Classifying Assets
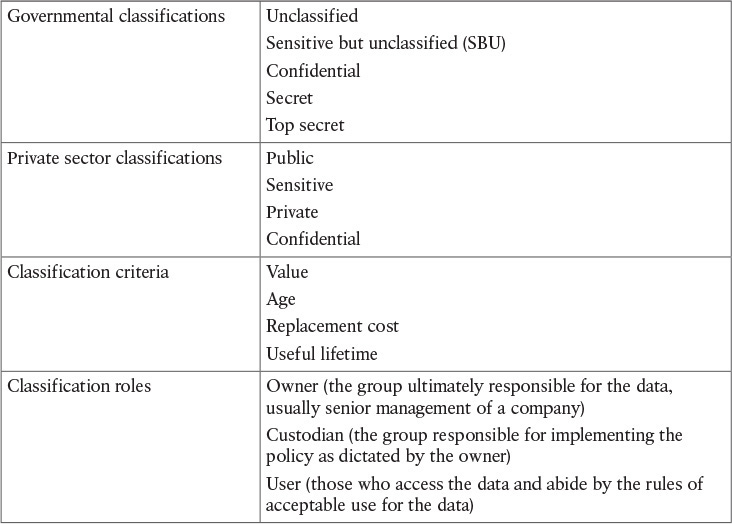
One reason to classify an asset is so that you can take specific action, based on policy, with regard to assets in a given class. Consider, for example, virtual private networks (VPN). We classify (that is, identify) the traffic that should be sent over a VPN tunnel. By classifying data and labeling it (such as labeling “top secret” data on a hard disk), we can then focus the appropriate amount of protection or security on that data: more security for top secret data than for unclassified data, for instance. The benefit is that when new data is put into the system, you can classify it as confidential or secret and so on and it will then receive the same level of protection that you set up for that type of data. Table 1-3 lists some common asset classification categories.
Table 1-4 describes the four classification levels used within the Traffic Light Protocol (TLP). The TLP is a set of designations developed by the US-CERT division to ensure that sensitive information is shared with the correct audience. It employs four colors to indicate different degrees of sensitivity and the corresponding sharing considerations to be applied by the recipients. The CERT division, part of the Software Engineering Institute and based at Carnegie Mellon University (Pittsburgh, Pennsylvania), is a worldwide respected authority in the field of network security and cyber security.