As we continue our pause from strict no-tech hacking, we’ll cover another low-tech skill: peer-to-peer (P2P) hacking. In keeping with the spirit of no-tech, let’s assume a guy has no budget, no commercial hacking software, no support from organized crime and no fancy gear. In fact, let’s even take away Google. With all those restrictions, is this guy still a threat to you? Have a look at this chapter and judge for yourself.
Understanding P2P Hacking
A peer-to peer (P2P) network is composed of a number of clients (called peers) who want to share files or data. Most often, peer-to-peer networks carry audio, video or program files shared by users who join the network. The workings of a P2P network are beyond the scope of this book, but for our purposes, let’s just say that P2P is one of the most common file sharing services in existence. In order to join a P2P network, you simply download a P2P client (such as Acquisition for the Mac, shown below), run it and begin searching for files to download.
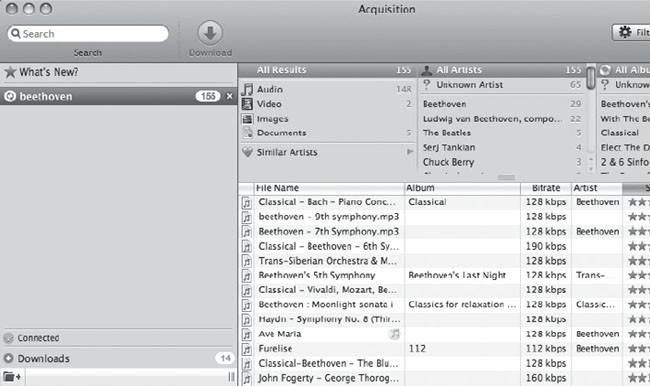
A search for Beethoven, like the one above “magically” returns a list of files other P2P users have shared that contain the word Beethoven. Results are typically sorted by popularity. In the example above, the top three results include a piano concerto by Bach (mistakenly listed as being by Beethoven), and Beethoven’s 7th and 9th symphonies. This brings up an interesting point—shared files on P2P networks are not always what they appear to be. A Bach concerto listed as being performed by Beethoven is a fairly benign example, but since any user can share any kind of file, the concerto could just as easily be anything: a movie about mayo, a picture of a pickle, or a file containing a computer virus. A malicious user could easily share any kind of nasty file. B the malicious files don’t interest me as much as the files shared accidentally.
As no-tech hackers already know, there are thousands of Internet users who have downloaded and installed P2P software and have accidentally shared sensitive files.
Gaining access to these files is as easy as installing a P2P client and submitting creative searches. In this chapter, we’ll take a look at some of the files I’ve found floating around various peer-to-peer networks.
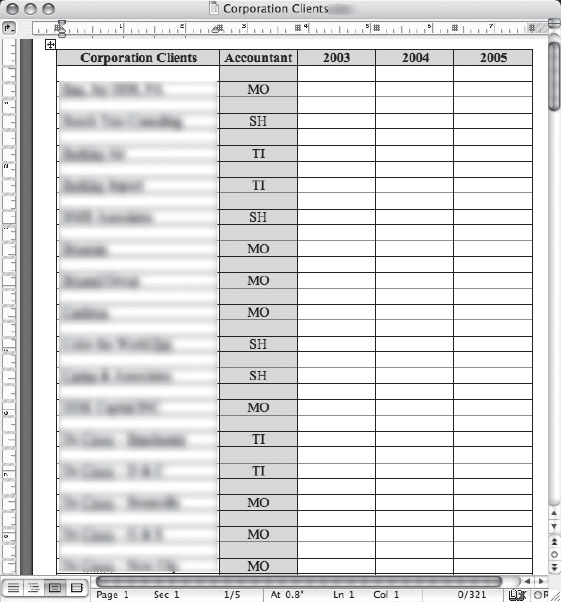
We’ll start with some basics and work our way up to some really interesting stuff. The next photo shows a relatively simple-looking Word document that lists a company’s corporate clients.
The quality of this next photo is awful, but I’ll present it as I found it. I think it’s a screen printout that was scanned in as an image. Hopefully it’s not what it looks like—a photo that was printed in a newspaper.
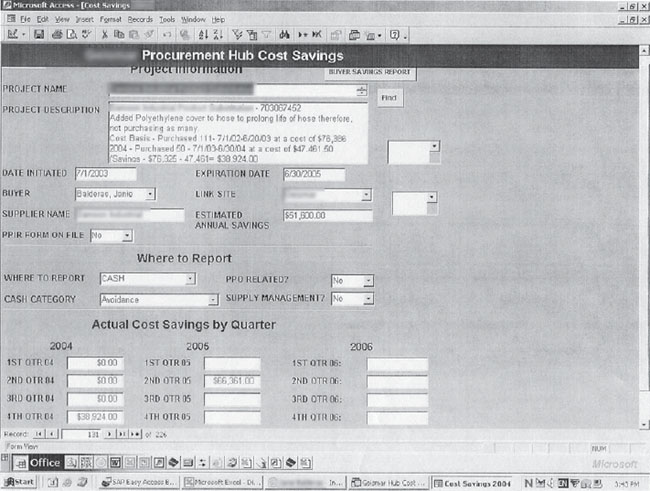
However the photo came into being, it reveals an awful lot of information. The task bar at the bottom is a shoulder surfer’s dream, but the Access database screen is a goldmine of information. The screen shows a cost savings report for a large company that lists very specific details about a project, including expenses and annual cost savings. The information is extremely dated, but based on the recognizable name of the company; someone would certainly be interested in more info just like it.
Once you find an interesting document, it’s simple to find more from the same computer. Most P2P clients allow you to browse all the shared files on a P2P user’s computer. If an attacker finds one marginally sensitive document, he’ll almost certainly browse the machine that shared the file to find more. Although his search will only be limited to the files that user is sharing, if the user’s sharing one sensitive document, he’s almost certainly sharing others.
The next photo shows a customer invoice.

This invoice is dated as well, but it reveals client information and pricing data. The most interesting thing to me is that the invoice lists item descriptions, which seem to layout a very high-end security system. It lists video servers (capable of supporting up to forty cameras), video encoders, power supplies and more. It seems ironic that the invoice for this high-tech security system would be sitting out on a P2P network for the world to see.
Here’s another interesting document: a cellular phone bill.

I don’t personally think I’d want to share this info with the world. The 24-page document lists the customer’s name, address and phone number and goes on to list an entire month’s cellular phone history. It lists every call placed and every call received. It goes on to list the time, duration and charge of a month’s worth of calls. If a high-tech hacker were to try to gain access to this data electronically, it would be a difficult task. But for a no-tech hacker, it only takes a quick P2P hacking session or a round of dumpster diving.
What If a Hacker Is after Me?
It’s scary to think about a hacker targeting your personal information, but understand that P2P hacking is not about targeting specific individuals. P2P hacking is about finding interesting information based on specific keywords. If a hacker’s after you, he or she is probably not going to log into a P2P client in search of your information because this makes the assumption that you’re running a P2P client and that you have shared personal data there. Both of these are rather wild assumptions. So if you do run P2P software, make sure you know exactly what it is you are sharing, and then focus your attention on making sure your personal firewall, and anti-virus/spyware/adware software is current and correctly configured.
Word documents abound on P2P networks, and may are great sources of personal information. The document below lists more info than most.

The name, date of birth and social security number are interesting bits of information, but this document reveals insurance policy information as well. This all pales in comparison to financial information. Take a look at the document below.
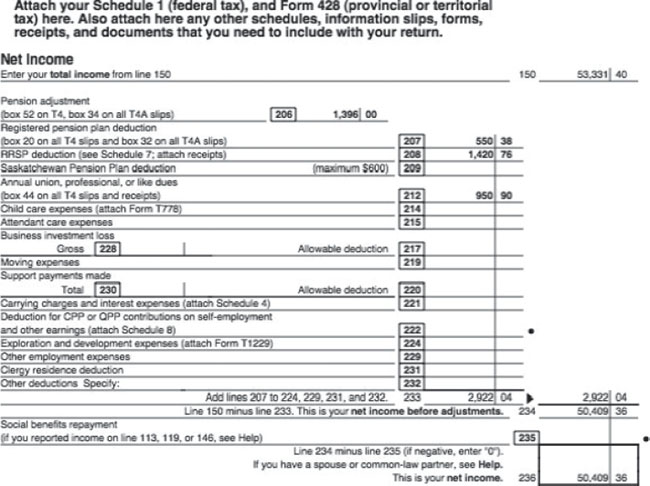
This tax document was most likely part of a computer-based tax preparation program. It provides a summary of this individual’s financial information. Even more financial information can be found in documents like the one below, which really caught my eye because of the words direct debit in the header.
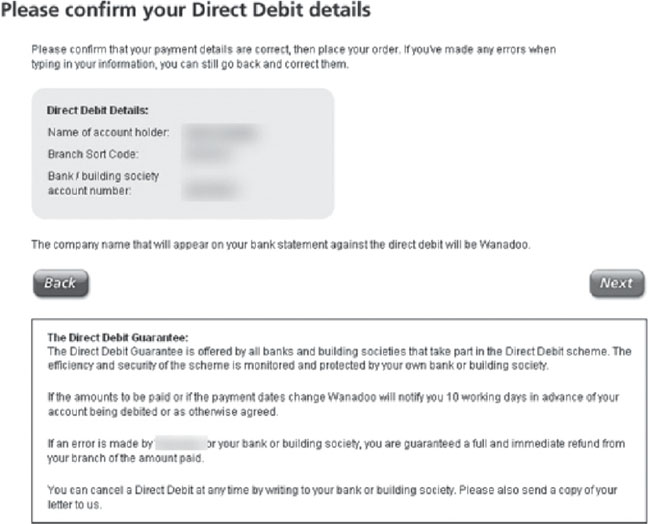
The owner of this document first viewed it in his or her browser, and then probably saved it as a file on the local hard drive. Unfortunately, it was saved into a directory that peer-to-peer software used as a share folder, and the saved document was shared to the world. Unfortunately for this user, his name, bank account number and branch code are now a matter of public record.
Other bank information is easy to come by also as shown in the next photo.

This multi-page document lists account information including account number, balances, charges and withdrawals. Page after page of the document are included in the report as shown below.

This is great stuff for a no-tech hacker, but it only describes a single account. Documents like the one below list information about multiple accounts. Now we’re getting into some really crazy stuff.

This is a full-blown credit report. It lists account names, bank information, balances, loans and more—just about every bit of financial information a person can accumulate. Identity thieves need much less information than this to completely take over a person’s identity. Unfortunately, as the next capture shows, there is no shortage of this kind of information available.

I could list hundreds of these things, but let’s take a look at one more. Check out the next report.

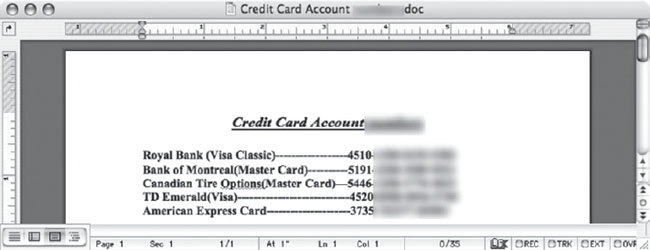
Other simpler documents, like the one below, just list the sensitive bits. It’s like credit-report-concentrate (no pulp).
I could go on and on, but there’s really no need. There’s no shortage of sensitive information on P2P networks, and it doesn’t take much skill at all to find it. Let’s take a look at a real-world P2P hacking session.
Real World P2P Hacking: The Case of the Naughty Chiropractor
When I found the document below, I distinctly remember thinking “how cute.” It’s not really an interesting document—it simply welcomes new chiropractic patients, and goes on a bit about how important muscles and spines and stuff really are.
But after thinking about it a moment, I began to wonder if I had stumbled on to a doctor’s home PC. I right-clicked the file in my P2P client, and selected Browse to see other files on that computer. The results are shown in the next photo.

I clicked the Text link to see text-based files, such as Microsoft Word documents, and as the results scrolled down the screen, I could hardly believe my eyes. I saw file after file of records, private patient data, and meds (medication) requests. I was looking at private patient data. I was scrolling through a list of documents that contained some extremely sensitive patient medical data, and there was a good chance that others in the P2P network had already downloaded these documents. There was no telling where in the world this data had already traveled. This info made me realize that this probably wasn’t a personal machine—it was most likely the machine the doctor used for business. I decided to browse the machine a bit more. I clicked the Movies link at the top of the P2P screen and glanced through the results, shown in the next screen.
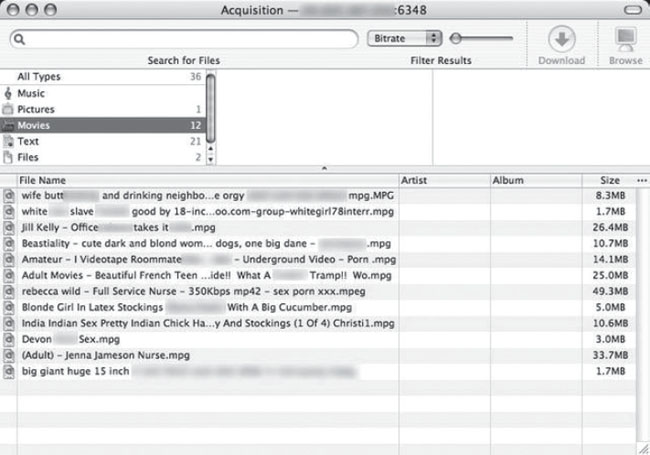
The names of the videos were so foul that I instinctively looked over my shoulder to see if anyone was seeing what I was seeing. Most of the pornographic videos centered on sexy nurses, teenage girls and women in stockings. Some of the video titles were so disgusting I had to blur out the majority of the title to even present the photo. The most disturbing videos described sex acts with animals and mentioned terms like “white slave.” The videos were nasty enough, but then I remembered this was most likely a doctor’s machine. If this was the doctor’s machine, I wondered if his patients had any idea that he was not only completely irresponsible with their records, but that he was a complete sleaze to boot. I know I wouldn’t want a doctor that collected this kind of stuff touching anyone I cared about.
I flipped back to the Text list, and read the name of a file that did not seem sensitive in nature. I downloaded the file, shown in the next photo.

The document wasn’t meant to be funny, but it made me laugh nonetheless. It was a non-disclosure agreement that the doctor’s employees were to sign and date, agreeing that they would not release patient information without a signed consent. It went on to state that employees had certain moral and professional obligations to protect patient confidentiality, and that there are penalties for the unauthorized release of patient information. I couldn’t believe that this document was sitting in the same folder as private patient data and hot nurse porn. But no-tech hackers see all sorts of interesting things.
