Open Systems Interconnection Reference Model
I don’t understand what all of these protocols are doing.
Response: Okay, let’s make a model to explain it then.
ISO is a worldwide federation that works to provide international standards. In the early 1980s, ISO worked to develop a protocol set that would be used by all vendors throughout the world to allow the interconnection of network devices. This movement was fueled with the hopes of ensuring that all vendor products and technologies could communicate and interact across international and technical boundaries. The actual protocol set did not catch on as a standard, but the model of this protocol set, OSI model, was adopted and is used as an abstract framework to which most operating systems and protocols adhere.
Many people think that the OSI reference model arrived at the beginning of the computing age as we know it and helped shape and provide direction for many, if not all, networking technologies. However, this is not true. In fact, it was introduced in 1984, at which time the basics of the Internet had already been developed and implemented, and the basic Internet protocols had been in use for many years. The Transmission Control Protocol/Internet Protocol (TCP/IP) suite actually has its own model that is often used today when examining and understanding networking issues. Figure 7-1 shows the differences between the OSI and TCP/IP networking models. In this chapter, we will focus more on the OSI model.
Figure 7-1. The OSI and TCP/IP networking models

Note

| The host-to-host layer is sometimes called the transport layer in the TCP/IP model. |
Protocol
A network protocol is a standard set of rules that determines how systems will communicate across networks. Two different systems that use the same protocol can communicate and understand each other despite their differences, similar to how two people can communicate and understand each other by using the same language.
The OSI reference model, as described by ISO Standard 7498, provides important guidelines used by vendors, engineers, developers, and others. The model segments the networking tasks, protocols, and services into different layers. Each layer has its own responsibilities regarding how two computers communicate over a network. Each layer has certain functionalities, and the services and protocols that work within that layer fulfill them.
The OSI model’s goal is to help others develop products that will work within an open network architecture. An open network architecture is one that no vendor owns, that is not proprietary, and that can easily integrate various technologies and vendor implementations of those technologies. Vendors have used the OSI model as a jumping-off point for developing their own networking frameworks. These vendors used the OSI model as a blueprint and developed their own protocols and interfaces to produce functionality that is different from, or overlaps, that of other vendors. However, because these vendors use the OSI model as their starting place, integration of other vendor products is an easier task, and the interoperability issues are less burdensome than if the vendors had developed their own networking framework from scratch.
Although computers communicate in a physical sense (electronic signals are passed from one computer over a wire to the other computer), they also communicate through logical channels. Each protocol at a specific OSI layer on one computer communicates with a corresponding protocol operating at the same OSI layer on another computer. This happens through encapsulation.
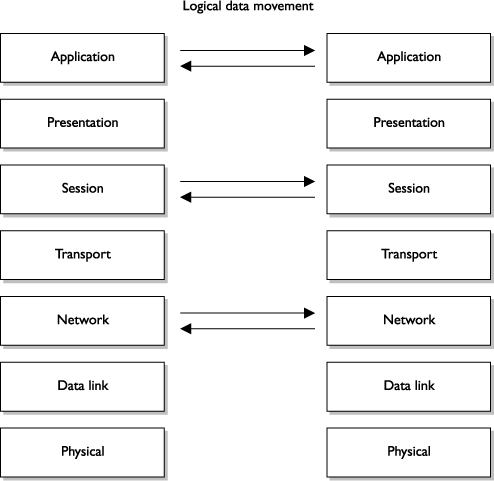
Here’s how encapsulation works: A message is constructed within a program on one computer and then passed down through the protocol’s stack. A protocol at each layer adds its own information to the message; thus, the message grows in size as it goes down the protocol stack. The message is then sent to the destination computer, and the encapsulation is reversed by taking the packet apart through the same steps used by the source computer that encapsulated it. At the data link layer, only the information pertaining to the data link layer is extracted, and the message is sent up to the next layer. Then at the network layer, only the network layer data are stripped and processed and the packet is again passed up to the next layer, and so on. This is how computers communicate logically. The information stripped off at the destination computer informs it how to interpret and process the packet properly. Data encapsulation is shown in Figure 7-2.
A protocol at each layer has specific responsibilities and control functions it performs, as well as data format syntaxes it expects. Each layer has a special interface (connection point) that allows it to interact with three other layers: 1) communications from the interface of the layer above it, 2) communications to the interface of the layer below it, and 3) communications with the same layer in the interface of the target packet address. The control functions, added by the protocols at each layer, are in the form of headers and trailers of the packet.
The benefit of modularizing these layers, and the functionality within each layer, is that various technologies, protocols, and services can interact with each other and provide the proper interfaces to enable communications. This means a computer can use an application protocol developed by Novell, a transport protocol developed by Apple, and a data link protocol developed by IBM to construct and send a message over the network. The protocols, technologies, and computers that operate within the OSI model are considered open systems. Open systems are capable of communicating with other open systems because they implement international standard protocols and interfaces. The specification for each layer’s interface is very structured, while the actual code that makes up the internal part of the software layer is not defined. This makes it easy for vendors to write plug-ins in a modularized manner. Systems are able to integrate the plug-ins into the network stack seamlessly, gaining the vendor-specific extensions and functions.
Understanding the functionalities that take place at each OSI layer and the corresponding protocols that work at those layers helps you understand the overall communication process between computers. Once you understand this process, a more detailed look at each protocol will show you the full range of options each protocol provides and the security weaknesses embedded into each of those options.
Application Layer
Hand me your information. I will take it from here.
The application layer, layer 7, works closest to the user and provides file transmissions, message exchanges, terminal sessions, and much more. This layer does not include the actual applications but rather the protocols that support the applications. When an application needs to send data over the network, it passes instructions and the data to the protocols that support it at the application layer. This layer processes and properly formats the data and passes the same down to the next layer within the OSI model. This happens until the data the application layer constructed contain the essential information from each layer necessary to transmit the data over the network. The data are then put on the network cable and are transmitted until that data arrive at the destination computer.
Some examples of the protocols working at this layer are the Simple Mail Transfer Protocol (SMTP), Hypertext Transfer Protocol (HTTP), Line Printer Daemon (LPD), File Transfer Protocol (FTP), Telnet, and Trivial File Transfer Protocol (TFTP). Figure 7-3 shows how applications communicate with the underlying protocols through application programming interfaces (APIs). If a user makes a request to send an e-mail message through her e-mail client Outlook, the e-mail client sends this information to SMTP. SMTP adds its information to the user’s information and passes it down to the presentation layer.
Figure 7-3. Applications send requests to an API, which is the interface to the supporting protocol.

Note

| The application layer in the TCP/IP architecture model is equivalent to a combination of the application, presentation, and session layers in the OSI model (refer to Figure 7-1). |
Presentation Layer
You will now be transformed into something that everyone can understand.
The presentation layer, layer 6, receives information from the application layer protocols and puts it in a format all computers following the OSI model can understand. This layer provides a common means of representing data in a structure that can be properly processed by the end system. This means that when a user constructs a Word document and sends it out to several people, it does not matter whether the receiving computer has different word processing programs; each of these computers will be able to receive this file and understand and present it to its user as a document. It is the data representation processing that is done at the presentation layer that enables this to take place. For example, when a Windows XP computer receives a file from another computer system, information within the file’s header explains what type of file it is. The Windows XP operating system has a list of file types it understands and a table describing what program should be used to open and manipulate each of these file types. For example, the sender could create a Word file in Word 2000, while the receiver uses Open Office. The receiver can open this file because the presentation layer on the sender’s system converted the file to American Standard Code for Information Interchange (ASCII), and the receiver’s computer knows it opens these types of files with its word processor, Open Office.
The presentation layer is not concerned with the meaning of data, but with the syntax and format of those data. It works as a translator, translating the format an application is using to a standard format used for passing messages over a network. If a user uses a Corel application to save a graphic, for example, the graphic could be a Tagged Image File Format (TIFF), Graphic Interchange Format (GIF), or Joint Photographic Experts Group (JPEG) format. The presentation layer adds information to tell the destination computer the file type and how to process and present it. This way, if the user sends this graphic to another user who does not have the Corel application, the user’s operating system can still present the graphic because it has been saved into a standard format. Figure 7-4 illustrates the conversion of a file into different standard file types.
Figure 7-4. The presentation layer receives data from the application layer and puts it into a standard format.

This layer also handles data compression and encryption issues. If a program requests a certain file to be compressed and encrypted before being transferred over the network, the presentation layer provides the necessary information for the destination computer. It includes instructions on the encryption or compression type used and how to properly present it to the user. Instructions are added to the data package that tell the receiving system how to decrypt or decompress the data properly.
Session Layer
I don’t want to talk to a computer. I want to talk to an application.
When two applications need to communicate, or transfer information, a connection session may need to be set up between them. The session layer, layer 5, is responsible for establishing a connection between the two applications, maintaining it during the transfer of data, and controlling the release of this connection. A good analogy for the functionality within this layer is a telephone conversation. When Kandy wants to call a friend, she uses the telephone. The telephone network circuitry and protocols set up the connection over the telephone lines and maintain that communication path, and when Kandy hangs up, they release all the resources they were using to keep that connection open.
Similar to how telephone circuitry works, the session layer works in three phases: connection establishment, data transfer, and connection release. It provides session restart and recovery if necessary and provides the overall maintenance of the session. When the conversation is over, this path is broken down and all parameters are set back to their original settings. This process is known as dialog management. Figure 7-5 depicts the three phases of a session. Some protocols that work at this layer are Network File System (NFS), Structured Query Language (SQL), NetBIOS, and remote procedure call (RPC).
Figure 7-5. The session layer sets up the connection, maintains it, and tears it down once communication is completed.
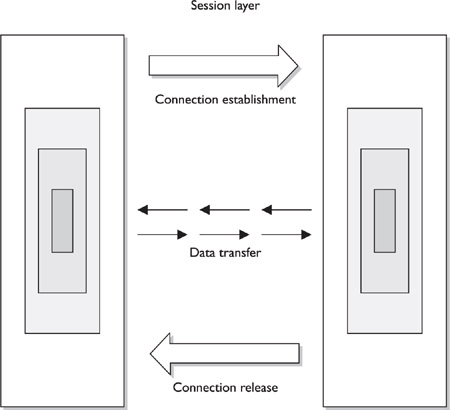
The session layer protocol can enable communication between two applications to happen in three different modes:
Simplex Communication takes place in one direction.
Half-duplex Communication takes place in both directions, but only one application can send information at a time.
Full-duplex Communication takes place in both directions, and both applications can send information at the same time.
Many people have a hard time understanding the difference between what takes place at the session layer versus the transport layer, because their definitions sound similar. Session layer protocols control application-to-application communication, whereas the transport layer protocols handle computer-to-computer communication. For example, if you are using a product that is working in a client/server model, in reality you have a small piece of the product on your computer (client portion) and the larger piece of the software product is running on a different computer (server portion). The communication between these two pieces of the same software product needs to be controlled, which is why session layer protocols even exist. Session layer protocols take on the functionality of middleware, which allows software on two different computers to communicate. The next section will dive into the functionality of the transport layer protocols.
Transport Layer
How do I know if I lose a piece of the message?
Response: The transport layer will fix it for you.
When two computers are going to communicate through a connection-oriented protocol, they will first agree on how much information each computer will send at a time, how to verify the integrity of the data once received, and how to determine whether a packet was lost along the way. The two computers agree on these parameters through a handshaking process at the transport layer, layer 4. The agreement on these issues before transferring data helps provide more reliable data transfer, error detection, correction, recovery, and flow control, and it optimizes the network services needed to perform these tasks. The transport layer provides end-to-end data transport services and establishes the logical connection between two communicating computers.
Note

| Connection-oriented protocols, such as TCP, provide reliable data transmission when compared to connectionless protocols, such as UDP. This distinction is covered in more detail in the “TCP/IP” section, later in the chapter. |
The functionality of the session and transport layers is similar insofar as they both set up some type of session or virtual connection for communication to take place. The difference is that protocols that work at the session layer set up connections between applications, whereas protocols that work at the transport layer set up connections between computer systems. For example, we can have three different applications on computer A communicating to three applications on computer B. The session layer protocols keep track of these different sessions. You can think of the transport layer protocol as the bus. It does not know or care what applications are communicating with each other. It just provides the mechanism to get the data from one system to another.
The transport layer receives data from many different applications and assembles the data into a stream to be properly transmitted over the network. The main protocols that work at this layer are TCP, User Datagram Protocol (UDP), and Sequenced Packet Exchange (SPX). Information is passed down from different entities at higher layers to the transport layer, which must assemble the information into a stream, as shown in Figure 7-6. The stream is made up of the various data segments passed to it. Just like a bus can carry a variety of people, the transport layer protocol can carry a variety of application data types. (The host-to-host, or transport, layer in the TCP/IP architecture model is equivalent to the transport layer in the OSI model. See Figure 7-1.)
Figure 7-6. TCP formats data from applications into a stream to be prepared for transmission.

Note

| Different references can place specific protocols at different layers. For example, many references place the Secure Sockets Layer (SSL) protocol in the session layer, while other references place it in the transport layer. It is not that one is right or wrong. The OSI model tries to draw boxes around reality, but some protocols straddle the different layers. SSL is made up of two protocols—one works in the lower portion of the session layer and the other works in the transport layer. For purposes of the CISSP exam, SSL resides in the transport layer. |
Network Layer
Many roads lead to Rome.
The main responsibilities of the network layer, layer 3, are to insert information into the packet’s header so it can be properly addressed and routed, and then to actually route the packets to their proper destination. In a network, many routes can lead to one destination. The protocols at the network layer must determine the best path for the packet to take. Routing protocols build and maintain their routing tables at this layer. These tables are maps of the network, and when a packet must be sent from computer A to computer M, the protocols check the routing table, add the necessary information to the packet’s header, and send it on its way.
The protocols that work at this layer do not ensure the delivery of the packets. They depend on the protocols at the transport layer to catch any problems and resend packets if necessary. IP is a common protocol working at the network layer, although other routing and routed protocols work there as well. Some of the other protocols are the Internet Control Message Protocol (ICMP), Routing Information Protocol (RIP), Open Shortest Path First (OSPF), Border Gateway Protocol (BGP), and Internet Group Management Protocol (IGMP). Figure 7-7 shows that a packet can take many routes and that the network layer enters routing information into the header to help the packet arrive at its destination. (The Internet layer in the TCP/IP architecture model is equivalent to the network layer in the OSI model. See Figure 7-1.)
Figure 7-7. The network layer determines the most efficient path for each packet to take.

Data Link Layer
As we continue down the protocol stack, we are getting closer to the actual network wire over which all these data will travel. The outer format of the data packet changes slightly at each layer, and it comes to a point where it needs to be translated into local area network (LAN) or wide area network (WAN) technology binary format for proper line transmission. This happens at the data link layer.
Note

| APSTNDP—To remember all the layers within the OSI model in the correct order, memorize “All People Seem To Need Data Processing.” Remember that you are starting at layer 7, the application layer, at the top. |
LAN and WAN technologies can use different protocols, network interface cards (NICs), cables, and transmission methods. Each of these technologies has different data format structures, and they interpret electricity voltages in different ways. The data link layer, layer 2, is where the network stack knows what format the data frame must be in to transmit properly over Token Ring, Ethernet, ATM, or Fiber Distributed Data Interface (FDDI) networks. If the network is an Ethernet network, for example, all the computers will expect the header to be a certain length, the flags to be positioned in a certain place within the packet, and the trailer information to be in a certain place with specific fields. On a Token Ring network, the computers would expect most of these parameters to be in different places and the frames to have particular formats. The data link layer is responsible for proper communication within these technologies and for changing the data into the necessary format for the physical layer. It will also manage to reorder frames that are received out of sequence, and notify upper-layer protocols when there are transmission error conditions.
The data link layer is divided into two functional sublayers, the Logical Link Control (LLC) and the Media Access Control (MAC). The LLC, defined in the IEEE 802.2 specification, communicates with the protocol immediately above it, the network layer. The MAC will have the appropriately loaded protocols to interface with the protocol requirements of the physical layer. The IEEE MAC specification for Ethernet is 802.3, Token Ring is 802.5, wireless LAN is 802.11, and so on. So when you see a reference to an IEEE standard, such as 802.11, 802.16, 802.3, and so on, it refers to the protocol working at the MAC sublayer of the data link layer of a protocol stack.
Some of the protocols that work at the data link layer are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Reverse Address Resolution Protocol (RARP), Layer 2 Forwarding (L2F), Layer 2 Tunneling Protocol (L2TP), FDDI, and Integrated Services Digital Network (ISDN). Figure 7-8 shows how the data link layer converts the information into bits and the physical layer converts those bits into electrical signals. (The network interface layer in the TCP/IP architecture model is equivalent to a combination of the data link and physical layers in the OSI model. See Figure 7-1.)
Figure 7-8. The data link layer converts the data into bits for the physical layer.
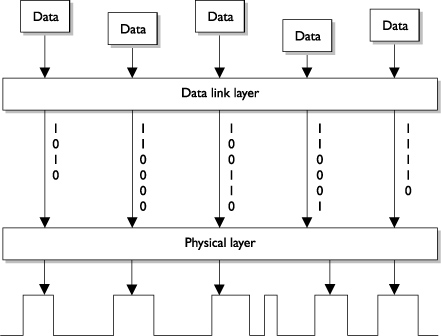
Each network technology (Ethernet, Token Ring, and so on) defines the compatible physical transmission type (coaxial, twisted pair, or fiber) that is required to enable network communication. Each network technology also has defined electronic signaling and bit patterns. This means, for example, that a signal of 0.5 volts may represent a 0 on one technology and a 1 on another technology. The data link layer protocol specifies the proper bit patterns, and the physical layer protocol translates this information into electrical encoding and electricity state transitions. Network cards bridge the data link and physical layers. Information is passed down through the first six layers and reaches the network card driver at the data link layer. Depending on the network technology being used (Ethernet, Token Ring, FDDI, and so on), the network card driver encodes the bits at the data link layer, which are then turned into electricity states at the physical layer and placed onto the wire for transmission.
Physical Layer
Everything ends up as electrical signals anyway.
The physical layer, layer 1, converts bits into voltage for transmission. Signals and voltage schemes have different meanings for different LAN and WAN technologies. If a user sends data through his dial-up software and out his modem onto a telephone line, the data format, electrical signals, and control functionality are much different than if that user sends data through the NIC and onto a unshielded twisted pair (UTP) wire for LAN communication. The mechanisms that control this data going onto the telephone line, or the UTP wire, work at the physical layer. This layer controls synchronization, data rates, line noise, and medium access. Specifications for the physical layer include the timing of voltage changes, voltage levels, and the physical connectors for electrical, optical, and mechanical transmission.
Functions and Protocols in the OSI Model
For the exam, you will need to know the functionality that takes place at the different layers of the OSI model, along with specific protocols that work at each layer. The following is a quick overview of each layer and its components.
Application
The protocols at the application layer handle file transfer, virtual terminals, network management, and fulfilling networking requests of applications. A few of the protocols that work at this layer include:
File Transfer Protocol (FTP)
Trivial File Transfer Protocol (TFTP)
Simple Network Management Protocol (SNMP)
Simple Mail Transfer Protocol (SMTP)
Hypertext Transfer Protocol (HTTP)
Presentation
The services of the presentation layer handle translation into standard formats, data compression and decompression, and data encryption and decryption. No protocols work at this layer, just services. The following lists some of the presentation layer standards:
American Standard Code for Information Interchange (ASCII)
Extended Binary-Coded Decimal Interchange Mode (EBCDIC)
Tagged Image File Format (TIFF)
Joint Photographic Experts Group (JPEG)
Motion Picture Experts Group (MPEG)
Musical Instrument Digital Interface (MIDI)
Session
The session layer protocols set up connections between applications, maintain dialog control, and negotiate, establish, maintain, and tear down the communication channel. Some of the protocols that work at this layer include:
Network File System (NFS)
NetBIOS
Structured Query Language (SQL)
Remote procedure call (RPC)
Transport
The protocols at the transport layer handle end-to-end transmission and segmentation into a data stream. The following protocols work at this layer:
Transmission Control Protocol (TCP)
User Datagram Protocol (UDP)
Secure Sockets Layer (SSL)
Sequenced Packet Exchange (SPX)
Network
The responsibilities of the network layer protocols include internetworking service, addressing, and routing. The following lists some of the protocols that work at this layer:
Internet Protocol (IP)
Internet Control Message Protocol (ICMP)
Internet Group Management Protocol (IGMP)
Routing Information Protocol (RIP)
Open Shortest Path First (OSPF)
Novel Internetwork Packet Exchange (IPX)
Data Link
The protocols at the data link layer convert data into LAN or WAN frames for transmission, convert messages into bits, and define how a computer accesses a network. This layer is divided into the Logical Link Control (LLC) and the Media Access Control (MAC) sublayers. Some protocols that work at this layer include the following:
Address Resolution Protocol (ARP)
Reverse Address Resolution Protocol (RARP)
Point-to-Point Protocol (PPP)
Serial Line Internet Protocol (SLIP)
Physical
Network interface cards and drivers convert bits into electrical signals, and control the physical aspects of data transmission, including optical, electrical, and mechanical requirements. The following are some of the standard interfaces at this layer:
High-Speed Serial Interface (HSSI)
X.21
EIA/TIA-232 and EIA/TIA-449
Note

| The security services defined in the OSI security model include data integrity (protection from modification and destruction), data confidentiality (protection from disclosure), authentication (verification of identity of the communication source), and access control services (enable mechanisms to allow or restrict access). |
Tying the Layers Together
Pick up all of these protocols from the floor and put them into a stack—a network stack.
The OSI model is used as a framework for many products and many types of vendors. Various types of devices and protocols work at different parts of this seven-layer model. Whereas computers can interpret and process data at each of the seven layers, routers can understand information only up to the network layer, because a router’s main function is to route packets, which does not require knowledge about any further information within the packet. A router peels back the header information until it reaches the network layer data, where the routing and IP address information is located. The router looks at this information to make its decisions on where the packet should be sent next. Bridges understand only up to the data link layer, and repeaters understand data only at the physical layer. Figure 7-9 shows what level of the OSI model each type of device understands.
References
Protocols.com listing of data communications protocols www.protocols.com
Google listings of protocols http://directory.google.com/Top/Computers/Internet/Protocols
Linktionary definition of OSI model www.linktionary.com/o/osi.html
Wikipedia entry for OSI model http://en.wikipedia.org/wiki/OSI_model


