CHAPTER 3
NETWORK AND COMPUTER ATTACKS
After reading this chapter and completing the activities, you will be able to:
![]() Describe the different types of malicious software and what damage they can do
Describe the different types of malicious software and what damage they can do
![]() Describe methods of protecting against malware attacks
Describe methods of protecting against malware attacks
![]() Describe the types of network attacks
Describe the types of network attacks
![]() Identify physical security attacks and vulnerabilities
Identify physical security attacks and vulnerabilities
As an IT security professional, you need to be aware of attacks an intruder can make on your network. Attacks include unauthorized attempts to access network resources or systems, attempts to destroy or corrupt information, and attempts to prevent authorized users from accessing resources. You must have a good understanding of both network security and computer security. Network security involves protecting the network infrastructure as well as stand-alone systems. Therefore, computer security is necessary to protect computers and laptops that aren’t part of a network infrastructure but still contain important or confidential information. Protective measures include examining physical security, right down to checking door locks, and assessing the risks associated with a lack of physical security.
This chapter gives you a strong foundation on what attackers are doing. Just as law enforcement personnel must be aware of the methods criminals use, you must know what computer attackers are up to. How can a denial-of-service attack be used to shut down a company? How can worms and viruses be introduced into a company’s corporate database? How can a laptop or desktop computer be removed from your office with little risk of the intruder being caught or stopped? In this chapter, you get an overview of attack methods and protective measures. To understand the importance of physical security, you also learn that an unscrupulous in-house employee can pick a lock in seconds.
MALICIOUS SOFTWARE (MALWARE)
Many network attacks are malicious, initiated to prevent a business from operating. Malware is malicious software, such as a virus, worm, or Trojan program, introduced into a network for just that reason. The main goal of malware used to be to destroy or corrupt data or to shut down a network or computer system. The goal today is about making money. Scores of cybercrime organizations have warehouses full of programmers who do nothing but write malware with signatures unknown to antivirus programs. The following sections cover different types of malware that attackers use.
Security Bytes
Security professionals know that the Russian Business Network (RBN, also known by many other names) is one of the most well-structured cybercrime organizations in existence. The RBN’s specialty is creating malware; hosting child pornography, spam, and phishing Web sites; and committing identity theft. RBN has employed experienced and dangerous computer programmers and hackers. When you learn how to use a security tool, remember that the bad guys are learning how to use it, too. Don’t give up, however! The good guys need good hackers who can give the bad guys a run for their money.
Viruses
A virus is a program that attaches itself to a file or another program, often sent via e-mail. The key word is “attaches.” A virus doesn’t stand on its own, so it can’t replicate itself or operate without the presence of a host. A virus attaches itself to a host file or program (such as Microsoft Word), just as the flu attaches itself to a host organism, and then performs whatever the creator designed it to do. For example, Figure 3.1 shows a virus attached to a .zip file. The virus sender uses a common ploy: purported naked pictures of his wife. This ploy lures a naive computer user into clicking and therefore running the attached infected file.
The bad news about viruses is that there’s no foolproof method of preventing them from attaching themselves to computers, no matter how skilled you are as a security professional. Many antivirus software packages are available, but none can guarantee protection because new viruses are created constantly. Antivirus software compares signatures (programming code) of known viruses against signatures of every file on a computer; if there’s a match, the software warns you that the program or file is infected. These signatures are kept in a virus signature file that the antivirus software maintains. If the virus isn’t known, however, the antivirus software doesn’t detect a match. Therefore, updating virus signature files regularly is crucial. Many antivirus software packages offer automatic updates. For example, with Symantec Antivirus, administrators can configure a server that handles pushing antivirus updates to client computers in an organization.
Figure 3.1
A virus attached to an e-mail message
Courtesy Course Technology/Cengage Learning
Table 3.1 Common computer viruses

Table 3.1 shows some common viruses that have plagued computer systems. As of this writing, thousands more viruses are being created. Listing all known viruses would take up this entire book.
It seems that many people have nothing but time on their hands to create these destructive programs. The following warning was sent to a user with a file called Price.cpl attached to the e-mail. The e-mail provider rejected sending the e-mail because the attachment was recognized as a potential virus.
This message was created automatically by mail delivery software. A message that you sent could not be delivered to one or more of its recipients. This is a permanent error. The following address(es) failed: [email protected] This message has been rejected because it has a potentially executable attachment "Price.cpl" This form of attachment has been used by recent viruses or other malware. If you meant to send this file then please package it up as a zip file and resend it. [Message header deleted for brevity] boundary="-----sghsfzfldbjbzqmztbdx"------sghsfzfldbjbzqmztbdx Content-Type: text/html; charset="us-ascii" Content-Transfer-Encoding: 7bit <html><body> :)) <br> </body></html> ------sghsfzfldbjbzqmztbdx Content-Type: application/octet-stream; name="Price.cpl" Content-Transfer-Encoding: base64 Content-Disposition: attachment; filename="Price.cpl" TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZS BydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAA+kgUEAAAAAAAAAAOAADi ELAQUMAAwAAAACAAAAAAAAQBUAAAAQAAAAIAAAAAAAEAAQAAAAAgAABAAAAAAAAAA [Several pages of code cut for brevity] GWxWigppFLPigOA6Iqb3ZYDSw1XilsV7d6oVtwKiyKmr4PDWUmgExWU6UOIHF6MK1Qp BexfKQoD6cNpr9elby7KaodMn9OajUYhI89GZ0TN1mpSHgZTXY+Ahx+NCkmcrKuwkr AHpUVFB13SzE3uIwvTQoZEU9kN6Jqsm2aMnsyrFibrBp4voRwv6diDqGfRRpprwZKA K8lF1dMNaqmBlOzbkAzqZeKAnWDoGm7rx4WJEJhMA9PhmgRULBlwHJRNbDESZCWNBUu WgAVvQ8Mh6RWTpNRT7tllLaWqwF8XoKZZ4BJtxGGnYWZS3Qvoj4DEJVZJY4VqlpzFVj GZFe7gINFdmEHhFKduVyiMbZqwZozp0oUqm44BwNnDx+YEZYpVZIGd5ytonizncRDYI6 aY14sJlkIhC8uQT6yVW9EFBhFrTszSoYRJY5DJzdgtKiJfTULswC+f10GAJoTiQZvFliar pRse0S+nQVQjF2SjKFNHjekwmQ3fbhSL4K+DxCtZDpLBWyncpWdFChbAbQzNSOxODu PwqoJCotamiRfBAUTFnCeGgaFs4MZo3OGKKBUJkCEFGV5vWeVRCxHKzwYIm2SRFN4Xl EgeAEaPg5iBXhMFxqQGi4GOXYh xmW2jGiqvmGWxZQFXJcSwYMUoo8CDWGbbw= =
This cryptic code has been encoded in base 64. As you learned in Chapter 2, base 2 (binary), base 8 (octal), and base 16 (hexadecimal) are common numbering systems that computers use. Base 64 is another one you should know. Typically, it’s used to reduce the size of e-mail attachments. Valid characters for base 64 are shown in the following chart:

To represent 0 to 63 characters, you need only 6 bits, or 26. So the binary representation of the letter A is 000000, B is 000001, C is 000010, and so on. Z is represented as 011001. Just remember that the high-order bit is the 32 column, not the 128 column, as with 8 bits. The lowest number you can represent with 6 bits is 000000 (0), and the highest number is 111111 (63). To convert a base-64 number to its decimal equivalent, simply break the sequence into groups of four characters, and represent each character by using 6 bits (24 bits = 6 × 4).
To see how this works, take a look at a simple example. To convert the base-64 string SGFwcHkgQmlydGh-kYXk = into its decimal equivalent, you use the following steps. In this example, the first four characters—S, G, F, and w—are written as three 8-bit numbers (24 bits = 3 × 8).
1. Convert the decimal value of each letter to binary:
S = 18 decimal, binary 010010
G = 6 decimal, binary 000110
F = 5 decimal, binary 000101
w = 48 decimal, binary 110000
2. Rewrite the four binary groups into three groups of 8 bits. For example, starting with the lower-order bit of the binary equivalent of w, writing from right to left produces [01]110000. The bracketed binary numbers represent the first two lower-order bits from the F binary equivalent, 1 and 0: 01001000 01100001 01110000
3. Convert the binary into its decimal equivalent:
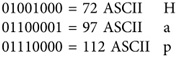
Repeat Steps 1 to 3 for the next four base-64 numbers, cHkg, until each letter’s base-64 number is converted. (One or two equal signs are used when 3 bytes [24 bits] aren’t needed to represent the integer.) What does the base-64 string convert to? Your answer should be “Happy Birthday.”
Base-64 decoders are available for purchase at retail outlets and online. As a security professional, you don’t need to know how to convert base-64 code manually, but it’s important to see how numbering systems are used in practical applications.
Running a base-64 decoder on the Price.cpl code reveals the following suspicious programming code:
This program cannot be run in DOS mode. user32.dll CloseHandle() CreateFileAb GetWindowsDirectory WriteFile strcat kernel32.dll Shell Execute shell32 KERNEL32.DLL USER32.DLL GetProcAddress LoadLibrary ExitProcess Virtual FreeMessageBox
This code shows something suspicious happening that’s contained in an attachment. The first line, “This program cannot be run in DOS mode,” identifies the text that follows as a program, which alerts you that the e-mail attachment contains a hidden computer program. In the third line, a shell being executed adds to the suspicious nature of the Price.cpl attachment. A shell is an executable piece of programming code that creates an interface to an OS for issuing system commands and shouldn’t appear in an e-mail attachment. References to User32.dll and especially Kernel32.dll should also raise a red flag because dynamic link library (DLL) files are executables. In addition, Kernel32.dll is responsible for memory management and I/O operations, so a reference to this file in an e-mail attachment should raise more than a red flag; it should raise your blood pressure! You can see that the e-mail provider’s rejection of this e-mail was valid.
Activity 3.1: Identifying New Computer Viruses and Worms
Time Required: 30 minutes
Objective: Examine some current computer virus threats.
Description: As a security professional, you must keep abreast of the many new viruses and worms that might attack networks and computers. If one computer is compromised, all computers in your network could be compromised. Many firewalls don’t detect malware attached to an executable program or a macro virus (covered later in this section), so security professionals need to train users on the dangers of installing software, including games and screen savers, on a computer. Remember, a firewall doesn’t examine packets internal to the network, so malware can spread internally in an organization regardless of how effective the firewall is. A good place to learn about new threats is the Internet.
1. Start your Web browser, and go to www.us-cert.gov.
2. On the home page, type Conficker Worm in the Search US-CERT text box, and then click the GO button. What OSs are affected by this worm?
3. Give a brief description of the Conficker worm and ways to remove it or prevent infection from it.
4. Next, go to www.symantec.com.
5. On the Symantec home page, click the View All Viruses And Risks link.
6. List the five most recent viruses or worms displayed on this page.
7. Select one of the viruses or worms you listed in Step 6, and describe its technical details briefly. Are any solutions for removing the virus or worm available? If so, what are they?
8. Leave your Web browser open for the next activity.
Security Bytes
Security professionals have many resources for finding information on current vulnerabilities or possible network attacks. You can visit many excellent Web sites to learn about OS and application vulnerabilities. One site that should be bookmarked in any security professional’s Web browser is the Mitre Corporation’s Common Vulnerabilities and Exposures site at www.cve.mitre.org. Other helpful sites are www.osvdb.org, www.packetstormsecurity.com, http://archives.neohapsis.com, www.neworder.box.sk/, www.securityfocus.com, Microsoft Security Bulletins (www.microsoft.com/security/bulletins/default.mspx), www.kb.cert.org/vuls, and, of course, www.google.com.
By identifying all the vulnerabilities associated with a customer’s OSs and applications, you can determine which type of attack to use on a network when conducting a security test. You might also discover a vulnerability associated with a different OS that could be used to compromise your client’s OS. Remember to think outside the box. Security testing is more than memorizing tools and rules; it relies heavily on creativity and imagination.
Note
No standard definitions of terms are currently available in the computer security field. Hence, security professionals sometimes use the terms “vulnerability” and “exposure” interchangeably. In this book, for the sake of simplicity, the terms are used in the broad sense to mean a flaw in a protection process that an unauthorized person might take advantage of. One difficulty in writing a book on network security is the varying terminology that professionals use. The Open Source Security Testing Methodology Manual (OSSTMM) attempts to solve this problem, but until all professional organizations adopt one standard, ambiguity will prevail.
Macro Viruses
A macro virus is a virus encoded as a macro in programs that support a macro programming language, such as Visual Basic for Applications (VBA). For example, you can write a macro, which is basically a list of commands, in Microsoft Word that highlights a document’s contents (Ctrl+A), copies the selected data (Ctrl+C), and then pastes the information into a different part of the document (Ctrl+V). Macro commands that open and close files, however, can be used in destructive ways. These commands can be set to run automatically as soon as a file is opened or clicked on, as in an e-mail attachment. The most infamous macro virus is Melissa, which appeared in 1999. It was initiated after a user opened an infected document; the virus then sent an e-mail message to the first 50 entries it located in the infected computer’s address book.
In the past, viruses were created by programmers who found the challenge of creating a destructive program rewarding. Today, even nonprogrammers can create macro viruses easily. In fact, anyone with Internet access can find many Web sites to learn how to create a macro virus step by step. This easy access adds to the problems you must deal with as a security professional. It’s helpful to put yourself in computer criminals’ frame of mind and, like an FBI profiler, try to understand how they think. A good place to start is visiting Web sites of virus creators and seeing what they have to say. For example, a Google search for “Macro Virus Tutorial” directs you to many different Web sites. The following excerpt was taken from http://web.textfiles.com/virus/mactut.txt :
Caution
Connecting to sites that offer hacking tools or information on creating viruses can be dangerous. Many of these sites contain Trojan programs and viruses that might compromise your computer.
LEGALESE ----------- I SHALL NOT BE HELD RESPONSIBLE FOR ANY DAMAGE CREATED BE IT DIRECT OR INDIRECT USE OF THE PUBLICISED MATERIAL. THIS DOCUMENT IS COPYRIGHT 1996 TO ME, DARK NIGHT OF VBB. HEREWITH I GRANT ANYBODY LICENSE TO REDISTRIBUTE THIS DOCUMENT AS LONG AS IT IS KEPT IN WHOLE AND MY COPYRIGHT NOTICE IS NOT REMOVED. SO IF I FIND ANY LAMERS WHO JUST TAKE THE CODE PUBLISHED HERE AND SAY IT IS THEIR OWN I WILL SEE THAT THEY'LL BE PUNISHED. (BELIEVE IT OR NOT :-))!!! INTRODUCTION ---------- MANY OF YOU MAY BE WONDERING RIGHT NOW WHO I AM AND WHO VBB IS. COME ON LAMERS! GET ALIVE. VBB IS ONE OF THE COOLEST VIRUS GROUPS AROUND. YOU CAN'T TELL ME YOU'VE NEVER HEARD OF US. WELL, OK I'LL ADMIT IT. WE'RE NOT THAT POPULAR YET, BUT THAT'LL COME. SO FOR NOW HERE'S MY CONTRIBUTION TO THE GROUP AS THE LEADER. WELCOME TO THE MACROVIRUS WRITING TUTORIAL PART 1! ENJOY!! THE TOOLS ---------- FIRST OF ALL YOU'LL NEED MS WORD 6.0 OR UP (DUH), THEN YOU MAY WANT TO GET VBB'S MACRO DISASSEMBLER BY AURODREPH SO THAT YOU CAN STUDY ENCRYPTED MACROS. ALSO YOU SHOULD MAKE BACK-UPS OF YOUR NORMAL.DOT TEMPLATE IN YOUR WINWORD6TEMPLATE DIRECTORY, AS THIS IS THE DOCUMENT COMMONLY INFECTED BY MACRO VIRII. SO WATCH OUT. ALSO I RECOMMEND TO HAVE AT LEAST A SMALL KNOWLEDGE OF WORD BASIC, SO THAT YOU KIND A KNOW WHAT'S GOING ON. WELL, THAT'S IT. YOU'VE MADE IT THIS FAR. IT'S NOW TIME TO GET INTO THE MACRO VIRUS GENERALS....
The rest of the document was deleted because of space constraints. However, you can see that finding information on creating a macro virus is all too easy.
Activity 3.2: Identifying Macro Viruses
Time Required: 30 minutes
Objective: Examine current macro viruses that are threats to users.
Description: Many antivirus programs detect macro viruses, so you need to know how to turn off the feature that enables macros to run automatically without prompting the user first. You should also be aware of new macro viruses. Again, the Internet is an excellent resource.
1. Start your Web browser, if necessary, and go to www.google.com.
2. Type macro virus in the text box, and click the Google Search button.
3. List some of the current macro viruses your search returned.
4. Select one of the macro viruses you listed in Step 3. Use the name of the macro to search for more information about the virus. Are any fixes available?
5. Begin a new Google query by entering macro virus tutorial in the text box at the top and clicking Search. Did you locate any sites with instructions on creating a macro virus? If not, try the search again with a different macro name.
6. Read the tutorial information on a site you discovered in Step 5. Does creating a macro virus seem difficult or easy?
7. Leave your Web browser open for the next activity.
Worms
A worm is a program that replicates and propagates itself without having to attach itself to a host (unlike a virus, which needs to attach itself to a host). The most infamous worms are Code Red (covered in Activity 3.3), Nimda, and Conficker. Theoretically, a worm that replicates itself multiple times to every user it infects can infect every computer in the world over a short period. This result is unlikely, but as with many pyramid schemes, it’s easy to see how a worm can propagate throughout an entire network and even across the Internet.
Table 3.2 describes some of the most infamous worms that have cost businesses millions of dollars as a result of lost productivity caused by computer downtime and time spent recovering lost data, reinstalling programs and operating systems, and hiring or contracting IT personnel. Security professionals are also working to protect automated teller machines (ATMs) from worm attacks, such as the Slammer and Nachi worms. Cyberattacks against ATMs are a serious concern for the banking industry and law enforcement agencies worldwide.
Table 3.2 Common computer worms

Activity 3.3: Identifying the Code Red Worm
Objective: Examine the Code Red worm.
Description: The Code Red worm wreaked havoc on networks. As a security professional, you should be aware of past attacks because history often repeats itself.
1. Start your Web browser, if necessary, and go to www.google.com.
2. Type Code Red in the text box, and click Google Search.
3. If the search doesn’t list CERT Advisory as the first site, change your search to look specifically for CA-2001-19.
4. What vulnerability did the worm use to propagate itself?
5. What port did Code Red use to connect to the attacked server?
6. Did the worm deface or destroy any Web pages?
7. What solutions were offered for infected computers?
8. Leave your Web browser open for the next activity.
Trojan Programs
One of the most insidious attacks against networks and computers worldwide takes place via Trojan programs, which disguise themselves as useful programs and can install a backdoor or rootkit on a computer. Backdoors or rootkits are programs that give attackers a means of regaining access to the attacked computer later. A root-kit is created after an attack and usually hides itself in the OS tools, so it’s almost impossible to detect. Back Orifice is still one of the most common Trojan programs used today. It allows attackers to take full control of the attacked computer, similar to the way Windows XP Remote Desktop functions, except that Back Orifice works without the user’s knowledge. The program has been around since 1999, but it’s now marketed as an administrative tool rather than a hacking tool. Table 3.3 lists some ports that Trojan programs use.
The programmer who wrote Backdoor.Slackbot.B, for example, can control a computer by using Internet Relay Chat (IRC), which is on port 6667. A good software or hardware firewall would most likely identify traffic that’s using unfamiliar ports, but Trojan programs that use common ports, such as TCP port 80 (HTTP) or UDP port 53 (DNS), are more difficult to detect. Also, many home users and small businesses don’t use software or hardware firewalls.
Table 3.3 Trojan programs and ports

Security Bytes
Many software firewall products for home users do a good job of recognizing port-scanning programs or detecting connection attempts from a computer via a questionable port, such as port 6667. However, many of these firewalls prompt users to allow or disallow this traffic. The problem is that users who aren’t aware of these Trojan programs simply click Allow when warned about suspicious activity on a port. Also, many Trojan programs use standard ports to conduct their exploits, which makes it difficult for average users to distinguish between suspicious activity and normal Internet traffic. You should educate network users about these basic concepts if there’s no corporate firewall or a corporate policy establishing rules and restrictions.
Spyware
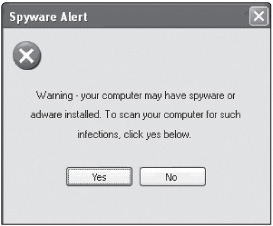
If you do a search on the keyword “spyware,” you’ll be bombarded with hundreds of links. Some simply tout spyware removal, but some install spyware on a computer when the user clicks the Yes button in a dialog box asking whether the computer should be checked for spyware (see Figure 3.2). When you click the Yes button, the spyware installation begins.
Figure 3.2
A spyware initiation program
Courtesy Course Technology/Cengage Learning
A spyware program sends information from the infected computer to the person who initiated the spyware program on your computer. This information could be confidential financial data, passwords, PINs—just about any data stored on your computer. You need to make sure users understand that this information collection is possible, and spyware programs can register each keystroke entered. It’s that simple. This type of technology not only exists but is prevalent. It can be used to record and send everything a user enters to an unknown person located halfway around the world. Tell users they shouldn’t assume that physical security measures, such as locked doors, are enough to keep all intruders out.
Activity 3.4: Identifying Spyware
Time Required: 30 minutes
Objective: Examine prevalent spyware programs.
Description: Network security professionals know that spyware is one of the worst types of malicious attacks on corporate networks. Spyware can be installed on any computer through various means; the most common approach is installing spyware automatically after a user clicks a hyperlink or runs a program without verifying its authenticity. You should be aware of any new spyware programs as well as software that can remove spyware from a computer.
1. Start your Web browser, if necessary, and go to www.google.com. Type spyware in the text box, and click Google Search.
2. List some of your search results.
3. Write a description of spyware based on one of the sites you listed in Step 2.
4. In your Web browser, go to www.spywareguide.com. On the home page, click the Spyware-Guide Product Database link.
5. Click one of the links you found in Step 4, and write a brief description of the spyware. (Note: The list is in alphabetical order; you can scroll through it with the arrow keys.)
6. Leave your Web browser open for the next activity.
Adware
The difference between spyware and adware is a fine line. Both programs can be installed without users being aware of their presence. Adware, however, sometimes displays a banner that notifies users of its presence. Adware’s main purpose is to determine a user’s purchasing habits so that Web browsers can display advertisements tailored to this user. The biggest problem with adware is that it slows down the computer it’s running on.
Security Bytes
Network security begins with each user understanding how vulnerable a computer is to attack. However, being aware of malware’s presence, just as you’re aware of unscrupulous telemarketers who call you during dinnertime, can better equip you to make valid decisions. If someone offers to sell you property in Tahiti for $99.95 over the phone and asks for your credit card number, you’d refuse. Computer users should be just as skeptical when prompted to click an OK button or install a free computer game.
PROTECTING AGAINST MALWARE ATTACKS
Protecting an organization from malware attacks is difficult because new viruses, worms, and Trojan programs appear daily. Fortunately, antivirus programs can detect many malware programs. For example, Figure 3.3 shows McAfee antivirus software detecting a potentially unwanted program. Educating users about these types of attacks and other attacks, covered later in this section, is also important. After all, users can’t be patched. Antivirus programs can mitigate some risks associated with malware, but users who aren’t trained thoroughly can open holes into a network that no technology can protect against.
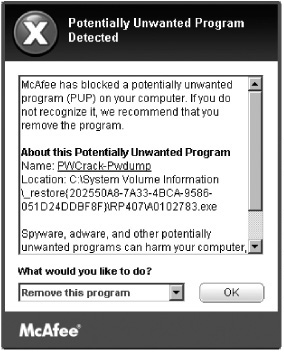
Courtesy Course Technology/Cengage Learning
Educating Your Users
No matter how hard you try to protect a network from malware being introduced, the most effective approach is conducting structured training of all employees and management. In fact, many U.S. government agencies make security awareness programs mandatory, and many private-sector companies are following their example. A simple but effective method of educating users is e-mailing monthly security updates to all employees to inform them of the most recent viruses, spyware, and adware detected on the Internet.
To help prevent viruses from being introduced into corporate networks, the most important recommendation you should make to a client is to update virus signature files as soon as they’re available from the vendor. Most antivirus software does this updating automatically or prompts the user to do so. An organization can’t depend on employee vigilance to protect its systems, however, so centralizing all antivirus updates from a corporate server is prudent.
To counter the introduction of spyware and adware into a corporate network, you might need to download additional software from the Internet. Many antivirus packages don’t fully address the problem of spyware and adware. As of this writing, the two most popular spyware and adware removal programs are SpyBot and Ad-Aware. Both are free and easy to install and can be downloaded from www.pcworld.com/downloads. Many other Web sites offer these programs, but remember to use caution when downloading any programs from unknown Web sites.
You can also help protect a network by installing a firewall (covered in more detail in Chapter 13). Many of the top antivirus vendors also offer software firewalls for home and small-business users who don’t have a hardware firewall or an intrusion detection system (IDS) installed. Companies using firewalls can follow the vendor’s configuration instructions. For example, the W32/Sobig.F worm uses UDP port 8998 to contact the attacker’s server. By blocking all outbound traffic on this port, you can prevent this attack from occurring. Also, many services are started by default on a computer, and they don’t need to be. For example, the average home user or small-business owner doesn’t typically use Telnet. This service shouldn’t be active on most computers because it’s vulnerable to many outside attacks.
Avoiding Fear Tactics
You’d be surprised how many users don’t know that clicking an icon in an e-mail message can activate a virus or Trojan program or allow another person to access their computers from a remote location. Consequently, some security professionals use fear tactics to scare users into complying with security measures. Their approach is to tell users that if they don’t take a particular action, their computer systems will be attacked by every malcontent who has access to the Internet. This method is sometimes used to generate business for security testers and is not only unethical, but also against the OSSTMM’s Rules of Engagement (included with the manual on this book’s online resources). The rule states: “The use of fear, uncertainty, and doubt may not be used in the sales or marketing presentations, websites, supporting materials, reports, or discussion of security testing for the purpose of selling or providing security tests. This includes but is not limited to crime facts, criminal or hacker profiling, and statistics.”
Your approach to users or potential customers should promote awareness rather than instill fear. You should point out to users how important it is not to install programs—especially those not approved by the company—on their desktops because of the possibility of introducing malware. Users should be aware of potential threats, not terrified by them.
In addition, when training users, be sure to build on the knowledge they already have. For example, some users are familiar with Windows XP Remote Assistance or other remote control programs, such as Symantec pcAnywhere. Users’ experience with these programs makes the job of explaining how an intruder can take control of their computers easier because they already know the technology is available.
INTRUDER ATTACKS ON NETWORKS AND COMPUTERS
An attack is defined as any attempt by an unauthorized person to access, damage, or use network resources or computer systems. Network security is concerned with the security of computers or devices that are part of a network infrastructure. Computer security is defined as securing a stand-alone computer that’s not part of a network infrastructure. The FBI, CIA, and Interpol warn that computer crime is the fastest growing type of crime worldwide. After all, attacking a corporate network from the comfort of home is much easier than breaking into a business at 3:00 a.m. Speaking on the subject of the difficulty of prosecuting computer criminals, FBI agent Arnold Aanui, Jr., from the Honolulu FBI Cybercrime Division stated in an interview: “Even if the FBI tracks down the computer used in a crime, if more than one person has access to that computer, the FBI can’t arrest the alleged perpetrator because any one of the users might have committed the crime.” Until the laws change so that the punishment for committing these crimes becomes more of a deterrent, security professionals will be busy for many years.
Security Bytes
Not too long ago, in an affluent neighborhood in Hawaii, the FBI stormed into a quiet residential home with warrants in hand, prepared to arrest the occupant and confiscate his desktop computer, which was alleged to contain records of drug transactions and other incriminating evidence. While FBI personnel were cautiously entering the front of the house, they heard a gunshot from a rear bedroom. When they entered the room, they saw a man seated on the bed and a 12-gauge shotgun leaned against a closed door. He had just emptied a round into the computer, destroying the hard drives so thoroughly that the data couldn’t be recovered. The FBI agents could have tried sending the disks to a lab that specialized in data recovery from hard disks but decided not to because they believed they had enough evidence from other sources.
Denial-of-Service Attacks
As the name implies, a denial-of-service (DoS) attack prevents legitimate users from accessing network resources. Some forms of DoS attacks don’t even involve computers. For example, intentionally looping a document on a fax machine by taping two pages together can use up reams of paper on the destination fax machine, thus preventing others from using it. In a DoS attack that does involve computers, attackers aren’t attempting to access information from servers. However, they might be using the attack to cripple the network until it’s vulnerable to a different type of attack.
As a security tester, you don’t usually install a virus or worm on a customer’s computer as part of your testing. Similarly, you should know how a DoS attack can take place and attempt to protect a company from it, but conducting the attack yourself isn’t wise. Doing so would be like a safety consultant blowing up a refinery after being hired to look for safety hazards. You simply need to explain how the attack could be carried out.
Distributed Denial-of-Service Attacks
A distributed denial-of-service (DDoS) attack is launched against a host from multiple servers or workstations. In a DDoS attack, a network could be flooded with literally billions of packets; typically, each participant in the attack sends only a few of the total number of packets. If one server bombards an attacked server with hundreds or even thousands of packets, available network bandwidth could drop to the point that legitimate users notice a performance degradation or loss of speed. Now imagine 1000 servers or even 10,000 servers involved, with each server sending several thousand IP packets to the attacked server. There you have it: a DDoS attack. Keep in mind that participants in the attack often aren’t aware their computers are taking part in the attack. They, too, have been attacked by the culprit. In fact, in one DDoS attack, a company was flooded with IP packets from thousands of Internet routers and Web servers belonging to Yahoo.com.
Security Bytes
Security professionals will be studying one of the world’s most widespread DDoS attacks for years. Estonia, in Northern Europe, fell victim to a DDoS attack in 2007 that shut down government Web sites, banks, and other financial institutions. The malicious traffic came from all over the world, including the United States and Canada. DDoS attacks are difficult to stop because owners of the compromised computers, referred to as zombies, are unaware that their systems are sending malicious packets to a victim thousands of miles away. These compromised computers are usually part of a botnet (a network of “robot” computers) following instructions from a central location or system. For more information, do a search on “Estonia DDoS.”
Buffer Overflow Attacks
A number of buffer overflow attacks on many different OSs have taken place over the years. In a buffer overflow attack, a programmer finds a vulnerability in poorly written code that doesn’t check for a defined amount of memory space use. For example, if a program defines a buffer size of 100 MB (the total amount of memory the program is supposed to use), and the program writes data over the 100 MB mark without triggering an error or preventing this occurrence, you have a buffer overflow. Basically, the attacker writes code that overflows the buffer, which is possible because the buffer capacity hasn’t been defined correctly in the program. The trick is to not fill the overflow buffer with meaningless data, but fill it with executable program code. That way, the OS runs the code, and the attacker’s program does something harmful. Usually, the code elevates the attacker’s permissions to an administrator’s level or gives the attacker the same privileges as the program’s owner or creator. Table 3.4 describes some current buffer overflow vulnerabilities.
In defense of programmers, many aren’t trained to write programs with computer security in mind. In the past, programs were written for ease of use and to create efficient executable code that ran quickly and used as few computer resources as possible. Today, the trend is to make sure programmers are aware of how their code might be vulnerable to attack, but checking for security vulnerabilities as a standard practice still isn’t widespread. Most universities don’t offer courses on writing programs with security in mind. At Microsoft, programmers are now rewarded for writing code that doesn’t show up later as a vulnerability in the system. In Activity 3.5, you take a look at some software with vulnerabilities caused by overlooking the security factor in their program design.
Table 3.4 Buffer overflow vulnerabilities


Activity 3.5: Identifying Software Vulnerabilities
Time Required: 30 minutes
Objective: Examine some vulnerabilities released by the U.S. Computer Emergency Readiness Team (US-CERT).
Description: As a security professional conducting a security test on a customer’s network, you need to investigate any vulnerabilities that might be exploited. After discovering vulnerabilities that might affect a client’s network, you must create documentation of your findings and make recommendations to correct the problem. In this activity, you examine vulnerabilities reported by US-CERT and learn what solutions or recommendations you might give to customers.
1. Start your Web browser, if necessary, and go to www.us-cert.gov.
2. On the Welcome to US-CERT home page, click the Technical Security Alerts link in the section “National Cyber Alert System.”
3. Click the first link, and note the description and release date of the vulnerability as well as the operating systems or programs it affects.
4. What recommendations would you give to someone whose system had been exploited because of this vulnerability?
5. Click the Web browser’s back button to return to the Technical Cyber Security Alerts page.
6. Scroll down the document and find several entries that discuss buffer overflow vulnerabilities. How is this type of vulnerability exploited?
7. Exit your Web browser.
The previous activity gives you insight into software vulnerabilities used to exploit an OS. Usually, a buffer overflow’s main purpose is to insert code into the overwritten area of memory that elevates the attacker’s permissions.
Ping of Death Attacks
The Ping of Death attack, a type of DoS attack, is not as common as it was during the late 1990s. The attacker simply creates an ICMP packet (discussed in Chapter 2) that’s larger than the maximum allowed 65,535 bytes. The large packet is fragmented into smaller packets and reassembled at its destination. The user’s system at the destination point can’t handle the reassembled oversized packet, thereby causing the system to crash or freeze.
Session Hijacking
Session hijacking enables an attacker to join a TCP session and make both parties think he or she is the other party. This attack, discussed briefly in Chapter 2 in relation to initial sequence numbers (ISNs), is a complex attack that’s beyond the scope of this book.
ADDRESSING PHYSICAL SECURITY
Protecting a network from attacks is not always a software issue. You should have some basic skills in protecting a network from physical attacks as well. No matter how effective your firewall is, you must secure servers and computers from an attack from within the organization. In fact, there’s a higher chance that an attacker who breaks into the network is from inside the company rather than outside.
Security Bytes
On a military base in Hawaii, a pickup truck parked in front of an office building, and the driver entered the building and walked into an empty office. He disconnected a computer from the network, carried it out of the office, placed it in the truck’s flatbed, and drove off, never to be seen again. When upper management questioned the staff, employees said they remembered seeing someone walking out of the building with the computer but assumed he was a help desk employee. Physical security is only as strong as the weakest link. All employees need to be aware of what’s happening in their work environment. For example, if they notice a stranger sitting in front of a computer downloading files, they should contact security and then confront the person. Employees should be vigilant and not depend on security personnel alone to pay attention.
Keyloggers
Keyloggers are hardware devices or software that can be used to capture keystrokes on a computer. Software keyloggers behave like Trojan programs and are loaded on a computer. A hardware keylogger is a small device, often smaller than an inch long. It can usually be installed in less than 30 seconds. It’s a simple matter of unplugging the keyboard, plugging the small device into the keyboard input jack, and then plugging the keylogger jack into the computer’s keyboard port. After installing the hardware, most vendors require you to run a word processing program, such as WordPad, and then enter the vendor-supplied password in a blank document. After entering the password, a menu is displayed. Some common hardware keyloggers are KeyKatcher and KeyGhost. In Figure 3.4, the KeyKatcher keylogger program captured a private message sent in an e-mail; the sender is informing Bob that he’s going to quit his job. If you’re conducting a security test on a system and need to obtain passwords, keyloggers can be a helpful tool. Of course, you should have written permission from the client before using software or hardware keyloggers.
Most keylogger products display similar menus for capturing keystrokes the user enters. Figure 3.5 shows the menu in KeyGhost, which has more storage area for capturing data than KeyKatcher. These products can be quite useful when conducting a security test or penetration test for a company and can be installed and configured in a few minutes. KeyKatcher and KeyGhost were created for companies or even parents who want to monitor computers. Both include a plastic, tubelike covering that can be melted with a lighted match onto the connection so that the user can’t unplug the unit before conducting questionable activity on the computer.
Figure 3.4
An e-mail message captured by KeyKatcher

Courtesy Course Technology/Cengage Learning
Unfortunately, attackers can also use keylogger devices. An unscrupulous employee can connect a keylogger to a manager’s computer and retrieve confidential information later. Installing this device does require access to the computer, which might pose a problem if the manager’s office is locked. However, as mentioned, keyloggers are also available as software (spyware) that’s loaded on a computer, and retrieved information can be e-mailed or transferred to a remote location.
When doing random visual tests of computers in your organization, keep an eye out for any suspicious hardware attached to the keyboard cable that wasn’t installed by security personnel. This check is a simple way to monitor for keyloggers (or even computer systems) that the company didn’t install.

Courtesy Course Technology/Cengage Learning
Behind Locked Doors
As a security professional, you should be aware of the types of locks used to secure a company’s assets. If an intruder gets physical access to a server, whether it’s running Linux, Windows, or another OS, it doesn’t matter how good your firewall or IDS is. Encryption or public key infrastructure (PKI) enforcements don’t help in this situation, either. If intruders can sit in front of your server, they can hack it. Simply put, lock up your server.
In the same way that terrorists can learn how to create a bomb by doing Internet research, attackers can find countless articles about lock picking. One paper, “MIT Guide to Lock Picking” by an author calling himself Ted the Tool (www.lysator.liu.se/mit-guide/MITLockGuide.pdf), discusses the vulnerabilities of tumbler locks. After a week or two of practice, the average person can learn how to pick a deadbolt lock in less than 5 minutes. Those who have more time on their hands, such as hackers, can learn to pick a deadbolt lock in under 30 seconds. If you’re responsible for protecting a network infrastructure that has night-shift workers, don’t assume that locked doors or cabinets can keep out unscrupulous employees with time on their hands. Typically, fewer employees are around during non-standard business hours, which makes it easier for them to get into areas to which they might not normally have access. Your server room should have the best lock your company can afford. Take the time to look into locks that organizations such as the Department of Defense use, where protecting resources might be a life-or-death situation. Spending $5000 to $10,000 on a lock isn’t unheard of in these organizations.
Rotary locks that require pushing in a sequence of numbered bars are more difficult to crack than deadbolt locks. However, neither lock type keeps a record of who has entered the locked room, so some businesses require using card access for better security. With this method, a card is scanned, and access is given to the cardholder while documenting the time of entry. This method also makes it possible for one card to allow access to several doors without having to issue multiple keys or having users memorize different combinations.
Security Bytes
Some legitimate sites offer tools and manuals on lock picking for police or security professionals. You might have to fill out some forms, but it could be worth your while if you plan to become a security professional. For example, if you’re conducting a security test on an organization that has a locked server room and you want to gain access, knowing how to pick a lock could be beneficial. Remember, however, that you must get written permission from management before conducting this level of testing.
Caution
Most police officers take a class to learn the basics of lock picking. When ordering lockpicking tools, be aware that many states or countries consider the mere possession of these tools a crime, as mentioned in Chapter 1. Remember that possession of certain hacking tools is also illegal.
CHAPTER SUMMARY
![]() Security professionals must be aware of attacks that can take place on both network infrastructures and stand-alone computers.
Security professionals must be aware of attacks that can take place on both network infrastructures and stand-alone computers.
![]() Network and computer attacks can be perpetrated by insiders as well as outside attackers.
Network and computer attacks can be perpetrated by insiders as well as outside attackers.
![]() Malicious software (malware), such as viruses, worms, and Trojan programs, can attack a network or computer. A virus attaches itself to a host. A worm can replicate and propagate itself without attaching itself to a host. A Trojan program disguises itself as a useful program or application and can install a back-door or rootkit on a computer.
Malicious software (malware), such as viruses, worms, and Trojan programs, can attack a network or computer. A virus attaches itself to a host. A worm can replicate and propagate itself without attaching itself to a host. A Trojan program disguises itself as a useful program or application and can install a back-door or rootkit on a computer.
![]() Users can install spyware programs inadvertently, thinking they’re installing software to protect their computers. Spyware can record information from a user’s computer and send it to the attacker.
Users can install spyware programs inadvertently, thinking they’re installing software to protect their computers. Spyware can record information from a user’s computer and send it to the attacker.
![]() Adware programs can also be installed without users’ knowledge. They’re used to discern users’ buying patterns for the purpose of sending Web advertisements tailored to their buying habits but can slow down a computer system.
Adware programs can also be installed without users’ knowledge. They’re used to discern users’ buying patterns for the purpose of sending Web advertisements tailored to their buying habits but can slow down a computer system.
![]() A denial-of-service (DoS) attack prevents authorized users from accessing network resources. The attack is usually accomplished through excessive use of bandwidth, memory, and CPU cycles.
A denial-of-service (DoS) attack prevents authorized users from accessing network resources. The attack is usually accomplished through excessive use of bandwidth, memory, and CPU cycles.
![]() A distributed denial-of-service (DDoS) is an attack on a host from multiple servers or computers.
A distributed denial-of-service (DDoS) is an attack on a host from multiple servers or computers.
![]() The main purpose of buffer overflows is to insert executable code into an area of memory that elevates the attacker’s permissions to the level of an administrator or the program owner or creator.
The main purpose of buffer overflows is to insert executable code into an area of memory that elevates the attacker’s permissions to the level of an administrator or the program owner or creator.
![]() In a Ping of Death attack, the attacker crafts an ICMP packet to be larger than the maximum 65,535 bytes, which causes the recipient system to crash or freeze. Most systems today aren’t affected by this exploit.
In a Ping of Death attack, the attacker crafts an ICMP packet to be larger than the maximum 65,535 bytes, which causes the recipient system to crash or freeze. Most systems today aren’t affected by this exploit.
![]() In session hijacking, the attacker joins a TCP session and makes both parties think he or she is the other party.
In session hijacking, the attacker joins a TCP session and makes both parties think he or she is the other party.
![]() Keyloggers make it possible to monitor what’s being entered on a computer system. They can be installed on a keyboard connector easily and use a word processing program to store information. Security personnel should conduct random checks of computer hardware to detect these devices.
Keyloggers make it possible to monitor what’s being entered on a computer system. They can be installed on a keyboard connector easily and use a word processing program to store information. Security personnel should conduct random checks of computer hardware to detect these devices.
![]() Physical security is everyone’s responsibility. All desktop systems and servers must be secured.
Physical security is everyone’s responsibility. All desktop systems and servers must be secured.