SP 800-30, common information-gathering techniques used in risk analysis include automated risk assessment tools, questionnaires, interviews, and policy document reviews. Keep in mind that multiple sources should be used to determine the risks to a single asset. The NIST SP 800-30 identifies the following steps in the risk assessment process:
1. Identify the assets and their value.
2. Identify threats.
3. Identify vulnerabilities.
4. Determine likelihood.
5. Identify impact.
6. Determine risk as a combination of likelihood and impact.
Information and Asset (Tangible/Intangible) Value and Costs
As stated earlier, the first step of any risk assessment is to identify the assets and determine the asset values. Assets are both tangible and intangible. Tangible assets include computers, facilities, supplies, and personnel. Intangible assets include intellectual property, data, and organizational reputation. The value of an asset should be considered in respect to the asset owner’s view. These six considerations can be used to determine an asset’s value:
![]() Value to owner
Value to owner
![]() Work required to develop or obtain the asset
Work required to develop or obtain the asset
![]() Damage that would result if the asset were lost
Damage that would result if the asset were lost
![]() Cost that competitors would pay for the asset
Cost that competitors would pay for the asset
![]() Penalties that would result if the asset was lost
Penalties that would result if the asset was lost
After determining the value of the assets, you should determine the vulnerabilities and threats to each asset.
Vulnerabilities and Threats Identification
When determining vulnerabilities and threats to an asset, considering the threat agents first is often easiest. Threat agents can be grouped into the following six categories:
![]() Human: This category includes both malicious and non-malicious insiders and outsiders, terrorists, spies, and terminated personnel.
Human: This category includes both malicious and non-malicious insiders and outsiders, terrorists, spies, and terminated personnel.
![]() Natural: This category includes floods, fires, tornadoes, hurricanes, earthquakes, or other natural disasters or weather events.
Natural: This category includes floods, fires, tornadoes, hurricanes, earthquakes, or other natural disasters or weather events.
![]() Technical: This category includes hardware and software failure, malicious code, and new technologies.
Technical: This category includes hardware and software failure, malicious code, and new technologies.
![]() Physical: This category includes CCTV issues, perimeter measures failure, and biometric failure.
Physical: This category includes CCTV issues, perimeter measures failure, and biometric failure.
![]() Environmental: This category includes power and other utility failures, traffic issues, biological warfare, and hazardous material issues (such as spillage).
Environmental: This category includes power and other utility failures, traffic issues, biological warfare, and hazardous material issues (such as spillage).
![]() Operational: This category includes any process or procedure that can affect CIA.
Operational: This category includes any process or procedure that can affect CIA.
These categories should be used along with the threat actors identified earlier in this chapter, in the “Extreme Scenario/Worst-Case Scenario Planning” section, to help your organization develop the most comprehensive list of threats possible.
Exemptions
While most organizations should complete a thorough risk analysis and take measures to protect against all risks, some organizations have exemptions from certain types of risks due to the nature of their business and governmental standards.
For example, the U.S. Environmental Protection Agency (EPA) has regulations regarding the use and storage of certain chemicals, such as ammonia and propane. Organizations that store quantities of these chemicals above a certain limit are required to follow the EPA’s Accidental Release Prevention provisions and Risk Management Program regulations. However, most farmers who need ammonia as a soil nutrient are not subject to these regulations. Neither are propane retail facilities.
In most cases, organizations should employ legal counsel to ensure that they understand any exemptions that they think apply to them.
Deterrence
Deterrence is the use of the threat of punishment to deter persons from committing certain actions. Many governmental agencies employ this risk management method by posting legal statements in which unauthorized users are threatened with fines and/or imprisonment if the unauthorized users gain access to their network or systems. Organizations employ similar methods that include warnings when accessing mail systems, ecommerce systems, or other systems that may contain confidential data.
Inherent
Inherent risk is risk that has no mitigation factors or treatments applied to it because it is virtually impossible to avoid. Consider an attacker who is determined and has the skills to physically access an organization’s facility. While many controls, including guards, CCTV, fencing, locks, and biometrics, can be implemented to protect against this threat, an organization cannot truly ensure that this risk will never occur if the attacker has the level of skills needed. That does not mean that the organization should not implement these controls that are considered baseline controls.
When possible, inherent risks should be identified for the following reasons:
![]() Knowing the risks helps to identify critical controls.
Knowing the risks helps to identify critical controls.
![]() Audits can then be focused on critical controls.
Audits can then be focused on critical controls.
![]() Inherent risks that have potential catastrophic consequences can be subjected to more stringent scenario testing.
Inherent risks that have potential catastrophic consequences can be subjected to more stringent scenario testing.
![]() The board and management of the organization can be made aware of risks that have potential catastrophic consequences.
The board and management of the organization can be made aware of risks that have potential catastrophic consequences.
Residual
No matter how careful an organization is, it is impossible to totally eliminate all risks. Residual risk is the level of risk that remains after the safeguards or controls have been implemented. Residual risk is represented using the following equation:
Residual risk = Total risk – Countermeasures
This equation is considered to be more conceptual in nature than for actual calculation.
Enterprise Security Architecture Frameworks
Many organizations have developed enterprise security architecture frameworks to help guide security professionals. It is always best to use these frameworks as a guideline to ensure that your enterprise’s security architecture is comprehensive. Most frameworks include business capabilities, reference models, and the business vision and drivers.
Consider the following scenario: A company has a team of security architects and designers that contribute to broader IT architecture and design solutions. Concerns have been raised due to the varying levels of quality and consistency of the security contributions. The team agrees that a more formalized methodology is needed that can take into account business drivers, capabilities, baselines, and reusable patterns. Introducing an enterprise security architecture framework in this situation would provide the needed guidance.
These frameworks assist organizations in creating and maintaining consistent security functions across the enterprise. The following sections discuss SABSA, CobiT, and NIST SP 800-53.
Sherwood Applied Business Security Architecture (SABSA)
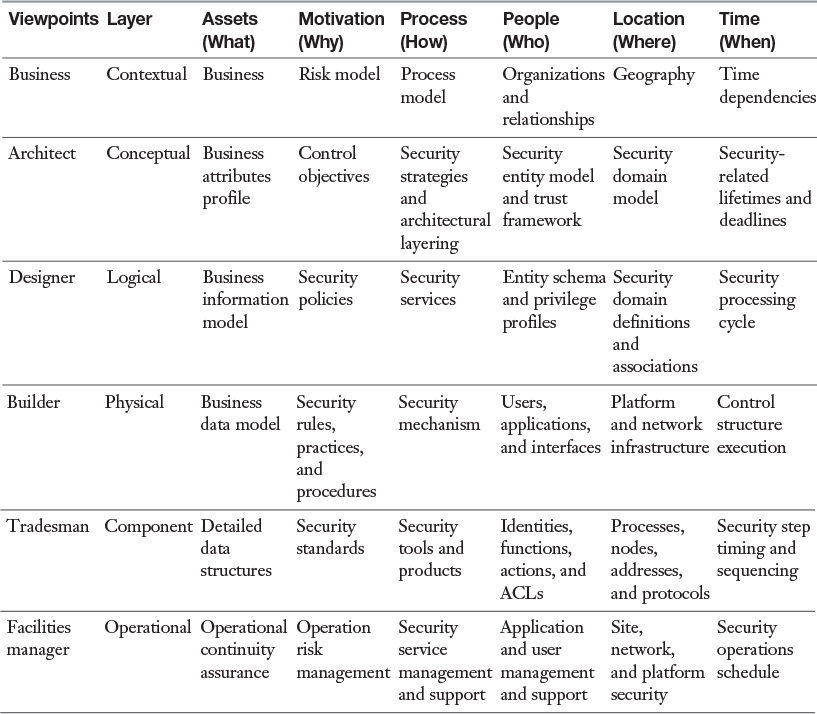
SABSA is an enterprise security architecture framework that is similar to the Zachman framework. It uses the six communication questions (What? Where? When? Why? Who? and How?) that intersect with six layers (operational, component, physical, logical, conceptual, and contextual). It is a risk-driven architecture. Table 7-6 provides the SABSA framework matrix.
Control Objectives for Information and Related Technology (CobiT)
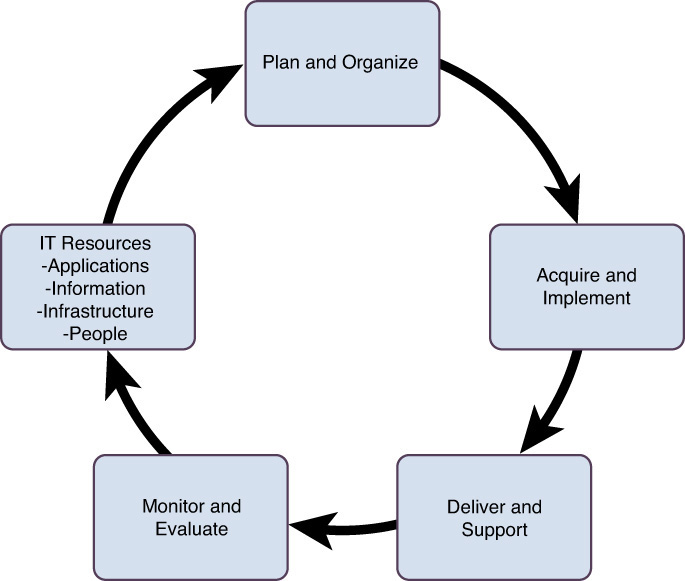
CobiT is a security controls development framework that uses a process model to subdivide IT into 4 domains: Plan and Organize (PO), Acquire and Implement (AI), Deliver and Support (DS), and Monitor and Evaluate (ME), as illustrated in Figure 7-1. These 4 domains are further broken down into 34 processes. CobiT aligns with the ITIL, PMI, ISO, and TOGAF frameworks and is mainly used in the private sector.
NIST SP 800-53
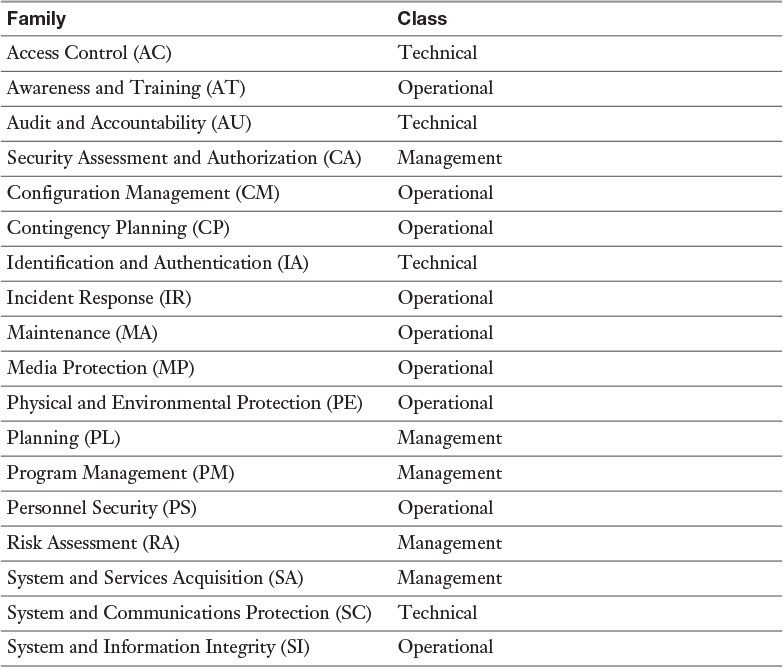
NIST SP 800-53 is a security controls development framework developed by the NIST body of the U.S. Department of Commerce. SP 800-53 divides the controls into three classes: technical, operational, and management. Each class contains control families or categories.
Note
Any published standards are under a constant review/revision process. Make sure that you as a security practitioner always remain up-to-date on any changes to published standards.
Table 7-7 lists the NIST SP 800-53 control families.
NIST 800-55 is an information security metrics framework that provides guidance on developing performance measuring procedures with a U.S. government viewpoint.
Continuous Improvement/Monitoring
Continuous improvement and monitoring of risk management is vital to any organization. To ensure continuous improvement, all changes to the enterprise must be tracked so that security professionals can assess the risks that those changes bring. Security controls should be configured to address the changes as close to the deployment of the changes as possible. For example, if your organization decides to upgrade a vendor application, security professionals must assess the application to see how it affects enterprise security.
Certain elements within the organization should be automated to help with the continuous improvements and monitoring, including audit log collection and analysis, antivirus and malware detection updates, and application and operating system updates.
Continuous monitoring involves change management, configuration management, control monitoring, and status reporting. Security professionals should regularly evaluate the enterprise security controls to ensure that changes do not negatively impact the enterprise.
Management should adopt a common risk vocabulary and must clearly communicate expectations. In addition, employees, including new hires, must be given training to ensure that they fully understand risk as it relates to the organization.
Business Continuity Planning
Continuity planning deals with identifying the impact of any disaster and ensuring that a viable recovery plan for each function and system is implemented. Its primary focus is how to carry out the organizational functions when a disruption occurs.
A business continuity plan (BCP) considers all aspects that are affected by a disaster, including functions, systems, personnel, and facilities. It lists and prioritizes the services needed, particularly the telecommunications and IT functions.
Business Continuity Scope and Plan
As you already know, creating a BCP is vital to ensuring that the organization can recover from a disaster or disruptive event. Several groups have established standards and best practices for business continuity. These standards and best practices include many common components and steps.
The following sections cover the personnel components, the project scope, and the business continuity steps that must be completed.
Personnel Components
Senior management is the most important personnel in the development of the BCP. Senior management support of business continuity and disaster recovery drives the overall organizational view of the process. Without senior management support, this process will fail.
Senior management sets the overall goals of business continuity and disaster recovery. A business continuity coordinator named by senior management should lead the BCP committee. The committee develops, implements, and tests the BCP and disaster recovery plan (DRP). The BCP committee should include a representative from each business unit. At least one member of senior management should be part of this committee. In addition, the organization should ensure that the IT department, legal department, security department, and communications department are represented because of the vital roles these departments play during and after a disaster.
With management direction, the BCP committee must work with business units to ultimately determine the business continuity and disaster recovery priorities. Senior business unit managers are responsible for identifying and prioritizing time-critical systems. After all aspects of the plans have been determined, the BCP committee should be tasked with regularly reviewing the plans to ensure that they remain current and viable. Senior management should closely monitor and control all business continuity efforts and publicly praise any successes.
After an organization gets into disaster recovery planning, other teams are involved.
Project Scope
To ensure that the development of the BCP is successful, senior management must define the BCP scope. A business continuity project with an unlimited scope can often become too large for the BCP committee to handle correctly. For this reason, senior management might need to split the business continuity project into smaller, more manageable pieces.
When considering the splitting of the BCP into pieces, an organization might want to split the pieces based on geographic location or facility. However, an enterprisewide BCP should be developed that ensures compatibility of the individual plans.
Business Continuity Steps
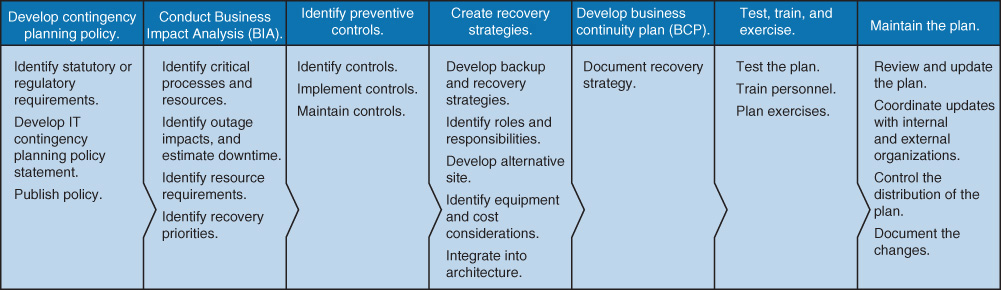
Many organizations have developed standards and guidelines for performing business continuity and disaster recovery planning. One of the most popular standards is NIST SP 800-34 Revision 1 (R1).
The following list summarizes the steps in SP 800-34 R1:
1. Develop contingency planning policy.
2. Conduct business impact analysis (BIA).
3. Identify preventive controls.
4. Create recovery strategies.
5. Develop business continuity plan (BCP).
6. Test, train, and exercise.
7. Maintain the plan.
A more detailed listing of the tasks included in SP 800-34 R1 is shown in Figure 7-2.
IT Governance
Within an organization, information security governance consists of several components that are used to provide comprehensive security management. Data and other assets should be protected mainly based on their value and sensitivity. Strategic plans guide the long-term security activities (3–5 years or more). Tactical plans achieve the goals of the strategic plan and are shorter in duration (6–18 months).
Because management is the most critical link in the computer security chain, management approval must be obtained as part of the first step in forming and adopting an information security policy. Senior management must take the following measures prior to the development of any organizational security policy:
1. Define the scope of the security program.
2. Identify all the assets that need protection.
3. Determine the level of protection that each asset needs.
4. Determine personnel responsibilities.
5. Develop consequences for noncompliance with the security policy.
By fully endorsing an organizational security policy, senior management accepts the ownership of an organization’s security. High-level polices are statements that indicate senior management’s intention to support security.
After senior management approval has been obtained, the first step in establishing an information security program is to adopt an organizational information security statement. The organization’s security policy comes from this statement. The security planning process must define how security will be managed, who will be responsible for setting up and monitoring compliance, how security measures will be tested for effectiveness, who is involved in establishing the security policy, and where the security policy is defined.
Security professionals must understand how information security components work together to form a comprehensive security plan. Information security governance components include:
![]() Policies
Policies
![]() Standards
Standards
![]() Baselines
Baselines
![]() Guidelines
Guidelines
![]() Procedures
Procedures
![]() Information classification and life cycle
Information classification and life cycle
Understanding these components is a starting place for applying your understanding of them in Chapter 8, “Security, Privacy Policies, and Procedures,” which covers developing and updating these components.
Policies
A security policy dictates the role of security as provided by senior management and is strategic in nature, meaning it provides the end result of security. Policies are defined in two ways: the level in the organization at which they are enforced and the category to which they are applied. Policies must be general in nature, meaning they are independent of a specific technology or security solution. Policies outline goals but do not give any specific ways to accomplish the stated goals. Each policy must contain an exception area to ensure that management will be able to deal with situations that might require exceptions.
Policies are broad and provide the foundation for development of standards, baselines, guidelines, and procedures, all of which provide the security structure. Administrative, technical, and physical access controls fill in the security and structure to complete the security program.
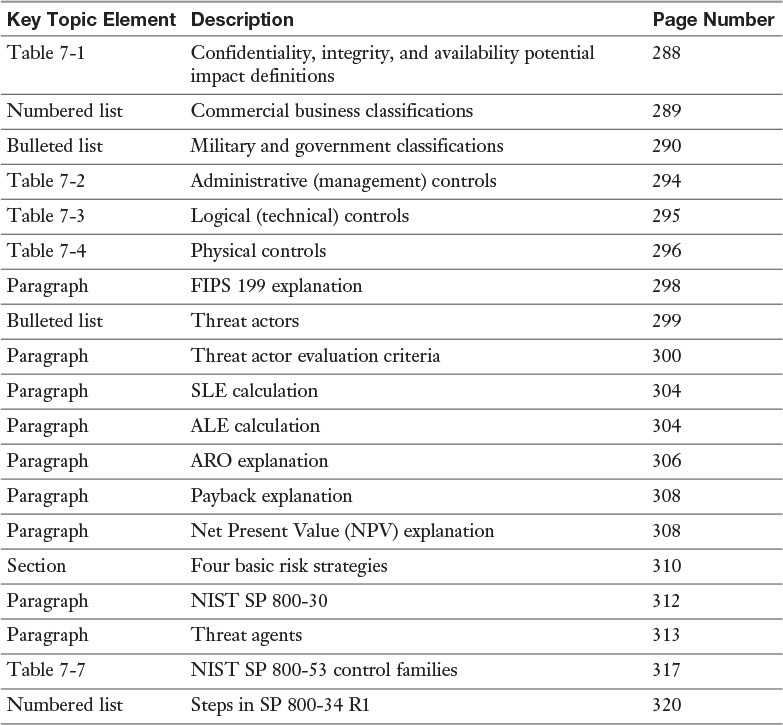
The policy levels used in information security are organizational security policies, system-specific security policies, and issue-specific security policies. The policy categories used in information security are regulatory security policies, advisory security policies, and informative security policies. The policies are divided as shown in Figure 7-3.
Organizational Security Policy
An organizational security policy is the highest-level security policy adopted by an organization. Business goals steer the organizational security policy. An organizational security policy contains general directions and should have the following components:
![]() Define overall goals of security policy.
Define overall goals of security policy.
![]() Define overall steps and importance of security.
Define overall steps and importance of security.
![]() Define security framework to meet business goals.
Define security framework to meet business goals.
![]() State management approval of policy, including support of security goals and principles.
State management approval of policy, including support of security goals and principles.
![]() Define all relevant terms.
Define all relevant terms.
![]() Define security roles and responsibilities.
Define security roles and responsibilities.
![]() Address all relevant laws and regulations.
Address all relevant laws and regulations.
![]() Identify major functional areas.
Identify major functional areas.
![]() Define compliance requirements and noncompliance consequences.
Define compliance requirements and noncompliance consequences.
An organizational security policy must be supported by all stakeholders and should have high visibility for all personnel and should be discussed regularly. In addition, it should be reviewed on a regular basis and revised based on the findings of the regular review. Each version of the policy should be maintained and documented with each new release.
System-Specific Security Policy
A system-specific security policy addresses security for a specific computer, network, technology, or application. This policy type is much more technically focused than an issue-specific security policy. It outlines how to protect the system or technology.
Issue-Specific Security Policy
An issue-specific security policy addresses specific security issues. Issue-specific policies include email privacy policies, virus checking policies, employee termination policies, no expectation of privacy policies, and so on. Issue-specific policies support the organizational security policy.
Policy Categories
Regulatory security policies address specific industry regulations, including mandatory standards. Examples of industries that must consider regulatory security policies include healthcare facilities, public utilities, and financial institutions.
Advisory security policies provide instruction on acceptable and unacceptable activities. In most cases, this policy is considered to be strongly suggested, not compulsory. This type of policy usually gives examples of possible consequences if users engage in unacceptable activities.
Informative security policies provide information on certain topics and act as an educational tool.
Standards
Standards describe how policies will be implemented within an organization. They are mandatory actions or rules that are tactical in nature, meaning they provide the steps necessary to achieve security. Just like policies, standards should be regularly reviewed and revised.
Baselines
A baseline is a reference point that is defined and captured to be used as a future reference. Although capturing baselines is important, using those baselines to assess the security state is just as important. Even the most comprehensive baselines are useless if they are never used.
Capturing a baseline at the appropriate point in time is also important. Baselines should be captured when a system is properly configured and fully updated. When updates occur, new baselines should be captured and compared to the previous baselines. At that time, adopting new baselines based on the most recent data might be necessary.
Guidelines
Guidelines are recommended actions that are much more flexible than standards, thereby providing allowance for circumstances that can occur. Guidelines provide guidance when standards do not apply.
Procedures
Procedures embody all the detailed actions that personnel are required to follow and are the closest to the computers and other devices. Procedures often include step-by-step lists on how policies, standards, and guidelines are implemented.
Exam Preparation Tasks
You have a couple of choices for exam preparation: the exercises here and the exam simulation questions on the CD-ROM.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 7-8 lists these key topics and the page number on which each is found.
Complete the Tables and Lists from Memory
Print a copy of CD-ROM Appendix C, “Memory Tables,” or at least the section for this chapter, and complete the tables and lists from memory. CD-ROM Appendix D, “Memory Tables Answer Key,” includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
redundant array of independent disks (RAID)
security requirements traceability matrix (SRTM)
annualized loss expectancy (ALE)
annualized rate of occurrence (ARO)
Sherwood Applied Business Security Architecture (SABSA)
Control Objectives for Information and Related Technology (CobiT)
organizational security policy
system-specific security policy
issue-specific security policy
Review Questions
1. You are analyzing a group of threat agents that includes hardware and software failure, malicious code, and new technologies. Which type of threat agents are you analyzing?
a. human
b. natural
c. environmental
d. technical
2. You have been asked to document the different threats to an internal file server. As part of that documentation, you need to include the monetary impact of each threat occurrence. What should you do?
a. Determine the ARO for each threat occurrence.
b. Determine the ALE for each threat occurrence.
c. Determine the EF for each threat occurrence.
d. Determine the SLE for each threat occurrence.
3. After analyzing the risks to your company’s web server, company management decides to implement different safeguards for each risk. For several risks, management chooses to avoid the risk. What do you need to do for these risks?
a. Determine how much risk is left over after safeguards have been implemented.
b. Terminate the activity that causes the risks or choose an alternative that is not as risky.
c. Pass the risk on to a third party.
d. Define the acceptable risk level the organization can tolerate and reduce the risks to that level.
4. You are currently engaged in IT security governance for your organization. You specifically provide instruction on acceptable and unacceptable activities for all personnel. What should you do?
a. Create an advisory security policy that addresses all these issues.
b. Create an NDA that addresses all these issues.
c. Create an informative security policy that addresses all these issues.
d. Create a regulatory security policy and system-specific security policy that address all these issues.
5. A security analyst is using the SCinformation system = [(confidentiality, impact), (integrity, impact), (availability, impact)] formula while performing risk analysis. What will this formula be used for?
a. to calculate quantitative risk
b. to calculate ALE
c. to calculate the aggregate CIA score
d. to calculate SLE
6. After experiencing several security issues in the past year, management at your organization has adopted a plan to periodically assess its information security awareness. You have been asked to lead this program. Which program are you leading?
a. security training
b. continuous monitoring
c. risk mitigation
d. threat identification
7. The chief information security officer (CISO) has asked you to prepare a report for management that includes the overall costs associated with running the organizational risk management process, including insurance premiums, finance costs, administrative costs, and any losses incurred. What are you providing?
a. ROI
b. SLE
c. TCO
d. NPV
8. While performing risk analysis, your team has come up with a list of many risks. Several of the risks are unavoidable, even though you plan to implement some security controls to protect against them. Which type of risk is considered unavoidable?
a. inherent risks
b. residual risks
c. technical risks
d. operational risks
9. A hacker gains access to your organization’s network. During this attack, he is able to change some data and access some design plans that are protected by a U.S. patent. Which security tenets have been violated?
a. confidentiality and availability
b. confidentiality and integrity
c. integrity and availability
d. confidentiality, integrity, and availability
10. An organization has a research server farm with a value of $12,000. The exposure factor for a complete power failure is 10%. The annualized rate of occurrence that this will occur is 5%. What is the ALE for this event?
a. $1,200
b. $12,000
c. $60