Chapter 12. Assessment Tools and Methods
This chapter covers the following topics:
![]() Assessment Tool Types: Topics covered include port scanners, vulnerability scanners, protocol analyzers, network enumerators, password crackers, fuzzers, HTTP interceptors, exploitation tools/frameworks, and passive reconnaissance and intelligence-gathering tools.
Assessment Tool Types: Topics covered include port scanners, vulnerability scanners, protocol analyzers, network enumerators, password crackers, fuzzers, HTTP interceptors, exploitation tools/frameworks, and passive reconnaissance and intelligence-gathering tools.
![]() Assessment Methods: This section describes assessment methods such as vulnerability assessments; malware sandboxing; memory dumping and runtime debugging; penetration testing; black box, white box, and gray box testing; reconnaissance; fingerprinting; code reviews; and social engineering.
Assessment Methods: This section describes assessment methods such as vulnerability assessments; malware sandboxing; memory dumping and runtime debugging; penetration testing; black box, white box, and gray box testing; reconnaissance; fingerprinting; code reviews; and social engineering.
This chapter covers CAS-002 objective 3.3.
Before it can secure a network, an organization must determine where security weaknesses exist. The only way to do this is to make an honest assessment of the current state of the network. Considering the multitude of types of weaknesses that can exist in a network, multiple methods of assessment should be used. This chapter discusses specific tools used for assessment and the weakness each is designed to reveal. The chapter also discusses methods for ferretting out other types of security weaknesses that cannot be discovered with those tools.
Foundation Topics
Assessment Tool Types
While it may seem to be an overwhelming job to maintain the security of a network, you can use many tools to do the job. Unfortunately, every tool that has a legitimate use may also have an illegitimate use. Hackers use these tools to discover, penetrate, and control our networks, but you can use the same tools to ensure that attacks do not succeed. The following sections discuss some of the most common assessment tools.
Port Scanners
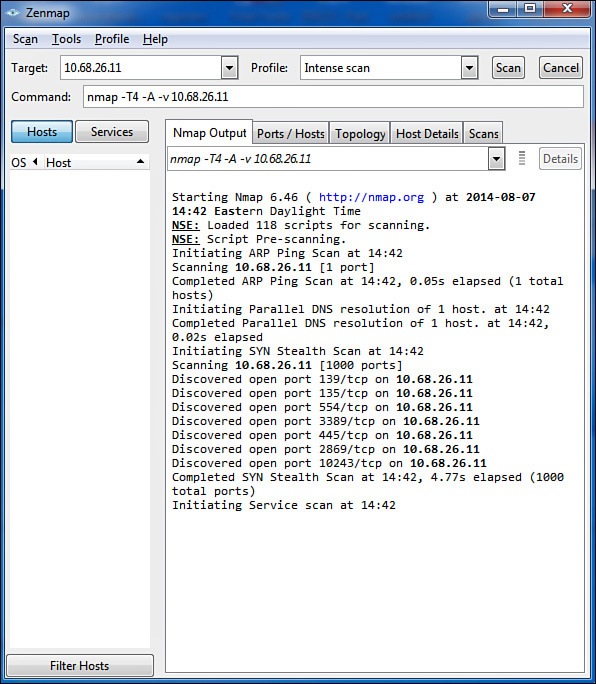
Internet Control Message Protocol (ICMP) messages can be used to scan a network for open ports. Open ports indicate services that may be running and listening on a device that may be susceptible to attack. An ICMP, or port scanning, attack basically pings every address and port number combination and keeps track of which ports are open on each device as the pings are answered by open ports with listening services and not answered by closed ports. One of the most widely used port scanners is Network Mapper (Nmap), a free and open source utility for network discovery and security auditing. Figure 12-1 shows the output of a scan using Zenmap, an Nmap security scanner GUI. Starting in line 12 of the output shown in this figure you can see that the device at 10.68.26.11 has seven ports open:
Discovered open port 139/tcp on 10.68.26.11
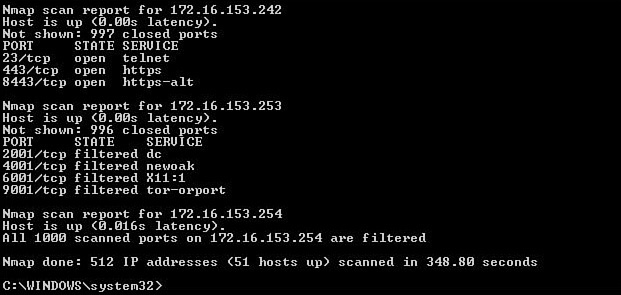
Figure 12-2 shows output from the command-line version of Nmap. You can see in this figure that a ping scan of an entire network just completed. From it you can see that the computer at 172.16.153.242 has three ports open: 23, 443, and 8443. However, the computer at 172.16.153.253 has no open ports. The term filtered in the output means that the ports are not open. To obtain this output, the command Nmap 172.16.153.0/23 was executed, instructing the scan to include all computers in the 172.16.153.0/23 network.
In a scenario where you need to determine what applications and services are running on the devices in your network, a port scanner would be appropriate.
Vulnerability Scanners
Whereas a port scanner can discover open ports, a vulnerability scanner can probe for a variety of security weaknesses, including misconfigurations, out-of-date software, missing patches, and open ports. One of the most widely used vulnerability scanners is Nessus, a proprietary tool developed by Tenable Network Security. It is free of charge for personal use in a non-enterprise environment. Figure 12-3 shows a partial screenshot of Nessus. By default, Nessus starts by listing at the top of the output the issues found on a host that are rated with the highest severity.
For the computer scanned in Figure 12-3, we see that there is one high-severity issue (the default password for a Firebird database located on the host), and there are five medium-level issues, including two SSL certificates that cannot be trusted and a remote desktop man-in-the-middle attack vulnerability.
When security weaknesses in a network go beyond open ports—such as when you have cases of weak passwords, misconfigurations, and missing updates—a vulnerability scanner would be the appropriate tool.
Protocol Analyzer
Sniffing is the process of capturing packets for analysis; sniffing used maliciously is referred to as eavesdropping. Sniffing occurs when an attacker attaches or inserts a device or software into the communication medium to collect all the information transmitted over the medium. Sniffers, called protocol analyzers, collect raw packets from the network; both legitimate security professionals and attackers use them. The fact that a sniffer does what it does without transmitting any data to the network is an advantage when the tool is being used legitimately and a disadvantage when it is being used against you (because you cannot tell you are being sniffed). Organizations should monitor and limit the use of sniffers. To protect against their use, you should encrypt all traffic on the network.
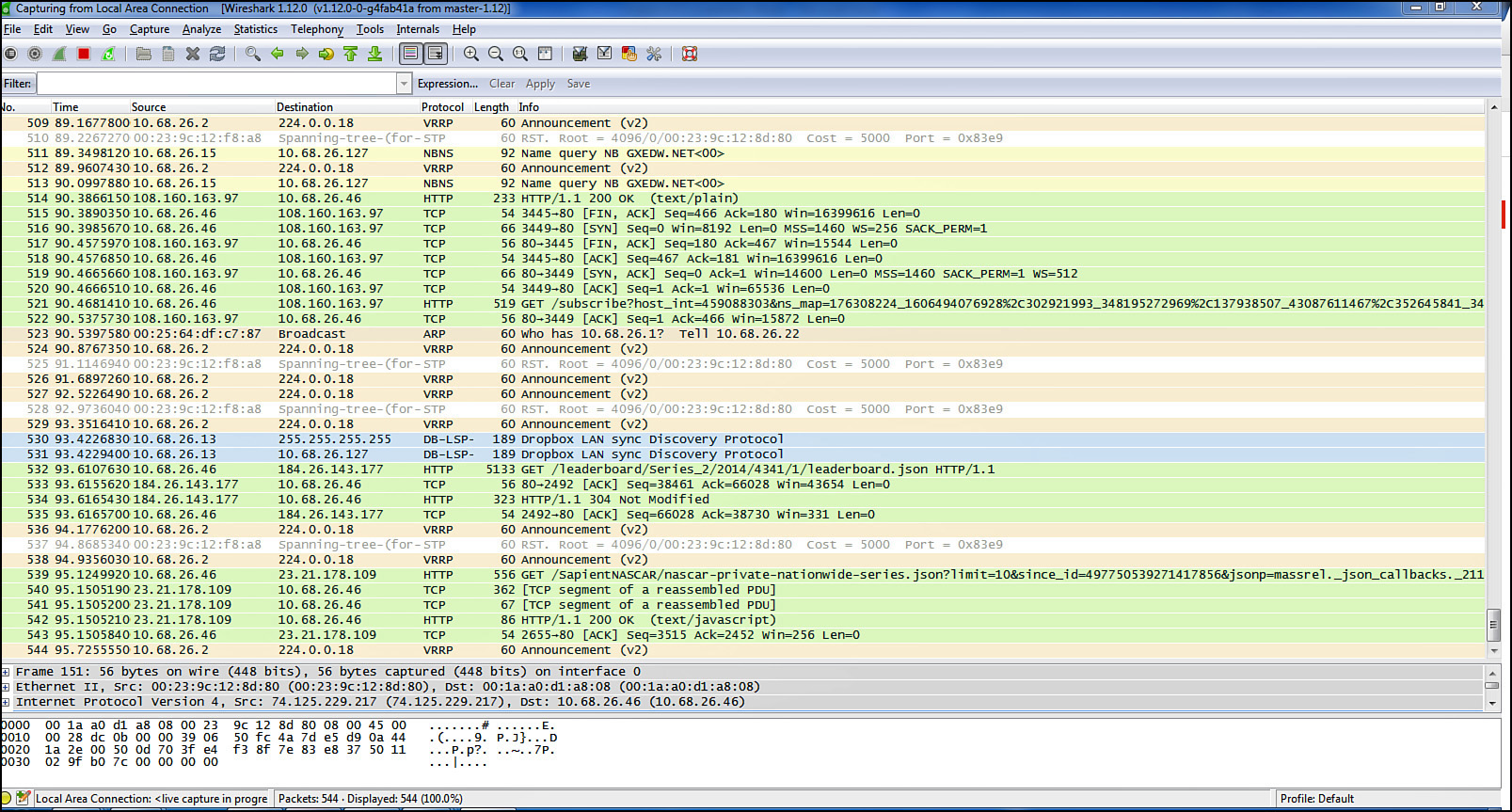
One of the most widely used sniffers is Wireshark. It captures raw packets off the interface on which it is configured and allows you to examine each packet. If the data is unencrypted, you will be able to read the data. Figure 12-4 show an example of Wireshark in use.
In the output shown in Figure 12-4, each line represents a packet captured on the network. You can see the source IP address, the destination IP address, the protocol in use, and the information in the packet. For example, line 511 shows a packet from 10.68.26.15 to 10.68.16.127, which is a NetBIOS name resolution query. Line 521 shows an HTTP packet from 10.68.26.46 to a server at 108.160.163.97. Just after that, you can see that the server sending an acknowledgement back. To try to read the packet, you would click on the single packet. If the data were clear text, you would be able to read and analyze it. So you can see how an attacker could acquire credentials and other sensitive information.
Protocol analyzers can be of help whenever you need to see what is really happening on your network. For example, say you have a security policy that says certain types of traffic should be encrypted. But you are not sure that everyone is complying with this policy. By capturing and viewing the raw packets on the network, you would be able to determine whether they are.
Network Enumerator
Network enumerators scan the network and gather information about users, groups, shares, and services that are visible—a process sometimes referred to as device fingerprinting. Network enumerators use protocols such as ICMP and SNMP to gather information. WhatsUp Gold is an example of such software. As you can see in Figure 12-5, it not only identifies issues with hosts and other network devices but allows you to organize and view the hosts by problem. It is currently set to show all devices. To see all devices with missing credentials, you could select the Devices Without Credentials folder in the tree view on the left.
As it is currently set, the output in Figure 12-5 shows all devices. In the details pane, you can see each device listed by IP address and the type of device it is. For example, the highlighted device is a Cisco switch with the IP address 192.198.205.2.
In situations where you need to survey the security posture of all computers in the network without physically visiting each computer, you can use a network enumerator to find that information and organize it in helpful ways.
Password Cracker
Password crackers are programs that do what their name implies: They attempt to identify passwords. These programs can be used to mount several types of password threats, including dictionary attacks and brute-force attacks.
In a dictionary attack, an attacker uses a dictionary of common words to discover passwords. An automated program uses the hash of the dictionary word and compares this hash value to entries in the system password file. While the program comes with a dictionary, attackers also use extra dictionaries that are found on the Internet. To protect against these attacks, you should implement a security rule which says that a password must not be a word found in the dictionary. Creating strong passwords is covered in Chapter 17, “Authentication and Authorization Technologies.”
Brute-force attacks are more difficult to perform because they work through all possible combinations of numbers and characters. These attacks are also very time-consuming.
The best countermeasures against password threats are to implement complex password policies, require users to change passwords on a regular basis, employ account lockout policies, encrypt password files, and use password-cracking tools to discover weak passwords.
One of the most well-known password cracking programs is Cain and Abel, which can recover passwords by sniffing the network; cracking encrypted passwords using dictionary, brute-force, and cryptanalysis attacks; recording VoIP conversations; decoding scrambled passwords; revealing password boxes; uncovering cached passwords; and analyzing routing protocols. Figure 12-6 shows sample output of this tool. As you can see, an array of attacks can be performed on each located account. This example shows a scan of the local machine for user accounts in which the program has located three accounts: Admin, Sharpy, and JSmith. By right-clicking on the Admin account, you can use the program to perform a brute-force attack on that account—or a number of other attacks.
Another example of a password cracker is John the Ripper. It can work in UNIX/Linux as well as Mac OS systems. It detects weak UNIX passwords, though it supports hashes for many other platforms as well. John the Ripper is available in three versions: an official free version, a community-enhanced version (with many contributed patches but not as much quality assurance), and an inexpensive pro version.
If you are having difficulty enforcing strong or complex passwords and you need to identify the weak password in the network, you could use a password cracker to find out which passwords are weak and possibly also crack them. If determining password security is time critical, you should upload the password file to one of your more capable machines (a cluster would be even better) and run the password cracker on that platform. This way you could take advantage of the additional resources to perform the audit more quickly.
Fuzzer
Fuzzers are software tools that find and exploit weaknesses in web applications, a process called fuzzing. They operate by injecting semi-random data into the program stack and then detecting bugs that result. They are easy to use, but one of the limitations is that they tend to find simpler bugs rather than some of the more complex ones. The Open Web Application Security Project (OWASP), an organization that focuses on improving software security, recommends several specific tools, including JBroFuzz and WSFuzzer. HTTP-based SOAP services are the main target of WSFuzzer.
A scenario in which a fuzzer would be used is during the development of a web application that will handle sensitive data. The fuzzer would help you to determine whether the application is properly handling error exceptions. For example, say that you have a web application that is still undergoing testing, and you notice that when you mistype your credentials in the login screen of the application, the program crashes, and you are presented with a command prompt. If you wanted to reproduce the issue for study, you could run an online fuzzer against the login screen.
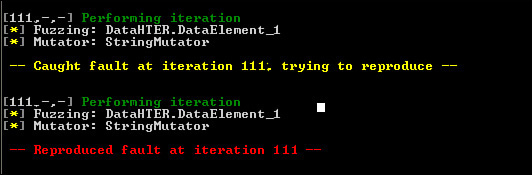
Figure 12-7 shows the output of a fuzzer called Peach. It is fuzzing the application with a mutator called StringMutator that continually alters the input over and over. You can see in this output that some input to the tool has caused a crash. Peach has verified the fault by reproducing it. It will send more detail to a log that you can read to understand exactly what string value caused the crash.
HTTP Interceptor
HTTP interceptors intercept web traffic between a browser and a website. They permit actions that the browser would not. For example, an HTTP interceptors may allow the input of 300 characters, while the browser may enforce a limit of 50. These tools allow you to test of what would occur if a hacker were able to circumvent the limit imposed by the browser. An HTTP interceptor performs like a web proxy in that it monitors the traffic in both directions.
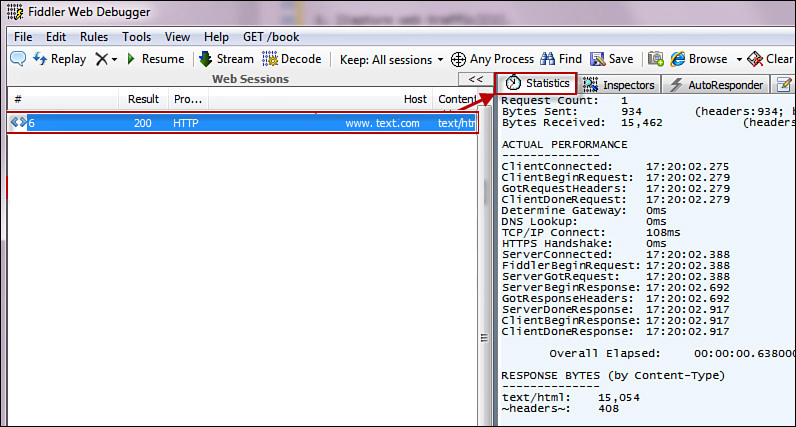
Some examples of HTTP interceptors are Burp Suite and Fiddler. Fiddler, a Windows tool, can also be configured to test the performance of a website, as shown in Figure 12-8.
The output in Figure 12-8 shows the connection statistics for a download from text.com. In the panel on the right, you see the elapsed time spent on each step in the process.
HTTP interceptors along with fuzzers should be a part of testing web applications. They can also be used to test the proper validation of input.
Exploitation Tools/Frameworks
Exploitation tools, sometimes called exploit kits, are groups of tools used to exploit security holes. They are created for a wide variety of applications. These tools attack an application in the same way a hacker would, and so they can be used for good and evil. Some are free, while others, such as Core Impact, are quite expensive.
An exploit framework provides a consistent environment to create and run exploit code against a target. The three most widely used frameworks are:
![]() Metasploit: This is an open source framework that, at this writing, ships with 566 exploits.
Metasploit: This is an open source framework that, at this writing, ships with 566 exploits.
![]() CANVAS: Sold on a subscription model, CANVAS ships with more than 400 exploits.
CANVAS: Sold on a subscription model, CANVAS ships with more than 400 exploits.
![]() IMPACT: This commercially available tool uses agent technology that helps an attacker gather information on the target.
IMPACT: This commercially available tool uses agent technology that helps an attacker gather information on the target.
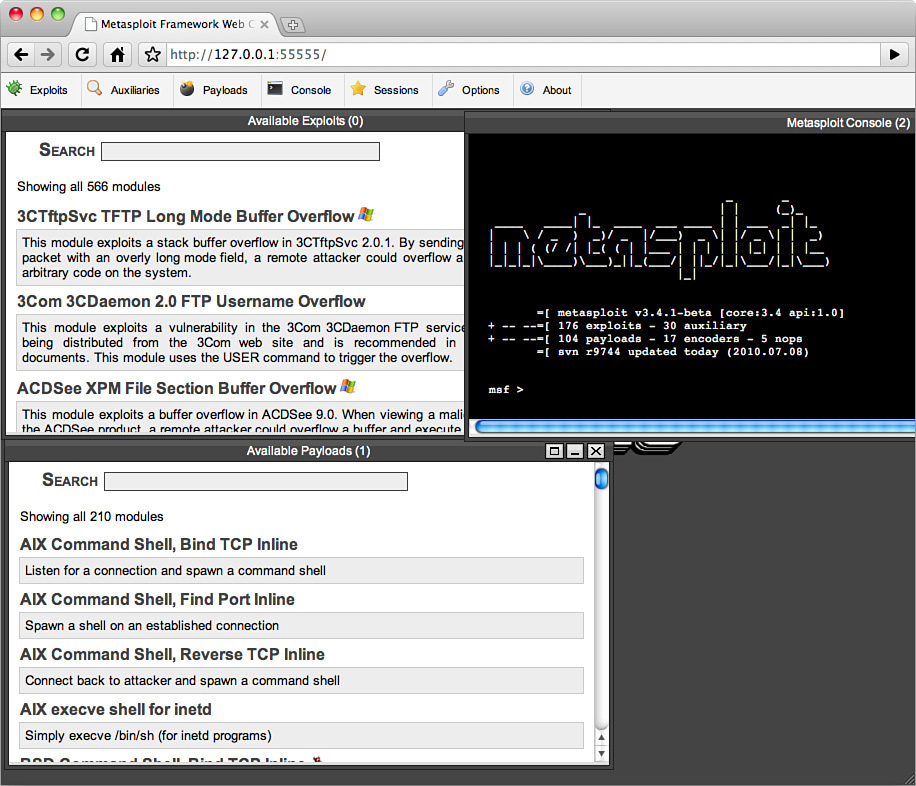
Figure 12-9 shows the web interface of Metasploit. The attacker (or the tester) selects an exploit from the top panel and then a payload from the bottom. Once the attack is launched, the tester can use the console to interact with the host. Using these exploitation frameworks should be a part of testing applications for security holes.
Passive Reconnaissance and Intelligence-Gathering Tools
While active tools can be used to probe both applications and networks for security weaknesses, they are not the only source of helpful information available to hackers. In many cases, passive tools enhance the effectiveness of active tools by providing helpful information, such as details about network configurations or general information concerning product releases, unpublicized projects, and details about key players in the organization. The following sections discuss some of the most common methods of passive reconnaissance.
Social Media
Organizations are increasingly using social media to reach out and connect with customers and the public in general. While the use of Twitter, Facebook, and LinkedIn can enhance engagement with customers, build brands, and communicate information to the rest of the world, these social media sites can also inadvertently expose proprietary information. Specifically, some of the dangers presented by the use of social media are:
![]() Mobile apps on company devices: We can’t completely blame social media for the use of mobile applications on company devices, but the availability and ease with which social media and other types of mobile apps can be downloaded and installed presents an increasing danger of malware.
Mobile apps on company devices: We can’t completely blame social media for the use of mobile applications on company devices, but the availability and ease with which social media and other types of mobile apps can be downloaded and installed presents an increasing danger of malware.
![]() Unwarranted trust in social media: Trade secrets and company plans may be innocently disclosed to a friend with the misplaced expectation of privacy. This is complicated by the poorly understood and frequently changing security and privacy settings of social media sites.
Unwarranted trust in social media: Trade secrets and company plans may be innocently disclosed to a friend with the misplaced expectation of privacy. This is complicated by the poorly understood and frequently changing security and privacy settings of social media sites.
![]() Malware in the social media sites: Malicious code may be lurking inside advertisements and third-party applications. Hackers benefit from the manner in which users repost links, thereby performing the distribution process for the hackers.
Malware in the social media sites: Malicious code may be lurking inside advertisements and third-party applications. Hackers benefit from the manner in which users repost links, thereby performing the distribution process for the hackers.
![]() Lack of policies: Every organization should have a social media policy that expressly defines the way in which users may use social media. A social media director or coordinator should be designated, and proper training should be delivered that defines what users are allowed to say on behalf of the company.
Lack of policies: Every organization should have a social media policy that expressly defines the way in which users may use social media. A social media director or coordinator should be designated, and proper training should be delivered that defines what users are allowed to say on behalf of the company.
The best way to prevent information leaks through social media that can be useful in attacking your network is to adopt a social media policy that defines what users are allowed to say on behalf of the company in social media posts.
Whois
Whois is a protocol used to query databases that contain information about the owners of Internet resources, such as domain names, IP address blocks, and autonomous system (AS) numbers (used to identify private Border Gateway Protocol (BGP) networks on the Internet). This information provides a treasure trove of information that can enhance attacks on a network.
While originally a command-line interface application, Whois now also exists in web-based tools. Although law enforcement organizations in the United States claim that Whois is an important tool for investigating violations of spamming and vishing, the Internet Corporation for Assigned Names and Numbers (ICANN) has called for scrapping the system and replacing it with one that keeps information secret from most Internet users and discloses information only for “permissible” reasons.
Some organizations use third-party privacy services to remove their information from the Whois database. Although this can be done, it may leave the general public wondering what you have to hide. It may make them less likely to do business with you. So when considering our options, you should balance the pros and cons.
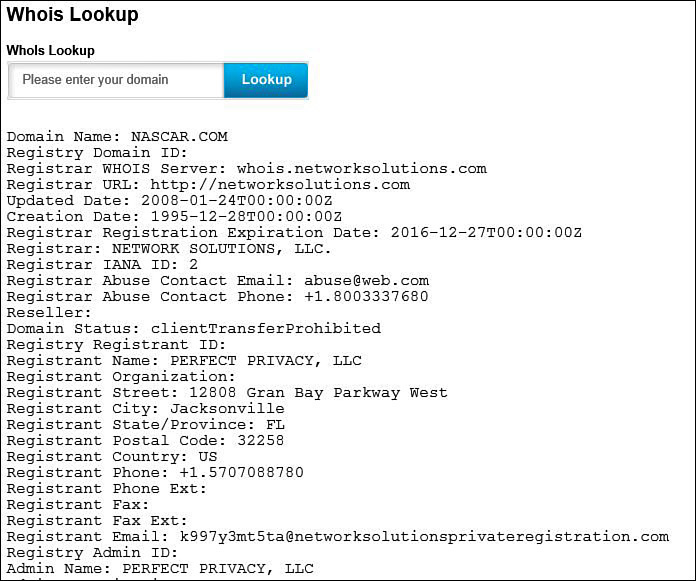
Figure 12-10 shows a part of the output of a domain name search in Whois. As you can see, you can obtain quite a bit of information about an organization by using Whois.
Routing Tables
Routing occurs at layer 3 of the OSI model. This is also the layer at which IP operates and where the source and destination IP addresses are placed in the packet. Routers are devices that transfer traffic between systems in different IP networks. When computers are in different IP networks, they cannot communicate unless there is a router available to route the packets to the other networks.
Routers use routing tables to hold information about the paths to other networks. These tables can be populated several ways: Administrators can manually enter these routes, or dynamic routing protocols can allow the routers to exchange routing tables and routing information. Manual configuration, also called static routing, has the advantage of avoiding the additional traffic created by dynamic routing protocols and allows for precise control of routing behavior; however, it requires manual intervention when link failures occur. Dynamic routing protocols create traffic but can react to link outages and reroute traffic without manual intervention.
From a security standpoint, routing protocols introduce the possibility that routing update traffic may be captured, allowing a hacker to gain valuable information about the layout of the network. Moreover, Cisco devices (perhaps the most widely used) also use a proprietary layer 2 protocol by default called Cisco Discovery Protocol (CDP), which they use to inform each other about their capabilities. If CDP packets are captured, additional information can be obtained that can be helpful in mapping the network in preparation for an attack.
Hackers can also introduce rogue routers into a network and perform a routing table update or exchange with a legitimate company router. Not only can a hacker do this to learn the routes and general layout of the network, he can also do it to pollute the routing table with incorrect routes that may enhance an attack.
The following is a sample of a routing table before it is compromised:
Source Network Next hop Exit interface
O 10.110.0.0 [110/5] via 10.119.254.6, 0:01:00, Ethernet2
O 10.67.10.0 [110/128] via 10.119.254.244, 0:02:22, Ethernet2
O 10.68.132.0 [110/5] via 10.119.254.6, 0:00:59, Ethernet2
O 10.130.0.0 [110/5] via 10.119.254.6, 0:00:59, Ethernet2
O 10.128.0.0 [110/128] via 10.119.254.244, 0:02:22, Ethernet2
O 10.129.0.0 [110/129] via 10.119.254.240, 0:02:22, Ethernet2
The routing table shows the remote networks to which the router has routes. The first column above shows the source of the routing information. In this case, the router sees the O in the first column and knows about networks from the Open Shortest Path First (OSPF) protocol. The second column is the remote network, the third column shows the next-hop IP address to reach that network (another router), and the last column is the local exit interface on the router.
Once the hacker has convinced the local router to exchange routing information and polluted the local routing table, it looks like this:
O 10.110.0.0 [110/5] via 10.119.254.6, 0:01:00, Ethernet2
O 10.67.10.0 [110/128] via 10.119.254.244, 0:02:22, Ethernet2
O 10.68.132.0 [110/5] via 10.119.254.6, 0:00:59, Ethernet2
O 10.130.0.0 [110/5] via 10.119.254.6, 0:00:59, Ethernet2
O 10.128.0.0 [110/128] via 10.119.254.244, 0:02:22, Ethernet2
O 10.129.0.0 [110/129] via 10.119.254.178, 0:02:22, Ethernet2
Look at the route to the 10.129.0.0 network. It is now routing to the IP address 10.119.254.178, which is the address of the hacker’s router. From there, the hacker can direct all traffic destined to a secure server at 10.119.154.180 to a duplicate server at 10.119.154.181 that he controls. The hacker can then collect names and passwords for the real secure server.
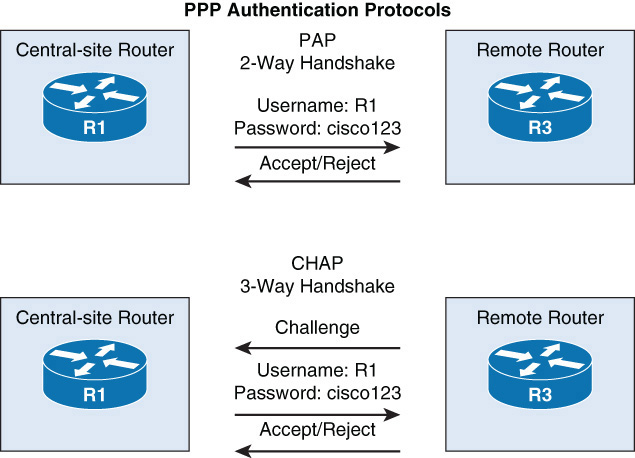
To prevent such attacks, routers should be configured with authentication so that they identify and authenticate any routers with which they exchange information. Routers can be configured to authenticate one another if the connection between them has been configured to use Point-to-Point Protocol (PPP) encapsulation. PPP is a layer 2 protocol that is simple to enable on a router interface with the command encapsulation ppp. Once enabled, it makes use of two types of authentication: PAP and CHAP.
Password Authentication Protocol (PAP) passes a credential in cleartext. A better alternative is Challenge-Handshake Authentication Protocol (CHAP), which never passes the credentials across the network. The CHAP process is as follows:
1. The local router sends a challenge message to the remote router.
2. The remote node responds with a value calculated using an MD5 hash salted with the password.
3. The local router verifies the hash value with the same password, thus ensuring that the remote router knows the password without sending the password.
Figure 12-11 compares the two operations.
Assessment Methods
A variety of assessment methods can be used to identify security weaknesses. While some involve determining network shortcomings, many others focus on insecure web server and application configurations. The following sections cover assessment methods, with a focus on a conceptual approach rather than specific tools.
Vulnerability Assessment
Regardless of the components under study (network, application, database, etc.), any vulnerability assessment’s goal is to highlight issues before someone either purposefully or inadvertently leverages the issue to compromise the component. The design of the assessment process has a great impact on its success. Before an assessment process is developed, the following goals of the assessment need to be identified:
![]() The relative value of the information that could be discovered through the compromise of the components under assessment: This helps to identify the number and type of resources that should be devoted to the issue.
The relative value of the information that could be discovered through the compromise of the components under assessment: This helps to identify the number and type of resources that should be devoted to the issue.
![]() The specific threats that are applicable to the component: For example, a web application would not be exposed to the same issues as a firewall, due to the differences in their operation and positions in the network.
The specific threats that are applicable to the component: For example, a web application would not be exposed to the same issues as a firewall, due to the differences in their operation and positions in the network.
![]() The mitigation strategies that could be deployed to address issues that might be found: Identifying common strategies may suggest issues that weren’t anticipated initially. For example, if you were doing a vulnerability test of your standard network operating system image, you should anticipate issues you might find and identify what technique you will use to address each.
The mitigation strategies that could be deployed to address issues that might be found: Identifying common strategies may suggest issues that weren’t anticipated initially. For example, if you were doing a vulnerability test of your standard network operating system image, you should anticipate issues you might find and identify what technique you will use to address each.
A security analyst who will be performing a vulnerability assessment needs to understand the systems and devices that are on the network and the jobs they perform. Having this information will ensure that the analyst can assess the vulnerabilities of the systems and devices based on the known and potential threats to the systems and devices.
After gaining knowledge regarding the systems and device, a security analyst should examine existing controls in place and identify any threats against those controls. The security analyst will then use all the information gathered to determine which automated tools to use to analyze for vulnerabilities. Once the vulnerability analysis is complete, the security analyst should verify the results to ensure that they are accurate and then report the findings to management, with suggestions for remedial action. With this information in hand, threat modeling should be carried out to identify the threats that could negatively affect systems and devices and the attack methods that could be used.
In some situations, a vulnerability management system may be indicated. A vulnerability management system is software that centralizes and to a certain extent automates the process of continually monitoring and testing the network for vulnerabilities. Such a system can scan the network for vulnerabilities, report them, and in many cases remediate the problem without human intervention. While a vulnerability management system is a valuable tool to have, these systems, regardless of how sophisticated they may be, cannot take the place of vulnerability and penetration testing performed by trained professionals.
Keep in mind that after a vulnerability assessment is complete, its findings are a snapshot. Even if no vulnerabilities are found, the best statement to describe the situation is that there are no known vulnerabilities at this time. It is impossible to say with certainty that a vulnerability will not be discovered in the future.
Malware Sandboxing
Malware sandboxing is the process of confining malware to a protected environment until it can be studied, understood, and mitigated. Malware sandboxing aims at detecting malware code by running it in a computer-based system to analyze it for behavior and traits indicative of malware. One of its goals is to spot zero-day malware—that is, malware that has not yet been identified by commercial antimalware systems and therefore does not yet have a cure.
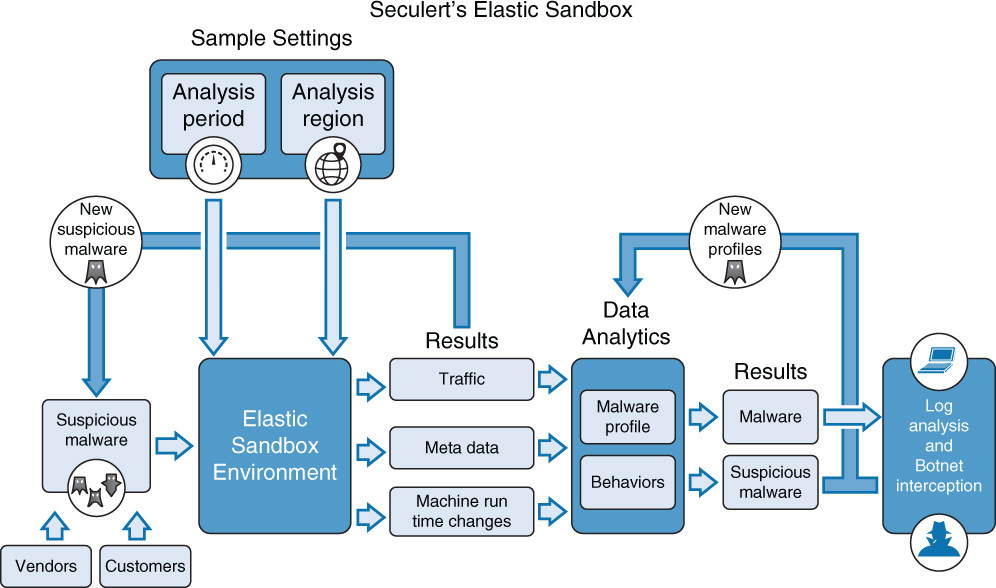
One example of commercial malware sandboxing is Cuckoo, an open source automated malware analysis system. Another example of a cloud-based solution is Seculert’s Elastic Sandbox. Customers, partners, vendors, and the malware experts at Seculert upload suspicious executables to the Elastic Sandbox, using an online platform or API. Within the sandbox, the behavior of the code is studied, including network communications, metadata in the network traffic, and host runtime changes. Using analytics, all the available information is processed to determine whether the code under investigation is malicious.
While this is only one example of how malware sandboxing works, the Elastic sandboxing process is depicted in Figure 12-12. Vendors and customers can use this sandbox environment to test malware and benefit from the results of all in the analysis.
In summary, malware sandboxing can be used to analyze and identify malware that has not been identified by the major commercial antimalware vendors.
Memory Dumping, Runtime Debugging
Many penetration testing tools perform an operation called a core dump or memory dump. Applications store information in memory and can include sensitive data, passwords, and usernames and encryption keys. Hackers can use memory-reading tools to analyze the entire memory content used by an application. Any vulnerability testing should take this into consideration and utilize the same tools to identify any issues in the memory of an application.
Examples of memory reading tools are:
![]() Memdump: This free tool runs on Windows, Linux, and Solaris. It simply creates a bit-by-bit copy of the volatile memory on a system.
Memdump: This free tool runs on Windows, Linux, and Solaris. It simply creates a bit-by-bit copy of the volatile memory on a system.
![]() KnTTools: This memory acquisition and analysis tool used with Windows systems captures physical memory and stores it to a removable drive or sends it over the network to be archived on a separate machine.
KnTTools: This memory acquisition and analysis tool used with Windows systems captures physical memory and stores it to a removable drive or sends it over the network to be archived on a separate machine.
![]() FATKit: This popular memory forensics tool automates the process of extracting interesting data from volatile memory. FATKit has the ability to visualize the objects it finds to help the analyst understand the data that the tool was able to find.
FATKit: This popular memory forensics tool automates the process of extracting interesting data from volatile memory. FATKit has the ability to visualize the objects it finds to help the analyst understand the data that the tool was able to find.
Runtime debugging, on the other hand, is the process of using a programming tool to not only identify syntactic problems in code but also discover weaknesses that can lead to memory leaks and buffer overflows. Runtime debugging tools operate by examining and monitoring the use of memory. These tools are specific to the language in which the code was written.
Table 12-1 shows examples of runtime debugging tools and the operating systems and languages for which they can be used.
Memory dumping should be used to determine what a hacker might be able to learn if she were able to cause a memory dump. Runtime debugging would be the correct approach for discovering syntactic problems in an application’s code or to identify other issues, like memory leaks or potential buffer overflows.
Penetration Testing
A penetration test (often called a pentest) is designed to simulate an attack on a system, a network, or an application. Its value lies in its potential to discover security holes that may have gone unnoticed. It differs from a vulnerability test in that it attempts to exploit vulnerabilities rather than simply identify them. Nothing places the focus on a software bug like the exposure of critical data as a result of the bug.
In many cases, one of the valuable pieces of information that come from these tests is the identification of single operations that, while benign on their own, create security problems when used in combination. These tests can be made more effective when utilized with a framework like Metasploit or CANVAS (discussed earlier in this chapter).
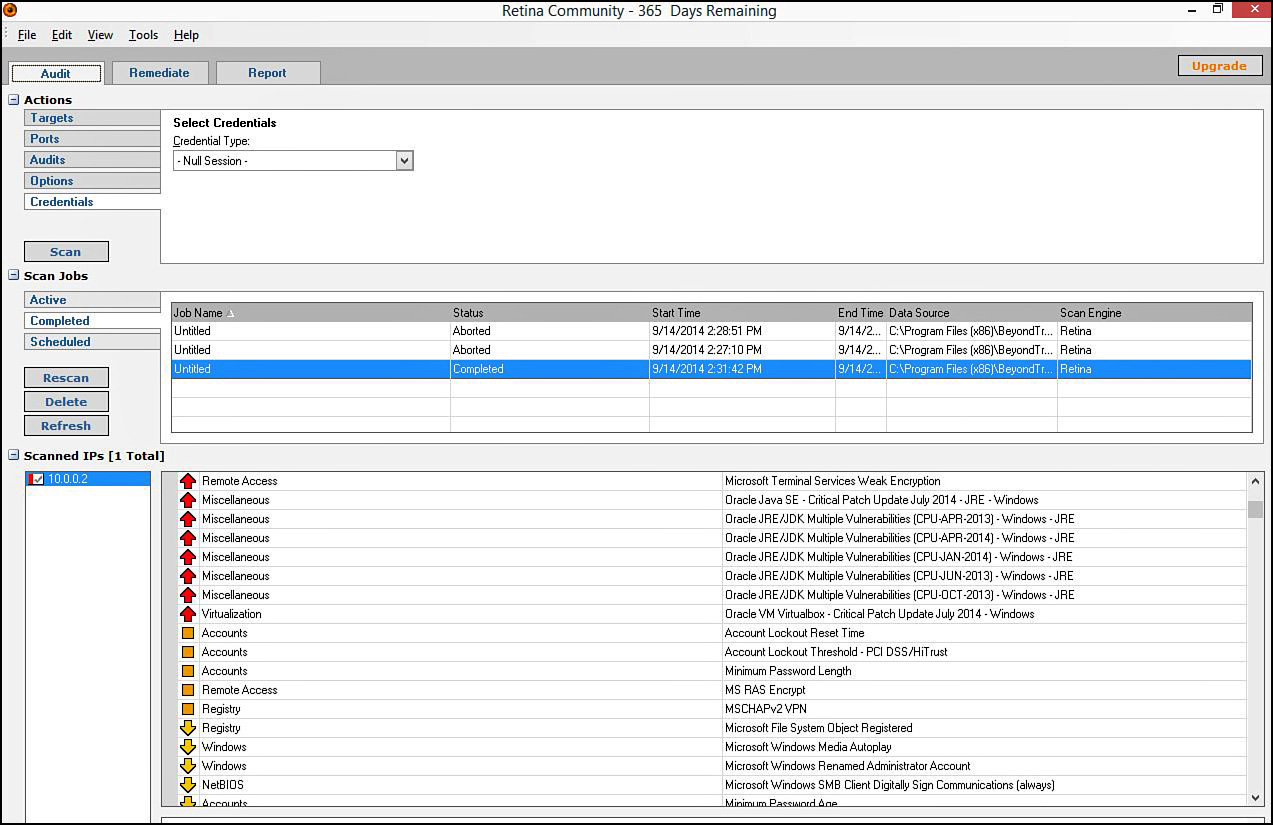
Penetration testing should be an operation that occurs at regular intervals, and its frequency should be determined by the sensitivity of the information on the network. An example of a pentest tool is Retina. Figure 12-13 shows the output of scanning a single device. In this output, you can see that the tool has identified eight serious problems (indicated by the upward-pointing arrows): weak encryption in Terminal Services, and six weaknesses related to Oracle, and one weakness related to a virtualization product on the machine called Oracle VirtualBox.
The steps in performing a penetration test are as follows:
1. Document information about the target system or device.
2. Gather information about attack methods against the target system or device.
3. Identify the known vulnerabilities of the target system or device.
4. Execute attacks against the target system or device to gain user and privileged access.
5. Document the results of the penetration test and report the findings to management, with suggestions for remedial action.
Both internal and external tests should be performed. Internal tests occur from within the network, while external tests originate outside the network and target the servers and devices that are publicly visible.
Strategies for penetration testing are based on the testing objectives defined by the organization. The strategies that you should be familiar with as a CASP candidate include the following:
![]() Blind test: The testing team is provided with limited knowledge of the network systems and devices and performs the test using publicly available information only. The organization’s security team knows that an attack is coming. This test requires more effort from the testing team.
Blind test: The testing team is provided with limited knowledge of the network systems and devices and performs the test using publicly available information only. The organization’s security team knows that an attack is coming. This test requires more effort from the testing team.
![]() Double-blind test: This test is like a blind test, except the organization’s security team does not know that an attack is coming. This test usually requires equal effort from both the testing team and the organization’s security team.
Double-blind test: This test is like a blind test, except the organization’s security team does not know that an attack is coming. This test usually requires equal effort from both the testing team and the organization’s security team.
![]() Target test: Both the testing team and the organization’s security team are given maximum information about the network and the type of test that will occur. This is the easiest test to complete but does not provide a full picture of the organization’s security.
Target test: Both the testing team and the organization’s security team are given maximum information about the network and the type of test that will occur. This is the easiest test to complete but does not provide a full picture of the organization’s security.
Penetration testing is also divided into categories based on the amount of information to be provided. The main categories that you should be familiar with include the following:
![]() Zero-knowledge test: The testing team is provided with no knowledge regarding the organization’s network. The testing team can use any means at its disposal to obtain information about the organization’s network. This is also referred to as closed or black-box testing.
Zero-knowledge test: The testing team is provided with no knowledge regarding the organization’s network. The testing team can use any means at its disposal to obtain information about the organization’s network. This is also referred to as closed or black-box testing.
![]() Partial-knowledge test: The testing team is provided with public knowledge regarding the organization’s network. Boundaries may be set for this type of test.
Partial-knowledge test: The testing team is provided with public knowledge regarding the organization’s network. Boundaries may be set for this type of test.
![]() Full-knowledge test: The testing team is provided with all available knowledge regarding the organization’s network. This test is focused on what attacks can be carried out.
Full-knowledge test: The testing team is provided with all available knowledge regarding the organization’s network. This test is focused on what attacks can be carried out.
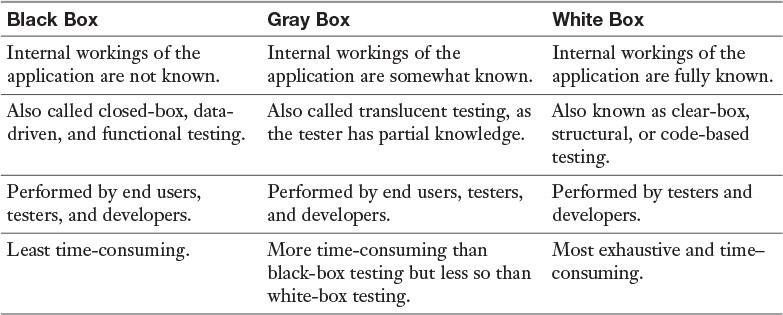
Black Box
Penetration testing can be divided into categories based on the amount of information to be provided. In black-box testing, or zero-knowledge testing, the team is provided with no knowledge regarding the organization’s network. The team can use any means at its disposal to obtain information about the organization’s network. This is also referred to as closed testing.
White Box
In white-box testing, the team goes into the process with a deep understanding of the application or system. Using this knowledge, the team builds test cases to exercise each path, input field, and processing routine. In the case of a network, the team would have access to all network information, which the team can use and leverage in the test.
Gray Box
In gray-box testing, the team is provided more information than in black-box testing, while not as much as in white-box testing. Gray-box testing has the advantage of being non-intrusive while maintaining the boundary between developer and tester. On the other hand, it may uncover some of the problems that might be discovered with white-box testing.
Table 12-2 compares the three testing methods.
When choosing between black-, white-, and gray-box testing, consider the security implications of each. You should only allow white-box testing by very trusted entities, such as internal testers, as it exposes the code to the testers. Black-box testing would be more appropriate for untrusted entities, like third-party testers. Black-box testing should be done by a third party that is large enough to have the resources to use as many test cases as required and to test all code paths.
You should also consider the type of malicious behavior that you are trying to determine is possible. For example, if you are interested in determining the likelihood of an attack from outside the network, you should use a black-box test, since presumably anyone attempting that would have no internal knowledge of the application. On the other hand, if you are more interested in the types of attacks that may come from your own people, you might want to use gray-box testing, where the attacker would have some knowledge of the system.
Finally, you should consider the effect that the testing method may have on the network. While white-box testing has a low risk of impacting system stability, black-box testing has a higher likelihood of creating instability in the system.
Reconnaissance
A network attack is typically preceded by an information-gathering phase called reconnaissance. Both technical tools and nontechnical approaches can be used to identify targets and piece together helpful information that may make a target easier to attack. Many of the tools discussed in this chapter (including enumerators, penetration testers, and port scanners) can be used as part of this information-gathering process. You might compare this stage of the hacking process to a bank robber casing a bank location before launching a robbery.
Fingerprinting
Fingerprinting tools are designed to scan a network, identify hosts, and identify services and applications that are available on those hosts. They help a hacker weed through the all the uninteresting items in the network and locate what is really of interest. By fingerprinting or identifying the operating system of a host, a hacker can also identify exploits that may work on the host. There are two forms of fingerprinting:
![]() Active: Active fingerprinting tools transmit packets to remote hosts and analyze the replies for clues about the replying system. Earlier in this chapter we looked at one such tool, Nmap, and you saw a port scan of an individual host in the discussion of port scans (refer to Figure 12-2). In the real world, that scan would probably have been preceded by a ping scan to identify all the hosts in the network. Figure 12-14 shows the result of a ping scan.
Active: Active fingerprinting tools transmit packets to remote hosts and analyze the replies for clues about the replying system. Earlier in this chapter we looked at one such tool, Nmap, and you saw a port scan of an individual host in the discussion of port scans (refer to Figure 12-2). In the real world, that scan would probably have been preceded by a ping scan to identify all the hosts in the network. Figure 12-14 shows the result of a ping scan.
If you examine the output in Figure 12-14, you can see the following:
![]() There are five Dell computers with addresses 10.68.26.10 to 10.68.26.13 and 10.68.26.15.
There are five Dell computers with addresses 10.68.26.10 to 10.68.26.13 and 10.68.26.15.
![]() There are three ShorTel devices (VoIP phones) at 10.68.26.16, 10.68.26.17, and 10.68.26.20.
There are three ShorTel devices (VoIP phones) at 10.68.26.16, 10.68.26.17, and 10.68.26.20.
![]() There is a Juniper device (a router, a switch, or both) at 10.68.26.2.
There is a Juniper device (a router, a switch, or both) at 10.68.26.2.
Using this information, the hacker would perform a port and services scan of the machines of interest.
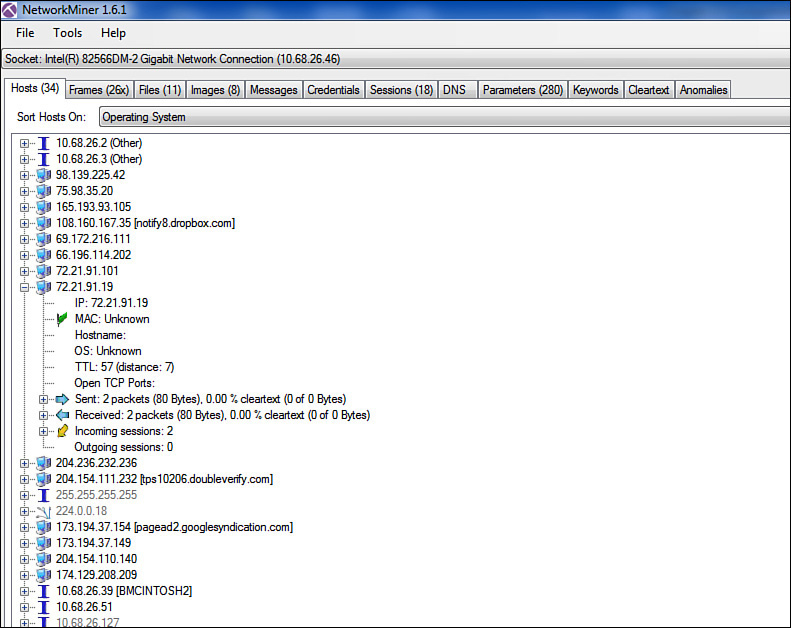
![]() Passive: It is possible to simply capture packets from a network and examine them rather than send packets on the network. NetworkMiner is an example of a passive tool. The output shown in Figure 12-15 identifies the OS, and you can see additional information by expanding the host. All this information is gathered through passive scanning.
Passive: It is possible to simply capture packets from a network and examine them rather than send packets on the network. NetworkMiner is an example of a passive tool. The output shown in Figure 12-15 identifies the OS, and you can see additional information by expanding the host. All this information is gathered through passive scanning.
The output in Figure 12-15 lists all the machines NetworkMiner discovered, by IP address. By tunneling into the details of each machine, you can see the IP address, MAC address, hostname, operating system, and other information. In this case, the scan has not been running long enough for the all the information about the machine at 77.21.91.19 to be generated.
Code Review
Code review is the systematic investigation of the code for security and functional problems. It can take many forms, from simple peer review to formal code review. There are two main types of reviews:
![]() Formal review: This is an extremely thorough, line-by-line inspection, usually performed by multiple participants using multiple phases. This is the most time-consuming type of code review but the most effective at finding defects.
Formal review: This is an extremely thorough, line-by-line inspection, usually performed by multiple participants using multiple phases. This is the most time-consuming type of code review but the most effective at finding defects.
![]() Lightweight: This type of code review is much more cursory than a formal review. It is usually done as a normal part of the development process. It can happen in several forms:
Lightweight: This type of code review is much more cursory than a formal review. It is usually done as a normal part of the development process. It can happen in several forms:
![]() Pair programming: Two coders work side-by-side, checking one another’s work as they go.
Pair programming: Two coders work side-by-side, checking one another’s work as they go.
![]() Email: Code is emailed around to colleagues for them to review when time permits.
Email: Code is emailed around to colleagues for them to review when time permits.
![]() Over the shoulder: Coworkers review the code, while the author explains his or her reasoning.
Over the shoulder: Coworkers review the code, while the author explains his or her reasoning.
![]() Tool-assisted: Perhaps the most efficient method, this method uses automated testing tools.
Tool-assisted: Perhaps the most efficient method, this method uses automated testing tools.
While code review is most typically performed on in-house applications, it may be warranted in other scenarios as well. For example, say that you are contracting with a third party to develop a web application to process credit cards. Considering the sensitive nature of the application, it would not be unusual for you to request your own code review to assess the security of the product.
In many cases, more than one tool should be used in testing an application. For example, an online banking application that has had its source code updated should undergo both penetration testing with accounts of varying privilege levels and a code review of the critical models to ensure that defects there do not exist.
Social Engineering
Social engineering attacks occur when attackers use believable language and user gullibility to obtain user credentials or some other confidential information. Social engineering threats that you should understand include phishing/pharming, shoulder surfing, identity theft, and dumpster diving.
The best countermeasure against social engineering threats is to provide user security awareness training. This training should be required and must occur on a regular basis because social engineering techniques evolve constantly.
Phishing/Pharming
Phishing is a social engineering attack in which attackers try to learn personal information, including credit card information and financial data. This type of attack is usually carried out by implementing a fake website that is nearly identical to a legitimate website. Users enter data, including credentials, on the fake website, allowing the attackers to capture any information entered. Spear phishing is a phishing attack carried out against a specific target by learning about the target’s habits and likes. Spear phishing attacks take longer to carry out than phishing attacks because of the information that must be gathered.
Pharming is similar to phishing, but pharming actually pollutes the contents of a computer’s DNS cache so that requests to a legitimate site are actually routed to an alternate site.
You should caution users against using any links embedded in email messages, even if the message appears to have come from a legitimate entity. Users should also review the address bar any time they access a site where their personal information is required to ensure that the site is correct and that SSL is being used.
Shoulder Surfing
Shoulder surfing occurs when an attacker watches when a user enters login or other confidential data. Users should be encouraged to always be aware of who is observing their actions. Implementing privacy screens helps ensure that data entry cannot be recorded.
Identity Theft
Identity theft occurs when someone obtains personal information, such as driver’s license number, bank account number, and Social Security number, and uses that information to assume the identity of the individual whose information was stolen. Once the identity is assumed, the attack can go in any direction. In most cases, attackers open financial accounts in the user’s name. Attackers also can gain access to the user’s valid accounts.
Dumpster Diving
Dumpster diving occurs when attackers examine the contents of physical garbage cans or recycling bins to obtain confidential information. This includes personnel information, account login information, network diagrams, and organizational financial data.
Organizations should implement policies for shredding documents that contain this information.
Exam Preparation Tasks
You have a couple of choices for exam preparation: the exercises here and the exam simulation questions on the CD-ROM.
Review All Key Topics
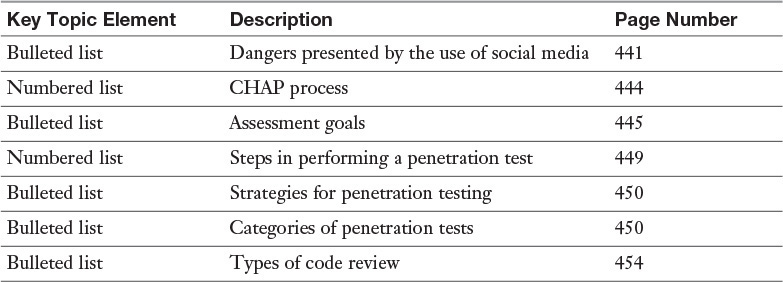
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 12-3 lists these key topics and the page number on which each is found.
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
Review Questions
1. You have recently suffered some network attacks and would like to discover the services that are available on the computers in your network. Which of the following assessment tools would be most appropriate for this?
a. port scanner
b. protocol analyzer
c. password cracker
d. fuzzer
2. Recently someone stole data from your network, and that data should have been encrypted, but it’s too late to figure out whether it was. What tool could you use to determine if certain types of traffic on your network are encrypted?
a. port scanner
b. protocol analyzer
c. password cracker
d. fuzzer
3. A web application developed by your company was recently compromised and caused the loss of sensitive data. You need a tool that can help identify security holes in the application before it is redeployed. Which tool could you use?
a. port scanner
b. protocol analyzer
c. password cracker
d. fuzzer
4. You would like to prevent the corruption of the routing tables in your network. Which of the following would be the best approach to mitigate this?
a. Implement CDP.
b. Configure CHAP between routers.
c. Implement sandboxing.
d. Disable CDP.
5. You need to identify zero-day malware. What technique could be used to help in this process?
a. fuzzing
b. deploying an HTTP interceptor
c. malware sandboxing
d. establishing a social media policy
6. You implemented a procedure whereby a testing team was provided with limited knowledge of the network systems and devices using publicly available information. The organization’s security team was informed that an attack is coming. What type of test have you implemented?
a. double-blind test
b. target test
c. full-knowledge test
d. blind test
7. Which of the following testing types would you use if you wanted to spend the least amount of time on the test?
a. black box
b. gray box
c. white box
d. clear box
8. A group of your software developers just reviewed code while the author explained his reasoning. What type of code review have they just completed?
a. pair programming
b. over-the-shoulder
c. tool assisted
d. email
9. Recently your users were redirected to a malicious site when their DNS cache was polluted. What type of attack have you suffered?
a. phishing
b. shoulder surfing
c. pharming
d. dumpster diving
10. What is the last step in performing a penetration test?
a. Gather information about attack methods against the target system or device.
b. Document information about the target system or device.
c. Execute attacks against the target system or device to gain user and privileged access.
d. Document the results of the penetration test and report the findings.