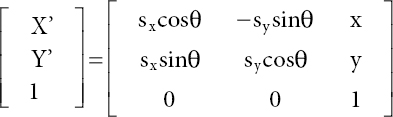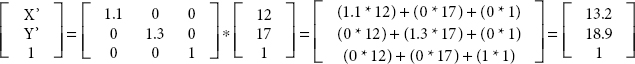5
Generation of Two-Dimensional Text-Based CAPTCHA Using Graphical Operation
S. Pradeep Kumar* and G. Kalpana
Dept. of CSE, Saveetha School of Engineering, Saveetha Nagar, Thandalam, Chennai, India
Abstract
Text-based CAPTCHA is used as a standard security method to prevent the websites from bots and phishing attacks. However, nowadays, hackers are writing a false program to break the text-based CAPTCHA scheme due to their poor strength. In the proposed two-dimensional text-based CAPTCHA approach, the number of characters is dynamic, i.e., changes with every attempt, and all the characters are tilted and rotated in some specific angle, using graphical operation. To further intensify the security, the characters will collide with each other forming a parabolic shape and each will be of different sizes and colors, creating multiple permutations and combinations of size and pixel intensity. The resultant CAPTCHA thus generated is highly secure and can be used in sensitive applications such as defense, inventory management, social media, and banking services.
Keywords: Web security, graphical operation
5.1 Introduction
In the year 2000, researchers from Carnegie Mellon University designed a text-based CAPTCHA approach to restrict attackers entering the Yahoo Chat Rooms [1]. CAPTCHA, Completely Automated Public Turing Test to Tell Computers and Humans Apart [2], are also called as a Reverse Turing Test; subsequently, they were and are envisioned to enable a computer to determine whether a remote client is a human or machine [3]. There are many types of the same such as Character Recognition Based, Optical Character Recognition (OCR), and Non-OCR (using hypermedia such as acoustic and video).
In the recent years, CAPTCHA have evolved and found its application in major websites such as Google, Microsoft, Hotmail, Yahoo, and E-Bay [4]. Below are the key applications of CAPTCHA in multiple platforms.
Nowadays, CAPTCHA is commercially used to block unwanted person to enter into the corresponding websites. The representation of various CAPTCHA in different sites is shown below. Table 5.1 shows the usage of text-based CAPTCHA in web applications with drawbacks.
From the above table, the design of the CAPTCHA in various sites is not convenient for the user to attempt in CAPTCHA screening test [5]. However, the solution has failed to last long, as architecture of bots are improved with sophisticated software programs to break the poorly designed text-based CAPTCHA. The hackers now increase the incoming traffic of a site with scripts to perform false registrations, with misleading information, at high volumes causing spike in the usage of the website. This, in turn, affects the experience of a target user of the site with it being non-responsive, slow, or down. Further, the most commonly used CAPTCHA approach is one of the distorted characters with complex notations, which makes it difficult for the end users to comprehend the characters [5].
There are some rules to be followed for design the CAPTCHA.
- (i) Computer program can able to produce the CAPTCHA character at that time and there.
- (ii) User can able to distinguish these CAPTCHA characters with a rational amount of time.
- (iii) Hackers wrote malicious program using sophisticated software to detect CAPTCHA character at any time.
In this work, Section 5.2 gives the type of CAPTCHA information, and Section 5.3 tells the designing of CAPTCHA problems in older days. Section 5.4 designates the new proposed technique for employing the graphical operations-based CAPTCHAs. Section 5.5 stretches the features of a text-based CAPTCHA character scheme. Section 5.6 describes the breaking methodology of the text-based CAPTCHA scheme. Section 5.7 shows the performance of text-based CAPTCHA using graphical operation. Section 6.8 shows the proposed graphical-based CAPTCHA used in online applications. Finally, Section 5.9 designates the conclusion and future enhancement on graphical operation CAPTCHA scheme.
Table 5.1 Text-based CAPTCHA used in commercial website.
| S. no. | Text-based CAPTCHA | Website | Problem faced |
| 1 |  | Wikipedia | Segmentation can be easily done by the hackers. |
| 2 |  | Discuz | Some interface problems are taken place in the texture background. |
| 3 | In the back ground view, the same black and white color can be used. So, the human user gets confused to predict the correct user. | ||
| 4 |  | Sina | Some interface lines cause the hallow effect to make adhesion operation. |
| 5 |  | Yandex | Some interface lines cause the distortion effect to make adhesion operation. |
| 6 |  | Due to the collision of similar color collide character, human user got confuse to recognize CAPTCHA character. | |
| 7 |  | Microsoft | Same color can be used for cracking and CAPTCHA character. |
| 8 |  | Hot Mail | Due to the collision of similar color collide character, human user got confuse to recognize CAPTCHA character. |
5.2 Types of CAPTCHAs
A wide classification of CAPTCHA mechanisms [3] is labeled as follows.
5.2.1 Text-Based CAPTCHA
Many websites (like Google, Yahoo, and Microsoft) use the own style of text-based CAPTCHA representation. It is easily implemented in the programming language like JavaScript, Python, and ASP.net. There are 26 alphabets and 10 digits to generate a distorted combination of numeric and alphabets in a text-based CAPTCHA. These methods produce a casual arrangement of characters and entrench them in an image that is highly one-sided and designed in a distorted (by computer programs) form so that only the correct user can identify the characters entrenched in the image (see Figure 5.1). The manipulator has to recognize the characters and inscribe them in the allocated area to provide and submit. The operator is defensible as a correct user when the characters competition with that used by server and CAPTCHA producer system. However, many practices contain use of single image only, a performance [3] brands use of set of 12 pictures and enquires operator to find four pictures that contain English language word by just marking onto them instead of only if the fillings of the pictures as the response.
These methods are inhibited by problems such as follows:
- In Figure 5.1, distortion made a confusion to recognize the correct character to the user. The sequences characters such S and P, E and R, and E and Q impose observing problems as shown (see Figure 5.1) [4].
A method has been planned [5] that is able to produce alike CAPTCHA images as that made by Google, Yahoo, and Hotmail with precisions ended 85% for individually. Also, they have referred the pre-processing, subdivision, and post-dissection that work till finding out the totality of characters as shown (see Figure 5.1).
These practices are susceptible to OCR attacks as their safety is reliable upon the grade of distortion while maintaining the ease of determining the characters by human users [6].
Additional issues are such as linguistic reliance because some users not have fluency in English and they have not a clear idea to type the characters. They do not know the English alphanumeric characters have problems to identify the characters. These effects indicated that language does disturb the efficiency of a CAPTCHA’s application for worldwide users.

Figure 5.1 Example of text CAPTCHA.
5.2.2 Image-Based CAPTCHA
The methods used in the image-based CAPTCHA referred as Image Recognition CAPTCHA (IRC). HumanAuth solver made the trial from a website implementing HumanAuth IRC and recognized the solution correctly. So, it is decided that IRCs are identifiable. IRCs are also susceptible to AI attacks.
Additional issues related with IRCs that prevent their usage are follows:
- (i) Huge database is essential to generate a test because active formation of images from which an operator can deduce some meaning is not possible as of now.
- (ii) A solitary trial needs a huge number of images and, thus, enforces a bound on the recurrence of similar image for the consecutive test.
- (iii) Adequately big images needs so that they can take a meaning perceivable by human user.
Hence, the IRC become complex, because maximum of the techniques refers to the user to identify, either the landscape or type of the image(s) being displayed and then reply with the precise answer. Newest instance of such techniques is Anomaly CATPCHA [2] (see Figure 5.2). Identification of image by the user that does not belong to the feature/category depicted by rest of the images. In the image-based CAPTCHA, usually 8 to 16 images are loaded in the given grid layout. These images are collected from the database available in the restricted website. The user has to select an image based on the information available on the test and then go for submission. This test is evaluated for the extreme of four times in order to restrict the bots to contact the evidence from the web. The sample figure has been collected from the web link for the user entry image-based CAPTCHA screening test. Some users have the problem to identify the image due to the low version and blurring images.
5.2.3 Audio-Based CAPTCHA
Audio-based CAPCHA is a sound-based system (ability between the computer and the user to recognize the spoken language) and it is mainly designed for the visually challenged user. The users have the tendency to put more effect to recognize the spoken word and also the end user must be good in English vocabulary. Then, the distorted sound clip is accessible to the user to enter the correct number or word. Some words have the similar sounds.

Figure 5.2 Image-based captcha.
Such methods the users need to put much more effect to recognize a noisy audio narrated by a speech that references some characters. Operators have to recognize those characters and enter them to server in order to show themselves as persons. The voice motion is slanted by added noise so that the fonts are not effortlessly identifiable by artificially intellectual systems or AI bouts.
5.2.4 Video-Based CAPTCHA
This CAPTCHA method shows the category of video and animation based on showing a clip to the user. The system asks the users to type what they have seen or what information the users have perceived. This CAPTCHA method is so complex and expensive compared to other methods. Due to the large size video, the user struggles to download the video and to find the CAPTCHA test. The implementation of video CAPTCHA makes it difficult to support for the multiple input interface with different devices such as keyboard, touch screen, and a speaker. Another potential issue is that for the screen reader to provide a support for the interface which element may have the chance for the bot to allow and play the game.
5.2.5 Puzzle-Based CAPTCHA
The system enables the user to load any CAPTCHA image containing mathematical equation. The user must solve the expression and answer them for the entry process. This CAPTCHA test provides a greater solution to restrict the bots to clear the screening test. These CAPTCHA tests are not convenient to the user to solve the puzzle quickly. Due to the ambiguities which are arising in the puzzle-based CAPTCHAs, the end users get confused to solve them.
5.3 Related Work
Gimphy method uses the CAPTCHA word for the screening test. Most of the words are offered from the glossary, and it is easily broken by the hackers. It is found in the Yahoo website and to find the CAPTCHA word simply. In a disorderly image, the task is to find three of the roughly seven words [6].
Using machine learning algorithm, Chellapilla and Simard had successfully attempt to break a number of visual CAPTCHA taken from the web— Google and Yahoo—and lead a success rate of around 66% [7].
Elie Bursztein has recommended that using DeCaptcha tools to interrupt most of the text-based or visual-based CAPTCHA and found in a well-known websites such as Digg, eBay, and Wikipedia [8].
Using modern technology, it is possible to improve the security of prevailing CAPTCHA by adding clatter and distortion for ordering the CAPTCHA character more forcefully. But it is harder for the user to identify the CAPTCHA character in higher rate and network load [9].
In this connection, the other researcher Yan has fragmented a most of the visual CAPTCHA as collected from Captcha service.org with a high success rate of 100%. Also, the character segmentation can be easily done with the help of current available OCR software, and it merely counts the number of pixels in each segment. Hence, it is necessary to propose a new policy that can consider all the above discussed issues while displaying the CAPTCHA in securable manner.
5.4 Proposed Technique
The development trends has introduced a CAPTCHA screening test that was designed based on the graphical operation. This proposed work shows the interaction of convince to the user entry and harder for the bots. The separate window screening test will be displayed during the execution of user entry test. In the proposed two-dimensional text-based CAPTCHA approach, the number of characters is dynamic, i.e., changes with every attempt, and all the characters are tilted and rotated in some specific angle, using graphical operations such as scaling, rotation, and translation. To further intensify the security, the characters will collide with each other forming a parabolic shape and will each be of different size and colors, creating multiple permutations and combinations of size and pixel intensity.
The technique is free from OCR and segmentation attacks. The parabolic representation makes it difficult for the hackers to projections and segmentations to extract the correct CAPTCHA. At the same time, readability of the characters is kept intact in order to enhance the user experience.
5.5 Text-Based CAPTCHA Scheme
In the beginning stage, hackers used a different type of pattern matching algorithms and identify a similarity index of all each CAPTCHA characters. Pattern matching algorithms to find the similarity index of CAPTCHA characters was used to crack the CAPTCHA codes in the initial days. Hence, the researchers focused on arresting segmentation of characters, resulting CCT (Crowding Character Together) technique. However, the CAPTCHA generated were posing a challenge to users, causing confusions due to colliding characters [10] as shown below. The problems mainly occur due to the space between the allocated CAPTCHA characters (as shown in Figure 5.3).
Figure 5.1 show how some characters are in complete collision with each other. This was intended to create ambiguity to make the similarity index algorithms fail. Meanwhile, the user got confused to recognize and predict the correct CAPTCHA character.
A good text-based CAPTCHA screening test must hold [11].
- (i) The CAPTCHA screening test must have a large enough space to carry out the entry process. The number of characters used in the screening test may vary.
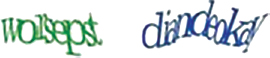
Figure 5.3 Confusing character in a Google CAPTCHA.
Table 5.2 Breaking methodology and success rate of various sources.
Source Sample CAPTCHA image Breaking methodology Breaking success rate Glimpy-R 
Using shape context matching algorithm (color matching algorithm) to segment the CAPTCHA character. Breaking 78% in the year 2004 EZ-Gimpy 
Correlation algorithm use the segmentation technique for connected region: Recognition: distortion evaluation Breaking 97% in the year 2004 Captcha-service 
Vertical projection can be done to do segmentation. Breaking 100% in the year 2007 Ego-share 
Segmentation: connected region Recognition: SVM (Support Vector Machine) Breaking 92% in the year 2009 Slide share 
Large space between the individual characters. More chance can have to do segmentation of each character. Breaking 93% in the year 2010 - (ii) Must contain graphical operations such as distortion, adhesion and overlap of distorted characters, making it difficult for segmentation.
- (iii) Different size, width, and font types of characters to reduce recognition accuracy.
- (iv) Allocating random lengths to shield against breaking CAPTCHA at fixed lengths.
- (v) The same color of the background and text, creating noise that would be very difficult to reduce, hence failing detection accuracies.
The safety of displaying a text-based CAPTCHA mainly depends on the visual interfering effects including rotation, scaling, adhesion, and overlapping. Table 5.2 shows the breaking methodology and success rate of various sources [12].
5.6 Breaking Text-Based CAPTCHA’s Scheme
The basic idea is to break the segmentation techniques for individual character features such as font size, varying pixel count, distortion of individual character, and blurring rotation of each character [13]. Text-based CAPTCHA uses an anti-segmentation technique to arrest segmentation of individual character [14].
From the above table, there are no adherent characters, and thus individual characters are easily obtained. Hence, this is a wrong way for designing CAPTCHA [15]. Below are examples of breaking text-based CAPTCHA schemes.
5.6.1 Individual Character-Based Segmentation Method
This method is helpful in analyzing the number of pixels in different positions to find out each character. It is completely based on the character position and is helpful to determine the optimal segmentation position. The approach is highly effective in breaking non-adherent and distorted CAPTCHA types [16]. These typical methods used a vertical projection segmentation operation can be easily do in order to extract individual segmented CAPTCHA character (as shown in Figure 5.4).
Bar code is used to segment the re-CAPTCHA image:
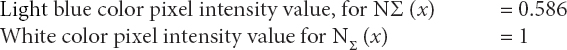

Figure 5.4 Segmentation method based on individual character.
Based on the above pixel values (as shown in Table 5.3), all the dark blue color is converted into black color pixel (intensity value 0) and light blue color is converted into white (intensity value 1). Thus, it completely removing the noise and making a clear image of CAPTCHA set. The extracted image allows furthermore segmentation based on the color and the gap between the characters in the given CAPTCHA.
5.6.2 Character Width-Based Segmentation Method
Segmentation-based character width is not easy method for segmenting to get an individual character. There are different widths for each character and the range is in between 0.75 and 1.6. Thus, each character primes to four gratitude results [17], from which an optimal division as the final acknowledgment result is uncovered [18]. The enhanced dynamic programming approach is to determine the optimal segmentation between the minimum and maximum width of several CAPTCHA characters (as shown in Figure 5.5).
Table 5.3 Pixel value changed entry.


Figure 5.5 Segmented CAPTCHA image.
5.7 Implementation of Text-Based CAPTCHA Using Graphical Operation
All the CAPTCHA characters are represented in different shapes, widths, and pixel intensity (by changing the color). For example, pixel intensity of letter “s” may vary as shown in Table 5.4. Every CAPTCHA character will collide with the center of adjacent characters [19]. The graphical operation helps show the characters in a parabolic format (as shown in Figure 5.6). The number of CAPTHA character used in the screening test from 6 to 8.
5.7.1 Graphical Operation
The various graphical operations have made in each character in order to represent a parabolic format. The operation used are scaling, rotation, and translation; each pixel that is in the position P(x,y) is shifted to a new position P’(x,y) [20].
Table 5.4 Look up table entry.
| Letter | Color used | Pixel count | CAPTCHA character |
| S | Violet | 169 |  |
| S | Blue | 175 |  |
| S | Green | 184 |  |
- (i) Scaling: The method is used to increase or reduce in size the CAPTCHA character with reverence to “X” or “Y” axis. It can be diverse up to 20%. The transformation for the successive scaling operations produces a composite scaling matrix [Equation (5.2)]. Scaling function is defined in Equation (5.1).
The matrix for the translation [Equation (5.2)] is as follows:
- (ii) Rotation: Some of the CAPTCHA characters that may spin in dissimilar angles can slander between 20° and −20°. Two successive rotations (θ1, θ2) are applied to produce a transformed operation. Scaling function is defined in Equation (5.3).
The matrix equation [Equation (5.4)] can be represented by
- (iii) Translation: Using a matrix revolution method, a finicky CAPTCHA character in a specified text box is translated.
The corresponding pixels are translated to some other position from p to p’.
The two consecutive translation vectors (tx1,ty1) and (tx2,ty2) are applied to a
Coordinate position p, then p’ = T(tx2,ty2).[T(tx1,ty1).p
p’->new position
The translation matrix equation can be represented in Equation (5.5).
Using all the above geometric graphical calculation, the entire set of CAPTCHA character has changed the position and shape with respect to different pixel coordinate position (as shown in Figure 5.6). Hence, the collectivization of all CAPTCHA characters is shown like a curve shape in parabolic formats.
5.7.2 Two-Dimensional Composite Transformation Calculation
In this CAPTCHA set, each and every CAPTCHA character can have the chance to signify in dissimilar colors and dissimilar shapes [21]. So, every character can have the fixed pixel count with respect to a particular color. The two-dimensional transformation has the combination of translation, scaling, and rotation to scale about P1 (x1,y1); the following sequence of the essential transformations is required [as define in Equation (5.6)]:

Figure 5.6 Graphical operation made CAPTCHA image.
- Translate the object by (tx, ty)
- Rotate the object by (θ)
- Scaling the object by (sx, sy)
This sequence of stages can be achieved as follows:
Now, the new coordinate point can be represented in Equation (5.7)
Consider a starting coordinate pixel position of an object is P(10,20) and do the translation by (5,10) with a rotation of an angle 30° and a scaling factor of (sx = 1.1, sy = 1.3).
- (i) Translation of vertex (20, 10): It is defined in Equation (5.8).
- (ii) Rotation of a pivot point to some angle. It is defined in Equation (5.9).
New point
- (iii) Scaling function to a pivot pixel point [round of value (11.65, 17.32) to (12, 17)].
It is defined in Equation (5.10).
Thus, the initial coordinate pixel position (20, 10) is shifted to (13, 19) position using the above graphical operation calculation. Moreover to do all remaining pixel position of an object to retrieve the correct accurate position.
All the tradition characters are exhibited inside the CAPTCHA screening test of a user typed web application form. Each character clutches a distinct grid layout. So, there are 36 separate {(a, b, …, z,), (0, 1, …, 9)} grid layout for the characters used. In each and every CAPTCHA test, all the arrangement of usage characters is to differ. There are preserving 10 different orders to confuse the bots for predicting the correct characters.
Advantages
- (i) Hackers using modern software cannot have the coincidental to analysis the CAPTCHA character at any time.
- (ii) Restrict to various attacks such as online guessing attacks, OCR attacks, and dictionary attacks.
- (iii) Even using graphical operation, user never gets confused to recognize a CAPTCHA character in the screening test.
5.8 Graphical Text-Based CAPTCHA in Online Application
User filled all the essential details in the presently used online application form and then the system permits to allow for the CAPTCHA screening test. If the user is not able to give the correct details in the application form as on time, then a new set of graphical CAPTCHA character will be generated. Each and all character may have the possibility to show in dissimilar colors.
Implementation
The picture of CAPTCHA must be a user friendly to the user and strongly restrict the bots to enter into the profitable websites. In the database, it maintains nearly a 600 CAPTCHA character set. Using the random number creator, collect the CAPTCHA character from the database and allotted in the screening test. The working algorithm (mouse clicked CAPTCHA) embraces the working process of a CAPTCHA transmission test. The proposed procedure is undergoing a different objective based on the user entry and representation of CAPTCHAs.
- (i) User Entry
Since our technique is based on the grouping of text and imaged, the user does not enter the characters as it is in the screening test. - (ii) Image Recognition
A separate window is allotted in the CAPTCHA screening test. The user clicked all the familiar character based on dynamic order CAPTCHAs. - (iii) Less Storage
Small-sized window is maintained during the screening test. Typically, users use mouse cursor and provide easily visible to the user. - (iv) OCR and Dictionary Attack
CAPTCHA character is represented on the curve-based format. All the CAPTCHA character is represented in different colors. It does not lead to the OCR and dictionary attack.
The time required to solve the clickable CAPTCHA cursor is to identify the English letter and numerical in the screening test is less. The regularity of repetitive challenge lead to the variability in the number of CAPTCHs character used (6 to 8) in the screen text, representation (upper/lower curve), and useable character. Curve-based CAPTCHA were solved with the help of a mouse, and traditionally, CAPTCHA was solved with the help of the keyboard.
In adding up to that, some graphical operation has prepared in the CAPTCHA character along with some clatter (black curve lines are there in the text box). This leads to the stronger safety level for their CAPTCHA refreshment. In this graphical-based design CAPTCHA screening test, the background texts demote in white color and foreground texts refer in distorted ordered of different colors of CAPTCHA characters (as shown in Figure 5.7). The user can give all the sufficient details in the web application form and then only the system permits for graphical-based CAPTCHA screening test. After that, the entire screening test can hold only for 25 seconds in the online application form. Thus, fixed time graphical-based CAPTCHA is helpful and not give chance for the hackers to guess the correct characters on time.
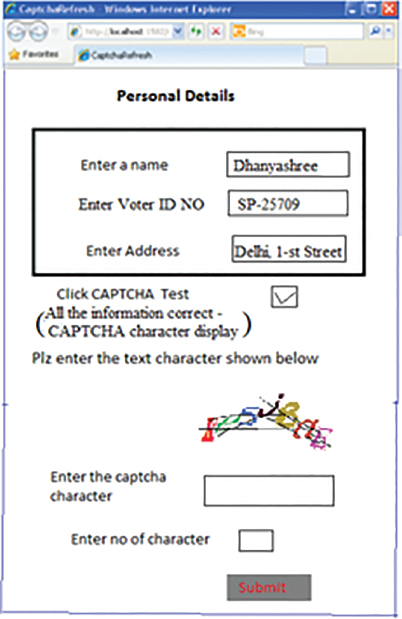
Figure 5.7 Graphical sesign CAPTCHA in online application.
5.9 Conclusion and Future Enhancement
This planned method shows all the CAPTCHA characters that have been given in dissimilar colors. Each character is colliding in middle of the neighboring character and creates a parabolic shape format. Vertical line segmentation has not feasible to identify a single character alone. Using graphical operation and take a longer time process to allocate the entire CAPTCHA letter in the screening test. At any situation, user never gets confused to recognize the CAPTCHA character in the online applications. The achievement rate on a model test has been boosted to 97% for the human user and 0% for the hackers regarding the recognition. In future, this technique is helpful to design a different cure-based format and enrolled in various applications like inventory, banking, and commercial websites, thus making the generation of two-dimensional text-based CAPTCHA using graphical operation approach as a secure and user-friendly way of CAPTCHA generation.
References
1. Hasan, W.K.A. and AlGharb, A., A Survey of Current Research on CAPTCHA. Int. J. Comput. Sci. Eng. Sur. (IJCSES), 7, 3, June 2016, https://aircconline.com/ijcses/V7N3/7316ijcses01.pdf
2. Yadava, P.S., Sahu, C.P., Shukla, S.K., A Framework for Devanagari Script-Based Captcha. Int. J. Adv. Inf. Technol. (IJAIT), 1, 4, August 2011, https://www.academia.edu/14911658/A_FRAMEWORK_FOR_DEVANAGARI_SCRIPT_BASED_CAPTCHA
3. Chen, J., Luo, X., Guo, Y., Zhang, Y., Gong, D., A Survey on Breaking Technique of Text-Based CAPTCHA. Secur. Commun. Netw., 2017, Article ID 6898617, https://doi.org/10.1155/2017/6898617.
4. Jeng, A.B., Tseng, C.C., Tseng, D.F., Wang, J.C., A Study of CAPTCHA and Its Application to User Authentication, in: Computational Collective Intelligence. Technologies and Applications. ICCCI 2010. Lecture Notes in Computer Science, vol. 6422, J.S. Pan, S.M. Chen, N.T. Nguyen (Eds.), Springer, Berlin, Heidelberg, 2010.
5. Roshanbin, N. and Miller, J., A Survey and Analysis of Current Captcha Approaches. J. Web Eng., 12, 1&2, 2013, 001–040© Rinton Press.
6. Azad, S. and Jain, K., CAPTCHA : Attacks and Weaknesse against OCR Technology. Glob. J. Sci. Technol. Neural Artif. Intell., 13, 3, version 1.0, May 2013.
7. Bursztein, E., Martin, M., Mitchell, J.C., Text based CAPTCHA Strengths and Weaknesses. ACM Computer and Communication security (CCS), pp. 1–14, 2011.
8. Mori, G. and Malik, J., Recognizing Objects in Adversarial Clutter:Breaking a Visual CAPCTHA, in: Proceeding of IEEE Conference on Computer Vision and Pattern Recognition, USA, June16-22, 2003, vol. 1, pp. 134–141.
9. Chellapilla, K. and Simard, P., Using Machine Learning toBreak Visual Human Interaction Proofs (HIPs), in: Advances in Neural Information Processing Systems 17, Neural Information Processing Systems (NIPS), MIT Press, USA, 2004.
10. Jawane, V. and Rath, V., Survey Paper on Secure Text-Based CAPTCHA. Open Access Int. J. Sci. Eng., 3, Special Issue 1, ISO3297:2007 Certified, March 2018.
11. Tariq Banday, M. and Shah, N.A., A Study of CAPTCHAs for Securing Web Services. Int. J. Secur. Digit. Inf. Age, 1, 2, December 2009.
12. Tang, M., Zhang, Y., Liu, Y., Zhang, P., Research on Deep Learning Techniques in Breaking Text-Based Captchas and Designing Image-Based Captcha, vol. 3, no. 3, pp. 572–577, 2018.
13. Sandeep, H. and Raghavendra, B.K., A New Security Primitive Model Based on Artificial Intelligence Using Captcha as Graphical Passwords. Int. J. Comput. Eng. Appl., ICCSTAR-2016, Special Issue, May 16, 2016.
14. Kumar, D. and Sharma, S., Highly Secured Intellectual Graphical CAPTCHA. Int. J. Modern Eng. Manage. Res., 6, 1, 2018.
15. Chandavale, A.A., Sapkal, A.M., Jainkar, R.M., A frame work to analysis the security Of text based CAPTCHA. Int. J. Comput. Appl., 27, 2010, No. 27, Article 19, 2010.
16. Sinha, A. and Tarar, S., Review Paper on Different CAPTCHA Techniques. Int. J. Comput. Sci. Technol., 7, 1, Jan - March 2016.
17. Moy, G., Jones, N., Harkless, C., Potter, R., Distortion Estimation Techniques in Solving Visual CAPTCHAs. IEEE Conference on Computer Vision and Pattern Recognition (CVPR’04), June 2004, vol. 2, pp. 23–28, 2004.
18. Oleg Starostenko Claudia Cruz- Perez Fernando Uceda-Ponga, Breaking text-based CAPTCHAs with variable word and character orientation, 48, 1101–1112, 2015.
19. Wu, X., Dai, S., Guo, Y., Fujita, H., A machine learning attack against variable- length Chinese character CAPTCHAs. 14, 4, pp. 1548–1565, 2018.
20. http://www.cs.cityu.edu.hk/~helena/cs31622000A/Notes02.pdf
21. Ye, Chen, Y., Zhu, B., The Robustness of a New 3D CAPTCHA. 2014 11th IAPR Workshop on Document Analysis Systems, Tours, pp. 319–323, 2014.
- *Corresponding author: [email protected]