How Security Became an Issue
It is interesting to pick up various computer books and see there is usually a history section that sets the stage for where society is today pertaining to computing and data processing. Unlike histories that tell of times long past, the history of computing typically begins in the 1960s. A lot has happened in a short period of time, and computer security is just starting to reach its time in the limelight.
Roughly 25 years ago, the only computers were mainframes. They were few and far between and used for specialized tasks, usually running large batch jobs, one at a time, and carrying out complex computations. If users were connected to the mainframes, it was through “dumb” terminals that had limited functionality and were totally dependent on the mainframe for their operations and processing environment. This was a closed environment with little threat of security breaches or vulnerabilities being exploited. This does not mean things were perfect, that security vulnerabilities did not exist, and that people were in a computing utopia. Instead, it meant there were a handful of people working in a “glass house” who knew how to operate the mainframe. They decided who could access the mainframe and when. This provided a much more secure environment, because of its simplicity, than what we see in today’s distributed and interconnected world.
In the days of mainframes, web sites describing the steps of how to break into a specific application or operating system did not exist. The network stacks and protocols used were understood by very few people relative to the vast number of individuals that understand stacks and protocols today. Point-and-click utilities that can overwhelm buffers or interrogate ports did not exist. This was a truly closed environment that only a select few understood.
If networks were connected, it was done in a crude fashion for specific tasks, and corporations did not totally depend on data processing as they do today. The operating systems of that time had problems, software bugs, and vulnerabilities, but not many people were interested in taking advantage of them. Mainframe operators were at the command line and if they encountered a software problem, they usually just went in and manually changed the programming code. All this was not that long ago, considering where we are today.
As companies became more dependent on the computing power of mainframes, the functionality of the systems grew and various applications were developed. It was clear that giving employees only small time slices of access to the mainframes was not as productive as it could be. Processing and computing power was brought closer to the employees, enabling them to run small jobs on their desktop computers while the big jobs still took place within the “glass house.” This trend continued and individual computers became more independent and autonomous, only needing to access the mainframe for specific functionality.
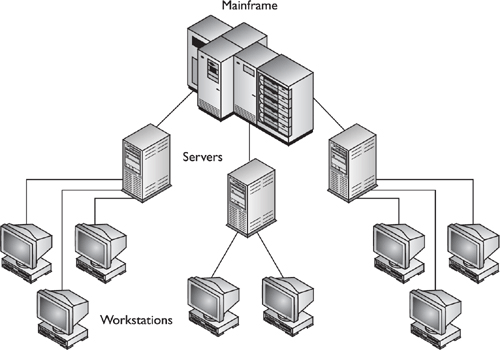
As individual personal computers became more efficient, they continually took on more tasks and responsibilities. It was shown that several users accessing a mainframe was an inefficient model; some major components needed to be more readily available so users could perform their tasks in an efficient and effective way. This thinking led to the birth of the client/server model. Although many individual personal computers had the processing power to compute their own calculations and perform their own logic operations, it did not make sense that each computer held information needed by all other computers. Thus, programs and data were centralized on servers, with individual computers accessing them when necessary and accessing the mainframes less frequently, as shown in Figure 2-1.
Figure 2-1. The relationship between a mainframe, servers, and workstations
With the increasing exposure to computing and processing, individuals who used computers learned more about using the technology and getting the most out of it. However, the good things in life often have a darker side. Taking technology down from the pedestal of the mainframe and putting it into so many individuals’ hands led to many issues never before dealt with in the mainframe days. Now there were thousands of inexperienced users who had much more access to important data and processes. Barriers and protection mechanisms were not in place to protect employees and systems from mistakes, so important data got corrupted accidentally, and individual mistakes affected many other systems instead of just one.
Because so many more people were using systems, the software had to be made more “idiot-proof” so that a larger audience could use the same platform. Computer operators in the mainframe days understood what the systems expected, how to format input, and how to properly read output. When this power was put into individuals’ desktops, every imaginable (and unimaginable) input was used, which corrupted information and mangled operating systems.
Companies soon realized that employees had to be protected from themselves and that data had to be protected from mishaps and mistakes. The employees needed layers of software between them and the operating system components and data they could potentially destroy. Implementing these layers not only enhanced security—by separating users from the core of the operating systems and files—but also increased productivity as functionality continued to be inserted to make computers more useful to businesses and individuals.
As the computing world evolved, symbiotic relationships grew among the technological advances of hardware, circuitry, processing power, and software. Once a breakthrough was made that enabled a computer to contain more memory and hard drive space, new software was right on its heels to use it and demand more. When software hit a wall because it was not supplied with the necessary registers and control units, the hardware industry was Johnny-on-the-spot to develop and engineer the missing pieces to the equations. As the hardware end grew to provide a stable and rich platform for software, programmers developed software that provided functionality and possibilities not even conceived of a few years earlier. It has been a wonderful game of leapfrog that does not seem to have any end in sight.
Lovely story, but what does it mean to security?
In the beginning, the issues associated with bringing computing closer to individuals brought along many mistakes, technological hurdles, and operational issues not encountered in the workforce before. Computers are tools. Just as a knife can be a useful tool to cut meat and vegetables, it can also be a dangerous tool if it is in the hands of someone with malicious intent. The vast capabilities and functionality that computers have brought to society have also brought complex and troubling methods of destruction, fraud, abuse, and insecurity.
Because computers are built on layers (hardware platform, chips, operating systems, kernels, network stacks, services, and applications), these complex issues have been interwoven throughout the strata of computing environments. Plugging the holes, writing better software, and providing better perimeter security are often easier said than done because of the density of functionality within an infrastructure, interoperability issues, and the availability requirements of the necessary functionality.
Over a short period of time, people and businesses have come to depend greatly upon computer technology and automation in many different aspects of their lives. Computers run public utilities, military defense systems, financial institutions, and medical equipment, and are heavily used in every possible business sector. Almost every company relies on data processing for one reason or another. This level of dependence and the extent of integration that technology has attained in our lives have made security a much more necessary and essential discipline.
Computer security is a marathon to be run at a consistent and continual pace. It is not a short sprint, and it is not for those who lack dedication or discipline.
