Chapter 12. Understanding Cybercrime Prevention
Topics we'll investigate in this chapter:
▪ Understanding Basic Cryptography Concepts
▪ Making the Most of Hardware and Software Security
▪ Understanding Firewalls
▪ Forming an Incident Response Team
▪ Designing and Implementing Security Policies
Summary
Frequently Asked Questions
Introduction
Understanding what cybercrime is and how cybercrimes can be committed gives an investigator only half the picture. Just as every police officer needs a good grasp of physical defensive tactics, the cybercrime investigator must be aware of the tactics that are commonly used to defend a network from criminal intrusion or attack. In this chapter, we discuss the basic concepts involved in computer and network security. This includes the importance of multilayered security and the components that make up a multilayered security plan. We also emphasize the need for investigators to “talk the talk” by learning computer security terminology.
We delve into the fascinating and complex world of cryptography, the study of “hidden writing.” We look at encryption technologies and algorithms and the many ways in which encryption can be used to protect data stored on computers or traveling across the network. You'll learn about the purposes of encryption in the context of network security and how it can provide for authentication, data confidentiality, and data integrity. We provide a brief history of cryptography and discuss common encryption protocols in use today. We also explain the differences between encryption and steganography and how these two techniques are used together for stronger security—by both the good guys and the cybercriminals. Finally, we discuss cryptanalysis and decryption techniques and how cryptographic software is being used today as a terrorist tool.
Moving from theory to implementation, we next discuss how organizations can make the most of both hardware- and software-based security products to protect their networks. First, we look at hardware devices, including firewall appliances. Then we discuss software-based security solutions, including cryptographic software, digital certificates, and the public key infrastructure.
The next section takes us into how firewalls—both hardware- and software-based—work “under the hood.” You'll learn about layered filtering and how the best firewalls provide protection at the packet, circuit, and application levels. Then we discuss integrated intrusion detection and the way that many firewall products can be configured to perform predefined attacks when an attack occurs.
After covering the specifics of available security products, we turn to another aspect of creating an overall security plan—the issue of how to form an incident response team to deal quickly and effectively with attacks when they occur. But having a team in place will not provide the protection that an organization needs unless the team—and the users and information technology (IT) professionals who make up the “human side” of the network—are governed by specific, detailed security policies that bring the organization's security plan into focus and incorporate it into the everyday use of the systems and network. Thus, the last section of this chapter deals with why and how solid security policies can be developed and put in place, creating a foundation for the implementation of all the security measures that we've addressed as well as laying the cornerstone of the organization's cybercrime prevention plan.
Understanding Security Concepts
In Chapter 10, you learned about “technical” intrusions and attacks on networks and how hackers (and hacker wannabes) can exploit protocols, operating systems, and applications to commit the criminal acts of unauthorized access, interrupting network communications, and destroying or damaging computer data. It is important for investigators to have at least a basic understanding of how these attacks are carried out. It is also important for investigators to be aware of how networks can be defended from further attacks, for several reasons:
▪ Understanding how various security measures work can lead investigators to log files and other sources of information useful in the investigation.
▪ Knowledge of security measures and concepts allows investigators to suggest to victims how they might prevent further incidents.
▪ Some of the measures used by the “good guys” to protect their networks and data (such as encryption) can also be used by the “bad guys” to cover their criminal activities.
Knowledge is power. That's a famous hacker motto (along with such other gems as “Information wants to be free”). However, it is a truism that applies not only to people attempting to gain access to data they aren't supposed to see, but also to those who are trying to protect themselves from the intruders. The first step in winning any battle—and network security is a battle over the ownership and control of your computer files—is the same as it's always been: “Know thine enemy.”
To protect a network's resources from theft, damage, or unwanted exposure, administrators must understand who initiates these things, why, and how they do it. Knowledge will make you, the investigator, powerful, too—and better able to track down and prosecute unauthorized intruders and attackers.
Applying Security Planning Basics
Securing a company's electronic assets from cybercriminals must involve much more than the IT department; it must involve the entire organization—just as a community policing effort, to be effective, must involve the police department as a whole and not just an isolated “community service division.” For cyberinvestigators to understand the security planning and implementation process, they need to start at the beginning, with the very basics of computer security. The following sections illustrate how some of the most basic tenets of traditional security can be applied to the context of computer networking.
Defining Security
A generic dictionary definition of security (taken from the American Heritage Dictionary) is “freedom from risk or danger; safety.” This definition is perhaps a little misleading when it comes to computer and networking security, because it implies a degree of protection that is inherently impossible in the modern connectivity-oriented computing environment.
This is why the same dictionary provides another definition, specific to computer science: “The level to which a program or device is safe from unauthorized use” [emphasis added]. Implicit in this definition is the caveat that the objectives of security and accessibility—the two top priorities on the minds of many network administrators—are, by their very nature, diametrically opposed. The more accessible the data, the less secure it is. Likewise, the more tightly you secure the data, the more you impede accessibility. Any security plan is an attempt to strike the proper balance between the two objectives.
The first step is to determine what needs to be protected, and to what degree. Because not every asset is equally valuable, some assets need stronger protection than others. This determination leads to the concept of instituting multiple layers of security.
The Importance of Multilayered Security
An effective security plan does not rely on one technology or solution, but instead takes a multilayered approach. Compare this approach to a business's physical security measures; most companies don't depend on just the locks on the buildings' doors to keep intruders and thieves out. Instead, they might also have perimeter security (a fence), perhaps additional external security such as a guard or guard dog, external and internal alarm systems, and to protect special valuables, further internal safeguards such as a vault. IT security should be similarly layered. For example:
▪ Firewalls at network entry points (and possibly a demilitarized zone [DMZ] or screened subnet between the local area network [LAN] and the network interface connected to the Internet) that function as perimeter protection
▪ Password protection at local computers, requiring user authentication to log on, to keep unauthorized persons out
▪ Access permissions set on individual network resources to restrict access of those who are “in” (logged on to the network)
▪ Encryption of data sent across the network or stored on disk to protect what is especially valuable, sensitive, or confidential
▪ Servers, routers, and hubs located in locked rooms to prevent people with physical access from hijacking data without authorization
The Intrusion Triangle
Crime prevention specialists use a model called the Crime Triangle to explain that certain criteria must exist before a crime can occur. We can adapt this same familiar law enforcement concept to network security: The same three criteria in the Crime Triangle must exist before a network security breach can take place. Figure 12.1 shows the three “legs,” or points of the triangle.
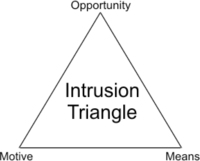 |
| Figure 12.1 The Three Legs of the Crime Triangle That Must Exist for a Network Intrusion to Occur |
Let's look at each point on the triangle individually:
▪ Motive An intruder must have a reason to want to breach the security of the network (even if the reason is “just for fun”); otherwise, he or she won't bother.
▪ Means An intruder must have the ability (either the programming knowledge or, in the case of script kiddies, the intrusion software written by others) or he or she won't be able to breach your security.
▪ Opportunity An intruder must have the chance to enter the network because of flaws in the security plan, holes in a software program that open an avenue of access, or physical proximity to network components. If there is no opportunity to intrude, the would-be hacker will go elsewhere.
If you think about the three-point intrusion criteria for a moment, you'll see that the network administrator or security specialist has control over only one leg of the triangle. It is unlikely that anyone can do much to remove the intruder's motive. The motive is likely to be built into the type of data that's on the network or even the personality of the intruder him- or herself. It is also not often possible to prevent the intruder from having or obtaining the means to breach your security. Programming knowledge is freely available, and many experienced hackers are more than happy to help less sophisticated ones. The one thing that people who strive to prevent cybercrime can affect is the opportunity afforded the hacker.
Removing Intrusion Opportunities
Crime prevention officers tell members of the community that they probably can't keep a potential burglar from wanting to steal, and they certainly can't keep the potential burglar from obtaining burglary tools or learning the “tricks of the trade.” What they can do is to take away, as much as possible, the opportunity for the burglar to target their own homes.
This means putting deadbolt locks on house doors (and using them); getting a big, loud dog that is unfriendly to strangers; and installing an alarm system. In other words, the homeowner's goal is not to prevent the burglar from burglarizing, but to make his or her own home a less desirable target. For network “owners,” the objective is to “harden” the network so that all those hackers out there who already have the motive and the means will look for an easier victim.
The best and most expensive locks in the world won't keep intruders out of your house if you don't use them. And if those locks are difficult to use and they cause you inconvenience in your everyday comings and goings, you probably won't use them—at least, not all the time. A poorly implemented network security system that is difficult to administer or that unduly inconveniences network users might end up similarly; eventually the person burdened with maintaining it will throw his or her hands up in frustration and just turn the darn thing off. And that will leave the network wide open to intruders.
Talking the Talk: Security Terminology
Every industry has its own “language,” the jargon that describes ideas, items, concepts, and procedures that are unique to the field. Lawyers speak “legalese,” rife with wherefores and hereuntos; doctors and nurses use terms such as crash cart and defib, and police reports are sprinkled with references to perpsand vics and MVAs. Computer networking is infamous for its “technotalk” and the proliferation of acronyms which often mystify outsiders. Specialty areas within an industry often have their own brands of jargon as well, and the computer security subfield is no exception.
It might not be absolutely necessary for the cybercrime investigator to understand all the technical aspects of how security measures work, but knowledge of the technical language used to describe security concepts and devices will serve a couple of important purposes:
▪ It will make you aware of what a hacker can and can't accomplish in a particular network environment.
▪ If you are able to “talk the talk”—to converse intelligently about security issues and measures—you will be better able to win the trust of and communicate with the IT professionals who provide much of the information necessary to your investigation.
It is not possible to provide a complete glossary of security-related terms within the scope of this chapter, but in this section, we define some of the more common words and phrases that you might encounter as you begin to explore the fascinating world of computer security:
▪ Authentication Verification of identity of a user, computer, or process.
▪ Authorization The actions that a user, computer, or process, once identified, is permitted to do.
▪ Audit To track security-related events, such as logging on to the system or network, accessing objects, or exercising user/group rights or privileges.
▪ Breach Successfully defeating security measures to gain access to data or resources without authorization, to make data or resources available to unauthorized persons, or to delete or alter computer files.
▪ Cipher A method used to encrypt data.
▪ Cipher text Data in encrypted form.
▪ Confidentiality of data Ensuring that the contents of messages will be kept secret. See also integrity of data.
▪ Cryptography (crypto) The science of hiding information.
▪ Encryption The process of converting data (plain text) into a format (cipher text) that cannot be read or understood by anyone except those authorized to receive it.
▪ Encryption algorithm A formula or calculation that is applied to data to encrypt, or scramble, it.
▪ Integrity of data Ensuring that data has not been modified or altered, that the data received is identical to the data that was sent.
▪ Key A variable that is used in conjunction with an algorithm to encrypt or decrypt data.
▪ Penetration testing Evaluating a system by attempting to circumvent the computer's or network's security measures.
▪ Reliability The probability of a computer system or network continuing to perform in a satisfactory manner for a specific time period under normal operating conditions.
▪ Risk management The process of identifying, controlling, and either minimizing or completely eliminating events that pose a threat to system reliability, data integrity, and data confidentiality.
▪ TCSEC Trusted Computer System Evaluation Criteria, a method for evaluating a system's level of security.
▪ Technical vulnerability A flaw or bug in the hardware or software components of a system that leaves it vulnerable to security breach.
▪ Vulnerability A weakness in the hardware, software, or security plan that leaves a system or network open to the threat of unauthorized access or damage to or destruction of data.
Note
You can find extensive lists of definitions for security-related terms on the Internet by visiting such sites as www.whatis.com and www.mobrien.com/terminology.shtml
Understanding Basic Cryptography Concepts
Cryptography is a word derived from the Greek kryptos (“hidden”), and the use of cryptography predates the computer age by hundreds of years. Keeping secrets has long been a concern of human beings, and the purpose of cryptography is to hide information or change it so that it is incomprehensible to people for whom it is not intended. Cryptographic techniques include:
▪ Encryption, which involves applying a procedure called an algorithm to plain text to turn it into something that will appear to be gibberish to anyone who doesn't have the key to decrypt it.
▪ Steganography, which is a means of hiding the existence of the data, not just its contents. This is usually done by concealing it within other, innocuous data.
Note
The words cryptography and encryption are often used interchangeably, but cryptography is a much broader term than encryption; encryption is a form of cryptography. In other words, all encryption is cryptography, but not all cryptography is encryption.
Understanding the Purposes of Cryptographic Security
Cryptographic techniques are an important part of a multilayered security plan. Some security measures, such as implementation of a firewall and use of access permissions, attempt to keep intruders out of the network or computer altogether, much like fences and door locks attempt to keep burglars off the grounds or out of the house. Cryptography provides an inner line of defense. Like a wall safe that is there in case the burglars do make it inside your house—and to protect valuables from people who are authorized to come into your house—cryptography protects data from intruders who are able to penetrate the outer network defenses and from those who are authorized to access the network but not this particular data.
Cryptographic techniques concern themselves with three basic purposes:
▪ Authentication Verifying the identity of a user or computer
▪ Confidentiality Keeping the contents of the data secret
▪ Integrity Ensuring that data doesn't change between the time it leaves the source and the time it reaches its destination
One or more of these goals may be a priority, depending on the situation. For example, if an investigator receives a message from his or her chief to fly to the West Coast to interview a witness in a case, the overriding concern might be to know that it was, indeed, the chief of police who sent the message and not a fellow officer playing a practical joke. In this case, authentication of the message sender's identity is of utmost importance. If the case relates to an internal affairs investigation and it is important that no one else in the department know where the investigator is going, confidentiality of the data might be important as well. And if the message states that the investigator is authorized to spend $3,000 on the trip, it might be important to ensure that the message has not been changed (after all, chiefs are not usually this generous) in transit—in other words, that the message's integrity has not been compromised.
All three mechanisms can be used together, or they can be used separately when only one or two of these considerations are important. In the following sections, we look more closely at how each one works in relation to network security.
A Historical Perspective on Cryptography
Cryptography has probably been around for almost as long as written language. According to A Short History of Cryptography, by Fred Cohen (www.all.net/books/ip/Chap2-1.html), the study of cryptography has been around for 4,000 years or more. Whenever communications are recorded, the issue of protecting those recorded communications arises.
In both business and personal communications, it is often not desirable to share the contents with everyone—in fact, in many cases doing so could have disastrous results. Thus, early civilizations looked for ways to conceal the contents of messages from prying eyes. In ancient Egypt, deviations on the hieroglyphic language in use were developed for that purpose. The Greeks used a “transposition code” in which each letter of the alphabet was represented by another that indicated where, in a grid, the original letter was located. In early India, spies employed by the government used phonetic-based “substitution codes” (the same concept children use for pig Latin). In biblical times, a substitution cipher called atbash, which worked by replacing the last letter of the Hebrew alphabet with the first and so on, was used to encrypt writings. Encryption methods were used by such diverse historical figures as Julius Caesar (after whom the “Caesar cipher” was named), Thomas Jefferson (who invented the cipher wheel), and Sir Francis Bacon. Governments have long used encryption to protect sensitive military messages.
Authenticating Identity
As we discussed in Chapter 11, you can determine the identity of a user or computer in numerous ways, but it generally requires that the user provide something that is associated with his or her user account that someone else could not easily provide. The requested credential is generally one (or more) of the following:
▪ Something you know, such as a password or personal identification number (PIN)
▪ Something you have, such as a smart card or certificate
▪ Something you are, in which biometric devices are used to identify you on the basis of your physical characteristics
Because none of these authentication methods (or any other) is absolutely foolproof, it makes sense in a high-security environment to use a multifactor authentication system (sometimes called two-way or three-way authentication, depending on the number of authentication methods used) by combining two or more of them. That is, a user is required to provide both something he or she has and something he or she knows (in fact, most smart card implementations require that the user not only insert the card in a reader, but also enter a PIN), or the user must both undergo a biometric scan and provide a password before being granted access.
Another method of implementation is layered authentication, in which one form of authentication is accepted to provide a lower level of access, and additional authentication is required for a higher level of access.
Note
Some security literature mentions a fourth means of proving identity: something you do. An example would be a sample of your handwriting. Voice prints might also be considered to be in this category.
As we saw in Chapter 11, a wide number of protocols are used for authenticating users on a network, many of which use various types of encryption to ensure that the data being passed by the user to the authentication server can't be intercepted and viewed by others. Some of these protocols include:
▪ Kerberos A logon authentication protocol that is based on secret key (symmetric) cryptography. It usually uses the Data Encryption Standard (DES) or Triple-DES (3DES) algorithm, although with the latest version, Kerberos Version 5, algorithms other than DES can be used. Kerberos uses a system of “tickets” to provide verification of identity to multiple servers throughout the network. This system works a little like the payment system at some amusement parks and fairs where, instead of paying to ride each ride, customers must buy tickets at a central location and then use those tickets to access the rides. Similarly, with Kerberos, a client who wants to access resources on network servers is not authenticated by each server; instead, all the servers rely on “tickets” issued by a central server, called the Key Distribution Center (KDC). The client sends a request for a ticket (encrypted with the client's key) to the KDC. The KDC issues a ticket called a Ticket-Granting Ticket (TGT), which is encrypted and submitted to the Ticket-Granting Service (TGS). The TGS can be running on the same physical machine that is running the KDC. The TGS issues a session ticket to the client for accessing the particular network resource that was requested (which is usually on a different server). The session ticket is presented to the server that hosts the resource, and access is granted. The session key is valid only for that particular session and is set to expire after a specific amount of time. Kerberos allows mutual authentication; that is, the identities of both the client and the server can be verified.
▪ NT LAN Manager (NTLM) Another Microsoft logon authentication method. Unlike Kerberos, with NTLM, when a client wants to access a server's resources, that server must contact the domain controller to have the client's identity verified. It uses MD4/MD5 hashing algorithms and DES encryption.
▪ Shiva Password Authentication Protocol (S-PAP) A remote access authentication protocol used for Point-to-Point Protocol (PPP) or dial-up connections. Shiva PAP (S-PAP) uses a two-way reversible authentication method that encrypts passwords so that they will not be subject to interception and misuse.
▪ Challenge Handshake Authentication Protocol (CHAP) Uses a hashing algorithm and a shared secret (more about that later in this chapter, in the section on encryption) to protect the password. CHAP provides more security than PAP. Microsoft developed its own version of the protocol, called MS-CHAP, which uses the DES encryption algorithm and LM/NTHASH.
▪ The Remote Authentication Dial-In User Service (RADIUS) Also used for authenticating remote connections. Exchanges are encrypted using a shared key, and multiple RAD-IUS servers can communicate with each other and exchange authentication information.
▪ Secure Shell (SSH) Allows users to log on to UNIX systems remotely. When using SSH, both ends of the connection (client and server) are authenticated, and data (including passwords) can be encrypted. 3DES, Blowfish, and Twofish are encryption algorithms that are supported by SSHv2, which also allows the use of smart cards.
A concept that is closely related to authentication is nonrepudiation. This is a means of ensuring that whoever sends a message cannot later claim that he or she didn't send it. Nonrepudiation is sometimes considered to be a fourth, separate purpose of cryptography, but we include it here in the discussion of authentication because the two concepts go together; nonrepudiation just goes a step further than authentication.
Providing Confidentiality of Data
Confidentiality refers to any method that keeps the contents of the data secret. Usually this means encrypting it to prevent unauthorized persons from understanding what the data says even if they intercept it. In a high-security environment, where network communications necessarily involve information that should not be shared with the world, it is important to use strong encryption to protect the confidentiality of sensitive data. We discuss exactly how that is done in the upcoming “Basic Cryptography Concepts” section.
Ensuring Data Integrity
Data integrity, in the context of cryptography, means that there is a way to verify that the data was not changed after it left the sender, that the data that was sent is exactly the same as the data that is received at the final destination. It is essential to be able to count on data integrity in network transactions such as e-commerce.
Note
The term data integrity has a broader meaning in terms of general computing and networking than it does in the context of cryptography. In this sense, it refers to protection of data from damage or destruction; the integrity of data can be threatened by a power surge, a magnetic field, fire, flood, or the like as well as by persons who would deliberately modify it. You can install utilities such as Tripwire (www.tripwire.org) to monitor changes to system data on the hard disk.
Basic Cryptography Concepts
Cryptographic techniques such as encryption are the basis of digital certificates, digital signatures, and the public key infrastructure, or PKI. All of these technologies are important components of an enterprise-level security plan, and we discuss the use of each later in this chapter. Now that you understand the purposes of cryptography, we can look at the mechanics of how these technologies are implemented.
Scrambling Text with Codes and Ciphers
There are many different ways to “scramble” text or hide its meaning in such a way that only authorized persons (at least in theory) are able to read it. This scrambled (encrypted) text is called cipher text. A method for encrypting text is called a cipher or a code. Technically, a code uses substitution at the word or phrase level, whereas a cipher works at the level of individual letters or digits. The two words are often used interchangeably, but computerized cryptographic techniques generally rely on ciphers that operate on the binary form of the data by applying an algorithm (a mathematical calculation). Some common cipher/code types are:
▪ Substitution
▪ Transposition
▪ Obscure languages
Substitution Ciphers
Simple substitution is a method often used by children in their first experiments with secret code. A substitution cipher merely substitutes different letters, numbers, or other characters for each character in the original text. The most straightforward example is a simplistic substitution in which each letter of the alphabet is represented by a numerical digit, starting with 1 for A. The message goodbye then becomes 7-15-15-4-2-25-5. This code is obviously extremely easy to break.
The Caesar Cipher used a simple shifting method, in which each letter of the message is represented by the letter two places to the right in the alphabet (A becomes C, B becomes D, and so on). Other substitution methods can be much more difficult to crack. For example, if two parties exchanging communications have an identical copy of a particular book, they might create a message by referencing page, line, and word numbers (for example, 73-12-6 tells you that the word in the message is the same as the sixth word in the twelfth line on page 72 of the code book). In this case, anyone who doesn't have a copy of the book (and to cite the correct pages, it must be the exact same edition and print run) will not be able to decipher the message.
Some types of substitution ciphers are:
▪ Monoalphabetic substitution Each letter is represented by another letter or character in a one-to-one relationship.
▪ Polyalphabetic substitution Different cipher-text characters can represent the same plain-text letter, making it more difficult to decrypt messages using the frequency analysis technique. Renaissance architect and art theorist Leon Battista Alberti is credited with developing this technique, earning him recognition as the “father of Western cryptography.”
▪ Polygraphic (block) cipher Several letters (or digits when we're dealing with binary data) are encrypted at the same time, using a system that can handle all the possible combinations of a set number of characters.
▪ Fractionation Multiple symbols are substituted for each plain-text letter, and then the letters or digits are transposed.
Transposition Ciphers
Transposition ciphers use tables in which the plain text is entered one way, and then read another way to create the encrypted text. For example, each character of text is entered into the table cells going across from left to right, and then the cipher text is produced by reading the characters in columns. A variation uses a square grid with holes that is placed on top of a sheet of paper, and then the message is written, rotating the grid at intervals.
Obscure Languages As Code
Obscure languages have been used as code by governments for military communications. Ancient (“dead”) languages have been used in this way. The U.S. military even used Navajo “code talkers” (speakers of the complex and little known Navajo language) in World War II to send secret communications. This language was chosen because it was hard to learn, and only a few people in the world knew it. The Navajo language had never been written, which made it even more obscure. Members of the Navajo tribe were recruited to develop a code based on the language.
Mechanical and Electrical Cipher Devices
Cipher devices such as cipher wheels and cylinders can be used to encrypt and decrypt text. An early example of this technique was the skytale cipher or staff cipher used by the Spartans. They wrapped a sheet of papyrus around a staff and wrote their message down the length of the staff. When the sheet was unwrapped, the message couldn't be easily read unless it was wrapped around a staff of the same diameter as the original one.
Leon Battista Alberti used a set of disks that had the alphabet etched on them to employ his polyalphabetic ciphering system. He lined up the two disks to determine what cipher-text character would represent each plain-text letter. By rotating the disks at set intervals, he caused different cipher-text letters to represent the same plain-text letters at different places in the message.
Many different cipher machines have been developed by government and military entities. Most use multiple rotating disks to create letter substitutions, and they can be operated either mechanically or electrically. Thomas Jefferson invented a cipher wheel of this type. During World War II, the Japanese used cipher machines called RED and PURPLE, and the German Enigma machine (a wired rotor machine that has equally spaced electrical contacts on each side of a disk, which are connected to one another in scrambled order) is perhaps the most famous—or infamous—of the cipher devices.
Computerizing the Ciphering Process
The availability of computer technology made it much easier to encrypt messages using very complex methods that would be difficult or impossible to use by hand or with mechanical and electrical devices. As we discussed in Chapter 4, when you get down to the heart of the system, computers really do only one thing: perform calculations on numbers. However, they can do an incredible number of such calculations incredibly quickly. This is exactly what is needed for complex encryption algorithms. Of course, computers also make it much easier to decrypt encrypted data. Ciphers that would take hundreds or thousands of years to break with a team of top cryptanalysts working on them manually can be cracked in hours, days, or weeks using high-powered computers.
One of the first well-known computer ciphering systems was LUCIFER, an IBM project that formed the foundation of the popular DES cipher that is still widely used (along with its more secure version, 3DES). LUCIFER was a block cipher, as is DES. It used a 128-bit key to encrypt blocks of binary data that were 128 bits in length. The cipher was applied to each block several times. Even though LUCIFER uses a larger block and key than DES, it is less secure. That's because its key schedule is regular and thus more predictable. In the upcoming “Encryption Algorithms” section, we discuss DES and other modern ciphers used by computerized encryption schemes.
What Is Encryption?
Encryption is a form of cryptography that “scrambles” plain text into unintelligible cipher text. Encryption is the foundation of such security measures as digital signatures, digital certificates, and the PKI that uses these technologies to make computer transactions more secure. Computer-based encryption techniques use keys to encrypt and decrypt data. A key is a variable (sometimes represented as a password) that is a large binary number—the larger, the better. Key length is measured in bits, and the more bits in a key, the more difficult the key will be to “crack.”
The key is only one component in the encryption process. It must be used in conjunction with an encryption algorithm (a process or calculation) to produce the cipher text. Encryption methods are usually categorized as either symmetric or asymmetric, depending on the number of keys that are used. We discuss these two basic types of encryption technology in the following sections.
Symmetric Encryption
Symmetric encryption is also called secret key encryption, and it uses just one key, called a shared secret, for both encrypting and decrypting. This is a simple, easy-to-use method of encryption, but there is one problem with it: The key must be shared between the sender and the recipient of the data, so a secure method of key exchange must be devised. Otherwise, if a third party intercepts the key during the exchange, an unauthorized person can easily decrypt the data.
Asymmetric Encryption
To address the problem of key exchange, another type of encryption was developed. Asymmetric encryption is also called public key encryption, but it actually relies on a key pair. Two mathematically related keys, one called the public key and another called the private key, are generated to be used together. The private key is never shared; it is kept secret and is used only by its owner. The public key is made available to anyone who wants it. Because of the time and amount of computer processing power required, it is considered “mathematically unfeasible” for anyone to be able to use the public key to re-create the private key, so this form of encryption is considered very secure.
The primary advantage of asymmetric encryption is that there is no need to securely transmit a secret key. Instead, the public key is published openly, made available to the entire world. There is no need to keep it secret, because it can't be used alone. The encryption process works like this:
1 The sender of a message uses the intended recipient's public key, which is freely available, to encrypt a message.
2 The recipient decrypts the message using his or her private key. Only the private key associated with the public key that encrypted it can be used to decrypt the message.
This key pair can also be used to provide for authentication of a message sender's identity using the keys a little differently: This time the sender uses his or her own private key to encrypt the message. This system provides no confidentiality, because anyone can decrypt the message using the owner's public key. However, it does verify the sender's identity, because if the associated public key will decrypt the message, it could only have been encrypted with that person's private key.
Obviously, the most important issue in public key cryptography is the protection of the private keys. This concept is especially important because compromise of a private key not only allows the unauthorized person to read private messages sent to the owner, but also allows the key thief to “sign” transactions emulating the owner, thus stealing the owner's identity. When the key pair is used for secure credit card or banking transactions, this loophole can be disastrous.
Securing Data with Cryptographic Algorithms
Literally thousands of different cryptographic algorithms have been developed over the years. Cryptographic algorithms can be classified as follows:
▪ Encryption algorithms that are used to encrypt data and provide confidentiality
▪ Signature algorithms that are used to digitally “sign” data to provide authentication
▪ Hashing algorithms that are used to provide data integrity
Algorithms (ciphers) are also categorized by the way they work at the technical level (stream ciphers and block ciphers). This categorization refers to whether the algorithm is applied to a stream of data, operating on individual bits, or to an entire block of data. Stream ciphers are faster because they work on smaller units of data. The key is generated as a keystream, and this is combined with the plain text to be encrypted. RC4 is the most commonly used stream cipher. Another is ISAAC.
Block ciphers take a block of plain text and turn it into a block of cipher text. (Usually the block is 64 or 128 bits in size.) Common block ciphers include DES, CAST, Blowfish, IDEA, RC5/RC6, and SAFER. Most Advanced Encryption Standard (AES) candidates are block ciphers.
Note
AES is a standard for cryptography used by the U.S. federal government to protect sensitive but unclassified information. A number of different algorithms were considered candidates for this standard. The National Institute of Standards and Technology (NIST) selected the Rijndael algorithm for the AES. You can find additional information on AES and its specifications at http://csrc.nist.gov/publications/fips/fips197/fips-197.pdf.
Encryption Algorithms
Some popular encryption algorithms (many of which were AES candidates) are:
Other encryption algorithms include SERPENT, RC4/RC5/RC6, LOKI-97, FROG, and Hasty Pudding.
Signature Algorithms
Signature algorithms are used to create digital signatures. A digital signature is merely a means of “signing” data (as described earlier in the section “Asymmetric Encryption”) to authenticate that the message sender is really the person he or she claims to be. Digital signatures can also provide for data integrity along with authentication and nonrepudiation. Digital signatures have become important in a world where many business transactions, including contractual agreements, are conducted over the Internet. Digital signatures generally use both signature algorithms and hash algorithms.
When a message is encrypted with a user's private key, the hash value that is created becomes the signature for that message. Signing a different message will produce a different signature. Each signature is unique, and any attempt to move the signature from one message to another would result in a hash value that would not match the original; thus, the signature would be invalidated.
Hashing Algorithms
Hashing is a technique in which an algorithm (also called a hash function) is applied to a portion of data to create a unique digital “fingerprint” that is a fixed-size variable. If anyone changes the data by so much as one binary digit, the hash function will produce a different output (called the hash value) and the recipient will know that the data has been changed. Hashing can ensure integrity and provide authentication as well.
The hash function cannot be “reverse-engineered”; that is, you can't use the hash value to discover the original data that was hashed. Thus, hashing algorithms are referred to as one-way hashes. A good hash function will not return the same result from two different inputs (called a collision); each result should be unique.
There are several different types of hashing, including division-remainder, digit rearrangement, folding, and radix transformation. These classifications refer to the mathematical process used to obtain the hash value. Standard hashing algorithms include:
▪ MD2, MD4, and MD5 These methods use a message digest (the hash value) that is 128 bits in length. They were created by Ron Rivest and are popularly used for digital signatures.
▪ Secure Hash Algorithm (SHA) There are several variations on this algorithm, including SHA1, SHA256, SHA384, and SHA512. The differences between them lie in the length of the hash value. SHA was created by a cooperative effort of two U.S. government agencies, NIST and the National Security Association (NSA).
How Encryption Is Used in Information Security
Encryption is used for a number of different purposes in organizations that deal with sensitive data of any type. In the “Designing and Implementing Security Policies” section later in this chapter, we discuss the types of information that should be protected. In this section, we look at the different ways encryption technologies can be used to protect that information.
Encrypting Data Stored on Disk
Disk encryption refers to encrypting the entire contents of a hard disk or other removable media. File encryption refers to encrypting data stored on disk on a file-by-file basis. In either case, the goal is to prevent unauthorized persons from opening and reading files that are stored on the disk.
Support for disk/file encryption can be built into an operating system or file system. The Encrypting File System (EFS) was introduced with New Technology File System (NTFS) Version 5, the native file system for Windows 2000 and later, and can be used to protect data on a hard disk or large removable disk. (EFS can't be used to protect data on diskettes because they cannot be formatted in NTFS format.) EFS allows encryption of individual files and/or folders. Windows Vista and Windows Server 2008 also uses BitLocker Drive Encryption, which uses the AES-CBC + Elephant diffuser encryption algorithm (which is the AES algorithm in CBC mode that's combined with a new component called Elephant) to encrypt entire volumes of data.
Third-party programs—such as DriveCrypt (www.securstar.com/disk_encryption.php) and SafeDisk (www.guardcomplete.com) for Windows operating systems and the Crypto File System and Transparent Cryptographic File System (TCFS) for UNIX/Linux—can be installed to provide encryption on file systems that don't natively support encryption or to provide partition-level or virtual drive encryption.
An excellent virtual drive encryption tool is Security Guardian from Frontier Information Enterprise, which is available from www.securityguardian.us.com. After installing it on a computer, inserting the Universal Serial Bus (USB) key into a USB port allows you to see a virtual drive on the machine. This virtual disk appears (and from the user's perspective functions) identical to a real hard disk, but data is actually stored on an area of your computer's hard disk. With the exception of the operating system, any files or programs can be installed in the virtual drive and encrypted using AES 256-bit encryption. As shown in Figure 12.2, by default, this drive is 32MB but can be resized up to 128GB using a utility that's accessed through an icon on the Windows taskbar. Because Security Guardian uses a combination of hardware and software to encrypt the data, anyone accessing the data must have the USB key to view the virtual drive and decrypt the data. Once the USB key is removed, the virtual drive is hidden. Anyone using the computer afterward will be completely unaware that a virtual disk even exists on the machine.
 |
| Figure 12.2 Security Guardian |
In looking at tools such as Security Guardian, it is easy to see their importance in protecting sensitive data. By encrypting the data, you ensure that information stored on a hard disk remains secure, even if the hard disk is removed or the computer is stolen. If a thief stole the computer, the data would remain inaccessible without the USB key to decrypt the data. In day-to-day use (especially on computers used by multiple users), the tool can be used to hide encrypted data on a machine, preventing others from viewing any sensitive data stored in the virtual drive. However, the ability to hide data is why law enforcement officers need to be aware that tools such as Security Guardian exist. If a person were crossing the border or going through Customs with a laptop, a Customs official might never realize that a virtual drive with encrypted data resided on the computer. The ability to smuggle data becomes easier if it's concealed.
With partition-level and virtual drive encryption, a user does not have to explicitly set encryption properties on individual files and folders (as is true with file-level encryption). Instead, an entire partition is marked as encrypted or an encrypted virtual drive is created, and all data that is stored there will be automatically encrypted. Many users choose these methods because performance is better than with file-level encryption. Some file/disk encryption methods use a password to protect encrypted data; when someone wants to access an encrypted file, he or she must enter a password. Other methods rely on the user account that is logged on to determine whether access will be granted. EFS, for example, uses digital certificates that are associated with the user account. These latter methods require less user interaction, but they have their drawbacks. It might not be possible to share encrypted files with others without decrypting them in cases where only one particular account is allowed access. In addition, there is a security risk if the user leaves the computer while logged on; then anyone who sits down at the machine can access the encrypted data.
Note
According to the document “AES-CBC + Elephant diffuser: A Disk Encryption Algorithm for Windows Vista,” by Niels Ferguson (available from www.microsoft.com/downloads), Microsoft's research shows that laptop computers are lost at a rate of around 1 percent to 2 percent per year. By encrypting the data on a laptop computer, it is less likely that a thief will be able to access the information on the computer if it is stolen.
Encrypting Data That Travels across the Network
In Chapter 11, we discussed how data can be intercepted and captured as it travels across a network and its contents revealed with a “sniffer,” or protocol analyzer. When sensitive data is transmitted across the network, users can protect against its decoding by ensuring that it is encrypted so that if unauthorized persons do intercept it, they won't be able to read it. The industry-standard method for doing this on a Transmission Control Protocol/Internet Protocol (TCP/IP) network is to use the Internet Protocol Security (IPSec) encryption mechanism.
Specifications for IPSec are laid out in Request for Comments (RFC) 2401. (A number of additional RFCs pertain to different protocols used by IPSec.) IPSec can be used with different operating systems and platforms. Windows 2000/XP/.NET include built-in support for IPSec. IPSec can provide machine-level authentication (verification of the identity of the computer from which a network transmission originated). It can be configured to work in one of two modes:
▪ Transport mode This mode provides end-to-end security, from the source computer to the destination computer. It is also called host-to-host mode.
▪ Tunnel mode This mode provides for encryption between two secure gateways (the computers that act as gateways between an internal network and the Internet or other internetwork).
Because it is capable of tunneling, IPSec can be used to create virtual private networks on its own, and it is also used in conjunction with Layer 2 Tunneling Protocol (L2TP) to provide encryption in an L2TP virtual private network (VPN) tunnel.
Although often referred to as a protocol, IPSec is actually a security scheme that incorporates several different protocols. These include the following:
▪ Authentication Header (AH) protocol This protocol is used for authentication and to ensure data integrity by signing each data packet. AH signs the entire packet (including the Internet Protocol [IP] headers) but does not provide data confidentiality.
▪ Encapsulating Security Payload (ESP) protocol This protocol is used to encrypt data for confidentiality. It also signs the data portion of the packet for authentication and integrity, but it doesn't sign the entire packet.
These two protocols can be used separately or together (in the latter case, when both data confidentiality and signing of the entire packet are desired). Other protocols used by IPSec include:
▪ The Oakley Key Generation Protocol This protocol creates the keys used during the transaction. These are temporary keys that are discarded after the communication session is terminated.
Because IPSec uses shared keys (symmetric encryption), it is important that there be a way to exchange keys securely across the network. The Diffie-Hellman Key Exchange algorithm provides a way for the computers on both sides of the transaction to generate identical keys without ever actually sending the key itself across the network and exposing it to possible interception. The encryption algorithms used by IPSec are standard ciphers such as DES/3DES, IDEA, Blowfish, RC-5, and CAST-128.
Another important feature of IPSec is its ability to provide antireplay—protection against hackers who might try to capture transmissions and replay them to create a communication session, emulating one of the parties to the original transaction. IPSec is an important mechanism for protecting data during the vulnerable period when it is being sent across a network. The current version of IP, IPv4, allows the use of IPSec as an option; the next generation, IPv6, will require it.
Encrypting E-mail Communications
E-mail has become one of the most common forms of communication, including for messages that contain sensitive personal or business information. Several software programs encrypt e-mail; the most popular is Pretty Good Privacy (PGP), which was created by Phil Zimmermann in the early 1990s. Since then, PGP has become widely distributed, and versions are available for most common operating systems, including Windows XP and Mac OS X.
PGP first compresses and then encrypts the plain-text data using a one-time secret key (or session key), which is itself then encrypted with the public key of the intended recipient. The encrypted session key is sent to the recipient along with the encrypted data, and the recipient uses his or her private key to decrypt the session key so that it can be used to decrypt the message itself. Because both symmetric and asymmetric encryption is used in this process, PGP is called a hybrid cryptosystem. Different versions of PGP use different encryption algorithms. Version 2.6.x (sometimes called “classic PGP” and considered by some to be more secure than newer versions) uses a combination of the RSA asymmetric cipher and the IDEA symmetric cipher. The MD5 hash algorithm is also used to create a fixed-length replacement for very long text strings in digital signatures.
Public keys and private keys are stored in separate files called keyrings on the hard disk of the computer where PGP is installed. Both the sender and recipient must have PGP installed to use the program for secure communications.
PGP's biggest vulnerability is related to the fact that users have to use a passphrase to perform actions such as signing documents and decrypting messages (anything for which the private key is used). Protecting this passphrase is a big security issue; good security practices require that the passphrase not be revealed to anyone else or stored on the system for “automatic” entry. Anyone who knows the passphrase can read the encrypted messages or send messages that purport to be from the legitimate user. If the passphrase does become compromised, a key revocation certificate can be generated and issued to render the associated public key null and void. PGP also includes a wipe option (–w) that can be used to overwrite the contents of an encrypted file when you delete it so that it can't be easily recovered using data recovery utilities.
Note
For more information about PGP, see the International PGP home page at www.pgpi.org
A number of tools and services use PGP or the Open PGP standard for encrypting e-mail. Many of these solutions are also available on the Web, including Hushmail (which we discussed in Chapter 9), but these are primarily for private use. Larger organizations commonly use services such as e-mail encryption software from Entrust (www.entrust.com/email-encryption/). Entrust uses Secure/Multipurpose Internet Mail Extensions (S/MIME), PGP, and Entrust encryption formats to encrypt messages, and Entrust server software is available to encrypt messages on a network so that they can't be viewed after being to other networks such as the Internet. Entrust is used not only for e-mail programs such as Outlook, but also by mobile devices such as BlackBerry handheld devices.
What Is Steganography?
Steganography (from the Greek word for covered writing) refers to a method of hiding data—not just concealing its contents as encryption does, but concealing its very existence. Steganography is usually used in conjunction with encryption for added protection of sensitive data. This method ameliorates one of the biggest problems of encrypting data—the fact that it is encrypted draws the attention of people who are looking for confidential or sensitive information.
The concept of steganography has been around for a long time. The ancient Greeks are said to have sent secret messages by shaving the head of the messenger and writing the message on his scalp, then letting the hair grow back over it before sending him on his way to deliver the message. Early methods of steganography involved using “invisible ink” or concealing a message inside another message using a code whereby only every fifth word, for example, “counts” as part of the real, hidden message. One of the earliest books on the subject, Steganographica, by Gaspari Schotti, was published in the 1600s.
Steganography in the computer world also hides data inside other data, but the way it does so is a little more complex. Because of the way data is stored in files, there are often unused (empty) bits in a file such as a document or graphic. A message can be broken up and stored in these unused bits, and when the file is sent it will appear to be only the original file (called the container file). The hidden information inside is usually encrypted, and the recipient will need special software to retrieve it (and then decrypt it, if necessary). Messages can be concealed inside all sorts of other files, including executables and graphics and audio files. Another form of steganography is the hidden watermark that is sometimes used to embed a trademark or other symbol in a document or file.
A number of different software programs can be used for this purpose, including JP Hide and Seek, which conceals data inside .jpg files, and MP3Stego, which conceals data in .mp3 files. Steganos Security Suite is a package of software programs that provide steganography, encryption, and other services.
Other programs, such as StegDetect, are designed to look for hidden content in files. The process of detecting steganographic data is called steganalysis.
Note
For more information and links to lots of good steganography Web sites, see “Information Hiding” at http://www.jjtc.com/steganography
Modern Decryption Methods
The use of cryptography naturally led to the science of cryptanalysis, the process of decrypting encrypted messages. One of the early methods for “cracking” polyalphabetic substitution ciphers was frequency analysis, which involved examining the encrypted text for repeated character strings and using the distance between the repeated strings to calculate the key length. (Repetitions of identical plain-text characters that are ciphered in the same way will occur at intervals that are a multiple of the key length.) Then statistical methods can be used to painstakingly determine which plain-text character each cipher-text character represents.
Cryptanalysts throughout history have used a number of different methods to break encryption algorithms, including the following:
▪ Known plain-text analysis If the analyst has a sample of decrypted text that was encrypted using a particular cipher, he or she can sometimes deduce the key by studying the cipher text.
▪ Differential cryptanalysis If the analyst can obtain cipher text from plain text but is unable to analyze the key, it can be deduced by comparing the cipher text and the plain text.
▪ Ciphertext-only analysis This is used when only the cipher text is available and the analyst has no sample of plain text.
▪ Timing/differential power analysis This is a means of measuring the differences in power consumption over a period during which a computer chip is encrypting information to analyze key computations.
▪ Key interception (man in the middle) The analyst tricks two parties to an encrypted exchange into sending their keys by making them think they're exchanging keys with each other.
A Perfect Cipher?
A perfect cipher is one in which every possible cipher text is equally likely for every method, thus rendering the encryption unbreakable without the key.
In his paper “A Communications Theory of Secrecy Systems,” published in 1948, Claude Shannon, a Bell Labs mathematician sometimes called the “father of information theory,” postulated that given enough time and a large enough sample of the cipher text, every cipher can be broken. He held that a number he called the unicity distance, which represented the amount of cipher text that is needed to be able to decrypt a message, could be used as a measurement of how strong a cipher is. If the unicity distance is infinite (the sequence of numbers in the key is genuinely random and is at least as long as the message, and the key is used only for that one message), the cipher is called a one-time pad and the message is undecipherable.
Another example of an undecipherable message is one in which the length of the entire message is shorter than the amount of cipher text needed to break the key. If an alphabetical substitution cipher has a key length that is greater than the message length, the message can't be decrypted by analyzing the cipher text.
Mathematician Claude Shannon (see the sidebar in this section) put forth the theory of workload. This term refers to the fact that increasing the amount of work (and the time required to do it) that is necessary to crack an encryption system increases the strength of the encryption and is an alternative to increasing the unicity distance (the amount of cipher text needed to crack the encryption).
Computer encryption ciphers are difficult to crack, but it can be done. With enough time and patience, a brute force attack that tries every possible key will be successful. The goal of cryptographers is to create ciphers for which this process will take such a long time—even using supercomputers or distributed processing methods—that the effort will not be worthwhile. Today's popular encryption algorithms rely on this deterrent effect.
Cybercriminals' Use of Encryption and Steganography
We have been discussing the legitimate use of cryptographic techniques as part of an organization's security plan. There are many reasons to take steps to provide extra protection for data such as trade secrets, customer and client personal information, and so forth. However, these same technologies can be—and often are—also used by cybercriminals to conceal the self-incriminating information in messages they send to one another. Terrorists are believed to use steganography and encryption (as well as less technical code words inserted in seemingly innocuous e-mails or Web pages) to communicate with one another and coordinate their financial activities and attacks.
In cases of serious crimes, investigators might need to employ the services of a cryptanalyst to help decipher encrypted data that could contain information essential to identifying criminals or preventing future criminal activities.
Cryptography As a Terrorist Tool
According to an article in USA Today and later reported on the Wired Web site at www.wired.com/politics/law/news/2001/02/41658, government officials believe Al Qaeda terrorists use steganography to hide their secret communications “in plain sight” in messages and files posted on bulletin board Web sites and exchanged in Internet chat rooms, and encryption technologies to conceal the true content of e-mail messages. Encrypted files containing terrorist plans have been found on the computers of various terrorist suspects, including Pakistani terrorist Khalil Deek and the terrorist convicted of plotting the first World Trade Center bombing in 1993, Ramzi Yousef. In both cases, mathematicians working for the FBI were able to use supercomputers to decrypt the files, although in the case of some files, it took more than a year to do so.
For more information, see www.usatoday.com/life/cyber/tech/2001-02-05-binladen.htm
Making the Most of Hardware and Software Security
A multilayer security plan will incorporate multiple security solutions. Security is not a “one size fits all” issue, so the options that work best for one organization are not necessarily the best choice for another. Security solutions can be generally broken down into two categories: hardware solutions and software solutions.
Implementing Hardware-Based Security
Hardware security solutions can come in the form of network devices: Firewalls, routers, and even switches can function to provide a certain level of security. In general, these devices are dedicated computers themselves, running proprietary software.
Hardware-Based Firewalls
Many firewall vendors provide hardware-based solutions. Some of the most popular hardware firewalls include the Cisco PIX firewall, SonicWALL, Sun's iForce VPN/Firewall, Sidewinder G2, and home-based firewalls from D-Link and Linksys. Hardware solutions are available for networks of all sizes. For example, the D-Link and Linksys products focus on small office/home office (SOHO) users, whereas the Cisco PIX comes in configurations that support up to 500,000 connections.
Hardware-based firewalls are often referred to as firewall appliances. A disadvantage of hardware-based firewalls is the proprietary nature of the software they run. Another disadvantage of many of these products, such as Cisco's highly respected PIX, is the high cost. Of course, the range in price is based on how many connections are supported, and features that aren't found in firewalls designed for home and small-business use. Hardware-based firewalls perform basically the same functions as software-based firewalls. Later in this chapter, in the section “Understanding Firewalls,” we discuss how both of these work.
Authentication Devices
As we discussed in Chapter 11, you can use a number of hardware-based components to authenticate users, and you can implement them as part of your network security plan to provide extra security. These devices may use biometrics, which analyzes characteristics of the person, or smart cards that contain computer chips to help authenticate the user. The costs of these devices can vary, but they have dropped dramatically in recent years as security has become a priority for homes and businesses alike.
Implementing Software-Based Security
Software security solutions cover a much broader range than do hardware-based solutions. These solutions include the security features built into the network operating system as well as additional security software made by the operating system vendors or third-party vendors. Software security has its advantages: It is often less expensive than hardware-based solutions and it integrates more easily into the system and network. However, software security often suffers from decreased performance, compared to hardware-based security implementations, and security applications that run on popular operating systems can be easier to hack than the proprietary programs that run on dedicated hardware devices. Nonetheless, software security is popular and provides a full range of methods for protecting data and providing authentication, confidentiality, and integrity.
Cryptographic Software
Thousands of cryptographic products are available for different purposes: disk/file encryption, e-mail encryption, steganography, and more. We have mentioned some of these in the sections addressing how the technologies work. In addition to the commercial products, many encryption and authentication software programs are available as freeware.
Digital Certificates
As mentioned earlier, public key encryption is more secure than secret key encryption because there is no need to transmit a key across unsecured channels, but public key cryptography is also more complex, and it's more difficult to implement on a large scale. There must be a system that ensures that public keys that are posted to the Internet are not forgeries posted by someone who purports to be another user. If this happens, the data that is encrypted with that public key (and intended to be sent to the user whose name was associated with it) could be intercepted by the unauthorized user who posted the key. That unauthorized person would then be able to decrypt the data and read the message.
We need a mechanism that will provide a way for a trusted third party to confirm that the user who publishes the public key is in fact who he or she claims to be. A digital certificate provides this assurance. To understand how a digital certificate works, think of the way a driver's license or government-issued ID card is used for identity verification. If a store or bank requires that you prove your identity by producing a license or ID card, that entity is relying on the word of a trusted third party (in this case, the Department of Motor Vehicles [DMV]) that you are who you say you are. The store or bank presumes that the DMV has checked you out and would not have issued the official identification document unless your identity was confirmed.
Just as the store or bank accepts your driver's license as proof of your identity, another computer with which you want to exchange data or make transactions will accept the digital certificate issued by a trusted third party. In the case of digital certificates, the trusted third party is a certificate authority (CA). The CA verifies that a particular identity is bound to the public key that is included in the certificate.
Some public CAs, such as VeriSign, issue certificates to persons on the Internet. Some private (internal) CAs are set up by organizations to issue certificates to users within the local network. The CA is a server that runs special software that allows it to issue, manage, and revoke digital certificates. The CA's role is to guarantee to other users, computers, and applications that a particular public key really belongs to the entity with whose name it is associated.
The Public Key Infrastructure
A public key infrastructure, or PKI, is a security framework based on digital certificates. The PKI provides a system for users to request certificates and for CAs to issue, manage, and revoke certificates and disseminate certificate revocation lists (CRLs) so that other entities will know when a particular entity's certificate is no longer valid. The PKI is based on the X.509 standards established by the International Organization for Standardization (ISO).
An important component of the PKI is the set of security policies that governs it. These policies should define the rules for issuance and use of digital certificates and the keys that are associated with them. Public certification authorities such as VeriSign are required to provide a certificate practice statement (CPS). This is a document that outlines in detail the procedures for implementing the PKI.
When multiple CAs are in the same PKI, as is the case in most large organizations, they are arranged in a hierarchical manner. The root CA is the most trusted CA in the PKI. Its certificate is self-signed, and it is responsible for issuing certificates to all the other CAs in the PKI, which are called subordinate CAs. The subordinate CAs issue certificates to users and computers, whereas the root CA generally issues certificates only to subordinate CAs. Public CAs are published in the Global Trust Register, which acts like a root CA for public CAs (albeit in printed form).
Certificates can be issued by a CA for many different purposes, including file encryption, smart card authentication, e-mail, IP security, and network logon. Users can export or import certificates, moving them from one computer to another. The export function is also used to create a backup of a certificate, which can then be restored to the certificate store, the location on the hard disk where certificates are kept, if the original certificate is destroyed. Certificates are issued automatically in some cases; in other cases, they must be explicitly requested by the user. There are different ways to request a certificate, depending on the CA software and the PKI policies. Requesting a certificate from a public CA usually involves filling out an application form on the CA's Web site.
It is very important that a PKI contain a mechanism for publishing certificate revocations so that other entities won't mistakenly rely on a certificate that is no longer valid. Certificates are revoked when the public key is compromised or when users leave the company or for some reason are no longer trusted. A CRL lists certificates that have been revoked and is updated regularly and distributed throughout the organization by the CA.
Software-Based Firewalls
In addition to the PKI software that provides for verification of identity, a vitally important type of software-based security is the software firewall. In reality, all firewalls are software-based. The hardware devices sold as firewalls run proprietary software that performs basically the same functions as a software program that can be installed on a regular PC. We use the term software-based firewall to describe firewall products such as Microsoft ISA Server, as opposed to hardware/software (or firmware) combination appliances such as those produced by Cisco Systems. Some vendors, such as Check Point, market both types of products. In the next section, we discuss in detail how firewalls work.
The Difference between a Firewall and a Proxy
Proxy servers have been around for quite a while. The original meaning of the term proxy was “one who is authorized to act for another.” Perhaps the most famous—or infamous—use of the word came about in relation to the practice of marriage by proxy, in which a substitute would stand in for one of the parties, allowing a wedding ceremony to be performed even though the groom (or less commonly, the bride) was not physically present. Proxy weddings at one time were a popular way for a couple to get “hitched” while the groom was serving in the military.
Proxy servers are so named because, like the hapless stand-in who says “I do” when it's really someone else who does, they act as go-betweens to allow something to take place (in this case, network communications) between systems that must remain separate.
Proxy servers “stand in” between the computers on a LAN and those on the public network outside. Another good analogy is a gatekeeper who is stationed at the entrance to an estate to check all incoming visitors to ensure that they are on the list of invited guests. The proxy can actually hide the computers on the LAN from outsiders. Only the IP address of the proxy server is “visible” to others on the Internet; internal computers use private IP addresses (nonroutable over the Internet) that cannot be seen from the other side of the proxy.
In fact, a proxy can go further and function more like a prison guard, who not only makes certain that only authorized persons get in, but also sees that only those who have permission to go out are allowed to leave. Just as the guard checks his list before letting anyone in or out, the proxy filters outgoing and incoming data according to predefined criteria. At this point, the proxy is behaving like a firewall.
Understanding Firewalls
A firewall goes a bit further than just “standing in” for the local computers and hiding them from view on the global network, as a proxy server does. Firewalls are specifically designed to control inbound and outbound access, preventing unauthorized data from entering the network and restricting how and what type of data can be sent out.
The firewall gets its name from the building industry. In commercial structures, it is common to build a barrier wall made of fireproof material between two areas of a building. This wall is designed to prevent fire from spreading from one part of the building to the other. Another example is the heat barrier between the engine of an automobile and the passenger compartment, also called a firewall. Likewise, a network firewall acts as a barrier to prevent “bad data”—whether that is virus code or simply messages to or from unauthorized systems—from spreading from the outside network (usually the Internet) to the internal network. It also prevents packets of a particular type or to or from a particular user or computer from spreading from the LAN to the outside network.
In choosing among different firewall solutions, organizations encounter two basic firewall design options:
▪ A firewall can be designed to permit all packets to pass through unless they are expressly denied.
▪ A firewall can be designed to deny all packets unless they are expressly permitted.
Obviously, the second method is more secure, but it can result in the denial of access that administrators actually want to allow. The first method is easier to implement but is also more easily penetrated or circumvented.
How Firewalls Use Layered Filtering
Firewall products support the filtering of messages to either allow data to pass through or prevent it from doing so, according to specified criteria. The best firewalls support layered filtering. This means they can perform filtering at the packet layer, the circuit layer, or the application layer; some firewalls support only one of these filtering types, but most advanced firewall products, such as Microsoft ISA Server and Check Point's Firewall-1 product, support all three types. Firewalls that combine packet filtering, circuit filtering, and application layer filtering provide the highest level of security. These types of firewalls also tend to be the most expensive. In the following sections, we look briefly at how each filtering method works.
Packet Filtering
Packet filtering does most of its work at the network layer of the Open Systems Interconnection (OSI) networking model (equivalent to the internetwork layer of the Department of Defense [DoD] model), dealing with IP packets. Packet filters examine the information contained in the IP packet header of a message and then either permit the data to cross the firewall or reject the packet based on that information. When IP packet filtering is enabled, the firewall will intercept and evaluate packets before passing them on to a higher level in the firewall or to an application filter.
The information that the packet filter uses to make its decision includes the IP address of the source and/or destination computer(s) and the Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) port number. (Yes, the port numbers are in the transport layer header, so technically, although packet filtering generally operates at the network layer, it also processes some higher-layer information.) Packet filtering allows the data to proceed to the transport layer only if the packet-filtering rules allow for it to do so.
Packet filtering lets administrators block packets that come from a particular Internet host or those that are destined for a particular service on the network (for example, the Web server or Simple Mail Transfer Protocol [SMTP] server). Dynamic packet filtering provides higher security because it opens the necessary port(s) only when required for communication to take place, and then closes the port(s) immediately after the communication ends. Static packet filters are configured to allow inbound and outbound access to a predefined IP address (or group of IP addresses) and port number (or groups of ports).
It is important to note that packet filters cannot perform filtering that is based on anything contained in the data field of the packet, nor can they use the state of the communication channel to aid in making their decision to accept or reject the packet. If filtering decisions need to be made on the basis of either of these criteria, the firewall must be configured to use filtering that operates at a different layer (circuit or application filtering).
Circuit Filtering
Circuit filters operate at a higher layer of the OSI model, the transport layer (the host-to-host layer in the DoD model). Circuit filters restrict access on the basis of host machines (not users) by processing the information found in the TCP and UDP packet headers. This allows administrators to create filters that would, for example, prohibit anyone using Computer A from using File Transfer Protocol (FTP) to access Computer B.
When circuit filters are used, access control is based on TCP data streams or UDP datagrams. Circuit filters can act based on TCP and UDP status flags and sequencing information, in addition to source and destination addresses and port numbers. Circuit-level filtering allows administrators to inspect sessions rather than packets. A session is sometimes thought of as a connection, but actually a session can be made up of more than one connection. Sessions are established only in response to a user request, which adds to security.
Circuit filters don't restrict access based on user information; they also cannot interpret the meanings of the packets. That is, they cannot distinguish between a GET command and a PUT command sent by an application program. To do this, application filtering must be used.
Application Filtering
At times, the best tactic is to filter packets based on the information contained in the data itself. Packet filters and circuit filters don't use the contents of the data stream in making filtering decisions, but this can be done with application filtering. An application filter operates at the top layer of the networking model, the appropriately named application layer. Application filters can use the packet header information but are also able to allow or reject packets on the basis of the data contents and the user information.
Administrators can use application filtering to control access based on a user's identity and/or based on the particular task the user is attempting to perform. With application filters, criteria can be set based on commands issued by the application. This means that, for example, the administrator could restrict a particular user from downloading files to a specified computer using FTP. At the same time, the administrator could allow that user to upload files via FTP to that same computer. This is possible because different commands are issued depending on whether the user is retrieving files from the server or depositing them there.
Many firewall experts consider application gateways to be the most secure of the filtering technologies. This is because the criteria they use for filtering cover a broader span than the other methods. Sometimes hackers write malicious programs that use the port address of an authorized application, such as port 53, which is the domain name system (DNS) address. A packet or circuit filter would not be able to recognize that the packet is not a valid DNS request or response and would allow it to pass through. An application filter, however, is able to examine the contents of the packet and determine that it should not be allowed.
There are drawbacks to this filtering type. The biggest problem is that there must be a separate application gateway for every Internet service that the firewall needs to support. This makes for more configuration work; however, this weakness is also a strength that adds to the security of the firewall. Because a gateway for each service must be explicitly enabled, an administrator won't accidentally allow services that pose a threat to the network. Application filtering is the most sophisticated level of filtering performed by the firewall service and is especially useful in protecting the network against specific types of attacks, such as malicious SMTP commands or attempts to penetrate the local DNS servers.
Integrated Intrusion Detection
Many firewalls also incorporate an intrusion detection system (IDS) that can actually recognize that an attack of a specific type is being attempted and can perform a predefined action when such an intrusion is identified, such as one of the following:
▪ Send an e-mail message to the administrator
▪ Page the administrator
▪ Write an event entry to the event log
▪ Run a previously specified program or script
▪ Stop the firewall service
IDSes can recognize many different common forms of network intrusion, such as port scans, LAND attacks, the Ping of Death, UDP bombs, out-of-band attacks, and others. Special detection filters may also be built in, such as a Post Office Protocol (POP) intrusion detection filter that analyzes POP mail traffic to guard against POP buffer overflows, or a DNS intrusion detection filter that can be configured to look for DNS hostname overflow or length overflow attacks.
Forming an Incident Response Team
An intrusion or attack can be scary, frustrating, and maddening—as with a physical attack on one's person, the emotional reactions can make it difficult to exercise good judgment and make the correct decisions about how to respond. This situation is made easier if you have properly prepared for it. Many companies, taking the proactive approach, form incident response teams—called computer incident response teams, or CIRTs—made up of individuals who train together (much like a military unit or police SWAT team) in how to handle anticipated incidents. The goal is to be able to swing into action when an actual incident occurs, with each team member covering a preassigned area of responsibility and thus decreasing the amount of damage and increasing the likelihood of apprehending the perpetrator of the incident.
In their book Incident Response: Investigating Computer Crime, Chris Prosise and Kevin Mandia define an incident as “an event that interrupts normal operating procedure and precipitates some level of crisis.” The CERT guidelines define specific incidents, including violation of security policy, attempts to gain unauthorized access, unwanted denial of service/resources, unauthorized use, and changes made to a system or data without the owner's knowledge, instruction, or consent. An incident can be anything from an attack that crashes all the servers and cuts off all network communications to an intrusion that causes no actual damage but demonstrates the vulnerability of the organization's systems. The various types of attacks described in Chapter 10 (for example, the many varieties of denial-of-service/distributed denial-of-service [DoS/DDoS] attacks) certainly qualify as incidents.
The response team should have its own hardware and software to use in conducting the investigation. It is important that the victim systems be preserved in the state they were in when the incident was discovered. Any changes made to these systems can compromise the integrity of the evidence and affect its admissibility in court.
Response team members may be called to testify in court if criminal charges or civil lawsuits are brought in relation to the incident. This is another reason to create extensive documentation that can be reviewed prior to giving testimony. Often, a case doesn't come to trial until months or even years after the incident, and the human memory often isn't reliable after so long a time without a little help. The team member who creates the documentation should be the one to testify to its authenticity if it is to be entered into evidence.
Note
It is important for team members to understand that their reports regarding the incident may end up being entered into evidence at trial. For this reason, such documentation should be kept in a special notebook with numbered pages, and the notebook should not contain any personal information, because the entire notebook may become part of the official record.
The steps involved in incident response include:
▪ Training Once versed in the theory of incident response, the team should train together in realistic scenario-based drills until response actions become automatic. Training should also address the law relating to privacy considerations and other issues that could affect or restrict team members' activities during the response.
▪ Incident recognition Monitoring should be conducted to ensure that team members are alerted to the possibility that an incident is occurring in its earliest stages.
▪ Incident verification This step involves examining logs, observing system/network behavior, interviewing witnesses, and so on to verify that an incident has in fact occurred.
▪ Incident containment Immediate steps should be taken to stop the incident and prevent any more damage.
▪ Evidence preservation Immediate steps should be taken to preserve all evidence of the incident for the purposes of tracking the offender and possible prosecution or civil litigation.
▪ Incident analysis A thorough investigation should be conducted to determine exactly what happened and how.
▪ Restoration Systems should be brought back to a working state as soon as possible, to minimize loss of productivity.
▪ Follow-up activities New security measures should be established to ensure that the same type of incident doesn't occur again.
▪ Documentation Each step of the response process should be documented and preserved for later review and use.
Note
Documentation may include “crime scene photographs”; photos or screenshots to preserve the information on the monitor might be desirable in some cases. A digital camera should be part of the investigative team's response kit.
It is not necessary for every member of the team to participate in every step of the response process. All team members should know their own roles and allow other team members to perform as assigned. Team member roles should be assigned according to each individual's area of expertise. Teams often include persons from the IT department, corporate security, management, legal department, and even the financial, human resources, and public relations departments. Response team members should be on call and able to respond to incidents at all hours and on any day of the week.
Incident response is the culmination of everything we've discussed in this book and the first step in the investigative process. In this chapter, we've moved from security theory and concepts to the “hands-on” aspects of a security plan: implementation of security measures and finally, should those fail, planning to respond to an attack. However, the document that brings all these topics together is the organization's security policy, which governs everything from the way security technologies are to be used to the procedures prescribed for the incident response team. The next section provides an overview of security policies: what they are (and aren't) and how they're developed. We include examples of some specific policy issues that every organization should address.
Designing and Implementing Security Policies
Security issues are at the forefront of organizational priorities today. Companies lose millions of dollars and untold hours of worker productivity due to lax security. Companies realize that protection of their assets—digital as well as physical—is no longer a luxury; in the twenty-first century, it has become a necessity.
An enormous amount of a company's most crucial information, including financial data, personnel records, customer information, and trade secrets, is concentrated in one virtual “place”: the organization's network. This location renders this information vulnerable to unauthorized access and accidental or intentional destruction, both from within and (assuming the local network is connected to the Internet, as most today are) from outside intruders. Implementation of security measures, to be effective, must be based on an organized plan that takes into account all aspects of the organization's security needs. There must be rules and guidelines governing how the plan is put into action. These are disseminated throughout the organization as policies.
Understanding Policy-Based Security
Those of us in the security field often stress the need for detailed policies that are customized to fit the needs of each particular organization—sometimes to the point of sounding like a broken record. However, there's a good reason for this: The security policy is the foundation of an organization's security plan. It is the governing document, much like a police department's general orders, a city's charter, or a corporate board's mission statement. The following sections discuss the purpose and function of an IT security policy and the process of evaluating and defining security needs, developing the policy, and implementing it throughout the organization.
What Is a Security Policy?
A security policy, as the term is used here, refers to a written document that defines an organization's approach to security or a specific security area (in this case, computer and network security) and lays down a set of rules to be followed in implementing the organization's security philosophy.
Note
Guidelines usually function as recommended procedures rather than hard-and-fast rules. Guidelines can supplement policies, but they do not replace them.
Organizations may establish both written and unwritten rules pertaining to security matters and may issue a number of different types of documents dealing with these issues. How does the security policy differ from security-related memoranda and directives, standards, specifications, guidelines, and procedural documents?
Security Memoranda
Generally, a security memorandum or freestanding security directive is issued in response to a particular incident and may be used as a way to establish a rule that is not covered in the policy. If the rule applies only to a specific one-time situation or will be in effect for only a limited time, a memora-ndum might be all that's needed. If the rule will be permanent or long-term and is applicable to a broader spectrum of situations, it should be incorporated into the organization's formal policy as soon as possible. A memorandum can also be informational only, its purpose to make users aware of security considerations without laying out specific rules or guidelines.
Security Standards and Specifications
Standards and specifications are generally requirements that are to be met in implementing system-specific security procedures and may be used to measure or rate the overall reliability, compatibility, or other characteristics of the system. The Common Criteria for Information Technology Security Evaluation (which is commonly called the Common Criteria) is an international standard for computer security, which is outlined under ISO/IEC 15408. It is a framework that outlines the evaluation criteria for IT security. It evolved from the government standards used by several countries, and it provides a framework that is used by users, vendors, and testing laboratories to specify, implement, and test IT security.
Security Procedures
Procedural documents supplement the policy and may be incorporated into it as part of a policies and procedures manual. The procedural document gives step-by-step technical instructions for tasks that are required to implement the policies. For example, if the policy states that users must change their passwords every 30 days, you might have two associated procedural documents: one directed to network administrators that details how to set password requirements on the Windows domain controller to force users to change passwords at 30-day intervals, and another directed to users detailing how to change their passwords. When contained in separate documents, the policy section and associated procedural document(s) should reference one another.
Why This Information Matters to the Investigator
Investigators responding to cybercrimes that involve a corporate network need to have a thorough understanding of how security is implemented within the organization, just as an investigator responding to a home invasion needs to know the layout of the house, how and where commercial security devices are in place, what the family's security philosophy is, and so forth. Unlike most residential situations, corporations will often have formal, written documentation that lays out all the guidelines followed in implementing the security plan.
However, these documents aren't always easy to understand—unless you also understand the process by which they're created, adopted, and implemented. In the following sections, we provide an overview of that process: how organizations assess their security needs based on known risk factors, threat levels, and other factors that determine how much and what types of security will be implemented; how policy areas are defined; and how the document itself is developed (usually by a policy development team).
This background will make it easier for investigators to come into an organization and analyze its role as the victim or source of cybercrimes based on information contained in the policy document. For example, if an examination of the policies shows that the organization has an extremely strong password policy, and further investigative techniques such as interviewing employees reveal that the policies are universally enforced, this could indicate that intruders used techniques other than password cracking to gain access, or it could indicate that there is a “leak” inside the organization. In other words, understanding the policies can help to narrow the focus of the investigation. This is often one of the most difficult and most vital steps in the investigative process.
Evaluating Security Needs
If we accept the stated definition of security policy, it becomes obvious that there is not and cannot be a one-size-fits-all IT security policy that will work equally well for all organizations. Security needs differ, based on:
▪ Risk factors
▪ The perceived and actual threat levels
▪ Organizational vulnerabilities
▪ The organization's philosophy (open versus closed system)
▪ Legal factors
▪ Available funds
It is important to analyze all of these factors carefully when developing a policy that offers both adequate protection and a desirable level of access.
Components of an Organizational Security Plan
Security features are now built into operating system software; Windows XP, Vista, Server 2003, and Server 2008 include numerous security features. UNIX and Linux distributions as well as Mac OS X also come with built-in security features. IT security products, both hardware and software, abound. Security training and numerous security certifications are available, and IT professionals are seeking them out. These are all important components of an organization's overall security plan, but they are not enough. Effective coordination and interaction of all these parts require one more thing: a comprehensive security policy.
Defining Areas of Responsibility
To assess security needs accurately, someone should review the company's infrastructure, processes, and procedures and involve personnel at all levels of the organization and from as many different departments as possible. Ideally, the following tasks will be performed by a carefully selected team that includes, at a minimum, members of management, IT personnel, and a company legal representative. Each team member should be assigned specific areas of responsibility, and deadlines for completion should be provided.
Responsibility for Developing the Security Plan and Policies
The initial creation of a good security plan requires a great deal of thought and effort. The policy will impact those at all levels of the organization, and it is desirable to solicit input from as many representatives of different departments and job descriptions as is practical. An effective approach is to form a committee consisting of people from several areas of the organization to be involved in creating and reviewing the security plan and policies. A security planning committee of this type might include some or all of the following:
▪ The network administrator and one or more assistant administrators
▪ The site's security administrator
▪ Department heads of various company departments or their representatives
▪ Representatives of user groups that will be impacted by the security policies (for example, the secretarial staff, the data processing center)
▪ A member of the legal department who specializes in computer and technology law
▪ A member of the finance or budget department
▪ A member of upper management
Responsibility for Implementing and Enforcing the Security Plan and Policies
Security policies will generally be implemented and enforced by network administrators and members of the IT staff. Job descriptions and policies should designate exactly who is responsible for the implementation of which parts of the plan. There should be a clear-cut chain of command that specifies whose decision prevails in case of conflict. In some cases—such as physical penetration of the network—the company security staff will become involved. Written, clearly formulated policies should be in place, which stipulate which department has responsibility for which tasks in such situations.
The security plan should also address the procedures for reporting security breaches, both internally and if the police or other outside agencies are to be brought in. In addition, it should be specified who is responsible for or has the authority to call in outside agents.
As we mentioned in Chapter 5 when we discussed the investigation of policy violations, one of the most important factors in a good security policy is that it must be enforceable. If the policy can be enforced through security tools, this method is preferred. If the policies must be enforced through reprimand or other actions against employees who violate them, there should be clearly worded, universally distributed written documentation of what constitutes a violation and what sanctions will result, as well as who is responsible for imposing such sanctions.
Analyzing Risk Factors
Before the policy development team can set policies, they need to determine both the nature and the level of the security risks to the organization. Traditionally, risk analysis involves:
This process is known as quantitative risk analysis. Another type of risk analysis, qualitative risk analysis, disregards the probability element and instead focuses on potential threats and the characteristics of the system or network that make it vulnerable to these threats. Then methods are developed for preventing or reducing the likelihood of breaches, detecting when breaches do occur, and decreasing and repairing the damage done if a breach does occur. To help identify threats and vulnerabilities, rate the threat level, estimate the impact on the organization, and recommend solutions, risk assessment tools may be used.
Why is a risk analysis necessary? There are several reasons, including the following:
▪ From the IT professional's point of view, a detailed risk analysis is the first and perhaps most important step in justifying to management the cost to implement needed security measures.
▪ From the business manager's point of view, the risk analysis document provides a solid, objective basis for making budgetary and personnel-impacting decisions.
▪ Data collected during the risk analysis process forces both IT and management to face and acknowledge threats and vulnerabilities of which they might not have been aware or which they previously might have been able to ignore.
▪ Risk analysis allows the organization to focus resources on the existing threats and vulnerabilities and avoid wasting time and funds on unnecessary measures.
▪ Because the risk analysis process involves personnel throughout the organization, it can raise security awareness and help make appropriate security practices the responsibility of everyone who uses the computers and network. This is a basic tenet of crime prevention.
Assessing Threats and Threat Levels
The dictionary defines a threat as “somebody or something likely to cause harm.” The threat assessment portion of the risk analysis should include:
▪ Sources of potential threats
▪ The nature of potential threats
▪ The likelihood of occurrence of each potential threat type
▪ The estimated impact of each potential threat type
Sources of potential threats can be divided into internal and external categories. Although many security policies focus on the threat of a security breach from outside the network or organization (across the Internet), in actuality many organizations find that their biggest potential losses come from inside—the deliberate or unintentional actions of employees, contractors, and others who have legitimate access to the network. It is important to address both categories when performing a threat assessment.
Defining threat sources further requires that the assessment team determine both who and what could pose a threat to the network. For example, people who could pose a threat include most of the cybercriminal types discussed in Chapter 3. The nature of possible threats is the what in this equation. Any of these people could initiate threats of one or more of the following natures:
▪ Unauthorized access to data
▪ Unauthorized disclosure of information
▪ Destruction of data
▪ Modification or corruption of data
▪ Introduction of viruses, worms, or Trojans
▪ Denial or interruption of service or network congestion/slowdown
Note
A thorough threat assessment program will not overlook the threats posed by events such as fire, flood, and power loss as well as those caused by human agents.
The next step in threat analysis consists of assigning a likelihood or probability to each type of threat event. A high probability indicates that the threat event is more likely than not to occur, as when there is a history of its occurrence in the past. A medium probability indicates that the threat event might or might not occur. A low probability indicates that the threat event is not likely to occur, although it is possible. Finally, the assessment team must evaluate the probable impact on the organization for each potential threat event. For example:
▪ If the company's customer database were destroyed, how would this affect such activities as sales, billing, and so on?
▪ If the company network were down for one day, what is the potential cost to the company in lost sales, lost employee productivity, and the like?
▪ If the company's client records were made public, what is the potential loss in terms of lawsuits, withdrawal of client business, or similar actions?
Once all of these questions have been asked and answered, it is a relatively simple matter to construct a threat assessment matrix that will put this information into perspective and help the policy development team focus the company's security policies on the threat areas of highest likelihood and most significant impact.
Analyzing Organizational and Network Vulnerabilities
In previous chapters, we discussed how to analyze a network's technical vulnerabilities. These vulnerabilities are those characteristics or configurations that an attacker can exploit to gain unauthorized access or misuse your network and its resources. Network vulnerabilities are often referred to as security holes. Security holes should be identified as part of the policy development process. These vulnerabilities can be caused by a programming characteristic or (mis)configuration of the operating system, a protocol or service, or an application. Examples might include:
▪ Operating system code that allows hackers to crash a computer by accessing a file whose path contains certain reserved words
▪ Unnecessarily open TCP/UDP ports that hackers can use to get into or obtain information about the system
▪ A Web browser's handling of scripts which allow malicious code to execute unwanted commands
The network's connections to the Internet and other networks obviously affect vulnerability. Data on a network that is connected 24/7 via a high-speed link is more vulnerable than data on a network that is only intermittently connected to the outside. A network that allows multiple outside connections (such as modems and phone lines on a number of different computers) increases vulnerability to outside attack. Dial-up modem connections merit special consideration. Although a dial-up connection is less open to intrusion than a full-time dedicated connection—both because it is connected to the outside for a shorter time period, reducing the window of opportunity for intrusion, and because it usually has a dynamic IP address, making it harder for an intruder to locate it on multiple occasions—allowing workstations on the network to have modems and phone lines can create a huge security risk.
If improperly configured, a computer with a dial-up connection to the Internet that is also cabled to the internal network can act as a router, allowing outside intruders to access not just the workstation connected to the modem, but also other computers on the LAN. One reason for allowing modems at individual workstations is to allow users to dial up connections to other private networks. A more secure way to do this is to remove (or in the case of laptops, disable) the modems and have the users establish a VPN connection with the other private network through the LAN's Internet connection. The best security policy is to have as few connections from the internal network to the outside as possible and to control access at those entry points (the network perimeter).
Note
Third-party software tools known as vulnerability scanners are designed to discover the vulnerabilities on a network, using a database of known commonly exploited weaknesses and probing for those weaknesses on your network.
Organizational vulnerabilities are those areas and data that are open to danger or harm if exposed to an attack. To determine these vulnerabilities, the policy team should first identify the assets that could be exposed to the types of threats previously identified. These could include financial records, trade secrets, personal information (including customer/client information), intellectual property, and marketing and strategy documents.
You should consider a number of factors when you are assessing vulnerabilities, including the nature of the data that goes through the organization's network. The vulnerability of data that is highly confidential (such as trade secrets) or irreplaceable (such as original artwork or writing) should be of highest priority. Vulnerability is also affected by the size of the organization and network. A larger number of people who have access to the network indicates a greater chance of exposure to someone who will want to do harm.
Analyzing Organizational Factors
The next step in evaluating security needs is to determine the philosophy of the organization's mana-gement regarding security versus accessibility. It is important to remember that the two are conflicting characteristics; the more of one that a system has, the less of the other it will have. The organizational philosophy determines where on the security-access continuum a particular network falls (and thus determines its policies).
Some companies institute a highly structured, formal management style. Employees are expected to respect a strict chain of command, and information is generally disseminated on a “need to know” basis. Government agencies, especially those related to law enforcement such as police departments and investigative agencies often follow this philosophy, sometimes referred to as the paramilitary model.
Other companies, particularly those in “creative” industries and other fields that are subject to little state regulation, are built on the opposite premise: that all employees should have as much information and input as possible, that managers should function as “team leaders” rather than authoritarian supervisors, and that restrictions on employee actions should be imposed only when necessary for the efficiency and productivity of the organization. This is sometimes called the “one big happy family” model. Creativity is valued more than “going by the book,” and job satisfaction is considered to be an important aspect of enhancing employee performance and productivity.
In business management circles, these two diametrically opposed models are called Theory X (traditional paramilitary style) and Theory Y (modern, team-oriented approach). Although numerous other management models have been popularized in recent years, such as management by objective (MBO) and total quality management (TQM), each company's management style falls somewhere on the continuum between Theory X and Theory Y. The management model is based on the personal philosophies of the company's top decision makers regarding the relationship between management and employees.
The management model can have a profound influence on what is or isn't acceptable in planning security for the network. A “deny all access”-based security policy that is viewed as appropriate in a Theory X organization could meet with so much resentment and employee dissatisfaction in a Theory Y company that it disrupts business operations. Policy makers must always consider the company “atmosphere” as part of security planning. If there are good reasons to implement strict security in a Theory Y atmosphere, the restrictions will probably have to be justified to management and “sold” to employees, whereas those same restrictions might be accepted without question in a more traditional organization.
Considering Legal Factors
Security needs not only depend on the wishes of company managers, but they may also be dictated or at least guided by the criminal and civil laws in a particular jurisdiction. If the company's industry is subject to government regulations, the information on its network falls under privacy protection acts, or company contracts prohibit disclosure of information on the company network, these are legal factors that must be considered in establishing security policies.
It is important to protect the company from liability that might be incurred if employees or others using the network violate laws. For this reason, it is essential that the security policy development team include one or more attorneys who are well versed in applicable laws, and who are familiar with the terms of the company's contracts with partners, vendors, clients, and others.
Analyzing Cost Factors
Finally, but rarely of least concern, the needs evaluation must take into account the monetary cost of implementing heightened security. Determining the funds available for security upgrades will affect security policies by forcing the development team to differentiate the organization's security needs from security wants.
Cost factors can also force the team to prioritize security needs so that those threats that are most likely or most imminent can be addressed, those assets that are most important can be protected, and those vulnerabilities that are most egregious can be closed first.
Assessing Security Solutions
Once the company has identified and documented its security needs and established a working budget for addressing those needs, it is possible to assess solutions and determine which one(s) meet those needs within that budget. Network security solutions can generally be divided into three broad categories: hardware, software, and policy-only solutions.
Hardware Solutions
Hardware-based security solutions involve adding some physical device such as a dedicated firewall to protect the network or a smart card reader for logon authentication. Removal of diskette and CD/DVD drives from desktop computers to prevent unauthorized copying of files to removable media or introduction of viruses is also a hardware-based solution. Other security hardware devices include:
▪ Keystroke capture devices for monitoring computer use
▪ Hardware tokens for storing security keys
▪ Cryptographic hardware devices for offloading the processing of crypto operations
▪ Biometric authentication devices such as fingerprint or retina scanners
Hardware solutions can be more costly than software-only solutions, but they offer several advantages. Hardware security is usually more secure because there is less exposure of security information such as private keys, and it is more difficult to tamper with hardware than software. Hardware solutions also often offer faster performance.
Software Solutions
Software solutions include IDSes, packet/circuit/application filtering software, and security auditing software, as well as software firewall packages such as Microsoft's Internet Security and Acceleration (ISA) Server, which combine these functions. Other software security solutions are antivirus (AV) programs such as those made by Symantec, “spyware” used to monitor how computers are being used (including packet sniffer software that can capture and analyze network traffic), and network management packages that incorporate security features. Operating system and application “fixes” that patch security holes can also be placed in this category.
Policy Solutions
Most hardware and software security measures have accompanying policies that prescribe when and how they are to be deployed and used, but many security measures consist of policies only. For example:
▪ Policies that prohibit users from disclosing their passwords to anyone else
▪ Policies that require users to lock their workstations when they leave their desks
▪ Policies that require users to get permission before installing any software on their machines
▪ Policies that prohibit users from allowing anyone else to use the computer after they've logged on
Of course, in many cases policies will be enforced via software or hardware. For example, a policy that prohibits users from copying network files to their local disks can be enforced by permissions that allow read-only access. A policy that requires users to change their passwords every 30 days can be enforced by setting passwords to expire after that time period.
Complying with Security Standards
The security policy document should lay out standards regarding such issues as confidentiality and integrity of data, authorization and authentication, access, appropriate use of network resources, and employee privacy issues. If compliance with federal standards (such as a C2 rating) or industry-specific standards (such as HIPAA for healthcare organizations) is required, the specifications should be included and mandated in the policy document.
Policies should be reviewed for compliance with international standards such as ISO 17799. You might want to reference related sections of ISO 17799 in individual policies similarly to the reference to related policies.
Government Security Ratings
Security ratings might be of interest in the development of a company's security policy, although they are not likely to be important unless the organization works under government contract requiring a specified level of security. An international standard for computer security is ISO/IEC 15408, which was based on TCSEC (United States, CTCPEC (Canada), and ITSEC (Western Europe). As we discussed earlier, this standard is called the Common Criteria for Information Technology Security Evaluation (or Common Criteria for short). Your security policy might specify adherence to this particular set of standards or specifications.
A copy of ISO/IEC 15408 is available from the ISO Web site athttp://standards.iso.org/ittf/PubliclyAvailableStandards/index.html.
Utilizing Model Policies
Model security policies can be used to guide the policy development team in preparing a comprehensive policy document. Policy templates can be purchased from various sources (for example, RUSecure Information Security Policies), and sample policies are available for download from such organizations as the SANS Institute.
An advantage is that purchased model policies may be guaranteed to be compliant with ISO standards, HIPAA, or the like. However, policy makers should beware of simply copying a sample policy without an extensive review to ensure that the policies fit the organization's philosophy, budget, and business model. Sample policies are usually “sanitized”—that is, organization-specific issues have been removed to provide a generic policy that is designed to serve as a starting point in creating customized policies.
Common Policy Areas
In creating policies for an organization, a number of policy areas often need to be addressed. These include the following:
▪ Password Policies define the length and complexity of passwords, how often they must be changed, and other important qualities that we discussed in Chapter 11.
▪ Server and workstation security policies define rules governing physical security of network-connected computers, mandating logoff or password-protected screensavers when leaving a station unattended, system shutdown policies, sharing of workstations, and so forth.
▪ Encryption policies define when encryption should or shouldn't be used and the encryption technologies or algorithms that are acceptable. For example, a policy might mandate that specific proven algorithms such as 3DES, RSA, or IDEA be used and prohibit use of proprietary or nonstandard algorithms.
▪ E-mail policies govern such matters as opening e-mail attachments, using e-mail clients configured to display Hypertext Markup Language (HTML) mail, forwarding internal e-mail to people outside the organization, and so forth.
▪ Remote access policies define rules for connecting to the company network from outside using dial-in or VPN connections, specify what remote authentication methods can be used, prohibit “dual homing” (being connected to another network while simultaneously being connected to the company network), and so forth.
▪ Wireless access policies set forth standards for connecting to the corporate network using wireless equipment, requiring use of Wireless Equivalent Privacy (WEP) or other encryption technologies, prohibiting connection of unauthorized wireless access points to the network, and so forth.
▪ Acceptable use policies define what users are allowed to do or are prohibited from doing on the network, governing personal use (such as Web surfing, sending personal e-mail), downloading files, posting to newsgroups, prohibiting installation of unauthorized software applications, and so forth. We discussed this type of policy in Chapter 5.
Many other policy areas could be applicable to specific organizations; defining policy areas to be addressed is an important task for the policy development team. You can view examples of policy documents that cover the areas mentioned (and others) on the SANS Institute's Security Policy Project resource page at www.sans.org/resources/policies/
Developing the Policy Document
The policy development team should ideally be chosen prior to and be involved in the needs evaluation process. The team should comprise management and IT personnel, along with someone from each department within the organization. The team should include a legal advisor. As they begin to solidify and codify your policies, the team members must work closely together to:
▪ Establish security priorities based on the threat assessment matrix.
▪ Consider and incorporate security standards as needed.
▪ Determine the practices and procedures that are necessary to achieve the desired level of security at both the administrative and user levels.
▪ Clearly define both required and prohibited behaviors.
▪ Determine and define consequences for violations.
▪ Determine what policies are enforceable and methods for enforcement.
▪ Policies should represent a consensus as to what is and is not appropriate computer-related behavior.
Establishing Scope and Priorities
The policy development team should determine the scope of the policy document. For example, will policies regarding telephone, mobile phone, and fax use be included in the IT security policy or be part of a separate policy document? Will procedures for purchasing hardware and software be covered, or will this area be addressed in an overall organizational purchasing policy document? The easiest way to create a policy nightmare is to have two policy documents with conflicting directives.
Funds might not be available to address all security needs. Even if enough funds are allocated, most organizations will not be able to implement all security measures simultaneously. Thus, the team must establish priorities to determine which policies will be implemented first. Prioritization will be based on such factors as:
▪ Immediacy of the threat
▪ Potential loss
▪ Ease of implementation
▪ Available funding
We discussed immediacy of the threat and potential loss in the threat assessment section. Ease of implementation can also be a factor in prioritizing. Policies that can easily and quickly be implemented can be put in place first, while work begins on those that require more time and effort. Policies generally mandate one or more of the following: physical safeguards, technical security mechanisms, and/or administrative procedures. It can often be faster and easier to change administrative procedures than to implement physical safeguards (which could require purchase and setup of equipment or modifications to the facilities) or technical mechanisms (which could require purchase of software as well as a learning curve for IT personnel and users).
Policy Development Guidelines
Policies can be divided into different policy types: regulatory policies, which must be implemented to comply with the law or regulatory agency requirements; advisory policies, which are strongly recommended though not mandated; and information policies, which provide information but do not prescribe or proscribe any action.
Security policies can serve a number of secondary purposes in addition to the primary purpose of preventing unauthorized use of the network. For example, the policies can be the basis for personnel action (discipline or termination), can be used in the company's defense (or against it) in a civil lawsuit, and can even be instrumental in building a criminal case for prosecution. Thus, it is imperative that the policies that are finally published be well thought out, reasonable, and clearly articulated.
Policy writers should avoid technical jargon insofar as is possible; the security policies must be understandable to and usable by company managers, human resources personnel, and the users to whom they apply, as well as IT personnel. It's a good idea to include a glossary to define the technical terminology that is unavoidable. It is also important to create accountability; the person(s) responsible for each area of network/computer security and that person's scope of responsibility should be identified in the policy document.
Policies should state what actions are required, recommended, or prohibited. In addition to defining the action, they should give an example of behavior that would constitute that action, or a violation. For example, if the policy states, “Each user is required to protect the secrecy of his or her network logon password,” it should give concrete examples such as, “Users are required to memorize their passwords. Users are prohibited from possessing any written record of their passwords anywhere on company property and are prohibited from divulging their passwords to any other person. If any person asks a user to divulge his or her password, the user is required to report the request to the network administrator immediately.”
Policies should clearly state the consequences for violation. Consequences should be based on the severity of the violation, damage/loss caused, intent or lack thereof, and history of past violations. It's always important to ensure that the policies are consistent—not just with one another within the IT security policy document, but also with other company and departmental policies. Finally, it's imperative to make sure that policies don't conflict with any local, state, or federal laws.
Policy Document Organization
The policy document should not be a hodgepodge collection of security directives. It should be logically organized so that related policies are brought together under broadly defined areas. For example, sections might include:
▪ Physical security (placement of servers, installation of hardware, securing cabling, securing printers, location of backup tapes, and access to rooms/buildings where computer equipment is located)
▪ Password security (policies governing length of passwords, complexity of passwords, changing passwords, and protection of passwords)
▪ Network security (policies governing use of firewalls, downloading/uploading of files, Web access, and using instant messaging [IM] software)
▪ Server security (access to servers, protection of Web servers, file servers, DNS servers, and authentication servers)
▪ Remote access security (policies governing telecommuters, on-the-road executives, after-hours access from home, and designated VPN software and configurations)
▪ Data management and document-handling policies (policies that govern transferring and exchanging data, securing databases, modifying directory structures, creating/deleting files, naming files, and classifying data sensitivity)
▪ E-mail security (policies governing sending/receiving attachments, use of HTML mail, and e-mail client configuration settings)
▪ Software development policies (governing security and control over in-house software code)
▪ E-commerce security (governing online sales and purchases)
▪ Wireless communication security (policies governing standards for use of wireless devices on the network)
▪ Intranet and extranet policies (governing terms of access, acceptable use)
▪ Backup policies (scheduling, responsibility, retention, and storage)
▪ Disaster prevention and recovery policies (continuity of service, power backup)
▪ Policies governing security violations (responsibility to report, response handling)
▪ Policies governing employees who leave the company, both on friendly and on hostile terms (e.g., turning over equipment and access cards, deactivation of network accounts)
The policy document should contain a detailed table of contents. Each individual policy should have the following components:
▪ A title that describes clearly what the policy pertains to and a notation of any policy that it supercedes or replaces
▪ The effective date of the policy (and duration or expiration date if the policy is temporary)
▪ Reference to related policies
▪ A section stating the purpose or objective of the policy
▪ A section identifying the threat or vulnerability being addressed
▪ A section that lays out in detail the policy itself—that is, defining the act or acts that are required or prohibited; this should include identification of people responsible for implementing the policy, to whom the policy applies, and any exceptions to the policy
▪ Signature of the authority issuing the policy
Educating Network Users on Security Issues
The best security policies in the world will be ineffective if the network users are not aware of them or if the policies are so restrictive and place so many inconveniences on users that users go out of their way to attempt to circumvent them. The security plan itself should contain a program for educating network users—not just as to what the policies are, but why they are important and how the users benefit from them. Users should also be instructed in the best ways to comply with the policies and what to do if they are unable to comply or if they observe other users deliberately violating the policies. If users are involved in the planning and policy-making stages, it will be much easier to educate them and gain their support for the policies at the implementation and enforcement stages.
Policy Enforcement
To be effective, policies must be enforceable, and they must be enforced consistently. Policies that are unenforceable (perhaps because you don't have the means to detect violations) or that you are not willing to enforce are worse than useless; their existence undermines the credibility of the rest of the policies. Enforcement must not be selective; if exceptions to the policies are necessary for certain people or in certain circumstances, those exceptions should be laid out in the policy itself.
Enforcement authority should be divided among a number of people to provide a system of checks and balances. Employees should be made aware of who is responsible for policy enforcement, and the enforcement team must be given the authority to carry out the job (for example, the authority to monitor e-mail and Web access). Employees should be informed within the policy document that they may be subject to such monitoring.
Policy Dissemination
Copies of the IT security policy should be distributed to all personnel to whom the policies apply. All employees should be required to sign a statement acknowledging that they have received, have read, and agree to abide by the terms of the policy. Amendments to the policy should be distributed, and the distribution should be documented in the same way. This is important in the event that disciplinary action is taken against an employee for violation of the policy.
Copies of the policy can also be made available to organizational personnel in electronic format. This should be in addition to, not instead of, the procedure recommended earlier. One of the easiest ways to do this is on the intranet in HTML format. This allows the policy maker to create hyperlinks to reference documents and cross-reference related policies, and it makes it easy for users to search the document(s) for keywords and phrases. Security awareness and training policies might also be included and should specify required training for different levels of personnel (permanent staff members, temporary staff members, contractors, management, technical personnel, users of new systems, and so on).
Ongoing Assessment and Policy Update
The security policy is not a static document. Company business practices and priorities change, and new types of threats emerge as hackers learn new ways of accessing or attacking networks. The policy document should be reviewed on a regular basis and revised when necessary to meet new challenges and adapt to changing circumstances. The document itself should include a policy outlining the schedule for review, the person responsible for conducting the review, and the procedure for amending the document, as well as the procedure for disseminating changes to all affected personnel throughout the organization.
Summary
An understanding of basic security concepts gives a cybercrime investigator a distinct advantage in communicating intelligently with IT personnel and a better idea of exactly how a cybercrime was committed, based on the security measures in place at the time. Additionally, investigators should be proactive in helping the victims of cybercrime protect themselves against subsequent attacks. Although the investigator probably cannot and will not be expected to provide in-depth advice about the technical implementation of security systems, he or she should be able to discuss options in a general way and point crime victims in the right direction with some general suggestions.
A good investigator, like a good network security specialist or a good crime prevention officer, realizes that any security plan must be multilayered for it to be effective. It is important that all major security areas be addressed. These include physical security, perimeter security (through placement of firewalls at the network's entry points), security of data stored on disks (through file/disk encryption), security of data traveling across the network (through IP security), and a means of verifying the identities of users, computers, and other entities that have access to network resources (through the building of a PKI).
Many security technologies are based on or use cryptographic techniques. An investigator might encounter encrypted data or even suspect that the existence of additional data is being concealed using steganography. An understanding of how cryptography developed and how it works in the computerized environment can be invaluable in investigating many types of cybercrime. Knowing a little about different encryption types and the algorithms they use allows the investigator to assess just how secure a particular system is—whether it belongs to a cybercrime victim or to a cybercrime suspect.
Finally, it's useful for the investigator to understand the process involved in creating and deploying organizational security policies and to see samples of such policies to understand the “big picture” of where the policies came from (revealing the organization's overall security philosophy) and exactly how security is deployed within the organization to help narrow the focus of the investigation. A good cybercrime investigator has at least a surface knowledge of all aspects of IT security. He or she need not be a hands-on IT professional but should be able to “talk the talk” and understand what's being said when the real IT pros offer information about their organization's network.
Frequently Asked Questions
A No. Most security experts advise that only well-known, trusted, and tested algorithms be used. Although a vendor may claim that its product is more secure because the algorithms it uses are proprietary or secret, in reality proprietary algorithms are considered to be generally unsafe. Most of the best algorithms are public ones; knowing the algorithm doesn't help a hacker crack the encryption if the cipher is a strong one. If a vendor doesn't want to make its algorithm public, that might mean the vendor isn't confident that the algorithm can stand up to public scrutiny.
Q Is a firewall a foolproof, all-encompassing security method?
A There is no foolproof, all-encompassing security method; the only effective security plan is one that uses multiple layers of security. A firewall is an important part of such a plan. It provides protection at the perimeter of the network, but firewalls don't protect against many types of security breaches, such as internal breaches, physical breaches, or intrusions caused by compromise of user passwords. The Firewall FAQ site (www.faqs.org/faqs/firewalls-faq) notes that many organizations place a firewall on the network and think they're protected when there are numerous other vulnerabilities (such as dial-up modems on individual computers), similar to a person who has a 6-foot-thick steel door installed in a wooden house with unlocked windows. Firewalls also don't usually do a very good job of protecting against viruses and Trojans. On the other hand, the better firewalls do allow for very granular filtering of both incoming and outgoing data at different levels, based on the organization's needs. Every business network (and home computers that are connected to the Internet) should have some sort of firewall. Firewall products range from proprietary hardware appliances that cost thousands of dollars or high-end software firewalls that cost hundreds of dollars to simple freeware and shareware products that are suitable for home use. Windows XP and Vista even come with a built-in firewall; although it is a simple one that shouldn't be relied on to protect mission-critical systems.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
