Mobile forensics is a branch of digital forensics which is evolving in today's digital era. Android forensics deals with extracting, recovering and analyzing the data present on an Android device through various techniques. However, it is important to have a clear understanding of the platform and other fundamentals before we dive in and find out how to extract data. In this chapter, we will cover the following topics:
- Mobile forensics
- Mobile forensics approach
- Android architecture
- Android security
- Android hardware components
- Android boot process
The world today is experiencing technological innovation like never before. This growth is almost exponential in the field of mobile devices. Gartner, a technology research and advisory firm, in their forecasts published in June 2014, predicted that mobile phone shipments are soon set to break 2.4 billion units. This statistic alone reflects the unprecedented growth of mobile devices. Mobile phones have not only increased in number but also have become more sophisticated in terms of functionality.
The following screenshot referenced from http://en.wikipedia.org/wiki/File:Mobile_phone_subscribers_1997-2014_ITU.svg shows the increase in graph of mobile phone subscribers per 100 inhabitants from 1997 to 2014:
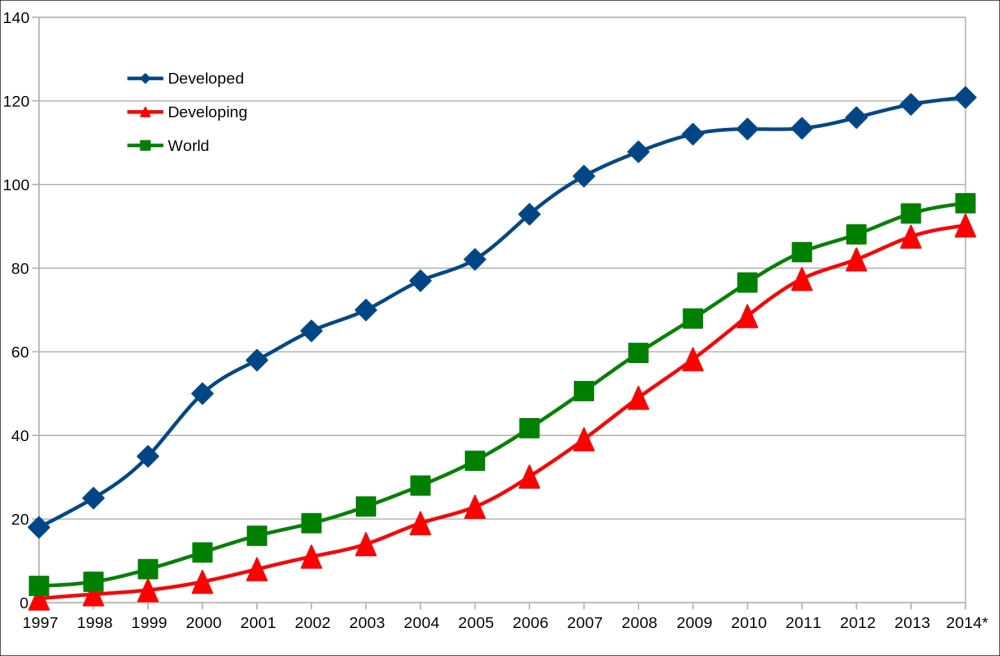
Mobile phone subscribers per 100 inhabitants from 1997-2014
Within mobile phones, smart phones are very much becoming the norm. Improvements in the computing power and data storage of these devices enable us to perform a wide range of activities. We are increasingly becoming dependent on these mobile devices for most of our activities. Apart from performing routine tasks such as making calls, sending messages, and so on, these devices also support other activities such as sending e-mails, surfing the Internet, recording videos, creating and storing documents, identifying locations with Global Positioning System (GPS) services, managing business tasks, and much more. In other words, mobile devices are now a repository of sensitive personal information, containing a wealth of user data. Quite often, the data sitting on a device is more valuable than the device itself. For instance, calls made from a device could be valuable information for law enforcement agencies. The fact that mobile forensics played a crucial role in solving high-profile cases, such as the 2010 Times Square car bombing attempt and the Boston marathon bombings, reaffirms the increasing role of mobile forensics in many government and law enforcement cases.
Mobile device forensics is a branch of digital forensics which deals with extracting, recovering and analyzing digital evidence or data from a mobile device under forensically sound conditions. Simply put, it deals with accessing the data stored on devices which includes SMS, contacts, call records, photos, videos, documents, application files, browsing history and so on, and also recovering data deleted from devices using various forensic techniques. It is important that the process of recovering or accessing details from a device is forensically sound, if it has to be admitted in a court of law and to maintain the integrity of the evidence. If the evidence has to be admitted in a court of law, it is important that the original device is not tampered with.
Note
The term forensically sound is often used in the digital forensics community to clarify the correct use of a particular forensic technology or methodology. Mobile forensics, especially Android forensics, is evolving fast, owing to the fact that it has a market share of 84 percent (as per market research firm IDC).
As explained by Eoghan Casey in his book Digital Forensics and Investigation, forensic soundness is not just about keeping original evidence unaltered. Even the routine task of acquiring data from a hard drive using a hardware write-blocker may cause alterations (for example, making a hidden area of the hard drive accessible) on the drive. One of the keys to forensic soundness is documentation. Documenting how the device is handled from the beginning is very important. Hence, an investigation can be considered forensically sound if the acquisition process preserves the original data and its authenticity and integrity can be validated. Evidence integrity checks ensure that the evidence has not been tampered with from the time it was collected. Integrity checks are done by comparing the digital fingerprint of the evidence taken at the time of collection with the digital fingerprint of the evidence in current state.
There is a growing need for mobile forensics due to several reasons. Some of the prominent reasons are:
- Use of mobile phones to store personal information
- Increased use of mobile phones to perform online activity
- Use of mobile phones in several crimes
Mobile forensics on a particular device is primarily dependent on the underlying operating systems. Thus we have different fields such as Android forensics, iOS forensics, Blackberry forensics, and so on.
