Chapter 11. Passwords, Vulnerabilities, and Exploits
Introduction
Operating systems, networks, and other systems that have integrated security (or the illusion of it) need to be able to identify who is attempting to use the system. In most systems, this is done through a combination of a username and password, although other methods of identifying the user may also be used. Once the system has established who you are, it can then give you the authorized level of access associated with your account. For example, on a network, the logon information would be used to determine whether you have access to certain folders on a server, or whether you are allowed to use specific printers. Conversely, failing to give the appropriate logon information will prevent you from being able to enter the system. Because passwords are so widely used and are so important in terms of controlling access, acquiring passwords (especially those of administrators) is a common objective of hackers.
In this chapter, we'll look at what makes a good password, and how to crack bad ones. We'll discuss various types of attacks used to acquire passwords, how passwords stored on a system can be discovered and exploited, and how hackers use social engineering to con authorized users into disclosing their passwords. Because passwords aren't the only way of proving the identity of a person, we'll also look at a number of authentication devices, such as smart card readers, fingerprint scanners, retinal and iris scanners, and voice analysis devices.
In addition to weaknesses in passwords, we'll also discuss other vulnerabilities that attackers commonly exploit to gain access to systems. Even if you have done everything correctly to prevent unauthorized people from guessing or acquiring your password, that doesn't mean that everything was done correctly when the operating system, application, or Web site was created and deployed. Hackers and malicious software can still exploit software bugs, system configuration mistakes, and other vulnerabilities, leaving your system open to attack.
Authentication
Authentication is the process of verifying the identity of a user, computer, or process. In other words, it is proving that someone or something is who or what it claims to be. You can use many different methods to authenticate a user's (or in some cases, a computer's) identity. In general, the user is asked to provide something that is associated with his or her user account that someone else could not easily provide. In information security, this falls into one of three categories, which are referred to as authentication factors:
▪ Something you know One way to determine that a person is really who he or she claims to be is to ask a question that only the “real McCoy” is likely to be able to answer. If you are engaging in online messaging with someone who purports to be your brother, before discussing personal or sensitive subjects, you might ask him what your mother's oldest sister's name is, or ask him to name the song that the two of you played in a piano duet as children. In information security, the “something you know” is usually a password or personal identification number (PIN).
▪ Something you have Passwords can be compromised. For example, as we'll discuss later in this chapter, someone can discover passwords through a brute force attack or by watching over a user's shoulder as he or she types the password. In many of these cases, the user doesn't know that someone else now knows the password. A better authentication method is to require that the user provide a physical object, such as a “smart card” (a credit-card-size device with an embedded chip that contains authentication information). If the card is lost or stolen, the user is likely to know about it. Smart cards are used to log on to computer networks and to access bank accounts and make purchases.
▪ Something you are Although a card or other physical object that must be in the user's possession is a step up from password authentication, cards can be lost or stolen or perhaps even duplicated. An even more secure method of proving identity is via what you are, that is, biological data such as a fingerprint, voice print, or retinal or iris scan. Biometric methods are much more difficult to defeat than other identification methods.
When Is Authentication Necessary?
Authentication is necessary in a number of different circumstances, and different authentication methods are used in different circumstances. For example:
▪ Logon authentication When a user initially accesses the computer or network (when he or she logs on), a secure operating system will require that the user authenticate to a security accounts database. When logging on to the local computer, the user must enter an account name and password that are stored in a local security database on that machine's hard disk. When logging on to a server-based network (such as a Windows domain or a NetWare network), the user must enter an account name and password that are in the authentication server's database. Additionally, Windows domains require that computers have a computer account to join the domain. (The computer's credentials are sent to the domain controller automatically, without any user intervention.)
▪ Remote access authentication When a user accesses the network over a remote connection (dial up or virtual private network [VPN]), security is especially important because the computer from which the user is logging on isn't physically wired to the local network. Different, additional protocols are used for remote access authentication. When a remote logon is initiated, the remote client and the remote access server generally negotiate an authentication method and protocols that both are configured to support. There are a number of different methods for authenticating remote users, some of which we discuss in the following section, “Authentication Protocols.”
Note
In a network that uses an authentication server, users are authenticated when they log on to the network, and then access to individual network resources is controlled based on the permissions granted to the account with which the user logged on. In workgroup (peer-to-peer, or P2P) networks, there is no authentication server, but access to resources can be protected using file-level security. Passwords are assigned to individual resources, and those passwords are shared with users who are authorized to access them. Every time a user wants to open a particular file or use a particular printer, he or she must enter the correct password. This is not really authentication, because the user's identity isn't verified (the password is not associated with a user account), although entering the password does verify that the user is authorized to access the resource.
Authentication Protocols
The protocols used for authenticating identity depend on the authentication type. Some common protocols used for authentication include the following:
▪ Kerberos The default logon authentication protocol used by Windows 2000, XP, and Vista, as well as by Windows Server 2003 and Windows Server 2008. It is also used by Mac OS X. This protocol is based on secret key (symmetric) cryptography, which we'll discuss in Chapter 12. This system uses tickets that a central server issues to determine whether a user can access the network and its resources. Rather than being used to log on to each server, the tickets are used by all of the servers to determine what a user is permitted to access.
▪ Challenge Handshake Authentication Protocol (CHAP) Uses a sequence in which one party sends a challenge and the other responds with an answer. The most common form of this sequence is the server requesting a password, which the client provides to gain access to a system. Microsoft developed its own version of the protocol, called MS-CHAP.
▪ NT LAN Manager (NTLM) Another Microsoft logon authentication method that is supported by newer versions of Windows. NTLMv2 provides more security than NTLMv1, and uses a challenge-response sequence to authenticate the user. Unlike Kerberos, with NTLM, when a client wants to access a server's resources, that server must contact the domain controller to have the client's identity verified. The client doesn't have credentials already issued (the session ticket in Kerberos) that the file or application server knows it can trust.
▪ Password Authentication Protocol (PAP) A remote access authentication protocol used for Point-to-Point (PPP) or dial-up connections. Its distinguishing characteristic (and the reason it should not be used on secure networks) is the fact that it sends passwords in plain text. This means an unauthorized person can intercept and use the passwords during transmission. The only good reason to use PAP is if you face a situation in which the remote server doesn't support other, more secure authentication methods. Shiva PAP (S-PAP) addresses this problem by using a two-way reversible authentication method that encrypts passwords so that they will not be subject to interception and misuse.
▪ The Remote Authentication Dial-in User Service (RADIUS) Another means of authenticating remote connections that takes the authentication responsibility off each individual remote access server by providing a centralized server to authenticate clients securely.
▪ Secure Shell (SSH) Allows users to log on to UNIX systems remotely. Both ends of the connection (client and server) are authenticated, and data—as well as passwords—can be encrypted.
Note
In Chapter 12, we'll discuss a number of these protocols and how many of them use various types of encryption to ensure that data passed between a client and a server is secure.
Identity Confirmed; Now What?
Once a user's identity has been established, the next step in the security process is authorization, which is concerned with what that user is permitted to do. Authentication and authorization work together to provide a security system that takes into account the need for different users to have different capabilities on the network.
Administrators can control which files and other objects a user can access and the level of access (read only, change, and so on) by setting permissions. Most network operating systems provide a mechanism for associating specific permissions on an object with certain user accounts or groups. For example, Windows computers that have hard disks formatted as New Technology File System (NTFS) provide for two levels of permissions: share permissions that apply only to users accessing the resource across the network, and file-level permissions (also called NTFS permissions) that apply both across the network and to users accessing the resource from the local machine.
Administrators can also control which system-wide actions a particular user (or group of users) can perform by setting user rights. User rights differ from permissions in that permissions apply to access of individual files, folders, printers, and other objects.
Passwords
The most common method used for authentication, and for determining whether someone should be allowed access, is the use of passwords. Passwords are a series of characters that are used to access computers, programs, and other secure systems that require security. They are used to prevent unauthorized access to computers, networks, and other technologies by forcing anyone who wants access to provide specific information. The password may consist of numbers, letters, symbols, or a combination of these.
Even though the password works like a key that gives you access, many people essentially leave the key under the mat by the front door. It's common that users don't consider the importance of their passwords, and use ones that are easy to remember, and thereby easy to guess. For example, a person may use the password “money” for his or her online banking, and administrators too often use the word “password” as a password for accessing servers or applications. Many systems also allow the use of spaces in the password so that multiple words can be used as a pass phrase. The problem with this is that users will often use easy-to-guess words, such as the name of their favorite sports team, or even their first and last names. Some of the other common errors people make when using passwords include:
▪ Using a sequence of numbers or letters, such as “1234” or “abcd”.
▪ Using characters that are adjacent on the keyboard, such as “qwerty”.
▪ Using common sources for passwords, such as your username, birthday, name of a loved one, and so on.
▪ Using numbers or symbols that look like letters, such as “P@ssw0rd”. This practice is so common that hackers will try such combinations when cracking a password. After all, many of them have been spelling words like this in chat rooms since the early days of the Internet, or even earlier on bulletin board systems (BBSes).
To make passwords more secure, strong passwords should be used. A strong password is a password that is complex and secure. You can create strong passwords by using a combination of two or more of the following keyboard characters:
▪ Lowercase letters (a–z)
▪ Uppercase letters (A–Z)
▪ Numbers (0–9)
▪ Special characters (({}[],.<>;:'”?/|`~!@#$%^&*()_-+=)
As you might expect, the more characters you use in a password, the more secure it will be. For this reason, many Web sites and networks require a minimum password length of eight or more characters. Unfortunately, by creating a long mix of characters, its not uncommon for people to forget their passwords.
A simple way to create a long password is to think of a sentence, and convert it to a strong password. For example, if we used the phrase “My daughter Sara is 5 years old,” we could take the first letter of each word to create the password MdSi5yo.
One Password, Many Places
Even if strong passwords are used, the same ones shouldn't be used again and again. A common practice is for people to have one or a few small passwords, and then reuse them on multiple sites. If you used a single password over and over, a person who acquired your password could then access multiple systems.
Password Policies
In the networking world, passwords (in combination with user account names) are normally the “keys to the kingdom” that provide access to network resources and data. To ensure the security of systems, policies should be in place dictating how a network user's password is created and changed. An effective password policy is a basic component of a security plan, but it is often more difficult to implement than it might appear at first glance. To be effective, a password policy must require users to select passwords that are difficult to “crack” yet easy for them to remember so that they don't commit the common security breach of writing the password on a “sticky note” that will end up stuck to the monitor or sitting prominently in the top desk drawer.
A good password policy is the first line of defense in protecting the network from intruders. Careless password practices (choosing common passwords such as god or love or the user's spouse's name; choosing short, all-alpha, one-case passwords; writing passwords down or sending them across the network in plain text) are like leaving your car doors unlocked with the keys in the ignition. Although some intruders might target a specific system, many others are just “browsing” for a network that's easy to break into. Lack of a good password policy is an open invitation to them.
Policy developers must remember that expensive, sophisticated firewalls and other strict security measures (short of biometric scanning devices that recognize fingerprints or retinal images, as we'll discuss later in this chapter) will not protect the network if an intruder has knowledge of a valid username and password. It is particularly important to use strong passwords for administrative accounts.
Best practices for password creation require that you address the following, each of which is discussed in the sections that follow:
▪ Password length and complexity.
▪ Who creates the password?
▪ Forced changing of passwords.
Password Length and Complexity
It's easy to define a “bad” password—it's one that someone other than the authorized user can easily guess. As we'll see later in this chapter, one way in which “crackers” do their work is via the brute force attack. In this kind of attack, the cracker manually or, more often, using a script or specially written software program, simply tries every possible combination of characters until he or she finally hits upon the right one. It goes without saying that using this method, it will be easier to guess a short password than a longer one because there are fewer possible combinations. For this reason, most security experts recommend that passwords have a minimum required length (for example, eight characters). Modern network operating systems such as Windows Server 200x allow domain administrators to impose such rules so that if a user attempts to set a password that doesn't meet the minimum length requirement, the password change will be rejected.
Who Creates the Password?
Network administrators might be tempted to institute a policy whereby they create all passwords and issue them to the users. This policy has the advantage of ensuring that all passwords meet the administrator's criteria in regard to length and complexity. However, it has a few big disadvantages as well:
▪ It places a heavy burden on administrators, who must handle all password changes and be responsible for letting users know what their passwords are. Of course, an administrator would not want to notify a user of his or her password via e-mail or other insecure channels. In fact, the best way to do so is to personally deliver the password information. In a large organization, this becomes particularly taxing if there is a policy requiring that passwords be changed on a regular basis.
▪ If the administrator creates all passwords, this means the administrator knows everyone's password. This might or might not be acceptable under the overall security policy. Some users (including management) could be uncomfortable with the idea that the administrator knows their passwords. Even though an administrator can generally access a user's account and/or files without knowing the password, it is less obvious to the users and thus less of a concern.
Allowing users to create their own passwords within set parameters (length and complexity requirements) is usually the best option. The user is less likely to forget the password because he or she can create a complex password that is meaningless to anyone else but has meaning to him or her. For example, it would be difficult for others to guess the password Mft2doSmis. It has 10 characters, combines alpha and numeric characters, and combines upper- and lowercase letters in a seemingly random manner. To a user, it might be easy to remember because it stands for “My favorite thing to do on Sunday morning is sleep.”
Password Change Policy
Best practices dictate that users change their passwords at regular intervals and after any suspected security breach. Modern network operating systems such as Novell NetWare and Windows Server 200x allow the administrator to set a maximum password age, forcing users to change their passwords at the end of the specified period (in days). Password expiration periods can be set from one to 999 days. Individual user accounts that need to keep the same passwords can be configured so that their passwords never expire. This overrides the general password expiration setting.
Because it is the nature of most users to make their passwords as easy to remember as possible, policies should strive to prevent the following practices, all of which can present security risks:
▪ Changing the password to a variation of the same password (for example, changing from Tag2mB to Tag3mB)
▪ Changing the password back and forth between two favored passwords each time a change is required (that is, changing from Tag2mB to VERoh9 and back again continuously)
▪ “Changing” the password to the same password (entering the same password for the new password as was already being used)
Administrators can use operating system features to prevent these practices. For example, in Windows XP and Vista, you can configure the operating system to remember the user's password history so that up to a maximum of the last 24 passwords will be recorded and the user will not be able to change the password to one that has been used during that time. As shown in Figure 11.1, you can configure these settings in the Microsoft Management Console (MMC) by loading the Local Users and Groups snap-in, and modifying the settings found in Local Computer Policy | Computer Configuration | Windows Settings | Account Policies | Password Policy.
 |
| Figure 11.1 Password Policy Settings in Local Computer Policy on Windows XP |
Summary of Best Password Practices
Here is a short overview of the best password practices:
▪ Passwords should have a minimum of eight characters.
▪ Passwords should not be “dictionary” words.
▪ Passwords should consist of a mixture of alpha, numeric, and symbol characters.
▪ Passwords should be created by their users.
▪ Passwords should be easy for users to remember.
▪ Passwords should never be written down.
▪ Passwords should be changed on a regular basis.
▪ Passwords should be changed anytime compromise is suspected.
▪ Password change policies should prevent users from making only slight changes.
How High Security Can Turn into High Risk
Paradoxically, overly restrictive security policies can even result in lowered security (while creating a false sense of high security) because frustrated employees will look for ways to circumvent security measures, intentionally or unintentionally. Gung-ho security enthusiasts who march in and “tighten up” a network without taking user needs into account can do more harm than good in the long run, despite the best of intentions.
The simplest example is the imposition of a policy that requires employees to use randomly generated 20-character passwords that change every week. Because they are unable to remember such passwords, employees are much more likely to resort to writing them down (even if that is a violation of policy) than if the employees themselves chose their own passwords so that the passwords would have meaning to the people who must remember them. Writing down the passwords (especially because people tend to keep that little note close to the computer, for convenience) poses a much greater security risk than the possibility that user-selected passwords might be a little easier to crack. A compromise solution here is to allow users to select their own passwords, but also to set policies (which can be enforced using appropriate software) requiring that user passwords meet a minimum length and complexity—for example, stipulating that both alpha and numeric characters must be included, and that the password must be at least eight characters long.
Locking Computers with Passwords
You also can configure computers to prevent unauthorized access by locking them with passwords. Computers can provide screensavers with password protection so that anyone without the password is unable to access the system. For example, Novell NetWare servers provide a password-protected screensaver that you can activate by entering the command SCRSAVER ACTIVATE from the server prompt. To deactivate the password, the user needs to enter a username and password with sufficient privileges. Windows computers also provide password protection on screensavers, which prevents access to the machines while the owner or designated user is away.
One of the problems with password-protected screensavers is that an intruder can bypass the protection by rebooting the machine. When the OS is loaded, the screensaver is off, so the intruder can access the data and applications on the machine. To ensure that this does not happen, you should use additional methods of protecting a machine with passwords. As we mentioned, you can set up local user accounts so that usernames and passwords must be entered to gain access once the OS has loaded. These types of accounts are different from network accounts, as they are used to control access on the machine itself. You can set up user accounts on a variety of OSes, including Windows XP and Vista, and provide protection from unauthorized access.
To set up local user accounts on Windows XP machines, you use the User Accounts applet in the Control Panel. As shown in Figure 11.2, the User Accounts applet provides an easy-to-use interface that allows you to create and maintain accounts on your computer. This is different from previous versions of Windows, in which all users could log on to the machine using the same account. In XP and Vista, each user is required to have his or her own account, allowing administrators to control what permissions and resources users have access to on the local machine. When you click on the Create a new account link, a wizard appears that takes you step by step through the process of setting up a new account. Once you've set up the new account, you can then click Change an account to modify a particular account's password, and other elements of the account.
 |
| Figure 11.2 The User Accounts Applet, Which You Use to Create Usernames and Passwords for the Local Computer |
The alternative method of accessing a version of this tool is through the Run command on the Start menu. When you type control userpasswords2 in Start | Run and then click OK, a dialog box similar to the one in Figure 11.3 will appear. As you can see from this dialog box, not only can you create and manage local users, but by checking the Users must enter a user name and password to use this computer checkbox, users are forced to have individual accounts that they must use to enter a username and password to log on to the computer.
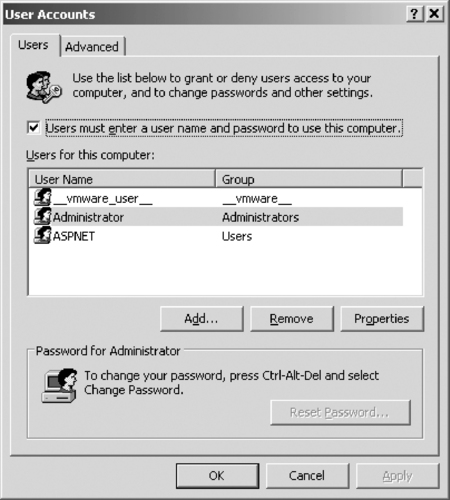 |
| Figure 11.3 The User Accounts Dialog Box, Which You Use to Force Users to Enter a Username and Password |
Although this prevents people without valid user accounts from using the machine, it does not prevent someone from accessing a system that a valid user has already logged on to. People often need to walk away from their computers, leaving themselves logged on with files open. Because it is not practical to shut down your computer every time you leave your desk, the Lock Workstation feature is available. The Windows Security dialog box appears when you press Ctrl + Alt + Del on machines running Windows OSes. When you click on the Lock Computer option, another dialog box requesting a username and password appears. Only the person logged on to the computer or an account that is a member of the Administrators group will be able to unlock the machine. A similar Lock Workstation feature is also available for machines running Novell NetWare.
You can force users to press Ctrl + Alt + Del to log on using either of two methods in Windows XP. When you open the User Accounts dialog box using the control userpasswords2 command, the Advanced tab has a checkbox titled “Require users to press CTRL+ALT+DEL” which, when checked, forces users to log on in this manner. You can also configure this setting using the Local Security Settings applet that you can access through Administrative Tools in the Control Panel. In Local Security Settings you would expand Local Policies and then click on Security Options. In the right pane, a listing of policies will appear. By double-clicking on Interactive logon: Do not require CTRL + ALT + DEL, you can enable or disable the policy.
Another method of protecting a machine is by setting passwords that prevent unauthorized users from starting up the machine and/or changing the settings. On many machines, you can access a setup program that allows you to configure the system by pressing the F10 or Del key when the computer is first turned on. When the setup software appears, generally you'll see options that allow you to set passwords. You can set a Power-On Password, requiring anyone who starts the computer to enter a password before the OS loads. This prohibits hackers from using password-cracking tools to gain entry through the OS. You also can set another password in the Basic Input Output System (BIOS) to prevent unauthorized people from accessing the setup software and making changes to the computer. Setting this password also prevents malicious users from configuring Power-On and BIOS passwords, which would restrict valid users from starting the computer or making system changes.
Understanding Password Cracking
The best way to get into a system is to “trick” the system into thinking you're an authorized user. In many cases, you can do this simply by using a valid account name and password. This method is called password cracking. In this section, we look at the tools and resources hackers use to crack passwords. Investigators need to be aware of all the techniques and tools that can be used to impersonate a legitimate user and how they work. Understanding how a crack was accomplished provides valuable clues to the cracker's skill level and how determined he or she is to get into a particular network, as well as other characteristics that can help track down the culprit.
Password cracking involves acquiring valid passwords. You can do this in several ways, including:
▪ Via various types of attacks
▪ Recovery and exploitation of passwords stored on the system
▪ Use of password decryption software
▪ Social engineering
In the following sections, we look at each of these methods and ways to protect against them.
Types of Password Cracking
Ever since the first passwords were used, methods have been available for trying to crack the actual text-based version of the password. We can crack passwords for two reasons. One, users can select a weak password if the administrator has not enforced a strict password policy; two, some vendors have done a poor job scrambling the password. We will discuss several methods of attacking passwords. The methods are guessing, dictionary, brute force, syllable attack, rule-based, and hybrid.
Guessing Attack
In the guessing attack, perpetrators are successful when they are able to guess a person's password. This can occur if a user has selected a blank password. It can also occur if the user has chosen a simple password such as “password.” Some users think they are smart, and will try a word in reverse, such as “drowssap.” Another problem is when users select a password based on their kids, spouse, relative, or other personal information that is easy to identify.
Dictionary Attack
With a dictionary attack you load a file of dictionary words into the password cracking tool, and if the password is one of the words within the dictionary file it is cracked. It is important to note that dictionary files are available for many languages; therefore, it is a simple process of loading your dictionary for the country in which you are conducting the testing. Consultants have successfully cracked many passwords of foreign languages using this technique—a dictionary even exists for the Klingon language.
Brute Force Attack
In the brute force method of password attacking, the concept is to try every possible combination of characters until a password is found. It is the slowest method of attack, but given enough time and resources it will discover any password.
Syllable Attack
The syllable attack is a combination of brute force attack and dictionary attack. The technique usually is used when the password is known to be a nonexistent word.
Rule-Based Attack
The rule-based attack is used when the perpetrator is able to get some information about the password, usually following some form of enumeration that has identified the password policy in place for an organization. For example, if the policy indicates that the length of the password is not fewer than eight characters and must contain at least numbers and a special character, the perpetrator will adjust and customize the cracking tool for this.
Hybrid Attack
A hybrid attack is used to find a password that is a dictionary word with combinations of characters prepended or postpended to it. This attack is surprisingly successful, because in most cases users will select a password that is a dictionary word surrounded by additional characters.
Rainbow Attack
The rainbow attack technique works by calculating all the possible hashes for a character set, and storing them in a table. The password hash is presented to the tool that uses the rainbow algorithm, and a table search is made until the password is found. This is a much quicker method than the other types of attack; however, the limitation of the rainbow technique is the size requirements for a table, so you need to think in terms of terabytes for complex passwords.
Password Recovery Tools
A large number of password recovery programs are available on the Internet, and they are often marketed as security tools. You might not immediately think that password-cracking programs also have a legitimate use. An employee might leave a company or die suddenly without revealing passwords that were used to protect important files, which other employees now need to access. Even if they're still around, sometimes employees forget their passwords. Some companies do password recovery as a service. One such company is Password Crackers Inc. (www.pwcrack.com). Programs marketed for legitimate purposes are usually called password recovery programs, but of course crackers can use the same software for less-than-legitimate purposes.
Note
Some recovery programs are focused on operating system passwords and others on application passwords. The Passware software at www.lostpassword.com is a modular system that lets you select modules according to your needs, to recover passwords in Windows 2000, XP, Vista, and other operating systems, as well as Excel, Access, Outlook, Word, WinZip, WordPerfect, QuickBooks, ACT, and more. The Passware Kit includes all the modules, and you can download a free demo version from the site.
Some password protection schemes are more difficult to crack than others. The passwords on documents created with older versions of Microsoft Office and zipped files are notoriously easy to crack with readily available software. With any password scheme, the better (the longer and more complex) the passwords, the longer it takes to crack them. For difficult cracking jobs, some tools even allow you to divide the task into parts and use multiple machines simultaneously to work on it in a method called distributed cracking. In the sections that follow, we'll discuss a number of the most popular tools used by network administrators, computer forensic investigators, and crackers alike.
Decryption Collection Enterprise
Paraben's Decryption Collection Enterprise is an advanced password recovery suite with support for Windows Vista and Server 2003, EFS, SQL, and Lotus Notes along with support for everything included in the Standard Edition of the suite. One of its most advanced features is its ability to distribute its processing on a network of up to 16 computers. This allows brute force or dictionary attacks using several computers. This tool is available from www.paraben-forensics.com and its features include:
▪ MD5 hash verification
▪ An easy-to-use interface that lets you just drag and drop the file to be recovered
▪ A listing of the most recent files recovered
▪ Hypertext Markup Language (HTML) reporting of recovery results
▪ A password cache for quick recovery of repeat passwords
▪ English password recovery accuracy of 90 percent and higher
Reactive Software
Reactive Software (www.reactive-software.com) has created a number of utilities that can decrypt the logon passwords used by instant messaging (IM) tools such as AOL Instant Messenger, Google Talk, Miranda, MSN Messenger, Paltalk, Trillian, and Windows Live Messenger. The company also has tools for acquiring passwords used in other tools and services, such as File Transfer Protocol (FTP) tools (CuteFTP, WS FTP, and so on), online mail services (Hotmail, Gmail), Voice over IP (VoIP) tools such as Skype, and other utilities.
Cain and Abel
A Windows-based password recovery tool, Cain and Abel uses multiple methods to capture password hashes. It can get the hash from the network, or it can dump it from the local machine. Cain and Abel uses dictionary attacks, brute force, and other cryptanalysis techniques to crack passwords. In addition, it can sniff the network for data, can record VoIP conversations, and has other features that go beyond simple password cracking. Figure 11.4 shows the password cracking capabilities of this tool.
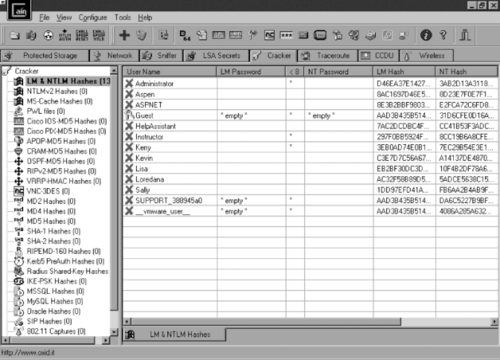 |
| Figure 11.4 Password Cracking with Cain and Abel |
LCP
The LCP tool was developed as a free alternative to the very popular L0phtcrack tool that was the pioneer in cracking passwords on a Windows platform. L0phtcrack is no longer offered, and LCP is an excellent way to get the features that used to be available with L0phtcrack. The tool offers the ability to import from a variety of formats, and it uses dictionary, hybrid, and brute force attack methodologies to discover passwords. Figure 11.5 shows the LCP tool with a dump of the SAM database.
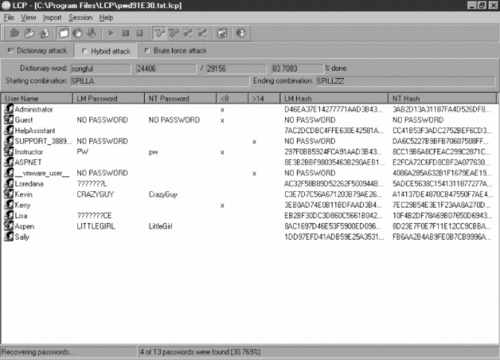 |
| Figure 11.5 LCP with a Dump of the SAM Database |
Ophcrack
Ophcrack is a Windows-based password cracker that uses the concept of rainbow cracking methodology by conducting the crack from existing rainbow tables. The algorithm deployed is based on the time-memory trade-off technique of precomputing all possible hashes and then applying the hash to the table.
John the Ripper
John the Ripper (JTR) is a fast password cracking tool that will not only crack Windows-based passwords, but also passwords on UNIX and Linux systems. The tool runs within UNIX and Linux environments.
Exploitation of Stored Passwords
Trying to guess passwords, even with software to expedite the process, is a tedious business. It would be much easier if a cracker could just find a list of passwords lying around somewhere. Well, in some cases, that's exactly what happens—the list is right there for the taking on the computer's hard disk. Passwords have to be stored somewhere; after all, how else will the system know whether a user has entered the correct password? Additionally, most people have several different passwords in addition to their logon passwords; these are used for e-mail access, entry to restricted Web sites, and the like. Rather than memorizing all these secondary passwords, many users elect to have the system “remember” the password for them. Because computers have short memories (you'll recall that all the data in RAM is lost when the computer is rebooted), these “remembered” passwords must be stored in a file somewhere. All a cracker has to do is get his or her eager little hands on that file.
Thank goodness it's a little more complicated than that. In most cases, passwords are not stored in a plain-text file that the cracker can simply open and read, except in cases in which a forgetful user creates such a file, diligently recording passwords for various services and applications. Usually, stored passwords are encrypted or hashed.
For example, UNIX systems store passwords in a file located in one of several places—the /etc /passwd file, /etc/shadow (or /etc/master.passwd on BSD systems)—along with other user information. The passwords are encrypted with a hash function. The computer doesn't compare the actual password you type in to a list to determine whether to log you on; instead, the password you enter is hashed and the resultant hash value is compared to that of the stored (hashed) password.
This system sounds foolproof, but it's not. The cracking software just needs to be a little more sophisticated. If the cracker can get the password file, the program uses whatever hash function the system uses and encrypts possible passwords (generating them via brute force and dictionary methods), then compares the results with the encrypted passwords in the password file. This technique is called comparative analysis.
Note
UNIX and Linux systems can use shadow passwords to circumvent comparative analysis techniques. If shadow passwords are enabled, the encrypted password in the passwd file is replaced by an x. The real passwords are stored in another file, called /etc/shadow. What good does it do to store the information in a different file, especially when everyone familiar with UNIX knows the name and location of that file? The secret is that the /etc/shadow file can be accessed only by the root account. Although group accounts usually aren't assigned passwords, they can be. Group passwords can be shadowed like user passwords. In that case, the encrypted passwords are stored in a file called /etc/gshadow.
Why does all of this matter to the investigator? In some cases, an investigator can use his or her knowledge of how various operating systems store passwords to track criminals' actions. If security auditing is properly configured, investigators will be able to tell whether and when various files have been accessed. Logs that record access to password files could indicate that passwords have been or will be compromised.
Interception of Passwords
Crackers don't always have to access password files or resort to guessing (brute force) to learn usable passwords. When passwords are sent across the network via local or remote access connections in plain-text form, they can be intercepted, as can other data traveling across the network, using sniffer software. Telnet sessions to UNIX computers can be intercepted and the plain-text password extrapolated if security measures haven't been taken. Use of nonsecure authentication protocols such as PAP for remote access results in sending plain-text passwords across the link and should be avoided when possible.
Note
We discuss authentication protocols in more detail in Chapter 12.
Another means of intercepting passwords is to use a keystroke logger. This is a hardware device or software program that captures and records every character that is typed—including passwords. In many cases, when the program or tool is installed on a computer, there is no indication that the program is running. Users on the machine have no idea that everything they type is being recorded to a file, or in some cases e-mailed at regular intervals to the person who installed the program.
It is often possible to detect an unauthorized packet sniffer on the wire using a device called a time domain reflectometer (TDR), which sends a pulse down the cable and creates a graph of the reflections that are returned. Users who know how to read the graph can tell whether and where unauthorized devices are attached to the cable.
Other ways of detecting unauthorized connections include monitoring hub or switch lights, using Simple Network Management Protocol (SNMP) managers that log connections and disconnections, or using one of the many tools designed for the specific purpose of detecting sniffers on the network.
Password Decryption Software
Most password-cracking programs don't actually decrypt anything. However, if the encryption algorithm is weak or implemented incorrectly, it is sometimes possible to use a technique called one-byte patching, which is able to decrypt the password by changing one byte in the program. Another technique used with weak algorithms requires that the cracker already have obtained one or more files in decrypted form; then they can be used to decrypt others that use the same algorithm. This is called the known plain-text method. This technique is popular as an attack against password-protected .zip, .rar, and .arj files. All of these are extensions used for compressed archive files.
When strong cryptography is used and complex passwords are chosen, it is much more difficult to use direct decryption; in these cases, a dictionary or brute force attack is more often successful. PDF “decryptors” such as Guaranteed PDF Decryptor/Restrictions Remover (GuaPDF) use a type of brute force that involves testing all possible keys.
The Weak Encryption Debate
Many security experts feel that weak, easily broken encryption is worse than no encryption at all because it gives users a false sense of security, leading them to be careless with sensitive data because they believe it is protected. Others argue that weak encryption is better than no encryption because it at least keeps out the casual, merely curious, or technically unsophisticated “snoop.” The truth, as usual, lies between the extremes; weak encryption might be beneficial in some situations—for example, for a noncritical document such as a personal journal that a user wants to protect from other, nontechnical users who share the computer. On the other hand, weak security can be disastrous in the case of vitally important information such as trade secrets or military data that is likely to be targeted by technically sophisticated crackers. In this situation, the weak encryption actually can be worse than none at all because the fact that the file is encrypted draws the attention of the cracker, who might otherwise have ignored it.
Authentication Devices
From the previous sections, it becomes apparent that despite the widespread use of passwords, they are not the safest way to authenticate a user … at least, not by themselves. Many organizations where security is a priority use multifactor authentication, in which a combination of authentication factors are used to identify who or what is attempting to access the system. To enhance security, usernames and passwords may be used with hardware-based solutions, such as:
▪ Smart card readers
▪ Fingerprint scanners
▪ Retinal and iris scanners
▪ Voice analysis devices
These devices can be used in environments that require a high level of security for secure and reliable network authentication. Microsoft has incorporated support for authentication devices such as smart card authentication for years, and continues to add new features that support hardware-based authentication.
Smart Card Authentication
The term smart card has several different meanings. In a broad sense, it refers to any plastic credit- card-size card that has a computer chip (a memory chip and/or a tiny microprocessor) embedded in it to hold information that can be changed (as opposed to less “smart” cards that use a magnetic strip that holds static information). A smart card reader—a hardware device—is needed to write to and read the information on the card. Smart cards can be used for different purposes, but one of the most popular is for authentication. Satellite television services use smart cards in the SATV receiver to identify the subscriber and that subscriber's service level. Banks use smart cards for conducting transactions.
Smart cards can also be used for network logon authentication. This provides an extra level of security, the “something you have” factor described earlier in this chapter. The cards are generally resistant to tampering and are relatively difficult for a hacker to compromise, because they are self-contained. They're also inexpensive in comparison to biometric authentication devices.
Smart cards used for logon authentication generally store a digital certificate that contains user identification information, the user's public key, and the signature of the trusted third party that issued the certificate, as well as a time for which the certificate is valid. As we'll discuss in greater detail in Chapter 12, digital certificates are used to prove the identity of users. The certificates are stored on the cards by an authorized administrator. To log on with a smart card, a user must insert the card in the reader or swipe it through and enter a PIN that is associated with the card. This PIN is a numeric sequence that serves the same purpose as a password. If the PIN is compromised, an administrator can change it or issue a new card. To use smart cards for network logon, the computer must run an operating system that supports smart card authentication, such as Windows 200x, XP, or Vista, or use add-on software such as Sphinx (www.securetech-corp.com/sphinx.html).
A number of companies manufacture smart cards and readers. Some vendors make keyboards that have built-in smart card readers, and there are combination fingerprint scanner/smart card readers for providing both card-based and biometric security.
Although smart cards provide for extra security, they (like all authentication methods) are not foolproof. Many cryptographers have been able to “break” smart card encryption. In general, there are two methods for defeating smart cards: logical and physical. An example of the logical attack is erasing parts of the data on the embedded microchip by raising or dropping the voltage; in some cases, this activity “unlocks” the security without deleting the data. A physical attack might involve actually cutting the chip out of the card and using a laser-cutter microscope to examine it. Although a determined attacker might be able to crack the smart card in this way, these methods are not easy and they don't always work.
Biometric Authentication
Biometric authentication devices rely on physical characteristics such as a fingerprint, facial patterns, or iris or retinal patterns to verify user identity. Biometric authentication is becoming popular for many purposes, including network logon. A biometric template or identifier (a sample known to be from the authorized user) must be stored in a database for the device to compare to a new sample given during the logon process. Biometrics is often used in conjunction with smart cards in high-security environments. The most popular types of biometric devices are the following:
▪ Fingerprint scanners These are widely available for both desktop and portable computers from a variety of vendors, connecting via a Universal Serial Bus (USB) or PCMCIA (PC Card) interface.
▪ Hand geometry recognition devices These are similar to facial pattern devices but analyze hand geometry.
▪ Iris scan identification devices Iris scanners analyze the trabecular meshwork tissue in the iris, which is permanently formed during the eighth month of human gestation.
▪ Retinal scan identification devices Retina scanners analyze the patterns of blood vessels on the retina.
A large number of physiological characteristics can be used as identifiers, and devices have been developed that verify identity based on knee scans, ear geometry, vein pattern recognition, and even body odor recognition. In addition, some devices analyze and compare behavioral traits using methods such as voice pattern recognition, signature verification, keystroke pattern recognition, breathing pattern recognition, gait pattern recognition, and even brainwave pattern recognition, although many of these are only in experimental stages. Biometrics is considered to be among the most reliable authentication methods possible.
Defeating “Foolproof” Authentication Mechanisms
In 2000, a French engineer/hacker named Serge Humpich (and known as “the Count of Monte Crypto”) was able to defeat the 640-bit encryption key used by smart cards issued by banks in France, which millions of French consumers used for purchasing items. The equipment he used to break the encryption key cost only $250.
Even supposedly “foolproof” biometric methods aren't foolproof. This is because the biometric data must be analyzed by a software program, and everyone who has worked with computers knows that there is no such thing as a software program that works perfectly. Thus, the vendors of biometric solutions establish fault-tolerance limits that are based on a certain level of false rejection and false acceptance rates (called FRRs and FARs, respectively). False rejection occurs when an authorized user is rejected by the system, and false acceptance occurs when an unauthorized user is “passed” by the software and is allowed access. In fact, fingerprint scanners have been defeated by such simple methods as blowing on the sensor surface to reactivate a fingerprint previously left there or by dusting a latent fingerprint on the sensor with graphite and then applying adhesive film to the surface and pressing on it gently. These techniques are examples of latent image reactivation. In a well-publicized case in May 2002, a cryptographer in Japan was able to create a phony fingerprint using gelatin, which he claimed fooled fingerprint scanners approximately 80 out of 100 times.
Social Engineering and Phishing
Hacking may be done through expert computer skills, programs that acquire information, or an understanding of human behavior. This last method is called social engineering. When social engineering is used, hackers misrepresent themselves or trick a person into revealing information. Using this method, a hacker may ask a user for his or her password, or force the user to reveal other sensitive information.
Hackers using social engineering to acquire information will often misrepresent themselves as authority figures or as someone in a position to help their victim. For example, a hacker may phone a network user and say that there is a problem with the person's account. To remedy the problem, all the caller needs is the person's password. Without this information, the person may experience problems with his or her account, or will be unable to access certain information. Because the person will benefit from revealing the information, the victim often tells the hacker the password. By simply asking, the hacker now has the password and the ability to break through security and access data.
Social engineering often involves subtler methods of acquiring information than simply asking for a password. In many cases, the hacker will get into a conversation with the user and slowly get the person to reveal tidbits of information. For example, the hacker could start a conversation about the Web site, ask what the victim likes about it, and determine what the person can access on the site. The hacker might then initiate a conversation about families and pets, and ask the names of the victim's family members and pets. To follow up, the hacker might ask about the person's hobbies. Because many users make the mistake of using names of loved ones or hobbies as a password, the hacker may now have access. Although the questions seem innocuous, when all of the pieces of information are put together, it can give the hacker a great deal of insight into getting into the system.
In other cases, the hacker may not even need to get into the system, because the victim reveals all the desired information. People enjoy when others take an interest in them, and will often answer questions for this reason or out of politeness. Social engineering is not confined to computer hacking. A person may start a conversation with a high-ranking person in a company and get insider information about the stock market, or manipulate a customer service representative at a video store into revealing credit card numbers. If a person has access to the information the hacker needs, hacking the system is not necessary.
The best way to protect an organization from social engineering is through education. People reveal information to social engineers because they are unaware that they are doing anything wrong. Often, they do not realize they have been victimized, even after the hacker uses the information for illicit purposes. Teaching users how social engineering works, and stressing the importance of keeping information confidential, will make them less likely to fall victim to social engineering.
Phishing
A variation of social engineering is phishing, or phising, in which a hacker uses e-mail to acquire information from the recipient. Because the hacker is fishing for information using the e-mail as bait, and hackers replaced “f” with “ph,” the term phishing was born. A hacker will send e-mail to groups of people, posing as some authoritative source, and request that the recipient provide specific information. This may be a single department, the entire company, or (most often) sent as spam across the Internet. For example, common e-mails on the Internet pose as banks or companies such as eBay, and request that people fill out an HTML form or visit a Web site to confirm their account information. The form asks for personal and credit card information, which can then be used to steal the person's identity. The same technique can be used to pose as network administrators, human resources, or other departments of a company, and request the recipient to confirm information stored in various systems. For example, it could ask them to provide their employment information (for example, name, position, department, Social Security number, and so forth), business information (business accounts, credit card numbers, and so forth), or network information such as usernames and passwords. Although many people are educated in this technique, it succeeds because out of the sheer number of people that are contacted, someone will eventually fall for the trick.
Phishing is particularly effective in business environments, because unlike banks or companies that don't use e-mail to collect information over the Internet, businesses may actually contact departments through internal e-mail to acquire information. For example, finance departments have requested that other departments provide information about their purchase accounts, credit cards, and other information, whereas human resources departments have requested updated information on employees. Because it takes knowledge to read the Multipurpose Internet Mail Extensions (MIME) information and identify whether e-mail was sent internally or externally, a member of a department may be easily duped by phishing. To prevent such problems, it is important to educate users and implement policies to specify how such information is to be collected. This may include stages, such as sending out internal e-mails stating that on a specific date, a request for such information will be sent out. It is equally important that measures be taken to inform users what sort of information is never requested, such as passwords.
Tailgating
Even with the most stringent physical security in place, there are ways of bypassing these methods and gaining access. One of the simplest methods is tailgating, or piggybacking, in which an unauthorized person follows an authorized person into a secure area. Regardless of whether a person has to use a key, PIN, card key, biometrics, or other methods to open a door and enter, all a second person needs to do is follow him or her through the door. Even if the first person notices the security breach, he or she may feel uncomfortable challenging the person who is tailgating, and not bother asking the person to provide identification, get out, or go back and use his or her own key or access to enter.
Intruders piggybacking on another person's access can be a real security challenge, because any existing security measures are rendered useless even though they're functioning properly. It is especially common if the authorized person knows the tailgater, such as when management, a coworker, or others who are visually recognized are piggybacking. It's common to see one person using a key card to enter a building and several others following their way in. However, even in these cases, you cannot be 100 percent sure whether one of them has been dismissed from the company, is under a disciplinary action (such as suspension), or is a contractor whose contract has ended. Even if the person legitimately works for the company, allowing him or her to piggyback into a server room could result in equipment being knocked over, sensitive documents (such as administrator passwords) being seen, or other problems.
Human nature can cause significant problems for any security measures you put in place, and there is no easy way to deal with it. Policies can be implemented that prohibit allowing anyone to enter an area unless he or she has used his or her own security access method (key, access card, PIN, and so forth), with procedures on what to do if someone does sneak in behind a person (such as challenging the person to produce ID, notifying security personnel, and so forth). However, most employees are neither trained nor willing to confront or physically remove a person from the premises, so often the policy may be ignored for personal safety reasons or because it is emotionally uncomfortable. After all, no one wants to ask his or her boss to get out of the building or room because the boss snuck in the door.
This makes education one of the best methods of combating the problem. Employees should be educated that tailgating is a security issue; that policies exist that make a person responsible for those permitted access; and that allowing an unauthorized person access could result in disciplinary actions (including termination of employment). Although this won't completely eliminate tailgating, it will limit the number of people who attempt or allow security breaches.
Dumpster Diving
Another threat that can be overlooked in companies is dumpster diving. As with tailgating, it is about as low-tech a method of threatening security as anyone could think of. It literally involves getting into a dumpster and going through the trash, searching through garbage bags, looking in wastebaskets, and rummaging through other places where people may have disposed sensitive information.
This method of breaching security remains popular because it is so effective. In addition to the rotting refuse of people's lunches, one can find discarded printouts of data, papers with usernames and passwords, test printouts that have Internet Protocol (IP) address information, and even old hard drives, CDs, DVDs, and other media containing the information you'd normally have to hack the network to obtain. Even the most innocuous waste may provide a wealth of information. For example, printouts of e-mail will contain a person's name, e-mail address, contact information, and other data that could be used for social engineering purposes (discussed in the next section).
There are many solutions to resolving dumpster diving as a security issue. Dumpsters can be locked with a padlock to limit access, or they can be kept in locked garages or sheds until they're ready for pickup. Companies can also implement a shredding policy so that any sensitive information is shredded and rendered unusable by anyone who finds it. This is especially important if the company has a recycling program, in which paper products are kept separate. If documents aren't shredded, the recycling containers make it even easier to find information, as all of the printouts, memos, and other documentation are isolated in a single container. Because discarded data isn't always in paper form, companies also need to implement a strict hardware and storage media disposal policy so that hard disks are completely wiped and old CDs and DVDs containing information are destroyed. By obliterating the data before the media is disposed, and protecting the waste containers used afterward, dumpster diving becomes difficult or impossible to perform.
Prevention and Response
Because passwords are the first—and in some networks, the only—line of defense in protecting a network from intruders, it is extremely important that steps be taken to ensure the integrity of all users' passwords. The following sections provide some general guidelines on protecting passwords and dealing with so-called social engineers.
General Password Protection Measures
Network administrators and users can take a number of measures to protect passwords, including the following:
▪ Configure settings so that user accounts are disabled or locked out after a reasonable number of incorrect password attempts.
▪ Use the Encrypting File System (EFS) on Windows 200x and XP computers, or BitLocker drive encryption on systems running Windows Vista and Windows Server 2008.
▪ Store critical data on network servers rather than local machines.
▪ Don't rely on the password protection built into most applications.
▪ Enable password shadowing on UNIX/Linux systems.
▪ Ensure that passwords are never sent across the network in plain-text form.
▪ Use antisniffer software and sniffer detection techniques to guard against crackers who try to intercept passwords traveling across the network.
Protecting the Network against Social Engineers
Administrators find it especially challenging to protect against social engineering attacks. Adopting strongly worded policies that prohibit divulging passwords and other network information to anyone over the telephone and educating users about the phenomenon are obvious steps that administrators can take to reduce the likelihood of this type of security breach. Human nature being what it is, however, some users on every network will always be vulnerable to the social engineer's con game. A talented social engineer is masterful at making users doubt their own doubts about his legitimacy.
The “wannabe” intruder could regale the user with woeful stories of the extra cost the company will incur if he or she spends extra time verifying his identity. The intruder could pose as a member of the company's top management and take a stern approach, threatening the employee with disciplinary action or even termination if he doesn't get the user's cooperation. Or the social engineer could try to make the employee feel guilty by pretending to be a low-level employee who is just trying to do his job and who will be fired if he doesn't get access to the network and take care of the problem right away. A really good social engineer is patient and thorough. He will do his homework and will know enough about the company he targets or the organization he claims to represent to be convincing.
Because social engineering is a human problem, not a technical problem, prevention must come primarily through education rather than technological solutions.
Vulnerabilities and Exploits
There is an expression among programmers: “If at first you don't succeed, call if version 1.” The reason for this expression is because programs often have flaws or issues (called bugs) that may not be apparent until after they're used by others. When a program is written, it is hopefully tested before being released for others to use. We say hopefully because even though testing is a common procedure, many times in-house programs are written and released before proper testing is done (primarily due to pressure by management). Even when software is tested, some things can be missed. A program may appear to function properly, even though it has programming that is weak and can be exploited by hackers and malicious programs that can crash the software or access its data.
Known vulnerabilities are another issue that often arises when new systems are released on the market. New versions of operating systems and applications are often released with known vulnerabilities. For example, when Windows Vista was released, word quickly spread that it had literally thousands of known vulnerabilities. Despite such knowledge, Microsoft released the software with the thought that a service pack, patches, and other updates would be released afterward to fix these issues. Unfortunately, if the end-user doesn't visit the vendor's Web site to download and apply these patches, the vulnerabilities will continue to exist until he or she upgrades the software to the next version. As we'll discuss in the sections that follow, many kinds of vulnerabilities may be present in operating systems and applications.
Application Exploits
Application software exploits are those that take advantage of weaknesses of particular application programs; these weaknesses are often called bugs. Like protocol exploits, intruders use application exploits to gain unauthorized access to computers or networks or to crash or clog up the systems to deny service to others.
Bug Exploits
Common “bugs” can be categorized as follows:
▪ Buffer overflows Many common security holes are based on buffer overflow problems. Buffer overflows occur when the number of bytes or characters input exceeds the maximum number the program allows.
▪ Unexpected input Programmers might not take steps to define what happens if invalid input (input that doesn't match program specifications) is entered. This could cause the program to crash or open a way into the system.
▪ Configuration bugs These are not really “bugs,” per se; rather, they are ways of configuring the software that leaves it vulnerable to penetration.
Popular software such as Microsoft Internet Information Server (IIS), Internet Explorer, and Outlook Express (MSOE) are the favorite targets of hackers looking for software security holes to exploit. ActiveX controls, JavaScript, and VBScript can be used to add animations or applets to Web sites or e-mail messages, but hackers can exploit these features to write controls or scripts that allow them to remotely plant viruses, access data, or change or delete files on the hard disks of unaware users who visit the page or open the mail and run the script.
Major software vendors regularly release security patches to fix exploitable bugs. It is very important for network administrators to stay up-to-date in applying these fixes to ensure that their systems are as secure as possible. The following sections take a closer look at some popular attacks that exploit application software.
Mail Bombs
A mail bomb is a means of overwhelming a mail server, causing it to stop functioning and thus denying service to users. A mail bomb is a relatively simple form of attack, accomplished by sending a massive quantity of e-mail to a specific user or system. Programs available on hacking sites on the Internet allow a user to easily launch a mail bomb attack, automatically sending floods of e-mail to a specified address while protecting the attacker's identity. A number of types of mail-bombing techniques can be used against the popular Sendmail program, including:
▪ Chain bombs, in which massive numbers of e-mails are sent to an e-mail server on a script. When this e-mail server is overwhelmed, the remaining e-mails are then sent to the next server in the chain. This continues until all of the mail servers listed in the script are brought down.
▪ Error message bombs, in which massive amounts of undeliverable e-mail are sent to a mail server. Because the e-mail messages are sent to an undeliverable address, the mail server returns an error message. However, in sending the e-mail, the bomber uses the e-mail address of an intended victim. Massive amounts of error messages flood the victim's e-mail account, and may also overwhelm the mail server used by the victim.
▪ Covert distribution channels, in which e-mail and files are sent using an intermediate mail server. The e-mail may consist of hate propaganda, pornography, or other illicit files and messages. The victim is fooled into believing that the e-mail actually originated from the intermediate server.
▪ Abuse-of-mail exploders, in which the bomber sends massive amounts of e-mail using automated mailing lists. These lists distribute the e-mail to everyone on the list.
One variation on the mail bomb automatically subscribes a targeted user to hundreds or thousands of high-volume Internet mailing lists, which fill the user's mailbox and/or mail server. Bombers call this attack list linking. Examples of these mail bomb programs include Unabomber, Extreme Mail, Avalanche, Voodoo, and Kaboom.
The solution to repeated mail bomb attacks is to block traffic from the originating network using packet filters. Unfortunately, this solution does not work with list linking because the originator's address is obscured; the deluge of traffic comes from the mailing lists to which the victim has unknowingly been subscribed.
Browser Exploits
Web browsers are client software programs such as Internet Explorer, Netscape, and Opera that connect to servers running Web server software such as IIS or Apache and request Web pages via a Uniform Resource Locator (URL), which is a “friendly” address that represents an IP address and particular files on the server at that address. The browser receives files that are encoded (usually in HTML) and must interpret the code or “markup” that determines how the page will be displayed on the user's monitor. Browsers are open to a number of types of attack.
Exploitable Browser Characteristics
Early browser programs were fairly simple, but today's browsers are complex; they are capable of not only displaying text and graphics, but also playing sound files and movies and running executable code. The browser software also usually stores information about the computer on which it is installed and even about the user (data stored as cookies on the local hard disk), which can be uploaded to Web servers—either deliberately by the user or in response to code on a Web site.
All of these characteristics serve useful purposes. Support for running code (as “active content” such as Java, JavaScript, and ActiveX) allows Web designers to create pages that interact with users in sophisticated ways. Cookies allow users to set preferences on sites that will be retained the next time they visit the site. However, hackers can exploit these characteristics in many ways. For example, a hacker can program a Web site to run code that transfers a virus to the client computer through the browser, erases key system files, or plants a “back door” program that then allows the hacker to take control of the user's system.
Web Spoofing
Web spoofing is a means by which an attacker is able to see and even make changes to Web pages that are transmitted to or from another computer (the target machine). These pages include confidential information such as credit card numbers entered into online commerce forms and passwords that are used to access restricted Web sites. JavaScript can be used to route Web pages and information through the attacker's computer, which impersonates the destination Web server. The attacker can send e-mail to the victim that contains a link to the forged page or put a link into a popular search engine. Secure Sockets Layer (SSL) doesn't necessarily prevent this sort of “man in the middle” attack; the connection appears to the victim user to be secure because it is secure. The problem is that the secure connection is to a different site than the one the victim thinks he or she is connecting to. Hyperlink spoofing exploits the fact that SSL doesn't verify hyperlinks that the user follows, so if a user gets to a site by following a link, the user can be sent to a spoofed site that appears to be a legitimate site.
Web spoofing is a high-tech form of con artistry. The point of the scam is to fool the user into giving confidential information such as credit card numbers, bank account numbers, or Social Security numbers to an entity that the user thinks is legitimate and then using that information for criminal purposes such as identity theft or credit card fraud. The only difference between this and the “real-world” con artist who knocks on a victim's door and pretends to be from the bank, requiring account information, is in the technology used to pull it off.
There could be clues that will tip off an observant victim that a Web site is not what it appears to be, such as the URL or status line of the browser. However, the attacker can use JavaScript to cover his or her tracks by modifying these elements. An attacker can even go so far as to use JavaScript to replace the browser's menu bar with one that looks the same but replaces functions that provide clues to the invalidity of the page, such as the display of the page's source code.
Web spoofing was a particular problem in older versions of browser software, but features in today's browsers make Web spoofing more difficult.
Web Server Exploits
Web servers host Web pages that are made available to others across the Internet or an intranet. Public Web servers (those accessible from the Internet) always pose an inherent security risk because they must be available to the Internet to do what they're supposed to do. Clients (Web browser software) must be able to send transmissions to the Web server for the purpose of requesting Web pages. However, allowing transmissions to come into the network to the Web server makes the system—and the entire network, unless measures are undertaken to isolate the Web server from the rest of the internal network—vulnerable to attackers.
Web server applications, like other software, can contain bugs that can be exploited. For example, in 2001 a flaw was discovered in Microsoft's IIS software that exploited the code used for the indexing feature. The component was installed by default. When it was running, hackers could create buffer overflows to take control of the Web server and change Web pages or attack the system to bring it down. Microsoft quickly released security patches to address the problem, but many companies don't upgrade their software or don't update it with available fixes, and new, different security holes are being found all the time in all major Web server programs.
Buffer Overflows
A buffer is a sort of holding area for data. To speed processing, many software programs use a memory buffer to store changes to data, and then the information in the buffer is copied to the disk. When more information is put into the buffer than it is able to handle, a buffer overflow occurs. Overflows can be caused deliberately by hackers and then exploited to run malicious code.
There are two types of overflows: stack overflows and heap overflows. The stack and the heap are two areas of the memory structure that are allocated when a program is run. Function calls are stored in the stack, and dynamically allocated variables are stored in the heap. A particular amount of memory is allocated to the buffer. Attackers can use buffer overflows in the heap to overwrite a password, a filename, or other data. If the filename is overwritten, a different file will be opened. If this is an executable file, code will be run that was not intended to be run. On UNIX systems, the substituted program code is usually the command interpreter, which allows the attacker to execute commands with Superuser privileges. On Windows systems, the overflow code can be used to send a Hypertext Transfer Protocol (HTTP) request to download malicious code of the attacker's choice.
Buffer overflows are based on the way the C programming language works. Many function calls don't check to ensure that the buffer will be big enough to hold the data copied to it. Programmers can use calls that do this check to prevent overflows, but many do not.
Creating a buffer overflow attack requires that the hacker understand assembly language as well as technical details about the operating system to be able to write the replacement code to the stack. However, the code for these attacks is often published so that others, who have less technical knowledge, can use it. Some types of firewalls, called stateful inspection firewalls, allow buffer overflow attacks through, whereas application gateways (if properly configured) can filter out most overflow attacks. We discuss firewalls in detail in Chapter 12.
Operating System Exploits
Some exploits are unique to a particular operating system or family of operating systems. These hacks exploit specific characteristics of the operating system code to carry out the attack. All operating systems have their own vulnerabilities.
A number of different sources can exploit these vulnerabilities. In addition to hackers using their own expertise to hack systems, prewritten scripts and tools are available on the Internet that novices (script kiddies) can use to hack systems. Tools such as Metasploit can be used to analyze systems for vulnerabilities, and then run previously developed exploits for penetration testing on your own systems or to hack those belonging to other people. Version 2 of this tool comes with more than 100 exploits that can be used. In addition to this, Trojan horses and other malicious programs take advantage of the vulnerabilities to access data or damage systems.
Most exploits are written to take advantage of vulnerabilities in the most popular operating systems, which as you would expect are versions of Windows. According to the Market Share Web site (http://marketshare.hitslink.com/report.aspx?qprid=8), the market share of different operating systems was as follows:
▪ Windows, 91.57 percent
▪ Mac, 7.48 percent
▪ Linux, 0.61 percent
Although these are rough statistics, they do show that Microsoft dominates the market, which is why most of the tools and scripts available are designed to exploit the weaknesses of various versions.
Windows Registry Attacks
The Registry is a database in which critical system and application configuration and initialization information is stored, and it is used in all Windows operating systems after Windows 3.x. Having this information in one centralized location instead of scattered in multiple initialization and configuration files offers many benefits, but it also makes the Registry vulnerable to hackers and attackers.
The Regedit tool in Windows allows the user to connect to the Registry on a remote system across the network and make changes to Registry settings. As shown in Figure 11.6, you can connect to another computer's Registry by selecting the Connect Network Registry menu item on the File menu, and then specifying the computer to which you want to connect. A hacker can exploit this ability and alter important information that could bring down the system. Administrative privileges are needed to edit remote registries.
 |
| Figure 11.6 The Regedit Utility, Which You Can Use to Connect to and Edit a Remote System's Registry |
Other Windows Exploits
Many vulnerabilities have been discovered in the Windows operating systems. Microsoft is generally quick to patch these vulnerabilities once they become known, but as we mentioned, this doesn't help if these patches aren't applied to the computer after the operating system is initially installed. Some of the vulnerabilities that have appeared in various versions of Windows include:
▪ The Messenger service in Windows XP being vulnerable to a buffer overrun that allows a hacker to execute code with local system privileges.
▪ The Task Scheduler in Windows XP allowing arbitrary code to be executed remotely.
▪ A heap overflow problem in Windows Server 2003 that allowed arbitrary code to be executed, and also provided hackers with the ability to capture segments of the host memory space.
▪ The domain name system (DNS) server in Windows Server 2003 being vulnerable to Cache Snooping attacks, in which a hacker can see which hosts have been recently resolved.
▪ An issue where Windows Vista failed to properly disable AutoRun and AutoPlay features, because of a problem handling the NoDriveTypeAutoRun value in the Registry. This allowed AutoPlay to be enabled, even if Group Policy and Registry values had been set to disable it. As such, a hacker could get a user to inadvertently execute code on removable devices, such as USB flash drives.
Keeping Up with Vulnerabilities
Windows users, administrators, and law enforcement officers can keep up with the latest Windows vulnerabilities by reviewing the Security Bulletins and Advisories section on the Microsoft TechNet Web site at www.microsoft.com/technet/security/bulletinsandadvisories/default.mspx These bulletins are released on a monthly basis, provide information on vulnerabilities that have been discovered in Microsoft products, and advise on how to secure systems against them.
UNIX/Linux Exploits
Many UNIX/Linux exploits aim at gaining root access. In UNIX, the root account is the equivalent of the Administrator account on a Windows system. A user logged on with the root account has full control of the system and is able to clear the logs to cover his or her tracks. “Getting root” often involves finding a file that has Superuser ID (SUID) permissions and running a script (downloadable from hacker sites on the Web) or exploiting bugs in Sendmail or some other service.
Rootkit Attacks
Despite its name, a rootkit attack is not a method of obtaining root account privileges—at least, not directly. It is a group of programs which install a Trojan logon replacement with a back door, along with a packet sniffer, on UNIX boxes. The sniffer can then be used to capture network traffic, including user credentials, thus giving the user access to the root account by logging on with legitimate credentials. Software such as Rkdet is available to detect rootkit installation or packet sniffers running on a UNIX system.
Other UNIX Exploits
As with other operating systems, a number of different vulnerabilities can appear in different distros of Linux and systems running UNIX. Like their Windows cousins, vulnerabilities have appeared over the years inclusive to a variety of buffer overflow exploits, insecure default configurations, and programming flaws that hackers can use to compromise systems and networks. Some of the vulnerabilities with different distros have included the following:
▪ The DNS server in Slackware Linux 11.0, SUSE Enterprise 10, and Ubuntu 6.10 was vulnerable to Cache Snooping attacks, which allow hackers to view what hosts have recently been resolved.
▪ The Very Secure FTP server in Slackware Linux 11.0 permitted anonymous connections by default.
▪ The Web server in SUSE Enterprise 10 and Ubuntu 6.10 had a default configuration with TRACK method support, which allowed a cross-site scripting attack.
Mac OS Exploits
Some Apple commercials have promoted Mac computers as being more secure and less vulnerable than other operating systems (notably Windows). Although fewer viruses and malicious software are written to attack Macs (primarily due to their having a lower market share), they are not without vulnerabilities. This isn't to say that Macs aren't an exceptional system. They have a significant number of security features, and they are configured with security in mind (such as not having built-in servers enabled, which prevents them from exploited). However, some security features are not enabled when the system is installed. For example, Mac OS X includes a firewall called Internet Protocol FireWall (IPFW), but it isn't initially enabled. In addition to this, a number of vulnerabilities have appeared over the years:
▪ A vulnerability on the Mac OS X 10.4 server allowed Directory Services to be remotely shut down by making excessive connections to the server.
▪ The DNS Server in Mac OS X 10.4 server was found to be vulnerable to Cache Snoop attacks.
▪ Mac OS X was found to have a vulnerability that allowed malicious Web sites to compromise the system. The help URI handler allowed arbitrary local scripts to be executed using help:runscript. Script files and other arbitrary files could also be run by placing them in a known location, and then run on the computer using the disk URI handler.
Keeping Up with Vulnerabilities
Apple provides a great deal of information regarding security features in its products, security guides, and updates to fix security issues. To ensure that your Mac is up-to-date with the latest patches, you should visit Apple's product security page at www.apple.com/support/security/
Prevention and Response
Administrators can take a number of steps to help prevent exploits, including the following:
▪ Ensure that all systems have the latest security patches. This assurance protects against many denial-of-service (DoS) attacks, which rely on operating system or protocol “bugs.”
▪ Disabling Java, JavaScript, ActiveX, and other active content in the Web browser thwarts many common browser exploits. We discussed browser security in greater detail in Chapter 9.
▪ Use application gateway firewalls to protect against buffer overflow attacks.
▪ Keep up-to-date by reviewing security bulletins regarding vulnerabilities that have been found in different systems. A good site to visit for this is the United States Computer Emergency Readiness Team (US-CERT) technical alerts site at www.us-cert.gov/cas/techalerts/
Summary
Passwords, pass phrases, and PINs are common methods of authenticating a user to confirm his or her identity, before the user is given access to systems. A secure client operating system such as Windows XP or Windows Vista requires an interactive logon with a valid account name and password to access the operating system. These systems allow users to “lock” the workstation when they are going to be away from it, so someone else can't just step up and start using the computer. Other systems, such as Web servers, applications, and other software, also use passwords to control access to systems.
To enhance security, passwords can be used with other authentication factors. Even if a password was compromised, authentication devices such as smart card readers, fingerprint scanners, retinal and iris scanners, and voice analysis devices will prevent unauthorized access. These require the user to prove his or her identity in other ways, such as through possession of a card or through characteristics and features unique to that person.
Even in the most secure settings, weak links in a chain will exist. This can be the people who work there, and are vulnerable to social engineering techniques, or vulnerabilities in the software that's used and can be exploited by hackers and malicious programs. Despite these common weak points, there are ways to strengthen security. People can be educated in what to do, and what not to do (such as revealing passwords to others). The other good news is that you can take many steps to prevent technical exploits on your systems. In fact, applying all the current patches, fixes, service packs, and other upgrades and running good antivirus (AV) software with updated virus file definitions will go a long way toward keeping intruders out and attackers at bay. The bad news is that administrators must be constantly vigilant to guard against new threats that appear on a daily basis.
Frequently Asked Questions
A When someone can guess or acquires a password, it's analogous to him or her having the keys to your house. He or she can get in, and can have the same access that you have. By using strong a password and taking steps to protect it and change it regularly, it is less likely that someone will be able to crack your password and use it to access sensitive information.
Q Someone is taking over my job temporarily. Can't I just given him my password, so he can do my job properly?
A No. Although this is a common problem in organizations, when someone uses your password, he or she appears in network logs as though he or she were you. This means that if this person committed a violation of policy or a crime using your account, it would appear as though you did it. The best way to deal with such situations is to notify a network administrator, so he or she can set up a new account with the same level of access.
Q What passwords are most easily cracked?
A Easy-to-guess passwords are the easiest to crack. Even without the benefit of password recovery tools, a person will be able to type in words that relate to you. Anyone who knows you or has access to information about you would be able to guess the name of a significant other, child's name, pet's name, birth date, favorite sports team, or other facts about you that you probably used for a password.
Q Exactly how does social engineering work? Why would anyone reveal his or her password to a stranger? Does this really happen?
A Yes, it really happens—and more often than you might think. Skilled social engineers are good con artists; they are masters at making other people trust them. In large companies, employees often aren't personally familiar with all the other employees, so it's relatively easy for the social engineer to come strolling in or even call on the phone and persuade a user that he or she is a member of the information technology (IT) department and needs the user's password. The social engineer might have a convincing story, saying, for instance, that a hacker has gotten into the system and discovered all the password files, and now the IT department needs to know everyone's old password so that they can reset them and issue new ones to protect against the hacker. Like all con artists, the social engineer usually plays on common human emotions. For example, the engineer will play up the danger that the hacker can access and destroy all of the user's data if the “IT worker” doesn't get the password immediately and make the change. In other cases, the engineer might exploit other emotions, such as people's natural desire to help, claiming that the “IT worker” will get in trouble with the “big boss,” maybe even get fired, if he or she is unable to get the password information that is needed. Social engineers are not above appealing to the user's ego or pretending sexual/romantic interest in the user to get the password, either. Although some might not categorize it as social engineering, another technique involves simply spying on the user to obtain the password (“shoulder surfing” or looking over the user's shoulder as he or she types the password) or going through the user's papers to find a written record of the password. Infamous hacker Kevin Mitnik is quoted as saying, “You can have the best technology, firewalls, intrusion detection systems, [and] biometric devices. All it takes is a call to an unsuspecting employee, and that's all she wrote, baby. They got everything.” Visit http://searchsecurity.techtarget.com/originalContent/0,289142,sid14_gci771517,00.html for more on this topic.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
