7.2 A Simplified DES-Type Algorithm
The DES algorithm is rather unwieldy to use for examples, so in the present section we present an algorithm that has many of the same features, but is much smaller. Like DES, the present algorithm is a block cipher. Since the blocks are encrypted separately, we assume throughout the present discussion that the full message consists of only one block.
The message has 12 bits and is written in the form , where consists of the first six bits and consists of the last six bits. The key has nine bits. The th round of the algorithm transforms an input to the output using an eight-bit key derived from .
The main part of the encryption process is a function that takes a six-bit input and an eight-bit input and produces a six-bit output. This will be described later.
The output for the th round is defined as follows:
where denotes XOR, namely bit-by-bit addition mod 2. This is depicted in Figure 7.1.
Figure 7.1 One Round of a Feistel System

This operation is performed for a certain number of rounds, say , and produces the ciphertext .
How do we decrypt? Start with and switch left and right to obtain . (Note: This switch is built into the DES encryption algorithm, so it is not needed when decrypting DES.) Now use the same procedure as before, but with the keys used in reverse order . Let’s see how this works. The first step takes and gives the output
We know from the encryption procedure that and . Therefore,
The last equality again uses , so that is 0. Similarly, the second step of decryption sends to . Continuing, we see that the decryption process leads us back to . Switching the left and right halves, we obtain the original plaintext , as desired.
Note that the decryption process is essentially the same as the encryption process. We simply need to switch left and right and use the keys in reverse order. Therefore, both the sender and receiver use a common key and they can use identical machines (though the receiver needs to reverse left and right inputs).
So far, we have said nothing about the function . In fact, any would work in the above procedures. But some choices of yield much better security than others. The type of used in DES is similar to that which we describe next. It is built up from a few components.
The first function is an expander. It takes an input of six bits and outputs eight bits. The one we use is given in Figure 7.2.
Figure 7.2 The Expander Function
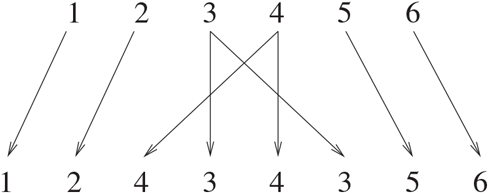
This means that the first input bit yields the first output bit, the third input bit yields both the fourth and the sixth output bits, etc. For example, 011001 is expanded to 01010101.
The main components are called S-boxes. We use two:
The input for an S-box has four bits. The first bit specifies which row will be used: 0 for the first row, 1 for the second. The other three bits represent a binary number that specifies the column: 000 for the first column, 001 for the second, ..., 111 for the last column. The output for the S-box consists of the three bits in the specified location. For example, an input of 1010 for means we look at the second row, third column, which yields the output 110.
The key consists of nine bits. The key for the th round of encryption is obtained by using eight bits of , starting with the th bit. For example, if , then (after five bits, we reached the end of , so the last two bits were obtained from the beginning of ).
We can now describe . The input consists of six bits. The expander function is used to expand it to eight bits. The result is XORed with to produce another eight-bit number. The first four bits are sent to , and the last four bits are sent to . Each S-box outputs three bits, which are concatenated to form a six-bit number. This is . We present this in Figure 7.3.
Figure 7.3 The Function

For example, suppose and . We have
The first four bits are sent to and the last four bits are sent to . The second row, fifth column of contains 000. The second row, last column of contains 100. Putting these outputs one after the other yields .
We can now describe what happens in one round. Suppose the input is
and , as previously. This means that , as in the example just discussed. Therefore, . This is XORed with to yield . Since , we obtain
The output becomes the input for the next round.
For work on this and another simplified DES algorithm and how they behave under multiple encryption, see [Konikoff-Toplosky].
