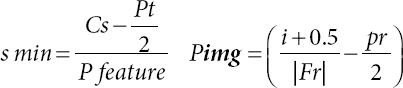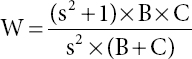8
Deep Learning–Enabled Smart Safety Precautions and Measures in Public Gathering Places for COVID-19 Using IoT
Pradeep Kumar S.1*, Pushpakumar R.1 and Selvakumari S.2
1IT Department, Vel Tech Rangarajan Dr. Sagunthala R&D Institute of Science and Technology, Morai, India
2ECE Sri Venkateswara Institute of Science and Technology, Tiruvallur, India
Abstract
The security dimensions of public gathering cannot be breached and periodic reporting is compulsory in most public gathering places. The Internet of Things (IoT) serving for human safety is widely used nowadays. This methodology incorporates the safety aspects verification of people were entering and traveling from one place to other public places with very high risk. The suggested approach is working on deep learning concepts verifies the presence of the safety things like mask, gloves, and also help to detect temperature to the public who enter in public places like working environments and open places. A camera is positioned in front of the door, entry door, and then from camera with temperature sensor connected with single-board computer (SBC) verifies the mask and gloves presence by the help of image processing. This project deals on low cost safety precautions that ensure the public safety inside the public gathering places. This device also have the sanitizer sprayer to auto spray when hand placed in front of it. This device includes sensor, Raspberry Pi 3, or any kind of SBC a locking actuators. The public gathering in common places may affect by COVID-19 and may not but safety precautions are important. Wearing of mask after entering into common gathering places is needed. In such a case, ensuring these safety precautions helps the public to travel in common place with safety. The obstacle sensor triggers the camera sensor, verified by the image processed by deep learning and the required safety requirements. Once the security elements are verified, the GPIO command opens the locks. If the safety aspects are not met, then the reputation of individuals is remembered by the supervisor for more safety measures and disciplinary acts.
By this methodology, above 95% object detection using the principle of deep learning and image processing is done with precision, and the overall output leads mainly to the worker’s safety of public places to install the safety measures of workers in less cost and also leads to reduce the workload of the supervisors and to reduce the man power.
Keywords: IoT, prevention and safety measures, deep learning method, image processing, low money for automation
8.1 Introduction
The common part of view the safety measures for the public is mandatory and that can be checked in routine bases. Nowadays, we are moving toward to technology world, and many kind of changes are keep on occurring in the medical field to safeguard the public before they became as a patient [1]. Huge IoT technology had been implemented to help medical field for shorting out the spending time for patient in testing, scanning, x-rays, and other kind of investigations. When the COVID-19 blasted in spreading in world, each and every one in the globe had been stunt to face these issues and struggled to stop the spreading virus. At last, the research scientist and doctors had find out that the issues cannot be stopped but prevention can be done to control COVID-19.
For preventing from COVID-19, the safety measure that made compulsory globally includes safety clinic mask, gloves, distance among crowd, and especially the sanitizer. Nowadays, each and every public gathering place had an employee for checking the people wearing mask or not. Because of this, man power is needed if the staff is not doing the work properly and the people may be affected by the COVID-19. It is not at all possible to maintain this kind monitoring using human [2]. For this reason, this project paper helps to resolve this kind of problem by using IoT concept.
8.2 Prelims
8.2.1 Digital Image Processing
This is a kind of task on image to upgrade the image or it is also done to remove some valuable data from the image. The image processing is the process that may lead us to make changes over the original image to digital formats. Many ways are introduced for signal agreement in the way of gathering the input data that is image and video edges. The image or requirements for the image may be picture or photo yield [14]. Digital image processing is wide range of technique that was spreading among the research field; this technique may be used to perform the many operations on the image, in order to obtain an enhanced image or to extract to get huge useful information about the data which is given in the format of image or video.
8.2.2 Deep Learning
Deep learning is widely used in technical research fields, machine learning fields, and mainly in IoT filed [5, 7, 21]. The deep learning concepts make us to consider the number of layers from which the data is obtained [3] that is altered to reach the goal of exact output which overcomes the drawbacks of the traditional algorithm of the machine learning [34–40, 46]. Almost all the quantity of the layers may be changed for which the given information may also be changed. More or less the deep learning systems are more important. In the fields of computer vision of version numbers, speech recognition, Natural Language Processing, audio recognition, social network filtering (SNF), machine translation, medical image analysis, and other forms of machine learning principles, the same learning concepts have been applied [32, 37, 41, 42]. Deep Learning designs are also constructed with these deliberations with a voracious layer-to-layer technique and helps to select which highlights improve in the execution section [4].
8.2.3 WSN
For sensor used for wireless network, it is referred as a network of huge point of equipment and devices that communicate the data and as well as various information that are combining and collected by the supervised field through the numbers of links using wireless network. From the beginning, wireless sensor networks (WSNs) have been recognized as key enablers of the Internet of Things (IoT) paradigm [8, 38]. WSNs are a resilient and efficient distributed data collection technology, but their large-scale use is still limited by issues related to reliability [6], autonomy, cost, and accessibility to application domain experts. Commercial solutions can tackle vertical application domains effectively, but they also lead to lock-ins in technology that hinder horizontal compensability and reuse. The huge varieties of sensors are available nowadays; each one differs based on their speed, size, cost, bandwidth, and memory commonly that vary based on the usage of the user need.
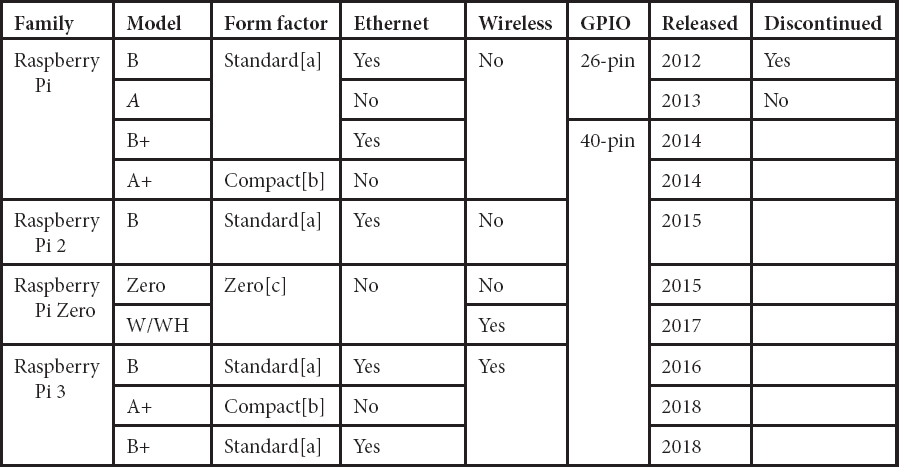
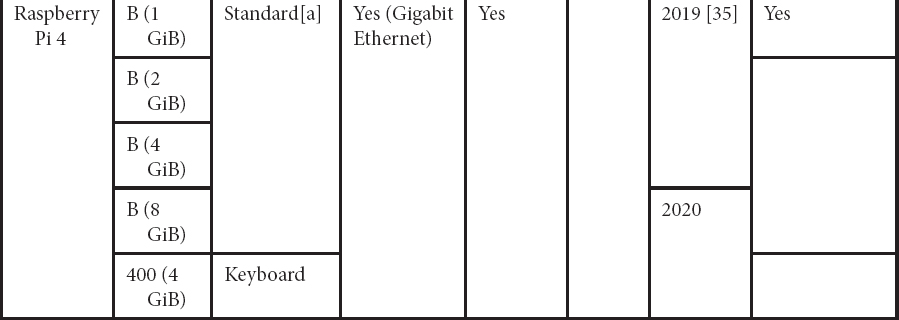
Table 8.1 Raspberry Pi history with version and configuration.
8.2.4 Raspberry Pi
The generation of the Raspberry Pi was started in the year of 2012, when it was introduced in the model of simple and cheaper model A. Later in the year of 2014, it was ARM11 processors that are used to produce the updated version. From that, continuously, the updated new version is available till date. Because of this, huge projects and new IoT and machine learning projects are invited and introduced [24–26]. Not only because it is cheaper, it also contains the huge number of features in newly invited versions. The clear configuration is displayed in Table 8.1. In Table 8.1, the family of the Raspberry Pi and configuration is available in initial state to till date. The single-board computer (SBC) is the common name called for these kinds of computers. Most of the common IoT patent and projects in 2020 common research people are going with the Raspberry Pi versions only. The common factor is cheaper and so easy to carry from place to another. Table 8.1 shows the version of the Raspberry Pi history and the configuration like model name with the GPIO pin numbers.
The Raspberry Pi 3 and Raspberry Pi 4 model may vary due to some model difference like 400 (4 GiB). In this project, Raspberry Pi 3 is used. The form factor is standard, and it is allowed to connect the pi camera and USBs. Ethernet is also allowed in this feature of SBC with the Gigabit of Ethernet connection. The Raspberry Pi 4 was introduced in the year of 2020, with high level of configuration.
8.2.5 Thermal Sensor
The thermal sensor is the small device which is used to measure the degree of both hotness and coolness in any kind of object. The process is made possible by the voltage across the diode. The coolness of the temperature will be automatically changed according to the diode’s resistance. This will be vice-versa for the temperature that changes directly proportional to the diode. Mainly two types of thermal sensors are “Contact Type Temperature Sensors” and “Non-Contact Type Temperature Sensors”. Based on the need, it may be used for the IoT projects.
8.2.6 Relay
The relay is a kind network which is used to transfer a kind of information between two devices over some distance. The source and destination are interconnected with nodes; in this case, the source and destination cannot communicate with each other directly because the distance is greater than transmission range. For this reasons, the relay network is used to share and exchange the information between the source and destination with short time lapse without any interruptions.
Because of this, the wireless networks take advantage of the relay network system. The basic concept of the relay can use in different topologies, from a base line to a ring type of tree shape structure to pass over the information with fast and more efficient way as possible.
8.2.7 TensorFlow
TensorFlow is the main technical tool used for the writing of machine learning applications [52–57]. One of the libraries commonly used to execute machine learning and various calculations, which includes a large account of scientific activities, is TensorFlow [8]. TensorFlow was created by famous IT Company Google and is one of machine learning’s best among the popular libraries. TensorFlow’s central component is the computational graph and tensors that move through edges between all the nodes. TensorFlow is a versatile artificial open source.
According to the flow of data construction a wide range of templates are implemented in the Graphical model, in the intellect library. It is often used to identify, interpret, comprehend, discover, anticipate, and construct.
TensorFlow excels in numerical computation, which is critical to profound learning. In most of the major languages and environments needed for deep learning projects, it has a rich set of application programming interfaces. A set of primitive values formed into an array of any number of dimensions which contain a TensorFlow. The reason why GPUs and various processors designed to perform end point arithmetic exceed expectations in initiate these cluster calculations and algorithms is because of these monstrous amounts of massive clusters’ calculations and algorithms.
8.2.8 Convolution Neural Network (CNN)
The most successful is image classification using CNN. We need a sequence of pictures, main, and leading. We take pictures in this shell, as our initial training data collection [9]. The total amount of images, image dimension, channel quantity, and the number of levels per pixel are the most common reflective data input parameters.
Figure 8.1 clearly shows the operating process of the convolutional neural network with effective development and classification models [43]. From Figure 8.1, the input is carried out via the camera [9], the convolution and the counting process is processed into the pooling process, and the same process is replicated again. Some of the algorithms are used to characterize the safety equipment method on the basis of the above procedure [44]. The safety equipment is identified, and with the aid of this input, the other process will begin [10]. Then, the output is compared to what is called deep learning based on the output (SBC) that will perform the rest of the process.

Figure 8.1 Convolutional Neural Network (CNN).
8.3 Proposed System
The anticipated system methodology of working is in deep learning terminology and this ensures as well as verifies the presence of safety precautions of COVID-19 like mask, gloves, and social distance among the people who want to enter into public gathering places like shopping malls, colleges, schools, and traditional places to ensure the safety to the public in common place [11]. The proposed line for the people is affected by the COVID-19 and incorporates the protection aspects confirmation of people in groups, either they are all maintaining the social distance or not [50, 51]. The proposed device also provides the automatic spraying of the sanitizer to the people who are all entering into the automatic gate which allowed them to enter into the place after ensuring them with mask and hand gloves; it is made possible by image processing as shown in the Figure 8.2. TensorFlow using Raspberry Pi 3 and Raspberry Pi 4 deep learning technique commonly used to do the verification time is measured with huge different subjects and the mask, gloves, and mainly social distance [12]. The camera is placed in the entrance gate which is facing the people who wants to enter via gate or main door and the feed from the IVR or IVSS from Pi-camera attached with the SBC ensures the mask presence through the image dispensation [13].

Figure 8.2 Dataflow diagram.
The key features of this job are deep learning and object detection servers. Inside the Raspberry Pi (SBC) style board, the python program code used to detect objects is run to identify objects [14]. The camera sensor is used to activate the mechanism, which is an obstacle detection sensor. The data for the system is from a camera sensor. The single-board machine named Raspberry Pi is attached as a USB to the camera [15]. The computer is connected to a laptop or any monitor via Wi-Fi.
Figure 8.3 is the process of ensure the safety masks, gloves, and social distance, allowing smart locking and opening the automated door [17]. From Figure 8.3, the fixed pi-camera is used to recognize the safety things of the people if they are not wearing the mask and gloves and they are not allowed in the public gathering places like schools, colleges, theaters, and traditional places [47, 49]. After measuring the safety equipment, the door will be opened and they will do their works.
The camera is attached with the SBC and that is completely trained device by the concept of the deep learning with the image processing. To process the above, all the said technique is executed by the programming language called as python.
Above proposed method includes the temperature sensing by the help of the thermal sensing sensors. Often, due to COVID-19, huge amount of man power are needed to keep on monitoring and to check the body temperature of public while they are entering in public places. This technology also helps to prevent the spreading of viruses from country to country. The invited methodology also helps to mandatory checking and monitoring of this process, while in the other country, people enter into our country. By the help of deep learning in machine learning concepts [27–29], this kind work obtains the best results and leads us achieve concepts results.
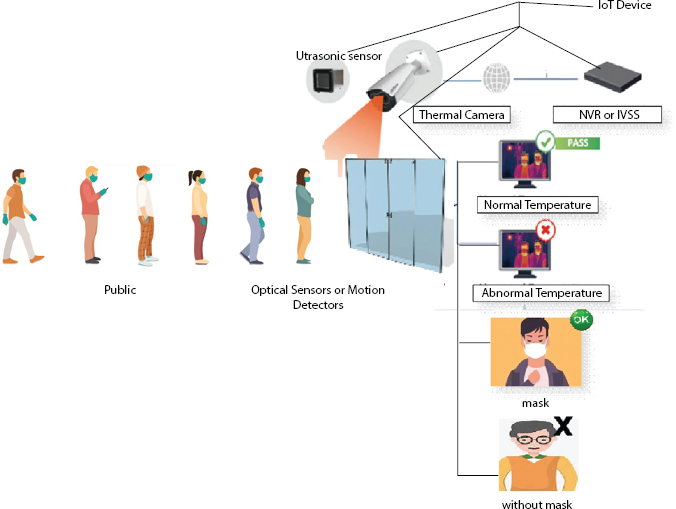
Figure 8.3 Safety equipment detecting.
8.4 Math Model
Contradictory to YOLO, SSD follows a various type of scale system which means that the element maps that are used to classify different objects are at various scales. While each component guide is generated from convolution results at a similar level, the convolution open platform of the various levels must be dissimilar in size [18–20]. In particular, the receptive fields of the sophisticated convolution layer are much larger than those of the lower layers, and the separate data of the abnormally high-level convolution layer lay out [33, 35]. The splitting of data comparing to an abnormal state mentioned highlighted layers is more short form of the entire data. The detail abstract of the extract features of the data is not as much detailed information will be; SSD discovery is similar to the heartless toward little articles.
The computation of the receptive field of convolution is according to the following formula:
where ZCRF(i) Ls is the size of the i-th layer’s convolution receptive region, and Ls is the length of phase.
The filter size is Th and Zf.
where (cs, ct) Ht is the height of the default bouncing box, wt is the width of the default bouncing box, h is the size of the part map, wfeature is the width of the element map,|fr|is the size of the r-th highlight map, wimg is the size of the first image, and wimg is the width of the first image, centered on (i+0.5 |fr|),(j+0.5 |Fzr|). In the event that the model SSD 300 × 300 is adopted, with the end goal that the size of the information image is 300 × 300, the component maps of the model are mostly made from layers [23]. The sizes of the convolution open field and the mapping region of the default bouncing box for each element map
In order to assess the recovery potential of the techniques, their ability to retrieve issues in each image was first assessed and a standard estimate of these outcomes was then calculated. Usually, the recovery potential is surveyed using the W-measure, which is the weighted normal of accuracy and review and communicates as follows:
8.5 Results
In our work, we have created a safe gathering environment for people using the deep learning method and image processing, ensuring the well-being of people and, at the same time, as working in the any organization. In addition, our work allows us to prevent major spreading for not only COVID-19; it also saves people in working places and to minimize manpower for monitoring [16]. In future, by this project, we can point out the particular people who remove the mask after entering into the common places by some color identifications. We also accomplish this approach at a minimal rate. The incentive for future work could be applied to other wearable safety materials with identifying the affected people by the diseases.

Figure 8.4 Detecting mask using deep learning.
Figure 8.4 shows the detecting mask using the deep learning using our device.
Figure 8.5 shows the detecting temperature of the human using the deep learning using our device with the help of the thermal sensor. If the body temperature is more the normal temperature, then the automatic door will open and allow the human to enter into the particular place [22, 48].

Figure 8.5 Detecting body temperature using thermal sensor.
If not, it would not allow above 5 seconds, if the man stands in front of the door, then the alarm will be on and the security will ask him to leave. This is made possible using thermal sensor and deep learning in wide range.
Figure 8.6 clearly shows the smart locking door system of the entrance door. After verifying the safety equipment like mask and gloves, the device enables the power supply to enable to open the smart locking door. When the trained device scans the people who stands and want to walk into the main door, as soon as the mask and gloves is detected, the green light glows and the doors open [43–45]. If the red light glows, it means the worker is not wearing the safety measures like mask, gloves, and social distance.
After ensuring that the mask and gloves are worn by the people, the smart device will open the door; meanwhile, if the people try to remove the mask and gloves, the smart device will alarm automatically [31–33]. So that the major spreading infection of COVID-19 can also be avoided. This may be the precautions for the people safety.
Another program extension is to recognize when staff and public people are keeping social distance and to detect the people who are all affected by not only COVID-19 but also by any other diseases; a third increase involves adding a program to identify a specialist based on the structure of a specialist and ordinary developments in the distance of the leg while walking using OpenCV and database like YOLO [41, 42]. This work also helps us to determine the temperature of the people who are all entering into the main door of all kinds of common places. In addition, the use of the board’s YOLO database for each people is being investigated with the ultimate aim that the software will record any one of the chronicles of the specialists in terms of violation of security law. Further research will continue until all the PPEs (gloves, sanitizer, and so on) can be sufficiently distinguished by the software [47–49]. When using this application, it would be easier to identify gloves and infected people than to differentiate and hand in packet and gloves since the cameras will not reliably capture the condition of the social distance and gloves because of their small size relative to safety measures [50, 51].

Figure 8.6 Raspberry Pi 3 connected with smart Locking door.
8.6 Conclusion
In this work, using the deep learning method and image processing, we built a healthy working and safety atmosphere for the people. This ensures the safety of public in the common gathering, unsafe environment, and working places, or while purchasing and traveling. This ensures the well-being of people. In addition, our work allows us to prevent wide range spreading of COVID-19 and reduce the monitoring capacity of humans, and we also accomplish this strategy at minimal cost. The work can be applied to other wearable protection materials in the future.
References
1. Kanagachidambaresan, G.R., Anand, R., Balasubramanian, E., Mahima, V. (Eds.), Internet of Things for Industry 4.0, Design, Challenges and Solution, EAI/Springer Innovations in Communication and Computing, 2020.
2. Kanagachidambaresan, G.R., Maheswar, R., Manikandan, V., Ramakrishnan, K. (Eds.), Internet of Things in Smart Technologies for Sustainable Urban Development, EAI/Springer Innovations in Communication and Computing, 2020.
3. Pradeep Kumar, S., Selvakumari, S., Praveena, S., Rajiv, S., Deep Learning Enabled Smart Industrial Workers Precaution System Using Single Board Computer (SBC), Internet of Things for Industry 4.0, Design, Challenges and Solution-EAI/Springer Innovations in Communication and Computing, 91–102, 2020.
4. Din, S., Paul, A., Ahmad, A., Gupta, B.B., Rho, S., Service Orchestration of Optimizing Continuous Features in Industrial Surveillance Using Big Data Based Fog-Enabled Internet of Things’- Digital Object Identifier. IEEE Access, 6, 21582–21591, 2018.
5. Krüger, J., Lien, T.K., Verl, A., Cooperation of human and machines in assembly lines. CIRP Ann.-Manuf. Technol., 58, 2, 628–646, 2009.
6. Haddadin, A., Albu-Schäffer, Hirzinger, G., Requirements for safe robots: Measurements, analysis and new insights. Int. J. Rob. Res., 28, 11–12, 1507–1527, Nov. 2009.
7. Asadi, E., Li, B., Chen, I.-M., Pictobot: A Cooperative Painting Robot for Interior Finishing of Industrial Developments. IEEE Rob. Autom. Mag., 25, 2, 82–94, 2018.
8. Krizhevsky, A., Sutskever, I., Hinton, G.E., ImageNet classification with deep convolutional neural networks. Proc. Adv. Neural Inf. Process. Syst., 1097–1105, 2012.
9. Xia, F., Campi, F., Bahreyni, B., Tri-Mode Capacitive Proximity Detection Towards Improved Safety in Industrial Robotics. IEEE Sens. J., 18, 12, 5058–5066, 2018.
10. Martin, A. and Voix, J., In-Ear Audio Wearable: Measurement of Heart and Breathing Rates for Health and SafetyMonitoring. IEEE Trans. Biomed. Eng., 65, 6, 1256–1263, 2018.
11. Lazzerini, B. and Pistolesi, F., Multiobjective Personnel Assignment Exploiting Workers’ Sensitivity to Risk-. IEEE Trans. Syst. Man Cybern.: Syst., 48, 8, 1267–1282, 2018.
12. Lazzerini, B. and Pistolesi, F., An Integrated Optimization System for Safe Job Assignment Based on Human Factors and Behavior. IEEE Syst. J., 12, 2, 1158–1169, 2018.
13. Tsukada, K., Tomioka, T., Wakabayashi, S., Sakai, K., Kiwa, T., Magnetic detection of steel corrosion at a buried position near the ground level using a magnetic resistance sensor. IEEE International Magnetic Conference (INTERMAG), pp. 1–1, 2018.
14. Rybczyński, A., Wolska, A., Wisełka, M., Matusiak, J., Pfeifer, T., Welding Arc Ignition and Photobiological Hazard Evaluation. IEEE Explore, 1–6, 2018.
15. Doan, D.R., Unrecognized Hazards [Electrical Safety]. IEEE Industry Appl. Magazine, 24, 5, 5–5, 2018.
16. Doan, D., Equipment Testing Safety [Electrical Safety]. IEEE Ind. Appl. Mag., 23, 4, 6–7, 2017.
17. Doan, D., Dangers of Distractions [Electrical Safety]. IEEE Ind. Appl. Mag., 23, 3, 5–72, 2017.
18. Jayawardena, A., Duffy, D., Manahan, J.M., Lighting Matters in Industrial Environments: A Framework Linking Workplace Safety to Lighting Quality Metrics. IEEE Ind. Appl. Mag., 23, 3, 54–63, 2017.
19. Spang, R.J., Integrated Safety Management: Creating an All-Inclusive Electrical Safety Program. IEEE Explore, 23, 3, 64–70, 2017.
20. Mayer, S., Hodges, J., Yu, D., Kritzler, M., Michahelles, F., An Open Semantic Framework for the Industrial Internet of Things. IEEE Intell. Syst., 32, 1, 13, 2017.
21. Doan, D., Workplace Hazards for the Electrical Worker’ [Electrical Safety]. IEEE Ind. Appl. Mag., 23, 2, 6–6, 2017.
22. Henriques, V. and Malekian, R., Mine Safety System Using Wireless Sensor Network. IEEE Access, 4, 3511–3521, 2016.
23. Khan, M., Silva, B.N., Han, K., Internet of Things Based Energy Aware Smart Home Control System’- Digital Object Identifier. IEEE - Explore, 4, 7556–7566, 2016.
24. Li, W., Zhao, R., Xiao, T., Wang, X., DeepReID: Deep filter pairing neural network for person re-identification, in: Proc. IEEE Conf. Comput. Vis. Pattern Recognit, Jun. 2014, pp. 152–159.
25. Luo, P., Tian, Y., Wang, X., Tang, X., Switchable deep network for pedestrian detection, in: Proc. IEEE Conf. Comput. Vis. Pattern Recognit, Jun. 2014, pp. 899–906.
26. Krizhevsky, A., Sutskever, I., Hinton, G.E., ImageNet classification with deep convolutional neural networks, in: Proc. Adv. Neural Inf. Process. Syst., pp. 1097–1105, 2012.
27. Lawrence, S., Giles, C.L., Tsoi, A.C., Back, A.D., Face recognition: A convolutional neural-network approach. IEEE Trans. Neural Netw., 8, 1, 98–113, Jan. 1997.
28. Chenand, C.F. and Hsiao, C.H., Haar wavelet method for solving lumped and distributed-parameter systems. IEE Proc.-Control Theory Appl., 144, 1, 87–94, Jan. 1997.
29. Marjani, M., Nasaruddin, F., Gani, A., Karim, A., Hashem, I.A.T., Siddiqa, A., Yaqoob., I., Big IoT Data Analytics: Architecture, Opportunities, and Open Research Challenges. IEEE Access, 5, 5247–5261, 2017. Panetta, K., Gartner’s top 10 strategic technology trends for 2017, 2016.
30. Mohammadi, M., Al-Fuqaha, A., Sorour, S., Guizani, M., Deep Learning for IoT Big Data and Streaming Analytics: A Survey. IEEE Commun. Surv. Tutorials, 20, 4, 2923–2960, 2018.
31. Kim, H.-G., Han, S.-H., Choi, H.-J., Discriminative Restricted Boltzmann Machine for Emergency Detection on Healthcare Robot. IEEE, 2017.
32. Fiore, U., Palmieri, F., Castiglione, A., De Santis, A., Network Anomaly Detection with the restricted Boltzmann Machine. Neurocomputing, Elsevier, 2012.
33. Aldwairi, T., Perera, D., Novotny, M.A., An evaluation of the performance of Restricted Boltzmann Machines as a model for anomaly network intrusion detection. Comput. Networks, Elsevier, 144, 111–119, 2018.
34. Hongqing, F. and Chen, H., Recognizing Human Activity in Smart Home Using Deep Learning algorithm. Proceedings of the 33rd Chinese Control Conference, IEEE, China, 2014.
35. Mocanu, E., Larsen, E.M., Nguyen, P.H., Pinson, P., Gibescu, M., Demand Forecasting at Low Aggregation Levels using Factored Conditional Restricted Boltzmann Machine, Power Systems Computation Conference, 2016.
36. Song, W., Feng, N., Tian, Y., Fong, S., Cho, K., A Deep Belief Network for Electricity Utilisation Feature Analysis of Air Conditioners Using a Smart IoT Platform. J. Inf. Process. Syst., 14, 2, 162–175, 2018.
37. Kim, H.-Y. and Kim, J.-M., A load balancing scheme based on deep-learning in IoT. Cluster Comput., 2016.
38. Cheng, Y., Zhou, X., Wan, S., Choo, K.-K.R., Deep Belief Network for Meteorological Time Series Prediction in the Internet of Things. IEEE Internet Things J., 14, 2015.
39. Zheng, W.-L., Zhu, J.-Y., Peng, Y., Lu, B.-L., EEG-Based Emotion Classification Using Deep Belie Networks. IEEE conference on multimedia and Expo (ICME), 2014.
40. Sun, J., Wyss, R., Steinecker, A., Glocker, P., Automated fault detection using deep belief networks for the quality inspection of electromotors. Tech. Mess., 81, 5, 255–263, 2014.
41. Alhussein, M. and Muhammad, G., Voice Pathology Detection Using Deep Learning on Mobile HealthcareFramework. IEEE Access, 2016.
42. Hsieh, Y.-Z. and Jeng, Y.-L., Development of Home Intelligent Fall Detection IoT System Based on Feedback Optical Flow Convolutional Neural Network. IEEE Access, 2017.
43. Granados, J., Westerlund, T., Zheng, L., Zou, Z., IoT Platform for Real-Time Multichannel ECG Monitoring and Classification with Neural Network, in: IFIP International Federation for Information Processing, Springer, 2018.
44. Islam, A., Hossan, Md T., Jang, Y.M., Convolutional neural network scheme–based optical camera communication system for intelligent Internet of vehicles. Int. J. Distrib. Sens. Netw., 14, 4, 2018.
45. Pamela, D. and Chitoor, M.K., Smart Logistics Using Convolutioal Neural Networks and Sensor Data fusion. International Conference on Intelligent Computing, Instrumentation and Control Technologies (ICICICT), IEEE, 2017.
46. Park, J., Jang, K., Yang, S.-B., Deep Neural Networks for Activity Recognition with Multi-Sensor Data in a Smart Home, 2018 IEEE 4th World Forum on Internet of Things (WF-IoT), 2018.
47. Du, S., Li, T., Gong, X., Yu, Z., Huang, Y., Horng, S.-J., A Hybrid Method for Traffic Flow Forecasting Using Multimodal Deep Learning, 2005.
48. Tornai, K., Oláh, A., Drenyovszki, R., Kovacs, L., Pinter, I., Levendovszky, J., Recurrent Neural Network Based User Classification for Smart Grids. IEEE-Explore, 2017.
49. Zhang, J., Wang, P., Yan, R., Gao, R.X., Long short-term memory for machine remaining life prediction. J. Manuf. Syst., Elsevier, 2018.
50. Fouladgar, M., Parchami, M., Elmasri, R., Ghaderi, A., Scalable Deep Traffic Flow Neural Networks for Urban Traffic Congestion Prediction. International Joint Conference on Neural Networks (IJCNN), 2017.
51. Cheng, Y., Xu, C., Mashima, D., Thing, V.L.L., Wu, Y., PowerLSTM: Power Demand Forecasting Using Long Short-Term Memory Neural Network, Springer Link, 2017.
52. Pham, T., Tran, T., Phung, D., Venkatesh, S., Predicting healthcare trajectories from medical records: A deep learning approach. J. Biomed. Inf., Elsevier, 2017.
53. Kong, F., Li, J., Lv, Z., Construction of Intelligent Traffic Information Recommendation System Based on Long Short-Term Memory. J. Comput. Sci., Elsevier, 2018.
54. Zhang, J., Zhu, Y., Zhang, X., Ye, M., Yang, J., Developing a Long Short-Term Memory (LSTM) based Model for Predicting Water Table Depth in Agricultural Areas. J. Hydrol., 2018.
55. Garcia, F.C.C., Creayla, C.M.C., Macabebe, E.Q.B., Development of an Intelligent System for Smart Home Energy Disaggregation Using Stacked Denoising Autoencoders. International Symposium on Robotics and Intelligent Sensors, IRIS 2016, IEEE, Japan.390 Tausifa Jan Saleem et al. Proc. Comput. Sci., 163, 2019, 381–390, 2016.
56. Ghosh, S., Asif, M.T., Wynter, L., Denoising autoencoders for fast real-time traffic estimation on urban road networks. 56th Annual Conference on Decision and Control (CDC), IEEE, Australia, 2017.
57. Gu, F., Khoshelham, K., Valaee, S., Shang, J., Zhang, R., Locomotion Activity Recognition Using Stacked Denoising Autoencoder. IEEE Internet Things J., 5, 3, 2085–2093, 2018.
- *Corresponding author: [email protected]