An Architectural View
Once we look at different types of vulnerabilities, attacks, and threats, we find they exist at different layers within a network. This digs into more of the technology of an environment and the complexity of each of these technologies at each layer. This applies to the various protocols, applications, hardware, and security mechanisms that work at one or more of the seven layers of the OSI model. (The OSI model is fully described in Chapter 7.) IP spoofing is an attack at the network layer, ARP attacks happen at the data link layer, traffic sniffing occurs at several layers, and viruses enter through the application layer. If an organization just employs strict password rules and a firewall, this leaves many layers vulnerable to other types of attacks.
Organizations often put too much faith in their shiny new firewalls, IDSs, and antivirus software. Once one or more of these solutions are implemented, a false sense of security may lull the IT staff and travel up to management. It is more important to look at the flow of data in and out of a network and how the applications and devices work together. This is an architectural view, versus a device or application view.
Taking an architectural view, you must look at the data flow in and out of the environment, how this data is being accessed, modified, and monitored at different points, and how all the security solutions relate to each other in different situations. The firewall, for instance, is only part of the overall architecture. It is the architecture itself that needs to have an adequate level of security, not just the firewall. A network could either perform as a well-tuned orchestra or as several pieces that play wonderfully by themselves but give you a headache when they are all brought into the same room. Each individual security component could be doing its job by protecting its piece of the network, but the security function may be lost when it is time to interrelate or communicate with another security component.
Each environment is dissimilar because of the many variations in installed hardware, software, technologies, and configurations. However, the main differences between environments are the goals each is trying to achieve. A local area network (LAN) provides authentication, resources to its users, and an overall controlled inner atmosphere. A wide area network (WAN) provides connections between users at remote sites through protocol tunneling and access control. An e-commerce arrangement provides a web interface to Internet users, connection to data held on back-end servers, access control, and a different type of authentication from what LANs and WANs use. These diverse goals require different architectures, but can use the same basic security concepts.
Because there are particular levels within an environment, as shown in Figure 2-10, different types of attacks can happen at these levels. (Four of the seven layers of the OSI model are shown in Figure 2-10.) The following is a short list of countermeasures, the layers they work at, and the vulnerabilities they protect against:
Application proxy firewall configurations protect at the application layer. These combat a range of attacks, including unauthorized access and packet spoofing.
Network address translation (NAT) works at the network layer. This hides LAN IP addresses and topology.
Shielded twisted pair (STP) cabling works at the physical layer. This helps protect against network eavesdropping and signal interference.
A network intrusion detection sensor monitors network traffic at the network and transport layers for known attack signatures. This identifies known attacks and resets TCP connections if necessary.
IP Security (IPSec), which works at the network layer, is configured for virtual private network (VPN) connections into the perimeter network. This protects against masquerading, data manipulation, and unauthorized access to confidential information via encryption.
Web server configuration provides protection within the application by using different sites for public versus confidential information. This protects against directory hopping and unauthorized access.
Only necessary services and ports are enabled on all perimeter devices, which work at the network and transport layers. This reduces entry points into the network and DoS attacks.
The mail server uses a store-and-forward method of messaging and runs antivirus software. This protects against viruses and DoS attacks.
Secure Sockets Layer (SSL), which works at the transport layer, is configured at the web sites when customers need to access personal confidential information. This provides confidentiality and data integrity, and protects against masquerading.
A network scanner runs a weekly probe on all perimeter network server ports to identify new vulnerabilities. This protects against new vulnerabilities resulting from configuration changes or additional technologies being added.
A web server uses embedded cryptography within Extensible Markup Language (XML) code and Distributed Component Object Model (DCOM) security. This provides confidentiality of information and restricts components from performing risky actions.
Web servers require valid digital certificates from each other for proper authentication. These protect against session hijacking and masquerading.
Figure 2-10. A graphical representation of devices and protocols and where they appear within the OSI model
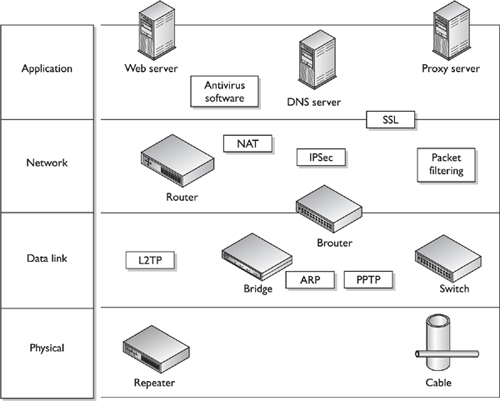
This list shows a small percentage of the activity that happens at different points of the OSI model and the company’s network. If one or more of the devices or software has incorrect configurations or if the environment is missing one of these components, it could leave an open portal for an attacker to gain entry into the network.
A Layer Missed
Many environments do not contain all the devices and components in the previous list of security vulnerabilities and solutions. The following example shows how employing several security mechanisms can seemingly provide a fully secured environment yet leave a small doorway of opportunity available that the clever attacker can take advantage of.
A network that has a firewall with packet filtering, a proxy server with content filtering, its public and private DNS records clearly separated, SSL for Internet users, IPSec for VPN connections, and public key infrastructure (PKI), as well as restricted service and port configuration, may seem like a fortified environment, and a network administrator most likely implemented these mechanisms with the best intentions. However, one problem is that it is fortified only for a moment in time. Without a scanning device that probes the environment on a scheduled basis or an IDS that looks out for suspicious activity, the environment could be vulnerable even after the company has spent thousands of dollars to protect it. Technology and business drivers continually change, and so do networks and environments. When you configure a new application, apply a patch, or install a device, the change to the environment could have unpredictable consequences (not to mention the new ways hackers have found to circumvent the original security mechanisms).
Bringing the Layers Together
It is not always necessary to purchase the newest security solutions on the market or pay top dollar for the hardware solution instead of buying the cheaper software solution. It is necessary to be aware of where threats can develop and take steps to make sure all your bases are covered. That’s what is meant by a layered approach.
In the computer and network world, the complexity of the levels can be a bit overwhelming at times. The most important first step is to understand the environment that needs to be protected. Many times, new IT members enter an environment that was established years ago by another group of people. The environment is continually added on to; it is never stagnant. Usually, there is no up-to-date network diagram because IT’s current daily tasks are time consuming, there is a lack of useful documentation, and no one person understands how the entire network works. This means that when something goes wrong, 80 percent of the effort and time is spent in a chaotic scramble for a solution. It does not need to work this way, and there would be fewer security compromises if this scene were not so common.
Instead of looking at updating that old network diagram (or creating a first one) as a boring task, you could approach it as a fact-finding mission for crucial information. Instead of putting down the IT staff after a successful hacker attack, you could change your attitude and think of what new practices need to be employed. New software, patches, and devices should be clearly tested prior to implementation for any unforeseen events. An IDS should be established in potentially vulnerable segments of the network, if not all segments. Security scans to seek out new vulnerabilities should take place regularly, not just when an audit is around the corner. In addition, every security administrator should stay up-to-date on the recent security compromises, be aware of how changes to the network could open a door to clever attackers, and keep those intrusion detection and antivirus signatures current.
Keeping current on network, software, configurations, and education can be overwhelming, but most of us in this line of work love to learn. Being effective in managing security means we will never stop learning.
