The Goal of IPsec
To best understand how IPsec operates, let’s take a look at a simple topology that we can use as a framework for this entire chapter, shown here in Figure 6-1.
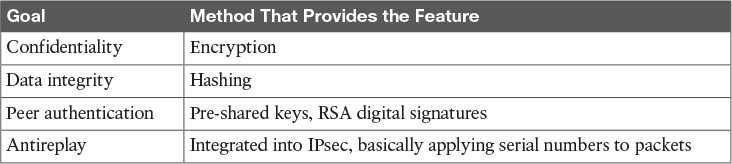
IPsec has four fundamental goals, as shown in Table 6-2.
The goals can be described as follows:
![]() Confidentiality: Provided through encryption changing clear text into cipher text.b
Confidentiality: Provided through encryption changing clear text into cipher text.b
![]() Data integrity: Provided through hashing and/or through Hashed Message Authentication Code (HMAC) to verify that data has not been manipulated during its transit across the network.
Data integrity: Provided through hashing and/or through Hashed Message Authentication Code (HMAC) to verify that data has not been manipulated during its transit across the network.
![]() Authentication: Provided through authenticating the VPN peers near the beginning of a VPN session using pre-shared keys (PSK) or digital signatures (leveraging digital certificates). Authentication can also be done continuously through the use of an HMAC, which includes a secret known only to two ends of the VPN.
Authentication: Provided through authenticating the VPN peers near the beginning of a VPN session using pre-shared keys (PSK) or digital signatures (leveraging digital certificates). Authentication can also be done continuously through the use of an HMAC, which includes a secret known only to two ends of the VPN.
![]() Antireplay protection: When VPNs are established, the peers can sequentially number the packets, and if a packet is attempted to be replayed again (perhaps by an attacker), the packet will not be accepted because the VPN device believes it has already processed that packet.
Antireplay protection: When VPNs are established, the peers can sequentially number the packets, and if a packet is attempted to be replayed again (perhaps by an attacker), the packet will not be accepted because the VPN device believes it has already processed that packet.
From our topology, we could decide that any traffic from the 10.0.0.0 network on the far left that needs to go to the 172.16.0.0 network on the far right should first be encrypted by R1, which would then send the protected packets over the Internet until they reach R2. The cloud between R1 and R2 represents an untrusted network, such as the Internet. R2 then decrypts each packet and sends the traffic on to its final destination, which may be a PC or server on the 172.16.0.0 network. The protected packets could be encrypted, hashed, and kept track of to provide the four major benefits previously listed.