Working with NetShell
NetShell, also known as netsh, is an indispensable command-line utility for both administrators and developers. Although netsh is primarily aimed at administrators because it allows them to administer network services, it is equally useful to a developer. To start netsh, open a command prompt, and type netsh.
NOTE
NetShell is available only when you have P2P networking option installed in Windows XP. Although NetShell is installed by default on Windows Vista, you need to allow that as an exception in the firewall for it to work.
The commands in netsh work with the concept of a "context" that determines the networking aspect within which you want to operate and accumulates various possible commands in that context. In most situations, you would switch to some context for the specific operation in which you are interested. Contexts can have subcontexts, which in turn can have further subcontexts, forming a tree-like hierarchy. Figure 12-6 shows how we switch the context to P2P ![]() PNRP
PNRP ![]() Cloud.
Cloud.
netsh context
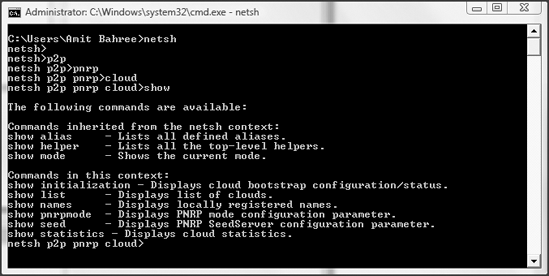
The commands you enter in netsh factor into the context on which you are working. For example, the command show entered (as shown in Figure 12-6) knows the context is cloud within a PNRP network and shows the commands for that context. You can switch from one context to another at any time.
Listing Clouds
If you want to see the clouds to which you are currently connected, then you will use the show list command, as shown in Figure 12-7. In this example, you can see two clouds, where one of those clouds was synchronizing, which later you can see has finished synchronizing.
Listing of clouds

To see the configuration and status of the cloud, you use show initialization (or the short form show init). If a computer is connected to the Internet, then it is part of the global cloud called Global_. If a cloud is connected to one or two LANs, then individual clouds are available for each network adapter (or link). In Listing 12-13, you can see two clouds called Global_ and LinkLocal_ff00::%8/8.
Example. Cloud Listing
Scope Id Addr State Name
----- ----- ----- ---------------- -----
1 0 1 Active Global_
Synchronize server: pnrpv2.ipv6.microsoft.com;pnrpv21.ipv6.microsoft.com
Use Server: Used
Use SSDP: No addresses
Use Persisted cache: No addresses
Cloud Configured Mode: Auto
Cloud Operational Mode: Full Participant
Scope Id Addr State Name
----- ----- ----- ---------------- -----
3 8 1 Alone LinkLocal_ff00::%8/8Synchronize server: Use Server: Disabled Use SSDP: No addresses Use Persisted cache: No addresses Cloud Configured Mode: Auto Cloud Operational Mode: Full Participant |
Scope, as the name suggests, represents the scope of the cloud and essentially shows the PNRPCLOUDINFO data structure that is part of the P2P SDK. The following list defines each of the columns in the previous data:
Scope:
This is the scope of the cloud and can be one of the four values shown in Table 12-1 (in the next section).
Id:
This represents the unique identifier for that cloud.
State:
This represents the state of the cloud and is represented by the PNRP_CLOUD_STATE structure in the SDK. This can be one of the seven values shown in Table 12-2 (in the next section).
Synchronize Server:
This represents the seed server used.
Use Server:
If a caching server was used to load the current state of the cloud, then this displays the DNS name of that server.
Use SSDP:
Simple Service Discovery Protocol (SSDP) is the protocol used to locate nearby nodes. You can use this to identify neighboring nodes if a seed server is not available.
Use Persisted cache:
This represents any previous cached entries loaded.
Clouds Scopes
The scope of a cloud can be one of the four values shown in Table 12-1.
| Value | Description |
|---|---|
| 0 | The cloud can be in any scope (represented by PNRP_SCOPE_ANY). |
| 1 | The cloud is a global scope (represented by PNRP _GLOBAL_ SCOPE). |
| 2 | The cloud is a site-local scope (represented by PNRP_SITE_LOCAL_SCOPE). |
| 3 | The cloud is a link local scope (represented by PNRP_LINK_LOCAL_SCOPE). |
The state of a cloud can be one of the seven values shown in Table 12-2.
| Value | Description |
|---|---|
| Virtual | The cloud is not yet initialized. |
| Synchronizing | The cloud is in the process of being initialized but is not active yet. |
| Active | The cloud is active. |
| Dead | The cloud has lost its connection to the network but was initialized. |
| Active | The cloud is active. |
| Disabled | The cloud is disabled in the registry. |
| No Net | The cloud has lost its connection to the network but was active. |
| Alone | The cloud is in stand-alone mode. |
Listing Peers in a Cloud
To see the locally registered nodes in a cloud, use the command show names in netsh. In Listing 12-14, you can have two peers identified by P2P Name connected to the cloud. Note the exact list of peers you see will of course be different from the ones shown here. If you have the QuickReturnTraderChat application running from earlier in the chapter, then you should see that.
Example. Peer Listing
P2P Name: 0.quickreturntraderchat
Identity: 2460f44f457b670116f55709f3e6324dd12ad70e.PnrpProtocolV2
Comment: a?????????
PNRP ID: cf284a913c76d8289f16c4fefbe18b7a.5bcca4c6a1090f379d15b0f12fc89b08
State: OK
IP Addresses: 192.168.1.73:11989 tcp
[2001:0000:4136:e37a:2847:1735:a83d:dc55]:11989 tcp
P2P Name: 0.78873591048
Identity: 2460f44f457b670116f55709f3e6324dd12ad70e.PnrpProtocolV2
Comment: Local Machine Id
PNRP ID: ad1d55aa343d35df9d118343e3c3de09.7700660055004400f956
ced74b6beb3cState: OK |
The following list defines each of the columns in the previous data:
P2P Name:
This is the name of the peer connected to the cloud. The first peer in Listing 12-14, called 0.quickreturntraderchat, is the QuickReturnTraderChat application discussed earlier in the chapter.
Identity:
As the name suggests, this represents the identities. Note that the identities of both peers are the same. This is because these peers are unsecure and the default identity is used for them.
PNRP ID:
This represents the corresponding 256-bit PNRP ID.
IP Addresses:
This represents the endpoints (including the ports) associated with this peer.
Cloud Statistics
To see the cloud statistics, enter the command show statistics (or the abbreviated show stat will also work) in netsh. This will display the statistics for all the active clouds. For example, Listing 12-15 lists statistics for the global cloud. Although most of the entries are self-explanatory, the IP Addresses column is a list of the addresses that is used to connect to the cloud.
Example. Statistics
IP Addresses: [2001:0000:4136:e37a:2847:1735:a83d:dc55]:3540 Number of cache entries: 34 Estimated cloud size: 142 Number of registered names: 3 Throttled resolves: 0 Throttled solicits: 0 Throttled floods: 0 Throttled repairs: 0 |
There are more commands within the cloud context; we discussed only the more important ones to give you a basic understanding. We encourage you to use the documentation and SDK to explore other commands in netsh.
Working with Peers
To switch to the peer context from within PNRP, just type peer in netsh. The peer's context, as the name suggests, allows you to work with peers and gives you the ability to add, delete, and enumerate entries, among other things. We will not be covering all the commands—just a couple of the more interesting ones. As you know, before one peer can talk to another peer, it needs to resolve that peer. To do this with netsh, you use the resolve command—passing it the peer name. In this example, if you try to resolve the peer 0.quickreturntraderchat, you get the result shown in Listing 12-16.
Example. Peer Resolution
netsh p2p pnrp peer>resolve 0.quickreturntraderchat
Resolve started...
Found:
Comment: aD????????
Addresses: [fe80:0000:0000:0000:79ae:4fe7:e034:eac7]%8:28365
Extended payload (binary):
Comment: aD????????
Addresses: [fe80:0000:0000:0000:79ae:4fe7:e034:eac7]%8:28136Extended payload (binary):
Comment: aD????????
Addresses: 169.254.2.2:28365
192.168.1.73:28365
[2001:0000:4136:e37a:2847:1735:a83d:dc55]%0:28365
Extended payload (binary): |
We have two instances of QuickReturnTraderChat running, which you can see in the previous example. We also have two network cards, one of which is connected to the Internet and the other of which is on an internal network. The first network adapter (which is connected to the Internet connection) has the IP address of 192.168.1.73 (this is NATed of course), and the local only is 169.254.2.2. Both are listening on port 28365.
The other command of interest is traceroute, which resolved a peer with path tracing. If the name is registered, then the result is quite similar to the resolve command used earlier, as shown in Listing 12-17.
Example. Known Peer Traceroute
netsh p2p pnrp peer>traceroute 0.quickreturntraderchat Global_
Resolve started...
Found:
Addresses: 169.254.2.2:28365 tcp
192.168.1.73:28365 tcp
[2001:0000:4136:e37a:2847:1735:a83d:dc55]%0:28365
tcp
Extended payload (string):
Extended payload (binary):
Resolve Path:
[2001:0000:4136:e37a:2847:1735:a83d:dc55]:3540, (0), (0)
Accepted
[2001:0000:4136:e37a:2847:1735:a83d:dc55]:3540, (0), (0)
Accepted Final Inquire |
However, on the other hand, if the peer is not registered, then you see more interesting behavior, as shown in Listing 12-18. Note an invalid name (0.quickreturntraderchatwedontkow) was provided to mimic this behavior. Also, the listing has been abbreviated for clarity. The exact number of hops would vary on the size of your cloud.
Example. Unknown Peer Traceroute
netsh p2p pnrp peer>traceroute 0.quickreturntraderchatwedontkow Global_
Resolve started...
Not Found.
Resolve Path:
[2001:0000:4136:e37a:2847:1735:a83d:dc55]:3540, (0), (0)
Accepted
[2001:0000:4136:e37e:140b:26c5:affa:3034]:3540, (8), (31)
Rejected (Dead end)[2001:0000:4136:e37e:244b:1e65:abdb:f294]:3540, (7), (140)
Rejected (Dead end)
[2001:0000:4136:e37e:1c75:1b9a:bef2:f5a3]:3540, (4), (312)
Accepted Suspicious
[2001:0000:4136:e37e:0c31:07f8:5351:cf06]:3540, (4), (2000)
Rejected (Unreachable)
[2001:0000:4136:e37e:1c75:1b9a:bef2:f5a3]:3540, (4), (125)
Rejected (Dead end)
[2001:0000:4136:e37a:384f:1905:bde1:91be]:3540, (4), (297)
Rejected (Dead end)
[2001:0000:4136:e378:1cb4:2170:a795:ebd9]:3540, (3), (78)
Rejected (Dead end)
[2001:0000:4136:e37a:0c25:34ef:e7ef:9e09]:3540, (2), (203)
Accepted |
