In order to perform forensic analysis on any system (desktop or mobile), it's important to understand the underlying file hierarchy. A basic understanding of how Android organizes its data in files and folders helps a forensic analyst narrow down his research to specific locations. If you are familiar with Unix-like systems, you will understand the file hierarchy in Android very well. In Linux, the file hierarchy is a single tree, with the top of the tree being denoted as /. This is called the root. This is different from the concept of organizing files in drives (as with Windows). Whether the filesystem is local or remote, it will be present under the root. Android file hierarchy is a customized version of this existing Linux hierarchy. Based on the device manufacturer and the underlying Linux version, the structure of this hierarchy may have a few insignificant changes. To see the complete file hierarchy, you need to have root access. The following screenshot shows the file hierarchy on an Android device:

Folders present under / (root) in Android
The following sections provide an overview of the directories present in the file hierarchy of an Android device.
This is the directory (/cache) where Android stores frequently accessed data and app components. Wiping the cache doesn't affect your personal data, but simply deletes the existing data there. There is also another directory in this folder called lost+found. This directory holds recovered files (if any) in the event of filesystem corruption, such as incorrectly removing the SD card without unmounting it and so on. The cache may contain forensically relevant artifacts, such as images, browsing history, and other app data.
This is a symbolic link to /sys/kernel/debug. This folder is used to mount the debugfs filesystem and to debug kernel.
This is the partition that contains the data of each application. Most of the data belonging to a user, such as the contacts, SMS, dialed numbers, and so on, is stored in this folder. This folder has significant importance from a forensic point of view as it holds valuable data. The following screenshot shows the folders present in this partition:

Contents of data partition of an Android device
The following sections provide a brief explanation of other important subdirectories present under the data folder.
As discussed in Chapter 1, Introducing Android Forensics, Android applications contain .dex files that are optimized versions of Java bytecode. When an application is installed on an Android device, some modifications are performed on the corresponding .dex file, and a resultant file called .odex file (optimized ,dex file) is created. It is then cached in the /data/dalvik-cache directory so that it doesn't have to perform the optimization process every time it loads application.log.
This folder contains several logs that might be useful during examination, depending on the underlying requirements. For example, the following screenshot shows one of the log files recovery_log.txt, which gives details about the recovery log:

The recovery_log.txt file output
The /data/data partition contains the private data of all the applications. Most of the data belonging to the user is stored in this folder. This folder has significant importance from a forensic point of view as it holds valuable data. This partition is covered in detail in the Internal Storage section.
This directory contains special device files for all the devices. This is the mount point for the tempfs filesystem. This filesystem defines the devices available to the applications.
As discussed in Chapter 1, Introducing Android Forensics, when booting the Android kernel, the init program is executed. This program present under this folder.
This directory serves as a mount point for all the filesystems, internal and external SD cards, and so on. The following screenshot shows the mount points present in this directory:

This is the mount point for the procfs filesystem that provides access to the kernel data structures. Several programs use /proc as the source for their information. It contains files that have useful information about the processes. For instance, as shown in the following screenshot, meminfo present under /proc gives information about the memory allocation:

meminfo file under proc folder in Android
This is the home directory for the root account. This folder can be accessed only if the device is rooted.
This contains binaries for several important daemons. This is not of much significance from a forensic perspective.
As the name suggests, this folder contains information about miscellaneous settings. These settings mostly define the state, that is, ON/OFF. Information about hardware settings, USB settings, and so on can be accessed from this folder.
This is the partition that contains the data present on the SD card of the device. Note that this SD card can be either removable storage or non-removable storage. Any app on your phone with the WRITE_EXTERNAL_STORAGE permission may create files or folders in this location. There are some default folders, such as android_secure, Android, DCIM, media, and so on, present in most of the mobiles. The following screenshot shows the contents of /sdcard location:

Contents of the sdcard partition of an Android device
Digital Camera Images (DCIM) is the default directory structure for digital cameras, smartphones, tablets, and related solid-state devices. Some tablets have a photos folder that points to the same location. Within DCIM, you will find photos you have taken, videos, and thumbnails (cache) files. Photos are stored in /DCIM/Camera.
Android developer's reference explains that there are certain public storage directories that are not specifically tied to a specific program. Here is a quick overview of these folders:
Music:Media scanner classifies all media found here as user music.Podcasts:Media scanner classifies all media found here as a podcast.Ringtones:Media files present here are classified as ringtones.Alarms:Media files present here are classified as alarms.Notifications:Media files under this location are used for notification sounds.Pictures:All photos, except the ones taken with a camera, are stored in this folder.Movies:All movies, except the ones taken with a camera, are stored in this folder.Download: Miscellaneous downloads are stored in this folder.
This directory contains libraries, system binaries, and other system-related files. The pre-installed applications that come along with the phone are also present in this partition. The following screenshot shows the files present in the system partition on an Android device:

Contents of the system partition of an Android device
Here are some of the interesting files and folders present in the /system partition that are of interest to a forensic investigator.
This file contains all the build properties and settings for a given device. For a forensic analyst, this file gives an overview about the device model, manufacturer, Android version, and many other details. Contents of this file can be viewed by issuing a cat command, as shown in the following screenshot:

The build.prop file output
As shown in the preceding output, you can find out the product model, CPU details, and Android version by viewing this file content. On a rooted device, tweaking the build.prop file could lead to a change in several system settings.
This folder contains system apps and preinstalled apps. This is mounted as read only to prevent any changes. The following screenshot shows various system-related apps that are present in this folder:
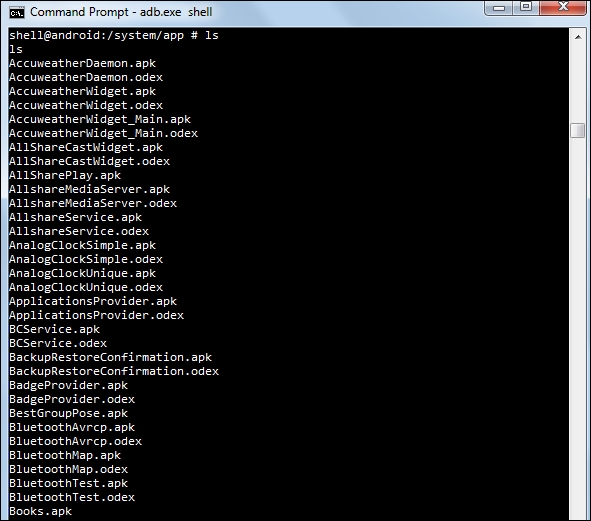
System apps present under the /system/app partition
Along with the APK files, you might have also noticed .odex files in the preceding output. In Android, applications come in packages, with the.apk extension. These APKs contain .odex files whose supposed function is to save space. The .odex files are collection of certain parts of an application that are optimized before booting.
These files contain configuration rules for the /dev directory.
To sum up, here is a screenshot of the Android file tree reference from http://wiki.robotz.com/index.php/Android_File_System:

Android file tree
