Organizational Security Model
My security model is shaped like a pile of oatmeal.
Response: Lovely.
An organizational security model is a framework made up of many entities, protection mechanisms, logical, administrative, and physical components, procedures, business processes, and configurations that all work together to provide a security level for an environment. Each model is different, but all models work in layers: one layer provides support for the layer above it, and protection for the layer below it. Because a security model is a framework, companies are free to plug in different types of technologies, methods, and procedures to accomplish the necessary protection level for their environment. Figure 3-4 illustrates the pieces that can make up a security model.
Figure 3-4. A comprehensive and effective security model has many integrated pieces.

Effective security requires a balanced approach and application of all security components and procedures. Some security components are technical (access control lists and encryption) and some are nontechnical (physical and administrative, such as developing a security policy and enforcing compliance), but each has an important place within the framework, and if one is missing or incomplete, the whole framework may be affected.
A security model has various layers, but it also has different types of goals to accomplish in different timeframes. You might have a goal for yourself today to brush your teeth, run three miles, finish the project you have been working on, and spend time with your kids. These are daily goals, or operational goals. You might have midterm goals: to complete your master’s degree, write a book, and get promoted. These take more time and effort and are referred to as tactical goals. Your long-term goals may be to retire at age 55, save enough money to live comfortably, and live on a houseboat. These goals are strategic goals because they look farther into the future.
The same thing happens in security planning. Daily goals, or operational goals, focus on productivity and task-oriented activities to ensure that the company functions in a smooth and predictable manner. A midterm goal, or tactical goal, could be to integrate all workstations and resources into one domain so that more central control can be achieved. Long-term goals, or strategic goals, could be to move all the branches from dedicated communication lines to frame relay, implement IPSec virtual private networks (VPNs) for all remote users, and integrate wireless technology with the necessary security measures into the environment.
Security planning can be broken down into three different areas: strategic, tactical, and operational. Strategic planning is the plans that fall in line with the business and information technology goals. The goals of strategic planning have a longer or broader horizon and can extend out as far as five years. Strategic planning may include some of the following goals:
Make sure risks are properly understood and addressed.
Ensure compliance with laws and regulations.
Integrate security responsibilities throughout the organization.
Create a maturity model to allow for continual improvement.
Use security as a business achievement to attract more customers.
Tactical planning refers to the initiatives and other support that must be implemented in order to reach the broader goals that have been put forth by the strategic planning. In general, the tactical plans are shorter in length or have a shorter planning horizon than those of the strategic plans.
And finally, operational planning deals with very specific plans, their deadlines, and goals. This involves hard dates and timelines by which the goals of the plan should be completed, as well as specific directions in how they are to be completed. These goals tend to be more of a short-term or interim nature to mitigate risks until larger tactical or strategic plans can be created and implemented. The following are a couple of examples of operational planning to help you better understand what it is:
Perform security risk assessment.
Do not allow security changes to decrease productivity.
Maintain and implement controls.
Continually scan for vulnerabilities and roll out patches.
Track compliance with policies.
This approach to planning is called the planning horizon. A company usually cannot implement all changes at once, and some changes are larger than others. Many times, certain changes cannot happen until other changes take place. If a company wants to implement its own certificate authority and implement a full public key infrastructure (PKI) enterprise-wide, this cannot happen in a week if the company currently works in decentralized workgroups with no domain structure. So, its operational goals would be to keep production running smoothly and make small steps toward readying the environment for a domain structure. Its tactical goal would be to put all workstations and resources into a domain structure, and centralize access control and authentication. Its strategic goal would be to have all workstations, servers, and devices within the enterprise use the PKI to provide authentication, encryption, and more secure communication channels.
Security works best if the company’s operational, tactical, and strategic goals are defined and work to support each other, which can be much harder than it sounds.
Security Program Components
I have a security policy, so I must have a security program.
Response: You have just begun, my friend.
Today, organizations, corporations, government agencies, and individuals are more involved in information security than ever before. With more regulations being promulgated by governments, continuing increases in both the number of attacks and the cost of fighting hackers and malware, and increasing dependence upon computing technology, concerns about information security are expanding from IT departments to the board rooms.
Most security professionals welcome this shift because it means the decision makers are finally involved and more progress can be made enterprise-wide. Experienced security professionals have always known that technology is just a small portion of overall organizational security. Business people, who are now becoming more responsible and liable for security, are not so thrilled about this shift, however.
The common scenario in businesses and organizations is as follows: A CEO and board members eventually are forced to look at information security because of new regulations, because the costs of viruses and attacks have reached a threshold, or because a civil suit has been filed regarding a security breach. The company typically hires a consultant, who tells the CEO and board that they need a security policy and a network assessment. The company usually pays for both to be done and, with that accomplished, believes the company is secure. However, this is a false sense of security, because the company still has no security program.
The company then hires a security officer (typically called either a Corporate Security Officer [CSO] or a Corporate Information Security Officer [CISO]). Senior management hires this person so it can delegate all security activities and responsibilities, and get security off of their desk, but fails to give this person any real authority or budget. Then, when security compromises take place, the CSO becomes the sacrificial lamb—because we always need someone to blame.
Now, as security professionals, we have three choices for dealing with this common scenario:
Stick our heads in the sand and hope all of this just goes away.
Continue to be frustrated and confused, develop ulcers, and shake our fists at the unfriendly security gods in the sky.
Understand that we, as a society, are in the first basic steps of our evolution in information security and therefore must be committed to learn and practice the industry’s already developed best practices.
The Corporate Information Security Officer (CISO) is responsible for having a strong understanding of the business processes and objectives for the organization, and then with that information they must be able to communicate to senior management about the risks that are threatening the organization, and what regulations and requirements the government has imposed that they will need to adhere to and comply with. This information will need to be reported to management through meetings and documentation. They will need to develop and provide security-awareness programs, and understand the business objectives of the organization. They will also need to develop the budget for any of the activities which occur that are related to information security. Other tasks that will fall to the CISO are the development of policies, procedures, baselines, standards, and guidelines. By having access to and an understanding of this material, they can maintain the awareness of threats and vulnerabilities that are emerging and which could potentially impact the organization. Staying abreast of emerging technologies will also provide them valuable information and tools they can implement or consider. Evaluation of responses to security incidents also falls to the CISO, as well as the task of developing a security compliance program and establishing security metrics. Auditors may be used during the evaluation processes and they can be used from both internal and external sources. By fulfilling all of these job responsibilities and requirements, the CISO will be more effective in making sure the security of the organization is working properly and addresses the risks that the business environment may create for it.
It is important that the security elements of the organization report as high as possible in the chain of management. This is because with new government regulations and direct business impacts it is vital that there is a limitation on any possible kinds of miscommunication that can potentially occur during the reporting process. It is also important that at whatever level the security elements are reporting to they maintain a strong working relationship that reinforces the credibility and reliability of the security elements. The last thing you want is the credibility of the CISO to come under question when they are reporting on the security of the organization. This is an individual that will be relied upon to properly report about the security status of the organization. This means when the CISO is reporting to the Chief Executive Officer, it will not only reduce any miscommunications, but also ensure that the correct information is being provided to the proper individuals.
The CISO will also need to be reporting information to the Information Technology (IT) department as well as reporting to other elements of the organization such as security, the administrative services department, the insurance and risk management department, the legal department, business unit, and the internal audit department. Effective and clear communications between the security elements and the other departments of the organization will go a long way toward enforcing security and mitigating risks.
Security Frameworks
The Control Objectives for Information and related Technology (CobiT) is a framework developed by the Information Systems Audit and Control Association (ISACA) and the IT Governance Institute (ITGI). It defines goals for the controls that should be used to properly manage IT and ensure IT maps to business needs. CobiT is broken down into four domains: Plan and Organize, Acquire and Implement, Deliver and Support, and Monitor and Evaluate. Each category drills down into subcategories. For example, Acquire and Implement contains the following subcategories:
Acquire and Maintain Application Software
Acquire and Maintain Technology Infrastructure
Develop and Maintain Procedures
Install and Accredit Systems
Manage Changes
So this CobiT domain provides goals and guidance to companies when they purchase, install, test, certify, and accredit IT products. This is very powerful because most companies use an ad hoc and informal approach when making purchases and carrying out procedures.
People who are new to CobiT quickly get overwhelmed by it, because it is massive and basically impossible to implement fully even in a 24-month period. Under each of these domains CobiT provides control objectives, control practices, goal indicators, performance indicators, success factors, and maturity models. It lays out a complete roadmap that can be followed to accomplish each of the 34 control objectives this model deals with.
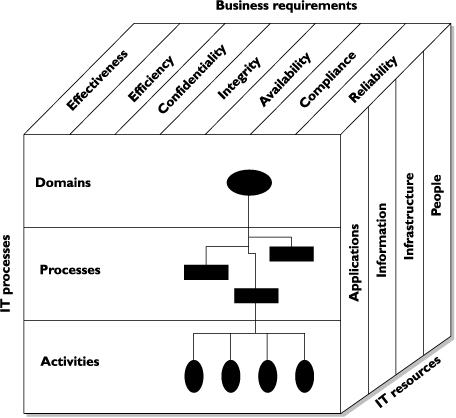
Figure 3-5 illustrates how the framework connects business requirements, IT resources, and IT processes. Many IS auditors use this framework as their criteria when determining the efficiency of the implemented controls. This means that if you want to pass an assurance audit, it is a good idea to know and fulfill control objectives in your company as it makes sense.
Figure 3-5. CobiT components
CobiT was derived from the COSO framework, which was developed by the Committee of Sponsoring Organizations of the Treadway Commission in 1985 to deal with fraudulent financial activities and reporting. The COSO framework is made up of the following components:
Control Environment
Management’s philosophy and operating style
Company culture as it pertains to ethics and fraud
Risk Assessment
Establishment of risk objectives
Ability to manage internal and external change
Control Activities
Policies, procedures, and practices put in place to mitigate risk
Information and Communication
Structure that ensures that the right people get the right information at the right time
Monitoring
Detecting and responding to control deficiencies
COSO is a model for corporate governance and CobiT is a model for IT governance. COSO deals more at the strategic level while CobiT focuses more at the operational level. You can think of CobiT as a way to meet many of the COSO objectives, but only from the IT perspective. COSO deals with non-IT items also, as in company culture, financial accounting principles, board of director responsibility, and internal communication structures. COSO is an acronym for the Committee of Sponsoring Organizations of the Treadway Commission, and was formed in 1985 to provide sponsorship for the National Commission on Fraudulent Financial Reporting, an organization that studies deceptive financial reports and what elements lead to them.
Developing and rolling out a security program is not as difficult as many organizations make it out to be, but it is new to them and new things are usually scary and confusing. This is why they should turn to standards and industry best practices, which provide the guidance and recipe for how to set up and implement a full security program.
The most commonly used standard is ISO 17799, which was derived from the de facto standard: British Standard 7799 (BS7799). It is an internationally recognized Information Security Management Standard that provides high-level conceptual recommendations on enterprise security. The British Standard actually has two parts: BS7799 Part 1, which outlines control objectives and a range of controls that can be used to meet those objectives; and BS7799 Part II, which outlines how a security program can be set up and maintained. BS7799 Part II also served as a baseline that organizations could be certified against. An organization would choose to be certified against the ISO 17799 standard to provide confidence to their customer base and partners and be used as a marketing tool. To become certified, an authorized third party would evaluate the organization against the requirements in ISO 17799 Part II. The organization could be certified against all of ISO 17799 Part II or just a portion of the standard.
While there has been plenty of controversy regarding the benefits and drawbacks of ISO 17799, it is the agreed upon mechanism to describe security processes, and is the benchmark we use to indicate a “correct infrastructure.” It is made up of ten domains, which are very close to the CISSP Common Body of Knowledge (CBK).
The ISO 17799 domains are as follows:
Information security policy for the organization Map of business objectives to security, management’s support, security goals, and responsibilities.
Creation of information security infrastructure Create and maintain an organizational security structure through the use of a security forum, a security officer, defining security responsibilities, authorization processes, outsourcing, and independent reviews.
Asset classification and control Develop a security infrastructure to protect organizational assets through accountability and inventory, classification, and handling procedures.
Personnel security Reduce risks that are inherent in human interaction by screening employees, defining roles and responsibilities, training employees properly, and documenting the ramifications of not meeting expectations.
Physical and environmental security Protect the organization’s assets by properly choosing a facility location, erecting and maintaining a security perimeter, implementing access control, and protecting equipment.
Communications and operations management Carry out operations security through operational procedures, proper change control, incident handling, separation of duties, capacity planning, network management, and media handling.
Access control Control access to assets based on business requirements, user management, authentication methods, and monitoring.
System development and maintenance Implement security in all phases of a system’s lifetime through development of security requirements, cryptography, integrity, and software development procedures.
Business continuity management Counter disruptions of normal operations by using continuity planning and testing.
Compliance Comply with regulatory, contractual, and statutory requirements by using technical controls, system audits, and legal awareness.
Now, CobiT and COSO provide the “what is to be achieved,” but not the “how to achieve it.” This is where ITIL and ISO 17799 come in. The Information Technology Infrastructure Library (ITIL) is the de facto standard of best practices for IT service management. ITIL was created because of the increased dependence on information technology to meet business needs. Unfortunately, a natural divide exists between business people and IT people in every organization because they use different terminology and have different focuses within the organization. The lack of a common language and understanding of each other’s domain (business versus IT) has caused many companies to not properly blend their business objectives and IT functions in an effective manner. The results of this lack of blending usually end up generating confusion, miscommunication, missed deadlines, missed opportunities, increased cost in time and labor, and frustration on both the business and technical sides of the house. ITIL is a customizable framework that is provided in a set of books or in an online format. It provides the goals, the general activities necessary to achieve these goals, and the input and output values for each process required to meet these determined goals. Where CobiT defines IT goals, ITIL provides the steps at the process level on how to achieve those goals. Although ITIL has a component that deals with security, its focus is more towards internal service level agreements between the IT department and the “customers” it serves. The customers are usually internal departments.
Note

| The technically correct names for the ISO standards listed earlier are ISO/IEC with a following number (ISO/IEC 17799:2005, ISO/IEC 27001:2005, and so on). IEC is the International Electrotechnical Commission, which jointly works with ISO to create global standards. In the industry, and on the exam, you could see the standards presented with or without IEC, but they are still referring to the same standards. Just using ISO is an abbreviation. |
References
The ISO 17799 Service and Software Directory www.iso17799software.com
The ISO 17799 Directory www.iso-17799.com
The ISO 17799 Community Portal www.17799.com
ISACA CobiT Framework www.isaca.org
IT Infrastructure Library (ITIL) www.itil.co.uk
Security Governance
We have security governance because I said so and it is written in our charter. Now, what is security governance again?
Security governance is very similar in nature to corporate and IT governance because there are overlapping functionality and goals among the three. All three work within an organizational structure of a company and have the same goals of helping to ensure the company will survive and thrive—each just has a different focus. As the amount of requirements in corporate governance has increased due to regulations and legislation, there has also been an increased need in security governance as well. This is because as the global marketplace increases, so does the need to comply with the multiple laws and practices of the countries in which they are conducting business. Just as the boards of directors of organizations are being held more and more accountable for the business practices and performance of their organizations, the need for information security governance has become more and more important in ensuring that the proper mechanisms are in place to provide the board of directors, as well as management, with the ability to conduct the proper oversight so as to manage the risks to the organization at levels that are acceptable and limit potential damages.
Many very professional and adult sounding definitions of security governance can be found, such as the following issued by the IT Governance Institute in its Board Briefing on IT Governance, 2nd edition.
“Governance is the set of responsibilities and practices exercised by the board and executive management with the goal of providing strategic direction, ensuring that objectives are achieved, ascertaining that risks are managed appropriately, and verifying that the enterprise’s resources are used responsibly.”
This definition is absolutely correct, but remains at a high level that is difficult for many of us mere mortals to fully understand or know how to actually carry out. This is more like a strategic policy statement, while the real skill is to properly interpret and transform it into meaningful tactical and operational functions and practices.
Security governance is all of the tools, personnel, and business processes necessary to ensure that the security implemented meets the organization’s specific needs. It requires organizational structure, roles and responsibilities, performance measurement, defined tasks, and oversight mechanisms. This definition is not much better, is it?
Let’s compare two companies. Company A has an effective security governance program in place and Company B does not. Now, to the untrained eye it would seem as though Companies A and B are equal in their security practices because they both have security policies, procedures, standards, the same security technology controls (firewalls, IDSs, identity management, and so on), and a security team run by a security officer. You may think, “Man, these two companies are on the ball and quite evolved in their security programs.” But if you look closer, you will see some critical differences (listed in Table 3-1).
| Company A | Company B |
|---|---|
| Board members understand that information security is critical to the company and demand to be updated quarterly on security performance and breaches. | Board members do not understand that information security is in their realm of responsibility and focus solely on corporate governance and profits. |
| CEO, CFO, CIO, and business unit managers participate in a risk management committee that meets each month, and information security is always one topic on the agenda to review. | CEO, CFO, and business unit managers feel as though information security is the responsibility of the CIO, CISO, and IT department and do not get involved. |
| Executive management sets an acceptable risk level that is the basis for the company’s security policies and all security activities. | CISO took some boilerplate security policies and inserted his company’s name and had the CEO sign them. |
| Executive management holds business unit managers responsible for carrying out risk management activities for their specific business units. | All security activity takes place within the security department, thus security works within a silo and is not integrated throughout the organization. |
| Critical business processes are documented along with the risks that are inherent at the different steps within the business processes. | Business processes are not documented and not analyzed for potential risks that can affect operations, productivity, and profitability. |
| Employees are held accountable for any security breaches they participate in, either maliciously or accidentally. | Policies and standards are developed, but no enforcement or accountability practices have been envisioned or deployed. |
| Security products, managed services, and consultants are purchased and deployed in an informed manner. They are also constantly reviewed to ensure they are cost-effective. | Security products, managed services, and consultants are purchased and deployed without any real research or performance metrics to be able to determine the return on investment or effectiveness. |
| The organization is continuing to review its processes, including security, with the goal of continued improvement. | The organization does not analyze its performance for improvement, but continually marches forward and makes similar mistakes over and over again. |
Does the organization you work for look like Company A or Company B? Most organizations today have many of the pieces and parts to a security program (policies, standards, firewalls, security team, IDS, and so on), but the management is not truly involved, and security has not permeated throughout the organization. Instead, organizations have all of these pieces and parts and have a small security team that is responsible for making sure security is properly carried out throughout the whole company—which is close to impossible. If security was just a technology issue, then this security team could properly install, configure, and maintain the products, and the company would get a gold star and pass the audit with flying colors. But that is not how the world of information security works today. It is much more than just technological solutions. Security professionals need to understand that security must be utilized throughout the organization and having several points of responsibility and accountability is critical. Security governance is a coherent system of integrated security components (products, personnel, training, processes, policies, and so on) that exist to ensure the organization survives and hopefully thrives.
Note

| It is easier to purchase a security solution than to attempt to change the culture of an organization. Even if the company has the most up-to-date and advanced products on the market, the company cannot achieve the necessary degree of security if the products are being used by untrained, apathetic, and careless employees. Evaluating the culture of an organization is very important when assessing an organization’s security posture. |
For there to be security governance, there must be something to govern. The collection of the controls that an organization must have in place is collectively referred to as a security program.
Security Program Development
It is important to understand that a security program has a life cycle that is always continuing, because it should be constantly evaluated and improved upon. The life cycle of any process can be described in different ways. We will use the following steps:
1. | Plan and Organize |
2. | Implement |
3. | Operate and Maintain |
4. | Monitor and Evaluate |
Many organizations do not follow a life cycle approach in developing, implementing, and maintaining their security management program. This is because they do not know how, or they feel as though this approach is cumbersome and a waste of time. The result of not following a life cycle structure usually results in the following:
Written policies and procedures that are not mapped to and supported by security activities
Severe disconnect and confusion between different individuals throughout the organization who are attempting to protect company assets
No way of assessing progress and the return on investment of spending and resource allocation
No way of fully understanding the security program deficiencies, and having a standardized way of improving upon the deficiencies
No assurance of compliance to regulations, laws, or policies
Relying fully on technology for all security solutions
A patchwork of point solutions and no holistic enterprise solution
A “fire alarm” approach to any breaches instead of a calm proactive and detective approach
A false sense of security with an undercurrent of confusion
Without setting up a life cycle approach to a security program and the security management that maintains the program, an organization is doomed to treat security as merely another project. Anything treated as a project has a start and stop date, and at the stop date everyone disperses to other projects. Many organizations have had good intentions in their security program kickoffs, but did not implement the proper structure to ensure that security management was an ongoing and continually improving process. The result was a lot of starts and stops over the years and repetitive work that cost more than it should, with diminishing results.
The main components of each phase are provided in the following:
Plan and Organize
Establish management commitment
Establish oversight steering committee
Assess business drivers
Carry out a threat profile on the organization
Carry out a risk assessment
Develop security architectures at an organizational, application, network, and component level
Identify solutions per architecture level
Obtain management approval to move forward
Implement
Assign roles and responsibilities
Develop and implement security policies, procedures, standards, baselines, and guidelines
Identify sensitive data at rest and in transit
Implement the following blueprints:
Asset identification and management
Risk management
Vulnerability management
Compliance
Identity management and access control
Change control
Software development life cycle
Business continuity planning
Awareness and training
Physical security
Incident response
Implement solutions (administrative, technical, physical) per blueprint
Develop auditing and monitoring solutions per blueprint
Establish goals, service level agreements (SLAs), and metrics per blueprint
Operate and Maintain
Follow procedures to ensure all baselines are met in each implemented blueprint
Carry out internal and external audits
Carry out tasks outlined per blueprint
Manage service level agreements per blueprint
Monitor and Evaluate
Review logs, audit results, collected metric values, and SLAs per blueprint
Assess goal accomplishments per blueprint
Carry out quarterly meetings with steering committees
Develop improvement steps and integrate into the Plan and Organize phase
Many of the items mentioned in the previous list are covered throughout this book. This list was provided to show how all of these items can be rolled out in a sequential and controllable manner.
Note

| Various organizations, consulting companies, and security professionals may follow different approaches to setting up a security program, but overall they cover the same topics. Although every organization has different acceptable risk levels, implemented controls, threats, and business drivers, each of the security programs contains basically the same components. Some components are just emphasized more than others based on the company’s business and security needs. |
Although these models and frameworks are very helpful, they are also very high level. For example, if a framework simply states an organization must secure its data, a great amount of work will be called for. This is where the security professional really rolls up her sleeves, by developing security blueprints. Blueprints are important tools to identify, develop, and design security requirements for specific business needs. These blueprints must be customized to fulfill the organization’s security requirements, which are based on its regulatory obligations, business drivers, and legal obligations. For example, let’s say Company Y has a privacy policy, and their security team has developed standards and procedures pertaining to the privacy strategy the company should follow. The blueprint will then get more granular and lay out the processes and components necessary to meet requirements outlined in the policy, standards, and requirements. This would include at least the following:
A diagram of the company network
Where the sensitive data resides within the network
The network segments that the sensitive data transverse
The different security solutions in place (VPN, SSL, PGP) that protect the sensitive data
Third-party connections where sensitive data is shared
Security measures in place for third-party connections
And more...
The blueprints to be developed and followed depend upon the organization’s business needs. If Company Y uses identity management, there must be a blueprint outlining roles, registration management, authoritative source, identity repositories, single sign-on solutions, and so on. If Company Y does not use identify management, there is no need to build a blueprint for this. Many of the blueprints most organizations need to develop are listed in the following:
Security management
Business continuity
Logging and monitoring
Identity management
Application integrity
Infrastructure
Asset management
Physical and environmental security
And more...
So the blueprint will lay out the security solutions, processes, and components the organization uses to match its security and business needs. These blueprints must be applied to the different business units within the organization. For example, the identity management practiced in each of the different departments should follow the crafted blueprint. Following these blueprints throughout the organization allows for standardization, easier metric gathering, and governance. The blueprints should follow best practices and are commonly mapped to the ISO 17799 framework. Figure 3-6 illustrates where these blueprints come into play when developing a security program. We will dig deeper into blueprints and their components in Chapter 5.
Business Requirements: Private Industry vs. Military Organizations
Which security model an organization chooses depends on its critical missions and business requirements. Private industry usually has much different missions and requirements than those of the military. Private industry thrives by beating the competition, which is done through marketing and sales, solid management decisions, understanding the target audience, and understanding the flow and ebb of the market. A private-sector business has a better chance of being successful if its data is readily available, so processing order requests and fulfilling service orders can happen quickly and painlessly for the customer. The data also must be accurate to satisfy customers’ needs. Out of the three security services (availability, integrity, and confidentiality), data integrity and availability usually rank higher than confidentiality to most private-sector businesses when compared to military requirements.
The military also thrives by beating its competition (other countries or its enemies), which requires proper training, readiness, intelligence, and deployment. Although the private industry does need a degree of secrecy and ensured confidentiality, confidentiality does not play as important a role as it does with a military organization. The military has more critical information that must not fall into the wrong hands; therefore, out of the three main security services, confidentiality is the most important to the military sector. Thus, a military installation must implement a security model that emphasizes confidentiality—commonly more strict than a private-sector organization’s security model.


