

Security
Each IBM FileNet P8 module has its own functionality, but they are all built on top of the IBM FileNet P8 Platform with Content Engine, Process Engine, and Workplace or Workplace XT, which are described in earlier chapters. The support for security around authentication and access control of processes and content of these products is provided by the core platform. This chapter describes the security issues to consider in an enterprise environment, how IBM FileNet P8 addresses them, and how to manage security effectively in an IBM FileNet P8 environment.
This chapter covers the following topics:
8.1 Authentication and authorization
This section describes how the IBM FileNet P8 Platform interacts with other enterprise systems to perform authentication. The various types of objects, services, and operations that can be protected using access control are discussed and how authorization is carried out for those elements.
8.1.1 Terminology
It is important to differentiate between authentication and authorization.
Authentication deals with asserting the unique identity of a user or a service, based on one or more credentials the user must provide, for example, a personalized secret password, an individual keycard, or a fingerprint. Users and services are instances of a more general concept: the security principal. A security principal is an entity that can be authenticated by a computer system or network. Authentication is the process of validating and confirming the identity of such an entity.
Authorization is about defining and regulating which permissions a given user has for a given object, which might be the permission to add a text annotation to a specific document in an ECM system, for example.
Authorization allows and also denies access rights. The following terms are used in relation with authorization:
•Explicit access right: The given access right (allow and deny) will explicitly be named in the access control list (ACL) of a given object.
•Implicit access right: All access rights that are not explicitly set will be implicit denied.
•Direct access right: The access right will be added straight on the ACL of a given object (either by default instance security or manually editing the ACL of a given object)
•Inherited access right: The access right will be related by reference to another object’s ACL
8.1.2 Authentication in IBM FileNet P8
IBM FileNet P8 must use a directory server to authenticate against and be able to look up user group membership information using Lightweight Directory Access Protocol (LDAP). Starting with version 4.0, IBM FileNet P8 uses the application server’s built-in support for authentication to a central directory server.
IBM FileNet P8 currently supports the following directory servers:
•Microsoft Active Directory 2003, 2008 SP1+, 2008R2
•Microsoft 2003 Active Directory Application Mode (ADAM)
•Microsoft 2008 SP1+, 2008R2 Active Directory Lightweight Directory Service (AD LDS)
•IBM Tivoli Directory Server 6.0, 6.1, 6.2, 6.3
•Sun Java Directory Server 5.2 SP3+, 6.3+; 7.x
•Novell eDirectory 8.7.3, 8.8.x
•CA Directory
•Oracle Internet Directory 10g (10.1.4.0.1+), 11g
The current list of the supported authentication providers is in the IBM FileNet P8 Hardware and Software Support Guide, which is available from the IBM web site at:
Also, see the Support Matrix of each directory server for lookup of supported directory features.
FileNet P8 supports two ways of authentication:
•Java Authentication and Authorization Services (JAAS)
•Web Services Security standard (WS-Security)
The following descriptions summarize the various supported default methods of authentication within FileNet environments. For detailed information and possibilities to enhance the standard feasibility, see the authentication area within the security section of the information center:
Java Authentication and Authorization Services
The FileNet Workplace and the Workplace XT use JAAS authentication in container-managed authentication mode. In this mode, the deployment descriptor for the application specifies the security constraints required to access application pages. Perimeter authentication is used for standard single sign-on (SSO) implementations of the FileNet modules. IBM Tivoli Access Manager and CA SiteMinder are currently qualified for FileNet 5.0.
Some limitations around SSO have to be considered:
•JAAS-based SSO integration is available only to J2EE-based clients (clients who can perform a JAAS login). This type of client includes most of those that are browser-based and work with a J2EE-based presentation-tier server.
•JAAS-based SSO integration generally does not extend to .NET-based clients or pure web-services-based clients.
•JAAS-based SSO integration is generally available only if the client's J2EE environment is supplied by the same application-server vendor hosting the Content Engine application.
•The configuration of SSO solutions generally requires a high level of product-specific expertise. Before installing a FileNet P8 solution, customers must work with their SSO and J2EE application server vendors to correctly configure the single sign-on environment. The industry-leading SSO products are designed to be highly flexible, supporting a wide range of credential types and configuration options. FileNet can only test a limited number of the infinite possible combinations of SSO vendor product configurations and application servers.
•In all cases, the third-party SSO product must be configured to work with the same underlying directory service (for example, Microsoft Active Directory and Novell e-Directory) used to resolve user and group credentials within FileNet P8.
After a caller is authenticated by a J2EE Servlet container, if the Servlet subsequently calls an EJB, the Servlet Container is required to propagate the caller's identity (JAAS Subject) to the EJB. Figure 8-1 on page 195 shows the container-managed authentication case as an example using forms-based authentication to authenticate the caller against an Active Directory service.

Figure 8-1 JAAS container managed authentication
The step-by-step walkthrough for the authentication scenario in Figure 8-1 is:
1. A user attempts to access a Servlet-based application.
2. The J2EE application server redirects the user to a page that requires credentials.
3. The user enters credentials and submits them to the server.
4. The J2EE server validates the user’s credentials through JAAS.
5. The J2EE server creates JAAS principals and subject objects using the Active Directory JAAS Login Module and places them in the user's session.
6. The J2EE server redirects the user back to the application page that was originally requested.
7. The Servlet container looks for a user principal available on the incoming request.
8. After invoked, the servlet makes a call to the P8 Content Engine server, and the user's JAAS subject is propagated to the EJB container in which the Content Engine resides.
Because of this approach, the only piece of information that the Content Engine uses from the JAAS context is the identifier of the user. Regardless of the JAAS module used, this identifier must be consumable by the Content Engine's configured LDAP user and group lookup filters. Typically this is accomplished by using the LDAP common name field, for example, the user name on the system.
The Content Engine does not use JAAS to get any information about group membership, roles, or permissions on objects. All group membership is looked up through LDAP by the Content Engine. All permissions are stored in the relevant Content Engine or Process Engine databases for that particular user's unique identifier. For an IBM FileNet P8 system that is linked to Active Directory, for example, the unique identifier is the user's SID, which means that the LDAP directory schema does not need any changes to it to support an IBM FileNet P8 solution. The only change that is required is creating users and groups to manage security of the system.
|
Lookup: In IBM FileNet P8 4.0 and above, all authentication and group membership lookup is delegated to the Content Engine. The Process Engine no longer performs its own lookups directly to the Directory Server, which
simplifies the configuration of Authentication and Single Sign-On. |
Although the JAAS standard is designed to abstract authentication and authorization, it occurs at the cost of mapping constructs into a tight JAAS model. The Content Engine has fine-grained support for access control, so it cannot use the Java security access control model. Many JAAS providers also do not support the more advanced security features of the most common directory servers. An example of this is Microsoft Active Directory's support for multiple forests with multiple domains. As such, IBM FileNet P8 performs its own group membership lookups and maintains its own access control lists internally.
This greater flexibility requires the developers to write code specifically to talk to each directory server. As a result, IBM FileNet P8 supports a specific subset of the most prevalent directory servers that are available on the market.
WS-Security
Two WS-Security profiles, the user name Token profile and the Kerberos profile, are supported by FileNet P8. Support for additional standard profiles and nonstandard WS-Security compliant approaches can be integrated with FileNet P8 Web services, using the FileNet P8 Web Service Extensible Authentication Framework. FileNet P8 does not provide any explicit support for SAML tokens. However, the Web Services Extensible Authentication Framework can be used to build support for authenticating through SAML-based credentials within FileNet P8 applications.
Figure 8-2 illustrates the WS-Security authentication.

Figure 8-2 WS-Security authentication
The steps for the authentication scenario in Figure 8-2 are:
1. For authentication purposes, the client logs into the Windows domain. The operating system collects the user's name and password and sends them to a KDC.
2. The KDC works with a directory service to validate the user's credentials and returns a ticket-granting ticket (TGT) to the caller.
3. Because the client wants to access a particular server, a ticket-granting exchange must occur. The client sends a second request to the KDC, specifying the service that it wants to access. (If the client was previously granted a service ticket that has not yet expired, then steps 3 and 4 are skipped).
4. The KDC issues a service ticket that grants the caller access to that service.
5. The client sends its request with the service ticket encoded in a WS-Security Kerberos token to the server.
6. The Web service listener on the Content Engine server performs a JAAS login using credentials supplied in the incoming WS-Security header.
7. The JAAS Login Module validates the client's ticket. No round-trip to the KDC is necessary. The server can use its own key (obtained from the KDC at startup time) to validate service tickets. The Login Module produces a valid JAAS subject based on the successful validation of the ticket. This JAAS subject is returned to the Content Engine Web service listener.
8. The Content Engine Web service listener passes the call along (with valid JAAS subject) to the Content Engine EJB layer.
For limitations concerning Microsoft’s Kerberos implementation, refer to the security information provided in the IBM FileNet P8 Version 5.0 information center.
Process Engine authentication
The Process Engine provides two different algorithms for authentication:
•Authenticating the Process Engine Java API client using Content Engine EJB transport and
•authenticating the Process Engine Java API client using the Content Engine Web Service transport.
Process Engine Java API client using Content Engine EJB transport
Figure 8-3 on page 199 shows the authentication process for the Process Engine Java API client using Content Engine EJB transport.

Figure 8-3 Process Engine Java API client using Content Engine EJB transport
Figure 8-3 shows the two-level authentication process, where the client first authenticates with JAAS. The client then authenticates with Content Engine, with the application server validating the JAAS credentials by invoking one of the configured Login Modules to confirm that the client's credentials are of a type accepted by this server and that they are valid. This process establishes the caller's identity and provides access to FileNet P8.
In detail, the following steps are executed:
1. The Process Engine client performs a JAAS login using the Login Module configured in the client environment. This login probably occurs before any interaction occurs with the Content Engine or Process Engine APIs. It can happen automatically as a result of a J2EE configuration, or the client can invoke the Login Module programmatically.
Depending on what Login Module is in use, the Login Module can make a call to the enterprise directory service, possibly through a proxy or some intermediate SSO solution.
2. The Process Engine Application makes a call to the Process Engine Java API.
3. The Process Engine Java API sees that the client is not authenticated to FileNet P8 yet, and therefore makes a call to the Content Engine Java API to obtain a FileNet P8 identity token.
4. The Content Engine Java API makes a call to the server. At the Content Engine server, the call arrives at the J2EE application server's EJB container with the caller's JAAS Subject. The application server examines its security policy configuration and how the Content Engine EJB is configured to determine what security policy is in place. The application server determines whether the JAAS Subject associated with the incoming request matches one of the authentication providers that are configured and enabled for use with the EJB. If it does, the application server makes a call to this authentication provider which performs any necessary checks on the JAAS Subject (this might involve contacting a directory service or SSO provider to validate the Subject). If any part of this application server authentication process fails, an appropriate error is returned to the caller (this occurs before any logic within the Content Engine EJB is invoked).
5. If the incoming JAAS Subject is validated by the application server, the call is passed through to the Content Engine EJB, and the JAAS Subject is available to the Content Engine EJB.
6. Within the Content Engine EJB, the Principal name is extracted from the JAAS subject, and searched for in the Content Engine user cache. If not found, Content Engine calls the enterprise directory service to expand the caller's identity information.
7. The EJB processes the incoming request. In this case, a FileNet P8 identity token is created and returned to the caller (the Process Engine Java API).
8. If all the previously mentioned steps are successful, the Process Engine Java API now has a FileNet P8 identity token, obtained from a Content Engine server. The Process Engine Java API makes a call to the Process Engine server, passing the identity token as a parameter. The Process Engine server examines the identity token, and the signature on it is validated. If the signature is valid, the Process Engine server trusts that the token and the user identified by the token are valid.
9. This optional step is unrelated to the authentication process, but occurs in many cases. In this step, Process Engine wants to retrieve the detailed user information (full name, DN, email address, group memberships, and so on). It does so by calling Content Engine (9a) to retrieve the requested user and group objects.
Process Engine Java API client using the Content Engine Web Service transport
Figure 8-4 on page 201 shows the Process Engine Web service listener, which is always co-resident with the Content Engine server.
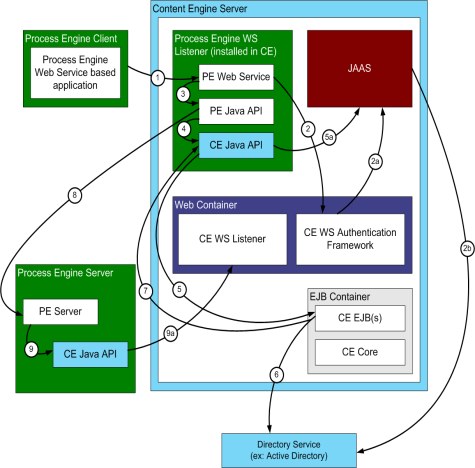
Figure 8-4 Content Engine responding to Process Engine Web service-based call
The following steps occur as Content Engine responds to a Process Engine Web service-based application call:
1. The Process Engine client sends a web service request to the Process Engine Web service listener.
2. The Process Engine Web service listener obtains the JAAS subject by using the Content Engine Web Services Authentication Framework, which expects to find the user name and password in the SOAP Header based on the WS-Security user name Token profile.
3. The Process Engine Application makes a call to the Process Engine Java API.
4. The Process Engine Java API sees that the client is not authenticated to FileNet P8 yet, and therefore makes a call to the Content Engine Java API to obtain a FileNet P8 identity token.
5. The Content Engine Java API makes a call to the Content Engine EJB home interface with the JAAS Subject obtained in step 2.
6. Within the Content Engine EJB, the principal name is extracted from the JAAS subject and searched for in the Content Engine user cache. If not found, Content Engine calls the enterprise directory service to expand the caller's identity information.
7. The EJB processes the incoming request. In this case, a FileNet P8 identity token is created and returned to the caller (the Process Engine Java API).
8. If all the previously mentioned steps are successful, the Process Engine Java API now has a FileNet P8 identity token, obtained from a Content Engine server. The Process Engine Java API makes a call to the Process Engine server, passing the identity token as a parameter. The Process Engine server examines the identity token, and the signature on it is validated. If the signature is valid, the Process Engine server trusts that the token and the user identified by the token are valid.
9. This optional step is unrelated to the authentication process, but occurs in many cases. In this step, Process Engine wants to retrieve the detailed user information (full name, DN, email address, group memberships, and so on). It does so by calling Content Engine to retrieve the requested user and group objects.
|
Supported credentials: The only credential type supported for this scenario are user name and password credentials. The Process Engine Web service does not support the Web Services Extensible Authentication Framework (WS-EAF).
|
ECM Widget integration
IBM ECM Widgets are only available for IBM WebSphere Application Server- based deployments. The user will login through Business Space or Lotus Mashups (depending on which container was installed). When the widgets are set up, Business Space (or Mashups), Workplace XT, and the ECM widgets war are put in the same WebSphere Application Server profile and configured for SSO so that they can share the login session through WebSphere Application Server LTPS. The Process Engine representational state transfer (REST) services and an internal ECM widgets-provided private REST service that communicates with Content Engine are installed as servlets in Workplace XT.
Figure 8-5 on page 203 shows the Widget integration.
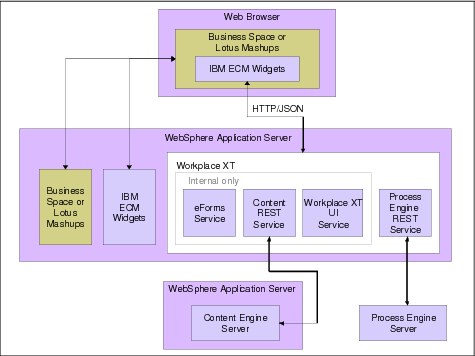
Figure 8-5 Widget integration in IBM FileNet P8
For additional information about access roles for Widgets and the handling with IBM WebSphere Business Spaces see:
8.1.3 Separated authorization
While authentication and authorization are fundamentally different in nature, they often are addressed with the same types of tool and with exactly the same tool instances, namely the same enterprise directory (respectively LDAP provider). This directory contains user and credential information for authentication and group and group membership information for authorization.
Authentication can be used commonly for all IT applications of an organization because the users are the same. The leading advantage having a common authentication is the ability—as long the application will support this kind of authentication—of a Single Sign-On (SSO).
For various reasons it might be necessary to separate authentication and authorization, which can be assigned to individual applications having their own directories for authorization purpose.
Reasons for separated authorization are, for example:
•The used LDAP already has a huge amount of groups and group memberships so that the security information exceeds the configurable Kerberos limits.
•Limited or forbidden access to the default LDAP.
•Organizational reasons.
IBM FileNet P8 allows for this separation following the concept of an application server channel for authentication and a Content Engine channel for authorization. The first is configured as part of application server security, while the latter is configured within the application (that is, the LDAP provider for the P8 Content Engine application).
In real-life projects, the separation of those two can be implemented with the application server channel pointing to a Kerberos ticket validation authority and the Content Engine channel pointing to an application specific Active Directory Lightweight Directory Services LDAP provider holding the group membership information to represent the permission groups and roles used in the IBM FileNet P8 environment.
To enable the separation, there must be a custom application established to ensure that the following requirements are fulfilled:
•Every user-account must have its equivalent in the authentication directory as well as in the authorization directory. Changes (for example, disabling of accounts) must be synchronized.
•Group memberships must be related in the authorization directory.
|
Note: Usually not only the application that technically fulfills these requirements (How will that be managed) must be individually created, but the definition of the user/group relationships must be automated (Why will the given relationship be created) by custom applications as well.
|
As of IBM FileNet P8 5.0 a major change in the use of the LDAP was implemented. Prior to release 5.0, the Security Identifier (SID) must have been related to the GUID of the used LDAP. As of Release 5.0, the LDAP attribute(s) used for the SID can now be chosen during the initial set up of Content Engine Directory Configurations:
•When set, values from the configured SID attribute are used for SIDs in Content Engine permissions rather than those from the default SID attribute.
•Can use the Distinguished Name (DN) as the SID attribute even though the DN is not an attribute in LDAP servers.
•Can set one SID attribute for users and another for groups.
•The configurable SID is set using IBM FileNet Enterprise Manager (FEM) or using the new Content Engine API properties: UserUniqueIDAttribute and GroupUniqueIDAttribute (which can be set only on create).
|
Important: It must be ensured that the used login attribute value for authentication is unique. If more than one security user or group was found in the configured realms that has the given attribute value, a SECURITY_TOO_MANY_MATCHES error is displayed. Authentication is not possible for the given account. Content Engine requires this given attribute value to be unique across the configured realms.
|
8.1.4 Single Sign-On
The term Single Sign-On, or SSO, is often misused and generally implies that there is no manual sign required in several scenarios. For clarity, the following definitions of methods of sign on are used:
•Traditional authentication
User name and password-based sign on made manually by users.
•Single Sign-On (SSO)
This is when a client authenticates to the first SSO-protected service that they use and does not have to log into any other. In other words, users sign in only one time. Before a user request is handled, an SSO provider is called that intercepts the request and authenticates the user. The SSO provider can either be one of the currently qualified end-to-end solutions (IBM Tivoli Access Manager and CA SiteMinder) or an SSO vendor has provided Java Authentication and Authorization Service (JAAS) Login Modules that work with a given application server. This user session is then asserted as valid to the application, so the user is not again asked to supply their user name or password, which is the process when using SSO software, such as Tivoli Access Manager with WebSeal.
Typically, the same gate keeper SSO software is used across multiple Web interfaces and signing into one of these means the user does not need to sign into the others. Web application SSO protection systems, such as secure reverse proxy software like WebSeal, provide their own login page instead of using the underlying services’ login page.
A common mechanism for SSO is Kerberos, which is the underlying technology that is used in Windows Integrated Login, which uses the same method when passing Kerberos tokens to applications. For Windows Integrated Login, the user's machine retrieves the Kerberos token from the Directory Server during initial login and passes it directly to the application server to validate. In this situation, the application server itself acts as the intercepting third party. Instead of the application server presenting a login prompt, it asks for a token but does not prevent access to the underlying application if it is not present.
•Token passing
Token passing occurs between two web-based applications that share a trusted relationship. Within Workplace, for example, a user might click a hyperlink that opens an Enterprise Records application. This URL also holds the user token so that Enterprise Records does not ask the user to log in again.
Notice that Single Sign-On requires third-party software to validate the user, which allows developers to abstract out any authentication code from the underlying application. Organizations can implement the same security access restrictions across all compliant applications, which is exactly what the Content Engine supports through JAAS.
The method used to assert credentials to a service where access is controlled by gate keeping SSO software can be one of two types. Under the first approach, some products can be configured to fake the login to the application, which allows the SSO software to look up the user name and password and passes that into the login box of the Web application being used. This method logs in the user in the background and then performs the user's request. The protected application has no idea that the client has not typed in an actual user name or password. This method is useful when adding SSO support to older applications that do not check for JAAS contexts.
The second method, and the method that Workplace XT uses, is to assert a JAAS context to the application server and have the application check for a valid context before forcing a manual login. This context can then be passed through the application stack to other JAAS-enabled software with which it communicates, such as the IBM FileNet P8 Content Engine and Process Engine. Figure 8-6 on page 207 shows a typical process for how Single Sign-On works with a third-party SSO provider.
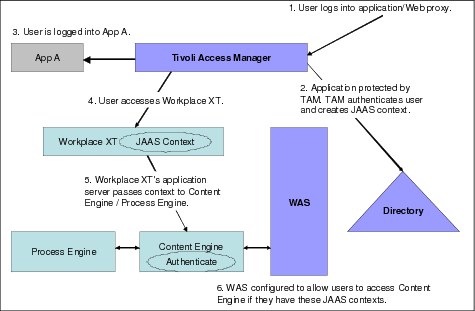
Figure 8-6 Typical Single sign-on (SSO) authentication behavior
Some application servers support token or SSO-based authentication themselves. An example of this is the WebSphere 6.1 support of the Simple and Protected GSSAPI Negotiation Mechanism (SPNEGO) client handshake method and in particular the Kerberos token that can be retrieved using that method. This requirement is common, especially in organizations that widely use Windows Integrated Login for their employee-accessed applications.
|
Note: The Content Engine can be used with any JAAS context configured in the application server. For latest support information, refer to the hard- and software requirement information provided in Hardware and Software Requirements Version 5.0 chapter Directory servers at:
|
There is a wide range of SSO authentication options that are available today. They are typically tightly linked to the application server and directory server being used. For a list of specific IBM FileNet P8 versions that are supported for each configuration, check the latest IBM FileNet P8 Hardware and Software Support Guide, which is available on the IBM web site.
For more information see:
•IBM Redbooks publication
Single Sign-On Solutions for IBM FileNet P8 Using IBM Tivoli and WebSphere Security, SG24-7675
•IBM Information Center IBM FileNet P8 section security subsection SSO:
•IBM Information Center IBM WebSphere Application Server section security subsection SSO: http://publib.boulder.ibm.com/infocentre/wasinfo/v6r1/index.jsp?topic=/com.ibm.websphere.express.doc/info/exp/ae/csec_sso.html
8.2 Securing core P8 components and resources
The IBM FileNet P8 modules offer much functionality that can be secured independently. In this section (8.2, “Securing core P8 components and resources” on page 208), a high-level summary of each component and the circumstances under which it makes sense to secure them are described. These areas are discussed in more detail in the following sections (as of chapter 8.3, “Access to information” on page 214).
Two different types of security must be discussed: securing documents and metadata from misuse and unauthorized access and the security that is needed for administrative purposes, such as installing and maintaining the system with all its facets.
8.2.1 Content Engine
The Content Engine has the richest set of authorization access controls of any part of the IBM FileNet P8 Platform, which is necessary to satisfy a range of use case scenarios. Thinking about security for the Content Engine is naturally thinking about access to document content and metadata but, in reality, access control goes far beyond that.
The Content Engine supports a wide range of permissions some of which are applicable only to certain types of objects, for example, the Major Versioning or View Content permissions are only applicable to instances of the document class and its subclasses. The View All Properties permission is applicable to documents, custom objects, folders, and many more objects in the Content Engine. The most commonly used permissions are described in chapter 8.3.1, “Security of Content Engine objects” on page 215.
At the heart of all the methods of assigning permissions in the Content Engine is the concept of Access Control Entries (ACEs). An ACE entry links a permission to a user or group in the directory server. ACEs are contained within an ACL in IBM FileNet P8 terminology that is attached to a Content Engine object.
ACLs are assigned to an object and are not classed as objects in their own right, which means that one cannot assign the same ACL to multiple objects. The Content Engine does, however, check whether newly created ACLs are identical to ones that already exist within the system. If the new ACL is the same as one that already exists, the Content Engine only stores one copy. This function is transparent to applications that are built on top of the Content Engine and allows for efficient caching of permissions.
The security objects that the Content Engine supports are Marking Sets, Security Policies, Document life cycle Policies, Dynamic Security Inheritance Objects, and Default Instance Security descriptors, and each of these are described in subsequent sections. An instance of a Content Engine object, such as a Document, maintains its own list of instance security, independent of the previously mentioned security mechanisms. This is populated when an instance is created by the Default Instance Security settings of the document class or specified explicitly by the application that added the document.
Workplace XT, for example, has the concept of Document Entry Templates. There can be many types of Entry Templates for a single class of document that the user chooses. These templates can set default values for properties, set a default filing location, and specify security ACEs. They are application-level constructs that are independent of built-in descriptors that are used within the Content Engine.
Entry Templates are useful in certain circumstances, for example, if a clerk enters a document to the Content Engine it is reasonable that the ACLs are defined automatically without any user intervention.
An interesting capability of the highly granular security model in the Content Engine is that it is possible to lock system administrators out from viewing the content using marking sets but still allow them to effectively maintain the system. This feature is especially useful in organizations, such as those in Financial Services, Healthcare, or Defense, where the need to secure information separately from the infrastructure might be a requirement. Because it is possible to lock such employees out of accessing Content Engine information, it can be ensured that stringent security policies cannot be circumvented through administrative or maintenance access.
8.2.2 Process Engine
The Process Engine has a concept of User Queues, Work Queues, and Component Queues. A user queue restricts access to work items in that queue to only the specific user that is assigned in the workflow definition. A Work Queue is accessible by multiple users and groups who all share a similar role within a workflow.
The following list contains IBM FileNet P8 terminology that is used in the context of workflows:
•Queue: A list of active work items grouped logically. A queue can contain several types of activities to be worked on by groups or users with allowed access (based of the particular security definitions) to that queue.
•Step: An item of work to be completed by either a user or a background system.
•Process Map: Also called a workflow definition. An executable definition of steps, routing conditions, and fields to be carried out by the Process Engine.
•Process: Also called a workflow. A running instance of a Process Map with its own data values and processing history.
•Isolated Region: An area in the Process Engine database that contains a group of processing queues, their configurations, related transferred workflow definitions and dependant work items and their related processing entries.
•Roster: A workflow roster is a database structure that stores information about a group of workflows in an isolated region. An isolated region can contain more than one roster.
A Component Queue is used to interact with instances of a Java class to perform some system task, which can be to file a document in a particular location set, fetch a document's properties, or update document security. Because this component is a system process, it is possible to specify a particular JAAS stanza (configuration) to use and the user name and password to pass to the configured login modules, for example, login modules exist for user name and password authentication to the appropriate Process Engine, Content Engine's Java APIs.
It is also possible to construct a component that asserts its own custom JAAS context using standard Java code for cases where it might be needed to interact with other third-party systems. This action is dependent on how the component is coded by the developer and independent of IBM FileNet P8.
Certain IBM FileNet P8 add-on products extend the security that is available in the Work and User Queues to restrict the list of work items that are displayed in the interface. Business Process Framework (BPF), for example, can be configured to specify an inbasket configuration that restricts a particular queue to a specified role, which can be further restricted by specifying that only a single step type is shown in this inbasket, or by constructing a queue filter to show only certain items based on the value of a process property. A good example of this is when there are junior and senior staff members with differing access authority. A Junior Approver queue filter can be created to restrict the list of pending credit approvals to those credit requests that are less than $10,000. This feature is also a useful way to limit the number of work items being displayed for a particular queue because it is possible to create more than one inbasket that lists a subset of the work items that are available to that user in the queue.
8.2.3 IBM FileNet P8 user interface access roles
The IBM FileNet P8 user interfaces (UI) extend the concept of user and group-based access control by restricting who can see and use certain functionality that is available in the interface to particular users and groups.
A Workplace XT role, for example, is simply a list of users and groups. An authors role can be created to allow only certain people to see the “Add document” or “Check in” user interface actions. This approach covers all actions that are available from the right-click document and folder menus and on the property pages for objects. Roles restrict who can see the main pages, such as Browse, My Workplace, Tasks, and Search.
Roles are commonly used to restrict who can see advanced authoring tools, such as the Search Template Designer or Process Designer. There is even a special role, called P8BPMProcessDesignerEx (is introduced when installing and configuring IBM FileNet Connector for Microsoft Visio), that lists who can see the Microsoft Office Visio diagram import option within the Process Designer applet.
Business Process Framework has its own concept of roles. BPF can be configured to use LDAP group integration where the role name is the same as a group in the directory server. Another alternative is to link a BPF role directly to an existing Workplace role with the same name, which is useful if your users access both user interfaces because it is only necessary to specify the members of each role one time rather than for both products. Another benefit is that users of BPF can have access to their queues removed from the Tasks interface of Workplace, which forces them to go through BPF to work on their tasks.
My Workplace acts as a mini portal where custom pages can be configured to show certain folders, search results, or actions. These pages can be restricted down to certain Workplace access roles. This restriction is particularly useful where an organization wants to deploy a configurable portal solution for ECM and BPM but does not want the overhead or cost that is associated with a full-blown enterprise portal solution.
8.2.4 Security aspects for installation and maintenance
Besides the security configuration for accessing the FileNet P8 environment for business purposes, the original intention of introducing an ECM system is that there are administrative security requirements for installing and maintaining the different modules.
As the general installation conditions vary from the dedicated security requirements of the contemplated environment. Usually production environments must fulfill the highest requirements within a dedicated company, and it has proven its worth to implement at least one test environment with a comparable security configuration.
Security requirements for installing IBM FileNet P8
There are various systems touched, when installing the core modules of the IBM FileNet P8 modules. This chapter discusses security requirements for security configuration of the communication between the systems because there are far too many different combinations in use. At this point, usually the following requirements must be considered:
•Protocols for communication between the modules under observance of the relation of the modules and the server—physical or virtual— the software is installed on. See also Figure 2-1 on page 20 for an extract of used protocols.
•Information concerning network addressing, such as MAC-addresses, IP-addresses, or ports.
•The use of ActiveX and JavaScript.
Also consider that firewalls can be required between client (applications) and servers as well as within the server environment. Additional purposes for administration, backup, recovery, and monitoring also must be regarded.
|
Administrative accounts: To prevent dependencies on single points of failure (loss of passwords) and to use dedicated and individual administrative accounts, configure groups instead of dedicated user accounts whenever applicable.
|
See Table 10-2 on page 361 in Appendix A, “User accounts” on page 359, which shows an overview of security requirements of user accounts related to a core IBM FileNet P8 environment (including database accounts) that are needed for installation and initial maintenance configuration.
For the current overview and a detailed description, see the security section in the Information Center subsection Users and groups required by FileNet:
Requirements for password changes
Table 8-1 lists the technical users for permanent configuration that can be involved when passwords within the core modules must be changed. For additional modules further changes might be necessary.
Table 8-1 Overview of the technical accounts
|
Function
|
Account name
|
Where to change and remarks
|
|
Content Engine service user (LDAP read access)
|
ce_service_user
(can also be used as ce_bootstrap_admin)
|
Logon to FEM as gcd_admin → Rootnode (Properties) → Tab: Directory Configuration
CEMPBoot.properties file
|
|
Content Engine system user (bootstrap administrator)
|
ce_bootstrap_admin
(can also be used as cce_service_user)
|
Logon to FEM as gcd_admin → Rootnode (Properties) → Tab: Directory Configuration
CEMPBoot.properties file
|
|
G CD Administrator
|
gcd_admin
(if used for component queue configuration)
|
Logon to PCC as pe_region_admin → Region[x] → Component Queues → CE_Operations (properties) → Tab: Adaptor
|
|
K2 security user
|
k2_sec_user
|
Logon to FEM as gcd_admin → Rootnode (Properties) → Tab: Verity Domain Configuration → select domain → Edit
|
|
Process Engine service user
|
pe_service_user
|
Logon to FEM as gcd_admin → PE Region Ids → select region → Tab: General
Logon to PTM as pe_region_admin → PE node → Tab: Security
Windows systems (autostart only)
Start → Control Panel → Administrative Tools → Services → <component> Services Manager → Tab: Log On where <component> is the name of the FileNet P8 component where Process Task Manager is running
|
|
Content Engine database accounts
|
ce_db_user
|
IBM WAS
Logon to WAS as ce_appserver_admin → Security → Global security → Area: Authentication → Java Authentication and Authorization Service → J2C authentication data
Oracle WebLogic
Logon to WL admin console as ce_appserver_admin Logon to admin console → Services → JDBC → Data Sources → data source of interest → Tab: Configuration → subtab: Connection Pool
JBoss
within the configuration file the username and password of the dedicated data source will be found in the xml-tag <data sources>
|
|
Process Engine database accounts
|
pe_db_user
|
Logon to PTM as pe_region_admin → PE node → Tab: Database → Tab: General
|
|
K2 operating system user
|
k2_os_user
|
Windows systems
Start → Control Panel → Administrative Tools → Services → Verity K2 6.1 Administration Server service → Tab: Log On
|
|
CSS operating system user
|
css_os_user
|
Windows systems
Start → Control Panel → Administrative Tools → Services → Content Search Service → Tab: Log On
|
The number of possible user account name-technical role combinations is quasi arbitrary and will have in real-life systems additional complex levels by additional modules and custom applications. Refer to the actual documentation for additional user account and group information, detailed configuration descriptions, and limitations.
8.3 Access to information
In this section, methods are described that are available within the Content Engine for creating access control lists. This information is available in more detail in the IBM Redbooks publication, IBM FileNet Content Manager Implementation Best Practices and Recommendations, SG24-7547.
It is of importance to the whole platform because all add-on products are built upon this security framework. In this section, specific references are made to where each method is used within expansion products and how overall security benefits from a platform architecture approach are showed.
Each securable object in the Content Engine maintains its own list of access control permissions, known as Access Control Entries. When several of the ACEs are attached to one object, it is known as an Access Control List. These ACLs can be specified at the document instance level to specify who can access particular documents. There are methods whereby ACLs can be reused across multiple objects, which is discussed later.
Any object within the Content Engine, from document class definitions to documents or custom objects to saved searches and folders, can have individual ACLs, which enable rich possibilities of predefined configurations to control inappropriate usage of these objects. Objects that shall not be used by unauthorized (relative to their access role) users, are not displayed or accessible without appropriate access rights.
The ACL of each securable object can be reviewed and defined by a security editor. The FileNet Enterprise Manager uses the security editor in the following three security tabs:
•Security: Displayed as part of the property sheet of all securable objects. (8.3.1, “Security of Content Engine objects” on page 215)
•Default Instance Security: Displayed as part of the property sheet of all securable classes. (8.3.2, “Default instance security” on page 221)
•Template Security: Displayed when the users accesses the General tab of a security policy and clicks Modify. (8.3.3, “Security precedence and inheritance” on page 223).
8.3.1 Security of Content Engine objects
To assign individual access rights or permissions of a current instance of a Content Engine object, the Security tab of the properties’ UI within the FEM can be used, as shown in Figure 8-7 on page 216.
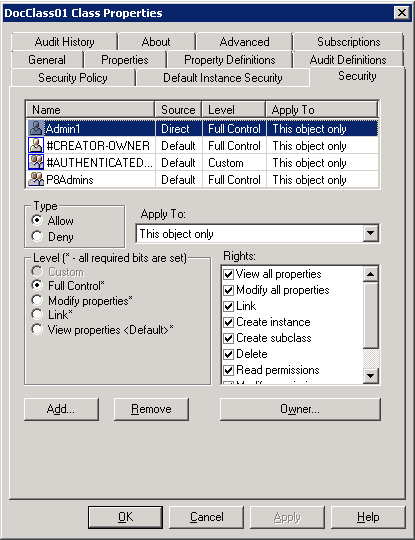
Figure 8-7 Class property security tab
Standard security levels can be used to group permissions together in the administration interface, as shown in Figure 8-8 on page 218. As needed, customized access levels can be individually defined for any selected group or user account.
Table 8-2 provides the symbols that are used in Figure 8-8 on page 218.
Table 8-2 Symbols
|
Symbol
|
Description
|
|
•
|
Indicates that dedicated access rights are available for the given standard access level
|
|
(•)
|
Indicates that dedicated access rights are only available for a subset of standard access level
|
|
*
|
Indicates deprecation
|
|
**
|
Indicates that an archive is deprecated
|
|
**
|
Indicates that it is defined in Workplace to include Modify permissions
|
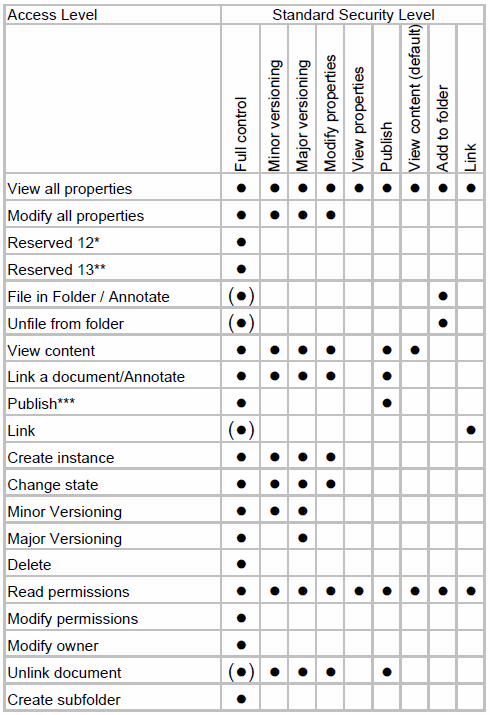
Figure 8-8 Overview of standard access rights level for Content Engine objects
Some of the rights in Figure 8-8 on page 218 are applicable to only some Content Engine objects. Table 8-3 is a list of which permissions are applicable to which objects.
Table 8-3 Object classes and permissions that affect access to them
|
Content Engine object class
|
Applicable permissions
|
|
Applicable to all
|
•View all properties
•Modify all properties
•Create instance
•Delete
•Read permissions
•Modify permissions
•Modify owner
|
|
Document
|
•Reserved 12
•Reserved 13
•View content
•Link a document
•Publish
•Create instance
•Change state
•Minor versioning
•Major versioning
•Unlink document
•create subfolder
|
|
Folder
|
•Reserved 12
•Reserved 13
•File in folder/annotate
•Unfile from folder
•Create subfolder
•Minor versioning
•Major versioning
•View content
•Change state
•Publish
|
|
Custom Object
|
•Link/annotate
|
|
Event action
|
•link a subscription
|
|
Other Classes incl.
Task
Task Relationship
|
•Link
•Create Subclass
|
|
Assigning permissions: It is possible to assign permissions to a Content Engine object that is not applicable to that class. This action is implemented to allow the inheritance of permissions from one object to another. See 8.4.4, “Dynamic security inheritance” on page 239.
|
A dedicated set of security configurations was established for Marking Sets, Object Stores, and P8 Domains.
Table 8-4 Content Engine object class and applicable permissions
|
Content Engine object class
|
Applicable permissions
|
|
Marking Sets
Only Full Control or custom access levels available
|
•Add marking
•Remove marking
•Use marked object
|
|
Object stores
Standard access levels
Full Control (F)
Use object store (U)
View object store (V)
|
•Connect to store F,U,V
•Create new objects F,V
•Modify existing objects F,V
•Delete objects F,V
•Read permissions F
•Modify permissions F
•Modify certain system properties F
•Modify retention F
|
|
Enterprise Manager [P8 Domain]
Standard access levels
Full Control (F)
Use stores and services (U)
|
•View all properties F,U
•Modify all properies F
•Create child objects F
•Delete child objects F
•Read permissions F
•Modify permissions F
|
Folders, Custom Objects, and Documents all have an owner property, which can be blank or point to a particular user or group. Whoever is assigned as the owner receives at least the following rights on the object:
•Read permissions
•Modify permissions
•Modify owner
By virtue of having the modify owner right, the owner also receives the read all properties right on the object; otherwise, the owner cannot see the owner property and therefore cannot modify it. If a user or group is given the modify any owner right on an object store, they are also given read all properties and modify owner rights on every object in the object store.
Markings and their constraints, which are discussed in chapter 8.4.1, “Marking sets” on page 229, are evaluated after the owner and object store permissions are assigned. As such, markings can be used to deny permissions that are granted to the owner of an object.
|
Assigning groups to the owner property: A group can be assigned to the owner property, which is useful where ownership of a document lies with a team rather than a user. Setting the owner to a group in this case gives anyone in that team the owner's rights. Over time, the group membership can be modified and no change to the owner field or access control list is required.
|
|
Evaluating the owner property: The owner property is evaluated after direct, template, and inherited permission sources. Any denial of those levels for the rights conferred by being an owner are overridden, and the owner still gets those permissions on the object.
|
8.3.2 Default instance security
Some securable object definitions can specify a Default Instance Security to apply to a new instance of this object when it is not provided by the application that is built on top of the Content Engine. Figure 8-9 on page 222 shows an ACL that is specified on a Content Engine document class object.
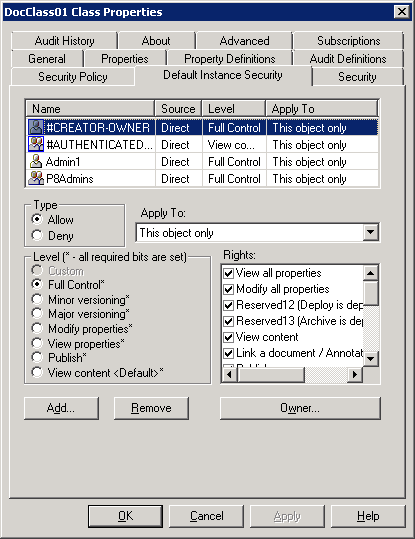
Figure 8-9 Default Instance Security on a document class object
The following Content Engine objects allow to define Default Instance Security:
•Document classes
•Other Classes
If a subclass of this class is created, these ACEs are copied to the new class. However, updating a higher-level class does not automatically update subclasses.
Within these ACLs, two special entries can be used:
•The #CREATOR-OWNER allows rights to be assigned to whomever added the document (or whomever is specified in the Owner field at creation time.
•The #AUTHENTICATED-USERS entry can be used to refer to any user who is logged into the system.
|
#AUTHENTICATED USERS: #AUTHENTICATED USERS as in different group must not be used for authorization purposes (beside exceptions). It is always advisable to create a role and user concept that defines dedicated access levels for the usage of the Content Engine. Explicit authorization must always be preferred to implicit allowed access.
Belated changes to existing ACLs for numerous mounds of objects can generate significant system load. Besides this technical limitation, the risk of unauthorized access by accident cannot be obviated.
|
The Owner of a document instance can also be specified at the class level. By default, this is left as #CREATOR-OWNER, meaning that the owner of the document is specified as the user who created it. This rule can be overridden, however, to point to another user or group on the system. The overridden owner of the document can be useful when the owner must always be assigned to a particular user or group of users. If the #CREATOR-OWNER is specified to have particular permissions on a document instance, rather than on a class' default instance security, then these permissions have no effect. When the document is created, #CREATOR-OWNER is determined and that user is assigned rights on the new document instance. So, if user1 logged in and added a document, and the default Owner field is left as #CREATOR-OWNER, any rights assigned on the default instance security tab to #CREATOR-OWNER are assigned to the user1 on the new document instance. In other words, the #CREATOR-OWNER permission entry does not exist on the instance. It instead shows user1 as assigned to those permissions.
8.3.3 Security precedence and inheritance
The elementary nature of the FileNet P8 modules is that every access to a given object (folders, documents, inboxes) must be authorized, as discussed in previous chapters. The authorization restrictions range from basic authorization for all authenticated users to granular restrictions on a user basis.
It is quite unlikely for any user in an organization to have access to perform all operations on a document or other objects of the ECM environment. There are instances where all users might have read permissions, such as for policy documents, but generally, all content is locked down to some extent. This lock down can be done individually for each and every object, but this is cumbersome and hard to manage.
There are often cases where it is useful for security to flow through various objects to a document. The classic example is in foldering, where it might be required that the security on the document reflects that of the containing folder. Another example might be a workgroup, such as an IBM Redbooks publication team, that specifies that a certain group of people have access to a set of documents. Perhaps the most classic example is security classification. These classification groups are created at an enterprise level and must be enforced to override or mask security permissions that are already on individual documents.
Before describing how authorization is calculated, the precedence of how these various security sources affect the target object must be discussed. The following list shows the highest priority security source first, followed by lower priority sources:
•Default or explicit (direct) Deny
•Default or explicit (direct) Allow
•Template Deny
•Template Allow
•Inherited Deny
•Inherited Allow
|
Permissions: A higher source of permission always overrides that of a lower source.
|
A source of default indicates that the security permission was assigned to the object through the default instance security mechanism that was previously mentioned. A direct permission is the same except it is assigned to the document instance directly rather than copied from the default instance security permission list. Both ways of assigning security result in explicit access rights on the given object.
Security Templates are assigned to an object based on the settings within its assigned Security Policy. These are permissions that are copied into a document's access control list when the document's state matches a corresponding state in the policy that has a security template configured. When a match exists, the permissions are copied to the document.
|
Security template assignment: A security template assignment only happens when a life cycle event occurs or an application explicitly assigns an application security template and not when the security is evaluated.
|
This behavior is similar to that of a document lifecycle policy. The difference is that a document lifecycle state change occurs when a custom application calls one of the methods to modify a life cycle on a document, not in response to a versioning action, which is the case for security policies. A particular document lifecycle policy state might or might not be configured to apply security permissions. For more information about security and document lifecycle policies, see 8.4.3, “Document lifecycle policies” on page 237.
Inheritance specifies that the security is carried forward from another object, which is different from the previous approaches because the ACEs are not copied into the document but are dynamically evaluated on-the-fly. This method is particularly useful from a management perspective because many objects can inherit security from the same source object. This method is used by the Security Folder property on a document and folder to indicate the object from which security settings are inherited. It is also used in property-based dynamic security inheritance that is described in 8.4.4, “Dynamic security inheritance” on page 239.
Figure 8-10 shows the access rights for a given object assigned by the Default Instance Security. Figure 8-11 shows the same object after assigning additional rights by inheritance from a Security Folder. The inherited rights are marked by a small folder symbol and do not overrule the direct access rights.

Figure 8-10 Standard explicit direct rights (sample)

Figure 8-11 Access rights with inherited rights from Security Folder (sample)
In Figure 8-11, User1 has explicit and direct View Content and View Properties rights and can view the content even having inherited Deny access rights. User2, in contrast, inherits the Full Control access rights from the Security Folder. The example demonstrates the ability to enhance rights and the inability to restrict access rights by using inheritance by Folder Security.
The missing check box in every row of inherited rights indicates that they cannot be removed. Inherited rights cannot be changed either (To open the security page, click the user name, but no changes to the ACE are possible).
8.3.4 Calculating authorization
Extra security ACLs for a document, folder, or custom object can be inherited. Security is calculated in the following order with each rule taking precedence over those that follow it in the list:
1. Explicit permissions that are assigned to the object instances are evaluated. A permission is marked as default if it is applied from the document class' default instance security settings.
Explicit individual Deny authorization overrules implicit (for example, by group membership) Allow access rights.
2. Template permissions are evaluated. A template permission is assigned by a document lifecycle state change or security template. See “Security policies” on page 234 and “Document lifecycle policies” on page 237.
3. Inherited permissions are evaluated. These permissions can be from the Security Folder field or any Object Value Property that is defined with a Security Proxy Type of Inheritance. See “Dynamic security inheritance” on page 239:
a. If a Security Folder is specified, it is checked for any ACEs that are specified to apply to the selected choice of entities: This object and immediate children or This object and all children. As of P8 5.0, the new additional inheritance entities’ Immediate children, but not this object and All children, but not this object are available. An object can be filed in multiple locations but can have only a maximum of one Security Folder. This value is not set by the Workplace XT applications but by the means of the FEM. If the security folder is null (that is, not specified), no folder security is evaluated at any level.
b. If this folder has its Inherit from security parent folder setting enabled, this folder's parents, starting with the immediate parent, are checked for all ACEs that apply to this object and all children.
c. If all parent folders have Inherit permissions from parent enabled, eventually the root folder's security is checked, which is the top level of potential security inheritance for folders. By default, the root folder gives write permission to all users for all properties of any contained object in the object store. It is important to change this security on a production system.
4. The owner of the object is checked. If this is the user trying to perform the current action, this user is granted read all properties, read permissions, modify permissions, and modify owner rights on the object.
5. The containing object store's ACL is checked. Some object store permissions affect documents, folders, and custom objects. These permissions are write any owner and privileged write. The first of these permissions allows the specified grantee to change the object owner. The second allows a grantee to modify certain properties on any object in the object store. These properties are creator, date created, last modifier, date last modified, and date checked in.
6. If the document has a property whose value is from a marking set, the specified marking is evaluated. If the current user does not have the use right on the marking, then the security permissions specified in the constraint are removed (masked) from the computed permissions list. Thus if a user has modify content rights but is not granted a marking's use right, the constraint can be configured to remove this right.
|
Note: On the General Tab of the properties of documents, as of IBM FileNet P8 4.0.1, the deprecated inheritance function Security Parent is offered. When selecting the Inherit Security from folder option in the pull-down box, all folders that the document is filed in are displayed to configure security inheritance. The purpose of this behavior is to support custom applications without change. The actual Security Folder property does not require containment of the document by the folder.
|
Refer to 8.9, “A practical example” on page 269, for a practical example that uses multiple sources of security, including inherited security, to illustrate how setting security at one level can override other security without causing any problems or gaps in the platform security landscape.
8.3.5 Authorization calculation example
Now an example for authorization will be discussed, assuming that there is a need to control the view content on a document instance. Table 8-5 shows the security settings that affect this particular document instance and its view content permission. Owner or object store granted permissions are not discussed to keep things simple. It is assumed, for the example, that none of the users are the document owner or have special rights from the object store permission list. The underlined permissions are those that have the highest precedence in our example.
Table 8-5 View content permissions and their sources for a sample document
|
Permission source
|
User A
|
User B
|
User C
|
User D
|
|
Direct Deny
|
|
Implicit deny
|
Y (Direct)
|
Implicit deny
|
|
Direct Allow
|
Y (Default)
|
|
|
|
|
Template Deny
|
Y (Document life cycle)
|
|
|
|
|
Template Allow
|
|
|
Y
(Security Policy)
|
Y
(Security Policy)
|
|
Inherited Deny
|
|
|
|
Y
(Security Folder)
|
|
Inherited Allow
|
|
Y
(Security Folder)
|
|
|
|
Marking use
|
Y
|
Y
|
Y
|
N
|
|
Marking applied constraint
|
N/A
|
N/A
|
N/A
|
Deny
|
|
Effective permission
|
Allow
|
Allow
|
Deny
|
Deny
|
Security for User A
This document’s default instance security grants User A a view content permission on all new instances of the example document's class. User A is also explicitly denied this permission by a property that is assigned from a document lifecycle policy. An explicit direct permission has precedence over a template permission, which means that the default allow permission is still valid. User A is also granted the use right on a marking that is associated with the document, so the view content permission is not denied to User A by the marking constraint mask, which results in User A having an allow permission for view content on our sample document.
Security for User B
Neither the default instance security nor the document itself assigns User B a permission for the sample document, which results in an implicit deny because by default, the Content Engine denies permissions unless they are explicitly granted (as long as no general authorization by #AUTHENTICADTED USERS assigns access rights to all users). This document instance does have a Security Folder specified, explicitly granting User B the view content permission. User B also has use rights on the marking constraint mask, which results in User B having an allow permission for view content on the document.
Security for User C
User C has an explicit direct deny for the view content permission on the sample document. Even though an allow view content right exists from an applied security template, this has a lower precedence than the explicit deny. User C does have the use right on the marking, but this does not grant any extra rights to the document (a lack of the use right means the constraint mask denies the right). The effective permission is therefore to deny view content because of the explicit deny User C from the direct permission on the document.
Security for User D
No direct or default allow for view content is specified for User D; therefore, User D is implicitly denied the view content right for the same reasons that User B is. User D is, however, granted the view content right from an applied security template, so this takes precedence. The Security Folder has a deny view content permission entry, but this is of lower precedence than the allow view content from the security template. At this point, User D has an allow view content permission. User D does not, however, have the use right on the marking that is assigned to the document. As a result, the constraint mask is applied to User D’s rights, denying User D view content rights on the document. Markings mask or remove individual permissions from a calculated permission list, so this is the setting that is applied. User D is denied view content rights on the sample document.
8.4 Setting security across the enterprise
When the default security for a particular class of object is known at design time, it can be assigned in the default instance security tab of the class. However, it is often the case that these security settings are common across document types and roles. This section describes techniques that allow security to be managed on a broader basis versus micro-managing every object's individual ACL. This process has advantages for both manageability and reduction of the database size due to access control entries. This section also describes how means of implicit security definition can support the configuration of a small instead of a huge number of objects to administer object security.
8.4.1 Marking sets
Marking sets provide a means to manage access to objects on a global basis through the values of specially defined marking-controlled properties, which are properties whose permitted values are drawn from the properties that are defined in the marking set and which influence the access check according to the definition of the Marking. Marking sets provide a generalized form of mandatory access control, also called labelling.
It is a fundamental nature of a marking set that access rights can only be denied and not allowed. Marking sets operate by having a list of values called markings, where each has its own list of grantees who are given the use right by the marking. A property can then be created on an object whose values are taken from a marking set, which works much the same way as choice lists except that choosing a particular marking value affects the security of the document.
The following limitations are to be considered when handling marking sets:
•Marking Sets are defined globally for a given P8 Domain
•Marking Sets are related to properties. As properties are defined within a dedicated object store, they are only active within the object store(s) and the related properties
•Marking Sets can only be defined when creating a property. They might be changed after creation, but not added to an existing property
•Marking Sets are not collocating with Choice Lists
•The number of Marking Sets within a single P8 Domain is limited to 100
Although the document instance security settings are still present, the marking constraints are applied or masked over these, which makes markings useful when stringent security that cannot be overridden must be applied across a number of document classes. A classic example of this is military or intelligence applications where there is a pre-existing security framework. A marking for a document can be created such that setting the value to Top Secret denies all users in lower security groups access to the object.
To use objects marked by marking sets, two separate conditions must be fulfilled:
•At least the use of the marking set related to a given property must be allowed.
•The configuration of the marking set itself cannot prevent the dedicated action on the document.
|
Markings: A marking differs significantly from other security methods used in IBM FileNet Content Manager. Normally, permissions that are given or denied from specified users and groups are explicitly listed. With a marking, however, only users and groups that have at least the Use Right On are required to be specified. If a user does not have this right, their computed permissions are masked (denied) by the constraint permissions that are enabled on the marking.
|
The use of marking sets can be restricted to:
•Add Marking: Related values can be changed by the given user.
•Remove Marking: Related values can be deleted by the given user.
•Use Marked Objects: The related value assigns access rights to the given user s as defined in the related marking set.
If a given user does not have at least Use Marked Objects rights or has explicit Deny access rights on the marking set, the user is not allowed to use that object even if the explicit direct Allow access rights on the document.
There are two types of marking sets:
•Non-hierarchical: Apply only the constraints that are present on the selected marking value.
•Hierarchical: Apply all lower marking use rights prior to its own, which means that, for the previous example, the Top Secret marking only holds additional entries for users with Top Secret level access rather than re-list all the entries for Secret, Confidential, Restricted, and Public. This makes administration much easier and prevents oversights in security from occurring.
For clarification shall the following example serve as a model. It shall be necessary to ensure that all non-HR users cannot read the properties or content of all documents that have a department marking property of HR. A marking set is created called Department Set with several markings, one of which is called HR Department. It is specified, that the use right is given to the HR Department group as held in the directory server. A constraint mask for all of the permissions that shall be denied is added. In Figure 8-12 on page 232, notice that all permissions to groups other than HR are denied.
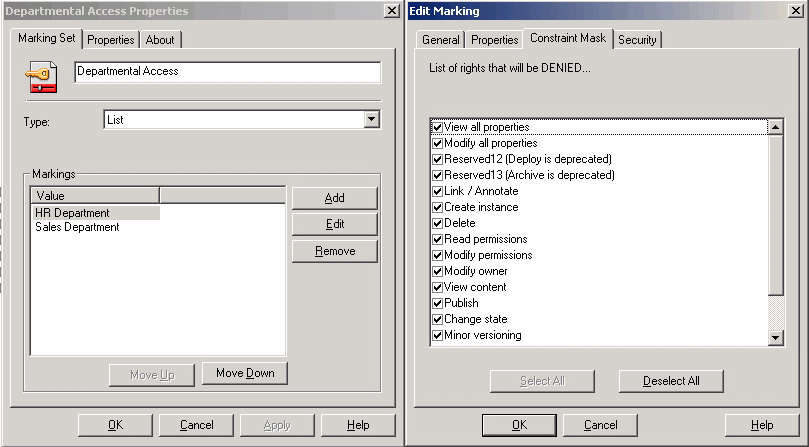
Figure 8-12 The marking set properties and marking properties dialog boxes
If a non-HR user tries to access the document, the user is prevented from reading the document's properties and content by virtue of the user not being in the HR Department group.
Implementing the equivalent security restrictions using permission lists requires specific enumeration of all groups that must not view content and properties, making security management across the organization far more difficult than using markings.
Markings do not exist at the object store level. They are configured on the IBM FileNet P8 Domain and as such can be re-used by any object store. This behavior must be considered when updating a marking that this has instant effect across the enterprise and not compulsive on a single object store. Multiple markings can be applied to the same document, which causes all constraint masks that are specified in the active markings to be enacted cumulatively.
Figure 8-13 on page 233 shows a sample security classification. A hierarchical marking set is created so that all access that is denied at the Restricted level is carried on to the Confidential, Secret, and Top Secret levels. Remember that a marking set propagates only the Add Marking, Remove Marking, and Use Marked Objects permissions. Permissions are only masked (and thus denied) by a marking if its constraints mask has specific permissions that are listed to deny. An hierarchical set that propagates Deny rights and implicit Allows (by not denying and assuming that the appropriate right was granted by direct ACL) in Figure 8-13.

Figure 8-13 Use permission propagated in security classification marking set example
As shown in Figure 8-13, hierarchical propagation has the effect of deny rights being propagated upwards and implicit allow rights being propagated downwards. In other words, if a user has use rights at the Secret level, they also receive use rights for all documents that are marked Confidential, Restricted, and Public.
On all markings other than Public, all permissions are specified in the constraint mask, which denies access to any object from anyone in the system who does not have the Use permission on the marking. For Public, an Allow use for all domain users was added. In our setup with Active Directory, all users are members of the domain users group. Consequently, no constraint mask for Public are added because it is not evaluated.
|
Markings: Markings allow content to be hidden from system administrators.A marking can be specified to deny the Modify Owner right to all users who
must not change a document, folder, or their security. The administrator can be included in this group. The Use Marked Objects right can then be assigned to all other users who need to change the document, folder, or their security. Adding a required property that uses this marking to the top level Document class (or Folder or Custom object) with the default value of the specific marking created enforces the marking for all new documents. In this way, administrator access is denied to any content within the system, while still allowing them to configure the system. |
Expansion products use the core functionality of the IBM FileNet P8 Platform and apply these capabilities to new problem domains. Marking sets are used extensively in IBM Enterprise Records to lock down content that is declared as a record. This marking prevents any user who is not a member of the Enterprise Records group from deleting or modifying the content and properties of any document version that is declared as a record. Setting marking set values can be a manual step, such as when an investigator accesses the document or an automated step during the records disposition process, checking, moving (to long term storage), or deleting a record during its life cycle.
This approach provides several advantages. The security mechanism in use is familiar to existing IBM FileNet Content Manager or IBM FileNet Business Process Manager (BPM) administrators, which makes it easier for administrators to start using an expansion product. Many of the groups and access control specifications might already be in place or can be re-used for an IBM Enterprise Records implementation. A customer also gets the added assurance of knowing this security feature was extensively tested in IBM FileNet Content Manager (or BPM) implementations.
|
Markings: Documents can have multiple markings. The effective constraint mask is calculated with all cumulative denials being applied.
It is also possible that a marking property can have more than one value. A document can, for example, be applicable to multiple departments, but might not be allowed to be accessed from anywhere else. Although it is allowed to assign hierarchical Marking Sets to multi-value properties, this is not recommended. Because an element in a hierarchical set inherits settings from lower precedence markings, it does not make sense to assign multiple hierarchical markings to the same property.
|
8.4.2 Security policies
Security policies provide a mechanism for automating changes to an object's ACL as its state changes, either through versioning operations or application-controlled state changes.
Security policies consist of security templates. These templates contain ACEs, just like an object instance's security settings. There are two types of security policy templates: version templates and application templates. A version template is assigned to a document when its versioning state changes (for example Released, In Process, Reservation, or Superseded). An application template, by contrast, is assigned by a custom application, explicitly setting the template through an API call.
This behavior makes security policies more decoupled from the document's properties. Permissions to apply do not need to be explicitly stated but rather change with the document's state. After this change is made, the permissions on the applicable security template are copied onto the document version. They are not dynamically resolved like they are for marking sets or dynamic security inheritance properties.
Whether the security policy adds the applicable template's entries to the document's security permissions or whether it completely replaces them can be specified. This option is particularly useful because each security template only needs to contain the changes to the document instance security that must be applied.
Security policies can be best thought of as objects that modify a document's security during its life cycle rather than as explicitly overriding security based on some manual action.
A default security policy can be assigned in the class definition settings dialog, as shown in Figure 8-14 on page 236. They can also be assigned to a specific version of a document later in its life cycle. However, changes to the current version's security policy is only processed the next time it is versioned because that is when the security templates are checked and applied. They cannot be applied to the current version and be expected to change the document's security immediately because that does not happen until some versioning state event occurs, such as Checkout.

Figure 8-14 Assigning a default security policy to a new instance of a class
In addition to the four default document states, custom or application states can also be created, which are useful in situations during a document's life cycle, during a managing process, or when it is known at design time who has access to a document.
Considering the example of a software company that produces and publishes documents, which are called technical papers. A technical paper can go through an authoring state at a minor version (such as 1.1, 1.2, and 2.4) and at an editorial state. After it is checked by an Editor, it can be promoted to a major version that is ready for publication. The security for these steps can be modified using versioning security templates. Considering that a member of the Legal team also checks the technical paper before it is published. The Legal team has access to the released version, thanks to a versioning security template. After they check the technical paper, they move its state to the Ready for Publication application state. This state prevents any further modification to the document and requires a custom application state to be specially created and applied to the technical paper class.
Using this method, technical papers are moved through their application-specific life cycle, modifying security along the way as most appropriate. This progressive movement is accomplished by configuring document states and security templates within the Content Engine and the process required no business process.
Of course there are situations where this approach falls short. An example might be, when security is not assigned to a group of people with a role, but rather it must be dynamically decided. This type of requirement is best accomplished within a business process, which is described in 8.5, “Gradual security requirement changes” on page 250.
There is also the issue where only one security policy can be assigned to a document at a given time. In certain situations, someone might want to add extra security to a document. An example might be adding a restriction on who can see a document by country because of specific local legislation. In this case, it is best to use a Marking Set or a Dynamic Security Inheritance Object, depending on the situation.
8.4.3 Document lifecycle policies
A mechanism similar to that provided by security policies is available for automating ACL updates as a document moves through the states defined by a document lifecycle policy. It is possible to create document lifecycle policies to have more granular control over how a document is accessed and worked on during its existence. If a simple document creation is considered, approval, and publishing example, a document life cycle can be used to set the visibility (view content permission) of a document at specific phases in its life cycle, as shown in Figure 8-15 on page 238.

Figure 8-15 A simple document editing, approval, and publishing life cycle
Security can optionally be assigned when a document transitions to a particular state. When going through approval and (re-)editing, the author's edit content rights might be temporarily removed and then added back again if a change is required. Not all states need to change security.
After a document is approved, all versioning and modification permissions are removed from both the content authors and content approver in the previous example. No further security modifications are needed until, for example, the document needs to be checked out for an update, so the Published template does not apply any security of its own.
It might be necessary to perform some system action based on changes in states, which is done by assigning a custom Java class as a life cycle action that is invoked whenever the state changes. For the example, it might be necessary to file the document in different locations after it is published, and then automatically move the life cycle on to the published state.
Any permissions that are assigned by a life cycle policy have a source of template and are therefore evaluated at the same level as security policies. A life cycle policy can be assigned to one or more document classes, but each class can only have one life cycle policy.
Document lifecycle policies can be useful if the processing requirement is simple and a full business process management solution is overkill.
8.4.4 Dynamic security inheritance
As mentioned in chapter 8.3.3, “Security precedence and inheritance” on page 223, the concept of security inheritance is a strong means for security design in IBM FileNet P8 environments. Rather than having a property value determine additional security on a document, the property, itself, specifies another Content Engine object from which to inherit the security settings.
In the previous chapters, explicit security settings set by default instance security or by configuring directly on the given object were described. They are not changed when the relative security source configuration is changed. This chapter describes means of security inheritance that dynamically change the ACLs of the related object whenever changes are made on the source of the inherited security settings.
The object that inherits the security still has its own direct security settings and they are not modified using this method, but they are supplemented by any inherited permissions. If a Content Engine object has direct, default, or template permissions, however, they have a higher precedence than inherited permissions.
For each ACE that is used for inheritance, five separate depths exist that must be configured individually. For the security definition, the security tab of the properties of the object to inherit from is used within the FEM, as shown in Figure 8-16 on page 240.
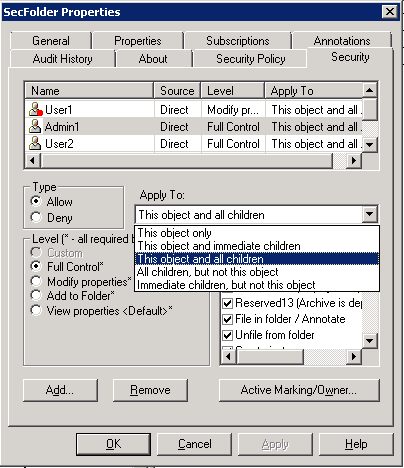
Figure 8-16 Possible configuration selection: security inheritance
In Figure 8-16:
•This object only: This ACE takes effect in access checking for the current object, but is not inherited by any children.
This is the default setting for new ACEs.
This is the default setting for new ACEs.
•This object and immediate children: This ACE applies to the object and is inherited by the parent object's children, but not by the child object's children. After inheritance takes place, the child ACE has an inheritable depth of This object only.
Use this option only if there is no structure beneath the given inheritance.
Use this option only if there is no structure beneath the given inheritance.
•This object and all children: This ACE applies to the object and is inherited by every generation of the parent object's child objects. After inheritance takes place, the child object's ACE has an inheritable depth of this object and all children.
Chose this option whenever the usage of the parent object and all its descendants are used with a similar configuration.
Chose this option whenever the usage of the parent object and all its descendants are used with a similar configuration.
•All children but not this object: This ACE is inherited by every generation of the parent object's child objects, but does not affect the parent object itself.
Use this option if the inherited security of a given group (or user) is different of the parent object. This results, for example, when objects used for security inheritance need separate administrative access rights for the security parent and the security children.
Use this option if the inherited security of a given group (or user) is different of the parent object. This results, for example, when objects used for security inheritance need separate administrative access rights for the security parent and the security children.
•Immediate children only, but not this object: This ACE is inherited only by the parent object's immediate children, but not by further generations, and does not affect the parent object itself.
Use this option if the inherited security of a given group (or user) is different for use of the parent object itself and it is conceivable that no additional level of inheritance is needed.
Use this option if the inherited security of a given group (or user) is different for use of the parent object itself and it is conceivable that no additional level of inheritance is needed.
The relationship between an inheriting object (the child) and the inherited-from object (the parent) is established through an object-valued property (OVP) of the child configured with a SecurityProxyType inheritance. The value set for such a property identifies the specific parent instance from which the child object inherits. A class can define multiple such properties, and in that case, the inherited ACEs for an instance of that class is the union of the inheritable ACEs drawn from all of the objects referenced by those properties.
Several system properties have the inheritance proxy characteristic and so provide out-of-the-box inheritance behavior. This object must have at least one inheritable ACE. For configuring security inheritance by using a custom object-valued property see:
|
Note: If the object class with OVP of a given object is changed to an object class without OVP, all inherited access rights are lost!
|
Table 8-6 on page 242 summarizes how objects receive initial security. Security inheritance takes place only if the source class or object has inheritable permissions.
Table 8-6 Relationships between security parents and their children
|
Object
|
Initial security comes from...
|
Inherits additional security from...
|
Its security can be inherited by...
|
|
Folder
|
The DefaultInstancePermissions of its class, or directly set when creating.
Security policy, if configured.
|
Its parent folder (the folder immediately above), if the Inherit parent permissions check box is selected on the child folder.
Custom object-valued properties with Security Proxy Type set.
|
Child folders, if Inherit parent permissions is enabled on those child folders, and if there are inheritable ACEs.
Documents or custom objects that consider the folder its security folder, if the folder has inheritable ACEs.
By other objects (document, custom object, folder) through a Security Proxy Type property and acting as security parent.
|
|
Document
|
The DefaultInstancePermissions of its class, or directly set when creating.
Security policy, if configured.
|
Security folder, if configured using Security Parent or Security Folder properties.
Custom object-valued properties with Security Proxy Type set to “Inheritance”.
|
Any annotations assigned to the document version, if the document has inheritable ACEs.
By other objects (document, custom object, folder) through Security Proxy and acting as security parent.
|
|
Custom object
|
The DefaultInstancePermissions of its class, or directly set when creating.
Security policy, if configured.
|
Same as Document.
|
By other objects (document, custom object, folder) through Security Proxy and acting as security parent.
|
|
Annotation
|
The DefaultInstancePermissions of its class, or directly set when creating.
|
Document, Folder, Custom Object.
|
None.
|
|
Other classes
|
Its parent class.
|
Any additional parent classes up to the top of the class hierarchy.
|
Child classes, if there are inheritable ACEs.
|
Dedicated folders, where every child had to be filed in the folder, formerly used as parent object for folder security inheritance, were deprecated as of IBM FileNet P8 4.0.1. This special folder ability as Security Parent remains only for compatibility purpose and was replaced by the described folder inheritance algorithms.
|
Inherited access rights: Inherited access rights cannot be configured separately on a user or group basis if related to a given object. If the inheritance is based on a security folder, this characteristic can be deleted from an earlier version of a given object without impact on existing later versions. The remaining latest version still inherit its current inheritance configuration and changes on the parent object immediately change the inherited child security.
Deleting the characteristic “inherit from security folder” must be executed using the FileNet Enterprise Manager and is not available within the standard UIs as Workplace XT or Widgets.
|
Together with the previously mentioned inheritance depths the means define disposition and possibilities of security inheritance. Detailed configuration descriptions are available at the IBM FileNet P8 Information Center in the Security section of the subsection Configure Security Inheritance. See also:
|
Tip: Creating a dedicated class or classes for managing inheritance is recommended in complex environments to provide an administrative advantage because these parent objects can easily be found by searching on the dedicated class.
Further on it might be helpful to use document and folder objects as parent objects for inheritance because they can be named in an easy-to-read manner.
|
Figure 8-17 on page 244 and Figure 8-18 on page 245 show the sample queries based on the previously-mentioned recommendation in Workplace XT and FEM respectively. This is an easy way to find security parent objects when they are organized within a single class (or a small number of classes). At the end of this chapter, 8.9, “A practical example” on page 269, gives a more detailed example.
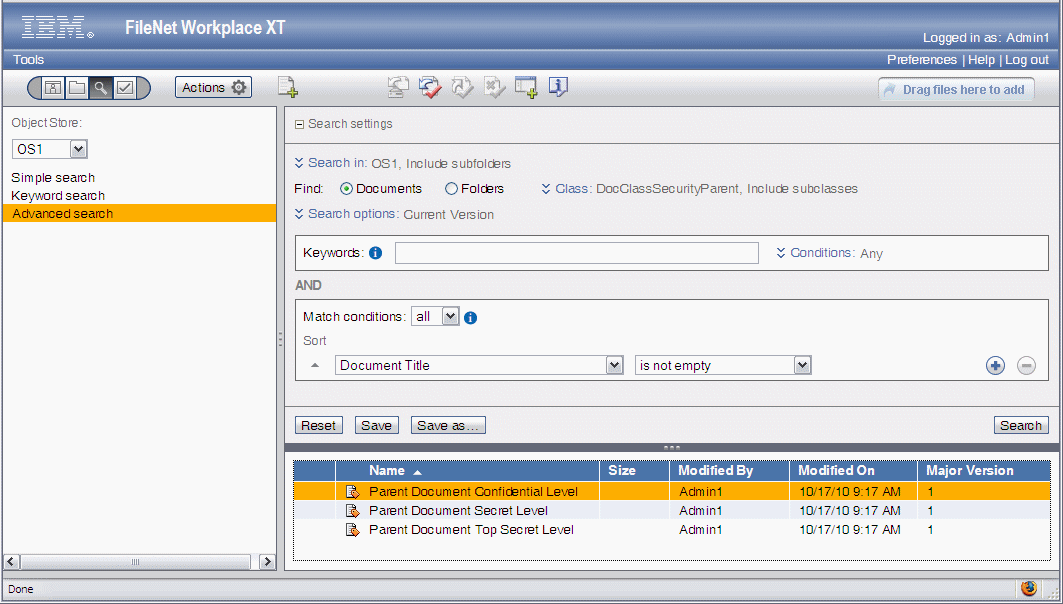
Figure 8-17 Search query and result for sample documents acting as security parents in Workplace XT

Figure 8-18 Search query for sample documents acting as security parents in FEM
8.4.5 Security-partitioned systems
It might be necessary to have systems that must be strictly bordered from each other. The reasons can be that the systems have multiple tenants with highly restricted contents or for compliant reasons. This section discusses various ways to partition systems under security aspects.
Recapitulating security instruments
The purpose of creating an ethical wall (previously known as Chinese wall) within a company’s environment is to ensure that two internal groups using the same IBM FileNet P8 system do not see each others' content, which occurs in competitive situations where an organization might be subcontracted by two or more competing line-of-businesses and must show compliance by securing all sets of content separately. This scenario can include design information, legal disclaimers, problem reports, or contractual amounts. Another scenario is the need of data separation for multi-tenancy purpose.
In such cases, it is vital that information is restricted only to the delimited users of the related given isolated data. For administrative activities, there are additional needs for system access without necessarily notice of content like document display.
There are different possibilities to build up complex security frameworks. Table 8-7 illustrates several general approaches as an assistance for the development of a security model beyond direct security definition on individual objects. Finally, the table summarizes major aspects of the previously-mentioned security capabilities.
Table 8-7 Security configuration general approaches
|
Mean of security configuration
|
Capable for
|
Less capable or unsuitable for
|
|
Organizational techniques
|
||
|
Dedicated P8 Domains
|
•Complete independent security models realizable, even for administrative purpose on P8 Domain level
|
•Complete independent security models, accordingly administrative overhead necessary
|
|
Dedicated object stores
|
•Separate data access for multi-tenancy, different lines of business, and so on
•Dedicated security models within a particular object store
•If necessary, dedicated data bases per object store
•Resolve concurrent security requirements
•Full capability of all object store related security means
•User access can be limited to single Object Stores
|
•A strongly increasing number of object stores result in a highly-increasing complexity of the given FileNet P8 Domain. Dependence on the individual complexity is the reasonable number of object stores to be reached at 10...20 object stores. However complex frameworks with clearly more than 100 object stores have been realized successful.
•No reduce of security complexity
•No magic bullet for any security configuration issue
|
|
Security instruments
|
||
|
Marking sets
|
•Enhancement of existing direct or inherited object security
•Deny access right by marking sets overrule existing explicit or implicit allows
•If dedicated functionality shall be declined while other functionality shall stay usable (e.g. if for administrative purpose documents shall only not be displayed)
•Changes on the marking sets have immediate impact on the objects they are used by
|
•No additional allow rights on the object’s security
•Data separation for multi-tenancy purpose only by marking sets not possible
•Mapping of complex allow and deny configurations
•Limited to ca. 100 marking sets per P8 Domain
|
|
Static configuration by default instance security
|
•Automatically provided predefined ACLs at creation time
•Offers a fine granularity of direct and explicit Allow and Deny access rights
•Can be manually changed after creation, when individually needed
|
•No automated changes when external changes (on the perspective of the given object) take place
•Changes to a large number of ACLs is difficult, if necessary
|
|
Quasi static configuration by security policies or lifecycle policies
|
•Enhancement of existing direct or inherited object security
•Versioning event used for security changes
•Predefined changes concerning the security alongside the lifecycle of an object possible
|
•No automated changes, when external changes (on the perspective of the given object) take place
•Active changes to a large number of ACLs is impossible without versioning and for all objects without relation to any security policy
•Existing ACLs—even when created by a security
policy— are not affected by changing the security policy |
|
Dynamic configuration by inheritance
|
•Changes on the parent object with immediate impact on the children objects
•Enhancement of existing direct or object security
|
•Direct Allow overrules inherited Deny
•Direct Deny overrules inherited Allow
|
Figure 8-19 shows a sample security architecture that encircles two data areas with a common administration.
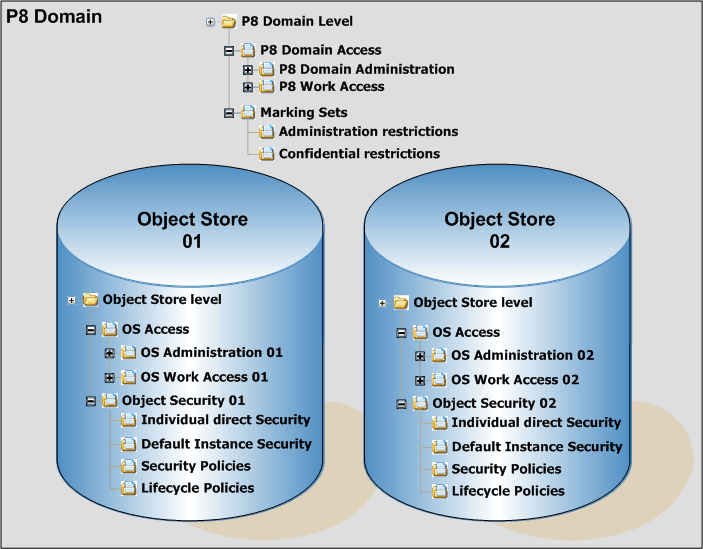
Figure 8-19 Sample Object Store separation
The overall concept of having a data (and security) separation, as shown in Figure 8-19, is to have:
•A common administration for the P8 Domain including the access right to define Marking Sets for administrative and highly restricted access rights in all Object Stores where appropriate.
•An individual Object Store (OS) security model for object access rights for various levels of OS specific groups and security means.
As a result, two or more widely-independent Object Stores can be operated. For separation purposes, non-administrative user are only enabled, by security restrictions, to use dedicated Object Stores. Administrative users can be restricted (for example, Deny access rights on View Content for all documents) highly granularly to fulfill all necessary administrative tasks. Enhanced administration can exceed splitting administrative tasks in P8 Domain wide and Object Store specific tasks. If the enhanced administration still is not applicable, only dedicated P8 Domains are appropriate. Based on the limitations of Marking Sets, they are no means for general security management but instead for dedicated tasks where particular restrictions are appropriate.
The #AUTHENTICATED USER ACE is not recommended for complex security configurations; instead, they must be deleted in an early stage of system configuration to prevent accidentally remaining security ACEs.
|
Security configuration: The security configuration must always be kept as simple as possible and as granular as essential. Increasing granularity activates proliferates administrative overhead in planning and maintaining the security.
|
Examples of using complex security configuration
Many organizations purchase emerging technologies at the departmental level until a critical mass is reached and it makes sense to deploy the technology centrally. A classic example of this is database applications. Many organizations started deploying databases as stand-alone storage mechanisms for application information and configuration. Databases gradually became more ubiquitous and managing the information, security, backups, and resilience to failure became a major challenge.
Most organizations now have central teams to manage mission-critical software, such as a database farm. As Enterprise Content Management systems become more common, the same trend of adoption can be seen. It might be that forward thinking departments are setting up a team to look after a service even while it is deployed at their department's level. This action enables them, in the future, to allow other users in the wider organization to have access to the same information, creating a single source for information stores. A classic example of this is customer information that is managed in separate departments, such as email support correspondence, account opening information, and billing statements.
It might also be the case that an organization wants to create a shared service while also maintaining independent, discrete sets of information. A fraud investigation team, for example, might need access to the entire organization's set of customer information, while separately maintaining its own secured repository for investigation reports. Such scenarios require a solution at the object store level, as described in 8.4.5, “Security-partitioned systems” on page 245, whereby such investigative users might act in an administrative role in one Object Store and as a single user role in another.
By using the same IBM FileNet P8 Domain for multiple applications, it is possible to not require additional server and software rollouts. Creating an extra object store requires the creation of a new database table space and configuration of some data sources. Dedicated Databases might be used. This process offers the full benefits of a secured repository that uses corporate-wide security settings from marking sets while implementing new application specific settings. It might also be that the wider organization must not see certain types of information, represented by Content Engine properties, that is stored with the documents. Creating a separate object store can hide the fact from the wider organization.
A separate object store is also useful when calculating how much resources departments are using at both the database and file storage levels. Because the entire application has its own storage locations, calculating the space used and the amount to charge that department becomes easy. It is also much more transparent to the department that uses the shared service.
There is an easier way to deny access to all objects in an Object Store without using marking sets, which is using a deny of the connect to store permission on the Object Store to anyone who must not have access to any object in the store. If wanted, additional to allow only read access, the deny of the modify existing objects or delete objects permissions might be applicable. This option has the added benefit of not requiring any change to the metadata model, as required with marking sets.
8.5 Gradual security requirement changes
Organizations are fluid environments. Staff and organizational changes are common. Documents might need to be restricted or made available to various audiences. Over time, business processes are modified, types of work are added, and content life cycles might change. There is a need to respond to the changing security landscape while ensuring that any existing information remains protected.
In this section, various issues that are related to a gradually changing security environment are described. It discusses how the IBM FileNet P8 Platform can be used to minimize the administration effort.
8.5.1 How document and process life cycle affects security
As discussed in chapter 8.4.2, “Security policies” on page 234, changes in documents during their life cycles can have implications for those who can access the documents. There is also the question of how to manage the assignment and removal of dynamic permissions. As an example, a customer sends a request to open a bank account. This request and related customer information is not made publicly available to anyone in the organization. At certain point, an account manager is assigned to the case. The account manager then gets the required permissions to the request and customer information to process the case.
In the examples provided so far in this chapter, this use case can be covered by assigning an application security policy template for a state of Account Manager assigned. However, the business requirement might want only individuals who are acting in a particular role to have Add access to the content.
Business process management is effective at retrieving and acting on information in real time. For a particular type of account, or the workload given to particular users, it can automatically be decided which user to assign as an account manager. A supervisory user can also be assigned within the Account Opening process to select the appropriate person to be the account manager. In either case, the information that concerns the person who must be assigned is present as part of the process, and it is the process that needs to act upon it. No document event happened to necessitate this change. It is purely a function of a management process reaching a particular stage.
There are several ways to secure this information within a business process management environment such as that provided by the IBM FileNet P8 Platform (specifically, IBM FileNet Business Process Manager). The user interface restricts who can see a work item. The concept of process attachments are used within a process and security on the queues to restrict who can view information. Although these are valid methods, to be totally sure that content access is secured, it must be ensured that the underlying security permissions are set, which is the only way to absolutely ensure that a user without permission cannot see the content. This feat is possible within IBM FileNet P8 because all expansion products are built upon the Content and Process Engines and are restricted from what they can see and process by virtue of those engines enforcing their security models onto the client application.
This ability brings up a range of questions. How can queues and individual work items locked down? How can the activities dynamically interact with the Content Engine to update security in real time? How are the updates or changes to such activities managed? How are such activities audited? What are the drawbacks? These questions are answered in the remainder of this section.
8.5.2 Managing security updates
To manage the security of an individual document, or class of documents, is relatively simple thanks to the rich features that are available in IBM FileNet Content Manager. After thinking at a more abstract level, things might become more difficult to manage, for instance, when 300 client applications must be worked on in a given week. If these applications are needed to be retained for five years and 100 new ones arrive per week, an additional historical set of 26,000 must be managed.
Let us assume security settings are assigned to the documents when they are being modified or versioned. If the security policy is changed within the organization to reflect a change in business, only the single security policy needs to be modified. Therefore, if the security policies are changed within the organization to reflect a change in how business is done, only the single security policy needs to be modified. Because there are 300 documents in process, all of these documents and new documents in the system have the policy applied the next time they are versioned. If the 26,000 historical records are relatively static, there is an administrative challenge to handle because the security on these are not updated to reflect the new policy.
Conversely, if marking sets are used instead to manage this security, changing this is immediately reflected by all documents within the system. However, the historical documents' security no longer reflects the security that was originally assigned to them at the time of processing, which can be a problem when trying to prove to a regulator that the security on a document, during or at the end of a process, was used to manage it.
Another problem with updating marking sets is that if a marking is removed or added, it is not reflected on any documents that currently use the marking set. Removing a marking from a document because it was removed from a set does not make sense because it can leave the content open. As such, the marking still applies to a document in the Content Engine until that the document is versioned or the property is modified, which still leaves a management overhead with lots of markings to add and remove, rather than just modifying the underlying permissions that they assign to content.
Table 8-8 on page 253 describes the various types of security, the ease of modifying their permissions and adding and removing elements, and therefore the longevity for which must be considered using them in a production, long-lived system.
Table 8-8 Advantages and disadvantages of various security methods
|
Security Method
|
Ease of updating
permissions |
Ease of adding or
removing elements |
Relative longevity
|
|
Direct assignment
|
Easy for individual documents, but difficult for large groups of documents.
|
Easy.
|
Short term. Might require changing many times during life cycle. Useful for short term, dynamic assignments of permissions.
|
|
Dynamic Security Inheritance Objects
|
Easy for large or small groups of documents. Instantly applied to all content. Requires quite detailed system knowledge. Can be used across an IBM FileNet P8 Domain.
Segmenting of similar secured objects to assign differing ACLs will be complex.
|
Easy. An element cannot be deleted if it is in use, but it can be hidden from being selected to prevent its use in the future.
|
Short-to-long term. Can be used effectively by business processes for application-specific security settings.
|
|
Marking Sets
|
Easy. Instantly applied to all content. Can be used across an IBM FileNet P8 Domain.
Segmenting of similar secured objects to assign differing ACLs will be complex.
|
Difficult because marking sets can only be defined when creating the property.
|
Long term. Use for rarely changing, enterprise-wide security types where permissions might change but the number of types of access do not change often. Use multiple marking sets if longevity varies considerably.
|
|
Security policies / document lifecycle policies
|
Medium. Easy to change, but is not applied until content is versioned or actioned in a custom application, for example, its state changes. Can be assigned at instant creation time.
|
Easy for version states, but difficult for a custom application because it requires coding in the application.
|
Medium. Useful while the document is in use because it abstracts the individual permissions from the document. Not good to lock down content over long periods of time.
|
|
Security folder
|
Easy and instant thanks to inheritance.
|
Medium. If a document is filed in multiple locations, users can get confused as to why security for one folder is not being applied. Also, there is no simple interface in Workplace XT to assign a security folder.
|
Short-to-medium. Useful while document and folder are in use, but difficult to maintain over time for retention purposes.
|
|
Default instance security
|
Medium because it is an administrative task. Only applies to new documents.
|
Not applicable. This applies to one per class.
|
Short. Only used at document creation. Useful to initialize owner, policies, dynamic security inheritance objects, and marking set values.
|
Table 8-8 on page 253 shows that all methods of assigning security to content can be useful but only applicable to specific use cases. To build a comprehensive solution to a problem that requires content to be managed over time, a mixture of methods often must be used.
The remainder of this chapter discusses how to perform changes over time. The example at the end of the chapter pulls these short-to-long term methods together in a real-world example to illustrate how a platform approach to these security issues can assist the management of information security.
8.5.3 Updates using business processes
It is often a requirement to update a document's security over the course of its life cycle. The examples that are provided so far are either manual or controlled by document lifecycle or security policies. There are other scenarios, however, where security might need to be updated dynamically in response to user decisions or information from an external system.
The Process Engine (offered through IBM FileNet Business Process Manager) can be used to execute component steps that call Content Engine API functionality to update security on Content Engine objects. An example of this is when a new customer requests a product and the request must be assigned to a dedicated Account Manager with the necessary permission to manage and see the documents. The Sales Administrator who is in charge of signing the Account Manager, does not need to remember what permissions in the Content Engine to assign to the Account Manager. The Sales Administrator simply selects the appropriate manager and let the business process handles the rest.
The readily available CE_Operations component does not have any security querying or modification functions, but they are simple to create. Consider Example 8-1.
Example 8-1 Sample code to add grantee level
public void addGranteeLevel(VWAttachment attachment,String username,String level) throws Exception {
Document doc = findDocument(attachment); // utility function
// create a new access permission object
AccessPermission ap = Factory.AccessPermission.createInstance();
Integer l = getAccessPermission(level); // utility function
// set access permissions
ap.set_GranteeName(username);
ap.set_InheritableDepth(new Integer(0));
ap.set_AccessType(AccessType.ALLOW);
ap.set_AccessMask(l);
AccessPermissionList apl = doc.get_Permissions();
// add the permissions to the list
apl.add(ap);
doc.save(RefreshMode.NO_REFRESH);
}
Example 8-1 uses the Content Manager Java API to find a document, create a new Access Control Entry, and save the changes. The access mask is computed by adding together the integer value of all permissions to be given to the grantee (user or group). A utility function is used in Example 8-1, so process developers can simply supply View Content to specify the level rather than remember the correct integer value for each of the constituent permissions.
Now that the access is secured to the documents throughout a process, it must be ensured that each step is accessed by the appropriate person. It has already been mentioned that queues and rosters can be restricted to particular users, but with IBM FileNet P8, work can be assigned to specific users and workflow groups. A workflow group is an array containing references to users in the system. A workflow group is completely different from an LDAP group and is only relevant to a particular process instance. Assigning a step to a workflow group means that each of these users are sent the step to work on. After these users all complete the work step, the routing condition is interpreted as usual.
It is possible to dynamically assign strings that contain user names to elements within a workflow group, which means that for the example the assigned account manager string field can be mapped to a workflow group and then the process can be routed to a step that is linked to this workflow group. In other words, even though at process design time there was no idea who would be assigned to do this work, it can still be effectively designed and the process can be routed. This can happen while guaranteeing that this information is provided for each process instance by a previously assigned user, which makes organizational changes easy to separate from business process design, thus maximizing the flexibility of the IBM FileNet P8 Platform.
8.5.4 Institutional reorganizations
People who move internally or join and leave an organization can prove to be a real security management challenge. This challenge is especially true of systems that assign security to information that is based on an individual rather than just a role. Take the example of an Account Manager who might have document instance security set such that only they can see their customers' documents. If this person leaves, how is that security updated?
|
Avoid mistakes: Substantial mistakes made by designing the security architecture will cause nameable efforts in adjusting the system and can cause heavy load and long runtimes at the database!
|
There is no simple answer to this question. Depending on the necessary tasks, there are several approaches that might only be resolved by custom code. In this chapter, some security architecture aspects are discussed; however, for coding issues refer to the appropriate development documentation at the Information Centre.
Some aspects in handling changing security needs are:
•Avoiding dedicated user authorization
When creating the technical and functional security concept, it is important to avoid any dedicated user authorization. Will it be necessary in spite of precautions to define dedicated user authorization? It is essential always to define at least one additional group-based ACE to keep a valid access right to the particular objects as an administrative fall back.
Additional object protection—if necessary and in addition to others—can be defined using marking sets or only temporary memberships in the fall back group.
Prevent arbitrary individual security configuration.
•Controlling individual document entry
IBM FileNet P8 offers a bundle of methods for controlling individual document entry:
– The Default Instance Security, especially the #CREATOR-OWNER ACEs, can be used for dedicated object classes for object entry to the P8 environment for individual purposes (for example, if the Content Engine is used as a compliant personal document repository alongside enterprise-wide processes).
– Document Entry templates can preconfigure security, as needed, to meet individual, business, and administrative needs.
•Using properties for granular object grouping
Using properties for grouping objects supports various possibilities to reorganize objects by means, such as executing search queries and related actions on the result list. Remember that there is no query that allows defining a search based on ACEs on Content Engine objects.
Using more than one property for object grouping purposes can enable (within limitations) one-to-many reorganizations.
•The Process Administrator Tool can be used to identify open work items for the dedicated user (for example, Work Item search query for F_BoundUser) and appropriate reactions to complete open work steps are decided by the responsible user in the Process Administrator Role. Changes to the object securities must not be made before impact to open work items are discussed.
•While designing a workflow map, it might be necessary to relate some steps to dedicated users (without standard redundancy) instead of groups. In this case, it is necessary to wrap that step in an escalation timer that escalates the task after a period of time by reassigning the step. This design mitigates personnel changes and also absence on vacation or other long-lasting reasons.
To prevent assigning new work to absent users without knowing the individual replacement person, use the out-of-office functionality of the Process Engine. Any work assigned to the user is assigned to the designated proxy user. The definition of the proxy user can be done by the given user to be covered using the user’s Preferences → Tasks → Out of Office configuration within the Workplace XT. A centralized way for the Out of Office configuration is using clicking Process Administrator Tool → Tasks → Out of Office. The responsible user in the Process Administrator Role can select a user of interest and define the proxy user.
8.6 Content-level security
After the system verifies that a user is actually authorized to access a piece of content, be it properties on a document, the content itself or a workflow item, security must also be ensured wherever that information flows. In this section, methods are described that are currently in use that can be taken advantage of. It is strongly advised that anyone who is interested in this section also seek the advice of a FileNet Certified Professional or Solutions Architect to discuss specific security requirements. There is a plethora of internal security features, such as encryption and storage of security keys and credentials, that are not mentioned in this section, but that might be of major interest in a given situation or requirement.
8.6.1 Local copies on user machines and client cache files
A major problem for organizations is preventing duplicate, local copies of content on individuals' machines. This problem is especially important when introducing a new enterprise content management system because there is usually some resistance to changing working practices by storing documents in a central system rather than keeping personal copies. The quicker this is resolved, the easier ensuring compliance becomes.
Various user access methods are possible with the IBM FileNet P8 Platform, which includes thin applications, such as Workplace and Business Process Framework, their viewers such as the Image Viewer, or integrated desktop applications, such as Microsoft Office.
Whenever a browser accesses a web page or download, the application makes a temporary local copy. It is advisable, therefore, that if the security of information is paramount, consider using controlled access methods rather than allowing general download access for content.
The application integration capabilities of Workplace and Workplace XT can be used to bring content under control while providing a rich and intuitive user experience to encourage adoption of the new system. Application integration embeds a set of IBM FileNet P8 menu options in Microsoft Office applications to open, check out, and check in documents from an IBM FileNet P8 repository.
If using Application Integration, FileNet Integration for Microsoft Office, or Workplace XT, there is an embedded application called File Tracker.
|
Note: Workplace and Workplace XT provide various File Tracker applications that cannot coexist on the same PC.
|
It monitors all documents that are downloaded using Workplace or Workplace XT and Office Integration and provides extra usability by tracking the repository object that a local file represents. This tracking makes checking in modifications to content fast because the system does not have to ask the user which document to check in.
The File Tracker has some extra, centrally configured settings that allow administrators to specify when local copies of content are deleted, which are configured in the Workplace or Workplace XT Site Preferences page, as shown in Figure 8-20. The most common scenario is to remove a local copy of a document when it is checked in to the content repository. This action ensures that there is always only one current version of a document within the organization.
Remember that the files, as long as they are checked out and stored locally (and that might be an unprotected network share as well), are not protected against improper access and changes.
Figure 8-20 File tracking options to ensure local copies are deleted
8.7 Network security
There are many issues to deal with when accessing an application over a network, especially if that network is potentially insecure. In this section, the issues are detailed and how they can be mitigated, thanks to the features of the IBM FileNet P8 Platform.
8.7.1 Demilitarized Zones
The classic approach to network security is to have a secured server layer that only allows access from specific machines in a so called Demilitarized Zone (DMZ). The DMZ is a protected area (usually by firewalls) with limited communication possibilities (protocols, ports, allowed IP-addresses, and so on) between the systems within and outside of the DMZ. One or more additional zones, with no direct communication allowed to systems, can exist within the DMZ.
The IBM FileNet P8 Platform supports this methodology and can be configured in several ways. A simple solution is a departmental system without any high-availability requirements and only a single zone within the DMZ. Workplace XT and Content engine might even use the same server. Access is made directly by a client using a browser or Microsoft Office client, which allows them to flow through the Workplace XT Web application. This application can be installed in the DMZ with the Content Engine, Process Engine, and database servers located in the same server layer, as shown in Figure 8-21 on page 261.

Figure 8-21 General illustration of a simple DMZ
On the opposite end of the scale, one might have a highly-available environment with clustering that is protected by secure protocols (for example, https, SSL off loading on hardware load balancers, or software based SSL off loading discussed in the next chapter) and secure web proxy products. The DMZ in Figure 8-22 on page 262 is divided into three zones in which access is restricted from one level to the direct following.
Figure 8-22 General illustration of a complex DMZ
The advantage in Figure 8-22 is that only the secure proxy is exposed in the DMZ. This method is used across many applications and not just IBM FileNet P8 in typical implementations. As such, there are fewer opportunities for compromising security in the DMZ layer because all application servers are located in the server layer. Having a highly-available environment also means that clients connect through one IP address that points to a (typically hardware) load balancer, which makes configuration of firewall rules easier to manage.
In the server layer, itself, the Workplace XT, Content, and Process Engines communicate to each other over known ports and protocol.
8.7.2 Encryption on the wire
It is often desirable to ensure that all clients are accessing content through a secured channel. Inside the DMZ and in the server layer(s) are defined to be confident that network traffic is protected. On a network with a large number of potentially compromised computers, however, extra steps are necessary to prevent unauthorized access to content.
All IBM FileNet P8 Platform web user interfaces are supported in application servers that use the Secure Sockets Layer (SSL) technology, which is desirable in non-Single Sign-On (SSO) environments where users enter their user name and password directly into a web page and in SSO environments to protect the communication itself. Many high-profile security breaches occur in situations where the login page of a site was not on a page that was protected by SSL and the target service was. It is a good idea to ensure that SSL is always used alongside the entire communication way from the client application to the hardware balancer immediate before or at the application server that hosts the Workplace XT.
SSL can be configured to provide three important data security features:
•The initiating handshake is used to identify the client that is sending the request.
•SSL can be configured to validate that the data was not modified in transit.
•SSL provides data confidentiality by encrypting data over the wire.
Behind the scenes in the server layer, it might also be wanted for all elements of the IBM FileNet P8 Platform to communicate securely with each other. This communication includes authorization lookups to the underlying Directory Server through LDAP and interaction between the core engines, such as Workplace XT and the Content Engine. SSL can be used to encrypt these internal communications.
It is important to note that some communications used by the IBM FileNet P8 Platform rely on the security support of the underlying systems. The JDBC database driver, for example, must support secure communications with the chosen database vendor's product; likewise, the application server's JAAS login module requires configuring to perform authentication requests using secure channels. While this is out of scope of the IBM FileNet P8 Platform, it is worth mentioning that to ensure as secure a system as possible, security all the way down the application stack into the database and storage layers is also an important, and often overlooked, consideration.
|
Note: Depending on the secure protocol that is used for client/server communication, issues concerning hardware load balancing might exist. Likewise there are dependencies between using firewalls, used protocols, and application-server products. It is absolutely necessary to contact the manufacturer of the selected hardware and software products and refer to the latest documentation at an early stage of the design phase.
|
8.7.3 Web services security
All web services APIs for both the Content Engine and Process Engine are supported over an SSL protected connection. By default, all information that is known to be sensitive, such as user names and passwords that are sent to the Content Engine, are encrypted using asymmetric public private key pairs. These keys are generated during installation of the Content Engine. For more information, see the IBM FileNet P8 Platform Installation Guide at:
The Content Engine EJB transport options, which include RMI-IIOP and T3 (Weblogic), both support the use of SSL to protect communication. Communication through the Web services APIs can also be secured using SSL-protected HTTP (https). It is important to identify limitations based on the actual planned architecture and the planned software to be used.
The Process Engine Java API connects to the Process Engine directly using RMI-IIOP, and for this API, the channel does not support SSL-protected communications. Network-based encryption techniques that preserve the IP packet must be used if this communication must be protected. Because all login and document retrieval requests are processed through the Content Engine Java API, this is only an issue if some of the process fields contain sensitive information because session tokens are transmitted encrypted.
IBM FileNet P8 processes can invoke, receive, and reply to Web services calls. The security aspects of these processes are important to discuss. The standards supported by the Process Engine's support for web services are:
•WS-BPEL for managing the orchestration conversations with services
•WS-Security for passing authentication and authorization information to those services
IBM FileNet P8 can interact with any web services that are protected using SSL communications. This communication is handled by the WSRequest component queue that is installed in the client application. The incoming messages are handled by a servlet that is configured in the Workplace or Workplace XT applications, depending on preference. To protect all incoming Web services messages requires configuring at least one Workplace/Workplace XT instance to be SSL protected.
Providing credentials within an IBM FileNet P8 process requires some manipulation of the web services partner link variable. Doing so requires changing the underlying XML header to include WS-Security information to the target web service. This is a flexible method and is the same approach that is used to dynamically change the host target for your web services call, which can be useful in situations where one wants to off load the web services call to a separate geography or service provider.
In Figure 8-23, MyUserName and MyPassword are passed in two process fields to generate the web services security header.
Figure 8-23 Providing WS-Security credentials for a Web service
For incoming web services requests, the process can be instructed to validate the incoming user name and password information against a specified set of user accounts. The Process Engine then checks with the authentication provider that IBM FileNet P8 uses to ensure that the user name and password are valid, as shown in Figure 8-24.

Figure 8-24 Configuring incoming authentication for a web services call
Security can only be provided to invoke external web services that store the authentication information in a WS-Security header. Some technologies, such as protected .NET 2.0 Web services, do not use this method and instead protect access by performing HTTP header manipulations and handshakes. These methods are not supported by the IBM FileNet P8 Platform. To interact with these services, WS-Security header support must be enabled rather than restrict access to the service through HTTP authenticated handshakes. It is also relatively trivial to create an unprotected .NET 2.0 Web service to accept the incoming request, extract the credential information, and invoke the target-protected Web service using HTTP headers. This works similarly to a proxy for Web services.
8.8 Auditing
In this section, the kinds of logging and auditing that the IBM FileNet P8 Platform supports, its core engines, and the most common expansion products are discussed. A brief summary of information is available both to security professionals and business managers to inform their activities and prove when and why particular actions are taken in the organization. These events range from small, atomic events, such as changing a document property, to major events that occur over the life cycle of a document or the course of a business process.
Auditing can be used to satisfy compliance requirements or maintain vital business interests. Logging on a user basis, to monitor the activities of a dedicated user, is not available when user information be part of the log entry.
8.8.1 Logging in the Content Engine
As mentioned in Chapter 7, “Building an ECM solution” on page 165, the Content Engine supports auditing of most actions that happen to Content Engine objects, which includes all actions that can occur to a document, custom object, or folder. These events can be subscribed to facilitate active content processing and can also be configured on a per-class basis to write audit logs for specific, configured actions on important content. It might be chosen, for example, to log all document check in and delete events in the repository. For certain critical document types, it might be necessary to enable logging of the viewing of properties or content of a document to be absolutely certain about who had access to the content and when (see the note at the end of chapter 8.8.1, “Logging in the Content Engine” on page 266).
To enable auditing on the related Object Store’s properties General tab, the Auditing enabled? option must be selected (Default: not selected). In addition, Audit Definitions must be created for the classes and events that are to be audited, as shown in the example in Figure 8-25 on page 267. The audit will immediately be enabled.
The log information is represented as a subclass of the Event object within the Content Engine, which means that it is stored as a row in the underlying object store database. As with any other object, instances of these audit items can be searched for and their properties retrieved. This process occurs through either the standard Content Engine search support or using the read-only JDBC provider. The audit history can also be analyzed at the Audit History tab of a given object with active auditing.
On a security perspective, especially the Update Security event will be of logging interest, as shown in Figure 8-25.
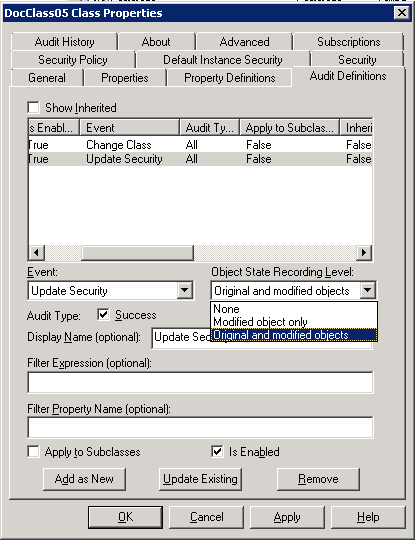
Figure 8-25 Configuring Security Update logging event
|
Note: If the object’s initial class will be changed, the initial audit configuration will not affect future objects.
|
Trace log files can also be created to log these (security) events, lower-level debugging, and diagnostic information for the Content Engine itself. The trace log is configured on the P8 Domain properties Trace Control tab. It is not recommended to use log files for security monitoring because they are not protected by the IBM FileNet P8 system and might be accessed by unauthorized personnel. On the other hand, the audit events can be seen only by personnel that either is allowed to have access rights to searches that might be able to search the audit events or access rights to the audited objects.
|
Note: Audit-Logging not only allocates space in the database but also creates performance overhead. Keep in mind that data collection must always be kept at the inevitable minimum. The logging of read access (for example, Get Content-event) results in an additional database consumption. In any case, the impact caused by logging must be included in the storage and performance calculation.
|
8.8.2 Logging in the Process Engine
The Process Engine log is concerned with all life cycle actions that occur during the course of a business process, which includes workflow creation, step completion, and exception handling. These events can be logged into a particular log database table. Multiple logs, each with its own database table, can be configured for the same Process Engine region, which allows the use of one log, for example, for several processes that make up a single application.
Each log that is shown in Figure 8-26 can be configured to record additional user-defined process fields to produce logs with more contextual information.
Figure 8-26 The default Process Engine log with extra configured user-defined fields
The type of Process Engine events to be logged are configured at the region level. These events can be predefined or user-defined events. These user-defined logs can be populated using the Log step type within a business process map. The event log to use is passed, the custom log message identifier, an integer, and the message to log. The Process Engine then handles the collection of the additional, configured process fields and logs the entire message in the specified log file.
This information is secured by preventing any user, without access to the corresponding process roster, from accessing any of the log items that correspond to it.
8.9 A practical example
As a practical example, we consider an enterprise content management solution with business process management features, the re-insurance placement and litigation application. Re-insurance encompasses the concept of large organizations that must ensure, for example, five buildings, a fleet of 80 cars, mobile phones, and a variety of other instruments. They use re-insurers as a single point-of-contact for all of their insurance needs. These re-insurance organizations then break down the total requirement into individual parts that they can get other insurance firms to in turn insure. In our example, this situation can mean that all vehicle insurance is grouped together and sent to three companies to bid on that part of the overall requirement.
These bids are then collected, and a full package cost is calculated with terms and conditions. A markup is added to cover costs and to create profit for the re-insurer, and this final amount and terms are presented to the re-insurance customer.
In our example, the flow of information is:
1. Customer submits a large requirements document to the re-insurer.
2. The document is scanned and routed to the account team.
3. The assigned manager receives the information and starts to put together individual elements to solicit bids.
4. These individual forms are submitted to a select few external insurance agents.
5. When all bids come back, or the time to bid is exceeded, they are evaluated by the account manager who chooses a preferred vendor for that element.
6. A total charge amount and legal terms are created and sent to Legal for approval.
7. After they are approved, they are sent to the customer who signs an agreement or asks for a reassessment of part of it or abandons the request.
Designing the business process is out of the scope of this book. Instead, we discuss the security issues that it entails:
•Preventing important competitive information from being available to some people on the account team.
Providing access for the same account team to all documents related to a particular customer
A customer folder is created with access permissions set such that the account team can view properties and content of any document that is linked to this folder by the security folder property. All subfolders are set up to inherit permissions from this folder. The parent folder itself, must not be set to inherit permissions from its higher-level folder to prevent unauthorized access.
We ensure that new documents that are being scanned into or added to the system initiate a Content Engine action handler that sets their security folder attribute to the correct value. We find the appropriate folder by making sure that the customer folder is a special class of folder with a required customer number attribute.
We can optionally create special business processes or subfolders to give a greater granularity to where documents are filed. If we receive hundreds of documents from this customer that relates to different matters, for example, we might want to file the incoming documents into the appropriate subfolders.
Hiding customer documents from other account teams
We must ensure that the customer folder does not inherit permissions from its parent folder. To ensure that security cannot be changed, we must remove any modify permissions rights from all non-essential users. We can limit this to just the Account Manager on the parent folder, for example, but allow no other person to have this right.
We must also ensure that no privileged permissions are assigned to users, which includes the write any owner and privileges write permissions on the object store. A user with these rights can modify the document owner and through this its security or modify the content, respectively.
We ensure that all customer documents have null in the owner field. We use a separate management workflow process to change ownership rather than allow this to occur manually.
Ensuring that documents do not leave the customer's legal jurisdiction
We create a required multi-value property on all customer documents called applicable jurisdictions. We create a marking set that consists of markings that restrict access from users in particular locations, which ensures that the document cannot leave the customer's applicable jurisdictions. We deny all rights from any users outside of applicable jurisdictions who use the constraint mask for each marking.
Preventing important competitive information from being available to some people on the account team
Some document properties, in addition to document content, might include competitive information, such as the value of a quote. We might have some people who are on the account team, such as customer service representatives, who must not see this sensitive information.
At the same time, we might have properties on the document that these users should see, which can be so that they can confirm to a customer that a document was indeed received.
We cannot directly secure individual properties on a Content Engine object, but we can secure objects themselves. Thus we can create an object to hold our securable properties and link this to the document by using an object value property. This object can be set up with a confidential security marking to deny the user from seeing this information.
We create a class called secured property document, which contains a secured information object value property that is required to point to one or zero security showcase document objects. These security showcase documents are required to have a value that is set for their security classification. As you can see in Figure 8-27, logging in as a user with sufficient clearance means that we can see the object and its metadata.
Figure 8-27 Logged in as Administrator, we can see the confidential properties
If we instead login as a user without confidential access, we can read other document properties, but we cannot see the confidential object or its properties, as shown in Figure 8-28 on page 273.
Figure 8-28 Logged in as a user who cannot see the confidential information
We also can define this property as having the document's security inherit from the secured information property and make this property required. If we then set permissions on the confidential information such that view content was denied and inherited by the confidential document and immediate children, and view properties was denied for the confidential document only, there is no need to explicitly deny view content rights to the top-level document.
In other words, the view content rights are determined by how sensitive the secured information was. In practice, this is useful if the properties are derived from the main document's content, which means that this security setting can be applied one time on the secured information object and not have to also add a permission to the main document to deny just view content to specific user groups. If confidentiality changed over time, this option is desirable from a manageability perspective.
|
Note: Do not forget that an explicit direct allow permission on the document overrides an inherited deny for view content permissions in this case, which illustrates the desirability of using inherited permissions over direct or default allow permissions.
|
Creating bid elements by the account manager
We use a business process to create a skeleton structure for a customer deal, which includes a bid elements folder. The Account Manager creates subfolders of class bid element that contains a required bid identifier property. We give the account manager create subfolder rights on the bid elements folder. We also ensure that, by default, the #CREATOR-OWNER of a bid element folder has the file in folder permission.
Because all subfolders of the top level customer folder inherit security permissions and all documents have their security parent property set, we ensure that anyone on the account team can also view properties and content of documents in the bid element folders, which means that the account manager does not have to worry about administering security and can instead concentrate on working on the content.
Tracking the instructions that an account manager sends to insurers, and what we receive back
We require an account manager to complete an electronic form with an instruction that is sent to all insurers who are asked to bid on an element. This form drives a business process. The bid element folder is attached to the business process at the same time the form is completed by using a form workflow policy process.
This policy locks down the form so that the account manager cannot modify its content to change what the instruction says or who the bid request is sent to after the form is submitted. To ensure security at the account manager's workstation, we require that the electronic form have a digital signature that the account manager signs just prior to submission. We make this lock down the fields on the form to prevent modification of a signed form by any privileged user.
The business process collects the relevant bid element documents and submits them using an encrypted Web services call to the relevant insurers. Any responses from the insurers are authenticated with the relevant user name and password for this insurance organization to ensure that fake bids do not enter the organization.
Ensuring that late bids are not considered
Upon expiration of the bid timer, the business process locks down the quotes subfolder for the relevant bid element, which prevents an incoming bid process from being able to add a bid after the timer is exceeded. If the bid comes later, the incoming bid process can reply to the insurer, notifying them automatically that their bid is not accepted because the submission deadline is not met. It also means that the account team does not worry about whether or not a bid is late. For large accounts, if doing it manually, late bids can be mistakenly considered or modified after submission. By making this electronic and secured, we can prevent this from becoming a problem.
|
Wait for condition: You can model a wait for condition in an IBM FileNet P8 business process to wait for a known maximum number of launched subprocesses, for example, you can have conditions on five routes to launch or wait for a maximum of five sub processes. Use a custom object with an array field called, for example, SubProcessStates. In the IBM FileNet P8 process, you launch each sub process in a loop passing it as reference to the custom object instance and the sub process’ own index number. Each sub process is responsible for updating its status within this custom object. The main process then periodically checks these values to determine when to continue.
An alternative to periodic checking is to have a Content Engine Java event handler check the custom object every time it is updated. If it finds that all status entries are marked as complete, it can fire a single re-awaken process. The main process then has a wait for condition waiting for this single process, which puts the minimum amount of load on the Content Engine and Process Engine for all of the process synchronization because the wait for condition values are checked when the waited-for process is modified.
|
Preventing bid elements from being modified after the total customer charge and legal terms are considered
In the re-insurance handling process, we have a system step to add an explicit deny permission for property and content modification to every bid element folder. Because no one can manually add a permission to a bid element document (thanks to default instance security), we know that the modification deny permission at the folder level cannot be overridden by a direct permission on the bid element document because no one can manually add any such permission.
Recording every quote that we send to a document
In case of legal action, we declare all documents that are involved in a re-insurance quote as a critical business record just prior to sending a quote response to a customer. We can use IBM Enterprise Records to manage the access to this information so that applying legal holds and managing disposition is automated and centrally controlled according to organization-wide policies, defined by the Legal and the records management teams.
Recording all agreement documents signed by a customer
When a customer agrees with our quote, we must also lock that information down and declare that as part of the same business record. Again, we use IBM Enterprise Records to do this.
Managing ad-hoc correspondence
We use the email management features of the IBM FileNet Content Collector to capture all customer correspondence and put them in the relevant correspondence folder. The correspondence is located in our customer folder and is automatically declared as a business record. We can, for example, have a default email storage policy of three years for all customer correspondence. The email can also be declared as a re-insurance quote acceptance record if it is related to a customer re-insurance request, perhaps with a different retention period. IBM Enterprise Records resolves these two record types and retains the correspondence accordingly. If bid-related documents are held for five years, for example, this prevents the disposition of the email after the usual minimum of three years, which allows us to prove compliance across different sources of content.
8.10 Summary
This chapter showed that there are many factors to consider when implementing an IBM FileNet P8 solution, which encompasses all elements of security, from authentication and authorization of users to encryption of communications, storage of content, through to proving compliance. Auditing and proving who has or has not modified content is just as important as securing information, and this is increasingly true due to increasing regulation and the litigation nature of business in the current environment.
The IBM FileNet P8 Platform has a rich set of security and auditing features. These features can be used by expansion products, such as IBM FileNet Business Process Framework, to provide the same capabilities to new business solutions. Auditing and security management showed how they can be extended with other IBM FileNet P8 Platform expansion products, such as IBM Enterprise Records.
The IBM FileNet P8 Platform provides a comprehensive set of security features that are sophisticated enough to solve a wide range of business and IT problems. This chapter explained how these features can be applied to new, complex business problems to enable deployments to be conceptualized quickly, which enables customers to rapidly configure, adapt, and extend an IBM FileNet P8 Platform-based solution, while maintaining tight control over the security of the overall system.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
