Chapter 10. Understanding Network Intrusions and Attacks
Topics we'll investigate in this chapter:
▪ Recognizing Preintrusion/Attack Activities
▪ Understanding Technical Exploits
▪ Attacking with Trojans, Viruses, and Worms
▪ Hacking for Nontechies
▪ Understanding Wireless Attacks
Summary
Frequently Asked Questions
Introduction
As we've discussed in earlier chapters, there are many different types of cybercrime, committed by all kinds of cybercriminals—some of whom have very little technical knowledge or skill. However, thanks to the news media and a few popular movies, most people associate the term cybercrime with a particular type of offense: hacking into a system or network from outside an organization. Included in this narrow definition are malicious attacks designed to crash computers and congest networks, even when no actual “illegal entry” takes place. In either case, the criminal is presumed to have a high level of knowledge about computers and networking.
Unlike the cyberscam artist who needs to know only enough about computers to send mass e-mailings, or the child pornographer whose technical know-how is limited to uploading and downloading files, the network intruder or attacker has traditionally been able to boast of a certain amount of skill. It takes knowledge (and sometimes talent) to circumvent security measures and slip through the holes programmers leave in applications and operating systems to gain access to someone else's servers. It takes a thorough understanding of how network protocols work to exploit their characteristics and bring down systems or entire networks. Or at least, it once did.
Dedicated hackers spend hundreds or even thousands of hours perfecting intrusion techniques and attacks. Today, however, many hackers who break into or bring down networks aren't really hackers at all—at least, not in the original sense of the word (which referred to computer “whiz kids” whose mastery of the technology was the key to their ability to penetrate and crack systems). This is because the “real” hackers have generously made available the fruits of their knowledge and labor in the form of scripts and executable programs that do all the work. The “script kiddies” who use them might be scorned as hacker “wannabes” by those with technical knowledge, but hacking tools still continue to proliferate, shared freely through “warez” newsgroups and Web sites, making intrusions and attacks easy. Beyond this, many of the same tools used by information technology (IT) professionals to test security and identify issues can also be used to hack the network. No longer does a would-be intruder or attack have to bother to learn the technical aspects of Windows vulnerabilities or Transmission Control Protocol/Internet Protocol (TCP/IP) security flaws. Now anyone, with no training at all, can “worm” his way into the network of a competing business or launch a massive denial-of-service (DoS) attack against a company whose politics he doesn't like.
It is important for cybercrime investigators who build cases charging unauthorized access or breach of network integrity to understand the basics of how intrusion techniques and system attacks work, even though intruders and attackers need not necessarily understand the technicalities of what they're doing. After all, the investigator could be required to testify in court about an important issue that must be established in every criminal case: whether probable cause existed to make the arrest. It could be difficult to convince a jury that you had enough evidence to believe the accused committed a crime if you're unable to explain exactly what the crime is and exactly how it was committed.
In this chapter, we provide overviews of the technical aspects of various types of intrusions and attacks. We start with a discussion of an intruder's preparatory activities that might precede an attack:
▪ Scanning for open ports on the targeted network
▪ Disguising the attacker's Internet Protocol (IP) address and other identifying information
▪ Placing software constructs or hardware devices (such as Trojan programs or keystroke monitors) to gather preliminary data that will help the attacker carry out the attack
Whereas in Chapter 11 we look at how intruders crack passwords and software exploits to gain access to systems and networks, in this chapter we'll discuss the many types of technical exploits that hackers use to access or attack networked computers. We also address the “script kiddie” and “click kiddie” phenomenon and show you how people with almost no technical expertise can use readily available tools to jumpstart their hacking careers. Finally, we discuss wireless networks, and some of the differences that make them prone to attacks.
Note
Some of the attacks and exploits discussed in this chapter might be considered by some to be “obsolete.” However, this is true only if we assume that all systems are running the latest versions of software and that all security patches have been applied. Unfortunately, this is not the case; in a world where a substantial number of business and government computers still run older versions of Windows, it would be naïve to assume that the vulnerabilities of older operating systems and applications are no longer relevant.
Understanding Network Intrusions and Attacks
Network intrusions and attacks come in many forms and from all directions. Although external threats (usually from across the Internet) get the most attention, attacks and intrusions can—and often do—come from employees, contractors, and others on-site or within a local network. Remember that just because someone is authorized to access a network doesn't mean that he or she has authorization to access all its resources.
We can no longer assume that attackers are particularly knowledgeable about computers. At one time, an attacker had to have a minimal level of skill to launch an attack, but today readily available tools completely automate the attack process. An attack really can come from just about anyone who has the motivation and the mindset to launch it.
Some intrusions and “attacks” can even be unintentional. Users with just enough technical knowledge to be dangerous could experiment with changing settings and crash the system or network; curious people could stumble on unsecured resources to which they shouldn't have access; and employees attempting to make things more convenient for themselves (for example, by installing wireless access points so that they'll have network connectivity when they take their laptops to the conference room for meetings) can unknowingly open up security holes.
In the following sections, we examine the difference between an intrusion and an attack; discuss various types of attacks, including accidental ones; and provide some guidelines for preventing intentional internal security breaches.
Considering Internal Threats
All cybercrime by its very definition involves using a network to access systems. However, when investigators are confronted with theft or destruction of data or attacks that crash servers, the possibility of an “inside job” shouldn't be discounted. Not all attacks or unauthorized entries into systems come from the Internet; they can also come from somewhere on the local area network (LAN) or via physical access to the affected machines.
Intrusions versus Attacks
It is important for investigators to understand the difference between an intrusion and an attack because whether there was an actual unauthorized entry to the network or system can be an important factor in proving the elements of a criminal offense. Attacks can be committed without gaining entry to the network or system, as in the case of DoS attacks. These attacks overload network resources to make the network unavailable to legitimate users, but the attacker never gains access to any computer on the network.
If investigators and prosecutors don't understand this difference (which they can do only by understanding the technical aspects of how the attack works), they could file charges that won't stand up in court or bring the wrong charges against a cybercriminal. This would be similar to a situation in which no one on the law enforcement team understood the difference between the offenses of robbery and burglary. Robbery requires that a physical assault or threat of serious bodily injury takes place during the commission or attempted commission of a theft. Burglary requires that the offender unlawfully enters the premises of another person to commit a theft. If law enforcement officers arrest a suspect for breaking into a home and stealing a television set while the residents are gone, and they charge the suspect with robbery (and if the prosecutor brings such a case to trial), the suspect will almost certainly be found not guilty, because the state doesn't have proof of the elements of the offense of robbery. This situation would never happen, because law enforcement officers are drilled in the technical differences between robbery and burglary from the time they attend the police academy, and all prosecuting attorneys are well versed in these differences. However, it's entirely plausible to imagine the wrong charges being filed in a computer crime case simply because no one involved understands the technical aspects of these types of crimes.
It's important, then, to be precise when we refer to specific computer crimes. DoS attackers should not be referred to as intruders when no intrusion occurs. Likewise, not all intruders can accurately be classified as attackers—although those who gain access and then destroy data or plant viruses are properly called by both names.
Analyzing the Law
As an example of how important it is to understand the elements of the offense, which vary from statute to statute and jurisdiction to jurisdiction, Texas Penal Code section 33.02 defines “Breach of Computer Security” as follows:
“A person commits an offense if the person knowingly accesses a computer, computer network, or computer system without the effective consent of the owner.”
At first glance, it would appear that this offense would not apply to attacks in which there is no entry to the network. The statute requires “access” as an element of the offense, and a standard dictionary definition of that word is “a means of entry.” However, to understand what the legislature intended when this statute was passed, we have to look back to the legal definitions that apply to this particular chapter of the Penal Code, which are contained in section 33.01. There, the term access is defined as follows:
“To approach, instruct, communicate with, store data in, retrieve or intercept data from, alter data or computer software in, or otherwise make use of any resource of a computer, computer network, computer program, or computer system.”
As you can see, this definition is broader. The key to bringing this charge against a DoS attacker is the phrase in italics. Because network bandwidth is a resource of a computer network, and because the attacker does indeed make use of that resource, the attacker could be charged under section 33.02.
It is very important for law enforcement officers to carefully analyze the statutes under which they intend to file charges and, if in doubt, to consult the district attorney or state attorney general for clarification of the language in the statute.
Recognizing Direct versus Distributed Attacks
Attackers can launch their attacks against a system or network in two different ways. A direct attack is launched from a computer used by the attacker (often after preintrusion/attack tools, such as port scanners, are used to find potential victims).
A distributed attack is more complex. Distributed attacks use someone else's system(s), rather than the attacker's, to perform the tasks that directly launch the attack. In this type of attack, there are multiple victims, which include not only the target of the attack but also intermediary remote systems from which the attack is launched that are controlled by the attacker. The intermediaries are referred to as agents or zombies. Software robots called botnets or bots are installed on the zombie computers, and can run autonomously and automatically. The bots can be configured to attack at a specific time, or take commands from the attacker on a remote computer. This type of attack, of course, makes it more difficult to track down the perpetrator, because the attack packets that reach the victim have multiple source addresses, and none of these is the address of the attack's originator. Commands from attacker to intermediary are often encrypted to further thwart tracing. Encrypted transmissions can't be read by a packet sniffer (a protocol analyzer).
A distributed attack works a little like the practical joke in which the jokester calls numerous pizza parlors, pretending to be a customer, and requests that pizzas be delivered to someone else's address. The primary victim is the resident at the target address who ends up with a flood of unwanted pizzas, but the pizza vendors are victims as well because their resources are used, without their prior knowledge or consent, to carry out the attack.
Note
To better understand the concept of DoS, the technicalities of which we discuss later in this chapter, let's take the pizza prank scenario described in this section a step further. If our attacker is really determined, he might call not only pizza parlors, but also all the Chinese restaurants, florists, and other “we deliver” businesses in the area, coordinating the requests so that all the delivery persons converge on the victim at the same time. If there are so many delivery vans parked on the street that the victim's family members are unable to get to their own driveway, this results in a denial of service to legitimate users of the driveway.
Attackers using the distributed method can launch their attacks simultaneously from dozens, hundreds, or even thousands of Internet hosts all over the world. This means that far more traffic can be generated than is possible with standard one-source attacks. A typical distributed attack model using UNIX-based computers, according to the CERT Distributed Systems Intruder Tools Workshop, has the attacker controlling several systems called masters. Each master controls a larger number of agents running daemons—the software that is used to launch the attack. The daemons are installed on the agent machines by exploiting operating system or protocol vulnerabilities. This entire process can be automated so that potential agents are discovered and penetrated and the daemon is installed on all of them, then steps are taken to hide the fact that an intrusion occurred, using batch scripts. (We discuss attack automation in more detail in the next section.) Table 10.1 outlines the distributed attack process (after installation of the daemons).
Because this model's components are arranged in a pyramid form, with one attacker controlling several masters, which in turn control numerous agents/daemons, it is easier to disable the attack system closer to the top, where there are fewer systems to deal with. If the masters are disabled, the agents and their daemon software will not be able to function. Of course, the most efficient disabling technique is to find the attacker, thus disabling the entire attack sequence.
Automated Attacks
An automated attack is one that's performed by a computer program rather than the attacker manually performing the steps in the attack sequence. For quite some time, hackers have distributed attack tools that make it easier to launch network attacks. However, prior to 2000, most of these tools would initiate only one attack sequence; launching additional attack sequences required the intervention of the human attacker. However, newer tools are able to continually initiate new attack cycles on their own. This was the case with worms such as Nimda and Code Red, which we'll discuss later in this chapter. This increasing level of automation makes these attacks more dangerous and more widespread. According to CERT, the increasing automation and sophistication of attack tools is one of the most significant trends in the “Black Hat” hacking community.
Today's attack tools can perform the entire attack process. Instead of a hacker being required to perform a port scan with one tool to identify vulnerable systems, then using a different tool to penetrate the victim network and yet another tool to propagate the attack, now one tool can do it all. This speeds up the process as well as makes it easier for hackers who lack technical skills to mount a successful attack. Some attack tools are executed at the command line, but many of them have user-friendly graphical interfaces as well as detailed help files to instruct attackers in their use. Configuration files might also allow users to customize the attack.
To avoid detection by intrusion detection system (IDS) software that relies on pattern recognition, modern tools can employ different techniques—such as random selection—to interrupt patterns that would trigger detection by the IDS. In addition, many of the tools use common protocols such as Hypertext Transfer Protocol (HTTP) and Internet Relay Chat (IRC), which disguise their packets by making them look like normal Internet traffic. These tools are widely available through anonymous File Transfer Protocol (FTP) sites and hacker newsgroups on the Internet. Hackers can also modify legitimate network analysis tools if they have the source code, turning them into attack tools by adding code to exploit the vulnerabilities that they find.
Note
It is ironic that hackers make their attack tools available on anonymous FTP sites, because anonymous FTP and Trivial File Transfer Protocol (TFTP) are themselves often exploited by attackers. Knowledgeable hackers can easily create tools and scripts that attempt an anonymous logon; try various commands such as pwd, mkdir, and rmdir (to print the working directory, make a directory, and remove a directory on UNIX/Linux systems, respectively); and plant a Trojan in the FTP site that then enables the hacker to access the system remotely, without a password.
Botnets
Botnets are one of the biggest and best hidden threats on the Internet. Often, a botnet will be installed on a machine as a worm or Trojan horse, and will run silently on a person's machine. The person who controls the botnets is referred to as the bot herder, and he or she can send commands to the bots and receive data (such as passwords or access to other resources) from them. The reason the bot herder does this can vary, ranging from using the bots to store files on other people's machines, to instruct them to send simultaneous requests to a single site in a DoS attack, or to send out spam mail.
To illustrate how a bot may be used, consider a bot herder who wishes to send spam to large numbers of users. These e-mail messages may claim they are from eBay or another popular site, and may ask the person to update his or her personal and credit card information. The bot herder sends out a Trojan horse that infects computers with the botnet. These infected computers are now referred to as agents or zombies, and will automatically log on to a Web server or IRC server, which is referred to as the Command and Control (C&C) server. The bot herder can now send messages to the botnets through the C&C server, instructing each zombie machine to send out the spam.
This creates a new problem for investigators. Although in the previous chapter we discussed how to trace an IP address back to its source, such an e-mail would lead back to the zombie computer, and not the actual bot herder. In other words, if a bot on your computer had sent out the e-mail, it would appear that it came from you. Investigators need to keep this in mind when tracing the source of a cybercrime as such e-mails may not appear in the Sent Items of the e-mail program on the zombie computer. Scanning for Trojans on the machine may identify the existence of known bots that have infected the machine.
Botnets
In 2005, Dutch police arrested three suspects (ages 19, 22, and 27) who had threatened a U.S. company with a DoS attack. The three had used the Toxbot Trojan to infect computers in preparation of the attack. However, when the Netherlands Computer Emergency Response Team and several Internet service providers (ISPs) began to dismantle the C&C and investigate the technical aspects of the botnet, they found that 1.5 million computers had been made into zombies.
Accidental “Attacks”
Some intrusions and “attacks” might actually be unintentional. Server or network crashes can be caused by users experimenting, visiting Web sites that run malicious code, or unknowingly downloading and introducing a virus into the system. In fact, a large number of virus attacks are initiated accidentally or unknowingly. The user who appears to have sent the virus via e-mail is often a victim of the attack him- or herself, because many viruses and worms are written to spread themselves by accessing the victim's address book and sending infected mail to all the addresses found there.
Accidental attacks can be just as destructive as deliberate ones, and network security personnel must be just as vigilant in protecting against them. However, from the law enforcement perspective, the perpetrator's intent matters very much. Most criminal offenses require that an act be committed intentionally or at least knowingly, so the elements of the offense might not be present if an employee causes an intrusion or attack without intending to—even if his or her actions were careless. On the other hand, some acts are still considered criminal when a lower state of culpability (recklessness or negligence) is present. It is very important for investigators to be aware of the culpable mental state that is specified as an element of each offense to be charged. If no level of culpability is specified, the criminal code usually defines a “default” level of culpability that applies.
Preventing Intentional Internal Security Breaches
Users inside the network are in the best position to gain access to information or sabotage the network's integrity. According to most computer security studies, as documented in Request for Comments (RFC) 2196, actual loss (in terms of money, productivity, computer reputation, and other tangible and intangible harm) is greater for internal security breaches than for those from the outside. Internal attackers are more dangerous for several reasons:
▪ People inside the network generally know more about the company, the network, the layout of the building(s), normal operating procedure, and other information that makes it easier for them to gain access without detection.
▪ Internal hackers know what information is on the network and what actions will cause the most damage.
Preventing such problems begins with the same methods used to prevent unintentional security compromises, but it goes a step further. To a large extent, unintended breaches can be prevented through education. This obviously will not have the same effect on network users who intend to breach security. The best way to prevent such breaches depends, in part, on the motivations of the employee(s) concerned.
Implementing auditing helps detect internal breaches of security by recording specified security events. Administrators are then able to track when objects such as files or folders are accessed, the user account used to access them, when users exercise user rights, and when users log on or off the computer or network. Modern network operating systems include built-in auditing functionality. We discuss methods of auditing security events in Chapter 13. We discuss interpreting and using security audit log files in Chapter 14.
Firewalls are helpful in keeping basically compliant employees from accidentally (or out of ignorance of security considerations) visiting dangerous Web sites or sending specific types of packets outside the local network. However, firewalls are of more limited use in preventing intentional internal security breaches. Simply limiting users’ access to the external network cannot thwart insiders who are determined to destroy, modify, or copy data. Because they have physical access, insiders can copy data to removable media or to a portable computer, or perhaps even print it to paper and remove it from the premises. They can change the format of the data to disguise it, or they can even employ steganography to hide it inside seemingly innocent files and then upload the files to Web-based data storage services.
In a high-security environment, measures should be taken to prevent this sort of theft. For example:
▪ Install computers without diskette drives and CD/DVD writers, and disable Universal Serial Bus (USB) ports so that external hard disks or flash drives can't be used. In situations where high security is necessary, it may even be prudent to use diskless workstations.
▪ Apply system or Group Policy that prevents users from installing software (such as that needed for a desktop computer to communicate with a BlackBerry or Palm OS device).
▪ Lock PC cases and cover physical access to serial ports, USB ports, and other connection points so that removable media devices can't be attached.
Intentional internal breaches of security constitute a serious problem, and company policies should treat them as such. We discuss this topic in more detail in Chapter 12, in the section “Designing and Implementing Security Policies.”
Preventing Unauthorized External Intrusions
External intrusions and attacks are the major concerns of many companies when it comes to network security issues. In a number of high-profile cases in recent years, the Web servers of prominent organizations have been hacked. Attempts to penetrate sensitive government networks, such as the Pentagon's systems, occur on a regular basis. Distributed denial-of-service (DDoS) attacks make front-page news when they crash servers and prevent Internet users from accessing popular sites.
Note
Psychological factors affect the ways in which companies handle various types of security breaches. Companies usually see internal breaches as personnel problems and handle them in an administrative manner. External breaches might seem more like violations and are more often prosecuted as criminal actions. Because the external intruder can come from anywhere, at any time, the sense of uncertainty and fear of the unknown can cause organizations to react in a much stronger way to this type of threat. Thus, law enforcement officers are more likely to become involved when the breach is external. Officers might then (erroneously) conclude that the ratio of external to internal breaches is greater than it really is.
The good news about external intrusions is that the area(s) that must be controlled are much more focused than with internal attacks. There are usually only a limited number of points of entry to the network from the outside. This is where a properly configured firewall can be invaluable, allowing authorized traffic into the network while keeping unauthorized traffic out. On the other hand, the popularity of firewalls ensures that dedicated hackers know how they work and spend a great deal of time and effort devising ways to defeat them.
Planning for Firewall Failures
Organizations should never depend on the firewall to provide 100 percent protection, even against outside intruders. To be effective, a security plan must be both multifaceted and multilayered. Although administrators can hope that a firewall will keep intruders out of the network completely, their planning must take into consideration the possibility that the firewall will fail and address such questions as:
▪ If intruders do get in, what is the contingency plan?
▪ How can we reduce the amount of damage attackers can cause?
▪ How can the most sensitive or valuable data be protected?
External Intruders with Internal Access
A special type of external intruder is the outsider who physically breaks into your facility to gain access to your network. Although not a true insider because he or she is not authorized to be there and does not have a valid account on the network, this intruder enjoys many of the same advantages as the true insider. In Chapter 13, we'll discuss physical security and its importance to securing a network.
Tactical Planning
In dealing with network intruders, network administrators should practice what police officers in defensive tactics training call if/then thinking. This strategy involves considering every possible outcome of a given situation and then posing the question: “If this happens, then what could be done to protect us from the consequences?” The answers to these questions should form the basis of the organization's security policy.
This tactic requires that administrators be able to plan responses in detail, which means thinking in specifics rather than generalities. The security threat assessment must be based in part on understanding the motivations of people initiating the attack and in part on the technical aspects of the type of attack that is initiated. In a high-security environment, these tasks should be the responsibility of an incident response team.
Recognizing the “Fact of the Attack”
If preventive measures don't work (and it's likely that sometimes they won't), the next step for network administrators is to shift into reactive mode and attempt to minimize the damage. Before they can do that, they must have a way to recognize that an attack is taking place.
IDSes use two methods to identify that an attack is occurring:
▪ Pattern recognition Analyzing files, network traffic, sequences in random access memory (RAM), or other data for repeated or recognizable signs of attack, such as unexplained increases in file size or particular character strings
▪ Effect recognition Identifying the results of an attack, such as a system crash caused by overload or a sudden reboot for no reason
It's easy to program an IDS to recognize specific patterns, but attackers can defeat it by making small changes to the pattern or by fragmenting the attack packets—that is, dividing the attack messages or code into fragmented packets. A number of TCP/IP exploits use fragmented packets; these exploits are called frag attacks. Effect recognition is more difficult because the “effects” often resemble normal network traffic or problems caused by hardware or software faults.
The problem with any IDS—indeed, with all computer software—is that it does only exactly what it is told to do. Thus far, true artificial intelligence (programs that can “think”) hasn't been achieved. Law enforcement officers know that the human factor—intuition and the ability to make great leaps of logic—can be very important in detecting and solving crimes. Unfortunately, no device or program is able to observe the behavior of computer systems and network components and intuitively recognize that there's something wrong. Very specific criteria must be set and met before an IDS will recognize an attack. This explains why human administrators will always remain an important ingredient in creating a proper security posture in any organization and why eternal vigilance is more than just a watchword for people with security responsibilities.
Identifying and Categorizing Attack Types
The attack type refers to how an intruder gains entry to your computer or network (if, indeed, entry is actually gained at all) and what the attacker does once he or she has gained entry (or without gaining entry). Some of the more common types of hack attacks include social engineering attacks, DoS attacks, scanning and spoofing, “nuke” attacks, and dissemination of malicious code. When you have a basic understanding of how each type of attack works, you will be better armed to guard against them.
It is useful for us to sort these different intrusions and attacks into categories such as the following:
▪ Preintrusion/attack activities.
▪ Password-cracking methods, which we discussed in detail in Chapter 11.
▪ Technical exploits (taking advantage of characteristics of the equipment or protocols). We'll discuss exploits involving operating systems and applications in Chapter 11.
▪ Malicious code attacks (Trojans, viruses, worms).
The following sections discuss specific types of attacks that fit into each category.
Recognizing Preintrusion/Attack Activities
Hacker how-to documents often break the hack/attack process into steps, as follows:
1 Preattack
2 Initial access
3 Full system access
4 Planting “back doors” for future access
5 Covering tracks
The preattack phase focuses on gathering information. Experienced hackers tell newbies to learn as much about the targeted victim as they can before initiating an attack. This “intel” information is vitally important for a hacker who has a concrete goal, such as corporate espionage.
Planning the Hack and Hacking the Plan
The most successful hackers plan their attack strategies in almost as much detail as a military unit or police SWAT team plans a strike or raid. Then they carry out the hack exactly according to plan. These are the real pros, and they are the most difficult to defend against or apprehend. The hackers who get caught are usually careless, hurried, or inexperienced. In contrast, amateur hackers “play it by ear,” breaking into systems and wandering around looking for something of interest. The term amateur refers to someone who does something for fun, just for the love of it. Professional hackers (hackers for hire) know exactly what they're after, and they get in, get it, and get out quickly, like a master thief. The planning phase can last many times longer than the actual execution of the hack. When professional hackers get caught, it's usually because they're egotistical and brag about their exploits to the wrong people.
Preattack information gathering and planning involve determining the goal of the hack, determining the target of the attack (the network or system that must be compromised to achieve the goal), and identifying the weaknesses of the target that can be exploited to carry out the hack. Preattack planning can also include taking steps to disguise the attacker's identity or putting preliminary programs or devices in place to gather information or to make it easier to get into the system when the time comes to carry out the attack. Some specific preattack activities include:
▪ Port scanning to identify potential targets and their weaknesses
▪ IP spoofing to disguise the attacker's identity
▪ Placing Trojans on the target system
▪ Placing tracking devices and software (such as keystroke loggers) on the target system
▪ Putting protocol analyzers (sniffers) in place to capture transmissions to and from the target system
In the following sections, we look at each of these activities in more detail.
Port Scans
A port is, in its simplest meaning, a point where information enters or leaves a computer. Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) use port numbers to provide separate “subaddresses” to identify what service or application incoming information is destined for, or from which outgoing information originates.
The term port scanner, in the context of network security, refers to a software program that hackers use to remotely determine what TCP/UDP ports are open on a given system and thus are vulnerable to attack. Scanners are also used by administrators to detect vulnerabilities in their own systems, to correct them before an intruder finds them.
Scanning is used for several purposes prior to penetration and/or attack:
▪ Target enumeration Locating host systems that are open to attack
▪ Target identification Identifying the target system
▪ Service identification Identifying the vulnerable services or ports on the target system
Note
A common saying among hackers is “A good port scanner is worth a thousand passwords.”
A good scanning program can locate a target computer on the Internet (one that is vulnerable to attack), determine what TCP/IP services are running on the machine, and probe those services for security weaknesses. Many scanning programs are available as freeware on the Internet, but numerous security tools are also available for purchase with greater reliability and functions.
Port scanning refers to a means of locating “listening” TCP or UDP ports on a computer or router and obtaining as much information as possible about the device from the listening ports. TCP and UDP services and applications use a number of well-known ports (see the “Who's Listening?” sidebar in this section), which are widely published. The hacker uses his or her knowledge of these commonly used ports to extrapolate information.
For example, Telnet normally uses port 23. If the hacker finds that port open and listening, he or she knows that Telnet is probably enabled on the machine. The hacker can then try to infiltrate the system by, for example, guessing the appropriate password in a brute force attack.
Who's Listening?
The official well-known port assignments are documented in RFC 1700, available on the Web at www.freesoft.org/CIE/RFC/1700/index.htm. The port assignments are made by the Internet Assigned Numbers Authority (IANA). In general, a service uses the same port number with UDP as with TCP, although there are some exceptions. The assigned ports were originally those from 0–255, but the number was later expanded to 0–1,023.
Some of the most used well-known ports include:
▪ TCP/UDP port 20: FTP (data)
▪ TCP/UDP port 21: FTP (control)
▪ TCP/UDP port 23: Telnet
▪ TCP/UDP port 25: Simple Mail Transfer Protocol (SMTP)
▪ TCP/UDP port 53: Domain name system (DNS)
▪ TCP/UDP port 67: BOOTP server
▪ TCP/UDP port 68: BOOTP client
▪ TCP/UDP port 69: TFTP
▪ TCP/UDP port 80: HTTP
▪ TCP/UDP port 88: Kerberos
▪ TCP/UDP port 110: Post Office Protocol 3 (POP3)
▪ TCP/UDP port 119: Network News Transfer Protocol (NNTP)
▪ TCP/UDP port 137: NetBIOS name service
▪ TCP/UDP port 138: NetBIOS datagram service
▪ TCP/UDP port 139: NetBIOS session service
▪ TCP/UDP port 194: IRC
▪ TCP/UDP port 220: Internet Message Access Protocol (IMAP) v3
▪ TCP/UDP port 389: Lightweight Directory Access Protocol (LDAP)
Ports 1,024–65,535 are called registered ports; these numbers are not controlled by IANA and can be used by user processes or applications. Some of these are traditionally used by specific applications (for example, SQL uses port 1,433) and could be of interest to hackers.
A total of 65,535 TCP ports (and the same number of UDP ports) are used for various services and applications. If a port is open, it responds when another computer attempts to contact it over the network. Port-scanning programs such as Nmap are used to determine which ports are open on a particular machine. The program sends packets for a wide variety of protocols, and by examining which messages receive responses and which don't it creates a map of the computer's listening ports.
Port scanning does no harm to a network or system, but it provides hackers with information they can use to penetrate the network. Because people conducting port scans are often up to no good, they frequently forge the source IP address to hide their identity.
Should Scanning Be Illegal?
Some in the IT industry argue that port scanning should not be illegal, because “no harm is done.” They say port scanning is similar to ringing someone's doorbell to see if anybody is home—not in itself a crime. However, laws are enacted not just to protect from actual physical harm, but also to protect people's privacy and their interests in their own property. Those on the other side of the argument say that port scanning is really more like the virtual equivalent of someone who goes from door to door in an apartment building, trying each one to find out whether it's locked and whether there is an easy way in. Although this practice might do no actual harm if the “door scanner” only collects information and doesn't enter the premises, and although the person might have the right to be in the public hallway, in most jurisdictions such behavior would, at the very least, cause discomfort to the building's residents and attract the attention of the police.
In 2000, in Moulton v. VC3, a U.S. District Court in Georgia ruled that port scanning does not damage a network and thus does not constitute a crime or create a cause of action for civil suit. Although the federal laws in regard to computer fraud and abuse have changed since then, there is still a requirement that loss or damage must occur to charge a violation.
Half scans (also called half open scans or FIN scans) attempt to avoid detection by sending only initial or final packets rather than establishing a connection. A half scan starts the SYN/ACK process with a targeted computer but does not complete it. (See the description of this process in the following section on TCP/IP exploits.) Software that conducts half scans, such as Jakal, is called a stealth scanner. Many port-scanning detectors are unable to detect half scans.
Address Spoofing
The Merriam-Webster Online Dictionary (www.merriam-webster.com) defines a spoof as a “light humorous parody” or hoax, but also defines it as being synonymous with a less benign action of deception. Hackers use spoofed addresses to deceive other computers and fool them into thinking a message originated from a different machine. Although IP spoofing is probably the most popular, it is not the only spoofing method used by hackers. Others include ARP spoofing, Web spoofing (which we'll discuss in Chapter 11), and DNS spoofing. Let's take a quick look at how each of these works.
IP Spoofing
IP spoofing involves changing the packet headers of a message to indicate that it came from an IP address other than the true source. In essence, the sending computer impersonates another machine, fooling the recipient into accepting its messages. The spoofed address is normally a trusted port, which allows a hacker to get a message through a firewall or router that would otherwise be filtered out. When configured properly, modern firewalls protect against IP spoofing.
Spoofing is used whenever it is beneficial for one machine to impersonate another. It is often used in combination with one of the other types of attacks. For example, a spoofed address is used to hide the true IP address of the attacker in Ping of Death, Teardrop, and other attacks. Any service that uses IP address authentication is susceptible to IP spoofing.
After deciding on the targeted victim, the next step in spoofing is to find out the address of a trusted host. Legitimate communications between the trusted host and the target can be intercepted and examined. Often, hackers use a DoS attack against the trusted host to prevent it from communicating on the network. Then the packet headers can be modified to make it look as though the attacker's messages are coming from the trusted host, and the packets are sent to a service or port that uses address authentication. One of the most difficult aspects of IP spoofing is the necessity of correctly guessing the sequence numbers of the trusted machine. This process is made easy for the attacker by the numerous spoofing tools that are available on the Web.
ARP Spoofing
The Address Resolution Protocol (ARP) maintains the ARP cache. This is a table that maps IP addresses to Media Access Control (MAC) or physical addresses of computers on the network. This cache is necessary because the MAC address is used at the physical level to locate the destination computer to which a message should be delivered. If there is no cache entry for a particular IP address, ARP sends a broadcast message to all the computers on the subnet, requesting that the machine with the IP address in question respond with its MAC address. This mapping then gets added to the ARP cache. ARP spoofing, also called ARP poisoning, is a method of sending forged replies which result in incorrect entries in the cache. This results in subsequent messages being sent to the wrong computer (the machine whose MAC address is incorrectly matched with the IP address). Once again, this process has been automated b hacker tools such as ARPoison and Parasite have automated this process.
DNS Spoofing
DNS spoofing refers to two methods of causing a DNS server to direct users incorrectly:
▪ “Poisoning” of the DNS cache (similar to ARP poisoning in that incorrect information is entered into the cache) of name resolution servers, resulting in those servers directing users to the wrong Web sites or e-mail being sent to the wrong mail servers
▪ Using the recursive mechanism of DNS to predict the request that a DNS server will send and responding with forged information
Either of these methods allows the attacker to intercept the victim's mail or to set up spoofed Web pages that give users inaccurate information. This method can even be used to con the victim into providing personal information through Web forms. (See the section on Web spoofing in the discussion of browser exploits in Chapter 11.)
What Makes DNS Spoofing So Dangerous?
Because the DNS is responsible for managing the resolution of domain names (such as www.microsoft.com) into an equivalent IP address (for example, 206.122.10.6), any successful replacement of a valid address with an alternate address causes people attempting to access the domain name to visit the wrong TCP/IP address. This gives attackers the chance to create their own Web site that masquerades as a legitimate site and to attempt to steal all kinds of information by getting between the user and the real site. Alternatively, the attackers can completely take over the apparent role of the real site. Because DNS helps mediate access to Web, FTP, e-mail, and other services, the opportunities for mischief inherent in DNS spoofing are serious and powerful.
Placement of Trojans
Trojans, or Trojan horse software, are programs that appear to be legitimate or innocent but actually do something else in addition to or instead of their ostensible purposes. We discuss Trojans in general later in this chapter, in the section “Attacking with Trojans, Viruses, and Worms.” As part of the preattack phase, a hacker can plant on the victim's computer a Trojan program that installs keystroke-logging programs to gather information for the main attack or that sets up the means by which the attacker will later get into the system. An infamous case of the latter was the Back Orifice Trojan, which could be disguised as a component of some other innocuous software program and, once installed, created a “back door” for attackers to take over control of the victim PC. For more information about the updated Back Orifice 2000 (BO2K), you can visit www.bo2k.com.
Placement of Tracking Devices and Software
If an attacker has on-site access to the victim system, one way to collect passwords and other information prior to an attack is to place a physical tracking device (a keystroke logger) on the system. This is a very small device, about 2 inches long and a half-inch in diameter, which you can install in less than a minute; you simply unplug the keyboard from the PC and plug the keyboard into the logger, and then plug the logger into the PC's keyboard port. It is not noticeable to most users.
Inside the logger are a microchip and a nonvolatile memory chip (similar to a CompactFlash card or memory stick). Depending on the amount of memory in the device, it can record anywhere from a few to dozens of pages of keystrokes; for example, 64 KB of memory will store about 32 pages. No software needs to be installed on the computer for the loggers to work, and they are compatible with a variety of PC operating systems. No battery or outside power source is required; the device draws power from the computer. Once the strokes have been captured, the attacker removes the device and attaches it to a different PC. The captured data can be password-protected; once the correct password is entered, it can be read in Notepad or another text editor. Afterward, the data can be saved to a file and the memory in the device can be erased. An example of a keystroke-logging device is the KeyGhost (see www.keyghost.com).
Keystroke Logging As an Investigative or Monitoring Tool
Keystroke loggers and spyware programs are not used exclusively by criminals. Law enforcement investigators use logging devices and software to gather evidence of offenses. In early 2000, Nicodemo S. Scarfo, Jr., was charged with illegal gambling, racketeering, and loan shark activities based on evidence in a file on his computer, which had been encrypted with Pretty Good Privacy (PGP). Investigators used a keystroke logger to get the information needed to break the encryption. Defense attorneys tried to get the evidence suppressed, arguing that the use of the tool represented an unconstitutional search. However, the court ruled against the petition to suppress, and Scarfo eventually pled guilty.
Keystroke loggers and spyware have other legitimate purposes. Companies may use them to monitor employees’ computer and Internet activities (according to company policy), and parents can use them to oversee what their children are doing on the Net.
Software programs can also perform keystroke logging, but the attacker needs to be able to log on to the system to install the software; the advantage of the physical device is that it can capture the passwords necessary to log on. Software-based loggers capture only the keystrokes made after booting into the operating system, whereas the hardware device can capture keystrokes made before the OS loads—for example, changes made to the Basic Input Output System (BIOS).
Other spyware programs can do much more than just log keystrokes. Many of these programs allow the person who installs and configures the software to specify criteria that will trigger the capture of screenshots. Some of the programs can even rename themselves and change their locations on the disk to avoid detection. One such example of these monitoring programs is Spector Pro (www.spectorsoft.com).
Placement of Packet Capture and Protocol Analyzer Software
Network monitors, also called protocol analyzers, allow administrators to capture and analyze the traffic on their networks for troubleshooting purposes or to monitor network activity. Hackers can use these same tools to capture packets surreptitiously and read the information in those packets. Analyzers that allow for placing the network adapter in promiscuous mode are especially useful to hackers. In this mode, the adapter can capture traffic sent to or from any computer on the network segment. Some analyzers, such as the Network Monitor built into Microsoft Windows 2000 Server and Windows Server 2003, limit capture to packets sent to or from the machine that is running the analyzer software. However, a version of Microsoft's NetMon comes with the company's Systems Management Server product and permits the use of promiscuous mode.
These programs are network sniffers. Any person with Administrative privileges can install the Network Monitor on a Windows Server and start “listening” to activity on the wire. Administrators—or hackers who have compromised an administrative account—can use the tool to collect network data and analyze it on the spot, or they can save the recorded activities to review at a later time. It is possible to set triggers for when certain events or data cross the wire, so the tool can be used, for example, when certain keywords in e-mail communications move through the network. The Network Monitor program allows its users to capture only those frames that they are interested in based on protocol or the source or destination computer. Even more detailed and exacting filters can be applied to data that has been collected, allowing the monitoring person to pinpoint the precise elements that he or she is looking for in the captured data.
Figure 10.1 shows the contents of a captured packet. You can see the text message (“Windows 2003 is great!”) that was sent across the network.
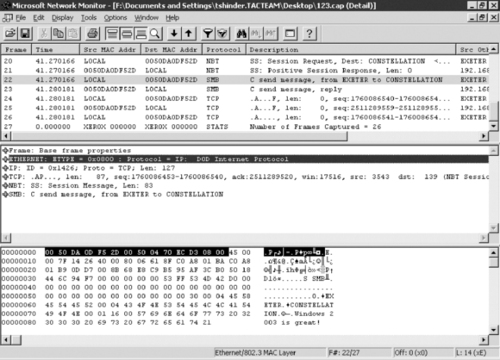 |
| Figure 10.1 The Contents of a Captured Packet |
Some commercial products provide greater functionality than the Network Monitor tool for Windows servers. You can use network information-gathering tools to obtain network data for forensic analysis and identify network issues; of course, malicious users also can use these tools for hacking purposes. These tools generally offer the functionality of a sniffer and an IDS combined. As we mentioned, sniffers are powerful programs that work by placing the host system's network card into promiscuous mode. A network card in promiscuous mode can receive all the data it can see, not just packets addressed to it. Switches segment traffic and know which particular port to send traffic to and block it from all the rest. Although this feature adds much needed performance gains, it does raise a barrier when attempting to sniff all potential switched ports. Forensic analysis will usually require the switch to be configured to mirror a port. Some common network monitoring tools include:
▪ NetWitness Designed to analyze network traffic and monitor it.
▪ NetResident Considered an advanced network content monitoring program that captures, stores, analyzes, and reconstructs network events such as e-mail messages, Web pages, downloaded files, and other types of network traffic.
▪ InfiniStream Security Forensics A commercial product that builds on sniffer technology by providing high-end tracking of absolutely everything.
▪ CA Network Forensics Allows the user to uncover and investigate network traffic. This program captures raw network data and uses forensic analysis to check for exploitation, internal data theft, and security violations.
▪ WireShark An open source protocol analyzer that can capture traffic in real time. Not only is it free to use, but it also works well in both a Windows and Linux environment. You can find more details about the program at the official site, www.wireshark.com.
Prevention and Response
There is no way to prevent port scanning—but IT professionals can control whether the scanner finds open doors to their networks. An important security step for administrators is to use port-scanning software themselves to learn about their own networks’ vulnerabilities and then plug the openings so that others will be unable to use them to gain access. Most firewalls log port-scanning attempts, and freeware or shareware such as Lockdown2000 or NukeNabber can be downloaded and installed to notify the administrator that ports are being scanned and provide the IP address from which the scan originates.
You can prevent IP spoofing using source address verification on the router, if it supports this function. Other steps you can take to protect against spoofing include:
▪ Using encrypted authentication
▪ Configuring the router to reject any messages from outside that appear to come from an internal (local) address
Administrators can prevent ARP spoofing using static ARP tables. A static table is manually configured by the administrator, so broadcast responses don't result in an automatic update of the cache. The problem with this solution is that it doesn't work well with large networks; the burden on the administrator to keep the tables current would be overwhelming. Another solution is MAC binding. This method is enabled on the network switches and allows automatic updating, but when a particular IP address has been associated with a MAC address, that association can't be changed except by an administrative action. Furthermore, some tools monitor changes to the cache, with automatic notification to administrators so that they will be aware of any attempts to use ARP spoofing.
Administrators can prevent DNS spoofing by securing the DNS servers on the Internet and by using the latest version of the DNS software. As vulnerabilities are identified, they are generally addressed in the next version.
Properly configured firewalls can help keep Trojans out of the network, and software such as Trojan Remover claims to be able to eliminate Trojan programs even when antivirus (AV) software cannot detect them. The usual virus protection guidelines (don't open unsolicited attachments, download files only from reputable sites, apply security patches diligently) can also help protect against Trojans.
Keystroke logging devices are impossible to detect via software. Physical examination of the cable connecting the keyboard to the computer reveals the presence of such devices. Antikeystroke logger programs can scan for keystroke logging activity and detect software-based loggers. An example is Anti-Keylogger, which is available from www.anti-keyloggers.com.
Protective measures against sniffers include limiting physical access to the network (because the sniffer software must be installed on a computer on the local subnet), using switches instead of hubs to prevent all packets from going to all the systems on the network, and using encryption. This last solution won't prevent sniffers from capturing network packets, but it will prevent the hacker from being able to read the data inside them. “Antisniffing” software can be used to scan the network for sniffers or for computers whose network adapters are running in promiscuous mode.
Understanding Technical Exploits
If a cyberintruder or attacker is unable to come up with passwords to get into the network posing as a legitimate user, he or she has numerous methods for breaking in without credentials. Generally, these methods exploit the characteristics of the protocols, operating system, or application software used on the targeted system or network. In the following sections, we discuss some popular technical exploits hackers use to gain access or to interrupt communications on networks. We will continue this discussion in Chapter 11, when we focus on exploits and vulnerabilities in operating systems and applications. Investigators should have a basic understanding of how these techniques work. Knowledge of how a cybercriminal commits the crime often provides valuable information for profiling that leads to apprehension.
Protocol Exploits
Protocol exploits use the characteristics of a protocol, such as the “handshake” method that TCP uses to establish a communications session, to obtain a result that was never intended—for example, overwhelming the targeted system to the point where it is unable to communicate with legitimate users. There are many ways that the normal behavior of network protocols can be manipulated to congest the network or server to the point where no legitimate communications can get through. In this section, we discuss in detail what a DoS attack is and the many ways that the characteristics of TCP/IP can be used to launch DoS attacks. We also discuss source routing attacks and other protocol exploits.
DoS Attacks That Exploit TCP/IP
DoS attacks, mentioned previously in this chapter, are one of the most popular choices of Internet hackers who want to disrupt a network's operations. In February 2000, massive DoS attacks brought down several of the world's biggest Web sites, including Yahoo.com and Buy.com. Many such attacks exploit various characteristics of the TCP/IP protocol suite. This section goes into detail on how various DoS attacks work. Attack types we discuss include:
▪ DNS DoS attacks, which exploit the DNS protocols
▪ SYN/LAND attacks, which exploit the way the TCP handshake process works
▪ The Ping of Death, which uses a “killer packet” to overwhelm a system
▪ Ping flood, fraggle, and smurf attacks, which use various methods to “flood” the network or server
▪ UDP bomb and UDP snork, which exploit User Datagram Protocol
▪ Teardrop attacks, which exploit the IP packet header fields
▪ Exploits of Simple Network Management Protocol (SNMP), which is included with most TCP/IP implementations
What Is Denial of Service?
Although they do not destroy or steal data like some other types of attacks, DoS attackers aim to bring down a network, denying service to its legitimate users. DoS attacks are easy to initiate; software is readily available from hacker Web sites and warez newsgroups that allow anyone to launch a DoS attack with little or no technical expertise.
The purpose of a DoS attack is to render a network inaccessible by generating a type or amount of network traffic that crashes the servers, overwhelms the routers, or otherwise prevents the network's devices from functioning properly. DoS can be accomplished by tying up the server's resources by, for example, overwhelming the CPU and memory resources. In other cases, a particular user or machine can be the target of DoS attacks that hang up the client machine and require it to be rebooted.
As we mentioned earlier in this chapter, distributed DoS, or DDoS, attacks use intermediary computers, called agents, on which programs called zombies have previously been surreptitiously installed. The hacker activates these zombie programs remotely, causing the intermediary computers (which can number in the hundreds or even thousands) to simultaneously launch the actual attack. Because the attack comes from the computers running the zombie programs, which could be on networks anywhere in the world, the hacker is able to conceal the true origin of the attack.
Examples of DDoS tools hackers use are Tribe FloodNet (TFN), TFN2K, Trinoo, and Stacheldraht (German for barbed wire). Early versions of DDoS tools targeted UNIX and Solaris systems, but TFN2K can run on both UNIX and Windows systems. Tools and information regarding DDoS attacks are available from http://packetstormsecurity.org/distributed/.
Because DDoS attacks are so popular, many tools have been developed to help you detect, eliminate, and analyze DDoS software that could be installed on your network. It is important to note that DDoS attacks pose a two-layer threat. Not only could your network be the target of a DoS attack that crashes your servers and prevents incoming and outgoing traffic, but also your computers could be used as the “innocent middlemen” to launch a DoS attack against another network or site.
DoS/DDoS attacks can be accomplished in a number of ways. Application exploits, operating system exploits, and protocol exploits can all be used to overload systems and create a denial of service. In the following sections, we address specific types of DoS and DDoS attacks and explain how they work.
DoS As a Weapon of Cyberwar
In November 2000, Lucent Technologies announced that a pro-Palestinian group named Unity had attacked its Web site using a tool called Defend, which creates a flood of messages designed to overwhelm the system and create a denial of service. Lucent was said to be targeted because it did business in Israel.
DNS DoS
The DNS DoS attack exploits the difference in size between a DNS query and a DNS response, in which all of the network's bandwidth is tied up by bogus DNS queries. The attacker uses the DNS servers as “amplifiers” to multiply the DNS traffic.
The attacker begins by sending small DNS queries to each DNS server that contains the spoofed IP address (see the “IP Spoofing” section earlier in this chapter) of the intended victim. The responses returned to the small queries are much larger in size so that if a large number of responses are returned at the same time, the link becomes congested and a denial of service will take place.
One solution to this problem is for administrators to configure DNS servers to respond with a “refused” response, which is much smaller in size than a name resolution response, when they receive DNS queries from suspicious or unexpected sources.
SYN/LAND Attacks
SYN attacks exploit the TCP “three-way handshake,” the process by which a communications session is established between two computers. Because TCP (unlike UDP) is connection-oriented, a session, or direct one-to-one communication link, must be created prior to sending data. The client computer initiates the communication with the server (the computer whose resources it wants to access).
The “handshake” includes the following steps:
1 The client machine sends a synchronization request (SYN) segment.
2 The server sends an acknowledgment (ACK) message and a SYN, which acknowledges the client machine's request that was sent in step 1, and sends the client a synchronization request of its own. The client and server machines must synchronize each other's sequence numbers.
3 The client sends an ACK back to the server, acknowledging the server's request for synchronization. When both machines have acknowledged each other's requests, the handshake has been successfully completed and a connection is established between the two computers.
Figure 10.2 illustrates how the process works.
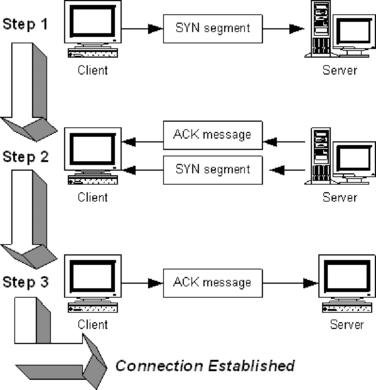 |
| Figure 10.2 TCP Using a “Three-Way Handshake” to Establish a Connection |
A SYN attack uses this process to flood the system targeted as the victim of the attack with multiple SYN packets that have bad source IP addresses. This causes the system to respond with SYN/ACK messages. The problem comes in when the system, waiting for the ACK message from the client that normally comes in response to its SYN/ACK, puts the waiting SYN/ACK messages into a queue. This is a problem because the queue is limited in the number of messages it can handle. When the queue is full, all subsequent incoming SYN packets will be ignored. For a SYN/ACK to be removed from the queue the client must return an ACK or an interval timer must run out and terminate the three-way handshake process.
Because the source IP addresses for the SYN packets sent by the attacker are no good, the ACKs that the server is waiting for never come. The queue stays full, and there is no room for valid SYN requests to be processed. Thus, service is denied to legitimate clients attempting to establish communications with the server.
The LAND attack is a variation on the SYN attack. In the LAND attack, instead of sending SYN packets with IP addresses that do not exist, the flood of SYN packets all have the same spoof IP address—that of the targeted computer.
You can prevent a LAND attack by filtering out incoming packets whose source IP addresses appear to be from computers on the internal network.
The Ping of Death
Another type of DoS attack is the so-called Ping of Death (also known as the large packet ping). The Ping of Death attack is launched by creating an IP packet larger than 65,536 bytes, which is the maximum allowed by the IP specification (sometimes referred to as a killer packet). This packet can cause the target system to crash, hang, or reboot.
Ping Flood/Fraggle/Smurf
The ping flood or ICMP flood is a means of tying up a specific client machine. It is caused by an attacker sending a large number of ping packets (ICMP echo request packets) to the victim. This flood prevents the software from responding to server ping activity requests, which causes the server to eventually time out the connection. A symptom of a ping flood is a huge amount of modem activity. This type of attack is also referred to as a ping storm.
The fraggle attack is related to the ping storm. Using a spoofed IP address (which is the address of the targeted victim), an attacker sends ping packets to a subnet, causing all computers on the subnet to respond to the spoofed address and flood it with echo reply messages.
The smurf attack is a form of brute force attack that uses the same method as the ping flood, but directs the flood of Internet Control Message Protocol (ICMP) echo request packets at the network's router. The destination address of the ping packets is the broadcast address of the network, which causes the router to broadcast the packet to every computer on the network or segment. This can result in a very large amount of network traffic if there are many host computers, and it can create congestion that causes a denial of service to legitimate users.
Note
The broadcast address is normally represented by all 1s in the host ID (in the binary form of the address). This means, for example, that on Class C network 192.168.1.0, the broadcast address would be 192.168.1.255. The number 255 in decimal represents 11111111 in binary, and in a Class C network, the last, or z, octet represents the host ID. A message sent to the broadcast address is sent simultaneously to all hosts on the network.
In its most insidious form, the smurf attacker spoofs the source IP address of the ping packet. Then both the network to which the packets are sent and the network of the spoofed source IP address will be overwhelmed with traffic. The network to which the spoofed source address belongs will be deluged with responses to the ping when all the hosts to which the ping was sent answer the echo request with an echo reply.
Smurf attacks can generally do more damage than some other forms of DoS, such as SYN floods. The SYN flood affects only the ability of other computers to establish a TCP connection to the flooded server, but a smurf attack can bring an entire ISP down for minutes or hours. This is because a single attacker can easily send 40 to 50 ping packets per second, even using a slow modem connection. Because each packet is broadcast to every computer on the destination network, the number of responses per second is 40 to 50 times the number of computers on the network—which could be hundreds or thousands. This is enough data to congest even a T1 link.
One way to prevent a smurf attack from using a network as the broadcast target is to turn off the capability to transmit broadcast traffic on the router. Most routers allow you to do this. To prevent the network from being the victim of the spoofed IP address, you should configure the firewall to filter out incoming ping packets.
UDP Bomb/UDP Snork
An attacker can use UDP and one of several services that echo packets on receipt to create service-denying network congestion by generating a flood of UDP packets between two target systems. For example, the UDP chargen service on the first computer, which is a testing tool that generates a series of characters for every packet that it receives, sends packets to another system's UDP echo service, which echoes every character it receives. UDP chargen is on port 19. By exploiting these testing tools, an endless flow of echoes goes back and forth between the two systems, congesting the network. This is sometimes called a UDP packet storm or UDP bomb.
In addition to port 7, the echo port, an attacker can use port 17, the quote of the day service (quotd), or the daytime service on port 13. These services also echo packets they receive. Disabling unnecessary UDP services on each computer (especially those mentioned earlier) or using a firewall to filter those ports or services protects you from this type of attack.
The snork attack is similar to the UDP bomb. It uses a UDP frame that has a source port of either 7 (echo) or 9 (chargen), with a destination port of 135 (Microsoft location service). The result is the same as the UDP bomb—a flood of unnecessary transmissions that can slow performance or crash the systems that are involved.
Teardrop Attacks
The Teardrop attack works a little differently from the Ping of Death, but with similar results. The Teardrop program creates IP fragments, which are pieces of an IP packet into which an original packet can be divided as it travels through the Internet. The problem is that the offset fields on these fragments, which are supposed to indicate the portion (in bytes) of the original packet that is contained in the fragment, overlap.
For example, normally two fragments’ offset fields might appear as shown here:
Fragment 1: (offset) 100 – 300
Fragment 2: (offset) 301 – 600
This indicates that the first fragment contains bytes 100 through 300 of the original packet and the second fragment contains bytes 301 through 600.
Overlapping offset fields appear something like this:
Fragment 1: (offset) 100 – 300
Fragment 2: (offset) 200 – 400
When the destination computer tries to reassemble these packets, it is unable to do so and could crash, hang, or reboot.
Variations include:
▪ NewTear
▪ Teardrop2
▪ SynDrop
▪ Boink
All of these programs generate some sort of fragment overlap.
SNMP Exploits
SNMP is used to monitor network devices and manage networks. It is a set of protocols that uses messages called Protocol Data Units (PDUs) over the network to various machines or devices that have SNMP agent software installed. These agents maintain Management Information Bases (MIBs) that contain information about the device. When agents receive the PDUs, they respond with information from the MIB. Vulnerabilities have been discovered in some implementations of SNMP that provide a means for attackers to disable the devices or create a DoS.
Source Routing Attacks
TCP/IP supports source routing, which is a means to permit the sender of network data to route the packets through a specific point on the network. There are two types of source routing:
▪ Strict source routing The data's sender can specify the exact route (rarely used).
▪ Loose source record route (LSRR) The sender can specify certain routers (hops) through which the packet must pass.
The source route is an option in the IP header that allows the sender to override routing decisions that are normally made by the routers between the source and destination machines. Network administrators use source routing to map the network or for troubleshooting routing and communications problems. You can also use it to force traffic through a route that will provide the best performance. Unfortunately, hackers can exploit source routing.
If the system allows source routing, an intruder can use it to reach private internal addresses on the LAN that normally would not be reachable from the Internet, by routing the traffic through another machine that is reachable from both the Internet and the internal machine. Source routing can be disabled on most routers to prevent this type of attack.
Router Exploits
Many hackers now target routers instead of computers for their attacks. The popularity of DSL and cable Internet connectivity has brought routers to home networks as well as business networks. This, in turn, has created a new point of vulnerability.
Many of the new, relatively inexpensive routers designed for broadband connections come with default administrator passwords that can be used on any of the vendor's devices if the administrator does not change the password. This means a hacker with knowledge of the default password could log on and make changes to the routing table or router configuration. This differs from most operating systems that do not come with a default password but require the user to create one during installation. In addition to the administrator password, some router vendors have created special so-called “back door” passwords for their systems, intended to be used by the vendor's tech support personnel so that if an administrator forgot the admin password, the vendor could help the administrator get back in. Of course, this system could also be exploited by hackers with knowledge of the secret “master” password.
Hackers can also obtain router passwords the same way they get the passwords for computers: using sniffer or spyware software, brute force attacks, or social engineering tactics. Whichever method the hacker uses to access the router, he or she can then create DoS attacks by changing routing table entries to send all messages to the same destination. In fact, if the router uses Routing Information Protocol (RIP) to dynamically update its routing tables, the attacker can send spoofed RIP messages to make the changes to the routing table without even needing to access the router directly.
Prevention and Response
Administrators can take a number of steps to help prevent exploits, including the following:
▪ You can protect Linux systems from SYN attacks by building the kernel with SYN cookies. Some versions of UNIX (such as Solaris 2.6 and later) have built-in protection against SYN attacks. In Windows servers, you can edit the Registry to protect against SYN attacks. For information and how-to instructions on hardening the TCP/IP stack against DoS attacks, see http://support.microsoft.com/kb/324270.
▪ You can configure routers to respond to directed broadcasts instead of passing them on to the subnet to guard against smurf attacks.
▪ You can configure DNS servers to respond with a “refused” response when they receive DNS queries from suspicious or unexpected sources to protect from DNS DoS attacks.
▪ You can configure the router to filter out incoming packets with a source IP address that appears to be from the local network.
▪ You can configure the system to ignore router redirects.
▪ You can disable SNMP, if it is not needed, to protect against exploits that rely on the protocol.
▪ You can change default passwords on routers and disable “back door” passwords.
Attacking with Trojans, Viruses, and Worms
Intruders who access networks and systems without authorization, or inside attackers with malicious motives, can plant various types of programs to cause damage to the network. These programs—often lumped together under the general term viruses, although there are other varieties—have cost companies and individuals billions of dollars in lost data, lost productivity, and the time and expense of recovery.
The cost of damage is impossible to determine accurately. Although you can calculate the hourly wage of a network administrator who must restore data from backups, or you can calculate the cost of AV software to purge the virus from systems, it is often difficult to calculate the monetary value of lost data. For example, if someone loses an unpublished novel on his or her computer, is it worthless because it isn't published, or has this person lost potential millions? Because of this, you hear wide ranges in how much a virus cost in damage. What is always certain is that there are new viruses every week, and more devastating ones always on the horizon.
Considering that Symantec provides a searchable database of viruses, Trojans, and worms on its site (www.symantec.com/security_response/index.jsp), it would be impossible to discuss all of them in this chapter. However, a number of viruses have had a great impact on networks, the Internet, and personal computers over the decades. By looking at these, we can get a better understanding of how they work:
▪ CIH/Chernobyl In the late 1990s, this virus caused a great deal of damage to business and home computer users. It infected executable files and was spread by running an infected file on a Windows 95/98 machine. There were several variants of CIH; these were “time bomb” viruses that activated on a predefined date (either April 26—the anniversary of the Chernobyl disaster—or every month on the 26th). Until the trigger date, the virus remained dormant. Once the computer's internal clock indicated the activation date, the virus would overwrite the first 2,048 sectors of every hard disk in the computer, thus wiping out the file allocation table and causing the hard disk to appear to be erased. However, the data on the rest of the disk could be recovered using data recovery software; many users were unaware of this capability. The virus also attempted to write to the BIOS boot block, rendering the computer unbootable. (This did not work on computers that had been set to prevent writing to the BIOS.) This virus started to show up again in spring 2002, piggybacking on the Klez virus, described later in this list.
▪ Melissa This was the first virus to be widely disseminated via e-mail, starting in March 1999. It is a macro virus, written in Visual Basic for Applications (VBA) and embedded in a Microsoft Word 97/2000 document. When the infected document is opened, the macro runs (unless Word is set not to run macros), sending itself to the first 50 entries in every Microsoft Outlook Messaging Application Program Interface (MAPI) address book. These include mailing list addresses, which could result in very rapid propagation of the virus. The virus also made changes to the Normal.dot template, which caused newly created Word documents to be infected. Because of the huge volume of mail it produced, the virus caused a denial of service on some e-mail servers. The confessed author of the virus, David Smith, was sentenced to 20 months in federal prison and was fined $5,000.
▪ Code Red In summer 2001, this self-propagating worm began to infect Web servers running Internet Information Server (IIS). On various trigger dates, the infected machine would try to connect to TCP port 80 (used for Web services) on computers with randomly selected IP addresses. When successful, it attempted to infect the remote systems. Some variations also defaced Web pages stored on the server. On other dates, the infected machine would launch a DoS attack against a specific IP address embedded in the code. CERT reported that Code Red infected more than 250,000 systems over the course of nine hours on July 19, 2001.
▪ Nimda In late summer 2001, the Nimda worm infected numerous computers running Windows 95/98/Me, NT, and 2000. The worm made changes to Web documents and executable files on the infected systems and created multiple copies of itself. It spread via e-mail, via network shares, and through accessing infected Web sites. It also exploited vulnerabilities in IIS versions 4 and 5 and spread from client machines to Web servers through the back doors left by the Code Red II worm. Nimda allowed attackers to then execute arbitrary commands on IIS machines that had not been patched, and denials of service were caused by the worm's activities.
▪ Klez In late 2001 and early 2002, this e-mail worm spread throughout the Internet. It propagates through e-mail mass mailings and exploits vulnerabilities in the unpatched versions of Outlook and Outlook Express mail clients, attempting to run when the message containing it is previewed. When it runs, it copies itself to the System or System32 folder in the system root directory and modifies a Registry key to cause it to be executed when Windows is started. It also tries to disable any virus scanners and sends copies of itself to addresses in the Windows address book, in the form of a random filename with a double extension (for example, file.doc.exe). The payload executes on the 13th day of every other month, starting with January, resulting in files on local and mapped drives being set to 0 bytes.
▪ MyDoom In January 2004, this worm (which is also called the Norvarg worm) set a record as to how fast it was disseminated, and actually managed to slow global Internet performance by 10 percent. The worm was spread as an e-mail that appeared to be an error message containing the text “Mail Transaction Failed.” When someone opened the e-mail, the worm would spread further by being sent to any e-mail addresses found in address books on the machine. It spread further through shared directories used by the file-sharing program Kazaa. It was estimated that during the first hours the worm was disseminated, one in 10 e-mails sent over the Internet contained MyDoom. It is no longer a threat, because MyDoom was programmed to stop after February 12, 2004.
These are only a few examples of the damage and inconvenience caused by various forms of malicious code. There are three broad categories of this type of code, identified as Trojans or Trojan horse programs, viruses, and worms. We take a brief look at each of these attack types in the following sections.
Trojans
The name Trojan is short for Trojan horse and refers to a software program that appears to perform a useful function but in fact performs actions that the program's user does not intend or is not aware of. Trojan horses are often written by hackers to circumvent a system's security. Once the Trojan is installed, the hacker can exploit the security holes it creates to gain unauthorized access, or the Trojan program may perform some action such as:
▪ Deleting or modifying files
▪ Transmitting files across the network to the intruder
▪ Installing other programs or viruses
Basically, the Trojan can perform any action that the user has privileges and permissions to do on the system. This means that a Trojan is especially dangerous if the unsuspecting user who installs it is an administrator and has access to the system files.
Trojans can be very cleverly disguised as innocuous programs, utilities, or screensavers. A Trojan can also be installed by an executable script (JavaScript, a Java applet, ActiveX control, or the like) on a Web site. Accessing the site can initiate the program's installation if the Web browser is configured to allow scripts to run automatically. Trojans can use the default behavior of Windows to disguise their true nature. Because the file extension (the characters that appear after the last dot in a filename) are hidden by default, a hacker can name a file something such as vacation.jpg.exe and it will be shown in Windows Explorer as vacation.jpg, seeming to be an innocent graphics file when it is really an executable program. Of course, double-clicking it to open the “picture” will run the program. Trojans that are designed to allow a hacker unauthorized access across the network (such as Back Orifice) are sometimes called remote access Trojans, or RATs.
Warning
Although Microsoft Office documents are not executable files themselves, they can contain macros, which are small programs that are embedded into the documents and can be used to spread malicious code. Thus, Office documents should be treated as though they are executables unless running macros is disabled in the Office program.
Viruses
Viruses are programs that are usually installed without the user's awareness and perform undesired actions that are often harmful, although sometimes merely annoying. Viruses can also replicate themselves, infecting other systems by writing themselves to any diskette that is used in the computer or sending themselves across the network. Viruses are often distributed as attachments to e-mail or as macros in word processing documents. Some activate immediately on installation, and others lie dormant until a specific date or time or a particular system event triggers them. For more information, see the article “How Computer Viruses Work” at www.howstuffworks.com/virus.htm.
Viruses come in thousands of varieties. They can do anything from popping up a message that says “Hi!” to erasing the entire contents of a computer's hard disk. The proliferation of computer viruses has also led to the phenomenon of the virus hoax, which is a warning—generally circulated via e-mail or Web sites—about a virus that does not exist or that does not do what the warning claims it will do.
Real viruses, however, present a real threat to your network. Companies such as Symantec and other AV software vendors design their products to detect and remove virus programs. Because new viruses are created daily, it is important to download new virus definition files, which contain information required to detect each virus type, on a regular basis to ensure that your virus protection stays up-to-date.
The types of viruses include:
▪ Boot sector viruses These are often transmitted via a diskette. The virus is written to the Master Boot Record (MBR) on the hard disk, from which it is loaded into the computer's memory every time the system is booted.
▪ Application or program viruses These are executable programs that, when run, infect your system. Viruses can also be attached to other, harmless programs and can be installed at the same time the desirable program is installed.
▪ Macro viruses These are embedded in documents (such as Microsoft Word documents) that can use macros, small applications or “applets” that automate the performance of some task or sequence.
Viruses that are programmed to “go off” (activate and destroy data or files) on a certain date are called time bombs or logic bombs. One of the first of this type to gain worldwide attention was the Michelangelo virus in the early 1990s, which attempted to erase the hard disks of infected PCs on March 6, the birthday of the famous painter. A few years later, a disgruntled ex-employee of Omega Engineering planted a time-bomb virus on the company's network that resulted in approximately $10 million in loss and damage. He was convicted of the crime and sentenced to 41 months in prison.
Understanding the Virus Threat
The most dangerous aspect of computer viruses (as is true of their biological counterparts) is their ability to “mutate” into something else. Of course, this mutation doesn't happen spontaneously, but virus writers build on the code of others to make relatively benign viruses more destructive—and to avoid detection by AV software.
Worms
A worm is a program that can travel across a network from one computer to another. Sometimes different parts of a worm run on different computers. Worms make multiple copies of themselves and spread throughout a network. The distinction between viruses and worms has become blurred. Originally the term worm was used to describe code that attacked multiuser systems (networks), whereas virus described programs that replicated on individual computers.
The primary purpose of the worm is to replicate. These programs were initially used for legitimate purposes in performing network management duties, but their ability to multiply quickly has been exploited by hackers who create malicious worms that replicate wildly and can also exploit operating system weaknesses and perform other harmful actions.
Prevention and Response
Protecting systems and networks from the damage caused by Trojans, viruses, and worms is mostly a matter of common sense. Practices that can help prevent infection include the following:
▪ Don't run executable (.exe) files from unknown sources, including those attached to e-mail or downloaded from Web sites.
▪ Turn off the Preview and/or HTML mail options in your e-mail client program.
▪ Don't open Microsoft Office documents from unknown sources without first disabling macros.
▪ Be careful about using diskettes that have been used in other computers.
▪ Install and use firewall software.
▪ Install AV software, configuring it to run scans automatically at predefined times and updating the definition files regularly.
▪ Use intrusion prevention tools called behavior blockers that deny programs the ability to execute operations that have not been explicitly permitted.
▪ Use behavior detection solutions such as Finjan's Real-Time Content Inspection (www.finjan.com) that can use heuristic techniques to analyze executable files and assess whether they are likely to be hostile.
▪ Use integrity checker software such as Tripwire (http://sourceforge.net/projects/tripwire) to scan the system for changes.
Recognizing the presence of malicious code is the first-response step if the system does get infected. Administrators and users need to be on the alert for common indications that a virus might be present, such as missing files or programs; unexplained changes to the system's configuration; unexpected and unexplained displays, messages, or sounds; new files or programs that suddenly appear with no explanation; memory “leaks” (less available system memory than normal) or unexplained use of disk space; and any other odd behavior of programs or the operating system. If a virus is suspected, a good AV program should be installed and run to scan the system for viruses and attempt to remove or quarantine any that are found. Finally, all mission-critical or irreplaceable data should be backed up on a regular basis in case all these measures fail.
Some virus writers create “proof of concept” viruses that do not cause damage and are designed merely to demonstrate that a particular type of virus can be written. For example, it was once thought that viruses could not be spread by simply reading e-mail; users were told that as long as they didn't open attachments, they were safe. The first viruses exploiting Hypertext Markup Language (HTML) e-mail to run and infect systems when a user opened the e-mail message (not an attachment) proved that the concept of a virus that could spread via e-mail alone. In June 2002, researchers at McAfee received a proof-of-concept virus called Perrun that is embedded in a JPEG image file. Although limited, this was the first known case of a virus embedded in a picture file that runs automatically when the graphic is viewed. That same month, Symantec reported the first cross-platform virus; it could infect both Linux and Windows systems.
The moral of the story is that virus writers are a creative and persistent bunch and will continue to come up with new ways to do the “impossible,” so computer users should never assume that any particular file type or operating system is immune to malicious code. The only sure way to protect against viruses is to power down the computer and to leave it turned off.
Hacking for Nontechies
As we've mentioned, highly developed technical skills are no longer necessary for people who want to break into computer systems and networks. Some say that hacking was originally an art that required great talent, that later required only a bit of skill, and that today can be done by anyone who has enough hand-eye coordination to click a mouse. To put it more eloquently, “Hacking has devolved from a labor of love to unskilled labor.” This process of deterioration began with the phenomenon of the script kiddie.
The Script Kiddie Phenomenon
You'll find a dozen definitions of script kiddie, depending on the source you consult. Webopedia (www.webopedia.com) defines the term as someone who “randomly seeks out a specific weakness over the Internet in order to gain root access to a system without really understanding what it is s/he is exploiting because the weakness was discovered by someone else.” The Jargon Lexicon at www.faqs.org/docs/jargon/index.html is a bit more judgmental: “The lowest form of cracker … People who cannot program but who create tacky HTML pages by copying JavaScript routines from other tacky HTML pages.”
Regardless of the precise definition, most agree on one thing: Script kiddies don't have much technical expertise themselves, but they use code written by others to wreak havoc. In the hacker culture, they are generally regarded with contempt or at least with a lack of respect. Nonetheless, hackers who do understand the technology continue to distribute scripts and programs that the script kiddies use to do their dirty work.
The number of people who write their own code to hack systems is relatively low in comparison to those who have marginal skills and use the scripts and tools of others. Script kiddies and their cousins, packet monkeys (people who launch DoS attacks against Web sites for “no apparent reason”), have been around for many years, and have caused considerable damage to systems throughout the world. An example is the large-scale DDoS attack that brought down Yahoo!, eBay, ZDNet, and CNN. The Yahoo! attack was launched by a Canadian teenager called “Mafiaboy” who used a utility called Stacheldraht that was written by a German hacker.
The “real” hackers spend years playing with computer systems and learning the intricacies of complex operating systems, often preferring to work with UNIX. They take pride in their knowledge and in the “elegance” of their attacks. They regard script kiddies, who rely on scripts written by others and even stoop to using hacking tools with graphical interfaces, in much the way a master jewel thief regards a street thug. Because script kiddies are unskilled (and thus are less able to cover their tracks) and because they tend to crave attention (whereas most skilled hackers take pride in being able to stealthily invade a system and get out without anyone knowing), script kiddies make up a large proportion of the network intruders and attackers who are caught and prosecuted.
Despite their disrespectful nickname and the low level of regard they're given in the hacker community, script kiddies can do a lot of damage, and the randomness of their attacks makes them especially dangerous. As with drive-by shootings that target random victims, script kiddies’ actions are impossible to predict and they place everyone at risk.
The “Point and Click” Hacker
As unsophisticated as script kiddies are, another variety of “wannabe” hacker is even less technically savvy. At least the average script kiddie knows enough to type a few commands to launch the script he or she got from somebody else. The newest incarnation of “do it the easy way” attackers is too unknowledgeable—or too lazy—to do even that. Instead, this new breed uses “point and click” utilities with pretty graphical interfaces or “fill in the blank” Web sites that serve as front ends to launch the chosen attack(s) against specified targets without the so-called hacker even needing to know how to download a file.
David Rhoades of Maven Security came up with the term click kiddies to describe these “rebels without a clue.” Rhoades travels to computer security conferences around the world with his presentation, called “Hacking for the Masses.” In his talk, he outlines just how easy it is for literally anyone to commit online breaking and entering—and much worse—with readily available tools that, to paraphrase Rhoades, are so user-friendly even your grandmother can bring down several servers before dinner.
Note
Rhoades’ discussion of this type of hacker is available to view in his presentations, called “Hacking for the Masses” and “De-Evolution of the Hacker,” which are available at www.mavensecurity.com/presentations.
Use of the Web-based attack tools favored by click kiddies also makes it more difficult to trace the origin of the attack, because the attack is coming from an intermediary (the Web site that provides the tool) instead of directly from the attacker.
Prevention and Response
The same preventive measures that we've already discussed apply to protecting a network from nontechie hackers. In addition, script kiddies can sometimes be lured in and caught by setting up a honeypot, which is a system designed specifically for the purpose of trapping attackers. The honeypot is a system or network that acts as an “open invitation” to hackers. It is connected to the Internet with minimal protection, running unpatched operating systems and application software that can be easily exploited. The systems are constantly monitored so that the attacker can be identified and traced before he or she has a chance to destroy evidence. We discuss honeypots in more detail in Chapter 14.
Understanding Wireless Attacks
In many corporate networks across the country, wireless devices are extending the network perimeter beyond the confines of the office walls and into neighboring buildings and public streets. No longer does an attacker need to gain network access by breaking into an office or attempting to bypass strict firewall policies. Now attackers can take advantage of an unsuspecting company that doesn't realize its wireless infrastructure security is so loose it can be hacked in less than 15 minutes.
You often read stories about hackers sitting in vehicles with a laptop and a high-powered wireless antenna, scanning for insecure wireless networks to compromise. These hackers may be looking for internal corporate intellectual property to sell to a competitor or data that may be used for blackmail or extortion. BJ's Wholesale Club, Lowe's Companies Inc., DSW, Wake Forest University School of Medicine, and TJX have all been victims of compromised wireless networks. The cost of these data breaches could be well into the millions of dollars, but their true cost remains difficult to calculate because we must take into consideration the money spent by the company to investigate the problem, provide damages to the victims, and fix the vulnerabilities, and factor in loss of revenue due to low consumer confidence.
As the cost to implement wireless networks continues to decrease, more and more companies and home users are using wireless technology. Since 2006, London has seen 160 percent more wireless access points, with New York increasing a substantial 49 percent. However, you don't need to look at statistics to realize that wireless networks are becoming more popular. Open your wireless configuration user interface and you will usually see three or four networks in the surrounding area. If you live in the city, that number can be as high as 15 to 20.
This section discusses the basics of wireless networks and the methods hackers use to attack them. Hackers have an advantage when it comes to wireless attacks due to anonymity and the difficulty of tracking down attacks. The attack surface is huge and the results are appealing because once a hacker gets in, he or she is on the internal network, bypassing many of the traditional network security barriers.
Basics of Wireless
A wireless access point connects the traditional wired network to wireless clients by transmitting network data through the air. The wireless access point acts as a relay between the wired network and wireless clients. Many companies implement many wireless access points that can hand off the wireless signal to ensure that the client does not get disconnected. These access points range from home or home office devices that cost less than $100 to enterprise access points that implement complex security features and allow for specialized configuration and management.
The wireless access points themselves simply provide a means for the data to travel from the wired network to the client. The network infrastructure services must still be provided to the client. Although most access points today have these features built into the device, you can also use your traditional servers to provide services such as Dynamic Host Configuration Protocol (DHCP) and routing.
For a client to connect wirelessly to a LAN, it must have a wireless network card compatible with the wireless standard used by the target network. With the majority of laptops today including built-in network devices, wireless networks are becoming a standard with most home and corporate networks. Although wireless LANs have traditionally been used for mobile devices, the ease and cost-effectiveness of extending the network has some companies implementing wireless cards on their desktop machines.
Even with all the advancements in recent years, installing a wireless network on your LAN is not something you should do without careful planning. Before adding wireless connectivity to your network, you should understand the major advantages and disadvantages of introducing wireless connectivity.
Different Types of Wireless Networks
Different types of wireless networks are available, the most common being 802.11 b/g. 802.11b was the first wireless standard developed for commercial use. It operates at 2.4 GHz and transfers data at a rate of 11 megabits per second (Mbps). Improving data transfer to 54 Mbps, 802.11 g was a welcome upgrade for consumers wanting faster throughput from their wireless infrastructure. Although the 2.4 GHz band would often lead to interference problems, backward compatibility and early adoption helped this combination become the standard for wireless devices.
For those companies that required less interference or that could not adopt the 2.4 GHz band as an acceptable solution, 802.11a was released that worked on the 5 GHz band. 802.11a improved on wireless stability, reducing dropped connections, while staying at the 54 Mbps transfer rate. The main downside is the expense of upgrading both the wireless access points and the client's wireless cards to devices that support this standard.
Wireless devices can also connect two remote locations by using line-of-sight antennas to send data from one location to another where the installation of cabling would not be feasible. A company that has a second building located less than a mile from the main building may choose to implement a line-of-sight wireless solution for Internet connectivity instead of spending the reoccurring cost of a traditional T1 line.
Advantages of a Wireless Network
Wireless networks offer users the following advantages:
▪ Ease of accessing the network No longer are employees bound to areas where they can plug into a wall jack to connect to the network. Being able to connect your laptop to the network from anywhere in the building allows for more freedom.
▪ Reduced cost of running cable The labor cost alone of wiring an office or office building can be quite high compared to the cost of purchasing and installing a wireless device and cards. With wireless cards available for desktop computers, an office can be network-available in a matter of minutes.
▪ Productivity Employees can now take their laptops with them to meetings or any other place required, and yet continue working.
Disadvantages of a Wireless Network
Wireless networks also have some disadvantages as well:
▪ Security The main disadvantage of wireless is its lack of security. If proper planning and configuration are not taken into consideration, any wireless network can be easily compromised.
▪ Complexity and reliability Although adding wireless access points increases accessibility to the wired network, it can also increase the complexity of the network design. System administrators must be aware of the impact that the wireless devices have on the network and troubleshoot problems such as weak signals and dropped wireless connections.
▪ Network performance Although the advertised speed of a wireless connection is 54 Mbps, the actual data throughput is often much lower, especially if many computers are using the same wireless connection. A wired network drop will almost always outperform a wireless connection.
Association of Wireless AP and a Device
To transmit and receive data through a wireless connection, the client must be associated with the access point. This association connects the two devices and allows the client to obtain an IP address and communication on the network. Signal power and security settings can interfere with the association process.
On Windows XP and Windows Server operating systems, Microsoft provides the Windows Wireless Zero Configuration (WZC) utility to assist the user with connecting to wireless networks. Although it does make the association process easier, it also introduces some security concerns you should be aware of.
If a preferred network is not available, WZC will probe for networks that are already connected. This information can be viewed by anyone using a wireless analyzer and can be used to set up fake access points to lure clients to connect. WZC will also attempt to connect to the wireless network with the strongest signal. Knowing this, an attacker can create fake wireless networks with high-power antennas and cause computers to associate with their access point rather than the legitimate one. When possible, it is recommended that you use the vendor-provided wireless management tool.
If you are using a wireless card from Linksys, Dell, or Netgear, you will likely have installed management software from the vendor that can control the association of the wireless device. This software has been designed by the manufacturer to work with the corresponding hardware and is typically more secure.
All wireless management software will require you to select the wireless network to which you would like to connect. You will select the service set identifier (SSID). The SSID is the public name of the wireless network. If the network has security enabled, you will be prompted to enter the passphrase or encryption key. If you do not know the key, you will not be allowed access to the network. If the network is open or you enter the correct security key, your computer will attempt to establish the connection.
Note
In Chapter 13, we'll discuss a number of security issues and methods used to protect wireless networks.
Wireless Penetration Testing
Wireless penetration testing involves using the same techniques that hackers use to attack wireless networks. A negative stigma is often associated with the use of hacker tools and methodologies. Network administrators and management frequently consider the use of these tools as the legitimization of hacker-based tactics and strategies. This attitude can lead to an insecure wireless network that has not been tested to determine the ability to prevent a true attack from succeeding.
Conducting penetration tests to determine the security of your wireless infrastructure is essential. Through the practice of learning, understanding, and implementing the same methods of attack the intruder will use, one can better assess vulnerabilities, overcome weaknesses, and fortify defenses. During a wireless penetration test, it is important to gather as much information about the network as possible. Most networks are discovered during wardriving (the process of scanning for insecure networks), so the attack may be targeted more toward a wireless vulnerability than a specific corporate network.
When conducting a penetration test you should conduct both are an internal and an external attack. The internal approach allows you to use information you already know about the network, such as encryption keys, network design, and signal ranges. This type of test validates the security of the network from an internal employee's point of view. External testing is done without using any knowledge of the network infrastructure. The tester uses tools an intruder would use and simulates an actual attack. It is important that a skilled security professional perform this test to ensure that these tools do not negatively impact network and server systems.
The key thing to remember during a wireless penetration test is that the goal is to assess the security of the wireless network. Management approval in writing of what tests are expected and the potential impact to the network is a good way to ensure no surprises for either side. Those performing the test should also do the following:
▪ Never do anything that will compromise or affect a neighboring wireless network.
▪ Never try any type of DoS attack on the network without approval.
▪ As various portions of the network are cracked (or are attempted to be penetrated), make sure to keep the results of the scan and penetration test confidential, and ensure that the results are stored safely.
▪ Report all findings to management with detailed explanations and security recommendations.
Search Warrants
Before you can investigate a device owned by someone else, you will need permission from an authorized party (the owner of that device) or you may be required to obtain a search warrant. You must verify that the search warrant includes the proper authorization to perform on-site examinations of computer equipment such as wireless access devices. Do not perform any forensic analysis on equipment you are not authorized to analyze.
Direct Connections to Wireless Access Points
Users that are persistent in their desire to connect to an unauthorized access point will keep an eye out for security professionals completing wireless audits and simply unplug the access point until the scan is complete. The amount of effort required for physical wireless scans can often result in less frequent scans. Detecting wireless access points from your wired network has many advantages. You can set automated scripts that search your network on a continuous basis, saving you time and money. By using tools such as Nmap and Nessus, you can scan sections of your network not easily accessible to wireless scanning.
To perform wired network scans for access points, you must be connected to the internal network and have the ability to connect to all the subnets you want to scan.
Rogue Access Points
For enterprise-class access point detection, organizations may want to consider investing in a wireless IDS/IPS system. A wireless IDS/IPS is an intrusion detection/intrusion prevention system that provides 24/7 monitoring on the network and can dynamically respond to wireless threats.
In addition to detecting rogue devices, a wireless IDS/IPS can terminate them using air or port suppression on the switch, provide forensic analysis of packets sent and received, and provide location tracking of the device by triangulating the signal between multiple sensors.
Rogue access points represent a growing threat to network administrators because users can plug in a wireless access point with a minimal configuration and extend the network wirelessly. This creates a lack of control regarding where data is being sent, and worse, who is listening.
Wireless Connection to a Wireless Access Point
Before initiating an attack, a hacker will want to know as much about the target network as possible, using various wireless tools to perform information gathering. Once the hacker feels comfortable with the information gathered, he or she may use injection techniques to force information across the wireless network that can be used to crack encryption schemes. Once this data has been captured, it is matter of time before the encryption key is discovered and the hacker is connected to the internal network via the wireless access point.
The tools used to perform these attacks are freely available on the Internet and are included in live security distributions. Some of these tools include:
▪ Aircrack-ng suite (www.aircrack-ng.org) A suite of tools for auditing wireless networks. It includes Airodump-ng (which logs the coordinates of access points and captures raw 802.11 packets), Aireplay-ng (which can be used to inject frames into wireless networks), Aircrack-ng (which can recover keys once enough packets have been captured), and Airdecap-ng (which decrypts encrypted capture files).
▪ Kismet (www.kismetwireless.net) A Layer 2 wireless packet analyzer that works with wireless cards that support raw monitoring mode. Kismet can quickly identify wireless networks by capturing wireless packets and retrieving information such as whether they have security-enabled SSID cloaking, network channels, and an SSID of the network.
BackTrack
Getting all the tools necessary to perform penetration-testing tasks can be quite daunting. Compatibility issues with kernels and dependent drivers can have a security analyst spending most of the time getting the tools to work instead of testing the security of his or her applications or devices. Live CDs are bootable CDs that contain preconfigured operating systems and tools that are distributed by groups over the Internet. One of the premier Security distributions is BackTrack (www.remote-exploit.org/backtrack.html).
The BackTrack live CD distribution comes with many security tools already installed and ready to use so that the tester can spend more time performing the penetration testing and finding security vulnerabilities in the systems. BackTrack not only contains the majority of the tools that we will discuss in this chapter, but it also contains tools for information gathering, network mapping, vulnerability identification, penetration testing, privilege escalations, Voice over IP (VoIP) and wireless analysis, and digital forensics. All you need to get started is to download the International Organization for Standardization (ISO) image and burn it to a CD.
Logging
Most wireless access points have the ability to log traffic and connections. It is important to consider logging requirements before an incident occurs. Being able to go back to a specific time when an event is thought to have occurred gives the investigator the ability to analyze and determine whether there was indeed a wireless attack on the network.
The logging on most access points does not provide the kind of granularity required for effective logging. You can set up a wireless IDS/IPS to monitor and log any suspicious wireless activity using wireless sensors. These sensors detect malformed wireless packets and log the data for forensic analysis later.
Investigating wireless attacks is difficult due to the nature of the technology. This is exactly the reason attackers like to use this method to gain access to corporate networks. The best solution is to configure your wireless network securely to ensure that hackers will not be able to gain access easily. If a wireless incident does occur, an investigator can use the same tools the attacker used to determine how the attack was done and decide how much information may have been exposed. Proactively reviewing event logs on servers and network devices is always a good step toward identifying attacks early and handling them appropriately.
Summary
The sheer number of ways that a hacker can intrude or attack a network can be overwhelming. As soon as one security “hole” is plugged, dozens more are discovered or created. Some of these methods are so subtle that no one might ever realize that the network's security has been compromised. Others are so blatant that everyone will know instantly.
Attackers range from charmers with lots of “people skills” who can persuade legitimate users to provide the credentials they need to break into the system, to technical “whiz kids” who can exploit the characteristics of network protocols, applications, and operating systems, and technically unsophisticated hacker “wannabes” who use scripts, GUI tools, and Web sites created by others to carry out their attacks. The attacks themselves can range from denials of service that disrupt communications on the entire network, to “benign” viruses that do no more than pop up an annoying message window. In many cases, the goal of an attack is to plant a “back door” in the system that will allow the hacker to reenter later at will.
The state of hacking has reached the point at which anyone and everyone who wants to launch an attack can do so, and the incidence of “drive-by hacking” has increased with the advent of easy-to-use hacking tools. To protect systems, network administrators and management should use the same methods used by hackers to identify weaknesses in their networks. This can include using tools installed on individual computers, and using various tools designed to hack cabled and wireless networks.
Frequently Asked Questions
A Many of these tools have legitimate uses. It is especially important for network administrators and security consultants to be able to use scanning tools to determine where the vulnerabilities are in their own or their clients’ networks to take the appropriate steps to “harden” the systems. After all, if scanning tools were outlawed, only outlaws would have scanning tools. These utilities—like many other things—can be used either offensively or defensively. Keystroke logging devices and other “spyware” can be useful in situations in which monitoring users’ activities is legal and appropriate—for example, for employers to keep tabs on what employees are doing on the network (especially when the employer could be held liable for those activities) and for parents to exercise control over children's online activities.
Q If a company has a good firewall installed, won't that protect the company from all these attacks?
A No. Firewall products are very useful for controlling what comes into or goes out of a network. But a firewall is like a computer (in many cases, a firewall is a specialized computer); it does only what the person who configures it tells it to do. Some types of attacks are recognized and can be stopped by firewalls, but others exploit the characteristics of the protocols commonly used for legitimate network communications, and packets might appear to be nothing more than a benign bit of data destined for a computer on the internal network. Trojans, viruses, and worms piggyback into the network as e-mail attachments or through remote file sharing. Firewalls won't catch them, but a good AV program, frequently updated and set to scan all incoming e-mail, might be able to do so. Many companies seem to operate under the assumption that installing a firewall is akin to invoking a magic spell that casts a force field of protection around their networks, rendering them completely immune to attack. Even the best firewall won't protect against social engineering attacks, nor will it do any good against internal attackers who have physical access to the network. Studies have shown that a large number of network-related crimes are actually “inside jobs.” In Chapter 12, you'll learn in detail how firewalls work, which will make it easier to understand why they are not the “cure-all” solution to network security that they're sometimes made out to be.
Q I think I understand the differences between a virus, a Trojan, and a worm. But what are all these other types of viruses I hear about: stealth viruses, polymorphic viruses, armored viruses, and cavity viruses?
A Stealth viruses are able to conceal the changes they make to files, boot records, and the like from AV programs. They do so by forging the results of a program's attempt to read the infected files. A polymorphic virus makes copies of itself to spread, like other viruses, but the copies are not exactly like the original. The virus “morphs” into something slightly different in an effort to avoid detection by AV software that might not have definitions for all the variations. Viruses can use a “mutation engine” to create these variations of themselves. An armored virus uses a technique that makes it difficult to understand the virus code. A cavity virus is able to overwrite part of the infected (host) file while not increasing the length of the file, which would be a tip-off that a virus had infected the file.
A The Internet has made it possible for anyone who is curious to become a viable threat when it comes to hacking, no matter where he or she lives or how much computer knowledge he or she has. Long gone are the days when a hacker would have to code an application from scratch to exploit vulnerabilities. Now, it is as simple as downloading the application and following instructions. BackTrack is a security operating system distribution that provides many of the tools discussed in this book, and is available free of charge. These days, the tools that security professionals use to test systems for vulnerabilities are often the same ones hackers use for malicious intent.
Q How do I detect whether a hacker has associated to my wireless access point?
A The first step is to look at the management interface and determine whether any machines look unfamiliar. Most management consoles will provide the client MAC address and computer name. Because this information can be spoofed, it should not be considered 100 percent reliable. Instability in the network may be another indication that an attacker is attempting to capture corporate data. The best solution is to implement an IDS/IPS. This system would monitor the network and search for suspicious network traffic, providing alerts to security and system administrators when an alarm is raised.
Q Are wireless networks safe?
A No network solution is 100 percent safe, but by taking proper precautions and using strong encryption techniques, you will be able to deter the majority of attacks. If wireless security is a top priority, investing in an IDS/IPS that is designed for wireless networks will provide the highest level of security. A wireless IPS can actually intercept and suppress wireless attacks in the air, preventing many of the most common attacks from reaching your access points. It can also detect rogue access points and provide wireless packet forensic analysis.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
