Chapter 6 Google Hacking Showcase
A decent no-tech hacker can accumulate a library of significant data just by observing the world around him. But often that data is completely useless on its own. When it comes time to turn data into information, Hollywood tells us that the hacker will have thirty-two plasma screens (divisible by eight, naturally) in his black-walled, red-lighted room that would put NORAD’s computer center to shame. In real life, a hacker doesn’t even need his own computer to do the necessary research. If he can make it to a public library, Kinko’s or Internet cafe, he can use Google to process all that data into something useful. Other times, a hacker will just use Google to troll for targets and sensitive information.
Reprinted from my book Google Hacking for Penetration Testers, Volume Two, this chapter shows what hackers are capable of when armed only with a search engine and a bit of ingenuity. Be warned though—this is not no-tech hacking, but rather what I’d call low-tech hacking. Still, Google Hacking is an indispensable tool in every no-tech hacker’s arsenal, and once you see the examples in this chapter, I think you’ll understand why.
Introduction to the Introduction
This chapter is reprinted from my book Google Hacking for Penetration Testers, Volume 2. Arguably the most well-known of no-tech hacking techniques among hackers in the know, Google hacking has become a standard weapon in every attacker’s arsenal. I’m generally not fond of reprints, but often it’s more important to give you the content rather than point you to it–and ask you to pay more hard-earned money for it. So with that in mind, I present this chapter, cobbled together from the now moderately famous Google Hacking book. Since this is a reprint, the format and style of this chapter does not match the rest of the book you now hold. I hope you understand. Enjoy. -Johnny
Introduction
A self-respecting Google hacker spends hours trolling the Internet for juicy stuff. Firing off search after search, they thrive on the thrill of finding clean, mean, streamlined queries and get a real rush from sharing those queries and trading screenshots of their findings. I know because I’ve seen it with my own eyes. As the founder of the Google Hacking Database (GHDB) and the Search engine hacking forums at http://johnny.ihackstuff.com, I am constantly amazed at what the Google hacking community comes up with. It turns out the rumors are true—creative Google searches can reveal medical, financial, proprietary and even classified information. Despite government edicts, regulation and protection acts such as HIPAA, Sarbanes-Oxley, and Graham-Leach-Bliley, and the constant barking of security watchdogs, this problem still persists. Stuff still makes it out onto the Web, and Google hackers snatch it right up.
In my quest to shine a spotlight on the threat, I began speaking on the topic of Google hacking at security conferences such as Black Hat and Defcon. In addition, I was approached to write my first book. After months of writing, I assumed our cause would finally catch the eye of the community at large and that change would be on the horizon. I just knew people would be talking about Google hacking and that awareness about the problem would increase.
Google Hacking, first edition, has made a difference. But nothing made waves like the “Google Hacking Showcase,” the fun part of my infamous Google hacking conference talks. The showcase wasn’t a big deal to me—it consisted of nothing more than screenshots of wild Google hacks I had witnessed. Borrowing from the pool of interesting Google queries I had created, along with scores of queries from the community; I snagged screenshots and presented them one at a time, making smarmy comments along the way. Every time I presented the showcase, I managed to whip the audience into a frenzy of laughter at the absurd effectiveness of a hacker armed only with a browser and a search engine. It was fun, and it was effective. People talked about those screenshots for months after each talk. They were, after all, the fruits of a Google hacker’s labor. Those photos represented the white-hot center of the Google hacking threat.
It made sense then to include the showcase in this edition of Google Hacking. In keeping with the original format of the showcase, this chapter will be heavy on photos and light on gab because the photos speak for themselves. Some of the screenshots in this chapter are dated, and some no longer exist on the web, but this is great news. It means that somewhere in the world, someone (perhaps inadvertently) graduated from the level of googledork and has taken a step closer to a better security posture.
Regardless, I left in many outdated photos as a stark reminder to those charged with protecting online resources. Those photos serve as proof that this threat is pervasive—it can happen to anyone, and history has shown that it has happened to just about everyone.
So without further ado, enjoy this print version of the Google Hacking Showcase, brought to you by myself and the contributions of the Google Hacking community.
Geek Stuff
This section is about computer stuff. It’s about technical stuff, the stuff of geeks. We will take a look at some of the more interesting technical finds uncovered by Google hackers. We’ll begin by looking at various utilities that really have no business being online, unless of course your goal is to aid hackers. Then we’ll look at open network devices and open applications, neither of which requires any real hacking to gain access to.
Utilities
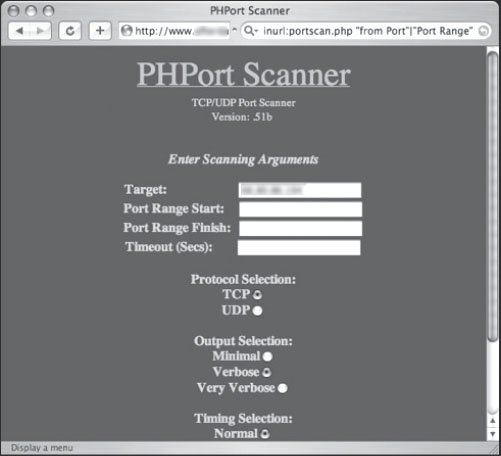
Any self-respecting hacker has a war chest of tools at his disposal, but the thing that’s interesting about the tools in this section is that they are online—they run on a web server and allow an attacker to effectively bounce his reconnaissance efforts off of that hosting web server. To make matters worse, these application-hosting servers were each located with clever Google queries. We’ll begin with the handy PHP script shown in Figure 6.1 which allows a web visitor to ping any target on the Internet. A ping isn’t necessarily a bad thing, but why offer the service to anonymous visitors?

Figure 6.1 Php-ping.cgi Provides Free Ping Bounces
Unlike the ping tool, the finger tool has been out of commission for quite a long time. This annoying service allowed attackers to query users on a UNIX machine, allowing enumeration of all sorts of information such as user connect times, home directory, full name and more. Enter the finger CGI script, an awkward attempt to “webify” this irritating service. As shown in Figure 6.2, a well-placed Google query locates installations of this script, providing web visitors with a finger client that allows them to query the service on remote machines.
Pings and finger lookups are relatively benign; most system administrators won’t even notice them traversing their networks. Port scans, on the other hand, are hardly ever considered benign, and a paranoid administrator (or piece of defense software) will take note of the source of a port scan. Although most modern port scanners provide options which allow for covert operation, a little Google hacking can go a long way. Figure 6.3 reveals a Google search submitted by Jimmy Neutron which locates sites that will allow a web visitor to portscan a target.
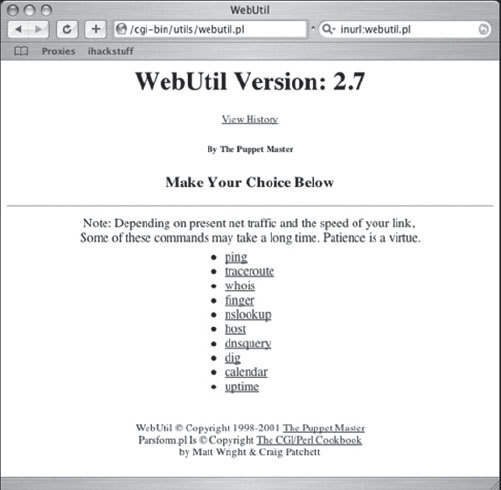
Remember, scans performed in this way will originate from the web server, not from the attacker. Even the most paranoid system administrator will struggle to trace a scan launched in this way. Of course, most attackers won’t stop at a portscan. They will most likely opt to continue probing the target with any number of network utilities which could reveal their true location. However, if an attacker locates a web page like the one shown in Figure 6.4 (submitted by Jimmy Neutron), he can channel various network probes through the WebUtil Perl script hosted on that remote server. Once again, the probes will appear to come from the web server, not from the attacker.
The web page listed in Figure 6.5 (submitted by Golfo) lists the name, address and device information for a school’s “student enrollment” systems. Clicking through the interface reveals more information about the architecture of the network, and the devices connected to it. Consolidated into one easy-to-read interface and located with a Google search, this page makes short work of an attacker’s reconnaissance run.
Open Network Devices
Why hack into a network server or device when you can just point and click your way into an open network device? Management devices, like the one submitted by Jimmy Neutron in Figure 6.6, often list all sorts of information about a variety of devices.

Figure 6.6 Open APC Management Device
When m00d submitted the query shown in Figure 6.7, I honestly didn’t think much of it. The SpeedStream router is a decidedly lightweight device installed by home users, but I was startled to find them sitting wide-open on the Internet. I personally like the button in the point-to-point summary listing. Who do you want to disconnect today?

Figure 6.7 Open SpeedStream DSL Router Allows Remote Disconnects
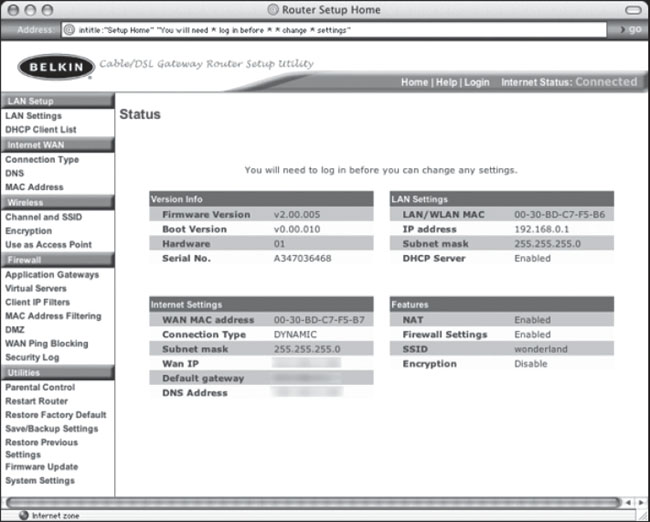
Belkin is a household name in home network gear. With their easy-to-use web-based administrative interfaces, it makes sense that eventually pages like the one in Figure 6.8 would get crawled by Google. Even without login credentials, this page reveals a ton of information that could be interesting to a potential attacker. I got a real laugh out of the Features section of the page. The firewall is enabled, but the wireless interface is wide open and unencrypted. As a hacker with a social conscience, my first instinct is to enable encryption on this access point—in an attempt to protect this poor home user from themselves.
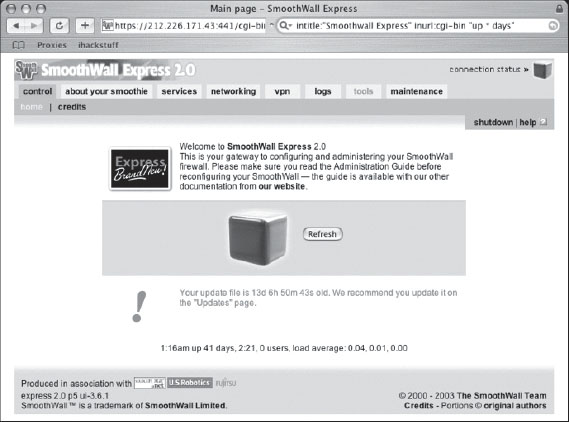
Milkman brings us the query shown in Figure 6.9, which digs up the configuration interface for Smoothwall personal firewalls. There’s something just wrong about Google hacking someone’s firewall.
As Jimmy Neutron reveals in the next two figures, even big-name gear like Cisco shows up in the recesses of Google’s cache every now and again. Although it’s not much to look at, the switch interface shown in Figure 6.10 leaves little to the imagination—all the configuration and diagnostic tools are listed right on the main page.

Figure 6.10 Open Cisco Switch
This second Cisco screenshot should look familiar to Cisco geeks. I don’t know why, but the Cisco nomenclature reminds me of a bad Hollywood flick. I can almost hear the grating voice of an over-synthesized computer beckoning, “Welcome to Level 15."

Figure 6.11 Welcome to Cisco Level 15
The search shown in Figure 6.12 (submitted by Murfie) locates interfaces for an Axis network print server. Most printer interfaces are really boring, but this one in particular piqued my interest. First, there’s the button named configuration wizard, which I’m pretty sure launches a configuration wizard. Then there’s the handy link labeled Print Jobs, which lists the print jobs. In case you haven’t already guessed, Google hacking sometimes leaves little to the imagination.

Figure 6.12 Axis Print Server with Obscure Buttonage
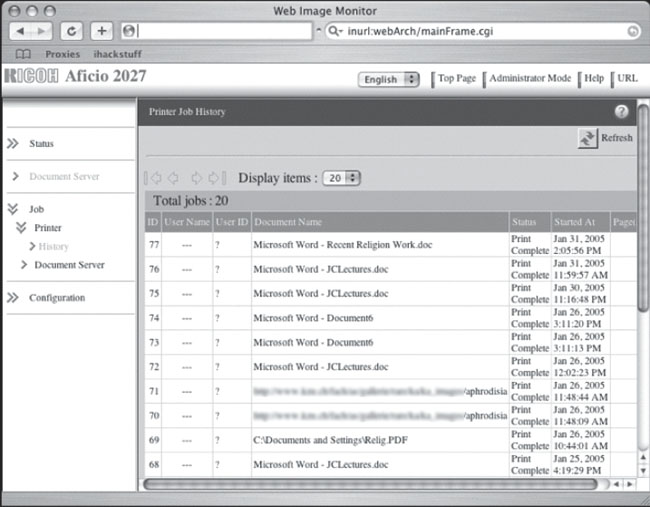
Printers aren’t entirely boring things. Consider the Web Image Monitor shown in Figure 6.13. I particularly like the document on Recent Religion Work. That’s quite an honorable pursuit, except when combined with the document about Aphrodisiacs. I really hope the two documents are unrelated. Then again, nothing surprises me these days.
CP has a way of finding Google hacks that make me laugh, and Figure 6.14 is no exception. Yes, this is the web-based interface to a municipal water fountain.
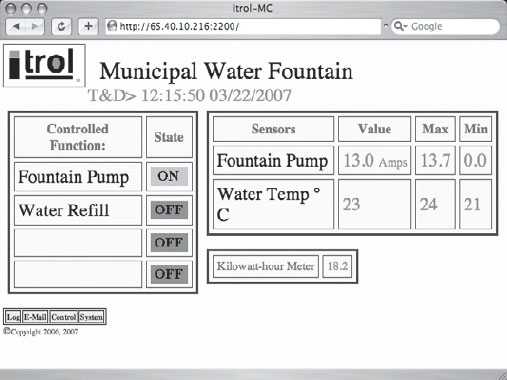
Figure 6.14 Hacking Water Fountains For Fun and Profit
After watching the water temperature fluctuate for a few intensely boring seconds, it’s only logical to click on the Control link to see if it’s possible to actually control the municipal water fountain. As Figure 6.15 reveals, yes it is possible to remotely control the municipal water fountain.

Figure 6.15 More Water Fountain Fun
One bit of advice though—if you happen to bump into one of these, be nice. Don’t go rerouting the power into the water storage system. I think that would definitely constitute an act of terrorism.
Moving along to a more traditional network fixture, consider the screenshot captured in Figure 6.16.
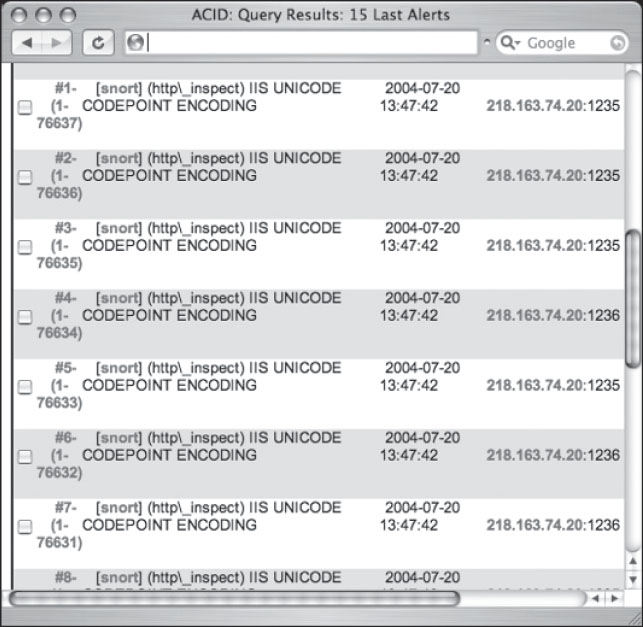
Now, I’ve been in the security business for a lot of years, and I’m not exactly brilliant in any one particular area of the industry. But I do know a little bit about a lot of different things, and one thing I know for sure is that security products are designed to protect stuff. It’s the way of things. But when I see something like the log shown in Figure 6.16, I get all confused. See, this is a web-based interfaced for the Snort intrusion detection system. The last time I checked, this data was supposed to be kept away from the eyes of an attacker, but I guess I missed an email or something. But I suppose there’s logic to this somewhere. Maybe if the attacker sees his screw-ups on a public webpage, he’ll be too ashamed to ever hack again, and he’ll go on to lead a normal productive life. Then again, maybe he and his hacker buddies will just get a good laugh out of his good fortune. It’s hard to tell.
Open Applications
Many mainstream web applications are relatively idiot-proof, designed for the point-and-click masses that know little about security. Even still, the Google hacking community has discovered hundreds of online apps that are wide open, just waiting for a point-and-click script kiddy to come along and own them. The first in this section was submitted by Shadowsliv and is shown in Figure 6.17.

Figure 6.17 Tricky Pivot Hack Requires Five Correct Field Fills
The bad news is that if a hacker can figure out what to type in those confusing fields, he’ll have his very own Pivot web log. The good news is that most skilled attackers will leave this site alone, figuring that any software left this unprotected must be a honeypot. It’s really sad that hacking (not real hacking mind you) can be reduced to a point-and-click affair, but as Arrested’s search reveals in Figure 6.18, owning an entire website can be a relatively simple affair.
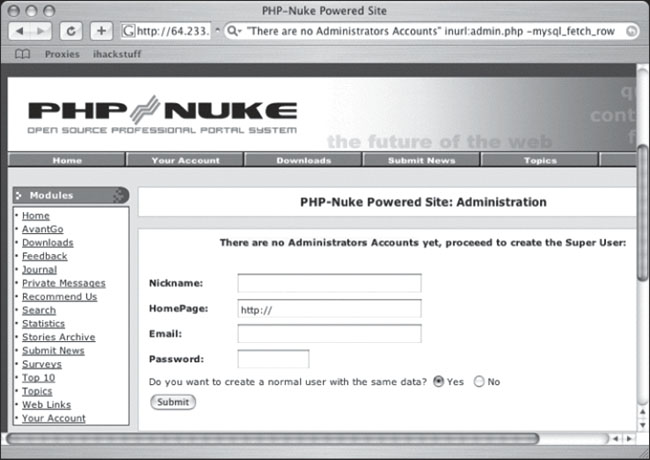
Sporting one less field than the open Pivot install, this configuration page will create a PHP-Nuke Administrator account, and allow any visitor to start uploading content to the page as if it were their own. Of course, this takes a bit of malicious intent on behalf of the web visitor. There’s no mistaking the fact that he or she is creating an Administrator account on a site that does not belong to them. However, the text of the page in Figure 6.19 is a bit more ambiguous.
The bold text in the middle of the page really cracks me up. I can just imagine somebody’s poor Grandma running into this page and reading it aloud. “For security reasons, the best idea is to create the Super User right NOW by clicking HERE.” I mean who in their right mind would avoid doing something that was for security reasons? For all Grandma knows, she may be saving the world from evil hackers … by hacking into some poor fool’s PHP-Nuke install.
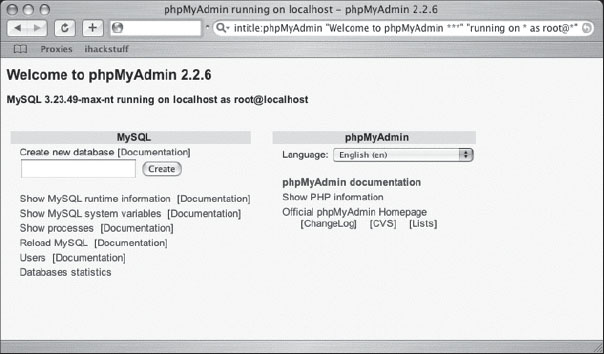
And as if owning a website isn’t cool enough, Figure 6.20 (submitted by Quadster) reveals a phpMyAdmin installation logged in as root, providing unfettered access to a MySQL database.
With a website install and an SQL database under his belt, it’s a natural progression for a Google hacker to want the ultimate control of a system. VNC installations provide remote control of a system’s keyboard and mouse. Figure 6.21, submitted by Lester, shows a query that locates RealVNC’s Java-based client.

Figure 6.21 Hack A VNC, Grab A Remote Keyboard
Locating a client is only part of the equation, however. An attacker will still need to know the address, port and (optional) password for a VNC server. As Figure 6.22 reveals, the Java client itself often provides two-thirds of that equation in a handy popup window.

Figure 6.22 VNC Options Handed Up with a Side of Fries
If the hacker really lucks out and stumbles on a server that’s not password protected, he’s faced with the daunting task of figuring out which of the four buttons to click in the above connection window. Here’s a hint for the script kiddie looking to make his way in the world: it’s not the Cancel button.
Of course running without a password is just plain silly. But passwords can be so difficult to remember and software vendors obviously realize this as evidenced by the password prompt shown in Figure 6.23.

Figure 6.23 Handy Password Reminder, In Case The Hacker Forgot
Posting the default username/password combination on a login popup is just craziness. Unfortunately it’s not an isolated event. Check out Figure 6.24, submitted by Jimmy Neutron. Can you guess the default password?
Graduating to the next level of hacker leetness requires a bit of work. Check out the user screen shown in Figure 6.25, which was submitted by Dan Kaminsky.

Figure 6.25 Welcome To Guest Access
If you look carefully, you’ll notice that the URL contains a special field called ADMIN, which is set to False. Think like a hacker for a moment and imagine how you might gain administrative access to the page. The spoiler is listed in Figure 6.26.

Figure 6.26 Admin Access through URL Tinkering
Check out the shiny new Exit Administrative Access button. By Changing the ADMIN field to True, the application drops us into Administrative access mode. Hacking really is hard, I promise.
Cameras
I’ve got to be honest and admit that like printer queries, I’m really sick of webcam queries. For a while there, every other addition to the GHDB was a webcam query. Still, some webcam finds are pretty interesting and worth mentioning in the showcase. I’ll start with a cell phone camera dump, submitted by Vipsta as shown in Figure 6.27.
Not only is this an interesting photo of some pretty serious-looking vehicular carnage, but the idea that Google trolls camera phone picture sites is interesting. Who knows what kind of blackmail fodder lurks in the world’s camera phones. Not that anyone would ever use that kind of information for sensationalistic or economically lucrative purposes. Ahem.
Moving on, check out the office-mounted open web camera submitted by Klouw as shown in Figure 6.28.

Figure 6.28 Remote Shoulder Surfing 101
This is really an interesting web cam. Not only does it reveal all the activity in the office, but it seems especially designed to allow remote shoulder surfing. Hackers used to have to get out of the house to participate in this classic sport. These days all they have to do is fire off a few Google searches.
Figure 6.29, submitted by Jimmy Neutron, shows the I.T. infrastructure of a tactical US nuclear submarine.

Figure 6.29 Not Really A Tactical US Nuclear Submarine
OK, so not really. It’s probably just a nuclear reactor or power grid control center or even a drug lord’s warehouse in Columbia (Maryland). Or maybe I’ve been reading too many Stealing The Network books. Either way, it’s a cool find none the less.
Figure 6.30, however (submitted by JBrashars) is unmistakable. It’s definitely a parking lot camera. I’m not sure why, exactly, a camera is pointed at a handicapped parking space, but my guess is that there have been reports of handicapped parking spot abuse. Imagine the joy of being the guard that gets to witness the CIO parking in the spot, leaping out of his convertible and running into the building. Those are the stories of security guard legends.
WarriorClown sent me the search used for the capture shown in Figure 6.31. It shows what appears to be a loading dock, and a field of white explosive containers.

Figure 6.31 Remote Exploding Container Fun
Although it looks pretty boring at first, this webcam is really a lot of fun. Check out the interesting button in the upper right of the capture. I’m pretty sure that clicking on that button fires a laser beam at the explosive white containers, which creates maximum carnage, but can only be done once – unless you set them to respawn, which will bring them back automatically. Oh, wait. That only works in Halo 3's Forge mode. OK, all these webcams are starting to make me loopy. In an attempt to get my imagination in check, I present pretty straightforward security camera view shown in Figure 6.32.
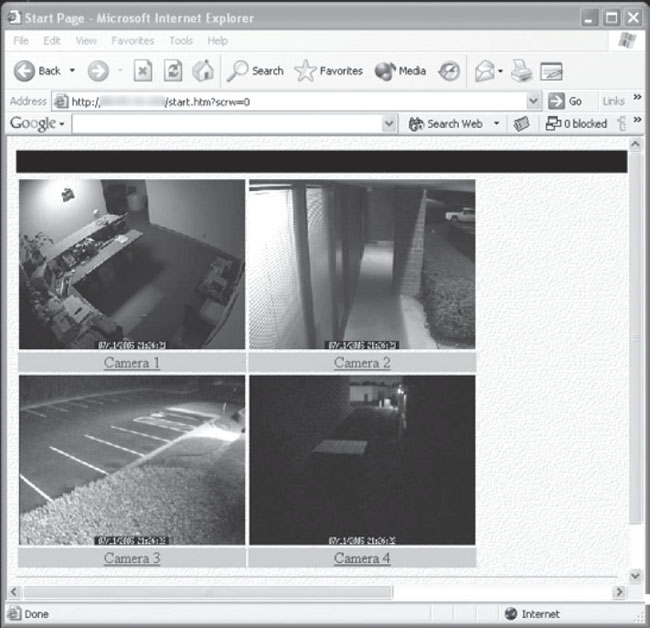
Figure 6.32 Open Web “Security” Cameras
I can’t be the only one that thinks it’s insane to put open security camera feeds on the Internet. Of course it happens in Hollywood movies all the time. It seems the first job for the hired hacker is to tap into the video surveillance feeds. But the movies make it look all complicated and technical. I’ve never once seen a Hollywood hacker use Google to hack the security system. Then again, that wouldn’t look nearly as cool as using fiber optic cameras, wire cutters and alligator clips.
Moving on, the search shown in Figure 6.33 (submitted by JBrashars) returns quite a few hits for open Everfocus EDSR applets.

Figure 6.33 EDSR Sounds Tame Enough
The Everfocus EDSR is a multi-channel digital video recording system with a web-based interface. It’s a decent surveillance product, and as such it is password protected by default, as shown in Figure 6.34.
Unfortunately, as revealed by an anonymous contributor, the factory-default administrative username and password provides access to many of these systems, as shown in Figure 6.35.
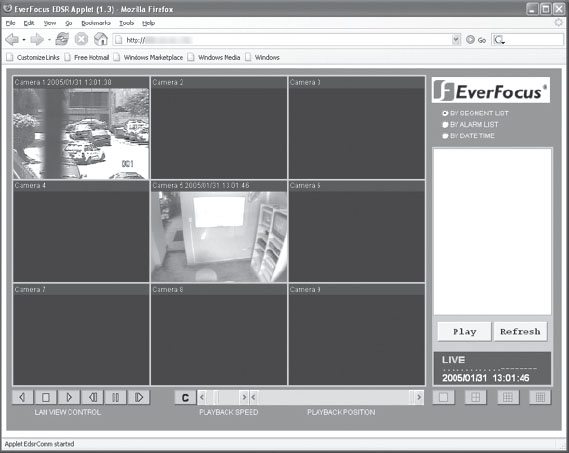
Figure 6.35 Welcome to Surveillance Central
Once inside, the EDSR applet provides access to multiple live video feeds and a historic record of any previously recorded activity. Again, just like the magic of Hollywood without all the hacker smarts.
The EDSR isn’t the only multi-channel video system that is targeted by Google hackers. As Murfie reveals, a search for I-catcher CCTV returns many systems like the one shown in Figure 6.36.
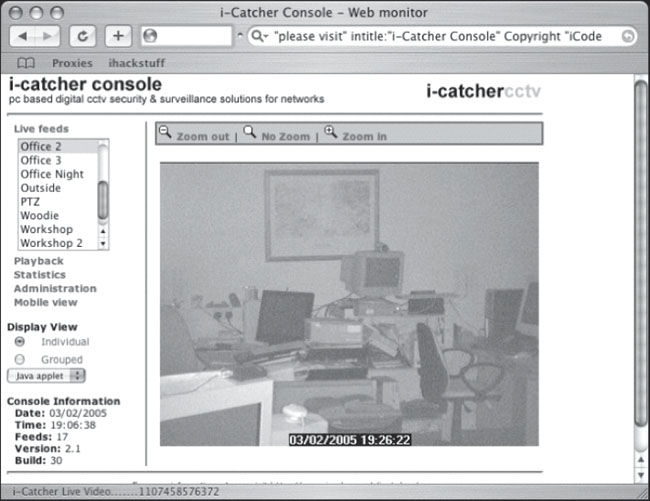
Figure 6.36 Housekeeper Needed. Apply Within
Although the interface may look simple, it provides access to multiple live camera views, including one called “Woodie” which I was personally afraid to click on.
These cameras are all interesting, but I’ve saved my favorite for last. Check out Figure 6.37.

Figure 6.37 Shoulder Surfing Meets Webcam Meets Password Stickers
This camera provides open access to web visitors. Located in a computer lab, the camera’s remote control capability allows anonymous visitors to peer around, panning and zooming to their hearts content. Not only does this allow for some great shoulder surfing, but the sticker in the above screen capture had me practically falling out of my chair. It lists a username and password for the lab’s online FTP server. Stickers listing usernames and passwords are bad enough, but I wonder whose bright idea it was to point an open webcam at them?
Telco Gear
I’ve never been much of a phreaker (phone hacker), but thanks to the depth of Google’s searching capabilities, I wouldn’t need to have much experience to get into this shady line of work. As JBrashar’s search reveals in Figure 6.38, the surge of Voice over IP (VOIP) service has resulted in a host of new web-based phone interfaces.

Figure 6.38 Google Hacking Residential Phone Systems
It’s interesting to me that by just using Google, an attacker could get phone history information such as last called number and last caller number. Normally, the Sipura SPA software does a better job of protecting this information, but this particular installation is improperly configured. Other, more technical information can also be uncovered by clicking through the links on the web interface, as shown in Figure 6.39.
There are so many VOIP devices that it’s impossible to cover them all, but the new kid on the VOIP server block is definitely Asterisk. After checking out the documentation for the Asterisk management portal, Jimmy Neutron uncovered the interesting search shown in Figure 6.40.
From this open, an attacker can make changes to the Asterisk server, including forwarding incoming calls, as shown in Figure 6.41.
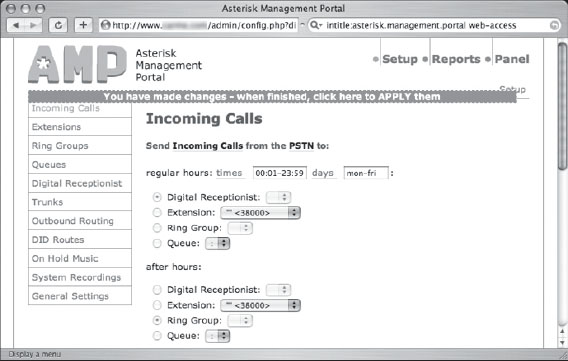
Figure 6.41 Google Hacking Asterisk Management Portals
Unfortunately, a hacker’s fun wouldn’t necessarily stop there. It’s simple to re-route extensions, monitor or re-route voicemail, enable or disable digital receptionists and even upload disturbing on-hold music. But Jimmy’s Asterisk VOIP digging didn’t stop there; he later submitted the search shown in Figure 6.42.

Figure 6.42 Redux. HackenBush. Heh
This flash-based operator panel provides access to similar capabilities, and once again, the interface was found open to any Internet visitor.
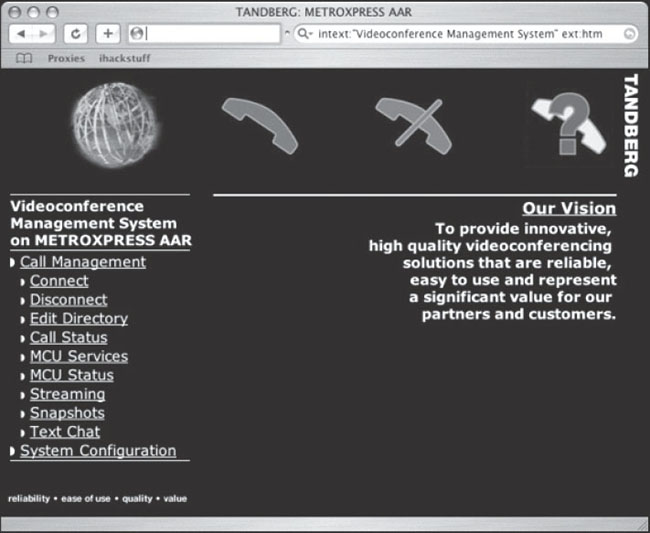
Moving along, Yeseins serves up the interesting search shown in Figure 6.43, which locates videoconferencing management systems.
This management system allows a web visitor to connect, disconnect and monitor conference calls, take snapshots of conference participants, and even change line settings as shown in Figure 6.44.
A malicious hacker could even change the system name and password, locking legitimate administrators out of their own system, as shown in Figure 6.45.

Figure 6.45 Videoconference System Ownage
Despite all the new-fangled web interfaces we’ve looked at, Google hacking bridges the gap to older systems as well, as shown in Figure 6.46.

Figure 6.46 Google Phreaking Old School Style
This front-end was designed to put a new face on an older PBX product, but client security seems to have been an afterthought. Notice that the interface asks the user to “Logout” of the interface, indicating that the user is already logged in. Also, notice that cryptic button labeled Start Managing the Device. After firing off a Google search, all a malicious hacker has to do is figure out which button to press. What an unbelievably daunting task.
Power
I get a lot of raised eyebrows when I talk about using Google to hack power systems. Most people think I’m talking about UPS systems like the one submitted by Yeseins in Figure 6.47.
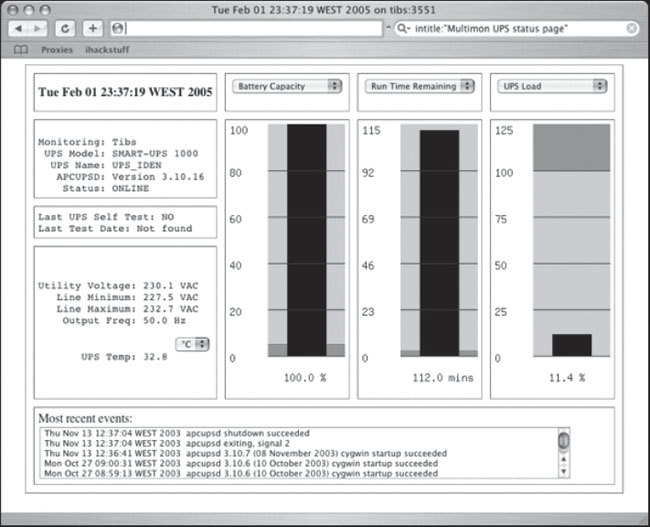
Figure 6.47 Whazzups?
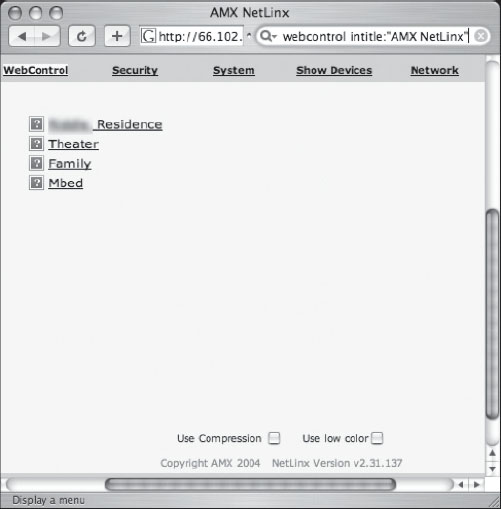
This is a clever Google query, but it’s only an uninterruptible power system (UPS) monitoring page. This can be amusing, but as Jimmy Neutron shows in Figure 6.48, there are more interesting power hacking opportunities available.
AMX NetLinx systems are designed to allow control of power systems. The figure above seems to suggest that a web visitor could control power in a theater, a family room and the master bedroom of a residence. The problem is that the Google search turns up a scarce number of results, most of which are password protected. As an alternative, Jimmy offers the search shown in Figure 6.49.
Although this query results in a long list of password-protected sites, many sites still use the default password, providing access to the control panel shown in Figure 6.50.
This control panel lists power sockets alongside interesting buttons named Power and Restart, which even the dimmest of hackers will undoubtedly be able to figure out. The problem with this interface is that it’s just not much fun. A hacker will definitely get bored flipping unnamed power switches – unless of course he also finds an open webcam so he can watch the fun. The search shown in Figure 6.51 seems to address this, naming each of the devices for easy reference.
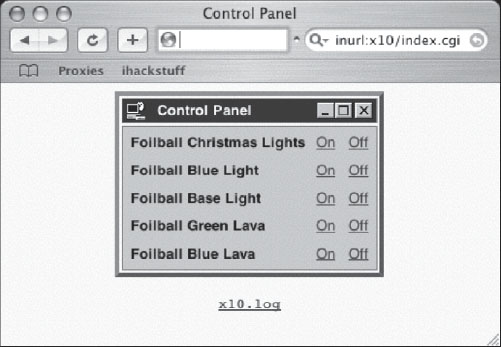
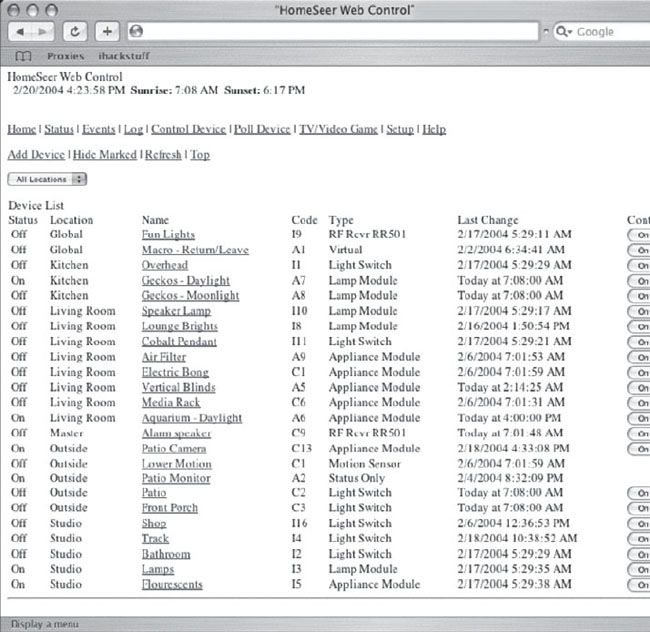
Of course even the most vicious hackers would probably consider it rude to nail someone’s Christmas lights, but no hacker in their right mind could resist the open HomeSeer control panel shown in Figure 6.52.
The HomeSeer control panel puts the fun back into power hacking, listing descriptions for each control, as well as an On, Off and slider switch for applicable elements. Some of the elements in this list are quite interesting, including Lower Motion and Bathroom. The best though is definitely Electric Bong. If you’re a member of the Secret Service looking to bust the owner of this system, I would suggest a preemptive Google strike before barging into the home. Start by dimming the lights, and then nail the motion sensors. Last but not least, turn on the electric bong in case your other charges don’t stick.
Sensitive Info
Sensitive info is such a generic term, but that’s what this section includes: a hodgepodge of sensitive info discovered while surfing Google. We’ll begin with the VCalendar search submitted by Jorokin as shown in Figure 6.53.
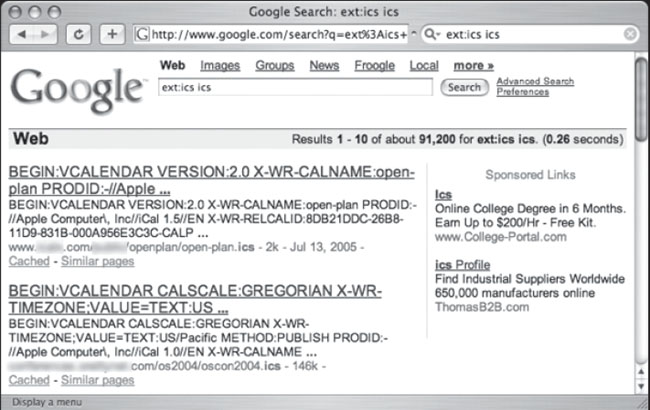
Figure 6.53 Let Me Check Their Calendar
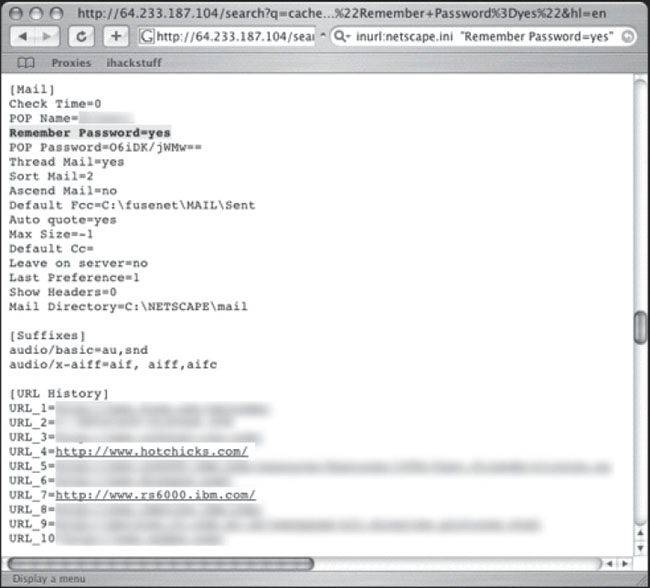
There’s at least a decent possibility that these calendar files were made public on purpose, but the Netscape history file submitted by Digital_Revolution in Figure 6.54 shouldn’t be public.
For starters, the file contains the user’s POP email username and encoded password. Then there’s the issue of his URL history, which contains not only the very respectable IBM.com, but also the not-so-respectable hotchicks.com, which I’m pretty sure is NSFW.
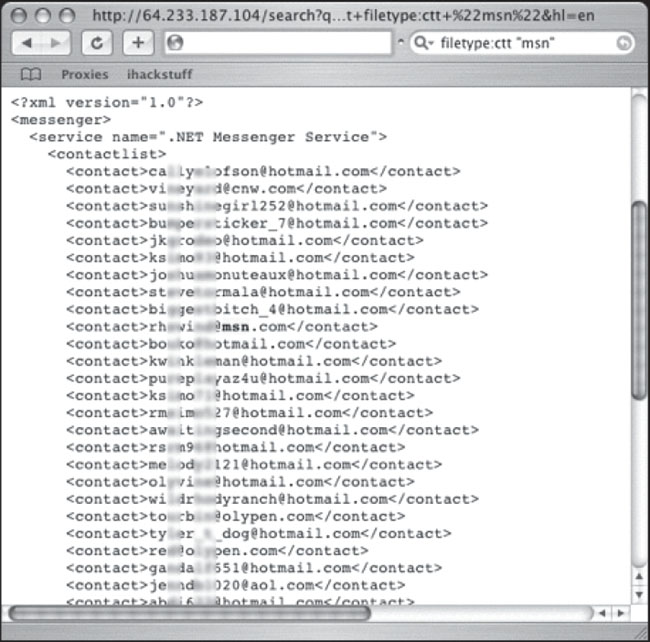
Next up is an MSN contact list submitted by Harry-AAC, which is shown in Figure 6.55.
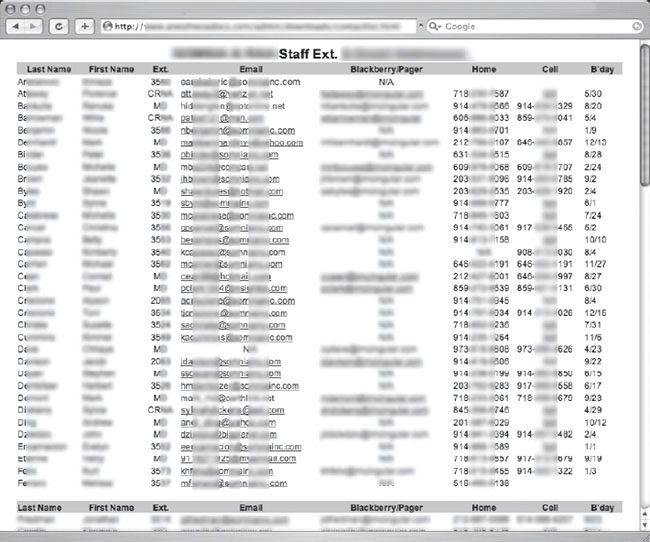
This file lists the contact names and email addresses found in someone’s contact list. At best, this file is spam fodder. There’s really no shortage of email address lists, phone number lists and more on the Web, but what’s surprising is how many documents containing this type of information were created with the express intention of sharing that information. Consider the screen shown in Figure 6.56, which was submitted by CP.
This document is a staff directory, which was created for internal use only. The only problem is that it was found on a public web site. While this doesn’t seem to constitute seriously private information, the search shown in Figure 6.57 (submitted by Maerim) reveals slightly more sensitive information: passwords.
This file lists the cleartext passwords for the Ghost Squad’s private Counterstrike remote administration console. Ask any GS gamer how embarrassing this could be. But hacking a game server is fairly tame. Consider, however, Figure 6.58 which was submitted by Barabas.
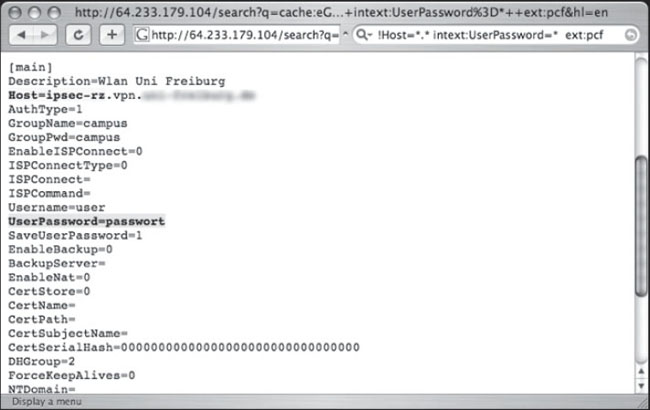
This file lists information and encoded passwords for a Cisco Virtual LAN (VLAN). About the only thing worse than revealing your VLAN’s encoded passwords is revealing your VLAN’s cleartext passwords. Ask and you shall receive. Check out Figure 6.59, again from Barabas.
Yup, that’s a cleartext password nestled inside a University’s configuration file. But interesting passwords can be found in all sorts of places, such as inside Windows unattended installation files, as shown in Figure 6.60, which was submitted by MBaldwin.
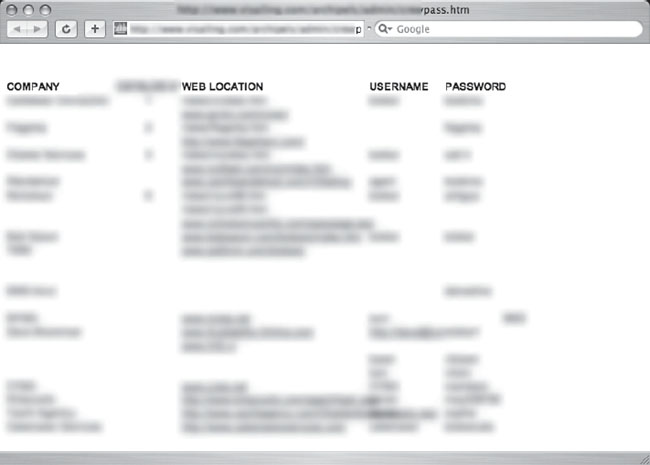
This file also reveals the product key of the installed software, which could be re-used to install the software illegally. Last but not least, check out Figure 6.61, submitted by CP.
This document lists usernames and passwords for various websites. The document was stored on a website, presumably to allow the owner easy remote access to it. However, at some point the document’s location was made public, and Google dutifully crawled it. Remember, public websites are generally just that—public. Don’t combine public and private data without a great deal of forethought.
Police Reports
From what I understand, most police records are a matter of public record. So it doesn’t surprise me when I see police reports like the one shown in Figure 6.62.
Figure 6.62 Police Reports Are Public Record. Okay
However, when I find a police report like the one shown in Figure 6.63, I begin to question the sanity of posting unfiltered police records.
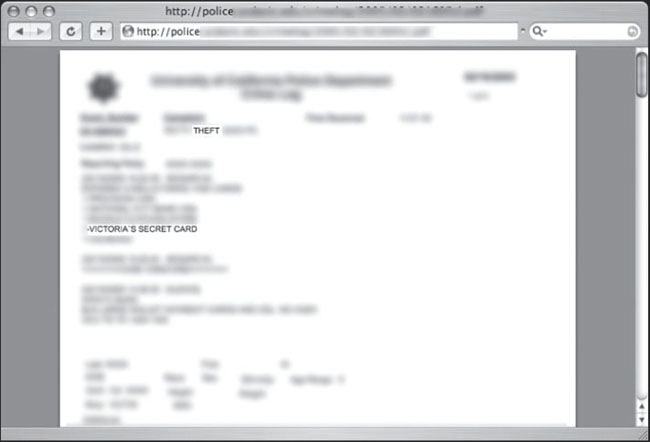
Figure 6.63 That Means Your Victoria’s Secret Account Info Is Too
This police report records the details of a theft of a woman’s purse. The problem is that the contents of the woman’s purse are listed in great detail, including the account number of her Victoria’s Secret card! This is not the only occurrence of such a detailed police report found on the web. Figure 6.64 shows another more revealing report.
This report details another petty theft, this time listing the account numbers of the Visa and MasterCard credit cards that were stolen. It’s very likely that the cards were cancelled immediately after they were reported stolen, but the police report shown in Figure 6.65 lists personal numbers that are not as easy to replace.
In this case, not only is the victim’s driver’s license number posted, but their social security number is listed alongside their mother’s driver’s license number—all of this posted on a public website, ripe for an identity thief’s picking.1
Social Security Numbers
The Social Security Number (SSN) is the most sensitive piece of information a United States citizen possesses. Even an inexperienced criminal can use a pilfered SSN to establish a bank account, open a line of credit or more—all under the victim’s name. In this section, we’ll take a look at some of the ways an individual’s SSN may end up online. Be advised that like the other sensitive searches in this book, every effort has been taken to obfuscate the selected documents and obscure the Google search that was used to locate them.
In most educational facilities, it is common to assign an identification number to students in order to keep their grades and personal information private. However, as shown in Figure 6.66, the identification number most often used is the student’s social security number.
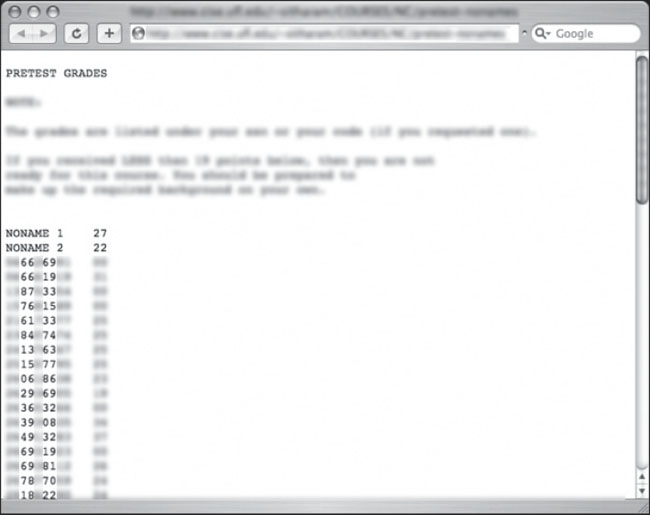
Figure 6.66 Social Security Numbers as Student ID Numbers
The SSN by itself is not necessarily a big deal, and when posted alongside student’s grades (as shown in Figure 6.67) the system works well to keep student’s progress private.

Figure 6.67 “Anonymous” Student Numbers and Grade Postings
However, in many cases, student’s names are posted right alongside their Social Security Number, as shown in Figure 6.68. This of course destroys the anonymity gained by using an identification number instead of a name.
In some cases, these documents are not intended for public viewing, but somehow end up on Internet-facing websites. This is, of course, an unsafe handling practice and the documents end up in Google’s cache. The document shown in Figure 6.69 was discovered sitting in an open directory by an anonymous Google hacker. Notice that it lists student’s names, SSN and more. To make matters worse, this document was found on a US Government training facility website. The document has since been removed.
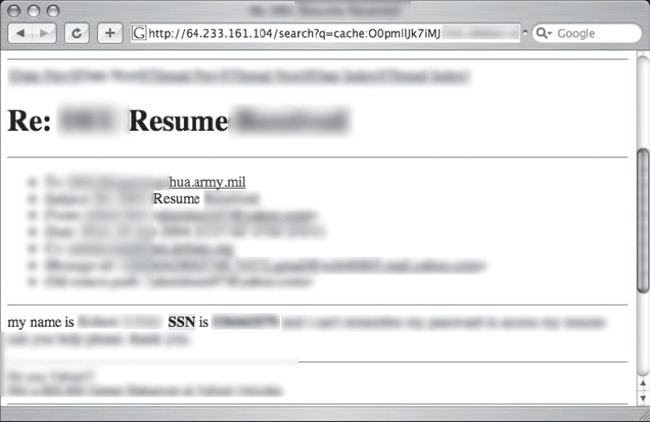
Social Security numbers appear on the web in other ways, most notably through user ignorance. The resume request shown in Figure 6.70 lists an individual’s SSN in a message group post.
The document shown in Figure 6.71 is known as curriculum vitae, or a CV. I wasn’t sure what a CV was, but after a bit of research I discovered it is a sort of résumé for really smart people.
As for me, I think I’ll keep my plain old résumé, especially if maintaining a CV means that I have to publicly expose my birthday and social security number. Finally, check out the spreadsheet shown in Figure 6.72 which lists the name, date of birth, sex, date of hire and SSN of a company’s employees.
Credit Card Information
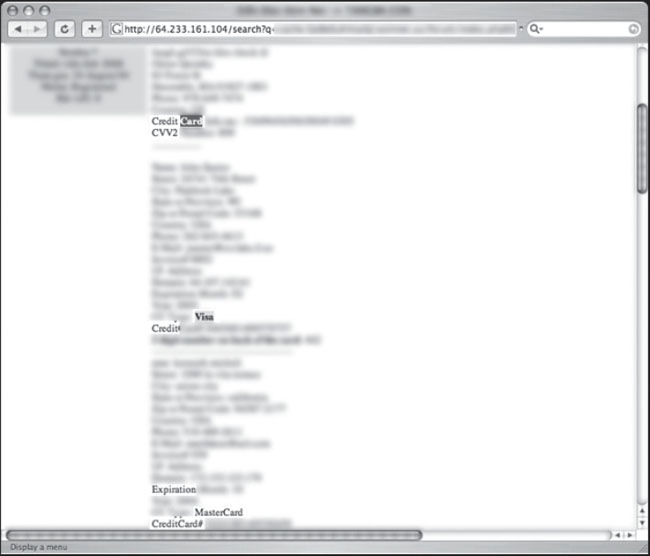
Credit card numbers are obviously very valuable, and should be kept well protected. However, as we’ll see in this section, those numbers can be found on the web with very little effort. Figure 6.73 shows a relatively small document that lists a Visa credit card number alongside the associated expiration date.
Figure 6.74 shows a larger document that lists no only credit card numbers and their associated expiration dates, but also the card certification value (CVV) number which is often used to validate that the card is in the hands of a legitimate bearer.
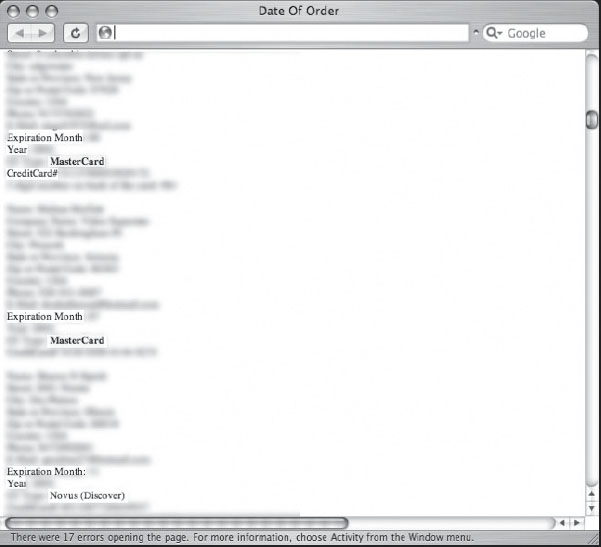
Figure 6.75 shows an extremely large document that contains hundreds of bits of personal information about victims including name, address, phone numbers, credit card information, CVV codes and expiration dates.
However, credit card numbers and expiration dates aren’t the only financially sensitive bits of information on the web, as shown in Figure 6.76.
How Does this Stuff Get on the Web?
Most often, information like this is collected by phishers – criminals using electronic communication to solicit personal information—and kept in an online list or database. In many cases, investigators locate these lists or databases and post links to them in online discussion groups. When Google’s crawlers follow the link, the captured data is exposed to Google Hackers. In other cases, carders (credit card number traders) post this data on the web in open-air web discussions, which Google then crawls and caches. For more information about phishing, see Phishing Exposed from Syngress Publishing.

Figure 6.76 Is Nothing Sacred?
These samples were collected from various web sites, and include bank routing numbers, PayPal usernames and passwords, eBay usernames and passwords, bank account and routing numbers and more, most likely collected by phishers.
Beyond Google
In some cases, Google is the first step in a longer hacking chain. Decent hackers will often take the next step beyond Google. In this section, we’ll take a quick look at some interesting Google hacks that took an extra few steps to pull off. Still simple in execution, these examples show the creative lengths hackers will go to.
This first screenshot, shown in Figure 6.77 (submitted by CP) reports that a staff directory has been removed from the web for privacy purposes.

Figure 6.77 Staff Contact List Removed?
This isn’t a bad idea, but the problem is that the old document must also be removed from the website, or sites like archive.org will hold onto the document’s link indefinitely. Figure 6.78 shows the staff contact document pulled from the original website, thanks to a link from archive.org.
Figure 6.78 Staff Contact List Recovered
In this next example, a Google hacker noticed a password reference sitting in a PDF document, as shown in Figure 6.79.
When downloaded, the PDF file does indeed contain a password reference. In this case, it comes in the form of a link to a password-protected PDF document as shown in Figure 6.80.

Figure 6.80 A Link to a Protected Document, And the Associated Password
As seen in Figure 6.81, the referenced PDF file is indeed password protected.

Figure 6.81 Password Protected PDF Document
Entering the password opens the document, as shown in Figure 6.82.
It makes no sense to password-protect a document then give out the password, but in this case the problem occurred because the original document containing the password reference was not meant to be public. In this case, the blunder lead to the revelation of a sensitive Government document.
Summary
This chapter is all about what can go drastically wrong when the Google hacking threat is ignored. Use this chapter whenever you have trouble conveying the seriousness of the threat. Help spread the word, and become part of the solution and not part of the problem. And before you go sending cease and desist papers to Google, remember—it’s not Google’s fault if your sensitive data makes it online.
1 We’re obviously in tricky water here, as these are dangerous searches indeed. All identifying information in these and following searches has been blurred out, and any information that could lead to the recreation of the Google query has been removed as well. Additionally, most of the sensitive documents found in this chapter have since been removed from the web.